A Review on Blockchain-Based Trust and Reputation Schemes in Metaverse Environments
Abstract
1. Introduction
- An integrated overview of all relevant works proposing metaverse trust/reputation mechanisms. We discuss each design in terms of whether it is token score-based and illustrate how each handles threats such as Sybil attack, colluding attackers, whitewashing attackers, and others.
- A taxonomy that categorizes these approaches with regard to multiple dimensions such as the underlying mechanism, the threats addressed, and architecture.
- Comparative analysis of the surveyed schemes with regard to key factors such as security, scalability, user privacy, and compatibility. We present various tables and charts to compare the quantitative as well as qualitative results presented in the literature.
- A perspective on the research and outstanding challenges in metaverse trust systems. We highlight areas such as reputation portability across platforms, privacy-preserving reputation calculation, the standardization of trust tokens/credentials, decentralized management of reputation, and real-time trust updates. We use examples to highlight the challenges and connect them to possible future research works.
2. Blockchain Integration in the Metaverse
2.1. Architecture of Blockchain-Enabled Metaverse
2.2. Current Applications and Case Studies
- Gaming Metaverses: Many metaverse games are built on blockchain [21]. Decentraland is a virtual world where land plots are ERC-721 NFTs on Ethereum. Each “LAND” is an NFT minted by burning the MANA token [8]. Ownership is fully on-chain, and a decentralized marketplace allows buying/selling parcels. Sandbox is another voxel-based metaverse on Ethereum operating as follows: users create 3D objects as NFTs stored on IPFS and trade them in a marketplace using the SAND ERC-20 token. The Sandbox also uses The Graph for scalability. The Axie Infinity ecosystem uses the Ronin sidechain to reduce Ethereum gas fees; players earn NFTs and utility tokens through gameplay. These platforms demonstrate blockchain’s value in games, guaranteeing true digital ownership, enabling player-driven economies, and securing scarce virtual goods [22].
- Virtual Real Estate: The metaverse environments tend to possess attributes that reflect real estate [23]. As pointed out by Gadekallu et al., metaverse virtual land is considered to be a scarce resource since “virtual land…is auctioned and traded as NFTs” [8]. Decentraland and The Sandbox are two examples of platforms that host regular land auctions with secondary market sales conducted through smart contracts [2,3]. The use of NFTs ensures that virtual real estate can be traced to be transferred. Businesses are experimenting with virtual land use, and all are utilizing blockchain technology.
- Healthcare: In metaverse-enabled healthcare applications, blockchain technology can be beneficial in securing patient data and digital healthcare resources. For example, patient data or virtual reality therapy sessions can be tied to a blockchain to ensure immutability and manage authorized access. In fact, survey studies carried out by Wang et al. indicate that “blockchain technology ensures secure, immutable record-keeping” and provides patients with privacy management capabilities through cryptographic keys [24]. Another metaverse healthcare solution has been proposed by Ali et al. with Explainable AI technology that employs blockchain to “ensure data security for patients while offering features such as data transparency, traceability, and immutability” [25]. Such applications include virtual hospitals, telemedicine with encrypted storage of data, and sharing data related to medical research among other areas with patient consent.
- Education: The educational metaverse uses blockchain to ensure that credentials are secured through the creation of new learning economies. As pointed out by Karunarathne et al., redundantly coupling metaverse and blockchain technology in education has resulted in revolutionary change to securely store student data [26]. For instance, certificates and degrees can be represented by blockchain tokens in an education-themed virtual reality environment. Decentralized IDs on blockchain could manage access to virtual labs or collaborative simulations. Projects like Learning Economy and blockchain-based MOOC platforms already explore these ideas. Overall, blockchain can support trust in academic records and micro-credentialing in virtual campuses.
- Other Domains: Blockchain-metaverse applications also appear in industry and commerce. In supply-chain-oriented metaverses, digital twins of factories can be anchored to blockchains for traceability. In retail, brands are opening virtual stores on metaverse platforms, selling blockchain certified goods (e.g., luxury NFTs) to users. While beyond the four focal domains, these cases underline blockchain’s broad metaverse potential.
2.3. Benefits of Blockchain in Metaverse
- Data Integrity and Security: By design, blockchain provides tamper-resistant records. Transactions and asset histories are immutable and replicated across nodes, ensuring that no data can be altered without consensus. For sensitive data, blockchain encryption and consensus give users “complete control of their data”. Decentralized storage also reduces single points of failure.
- Trust and Transparency: In open metaverse economies, trust among participants is crucial. Smart contracts enforce rules transparently without needing intermediaries. As Ali et al. [25] note, blockchain enables transparency and traceability in healthcare transactions, and it more generally assures all stakeholders of system integrity. Public ledgers let anyone audit digital asset provenance.
- Digital Ownership (NFTs and Tokens): Blockchain makes digital scarcity possible. Non-fungible tokens (NFTs) represent unique virtual items. Users have provable ownership and can trade these assets on-chain. This creates the following novel economic opportunities: for example, players in The Sandbox truly own and can sell their creations, rather than renting them from a company. Tokenized economies (ERC-20/721 tokens) allow in-world currency and novel finance as part of the metaverse.
- Decentralization and Resilience: Unlike centralized servers, blockchain-based metaverses do not rely on a single authority. This can improve uptime and censorship-resistance; virtual property rights persist even if one company shuts down. Interoperability protocols can allow users to move assets between different metaverses. Decentralization also means collaborative governance can emerge for virtual communities.
- Automated Enforcement (Smart Contracts): Business logic on blockchain via smart contracts automates complex interactions. For example, royalties on NFT resale can be coded so creators always earn a percentage. In education, smart contracts could automatically unlock course content upon payment or credential verification. These programmable agreements reduce overhead and ensure rules are executed as intended.
3. PRISMA Flow of Study Selection
4. Related Work
4.1. Blockchain-Enabled Reputation Systems for Metaverse Platforms
4.2. Self-Sovereign Identity and Credential-Based Trust
4.3. Trust Architectures and Specialized Metaverse Domains
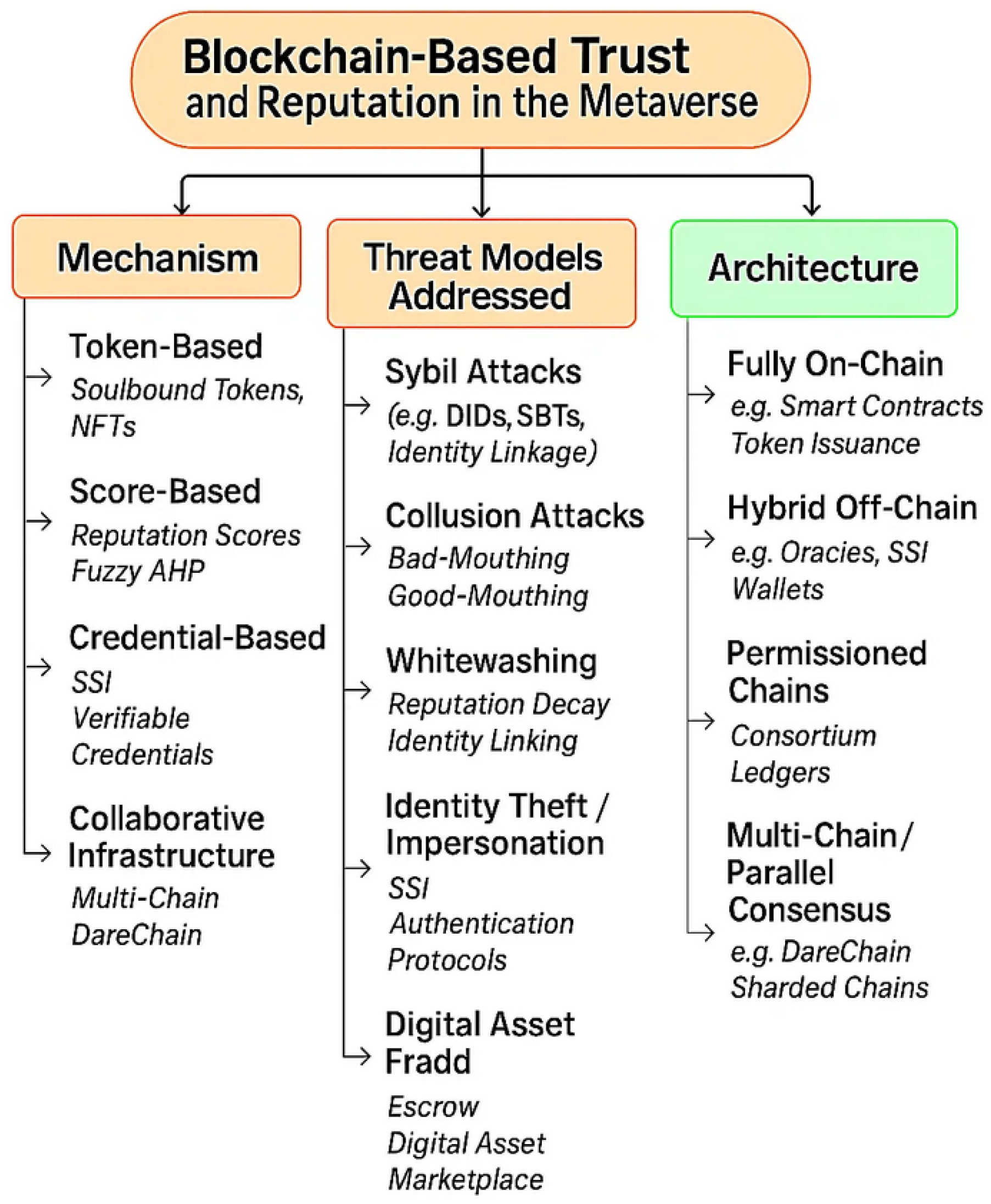
5. Taxonomy of Metaverse Trust Schemes
5.1. Mechanisms
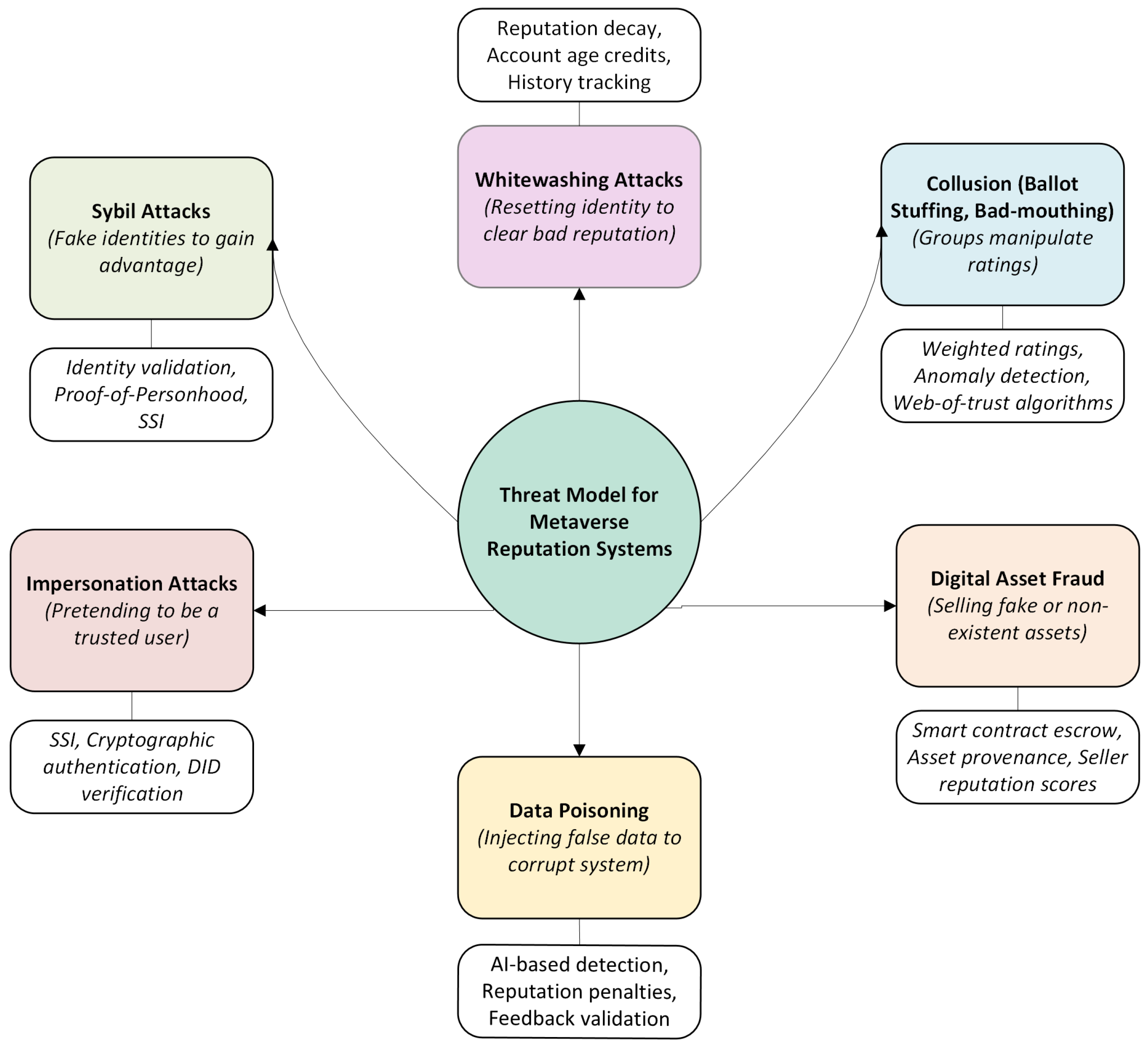
5.2. Threat Models Addressed
5.3. Architecture
6. Benchmark Analysis
6.1. Privacy and Data Governance
6.2. Interoperability and Standardization
Cross-Chain Trust Mechanisms
- -
- MAP Protocol (2024): A trustless interoperability solution that applies cryptographic proofs and a decentralized relay network to move assets and data across various blockchain platforms [58]. The architecture of MAP has concentrated on scaling through the use of various blockchain networks and performing transactions across those networks without the need to trust a custodian.
- -
- LayerZero: A messaging protocol functioning across multiple chains that facilitates communication between smart contracts on other chains [78]. LayerZero uses an Ultra Light Node architecture with an Oracle and a Relayer to validate the messages between the chains. Here, the requirement to manage the bridge is avoided; however, one party among Oracle and Relayer must be trustworthy. The trust model here can be customized to meet the requirements to ensure the interoperability of dApps.
- -
- Polkadot: A heterogeneous multi-chain system that enables trust across the Polkadot network through its Relay Chain [79]. In Polkadot, every parachain in the Polkadot network has shared validators on the Relay Chain that establish blocks and relay messages between parachains [80]. The solution offers excellent trust and security in interchain transactions but with the limitation that every chain must comply with Polkadot’s governance model.
- -
- Cosmos IBC: In Cosmos’ universe, every blockchain (or zone) has sovereignty over its transactions but still has the capability to communicate with other blocks through ‘Inter-Blockchain Communication’ (IBC) protocol [81]. The trust within every blockchain is placed upon the ‘light-client proofs’ to confirm transactions within other blocks. In Cosmos’ ecosystem, every blockchain has the capability to trust other blocks through direct verification proofs within every blockchain. This leads to an ‘increasingly more decentralized federation of worlds’.
6.3. Scalability and Performance
6.4. Performance Metrics and Quantitative Comparison
7. Open Challenges and Future Directions
7.1. Cross-Platform Reputation Portability
7.2. Privacy-Preserving Reputation
7.3. Reputation Governance and Trust Constitution
7.4. Dynamic and Real-Time Reputation
7.5. Sybil Resistance vs. Openness
7.6. Scalability to Massive Scale
7.7. User Experience and Transparency
7.8. Unified Evaluation and Collaboration
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Aygun, R.C.; Vural, T.; Zhang, L. Blockchain’s Role in Metaverse Trust and Transactions. In Proceedings of the 2023 IEEE International Conference on Metaverse Computing, Networking and Applications (MetaCom), Kyoto, Japan, 26–28 June 2023; pp. 786–792. [Google Scholar] [CrossRef]
- Decentraland Foundation. Decentraland Official Website. 2025. Available online: https://decentraland.org/ (accessed on 17 June 2025).
- The Sandbox Team. The Sandbox Official Website. 2025. Available online: https://www.sandbox.game/en/ (accessed on 17 June 2025).
- Metaverse Standards Forum. Unified Reputation Management for Metaverse Entities; Technical Report Version 1.0; Metaverse Standards Forum: Beaverton, OR, USA, 2025. [Google Scholar]
- GamesPad Editorial Team. The Role of Reputation Systems in Building Trust in the NFT Market. 2023. Available online: https://gamespad.io/the-role-of-reputation-systems-in-building-trust-in-the-nft-market/ (accessed on 17 June 2025).
- Ghosh, A.; Lavanya; Hassija, V.; Chamola, V.; El Saddik, A. A Survey on Decentralized Metaverse using Blockchain and Web 3.0 technologies, Applications, and more. IEEE Access 2024, 12, 146915–146948. [Google Scholar] [CrossRef]
- Qayyum, A.; Butt, M.A.; Ali, H.; Usman, M.; Halabi, O.; Al-Fuqaha, A.; Abbasi, Q.H.; Imran, M.A.; Qadir, J. Secure and Trustworthy Artificial Intelligence-extended Reality (AI-XR) for Metaverses. ACM Comput. Surv. 2024, 56, 1–38. [Google Scholar] [CrossRef]
- Huynh-The, T.; Gadekallu, T.R.; Wang, W.; Yenduri, G.; Ranaweera, P.; Pham, Q.V.; da Costa, D.B.; Liyanage, M. Blockchain for the metaverse: A Review. Future Gener. Comput. Syst. 2023, 143, 401–419. [Google Scholar] [CrossRef]
- Sathya, A.R. Blockchain: The Foundation of Trust in Metaverse; Springer International Publishing: Cham, Switzerland, 2023; pp. 117–129. [Google Scholar] [CrossRef]
- Jim, J.R.; Hosain, M.T.; Mridha, M.F.; Kabir, M.M.; Shin, J. Toward Trustworthy Metaverse: Advancements and Challenges. IEEE Access 2023, 11, 118318–118347. [Google Scholar] [CrossRef]
- Coinbase Learn Team. What Are Soulbound Tokens (SBT)? 2025. Available online: https://www.coinbase.com/learn/crypto-glossary/what-are-soulbound-tokens-sbt (accessed on 17 June 2025).
- Truong, V.T.; Le, L.; Niyato, D. Blockchain meets metaverse and digital asset management: A comprehensive survey. IEEE Access 2023, 11, 26258–26288. [Google Scholar] [CrossRef]
- Pattanayak, S.; Ramkumar, M.; Gupta, S. Blockchain Empowered Metaverse: Enhancing User Engagement through Trust, Collaboration, Authenticity, and Governance. Inf. Syst. Front. 2025. [Google Scholar] [CrossRef]
- Perey, C. Interoperability is a Fundamental Requirement for the Open Metaverse. In Proceedings of the 2024 IEEE International Symposium on Emerging Metaverse (ISEMV), Bellevue, WA, USA, 21 October 2024; pp. 21–24. [Google Scholar]
- Al-kfairy, M.; Alomari, A.; Al-Bashayreh, M.; Alfandi, O.; Altaee, M.; Tubishat, M. A Review of the Factors Influencing Users’ Perception of Metaverse Security and Trust. In Proceedings of the 2023 Tenth International Conference on Social Networks Analysis, Management and Security (SNAMS), Abu Dhabi, United Arab Emirates, 21–24 November 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Sky Mavis. Axie Infinity. 2024. Available online: https://axieinfinity.com/ (accessed on 3 July 2024).
- Sky Mavis. Ronin Blockchain. 2024. Available online: https://roninchain.com/ (accessed on 3 July 2024).
- Dapper Labs. Flow Blockchain. 2024. Available online: https://flow.com/ (accessed on 3 July 2025).
- Immutable. What Is Immutable X? 2024. Available online: https://docs.immutable.com/x/what-is-immutablex/ (accessed on 3 July 2025).
- Mourtzis, D.; Angelopoulos, J.; Panopoulos, N. Blockchain integration in the era of industrial metaverse. Appl. Sci. 2023, 13, 1353. [Google Scholar] [CrossRef]
- Gil, R.M.; Gutiérrez-Ujaque, D.; Teixidó, M. Analyzing the metaverse: Computer games, blockchain, and 21st-century challenge. Int. J. Hum.-Interact. 2024, 40, 6758–6775. [Google Scholar] [CrossRef]
- Nguyen, C.T.; Hoang, D.T.; Nguyen, D.N.; Dutkiewicz, E. Metachain: A novel blockchain-based framework for metaverse applications. In Proceedings of the 2022 IEEE 95th Vehicular Technology Conference:(VTC2022-Spring), Helsinki, Finland, 19–22 June 2022; pp. 1–5. [Google Scholar]
- Duan, H.; Li, J.; Fan, S.; Lin, Z.; Wu, X.; Cai, W. Metaverse for Social Good: A University Campus Prototype. In Proceedings of the 29th ACM International Conference on Multimedia (MM ’21), New York, NY, USA, 20–24 October 2021; pp. 153–161. [Google Scholar] [CrossRef]
- Wang, Y.; Zhu, M.; Chen, X.; Liu, R.; Ge, J.; Song, Y.; Yu, G. The application of metaverse in healthcare. Front. Public Health 2024, 12, 1420367. [Google Scholar] [CrossRef]
- Ali, S.; Abdullah; Armand, T.P.T.; Athar, A.; Hussain, A.; Ali, M.; Yaseen, M.; Joo, M.I.; Kim, H.C. Metaverse in healthcare integrated with explainable AI and blockchain: Enabling immersiveness, ensuring trust, and providing patient data security. Sensors 2023, 23, 565. [Google Scholar] [CrossRef]
- Karunarathne, L.; Ganesan, S.; Somasiri, N.; Pokhrel, S. Navigating the Future: Blockchain-based Metaverse in Education. J. Inf. Technol. Digit. World 2024, 6, 373–387. [Google Scholar] [CrossRef]
- Awan, K.A.; Din, I.U.; Almogren, A.S.; Seo-Kim, B. Blockchain-Based Trust Management for Virtual Entities in the Metaverse: A Model for Avatar and Virtual Organization Interactions. IEEE Access 2023, 11, 136370–136394. [Google Scholar] [CrossRef]
- Awan, K.A.; Ud Din, I.; Almogren, A.; Kim, B.S. Enhancing Performance and Security in the Metaverse: Latency Reduction Using Trust and Reputation Management. Electronics 2023, 12, 3362. [Google Scholar] [CrossRef]
- Tu, Z.; Zhou, H.; Li, K.; Song, H.; Yang, Y. A Blockchain-based Trust and Reputation Model with Dynamic Evaluation Mechanism for IoT. Comput. Networks 2022, 218, 109404. [Google Scholar] [CrossRef]
- Xia, P.; Li, J.; Shi, L.; Cao, B.; Tan, W.; Weng, J.; Liu, Y.; Han, Z. A Reputation-Aided Lightweight Consensus Service Framework for Multi-Chain Metaverse. IEEE Netw. 2024, 38, 201–210. [Google Scholar] [CrossRef]
- Rahaman, M.F.; Mohtasin, G.; Subhan, M.; Tuli, E.; Kim, D.S.; Lee, J.M. Meta-Governance: Blockchain-Driven Metaverse Platform for Mitigating Misbehavior Using Smart Contract and AI. IEEE Trans. Netw. Serv. Manag. 2024, 21, 4024–4038. [Google Scholar] [CrossRef]
- Dimitriou, T. Decentralized reputation, Cryptology ePrint Archive, Paper 2020/761. 2020. Available online: https://eprint.iacr.org/2020/761 (accessed on 10 November 2025).
- Baccour, E.; Erbad, A.; Mohamed, A.; Hamdi, M.; Guizani, M. A Blockchain-Based Reliable Federated Meta-Learning for Metaverse: A Dual Game Framework. IEEE Internet Things J. 2024, 11, 22697–22715. [Google Scholar] [CrossRef]
- Lin, Y.; Gao, Z.; Du, H.; Niyato, D.; Kang, J.; Xiong, Z.; Zheng, Z. Blockchain-Based Efficient and Trustworthy AIGC Services in Metaverse. IEEE Trans. Serv. Comput. 2024, 17, 2067–2079. [Google Scholar] [CrossRef]
- Kharvi, P.L. A Design Science Framework for Measuring Trust and Security in the Metaverse Space: A Holistic Approach to Digital Trustworthiness. Ph.D. Thesis, Marymount University, College of Business, Innovation, Leadership, and Technology, Arlington, VA, USA, 2025. [Google Scholar]
- Truong, V.T.; Le, H.D.; Le, L.B. Trust-Free Blockchain Framework for AI-Generated Content Trading and Management in Metaverse. IEEE Access 2024, 12, 41815–41828. [Google Scholar] [CrossRef]
- Ud Din, I.; Habib Khan, K.; Almogren, A.; Zareei, M.; Arturo Pérez Díaz, J. Securing the Metaverse: A Blockchain-Enabled Zero-Trust Architecture for Virtual Environments. IEEE Access 2024, 12, 92337–92347. [Google Scholar] [CrossRef]
- Ghirmai, S.; Mebrahtom, D.; Aloqaily, M.; Guizani, M.; Debbah, M. Self-Sovereign Identity for Trust and Interoperability in the Metaverse. arXiv 2023, arXiv:2303.00422. [Google Scholar] [CrossRef]
- Ohlhaver, P.; Weyl, E.G.; Buterin, V. Decentralized Society: Finding Web3’s Soul; Technical Report 4105763; SSRN Electronic Journal: Rochester, NY, USA, 2022. [Google Scholar]
- Wagmi Tips. Soulbound Tokens: What They Are and Why They Matter. 2025. Available online: https://wagmi.tips/guides/soulbound-tokens/ (accessed on 17 June 2025).
- EY Insights Team. If the Metaverse Is Intrinsically Anonymous, How Do You Encode Trust? 2023. Available online: https://www.ey.com/en_ch/insights/technology/if-the-metaverse-is-intrinsically-anonymous-how-do-you-encode-trust (accessed on 17 June 2025).
- Song, X.; Xu, G.; Huang, Y. A Fuzzy AHP-based trust management mechanism for self-sovereign identity in the metaverse. Appl. Soft Comput. 2025, 174, 112994. [Google Scholar] [CrossRef]
- Patwe, S.; Mane, S.B. Blockchain-enabled secure and interoperable authentication scheme for metaverse environments. Future Internet 2024, 16, 166. [Google Scholar] [CrossRef]
- Mebrahtom, D.; Hadish, S.; Sbhatu, A.; Aloqaily, M.; Guizani, M. Trust But Verify—Blockchain-Empowered Decentralized Authentication Schema on the Metaverse: A Self-Sovereign Identity Approach. In Proceedings of the 2023 International Conference on Intelligent Metaverse Technologies & Applications (iMETA), Tartu, Estonia, 18–20 September 2023; pp. 1–8. [Google Scholar] [CrossRef]
- Gebre, D.; Hadish, S.; Sbhatu, A.; Aloqaily, M.; Guizani, M. Establishing Trust and Security in Decentralized Metaverse: A Web 3.0 Approach. ACM Trans. Multimed. Comput. Commun. Appl. 2024, 20, 1–17. [Google Scholar] [CrossRef]
- Ling, A.; Butakov, S. Trust framework for self-sovereign identity in metaverse healthcare applications. Data Sci. Manag. 2024, 7, 304–313. [Google Scholar] [CrossRef]
- Xu, M.; Guo, Y.; Hu, Q.; Xiong, Z.; Yu, D.; Cheng, X. A trustless architecture of blockchain-enabled metaverse. High-Confid. Comput. 2023, 3, 100088. [Google Scholar] [CrossRef]
- Lotfi, I.; Qaraqe, M.; Ghrayeb, A.; Niyato, D. VMGuard: Reputation-Based Incentive Mechanism for Poisoning Attack Detection in Vehicular Metaverse. IEEE Trans. Veh. Technol. 2025, 74, 10255–10267. [Google Scholar] [CrossRef]
- Li, Q.; Kong, L.; Min, X.; Zhang, B. DareChain: A Blockchain-Based Trusted Collaborative Network Infrastructure for Metaverse. Int. J. Crowd Sci. 2023, 7, 168–179. [Google Scholar] [CrossRef]
- Liu, L.; Feng, J.; Wu, C.; Chen, C.; Pei, Q. Reputation management for consensus mechanism in vehicular edge metaverse. IEEE J. Sel. Areas Commun. 2023, 42, 919–932. [Google Scholar] [CrossRef]
- Awan, K.A.; Ud Din, I.; Almogren, A.; Rodrigues, J.J.P.C. QSTMF: Quantum-Secured Trust Management Framework for VANETs in Web 3.0 and Metaverse. ACM Trans. Auton. Adapt. Syst. 2025, 20, 1–29. [Google Scholar] [CrossRef]
- Kuru, K.; Kuru, K. Blockchain-Based Decentralised Privacy-Preserving Machine Learning Authentication and Verification with Immersive Devices in the Urban Metaverse Ecosystem. Preprints 2024, 317, v1. [Google Scholar] [CrossRef]
- Cao, Y.; Cao, J.; Cui, Z.; Bai, D.; Zhang, M.; Wen, L. PolyTwin: Edge Blockchain-empowered Trustworthy Digital Twin Network for Metaverse. In Proceedings of the 2024 IEEE International Conference on Metaverse Computing, Networking, and Applications (MetaCom), Hong Kong, China, 12–14 August 2024; pp. 81–88. [Google Scholar] [CrossRef]
- Islam, S. Trust in Digital Asset Transactions in a Web 3 Based Metaverse. Master’s Thesis, OULU Business School, University of OULU, Oulu, Finland, 2023. [Google Scholar]
- Civic Technologies, Inc. Civic Whitepaper: A Secure Identity Ecosystem. 2021. Available online: https://www.civic.com/ (accessed on 17 June 2025).
- Chainlink Labs. Chainlink 2.0: Next Steps in the Evolution of Decentralized Oracle Networks. 2021. Available online: https://research.chain.link/whitepaper-v2.pdf (accessed on 17 June 2025).
- Vijitha, S.; Anandan, R. Blockchain-based decentralized identifier in metaverse environment for secure and privacy-preserving authentication with improved key management and cryptosystem. Peer-Netw. Appl. 2025, 18, 210. [Google Scholar] [CrossRef]
- Cao, Y.; Cao, J.; Bai, D.; Wen, L.; Liu, Y.; Li, R. MAP the Blockchain World: A Trustless and Scalable Blockchain Interoperability Protocol for Cross-chain Applications. arXiv 2024, arXiv:2411.00422. [Google Scholar] [CrossRef]
- Ding, Y.; Huang, W.; Liang, H.; Wang, Y.; Yang, C.; Wang, H. A Fast Cross-Chain Protocol Based on Trusted Notary Group for Metaverse. Int. J. Netw. Manag. 2025, 35, e2302. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, N.; Xing, R.; Liu, D.; Lan, T.H.; Shen, X. A Survey on Metaverse: Fundamentals, Security, and Privacy. IEEE Commun. Surv. Tutor. 2023, 25, 319–352. [Google Scholar] [CrossRef]
- Huang, Y.; Li, Y.J.; Cai, Z. Security and Privacy in Metaverse: A Comprehensive Survey. Big Data Min. Anal. 2023, 6, 234–247. [Google Scholar] [CrossRef]
- Chow, Y.W.; Susilo, W.; Li, Y.; Li, N.; Nguyen, C. Visualization and Cybersecurity in the Metaverse: A Survey. J. Imaging 2023, 9, 11. [Google Scholar] [CrossRef]
- Polychronaki, M.; Xevgenis, M.G.; Kogias, D.G.; Leligou, H.C. Decentralized Identity Management for Metaverse-Enhanced Education: A Literature Review. Electronics 2024, 13, 3887. [Google Scholar] [CrossRef]
- Yousafzai, A.; Sheeraz, M.M.; Pogrebna, G.; Crowcroft, J.; Yaqoob, I. Blockchain for the Metaverse: Recent Advances, Taxonomy and Future Directions. J. Netw. Comput. Appl. 2025. early access. [Google Scholar]
- Sevim, H.O. A Survey on Trustless Cross-Chain Interoperability Protocols. In Proceedings of the Distributed Ledger Technology Workshop (DLT), Rome, Italy, 20 June 2022. [Google Scholar]
- Kausar, F.; Senan, F.M.; Asif, H.M.; Raahemifar, K. 6G technology and taxonomy of attacks on blockchain technology. Alex. Eng. J. 2022, 61, 4295–4306. [Google Scholar] [CrossRef]
- Hameed, K.; Barika, M.; Garg, S.; Amin, M.B.; Kang, B. A taxonomy study on securing Blockchain-based Industrial applications: An overview, application perspectives, requirements, attacks, countermeasures, and open issues. J. Ind. Inf. Integr. 2022, 26, 100312. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L.; Janicke, H. Blockchain technologies for the internet of things: Research issues and challenges. IEEE Internet Things J. 2018, 6, 2188–2204. [Google Scholar] [CrossRef]
- Garg, K. Digital identities in the metaverse: Privacy, security, and user authentication in virtual financial systems. Int. J. Financ. Eng. 2024, 11, 2442009. [Google Scholar] [CrossRef]
- OpenSea: NFT Marketplace. Available online: https://opensea.io/ (accessed on 23 June 2025).
- Liu, W.; Cao, B.; Peng, M.; Li, B. Distributed and parallel blockchain: Towards a multi-chain system with enhanced security. IEEE Trans. Dependable Secur. Comput. 2024, 22, 723–739. [Google Scholar] [CrossRef]
- Lin, Q.; Gu, B.; Nawab, F. RollStore: Hybrid Onchain-Offchain Data Indexing for Blockchain Applications. IEEE Trans. Knowl. Data Eng. 2024, 36, 9176–9191. [Google Scholar] [CrossRef]
- Kausar, F.; Sadiq, M.A.K.; Asif, H.M. Convergence of Blockchain in IoT Applications for Heterogeneous Networks. In Real-Time Intelligence for Heterogeneous Networks: Applications, Challenges, and Scenarios in IoT HetNets; Al-Turjman, F., Ed.; Springer International Publishing: Cham, Switzerland, 2021; pp. 71–86. [Google Scholar] [CrossRef]
- Hemphill, T.A. The ‘metaverse’and the challenge of responsible standards development. J. Responsible Innov. 2023, 10, 2243121. [Google Scholar] [CrossRef]
- Trust Over IP Foundation. Trust Over IP Foundation. 2025. Available online: https://trustoverip.org/ (accessed on 30 June 2025).
- Roblox Corporation. Roblox. 2025. Available online: https://www.roblox.com/ (accessed on 30 June 2025).
- Epic Games. Fortnite. 2025. Available online: https://www.epicgames.com/fortnite (accessed on 30 June 2025).
- Zarick, R.; Pellegrino, B.; Banister, C. Layerzero: Trustless omnichain interoperability protocol. arXiv 2021, arXiv:2110.13871. [Google Scholar] [CrossRef]
- Wood, G. Polkadot: Vision for a heterogeneous multi-chain framework. White Pap. 2016, 21, 4662. [Google Scholar]
- Abbas, H.; Caprolu, M.; Di Pietro, R. Analysis of polkadot: Architecture, internals, and contradictions. In Proceedings of the 2022 IEEE International Conference on Blockchain (Blockchain), Espoo, Finland, 22–25 August 2022; pp. 61–70. [Google Scholar]
- Cosmos Network. IBC-Go Documentation: The Golang Implementation of the Inter-Blockchain Communication Protocol. 2025. Available online: https://docs.cosmos.network/ibc/v10.1.x/intro (accessed on 10 November 2025).
- Fiege, U.; Fiat, A.; Shamir, A. Zero knowledge proofs of identity. In Proceedings of the Nineteenth Annual ACM Symposium on Theory of Computing, New York, NY, USA, 1 June 1987; pp. 210–217. [Google Scholar]
- zCloak Network. Proposing “zk-SBT” — A Zero-Knowledge Soulbound Token. 2022. Available online: https://mirror.xyz/zcloak-network.eth/BSqm-pLo3CbQgnBK_eMfrV9MUe3HL_MP65F3mkIyycc (accessed on 10 November 2025).
- Cabot-Nadal, M.À.; Playford, B.; Payeras-Capellà, M.M.; Gerske, S.; Mut-Puigserver, M.; Pericàs-Gornals, R. Private Identity-Related Attribute Verification Protocol Using SoulBound Tokens and Zero-Knowledge Proofs. In Proceedings of the 2023 7th Cyber Security in Networking Conference (CSNet), Montreal, QC, Canada, 16–18 October 2023; pp. 153–156. [Google Scholar] [CrossRef]
- Polyhedra Network. Introducing Polyhedra Network: ZkBridge and zkDID for Web3. 2025. Available online: https://blog.polyhedra.network/introducing-polyhedra-network/ (accessed on 10 November 2025).

| PRISMA Stage | Records (n) | Notes |
|---|---|---|
| Identification: total records from all databases | 1758 | IEEE, ACM, ScienceDirect, Scopus (2020–2025); search: blockchain & metaverse & (trust OR reputation) |
| Duplicates removed | 828 | ∼50% overlap across databases |
| Records after de-duplication (screened) | 930 | Title/abstract screening pool |
| Records excluded at title/abstract stage | 820 | Off-topic, language, or format filters |
| Full-text articles assessed for eligibility | 110 | Downloaded and reviewed in full |
| Full-text articles excluded | 87 | No trust mechanism; not metaverse-relevant; not blockchain-relevant; insufficient detail; non–peer-reviewed; duplicate concept |
| Studies included in qualitative synthesis | 23 | Papers analyzed in Table 1, Table 2, Table 3, Table 4 |
| Scheme (Year) | Mechanism Type | Blockchain Platform | Architecture | Target Context | Ref. |
|---|---|---|---|---|---|
| Trust-based Metaverse Framework (2023) | Score-based reputation (PoT consensus) | Assumed permissionless (Ethereum-like) | Mostly on-chain (smart contracts + monitoring) | General metaverse (resource sharing, VR/AR) | [28] |
| DEM-BTRM IoT Trust Model (2022) | Score-based reputation + decay | Permissioned (Hyperledger Fabric prototype) | Hybrid (off-chain calc, on-chain storage) | IoT/Metaverse crossover (trust in IoT data) | [29] |
| Rep-aided Consensus (2024) | Score-based reputation (weighted consensus) | Multi-chain metaverse (sharded chains) | On-chain integrated (consensus protocol level) | Blockchain infrastructure for metaverse | [30] |
| SSI Web3 Trust (2024) | Credential-based trust (SSI, DIDs) | Permissionless (Ethereum smart contracts) | Hybrid (off-chain wallet + on-chain verify) | Cross-platform user identity and auth | [38] |
| Fuzzy AHP Trust (SSI-based) (2025) | Hybrid score (multi-factor fuzzy) | Not specified (conceptual, any chain) | Hybrid (compute off-chain, publish on-chain) | Metaverse digital identity reputation | [42] |
| Trustless Architecture (2023) | Local trust groups (scores per group) | Not specified (generic blockchain layer) | Hybrid (blockchain + off-chain enclaves) | General metaverse (resource and security mgmt) | [47] |
| VMGuard Vehicular (2024) | Score-based reputation (feedback loop) | Blockchain not explicitly used; possible extension | Off-chain currently (could use blockchain log) | Vehicular metaverse (IoV data integrity) | [48] |
| Soulbound Tokens (2022) | Token-based reputation (non-transferable) | Ethereum and others (concept level) | On-chain tokens (issued via smart contract) | Web3 social trust (metaverse credentials) | [39] |
| DareChain (2023) | Collaborative multi-chain | Permissionless multi-chain | On-chain parallel consensus | Enterprise metaverse (govt, finance) | [49] |
| Blockchain SSI Auth (2024) | Credential-based (SSI) | Ethereum | Hybrid (wallet + smart contract) | Cross-platform user authentication | [43] |
| DPPML Authentication (2024) | Privacy-preserving ML-based | Conceptual urban metaverse | Hybrid (FL + blockchain) | Urban metaverse authentication | [52] |
| Vehicular Trust Consensus (2024) | Score-based PBFT consensus | Permissioned PBFT | Hybrid (off-chain rep/on-chain PBFT) | Vehicular edge metaverse | [50] |
| DID-Based Metaverse Authentication (2025) | Credential-based (DID + ILWKM-CS crypto) | Not specified (any DID-enabled chain) | Hybrid: DID issuance off-chain, login/auth proofs on-chain | E-learning metaverse—secure avatar login | [57] |
| Trust Framework for SSI (2024) | Credential-based (medical SSI) | Permissioned/ private healthcare chain | Hybrid: patient/doctor credentials off-chain; smart-contract checks on-chain | Secure telemedicine VR hospital scenarios | [46] |
| MetaTrade (2024) | Blockchain DAM (escrow-based) | Ethereum (EVM-compatible) | On-chain (smart contracts) | AI-generated content trading | [36] |
| Decentralized SSI Trust Framework (2024) | Credential-based (SSI wallet + verifiable credentials) | Ethereum smart contracts | Hybrid: mobile SSI wallet and dApp off-chain; auth proofs on-chain | Cross-domain avatar authentication and access control | [45] |
| QSTMF (2025) | Quantum-secured trust + blockchain reputation | Consortium chain + quantum cryptography | Hybrid (on-chain/off-chain/quantum) | Vehicular metaverse (Web 3.0/VANETs) | [51] |
| MAP (2024) | Trustless cross-chain interoperability (relay chain + zk-SNARK light clients) | Multi-chain; Ethereum; MAP relay chain | Decentralized, non-custodial, scalable | Web 3.0/metaverse; DeFi; NFTs | [58] |
| Meta-Learning (2024) | Federated meta-learning with blockchain-based reputation and dual-game incentives | Custom blockchain (smart contract) | Decentralized; transparent; incentive-aligned (Stackelberg/coalition games) | Metaverse (AI service, avatar reputation) | [33] |
| PolyTwin (2024) | Proof of consistency for DTs using edge AI + blockchain | Private/consortium blockchain among edge clusters | Edge-AI + blockchain; on-chain validation | Digital twins (PolyCampus, PolyExchange) | [53] |
| AI Generated Content (2024) | Blockchain-trustworthy AIGC with semantic comm + smart contracts | Consortium blockchain | Decentralized; verifiable; incentive-aligned (Stackelberg, IRM) | Metaverse (AIGC, personalized content) | [34] |
| Trusted Notary Group Cross-Chain (2024) | Fast cross-chain via trusted notary committee protocol | Multi-chain; consortium/permissioned | Notary group–based; semi-decentralized; high-throughput | Asset/data transfer; cross-domain interop | [59] |
| Blockchain-Enabled Zero-Trust Architecture (2024) | Collaborative infrastructure (zero-trust model) | General (EVM-compatible or similar) | Hybrid (on-chain + off-chain) | General metaverse (virtual environment security) | [37] |
| Survey (Venue, Year) | Scope | Main Angle | Trust/ Rep. | Mech. Taxonomy | Threat Coverage | Quant Bench. | Interop/ Cross-Chain |
|---|---|---|---|---|---|---|---|
| [8] (FGCS, 2023) | Blockchain for metaverse | Systems view (storage, sharing, privacy) | △ | △ | △ | ✗ | △ |
| [60] (IEEE ComST, 2023) | Metaverse fundamentals, security, privacy | Broad metaverse tutorial | △ | ✗ | ✓ | ✗ | △ |
| [61] (BDMA, 2023) | Metaverse security | Security/privacy taxonomy | △ | ✗ | ✓ | ✗ | △ |
| [62] (Journal of Imaging, 2023) | Visualization + cybersecurity | XR/visualization threats | ✗ | ✗ | ✓ | ✗ | ✗ |
| [63] (Electronics, 2024) | DID/SSI in metaverse education | Identity, credentials, privacy | △ | △ | △ | ✗ | △ |
| [64] (JNCA, 2025) | Blockchain for metaverse | Advances + taxonomy | △ | ✓ | △ | ✗ | ✓ |
| [65] (DLT Workshop, 2022) | Cross-chain interoperability | Trustless bridges/protocols | ✗ | ✗ | △ | ✗ | ✓ |
| This work (2025) | Metaverse trust/reputation | PRISMA SLR; mechanism–threat–architecture taxonomy; quantitative benchmarks; industrial vs. academic; cross-chain | ✓ | ✓ | ✓ | ✓ | ✓ |
| Scheme (Reference) | Sybil | Collusion | White-Washing | Impersonation /ID | Asset Fraud | Data Poisoning |
|---|---|---|---|---|---|---|
| SSI-based interoperable authentication [43] | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ |
| Soulbound-Token (SBT) credential system [39] | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ |
| Credential-based DID attestation [44] | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ |
| Reputation-driven voting [27] | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ |
| Fuzzy reputation with decay [42] | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ |
| Smart-contract escrow and provenance [70] | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ |
| DEM-BTRM [29] | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| Sybil-resistant consensus [30] | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| Local-trust groups [47] | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ |
| VMGuard [48] | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ |
| DareChain [49] | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ |
| DPPML Auth [52] | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ |
| ILWKM-CS [57] | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ |
| SSI (medical) [46] | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ |
| Trust-aware PBFT [71] | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ |
| MetaTrade [36] | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ |
| SSI Trust Framework [45] | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ |
| Blockchain-Enabled Zero-Trust [37] | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Architecture | What It Looks Like | Strengths | Limitations | When to Use |
|---|---|---|---|---|
| Fully on-chain | All reputation updates and logic in contracts; every event recorded on the ledger | Maximum transparency; tamper-resistant; easy auditability | Gas cost; latency; complex algorithms impractical on-chain | Small–medium scale; strong audit requirements; simple scoring |
| Hybrid off-chain | Heavy compute off-chain; on-chain anchors for state, proofs, or checkpoints | Scalable; low cost; flexible algorithms; preserves verifiability via proofs/logs | Trust in off-chain layer; oracle correctness; extra ops complexity | Large-scale interaction graphs; privacy-aware scoring; TEEs/ZK proofs available |
| Permissioned chains | Consortium/private ledger (e.g., Fabric) with vetted validators and policy controls | High throughput; predictable cost; governance and compliance controls | Reduced openness; interop frictions with public chains; trust in consortium | Enterprise/regulated domains; intra-organization trust exchange |
| Multi-chain/parallel consensus | Shards or federated chains; cross-chain reputation/identity portability | Throughput via parallelism; specialization; fault isolation | Bridge/relay security; global consistency; more moving parts | Cross-platform ecosystems; high concurrency; domain-specific chains |
| Scheme | Security (Attack Resilience) | Scalability (Performance) | Privacy (Data Exposure) | Interoperability (Cross-platform) |
|---|---|---|---|---|
| TrustMgmt [27] | High—multi-attack resistant | Medium—public chain (some optimizations) | Low—on-chain data visible | Low—platform-specific (Ethereum only) |
| PerfTrust [28] | Medium—specific threat focus | High—custom blockchain consensus (low latency) | Low—no privacy features | Low—platform-specific (private chain) |
| MetaGov [31] | Medium—stops harassment but Sybils possible | High—permissioned chain real-time AI | Medium—private chain logs identifiable | Low—tied to one platform (not portable) |
| PrivRep [32] | High—Sybil/whitewash proof | Low—heavy crypto public chain overhead | High—strong anonymity | High—user-centric shareable token |
| DEM-BTRM [29] | High—multiple attack mitigation via dynamic evaluations | High—permissioned blockchain efficient batching | Medium—partially identifiable transaction data | Medium—potential for multi-chain support |
| RepConsensus [30] | High—Sybil-resistant via reputation-weighted consensus | High—multi-chain sharded approach | Medium—data visible across shards | High—cross-chain reputation portability |
| LocalTrust [47] | Medium—local group trust reduces widespread attacks | High—scalable via local computations | High—local trust not globally visible | Medium—dependent on cross-group trust bridges |
| VMGuard [48] | High—data poisoning protection via reputation | High—regional feedback loops scale efficiently | Medium—vehicle data logs identifiable | Medium—city-wide application interoperability |
| DareChain [49] | High—attack resistant via parallel consensus | High—parallel chains increase throughput | High—data obfuscation layers | High—designed for enterprise interoperability |
| DPPML Auth [52] | High—impersonation protection via federated learning | Medium—federated computation scales linearly | High—privacy via federated learning | Medium—urban metaverse focused |
| Vehicular PBFT [71] | High—Sybil and collusion-resistant via PBFT | Medium—limited by PBFT nodes (<100 nodes) | Medium—data partially identifiable | Medium—edge-specific interoperability |
| SSI Trust Framework [46] | Medium—strict credential checks in healthcare | Medium—permissioned ledger fits hospital workloads | Very High—patient-driven consent | Medium—domain-specific but standards-compliant |
| ILWKM-CS [57] | High—ILWKM-CS mutual auth | Medium—lightweight crypto; global scale not yet measured | High—no personal data on-chain | Low—built for one e-learning metaverse |
| MetaTrade [36] | High—fraud resistance via smart contract escrow | Medium—blockchain dependent transaction speed | Medium—transaction details visible on-chain | High—portable digital asset standards |
| ZeroTrust-BC Framework [37] | High—multi-vector attack mitigation using blockchain-based zero-trust | High—scalable with fast response and low overhead | Medium—audit trail on-chain with strong access control | Medium—platform-agnostic design, not cross-chain tested |
| Scheme | Scalability Strategy | Reported Performance |
|---|---|---|
| Awanet al. [27] | Decentralized trust decisions; trust-weighted consensus reduces agreement steps so reputable nodes drive consensus. Reputation monitoring avoids expensive recovery from misbehavior. | Processes 2000 nodes in 340 ms vs. 520 ms baseline (≈35% faster). Integrating trust improved latency; near-linear scaling; graceful degradation; better throughput at scale. |
| Tu et al. [29] — BTRM | Dynamic updates and permissioned chain. Not every interaction triggers on-chain tx; reputation updates are batched/periodic. Uses Fabric’s high TPS; idle users pruned. | On Fabric, practical runtimes for reputation updates; scaled to large IoT pools without linear cost growth; low latency by limiting heavy computation frequency. |
| Xu et al. [47] | Metaverse partitioned into trust groups; computations scale per group. Edge compute for local loads; blockchain coordinates groups; minimizes on-chain ops; groups subdividable. | Conceptual (no numerics). Qualitatively scales: new users add load only to their group. Hypergraph trust supports incremental growth; avoids single bottlenecks. |
| Li et al. [49] — DareChain | Collaborative multi-chain: parallel chains (shards) handle different interactions. Consensus scales with chains/nodes; layered contracts distribute load. | High throughput via parallelism; overall TPS grows nearly linearly with added chains; low per-tx latency as each shard handles smaller load; maintains security/privacy. |
| Mebrahtom et al. [44] | Off-chain interactions with on-chain verification. SSI setup amortized; no redundant re-checks per login; blockchain can be fast layer-2 backend. | Prototype on Ethereum: . Qualitatively supports thousands of logins/checks concurrently. |
| Patwe et al. [43] | SSI-based hybrid. Auth via off-chain wallet interactions, on-chain validation. Heavy compute peer-to-peer/client-side; chain logs events/revocations; no central auth server. | Measured auth ms; comms 1256 bits. Lightweight enough for real-time VR login. Throughput limited by base chain; modern chains handle 100 s–1000 s TPS. |
| Kuru et al. [52] | Federated learning on device data; distributes compute across devices/edge. Blockchain stores checkpoints, not every interaction. | Early-stage concept. Scales with device count; per-user (tens of ms for light models). |
| Xia et al. [30] | Lightweight consensus reduces messaging; reputation streamlines leader election. Multi-chain design: shards handle regions/contexts in parallel. | Simulations show higher throughput per chain; filtering low-rep nodes may reduce consensus from O(n) to O(m), ; capacity increases with more shards. |
| Liu et al. [71] | Permissioned PBFT with trust scores. Offloads reputation off-chain/in parallel; PBFT uses weights; dynamic node set. | Simulations: dozens of vehicles per region with sub-second blocks. PBFT efficient with filtering; large scale via partitioned regional chains. |
| Lotfi et al. [48] | Localized feedback loops; each region computes trust locally; regions run in parallel; incentive throttling; if on blockchain, use regional permissioned chains or DAG. | Dozens to few hundred vehicles in real time. For millions, hierarchical clusters; near-linear scale by deploying more servers; needs fast/sharded chains. |
| Truong et al. [36] | On-chain escrow contracts; every trade hits the chain. Batch on high-TPS networks; reputation updated per trade/audit. | Secure trading focus. Typical L1 escrow: few hundred ms. Thousands/sec possible on L2. Reputation writes are small; scales with chain improvements. |
| Song et al. [42] | Hierarchical fuzzy trust: split factors, compute in parallel off-chain, aggregate; updates periodic or on significant change. | No explicit metrics (prototype). Off-chain heavy lifting; on-chain only final scores/proofs. Supports very large user sets with distributed compute. |
| Soulbound Tokens [39] | Static reputational credentials; mint/read/store are efficient; updates infrequent; batch issuance supported. | Seen at NFT scale (millions of tokens). L2/sidechains give high throughput/low cost. Internet-scale feasible; per-user data small. |
| Platform | Throughput (TPS) | Latency (per Block) | Consensus Mechanism | Gas/Energy Cost |
|---|---|---|---|---|
| Ethereum | ∼15 TPS | ∼12 s | Proof-of-Stake (Nakamoto-Finality) | High gas fees (moderate energy after PoS) [28] |
| Polygon (PoS) | – TPS (typical) | 2–3 s | PoS sidechain (checkpointed to ETH) | Low fees (fractions of cent) [30] |
| Ronin | TPS (estimated) | 2 s | PoA/DPoS (few validators) | Negligible fees (game transactions free) [49] |
| Flow | + TPS (practical) | ∼1 s | Proof-of-Stake (pipeline multi-node) | Low fees (optimized for NFTs) [30] |
| DareChain | ∼60 TPS | 1–5 s | Parallel PoW + BFT shards | Moderate (optimized, lower latency) [49] |
| Challenge | Mapped Solutions |
|---|---|
| Cross-platform portability |
|
| Privacy-preserving computation |
|
| Governance and fairness |
|
| Real-time updates |
|
| Sybil resistance vs. openness |
|
| Data integrity and false inputs |
|
| Massive-scale performance |
|
| User experience and transparency |
|
| Platform | Trust Model | Privacy Handling | Cross-Chain | Decentralization |
|---|---|---|---|---|
| Meta Horizon Worlds | Centralized moderation (Meta-controlled) | Platform-managed data; limited anonymity | None (closed ecosystem) | No (fully centralized) |
| Microsoft Mesh | Enterprise/host-managed trust | Corporate identity integration; enterprise privacy policies | None (closed ecosystem) | No (centralized cloud service) |
| Roblox | Centralized user trust (reputation via Roblox Corp) | Standard online privacy; provider-controlled data | None (no blockchain integration) | No (central servers) |
| Academic prototypes | Blockchain-based trust frameworks (e.g., SBT/SSI credentials) | Often pseudonymous or ZK-enabled privacy | Limited (single-chain or conceptual bridges) | Yes (decentralized ledgers; small-scale) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kausar, F.; Asif, H.M.; Hussain, S.; Mumtaz, S. A Review on Blockchain-Based Trust and Reputation Schemes in Metaverse Environments. Cryptography 2025, 9, 74. https://doi.org/10.3390/cryptography9040074
Kausar F, Asif HM, Hussain S, Mumtaz S. A Review on Blockchain-Based Trust and Reputation Schemes in Metaverse Environments. Cryptography. 2025; 9(4):74. https://doi.org/10.3390/cryptography9040074
Chicago/Turabian StyleKausar, Firdous, Hafiz M. Asif, Sajid Hussain, and Shahid Mumtaz. 2025. "A Review on Blockchain-Based Trust and Reputation Schemes in Metaverse Environments" Cryptography 9, no. 4: 74. https://doi.org/10.3390/cryptography9040074
APA StyleKausar, F., Asif, H. M., Hussain, S., & Mumtaz, S. (2025). A Review on Blockchain-Based Trust and Reputation Schemes in Metaverse Environments. Cryptography, 9(4), 74. https://doi.org/10.3390/cryptography9040074







