1. Introduction
The usual convolution and correlation operations have been used in some optical systems for image processing, such as filtering, encryption, decryption, comparison, authentication, pattern recognition and classification of images [
1,
2,
3,
4,
5,
6]. Shift operation has also been used in optical systems; for instance, shift operation is utilized at the input plane of the joint transform correlator (JTC) architecture in order to place two non-overlapping data distributions side-by-side [
7,
8]. The usual shift, convolution and correlation operators have been defined using the fractional Fourier transform [
9,
10] and these fractional operators were applied to the sampling theorem for fractional bandlimited signal [
11], time-variant filtering for non-stationary random signals [
12] and prediction, interpolation and filtering of
-stationary random signals [
13], where
is the fractional order of the fractional Fourier transform [
10].
In this paper, we propose to define a new generalized shift, convolution and correlation operators based on the gyrator transform (GT). The GT can be implemented using an optical system [
14,
15] or a digital algorithm [
16]; these implementations are used in applications of filtering and encryption of images, holography, beam characterization, optical mode converter and phase-amplitude retrieval, among other things [
17,
18]. The generalized shift is the simultaneous application of a spatial shift and a modulation by a pure linear phase term that does not introduce a shift in the gyrator domain (GD). The proposed convolution and correlation operators are generalized versions of the usual convolution and correlation operations and these generalized versions depend on the parameter
, which is the rotation angle of the GT. We provide explicit integral equations to compute the new convolution and correlation operators at the spatial domain. The new proposed convolution and correlation operators can also be computed in the GD using two GTs and a pure phase term. We apply the proposed new operators with the purpose of developing and defining the sampling theorem for images whose resulting GT has finite support. This result is important when it is necessary to sample properly the spatial domain or the GD of an optical system based on the GT. Finally, we present the application of the proposed new operators in order to describe and to simulate a nonlinear JTC-based encryption system in the GD [
19,
20].
2. The Gyrator Transform (GT) Operator
The gyrator transform (GT) operator at parameter
, which is the rotation angle, of a two-dimensional function
is [
14]
where
x and
y denote the coordinates at the spatial domain,
u and
v indicate the output coordinates in the gyrator domain (GD),
is the gyrator kernel and the possible values of the rotation angle are in the following interval
. For
, it corresponds to the identity transform. For
, it reduces to the direct Fourier transform with rotation of the coordinate at
. For
, the reverse transform is obtained. For
, it corresponds to the inverse Fourier transform with rotation of the coordinate at
[
14]. The inverse GT corresponds to the GT at rotation angle
. There are certain similarities in the properties of the GT and the fractional Fourier transform; however, these transforms are basically different, because the kernel of the GT is a product of the hyperbolic and plane waves, whereas the kernel of the fractional Fourier transform is the product of the spherical and the plane waves [
19].
The main properties of the GT, which will be used below in the following sections, are
where
,
,
and
are real constants. We can observe in Equations (
4) and (
5) that a shift or a modulation by a pure linear phase term applied to the function
produces a shift of the GT
, which is proportional to the parameters
,
,
,
and
. These properties of the shift or modulation by a pure linear phase term also introduce another modulation by a pure linear phase term in the GD. Other properties of the GT are described in [
14].
3. Generalized Shift Operator
We propose a generalized shift operator as the simultaneous application over a function of a spatial shift and a specific modulation by a pure linear phase term. The generalized shift operator at parameters , and is defined as
The generalized shift operator is a commutative group for a given parameter . The composition law is . When the parameter is equal to , the generalized shift operator is reduced to the usual shift operator . The GT at parameter of the generalized shift operator is given by
From the two previous equations, the parameter
corresponds to the rotation angle of the GT. The generalized shift operator does not produce a shift of the GT
in comparison with Equations (
4) and (
5). This property is very useful for centred optical systems.
4. Convolution Operator in the GD
We define a new convolution operator at parameter in the spatial domain by using the following integrals
The GTs of and allow to write the previous equation in the following form
The proposed convolution operator at parameter
in the GD can be computed using the product of the resulting GTs at parameter
of the functions
and
and the pure phase term given by
. The usual convolution is obtained from Equation (
8) when
, i.e.,
. The new convolution of a function
and a shifted Dirac delta function
is
Therefore, the generalized shift operator can be expressed in terms of the convolution operator proposed in this work
The proposed new convolution operator is invariant to the generalized shift operator
5. Correlation Operator in the GD
We propose the definition of a new correlation operator at parameter in the spatial domain by using the following integrals
Using the GTs and , the integral form of the new correlation operator can be expressed as
The new correlation operator at parameter in the GD is computed using the product of the GTs and and the pure phase term given by . The new correlation operator is reduced to the usual correlation when , i.e., . The new correlation operator is also invariant to the generalized shift operator
6. Sampling Theorem in the GD
Nowadays, the optical implementations of image processing systems are mainly carried out using optoelectronic devices, such as spatial light modulators or cameras. These devices introduce a sampling over the optical wave that it is used in an optical image processing system. Therefore, a right sampling at the spatial domain is necessary for a current optical image processing system when all features of the resulting GT for an image must be preserved by the mentioned optoelectronic devices.
In this section, we use the proposed operators in order to describe the sampling theorem for images whose resulting GT has finite support. We define a new Dirac comb function at parameter with periods and by
The GT at parameter of the new Dirac comb function is
Therefore, the GT at parameter of the new Dirac comb function at parameter with periods and is another new Dirac comb function at parameter with periods and .
In order to describe the sampling theorem in the GD, we consider a function whose GT has a finite support for the horizontal coordinate u and for the vertical coordinate v. The following function represents shifted replicas of
The inverse GT at parameter of the previous equation is
Equation (
19) is a sampled version of
for the sampling periods of the coordinates
x and
y given by
and
, respectively. The reconstruction of
is computed by using the image filtering of the function
with a low-pass filter in the GD; this image filtering is described with the proposed convolution operator of
Section 4. Thus, the reconstruction of
is
The low-pass filter in the GD is a rectangle whose extension on the horizontal coordinate is
and the extension on the vertical coordinate is
. Therefore, the extension of the low-pass filter in the GD is given by the size of the finite support of the GT
. Equation (
20) is the sampling theorem in the GD and this equation provides the values of
for every
x and
y in terms of the sampled version of
whenever the sampling periods are defined using the following conditions
and
. If the previous condition is not fulfilled, the reconstruction of
will have aliasing.
7. Optical Image Encryption System Using a Nonlinear Joint Transform Correlator (JTC) in the GD
Several optical image processing systems can be described and analysed using the new operators proposed in this work. The use of these new operators allows for an easy, simple and compact description of the behaviour for some optical image processing systems in the GD.
The proposed operators of the previous sections are used with the purpose of describing and simulating the nonlinear JTC-based encryption system that was presented in the work of references [
19,
20]. The real-valued image to encrypt
has their values in the interval [0, 1] and the two random phase masks (RPMs)
and
are represented by
where
and
are normalized positive functions randomly generated, statistically independent and uniformly distributed in the interval [0, 1].
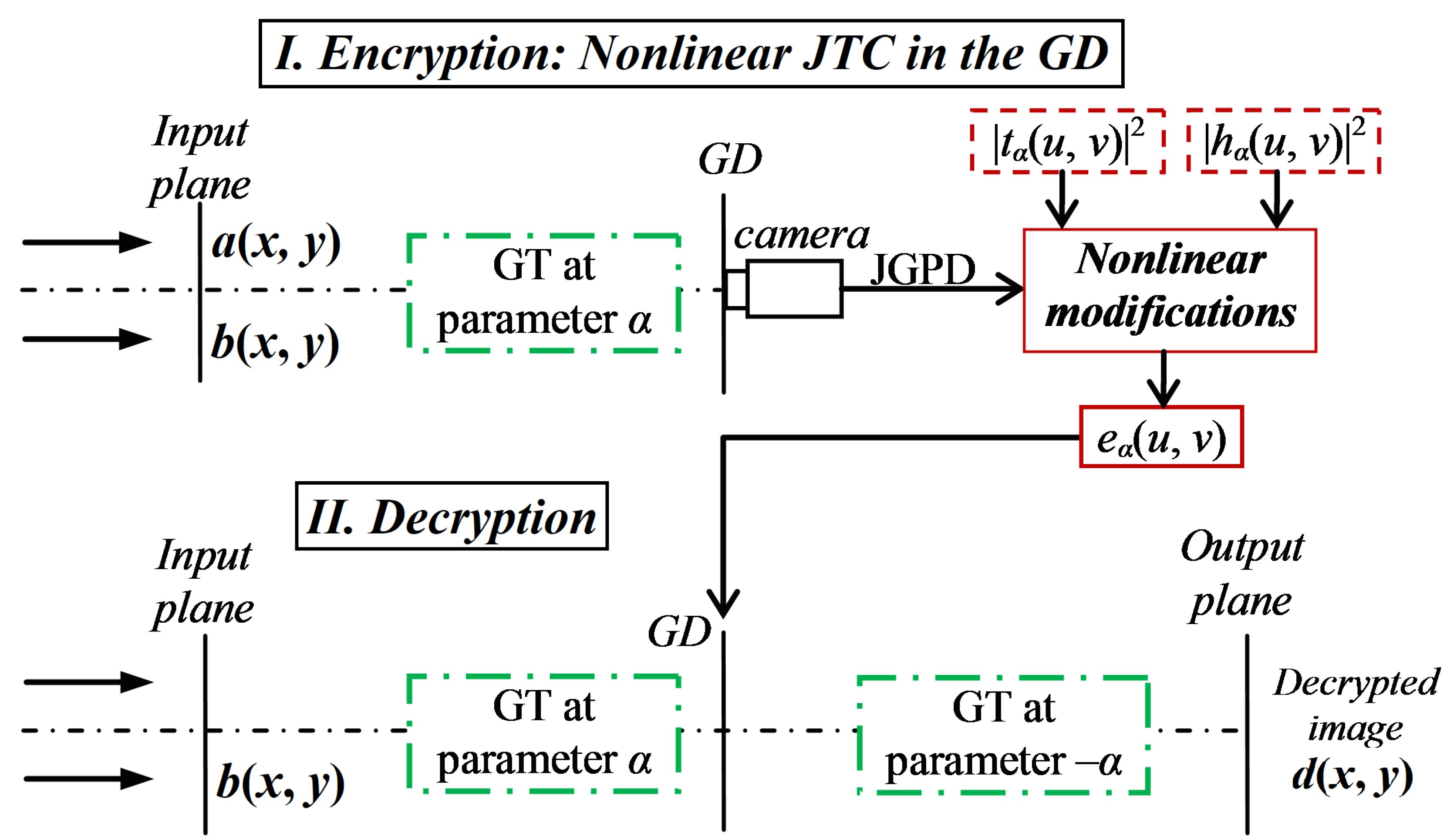
Figure 1 (part I) depicts the optical encryption scheme based on a nonlinear JTC architecture in the GD. The input plane of the JTC-based encryption system uses two non-overlapping data distributions placed side-by-side. The first data distribution
is the result given by the application of the generalized shift operator at parameters
,
and
over the real image to encrypt
placed against the RPM
The second data distribution of the input plane of the JTC corresponds to the result given by the application of the generalized shift operator at parameters , and over the RPM
The GT at parameter of the distributions and are denoted by
For the encryption system, the joint gyrator power distribution (JGPD) at parameter
is the intensity of the GT at parameter
applied over the input plane of the JTC [
19]
The encrypted image is computed using the following nonlinear processing on the JGPD [
19]
If
is equal to zero for a particular value of
u and
v, this intensity value is substituted by a small constant to avoid singularities when computing
. The encrypted image is a real-valued image that can be computed using the following three intensity distributions:
,
and
. The security keys of the encryption system are given by the RPM
and the rotation angle
of the GT. The RPM
is used to spread the information content of the original image
onto the encrypted image
[
19]. The inverse GT at parameter
of Equation (
26) denotes the encrypted image
in the spatial domain
where
. Therefore, the encrypted image
of reference [
19] can be described using the proposed generalized shift, convolution and correlation operators in this work.
For the initial step of the decryption system depicted in
Figure 1 (part II), we perform the product of the GT of the second data distribution
and the encrypted image
, in order to obtain the following result
Using the result of Equations (
7), (
9) and (
14), the inverse GT at parameter
of the previous equation is the output plane
of the decryption system
where
. The proposed operators in this work can also be used in order to describe the output plane
of the decryption system presented in reference [
19]. If we take the absolute value of the second term of the right side of Equation (
29), we obtain the decrypted image
centred at coordinates
and
We perform the numerical simulations of the encryption and decryption systems that were described using the the proposed generalized shift, convolution and correlation operators in this work.
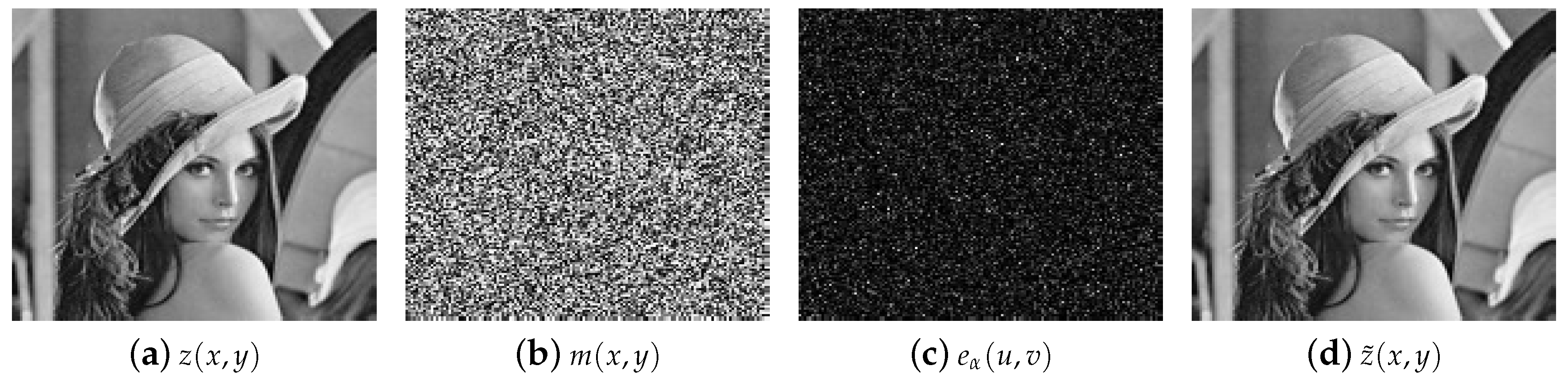
Figure 2a,b show the original image to encrypt and the random distribution code
of the RPM
, respectively. The random distribution code
of the RPM
has a similar appearance to the image presented in
Figure 2b but different values for their pixels. The image presented in
Figure 2c corresponds to the encrypted image
for the security keys
and the RPM
. The decrypted image
is shown in
Figure 2d when the right values of the security key are used in the decryption system. If a wrong value of the rotation angle
of the GT or an incorrect RPM
are used in the decryption process, the obtained decrypted image will be a random distribution image. In reference [
19], the authors showed that the sensitivity of the rotation angle of the GT over the resulting decrypted images is much higher than the sensitivity shown by the encryption–decryption system that uses generalized JTC to variations in the fractional order of the fractional Fourier transform.