- Feature Paper
- Article
MIND-Crypt: A Machine Learning Framework for Assessing the Indistinguishability of Lightweight Block Ciphers Across Multiple Modes of Operation
- Jimmy Dani,
- Kalyan Nakka and
- Nitesh Saxena
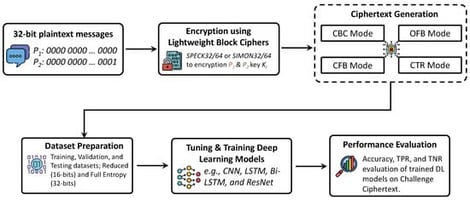
Indistinguishability is a fundamental principle of cryptographic security, crucial for securing data transmitted between Internet of Things (IoT) devices. This principle ensures that an attacker cannot distinguish between the encrypted data, also known as ciphertext, and random data or the ciphertexts of two messages encrypted with the same key. This research investigates the ability of machine learning (ML) to assess the indistinguishability property in encryption systems, with a focus on lightweight ciphers. As our first case study, we consider the SPECK32/64 and SIMON32/64 lightweight block ciphers, designed for IoT devices operating under significant energy constraints. In this research, we introduce MIND-Crypt (a Machine-learning-based framework for assessing the INDistinguishability of Cryptographic algorithms), a novel ML-based framework designed to assess the cryptographic indistinguishability of lightweight block ciphers, specifically the SPECK32/64 and SIMON32/64 encryption algorithms in CBC, CFB, OFB, and CTR modes, under Known Plaintext Attacks (KPAs). Our approach involves training ML models using ciphertexts from two plaintext messages encrypted with the same key to determine whether ML algorithms can identify meaningful cryptographic patterns or leakage. Our experiments show that modern ML techniques consistently achieve accuracy equivalent to random guessing, indicating that no statistically exploitable patterns exist in the ciphertexts generated by the considered lightweight block ciphers. Although some models exhibit mode-dependent bias (e.g., collapsing to a single-class prediction in CBC and CFB), their overall accuracy remains at random guessing levels, reinforcing that no meaningful distinguishing patterns are learned. Furthermore, we demonstrate that, when ML algorithms are trained on all possible combinations of ciphertexts for given plaintext messages, their behavior reflects memorization rather than generalization to unseen ciphertexts. Collectively, these findings suggest that existing block ciphers have secure cryptographic designs against ML-based indistinguishability assessments, reinforcing their security even under round-reduced conditions.
10 February 2026