The Construction of High-Order Robust Theta Methods with Applications in Subdiffusion Models
Abstract
:1. Introduction
- An exponential-type transformation strategy is proposed to transfer any known pth order () time-stepping methods into methods with the same accuracy.
- The robustness of numerical schemes obtained by the exponential-type transformation strategy for a trial equation is examined theoretically and verified numerically.
- Rigorous arguments of the optimal error estimates of the transformed fractional BDF-2 are provided for the subdiffusion Problem (1).
2. Preliminaries
2.1. Review of -Methods in SCQ
2.2. Stability Regions
3. Novel Transformation Strategy
4. Applications
4.1. Formulation of Fully Discrete Scheme
4.2. Optimal Error Estimates
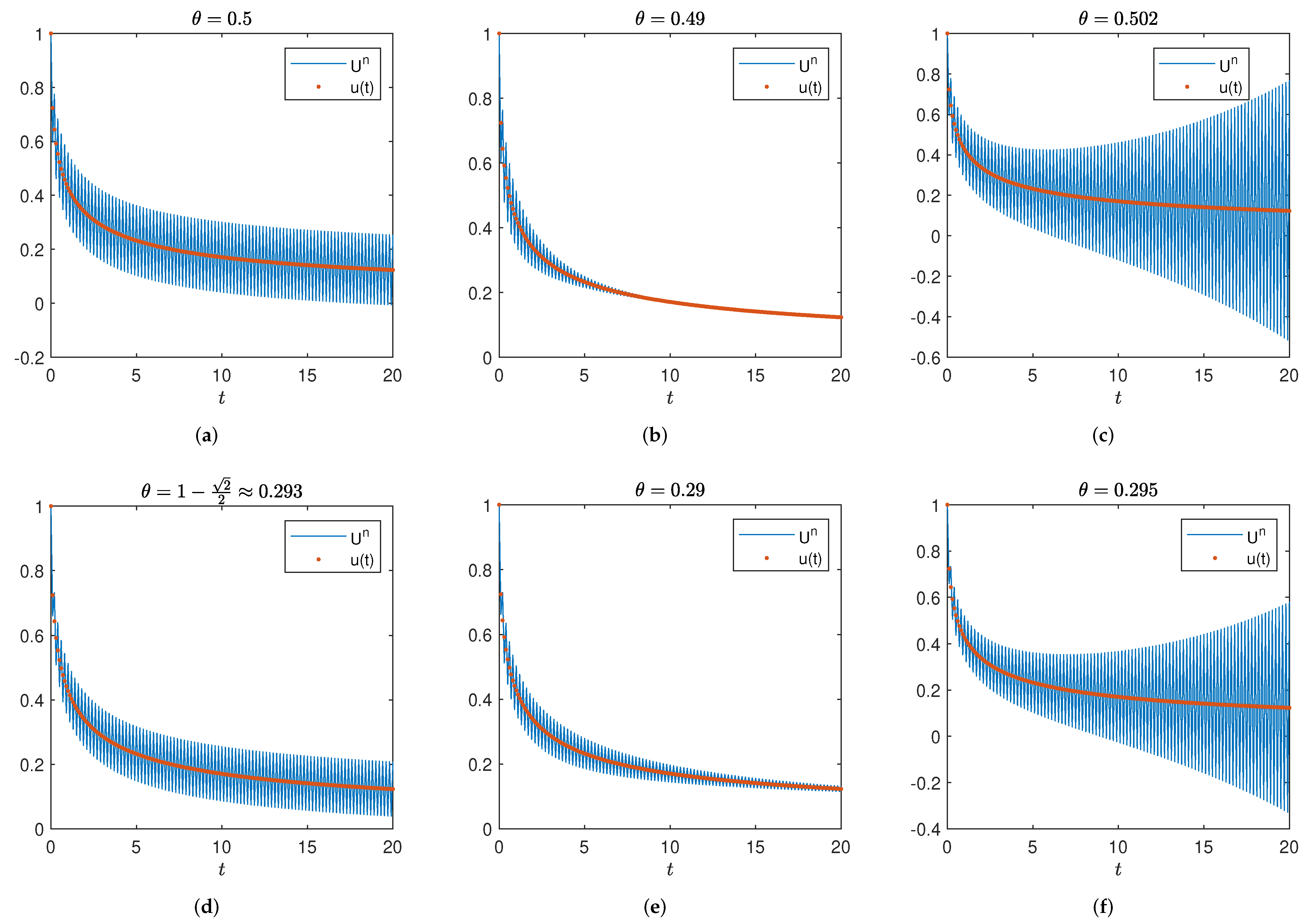
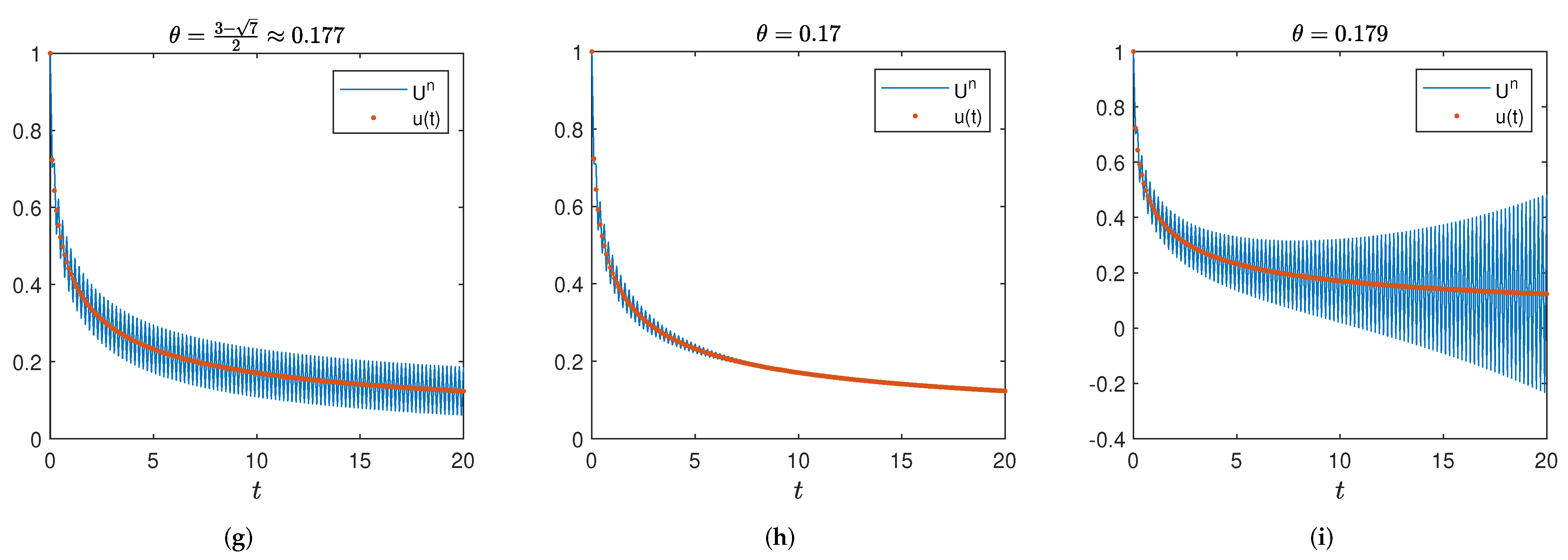
5. Numerical Tests
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| CQ | Convolution quadrature; |
| SCQ | Shifted convolution quadrature; |
| BDF | Backward difference formula. |
Appendix A
Appendix A.1.
Appendix A.2.
Appendix A.3. Schur Polynomial
References
- Jin, B.; Lazarov, R.; Zhou, Z. Numerical methods for time-fractional evolution equations with nonsmooth data: A concise overview. Comput. Methods Appl. Mech. Eng. 2019, 346, 332–358. [Google Scholar] [CrossRef]
- Metzler, R.; Klafter, J. The random walk’s guide to anomalous diffusion: A fractional dynamics approach. Phys. Rep. 2000, 339, 1–77. [Google Scholar] [CrossRef]
- Feng, L.; Turner, I.; Perré, P.; Burrage, K. An investigation of nonlinear time-fractional anomalous diffusion models for simulating transport processes in heterogeneous binary media. Commun. Nonlinear Sci. Numer. Simul. 2021, 92, 105454. [Google Scholar] [CrossRef]
- Povstenko, Y. Linear Fractional Diffusion-Wave Equation for Scientists and Engineers; Springer: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Wyss, W. The fractional diffusion equation. J. Math. Phys. 1986, 27, 2782–2785. [Google Scholar] [CrossRef]
- Podlubny, I. Fractional Differential Equations: An Introduction to Fractional Derivatives, Fractional Differential Equations, to Methods of Their Solution and Some of Their Applications; Elsevier: Amsterdam, The Netherlands, 1998. [Google Scholar]
- Lin, Y.; Xu, C. Finite difference/spectral approximations for the time-fractional diffusion equation. J. Comput. Phys. 2007, 225, 1533–1552. [Google Scholar] [CrossRef]
- Sun, Z.Z.; Wu, X. A fully discrete difference scheme for a diffusion-wave system. Appl. Numer. Math. 2006, 56, 193–209. [Google Scholar] [CrossRef]
- Lubich, C. Discretized fractional calculus. SIAM J. Math. Anal. 1986, 17, 704–719. [Google Scholar] [CrossRef]
- Wang, Z.; Vong, S. Compact difference schemes for the modified anomalous fractional sub-diffusion equation and the fractional diffusion-wave equation. J. Comput. Phys. 2014, 277, 1–15. [Google Scholar] [CrossRef]
- Zeng, F.; Zhang, Z.; Karniadakis, G.E. Second-order numerical methods for multi-term fractional differential equations: Smooth and non-smooth solutions. Comput. Methods Appl. Mech. Eng. 2017, 327, 478–502. [Google Scholar] [CrossRef]
- Yin, B.; Liu, Y.; Li, H.; Zhang, Z. Two families of novel second-order fractional numerical formulas and their applications to fractional differential equations. arXiv 2019, arXiv:1906.01242. [Google Scholar]
- Meerschaert, M.M.; Tadjeran, C. Finite difference approximations for fractional advection–dispersion flow equations. J. Comput. Appl. Math. 2004, 172, 65–77. [Google Scholar] [CrossRef]
- Galeone, L.; Garrappa, R. Explicit methods for fractional differential equations and their stability properties. J. Comput. Appl. Math. 2009, 228, 548–560. [Google Scholar] [CrossRef]
- Tian, W.; Zhou, H.; Deng, W. A class of second order difference approximations for solving space fractional diffusion equations. Math. Comput. 2015, 84, 1703–1727. [Google Scholar] [CrossRef]
- Ding, H.; Li, C.; Yi, Q. A new second-order midpoint approximation formula for Riemann–Liouville derivative: Algorithm and its application. IMA J. Appl. Math. 2017, 82, 909–944. [Google Scholar] [CrossRef]
- Yin, B.; Liu, Y.; Li, H. Necessity of introducing non-integer shifted parameters by constructing high accuracy finite difference algorithms for a two-sided space-fractional advection–diffusion model. Appl. Math. Lett. 2020, 105, 106347. [Google Scholar] [CrossRef]
- Stynes, M. Too much regularity may force too much uniqueness. Fract. Calc. Appl. Anal. 2016, 19, 1554–1562. [Google Scholar] [CrossRef]
- Sakamoto, K.; Yamamoto, M. Initial value/boundary value problems for fractional diffusion-wave equations and applications to some inverse problems. J. Math. Anal. Appl. 2011, 382, 426–447. [Google Scholar] [CrossRef]
- Diethelm, K.; Garrappa, R.; Stynes, M. Good (and not so good) practices in computational methods for fractional calculus. Mathematics 2020, 8, 324. [Google Scholar] [CrossRef]
- Yan, Y.; Khan, M.; Ford, N.J. An analysis of the modified L1 scheme for time-fractional partial differential equations with nonsmooth data. SIAM J. Numer. Anal. 2018, 56, 210–227. [Google Scholar] [CrossRef]
- Jin, B.; Li, B.; Zhou, Z. Correction of high-order BDF convolution quadrature for fractional evolution equations. SIAM J. Sci. Comput. 2017, 39, A3129–A3152. [Google Scholar] [CrossRef]
- Jin, B.; Li, B.; Zhou, Z. An analysis of the Crank–Nicolson method for subdiffusion. IMA J. Numer. Anal. 2018, 38, 518–541. [Google Scholar] [CrossRef]
- Wang, J.; Wang, J.; Yin, L. A single-step correction scheme of Crank–Nicolson convolution quadrature for the subdiffusion equation. J. Sci. Comput. 2021, 87, 1–18. [Google Scholar] [CrossRef]
- Yin, B.; Liu, Y.; Li, H.; Zhang, Z. Efficient shifted fractional trapezoidal rule for subdiffusion problems with nonsmooth solutions on uniform meshes. BIT Numer. Math. 2022, 62, 631–666. [Google Scholar] [CrossRef]
- Liao, H.l.; McLean, W.; Zhang, J. A discrete gronwall inequality with applications to numerical schemes for subdiffusion problems. SIAM J. Numer. Anal. 2019, 57, 218–237. [Google Scholar] [CrossRef]
- Liao, H.L.; Li, D.; Zhang, J. Sharp error estimate of the nonuniform L1 formula for linear reaction-subdiffusion equations. SIAM J. Numer. Anal. 2018, 56, 1112–1133. [Google Scholar] [CrossRef]
- Liu, Y.; Yin, B.; Li, H.; Zhang, Z. The unified theory of shifted convolution quadrature for fractional calculus. J. Sci. Comput. 2021, 89, 1–24. [Google Scholar] [CrossRef]
- Lubich, C. Convolution quadrature and discretized operational calculus. I. Numer. Math. 1988, 52, 129–145. [Google Scholar] [CrossRef]
- Lubich, C. Convolution quadrature revisited. BIT Numer. Math. 2004, 44, 503–514. [Google Scholar] [CrossRef]
- Yin, B.; Liu, Y.; Li, H. A class of shifted high-order numerical methods for the fractional mobile/immobile transport equations. Appl. Math. Comput. 2020, 368, 124799. [Google Scholar] [CrossRef]
- Yin, B.; Liu, Y.; Li, H.; Zeng, F. A class of efficient time-stepping methods for multi-term time-fractional reaction-diffusion-wave equations. Appl. Numer. Math. 2021, 165, 56–82. [Google Scholar] [CrossRef]
- Lubich, C. A stability analysis of convolution quadrature for Abel-Volterra integral equations. IMA J. Numer. Anal. 1986, 6, 87–101. [Google Scholar] [CrossRef]
- Miller, J.J. On the location of zeros of certain classes of polynomials with applications to numerical analysis. IMA J. Appl. Math. 1971, 8, 397–406. [Google Scholar] [CrossRef]
- Jin, B.; Lazarov, R.; Zhou, Z. Error estimates for a semidiscrete finite element method for fractional order parabolic equations. SIAM J. Numer. Anal. 2013, 51, 445–466. [Google Scholar] [CrossRef]

| Order p | 2 | 3 | 4 |
|---|---|---|---|
| Corrected Scheme (28) | Standard Scheme (27) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Rates | Rates | ||||||||||
| −0.9 | 4.33 × | 3.10 × | 6.92 × | 1.62 × | 2.09 | 7.50 × | 3.91 × | 1.96 × | 9.82 × | 1.00 | |
| 0.1 | −0.5 | 1.86 × | 8.76 × | 2.65 × | 7.13 × | 1.89 | 1.86 × | 8.76 × | 2.65 × | 7.13 × | 1.89 |
| 0.5 | 1.47 × | 3.43 × | 8.27 × | 2.02 × | 2.03 | 2.02 × | 9.97 × | 4.95 × | 2.47 × | 1.01 | |
| 0.9 | 2.53 × | 5.78 × | 1.38 × | 3.37 × | 2.03 | 2.87 × | 1.41 × | 6.95 × | 3.46 × | 1.01 | |
| −0.8 | 1.15 × | 2.49 × | 5.78 × | 1.39 × | 2.05 | 3.15 × | 1.60 × | 8.04 × | 4.03 × | 1.00 | |
| 0.5 | −0.5 | 3.86 × | 6.97 × | 1.44 × | 3.24 × | 2.15 | 3.86 × | 6.97 × | 1.44 × | 3.24 × | 2.15 |
| 0 | 2.35 × | 5.70 × | 1.40 × | 3.49 × | 2.01 | 5.49 × | 2.72 × | 1.35 × | 6.74 × | 1.00 | |
| 0.6 | 2.35 × | 5.70 × | 1.40 × | 3.49 × | 2.01 | 1.23 × | 6.02 × | 2.98 × | 1.49 × | 1.01 | |
| −0.5 | 2.35 × | 5.70 × | 1.40 × | 3.49 × | 2.01 | 3.05 × | 7.23 × | 1.76 × | 4.35 × | 2.02 | |
| 0.9 | −0.2 | 1.28 × | 2.95 × | 7.10 × | 1.74 × | 2.03 | 6.78 × | 3.30 × | 1.63 × | 8.10 × | 1.01 |
| 0.3 | 3.56 × | 8.65 × | 2.14 × | 5.31 × | 2.01 | 1.78 × | 8.72 × | 4.33 × | 2.15 × | 1.01 | |
| 0.6 | 7.64 × | 1.84 × | 4.51 × | 1.12 × | 2.01 | 2.44 × | 1.20 × | 5.95 × | 2.96 × | 1.01 | |
| Corrected Scheme | Standard Scheme | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Rates | Rates | ||||||||||
| 0.2 | −0.5 | 2.68 × | 7.74 × | 2.03 × | 5.14 × | 1.98 | 2.68 × | 7.74 × | 2.03 × | 5.14 × | 1.98 |
| −0.3 | 7.66 × | 1.92 × | 4.80 × | 1.18 × | 2.02 | 9.41 × | 4.69 × | 2.28 × | 1.07 × | 1.09 | |
| 0 | 1.83 × | 4.39 × | 1.07 × | 2.62 × | 2.03 | 2.42 × | 1.19 × | 5.75 × | 2.68 × | 1.10 | |
| 0.9 | 7.69 × | 1.75 × | 4.14 × | 9.97 × | 2.06 | 7.07 × | 3.40 × | 1.63 × | 7.56 × | 1.11 | |
| 0.8 | −0.5 | 8.79 × | 2.12 × | 5.20 × | 1.28 × | 2.03 | 8.79 × | 2.12 × | 5.20 × | 1.28 × | 2.03 |
| 0.1 | 1.99 × | 4.64 × | 1.12 × | 2.71 × | 2.04 | 7.59 × | 3.95 × | 1.95 × | 9.18 × | 1.09 | |
| 0.5 | 3.28 × | 7.47 × | 1.77 × | 4.27 × | 2.05 | 1.36 × | 6.82 × | 3.31 × | 1.54 × | 1.10 | |
| 0.7 | 4.11 × | 9.26 × | 2.18 × | 5.25 × | 2.06 | 1.68 × | 8.29 × | 3.99 × | 1.86 × | 1.10 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yin, B.; Zhang, G.; Liu, Y.; Li, H. The Construction of High-Order Robust Theta Methods with Applications in Subdiffusion Models. Fractal Fract. 2022, 6, 417. https://doi.org/10.3390/fractalfract6080417
Yin B, Zhang G, Liu Y, Li H. The Construction of High-Order Robust Theta Methods with Applications in Subdiffusion Models. Fractal and Fractional. 2022; 6(8):417. https://doi.org/10.3390/fractalfract6080417
Chicago/Turabian StyleYin, Baoli, Guoyu Zhang, Yang Liu, and Hong Li. 2022. "The Construction of High-Order Robust Theta Methods with Applications in Subdiffusion Models" Fractal and Fractional 6, no. 8: 417. https://doi.org/10.3390/fractalfract6080417
APA StyleYin, B., Zhang, G., Liu, Y., & Li, H. (2022). The Construction of High-Order Robust Theta Methods with Applications in Subdiffusion Models. Fractal and Fractional, 6(8), 417. https://doi.org/10.3390/fractalfract6080417







