Cybersecurity Strategy Development: Towards an Integrated Approach Based on COBIT and ISO 27000 Series Standards
Abstract
1. Introduction
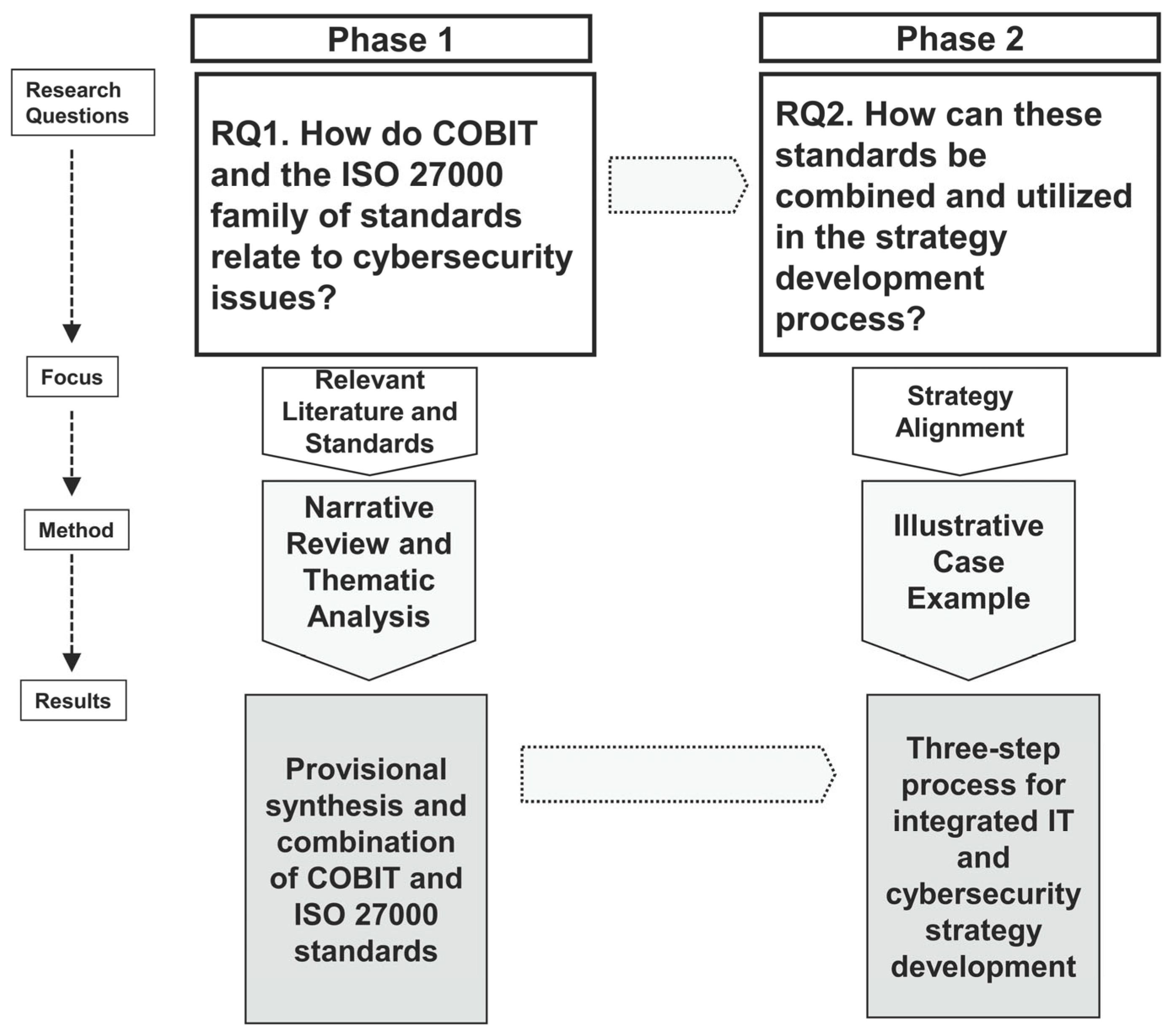
2. Research Method
2.1. Phase 1: Narrative Synthesis and Qualitative Content Analysis
2.2. Phase 2: Illustrative Case Example
3. Relevant Literature and Standards
3.1. Digital Technologies and Cybersecurity (Contextual Background)
3.2. Strategy Alignment and Integration (Contextual Background)
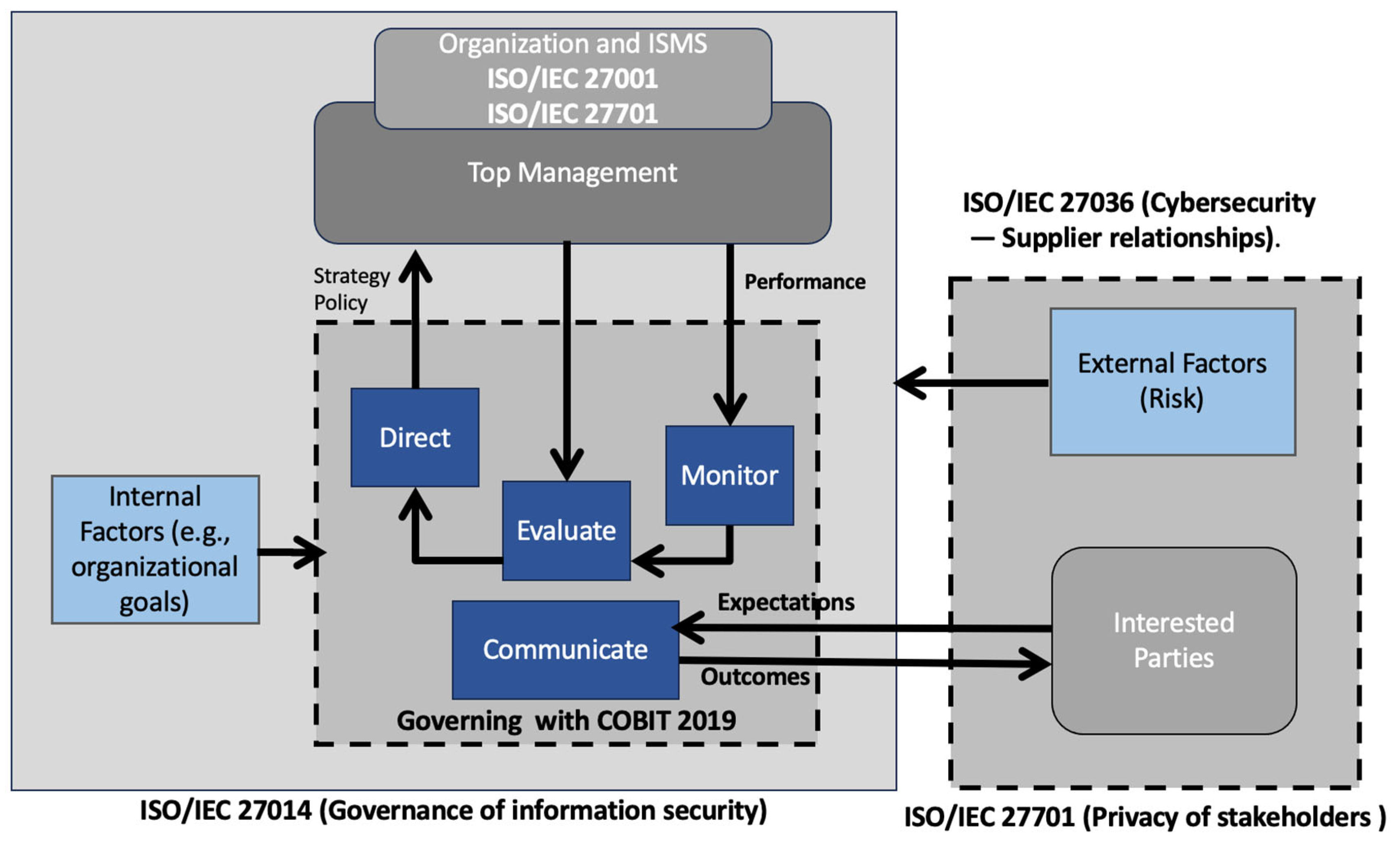
3.3. IT Governance: The COBIT and the ISO 27000 Standards
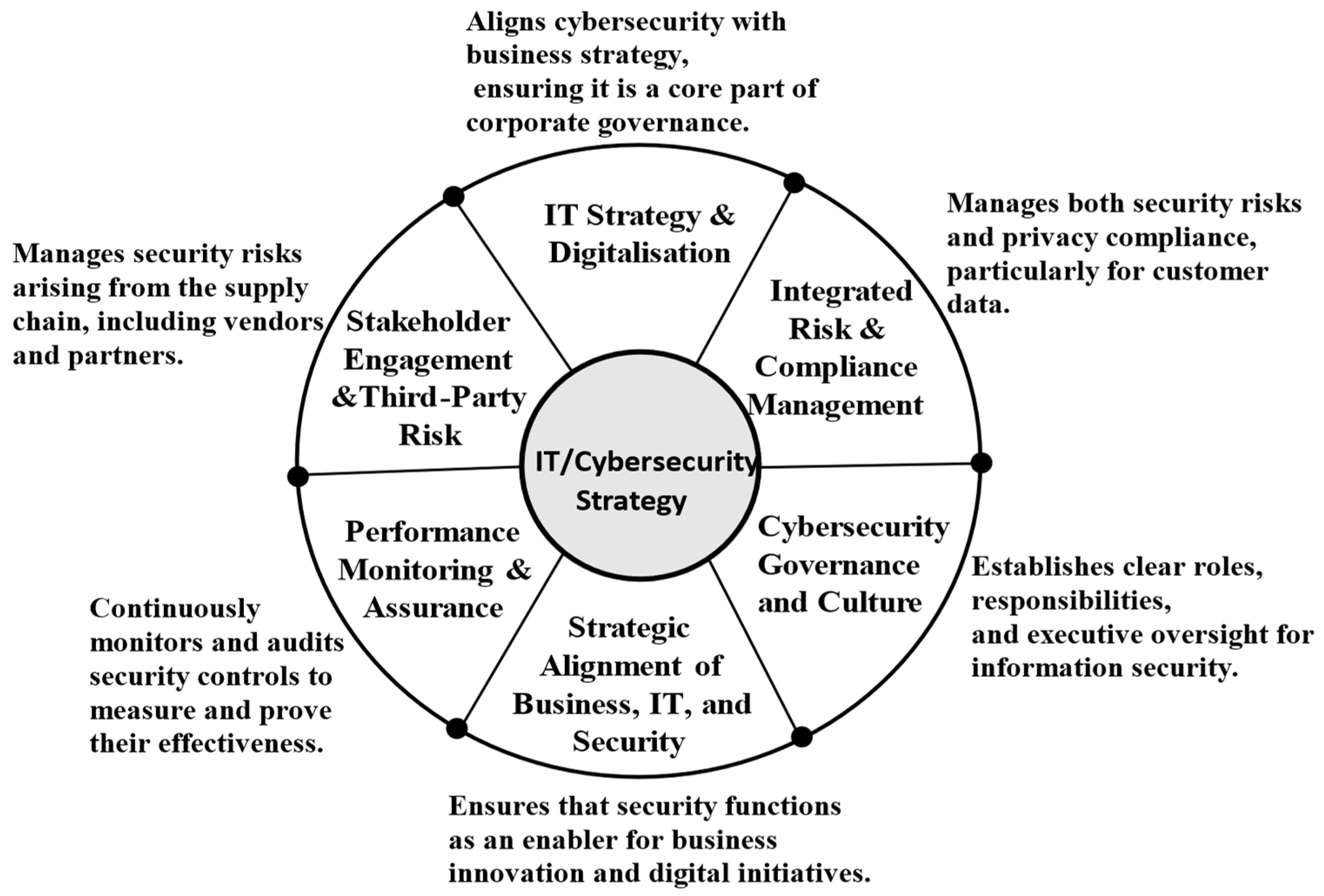
3.4. Provisional Conceptual Framework for Cybersecurity Strategy
4. Results
4.1. RQ1. How Do COBIT and the ISO 27000 Series Standards Relate to Cybersecurity Issues?
4.2. RQ2. How Can These Standards Be Combined and Utilized in the Strategy Development Process?
4.2.1. Step 1. Review and Align Business and IT Objectives
4.2.2. Step 2. Develop (or Revise) IT Strategy
4.2.3. Step 3. Define the Cybersecurity Strategy Integrating COBIT 2019 and ISO/IEC 27000 Series
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| SECTION | CONTENT |
|---|---|
| OVERVIEW | The IT function enables the company’s digital-first, customer-centric strategy through scalable cloud infrastructure, real-time data analytics, and secure, agile delivery platforms. |
| MISSION STATEMENT | To deliver reliable, innovative, and secure technology solutions that support rapid growth, operational efficiency, and exceptional customer experiences across 700+ locations in Turkey. |
| OBJECTIVES |
|
| ASSESSMENT/AUDIT | Current state: Hybrid model with internal strategic IT team (30–35 FTEs) and external managed services partner for infrastructure (Azure AKS, monitoring, DevOps). |
| INVENTORY—CLOUD & INFRASTRUCTURE |
|
| INVENTORY—APPLICATIONS & PLATFORMS |
|
| NETWORK COMPONENTS |
|
| PLAN—STRATEGIC ACTIONS |
|
| DEPARTMENT STRUCTURE |
|
| PROJECT BUDGET |
|
| APPROVAL DATE BY SENIOR MANAGEMENT | Q1 2025 |
Appendix B. Qualitative Content Analysis Illustrative Documents
| Code | Definition (What It Captures) | Inclusion Rules (Code When…) | Exclusion Rules (Do Not Code When…) | Typical Indicators in the Coded Corpus |
|---|---|---|---|---|
| IT Strategy & Digitalization | Direction for adopting/retiring technologies (AI, IoT, cloud, etc.) and linking such decisions to governance and risk. | Mentions acquisition/adoption direction, governance criteria for new tech, or risk-aware selection/outsourcing. | Pure technical features or tool lists without governance direction. | 27014: “set the direction of acquisition”; COBIT: APO02 Manage Strategy. |
| Cybersecurity Governance & Culture | Security-specific governance principles and fostering a security-positive culture led by top management/board. | Mentions security governance principles, roles/mandates, tone-from-the-top, culture/awareness. | Control configuration or training logistics without governance/culture intent. | 27014: entity-wide governance; security-positive culture. COBIT: EDM01. |
| Integrated Risk & Compliance Management | Risk-based decision-making at entity level and conformance/assurance integration (including privacy where relevant). | Mentions risk appetite/criteria, ERM integration, conformance/assurance planning or evidence requirements. | Isolated operational risks or checklists without governance of risk/conformance. | 27014: risk-based approach; conformance/assurance. COBIT: APO12; MEA03. |
| Strategic Alignment of Business, IT, & Security | Linking IS/IT objectives and benefits to enterprise goals; governance approval of strategy and measurable objectives. | Mentions alignment with business strategy, benefits delivery, measurable IS objectives, architecture fit. | Technology selection without business linkage or metrics. | 27014: ensure performance; evaluate/direct strategy. COBIT: EDM02. |
| Performance Monitoring & Assurance | Setting indicators/targets, monitoring/reviewing security performance, and assurance over controls. | Mentions KPIs/KRIs, dashboards, management review cadence, audit/assurance. | One-off testing with no linkage to performance or governance review. | 27014: “Monitor” process; COBIT: MEA01–MEA03. |
| Stakeholder Engagement & Third-Party Risk | Bi-directional communication with interested parties and governance of supplier/third-party risks. | Mentions reporting to stakeholders, expectations/outcomes, supplier requirements/assurance. | Internal team comms only; vendor how-to without governance requirements. | 27014: “Communicate” to interested parties; COBIT: EDM05; (contextual link to 27036 in discussion, not coded). |
| Source | Short Excerpt (≤25 Words, Verbatim) | Assigned Code | Rationale (Why This Code/Strategy Relevance) |
|---|---|---|---|
| ISO/IEC 27014:2020, 7.2.3 | “Set the direction of acquisition…” | IT Strategy & Digitalization | Ties adoption/outsourcing choices to governance criteria; mandates risk-aware strategic direction for AI/IoT/cloud decisions. |
| COBIT 2019, APO02 (purpose) | “Manage I&T strategy to support enterprise strategy and goals.” | IT Strategy & Digitalization | Frames I&T strategy as subordinate to business goals; ensures digital initiatives are governed for contribution and measurable outcomes. |
| ISO/IEC 27014:2020, 7.2.1 | “Information security objectives should be related to… the overall goals of the entity.” | Strategic Alignment of Business, IT, & Security | Forces explicit linkage of IS objectives to enterprise goals—alignment, value, and performance orientation. |
| COBIT 2019, EDM02 (purpose) | “Ensure benefits delivery from I&T-enabled investments.” | Strategic Alignment of Business, IT, & Security | Board-level accountability for benefits realisation; governance mechanism to track value and maintain alignment. |
| ISO/IEC 27014:2020, 7.2.2 | “Make decisions using a risk-based approach.” | Integrated Risk & Compliance Management | Entity-level mandate to apply risk appetite/criteria; integrates compliance/assurance expectations into decision-making. |
| COBIT 2019, APO12 (purpose) | “Manage I&T-related risk in line with enterprise risk management.” | Integrated Risk & Compliance Management | Integrates I&T risk with ERM; clarifies ownership, reporting, and control design under governance. |
| ISO/IEC 27014:2020, 7.3.4 | “Monitor performance of information security…” | Performance Monitoring & Assurance | Requires KPIs/KRIs and management review; establishes governance expectations for performance oversight. |
| COBIT 2019, MEA01 (purpose) | “Collect, validate and evaluate business, I&T and process goals and metrics.” | Performance Monitoring & Assurance | Sets a full metrics cycle—collection, validation, evaluation—and links to corrective actions and assurance. |
| ISO/IEC 27014:2020, 7.2.5 | “Foster a security-positive culture.” | Cybersecurity Governance & Culture | Elevates culture to a governance objective; assigns top-management responsibility for roles, awareness, competence. |
| COBIT 2019, EDM01 (purpose) | “Ensure governance framework setting and maintenance.” | Cybersecurity Governance & Culture | Establishes and maintains the enterprise governance framework—structure to manage culture and roles systematically. |
| ISO/IEC 27014:2020, 7.3.5 | “Report to interested parties…” | Stakeholder Engagement & Third-Party Risk | Mandates bidirectional reporting to stakeholders; strengthens accountability and transparency of security outcomes. |
| COBIT 2019, EDM05 (purpose) | “Ensure stakeholder Engagement for I&T governance.” | Stakeholder Engagement & Third-Party Risk | Requires stakeholder Engagement; frames expectation/outcome reporting, relevant to supplier/third-party contexts. |
| Rule | Description |
|---|---|
| Segmentation | ISO/IEC 27014 coded at clause/paragraph level; COBIT 2019 coded at objective “purpose” and management practice paragraph level. |
| Primary vs. secondary codes | Assign exactly one primary code per segment; add one secondary only if the text genuinely reflects two governance intents. |
| Ambiguity rule | If a segment fits both alignment and performance, prefer Strategic Alignment when it prescribes direction/objectives; prefer Performance Monitoring & Assurance when it prescribes measurement/review mechanics. |
| Negative evidence | If a segment states absence/shortcomings (e.g., “lack of metrics”), still code under the intended category and flag as NEG. |
| Memoing | Record coder notes and any inductive sub-codes in a shared log (date, coder, rationale). |
| Adjudication | Resolve disagreements by consensus; if unresolved, the senior coder adjudicates. Maintain version control for changes. |
| Code (Theme)— | Segments Coded (COBIT 2019) | Segments Coded (ISO/IEC 27014) | Total |
|---|---|---|---|
| IT Strategy & Digitalization | 2 | 1 | 3 |
| Cybersecurity Governance & Culture | 2 | 1 | 3 |
| Integrated Risk & Compliance Management | 2 | 2 | 4 |
| Performance Monitoring & Assurance | 3 | 2 | 5 |
| Strategic Alignment of Business, IT, & Security | 1 | 2 | 3 |
| Stakeholder Engagement & Third-Party Risk | 2 | 2 | 4 |
| Total | 12 | 10 | 22 |
References
- Gill, O.; Yorke, H. £1.5bn Rescue to Keep Wheels Turning Till Christmas at Hacked JLR and Suppliers. Sunday Times 2025, 489, 2. [Google Scholar]
- ISACA. COBIT 2019 Framework: Governance & Management Objectives; ISACA: Schaumburg, IL, USA, 2018; Available online: https://www.isaca.org/resources/cobit (accessed on 5 June 2025).
- Slim, A.; Sarah, O.; Kadhim, K.; Ali, B.; Hammood, A.; Othman, B. The effect of information technology business alignment factors on performance of SMEs. Manag. Sci. Lett. 2021, 11, 833–842. [Google Scholar] [CrossRef]
- Adaba, G.B.; Wilson, D.W.; Sims, J. The Impact of National Culture on Strategic IT Alignment: A Multiple-case Study of Subsidiaries of Multinational Corporations. Inf. Syst. Manag. 2022, 39, 288–304. [Google Scholar] [CrossRef]
- Alaceva, C.; Rusu, L. Barriers in achieving business/IT alignment in a large Swedish company: What we have learned? Comput. Hum. Behav. 2015, 51, 715–728. [Google Scholar] [CrossRef]
- Earl, M. Management Strategies for Information Technology; Prentice Hall: Hemel Hempstead, UK, 1989. [Google Scholar]
- Sayjari, T.; Melo Silveira, R. Cybersecurity and Corporate Risk Management: Aligning Information Security with Business Strategies. In Proceedings of the Congresso de Gestão de Riscos Corporativos (GRC), São Paulo, Brazil, December 2024. [Google Scholar]
- ISO/IEC 27000; Family—Information Security Management. ISO. Available online: https://www.iso.org/standard/iso-iec-27000-family#:~:text=IT%20security%2C%20cybersecurity%20and%20privacy,information%20entrusted%20by%20third%20parties (accessed on 12 November 2025).
- ISO/IEC 27014; Information Security, Cybersecurity and Privacy Protection—Governance of Information Security (ISO/IEC Standard No. 27014:2020). ISO/IEC: Geneva, Switzerland, 2020. Available online: https://www.iso.org/standard/74046.html (accessed on 23 July 2025).
- ISO/IEC 27001; Information Security, Cybersecurity, and Privacy Protection—Information Security Management Systems—Requirements (ISO/IEC Standard No. 27001:2022). ISO/IEC: Geneva, Switzerland, 2022. Available online: https://www.iso.org/standard/82875.html (accessed on 15 May 2025).
- ISO/IEC 27036; ISO/IEC 27036-1:2021 Cybersecurity—Supplier Relationships—Part 1: Overview and Concepts. ISO/IEC: Geneva, Switzerland, 2021. Available online: https://www.iso.org/standard/82905.html (accessed on 8 May 2025).
- ISO/IEC 27036-2; ISO/IEC 27036-2:2022 Cybersecurity—Supplier Relationships—Part 2: Requirements. ISO/IEC: Geneva, Switzerland, 2022. Available online: https://www.iso.org/standard/82060.html (accessed on 8 May 2025).
- ISO/IEC 27036-3; ISO/IEC 27036-3:2023 Cybersecurity—Supplier Relationships—Part 3: Guidelines for hardware, software, and services supply chain security. ISO/IEC: Geneva, Switzerland, 2023. Available online: https://www.iso.org/standard/82890.html (accessed on 8 May 2025).
- ISO/IEC 27036-4; ISO/IEC 27036-4:2016 Information Technology—Security Techniques—Information Security for Supplier Relationships—Part 4: Guidelines for Security of Cloud Services. ISO/IEC: Geneva, Switzerland, 2016. Available online: https://www.iso.org/standard/59689.html (accessed on 13 October 2025).
- ISO/IEC 27701:2025; Information Security, Cybersecurity and Privacy Protection—Privacy Information Management Systems—Requirements and Guidance (2nd ed.). Available online: https://www.iso.org/standard/27701 (accessed on 2 November 2025).
- Snyder, H. Literature review as a research methodology: An overview and guidelines. J. Bus. Res. 2019, 104, 333–339. [Google Scholar] [CrossRef]
- Webster, J.; Watson, R.T. Analyzing the past to prepare for the future: Writing a literature review. MIS Q. 2002, 26, xiii–xxiii. [Google Scholar]
- Popay, J.; Roberts, H.; Sowden, A.; Petticrew, M.; Arai, L.; Rodgers, M.; Britten, N.; Roen, K. Guidance on the conduct of narrative synthesis in systematic reviews. ESRC Methods Programme 2006, 1, b92. [Google Scholar]
- Petticrew, M.; Roberts, H. Systematic Reviews in the Social Sciences: A Practical Guide; Blackwell Publishing: Oxford, UK, 2006. [Google Scholar]
- Mayring, P. Qualitative Content Analysis. Forum Qual. 2000, 1, 20. Available online: https://www.qualitative-research.net/index.php/fqs/article/view/1089/2385 (accessed on 3 October 2025).
- Schreier, M. Qualitative Content Analysis in Practice; Sage: London, UK, 2012. [Google Scholar]
- Wynn, M.; Bakeer, A.; Forti, Y. E-government and digital transformation in Libyan local authorities. Int. J. Teach. Case Stud. 2021, 12, 119–139. [Google Scholar] [CrossRef]
- Taylor, J.; Wynn, M. Case study methodologies and a wider appreciation of development planning. Ekistics 1980, 47, 451–453. Available online: https://eprints.glos.ac.uk/8716/ (accessed on 3 October 2025).
- Mutlutürk, M.; Kor, B.; Metin, B. The Role of Edge/Fog Computing Security in IoT and Industry 4.0 Infrastructures: Edge/Fog-Based Security in Internet of Things; IGI Global: Hershey, PA, USA, 2021; pp. 211–222. ISBN 13: 9781799877400. [Google Scholar] [CrossRef]
- Metin, B.; Duran, S.; Telli, E.; Mutlutürk, M.; Wynn, M. IT Risk Management: Towards a System for Enhancing Objectivity in Asset Valuation that Engenders a Security Culture. Information 2024, 15, 55. [Google Scholar] [CrossRef]
- Wynn, M. E-business, Information Systems Management and Sustainable Strategy Development in the Digital Era. Sustainability 2022, 14, 10918. [Google Scholar] [CrossRef]
- Roose, K. The Brilliance and Weirdness of ChatGPT. The New York Times. 9 December 2022. Available online: https://www.nytimes.com/2022/12/05/technology/chatgpt-ai-twitter.html (accessed on 10 October 2024).
- NIST Information Technology Laboratory. AI Rısk Management Framework by NIST; NIST Information Technology Laboratory: Gaithersburg, MD, USA, 2023. Available online: https://www.nist.gov/itl/ai-risk-management-framework (accessed on 2 October 2025).
- Laux, J.; Wachter, S.; Mittelstadt, B. Trustworthy artificial intelligence and the European Union AI act: On the conflation of trustworthiness and acceptability of risk. Regul. Gov. 2024, 18, 3–32. [Google Scholar] [CrossRef]
- Wynn, M.; Jones, P. Corporate Digital Responsibility and the Business Implications of Quantum Computing. Adv. Environ. Eng. Res. 2023, 4, 1–18. [Google Scholar] [CrossRef]
- Cherbal, S.; Zier, A.; Hebal, S.; Louail, L.; Annane, B. Security in internet of things: A review on approaches based on blockchain, machine learning, cryptography, and quantum computing. J. Supercomput. 2024, 80, 3738–3816. [Google Scholar] [CrossRef]
- Goulart, V.G.; Liboni, L.B.; Cezarino, L.O. Balancing skills in the digital transformation era: The future of jobs and the role of higher education. Ind. High. Educ. 2022, 36, 118–127. [Google Scholar] [CrossRef]
- Tanriverdi, N.S.; Metin, B. Enterprise Information Security Awareness and Behavior as An Element of Security Culture During Remote Work: Security Awareness and Behavior During Remote Work; IGI Global: Hershey, PA, USA, 2021; pp. 119–138. ISBN 13: 9781799875130. [Google Scholar] [CrossRef]
- Sebastian, G. Privacy and Data Protection in ChatGPT and Other AI Chatbots: Strategies for Securing User Information. International. J. Secur. Priv. Pervasive Comput. 2023, 15, 1–14. [Google Scholar] [CrossRef]
- Jessani, A. Chatbots, AI and the Future of Privacy; IAPP: Portsmouth, NH, USA, 23 March 2023; Available online: https://iapp.org/news/a/chatbots-ai-and-the-future-of-privacy/ (accessed on 18 May 2025).
- Tom, J.; Adigwe, W.; Anebo, N.; Bukola, O. Automated Model for Data Protection Regulation Compliance Monitoring and Enforcement. Int. J. Comput. Intell. Secur. Res. 2023, 2, 47–57. [Google Scholar]
- Elmorshidy, A. Aligning IT With Business Objectives: A Critical Survival and Success Factor in today’s Business. J. Appl. Bus. Res. 2013, 29, 819–828. [Google Scholar] [CrossRef]
- Poelen, E. The Implications of Business-IT Alignment for Business Value of IT. 8 May 2017. Available online: http://arno.uvt.nl/show.cgi?fid=144854 (accessed on 8 May 2025).
- Koçu, L. Business -IT alignment effects on business agility. Int. J. Commer. Financ. 2018, 4, 60–93. [Google Scholar]
- Broadcom. Is Your IT Department Aligned with Your Business Outcomes? 1 September 2020. Available online: https://hbr.org/sponsored/2020/09/is-your-it-department-aligned-with-your-business-outcomes (accessed on 3 October 2025).
- Henderson, J.C.; Venkatraman, N. Strategic Alignment: Leveraging Information Technology for Transforming Organizations. IBM Syst. J. 1993, 32, 4–16. [Google Scholar] [CrossRef]
- Aversano, L.; Grasso, C.; Tortorella, M. Measuring the Alignment Between Business Processes and Software Systems: A Case Study. In Proceedings of the 2010 ACM Symposium on Applied Computing (SAC’10), Sierre, Switzerland, 22–26 March 2010. [Google Scholar]
- De Castro, V.; Marcos, E.; Vara, J.M. Applying CIM-to-PIM model transformations for the service-oriented development of information systems. J. Inf. Softw. Technol. 2011, 53, 87–105. [Google Scholar] [CrossRef]
- Kaplan, R.S.; Norton, D.P. Balanced Scorecard: Implementing and Action Strategy; Erlangga: Jakarta, Indonesia, 2000. [Google Scholar]
- Bricknall, R.; Darrell, G.; Nilsson, H.; Pessi, K. Aligning IT strategy with business strategy through the balanced scorecard in a multinational pharmaceutical company. In Proceedings of the 2007 40th Annual Hawaii International Conference on System Sciences (HICSS’07), Waikoloa, HI, USA, 3–6 January 2007. [Google Scholar]
- Balafif, S.; Haryanti, T. IT balanced scorecard (IT BSC) based strategic framework for assessing the impacts of Business Strategic- IT alignment. IOP Conference Series. Mater. Sci. Eng. 2020, 821, 12033. [Google Scholar] [CrossRef]
- Wynn, M.; Weber, C. Information Systems Strategy for Multi-National Corporations: Towards an Operational Model and Action List. Information 2024, 15, 119. [Google Scholar] [CrossRef]
- COSO. Committee of Sponsoring Organizations of the Treadway Commission, Internal Control—Integrated Framework: Executive Summary; COSO: New York, NY, USA, 1992. [Google Scholar]
- ISACA. Transforming Cybersecurity Using COBIT5; ISACA: Schaumburg, IL, USA, 2013; ISBN 978-1-60420-341-7. Available online: https://www.isaca.org/ (accessed on 12 May 2025).
- ISO/IEC 27005:2022; Information Security, Cybersecurity and Privacy Protection—Guidance on Managing Information Security Risks. ISO/IEC: Geneva, Switzerland, 2022. Available online: https://www.iso.org/standard/80585.html (accessed on 12 September 2025).
- Cameron, B.H. IT Portfolio Management: Implications for IT Strategic Alignment. In Proceedings of the Eleventh Americas Conference on Information Systems, Omaha, NE, USA, 11–14 August 2005. [Google Scholar]
- Violino, B. How to Better Integrate IT Security and IT Strategy. 2019. Available online: https://www.cio.com/article/3407737/how-to-better-integrate-it-security-and-it-strategy.html (accessed on 23 August 2025).
- ISACA. Designing Your Organization’s Custom COBIT; ISACA: Schaumburg, IL, USA, 2019; Available online: https://www.isaca.org/resources/news-and-trends/industry-news/2019/designing-your-organizations-custom-cobit (accessed on 25 October 2025).
- Wu, C.; Chen, J.; Li, J.; Xu, J.; Jia, J.; Hu, Y.; Feng, Y.; Liu, Y.; Xiang, Y. Profit or Deceit? Mitigating Pump and Dump in DeFi via Graph and Contrastive Learning. IEEE Trans. Inf. Forensics Secur. 2025, 20, 8994–9008. [Google Scholar] [CrossRef]
- Yin, R.K. Case Study Research and Applications: Design and Methods, 6th ed.; Sage: Thousand Oaks, CA, USA, 2018. [Google Scholar]
- Wynn, M.; Jones, P. New technology deployment and corporate responsibilities in the metaverse. Knowledge 2023, 3, 543–556. [Google Scholar] [CrossRef]


| PCF Themes | COBIT 2019 Basis | Aligned ISO 27000 Standards | Description/Key Activities |
|---|---|---|---|
| 1. IT Strategy & Digitalization | APO02—Managed Strategy | ISO/IEC 27014:2020 (Clause 7.2.3—Set the direction of acquisition) Clause 7.3.3—Direct) | This theme addresses the dual opportunities and threats of digitalization (AI, IoT, etc.) discussed in Section 3.1. COBIT APO02 provides the IT strategy framework, while ISO 27014 guides the risk assessment of new technology adoption. |
| 2. Cybersecurity Governance & Culture | EDM01—Ensured Governance Framework Setting and Maintenance | ISO/IEC 27014:2020 (Clause 7.2.1—Entity-wide governance; Clause 7.2.5—Security-positive culture) | COBIT provides the general IT governance structure, while ISO/IEC 27014 provides the specific information security governance principles, including the promotion of a “security-positive culture”. |
| 3. Integrated Risk & Compliance Management | EDM03—Ensured Risk Optimization APO12—Manage Risk MEA03—Managed Compliance with External Requirements | ISO/IEC 27014:2020 (Clause 7.2.2—Risk-based approach) ISO/IEC 27001 (Clause 6.1.2 risk assessment), Clause 6.1.3 (risk treatment) ISO/IEC 27701:2025 (PIMS) | This responds to the need to manage both security risks (ISO/IEC 27001/27014) and privacy/regulatory compliance (ISO/IEC 27701, GDPR) in a single, integrated framework. |
| 4. Strategic Alignment of Business, IT, & Security | EDM02—Ensured Benefits Delivery | ISO/IEC 27014:2020 (Clause 7.2.6—Ensure the security performance meets current and future requirements of the entity) ISO/IEC 27001:2022 Clause 6.2 (Information security objectives) | The value of alignment is discussed in the extant literature (see Section 3.2). COBIT EDM02 links IT investments to business strategy. ISO/IEC 27014 explicitly links security performance to organizational performance. |
| 5. Performance Monitoring & Assurance | MEA01—Managed Performance and Conformance Monitoring MEA02—Managed System of Internal Control MEA03—Managed Compliance with External Requirements | ISO/IEC 27014:2020 (Clause 7.3.4—Monitor) ISO/IEC 27001:2022 Clause 9 (Monitoring, measurement, analysis and evaluation), Clause 10 (Continual improvement) | There is a need to be able to measure the effectiveness of cybersecurity. This theme is derived from COBIT’s MEA (Monitor, Evaluate and Assess) domain, ISO/IEC 27014’s “Monitor” process, and ISO/IEC 27001’s clauses on performance evaluation. |
| 6. Stakeholder Engagement & Third-Party Risk | EDM05— Ensured Stakeholder Engagement | ISO/IEC 27036 Series (Cybersecurity—Supplier relationships); ISO/IEC 27036-2:2022 (Requirements for supplier relationships); ISO/IEC 27036-3:2023 (Guidelines for hardware, software, and services for supply chain security); ISO/IEC 27014:2020 (Clause 7.3.5—Communicate). | This theme integrates COBIT’s focus on stake-holder Engagement with ISO/IEC 27014’s Clause 7.3.5 “Communicate” process and, critically, the specific third-party/supply chain risk focus of the ISO 27036 series. |
| Cybersecurity Strategy Theme/Code | COBIT 2019 Reference & Extract | ISO/IEC 27014:2020 Reference & Extract | Comment/ Relevance |
|---|---|---|---|
| IT Strategy & Digitalisation | APO02—Managed Strategy: “Provide a consistent approach integrated with enterprise strategy management to ensure IT enables and supports the achievement of enterprise objectives”. | 7.2.3 Set the direction of acquisition: “The impact of information security risk should be adequately assessed when undertaking new activities, including adoption of new technology, outsourcing arrangements and contracts with external suppliers”. | Digitalisation, AI, IoT, blockchain, metaverse as emerging risks/opportunities. |
| Cybersecurity Governance & Culture | COBIT covers IT governance broadly but is not a dedicated cybersecurity strategy. Example: EDM01— Ensured Governance Framework Setting and Maintenance: “Evaluate, direct and monitor the governance system and practices”. | 7.2.1 Entity-wide governance: “Governance of information security should ensure that information security objectives are comprehensive and integrated at the entity level”. 7.3 Processes: “Evaluate, Direct, Monitor, Communicate”. | Developing a robust cybersecurity strategy; ISO fills COBIT’s gap at security governance level. |
| Risk & Compliance Integration | APO12—Managed Risk: “Establish and maintain a risk management framework that is integrated with enterprise risk management”. MEA03— Managed Compliance with External Requirements: “Evaluate adherence to laws, regulations and contractual requirements”. | 7.2.2 Risk-based approach: “Governance of information security should be based on compliance obligations and risk-based decisions”. 7.2.4 Conformance: “Ensure that policies and practices conform to internal and external requirements”. | Compliance issues and IT security risks as central challenges. |
| Strategic Alignment of Business, IT & Security | EDM02—Ensured Benefits Delivery: “Ensure that IT-enabled investments deliver the expected benefits in line with business strategy”. | 7.2.6 Ensure performance: “The governing body should link information security performance to the performance of the organization and of the entity”. | Alignment of business, IT, and cybersecurity strategies. |
| Performance Monitoring & Assurance | MEA01— Managed Performance and Conformance Monitoring: “Collect, validate and evaluate business, IT and process goals and metrics”. | 7.3.4 Monitor: “The governing body should receive the report on the effectiveness of the operation of each ISMS and evaluate it in the context of entity priorities”. | Framework usability is illustrated via an anonymised example, showing performance monitoring in practice. |
| Stakeholder Engagement & Third-party Risk | EDM05— Ensured Stakeholder Engagement: “Ensure that stakeholders are informed about the governance system’s performance and results”. | 7.2.5 Security-positive culture: “Top management should require, promote and support coordination to establish a positive information security culture”. 7.3.5 Communicate: “Report to external interested parties that the entity practices a level of information security commensurate with the nature of its activities and priorities”. | Stakeholder engagement, user awareness, and cultural adaptation in digitalised environments. |
| Business Objectives | IT Objectives |
|---|---|
| Increase system-wide sales by maintaining high digital penetration (70%+ of all orders) and growing online delivery share (currently 85% of delivery) | Ensure 99.9% uptime and sub-second response time for mobile/web ordering platforms during peak hours; scale Azure Kubernetes Service (AKS) infrastructure dynamically to handle traffic surges without degradation. |
| Maintain customer satisfaction through fast, reliable, and seamless digital experiences | Optimize end-to-end order fulfilment cycle time via real-time monitoring (Prometheus/Grafana/New Relic); reduce app crash rate to <0.1% and improve average page load time to under 1.5 s. |
| Ensure secure, compliant processing of payment transactions and customer data (PCI-DSS, privacy regulations) | Implement and maintain a formal Information Security Management System (ISMS) with annual third-party audits; enforce least-privilege access controls across all systems handling PII and payment data. |
| Support rapid product innovation and promotional agility (e.g., new menu launches, pricing experiments) | Enable CI/CD pipelines for zero-downtime deployment of new features and promotions; provide API-driven integration between CRM, POS, and marketing automation tools for targeted campaigns. |
| Optimize operational cost per order while scaling the store network (700+ locations) | Leverage cloud cost optimization tools (Azure Cost Management) to reduce infrastructure spend by 15% YoY; automate store-level technology provisioning via Infrastructure-as-Code (IaC). |
| Maintain executive and regulatory confidence as a publicly listed entity with significant third-party dependencies | Deliver quarterly cybersecurity risk reports to the Executive Committee; ensure documented SLAs and incident response coordination with the national managed services provider. |
| Business Objectives | IT Objectives | Cybersecurity Objectives | Key Initiatives/Control Sets (ISO Refs) | Accountable Owner & Timeline with KPI/KRI (MEA-Aligned) |
|---|---|---|---|---|
| Increase system-wide sales by maintaining high digital penetration (70%+ of all orders) and growing online delivery share (currently 85% of delivery) | Ensure 99.9% uptime and sub-second response time for mobile/web ordering platforms during peak hours; scale Azure Kubernetes Service (AKS) infrastructure dynamically to handle traffic surges without degradation. | Implement availability controls aligned with ISO/IEC 27001:2022 Clause 8.2 information security risk assessment. Ensure service continuity under load; embed DDoS protection and application-level WAF within AKS ingress to prevent disruption of revenue-generating channels. | High-availability architecture reviews; capacity/run-book tests; WAF & DDoS tuning; change gating for peak campaigns. ISO/IEC 27001 8.3; A.5.1, (info sec policy), A.8.6 (capacity management) A.5.30. (ICT readiness for business continuity) | CIO & CISO; Q2–Q3. KPI: % availability vs. SLA; failover MTTR. KRI: capacity breaches at peak. Review: MEA01. |
| Maintain customer satisfaction through fast, reliable, and seamless digital experiences | Optimize end-to-end order fulfillment cycle time via real-time monitoring (Prometheus/Grafana/New Relic); reduce app crash rate to <0.1% and improve average page load time to under 1.5 s. | Enforce secure software development lifecycle (SSDLC) practices to prevent vulnerabilities in user-facing applications; align with ISO/IEC 27001:2022 for secure development and testing. | Threat-model & SAST/DAST in pipeline; SBOM + dependency scanning; blue-green releases with rollback. ISO/IEC 27001 A.8.25 (Secure development life cycle), A.8.26 (Application security requirements), A.8.27 (Secure system architecture), A.8.28.(Secure coding), A.8.29 (Security testing in development) | Head of AppDev & CISO; Q2 pilot/Q3 rollout. KPI: % services with SSDLC gates; defect escape rate. KRI: P1 vulns age. Review: MEA01. |
| Ensure secure, compliant processing of payment transactions and customer data (PCI-DSS, privacy regulations) | Implement and maintain a formal Information Security Management System (ISMS) with annual third-party audits; enforce least-privilege access controls across all systems handling PII and payment data. | Establish a Privacy Information Management System (PIMS) per ISO/IEC 27701:2025, ensuring lawful processing of customer data; integrate PCI-DSS controls into cloud architecture (e.g., tokenization, encryption at rest/in transit). | RoPA (Record of Processing Activities), DPIA (Data Privacy Impact Assessment) where needed; tokenisation and key management; PCI DSS attestation workflow; least-privilege enforcement. ISO/IEC 27701; ISO/IEC 27001 A.8.10-13 (information deletion, data masking, data leakage prevention, information backup); A.5.34 (privacy and protection of PII) | DPO & CISO; Q2 gap analysis/Q3 remediation. KPI: % systems with RoPA; % PCI controls passed. KRI: privacy incidents per 10k tx. Review: MEA03. |
| Support rapid product innovation and promotional agility (e.g., new menu launches, pricing experiments) | Enable CI/CD pipelines for zero-downtime deployment of new features and promotions; provide API-driven integration between CRM, POS, and marketing automation tools for targeted campaigns. | Apply security-by-design principles to DevOps pipelines; ensure automated vulnerability scanning and secrets management are integrated into CI/CD—supporting ISO/IEC 27001:2022 A.8.25-29 and 27014’s “integration with enterprise architecture”. | Automated Vulnerability scanning; secrets detection; container baseline hardening; feature-flag kill-switches. ISO/IEC 27001 A.8.25-29 (secure development life cycle, application security requirements, secure system architecture, secure coding, security testing in development) | DevOps Lead; Q2–Q4 phased. KPI: % pipelines with security gates; time-to-restore. KRI: leaked secret events. Review: MEA01. |
| Optimize operational cost per order while scaling the store network (700+ locations) | Leverage cloud cost optimization tools (Azure Cost Management) to reduce infrastructure spending by 15% YoY; automate store-level technology provisioning via Infrastructure-as-Code (IaC). | Implement cloud security posture management (CSPM) to detect misconfigurations that could lead to breaches or financial loss; align with ISO/IEC 27001:2022 Clause 8.2 information security risk assessment on asset management and protection. | CSPM policies (public storage, key rotation, MFA); asset inventory reconciliation; zero-trust network rules. ISO/IEC 27001 Clause 8.2 information security risk assessment—A5.23 (information security for use of cloud services) | Cloud CoE Lead; Q2 baseline/Q3 enforcement. KPI: % compliant resources; cost-avoidance. KRI: critical misconfig count. Review: MEA01. |
| Maintain executive and regulatory confidence as a publicly listed entity with significant third-party dependencies | Deliver quarterly cybersecurity risk reports to the Executive Committee; ensure documented SLAs and incident response coordination with the national managed services provider. | Formalize third-party risk management per ISO/IEC 27036-3, including supplier agreements, continuous monitoring, and joint incident response plans; report security posture to board using ISO/IEC 27014:2020 Clause 7.3.4 (report on the effectiveness of the operation of each ISMS) | Supplier tiering; due diligence & contract clauses; continuous monitoring; incident notice terms. ISO/IEC 27036-2/-3; ISO/IEC 27014 Clause 7.3.5 Communicate. ISO/IEC 27001 A5.21-22 (managing information security in the ICT supply chain; monitoring, review and change management of supplier ser-vices) | Head of Procurement & Vendor Risk Manager with CISO; Q2 segmentation/Q3 contracts. Key Performance Indicator: % critical suppliers with 27036 clauses; % with evidence of controls. Key Risk Indicator: supplier non-conformities. Review: MEA03. |
| Cybersecurity Strategy Themes | Step 1—Review & Align (Business–IT): key Actions | Step 2—Develop/Revise IT Strategy (via COBIT 2019) | Step 3—Define Cybersecurity Strategy (via ISO/IEC 27000) |
|---|---|---|---|
| Strategic Alignment of Business, IT & Security | Link IS/IT objectives to enterprise goals; define value targets | APO02 (Managed strategy), APO05 (Managed portfolio), APO06 (Managed Budget and Costs) | 27014: Clause 7.3.3 Direct (approve IS strategy); 27001: Clause 6.2 Information Security objectives, Clause 5 Leadership, annex A (alignment controls) |
| Integrated Risk & Compliance Management | Set risk appetite/criteria; identify compliance obligations | APO12 (Managed risk), MEA03 (compliance), EDM03 (Ensured risk optimization) | 27014: Clause 7.2.2 risk-based decisions; 27001: Clause 6.2/6.3 risk assessment/treatment plan; map key obligations |
| Performance Monitoring & Assurance | Choose KPIs/KRIs; review cadence; accountability | MEA01 (performance), MEA02 (Managed internal control), MEA03 (Managed Compliance with External Requirements) | 27014: Clause 7.3.4 Monitor Clause 7.3.5 Communicate; 27001: Clause 9 (performance evaluation) |
| Cybersecurity Governance & Culture | Define “tone from the top”; roles/mandates; awareness goals | EDM01 (Ensured governance framework), APO07 (Managed Human Resource), APO08 (Managed relationships) | 27014: Clause 7.2 governance objectives Inc. Clause 7.2.5 Foster a security-positive culture; 27001: Clause 7.2-7.4 (competence/awareness/communication) |
| IT Strategy & Digitalisation | Prioritise digital adoption/retirement; sourcing choices | APO02 (managed strategy), BAI01 (Manage all programs from the investment portfolio in alignment with enterprise strategy), DSS01 (managed operations: coordinate and execute the activities and operational procedures required to deliver internal and outsourced I&T services), EDM04 (managed resource optimization) | 27014: Clause 7.2.3 (direction of acquisition); 27001: Cloud & ICT Supply Chain controls (A.5.21, A.5.23) |
| Stakeholder Engagement & Third-Party Risk | Set expectations/outcomes for stakeholders and suppliers | EDM05 (stakeholder engagement), APO10 (managed vendors) DSS01-DSS04 (Deliver, Service and Support domain) | 27014: report to interested parties; 27036: supplier governance; 27001: A.5.19-22 supplier controls |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Metin, B.; Sevim, S.B.; Wynn, M. Cybersecurity Strategy Development: Towards an Integrated Approach Based on COBIT and ISO 27000 Series Standards. Standards 2025, 5, 33. https://doi.org/10.3390/standards5040033
Metin B, Sevim SB, Wynn M. Cybersecurity Strategy Development: Towards an Integrated Approach Based on COBIT and ISO 27000 Series Standards. Standards. 2025; 5(4):33. https://doi.org/10.3390/standards5040033
Chicago/Turabian StyleMetin, Bilgin, Sibel Berfun Sevim, and Martin Wynn. 2025. "Cybersecurity Strategy Development: Towards an Integrated Approach Based on COBIT and ISO 27000 Series Standards" Standards 5, no. 4: 33. https://doi.org/10.3390/standards5040033
APA StyleMetin, B., Sevim, S. B., & Wynn, M. (2025). Cybersecurity Strategy Development: Towards an Integrated Approach Based on COBIT and ISO 27000 Series Standards. Standards, 5(4), 33. https://doi.org/10.3390/standards5040033








