Smart Home Gateway Based on Integration of Deep Reinforcement Learning and Blockchain Framework
Abstract
:1. Introduction
- Using a blockchain network for the smart home to investigate the problem of security.
- Evaluating the common IoT devices of the smart home based on hardware implementation.
- Presenting the architecture of a smart home gateway to relieve the recent challenges of the smart home.
- Improving the performance of the proposed system compared with other existing works.
- Deep Reinforcement Learning applied to predict and interpret the data.
- Deep Reinforcement Learning creates the safer smart home using IoT sensors for improving the performance of the process.
2. Related Works
2.1. Smart Home Based on Public Blockchain
2.2. Smart Home Based on Private Blockchain
2.3. Smart Home Gateway
2.4. Smart Home Based on Reinforcement Learning
3. Integration of Blockchain and Deep Reinforcement Learning in Smart Homes
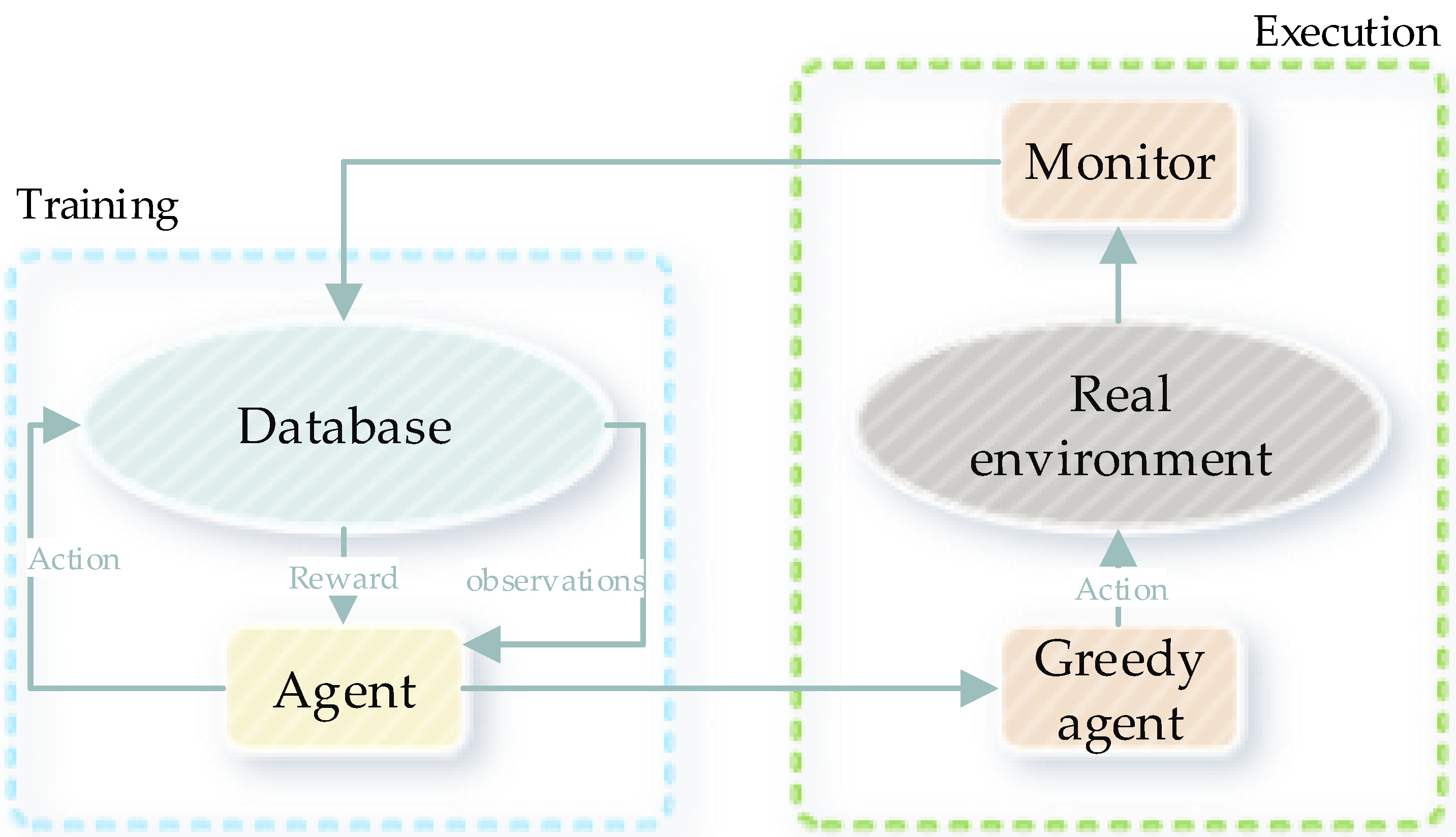
3.1. Deep Reinforcement Learning
Markov Decision Process and Q-Learning
| Algorithm1: Smart home simulation process |
|
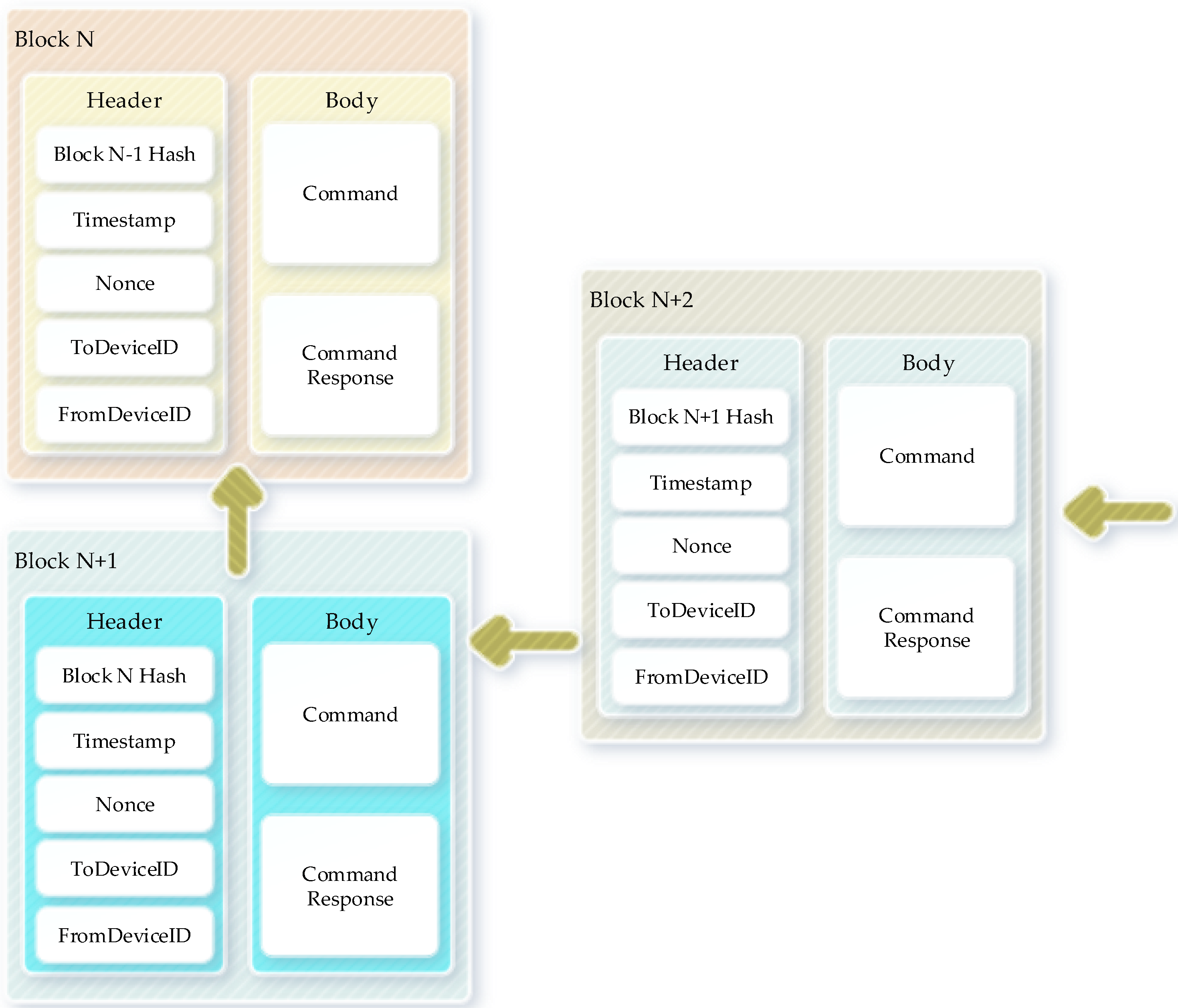
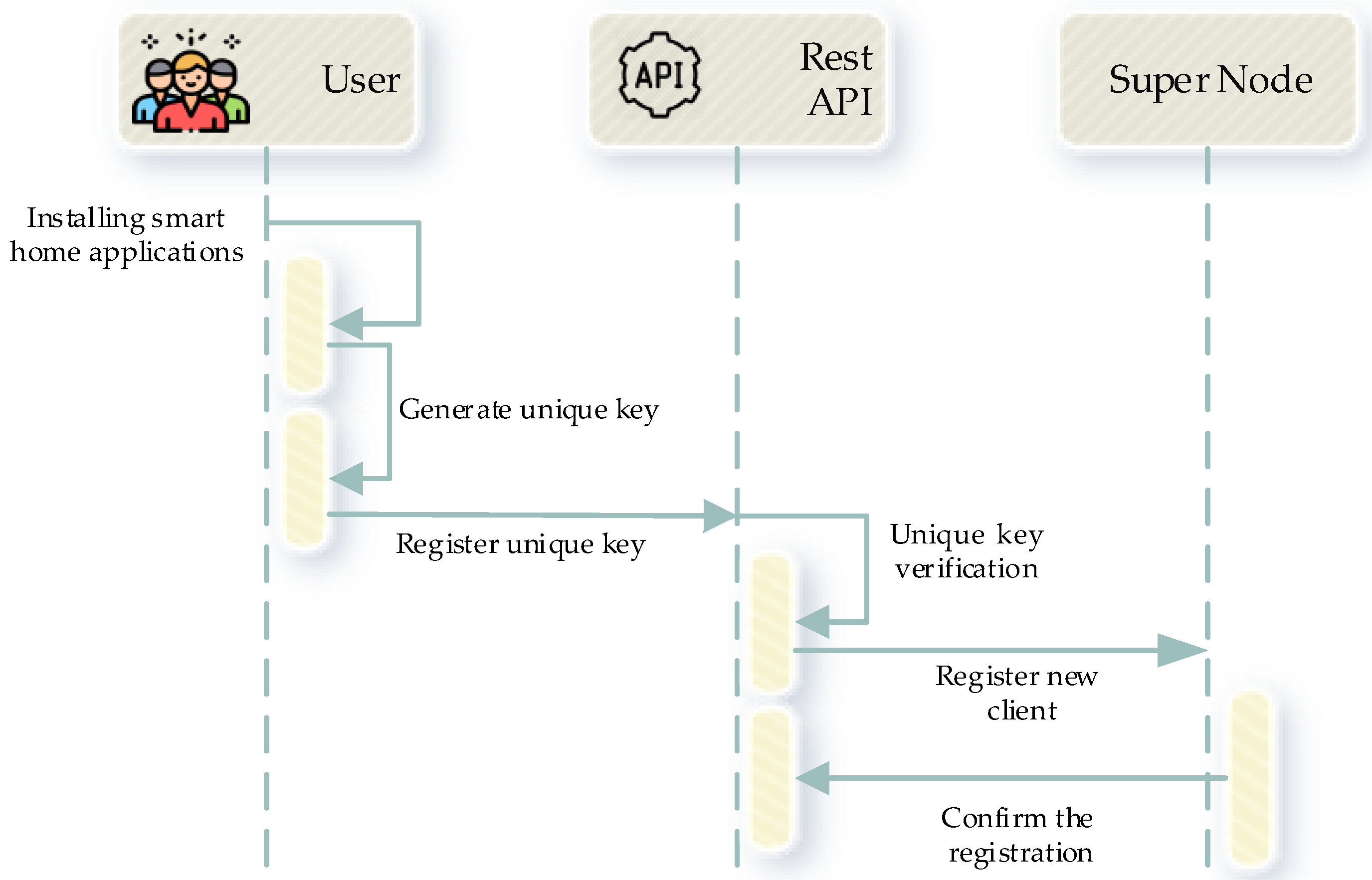
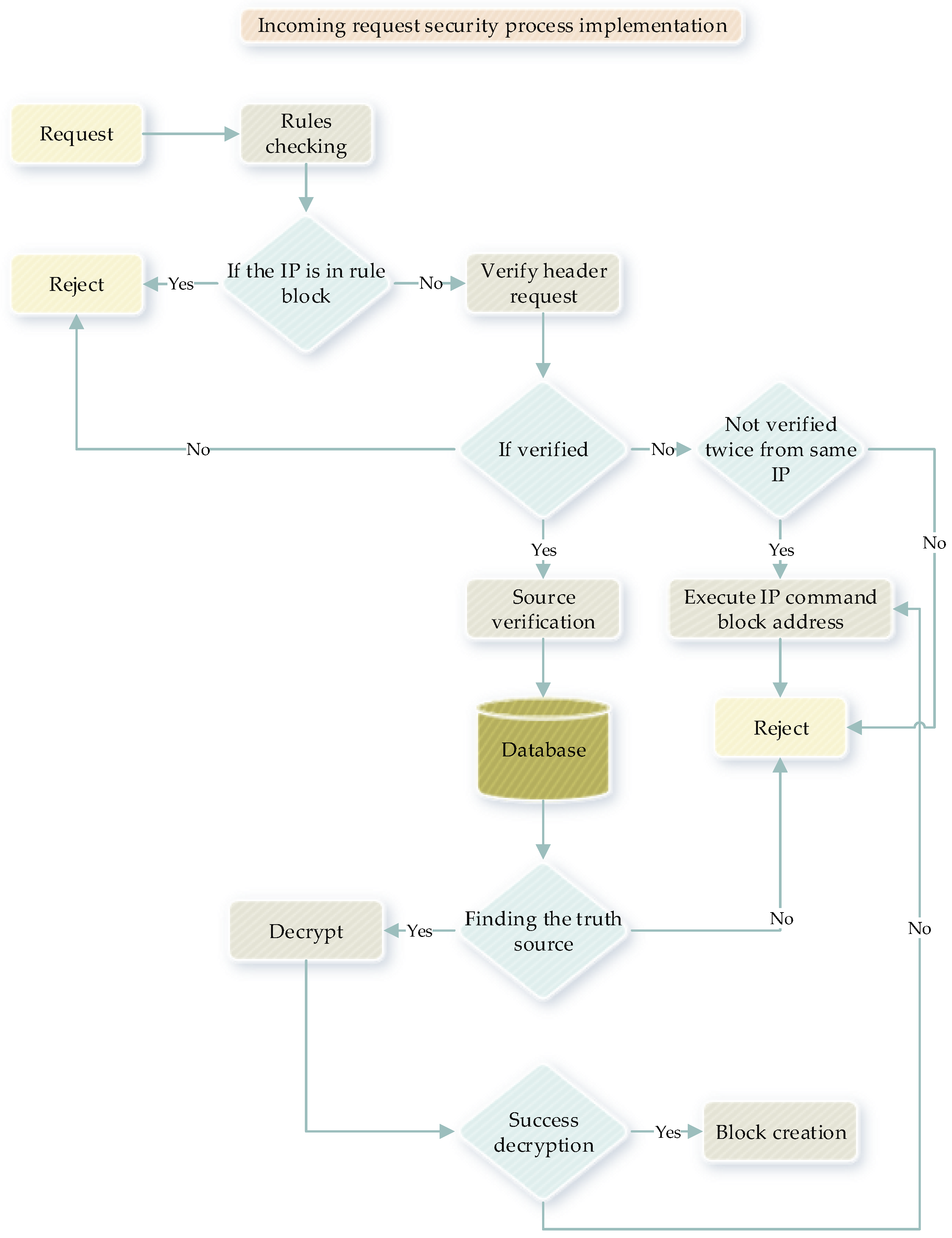
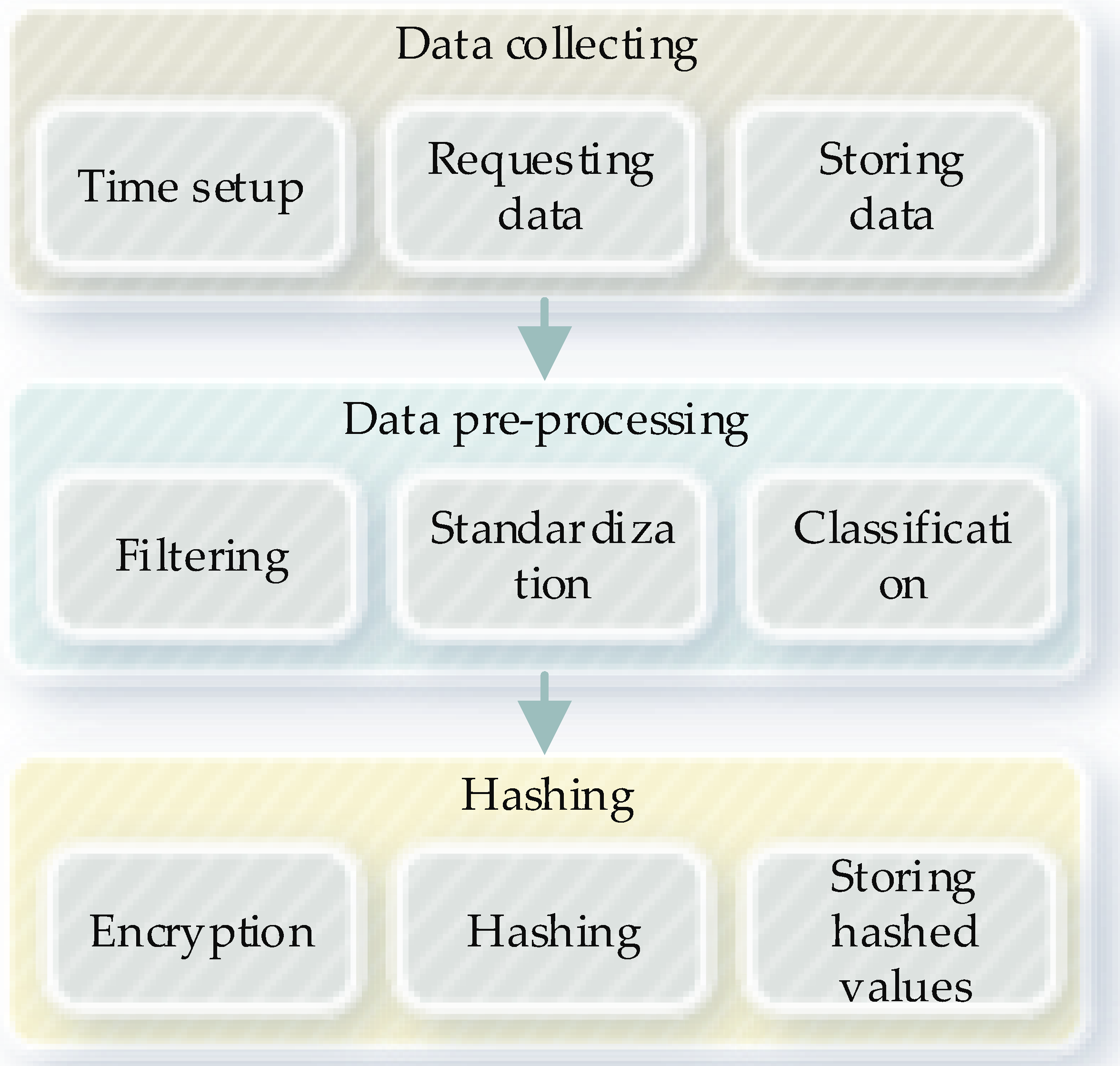
3.2. Gateway Network Based on Blockchain in Smart Homes
- Previous Block Hash: To keep the blockchain framework tamper-proof, the blocks always record the previous block hash information.
- Timestamp: To record the start and end time of any event, the timestamp is added to the block, stores the metadata, and logs as temporal information.
- Nonce: Nonce is a mathematical evaluation target value for generating the random numbers.
- FromDeviceID: Record of the coming transactions of the source device.
- ToDeviceID: Record the destination of the transaction of the target device.
4. Results and Discussion
4.1. Development Environment
4.2. Data
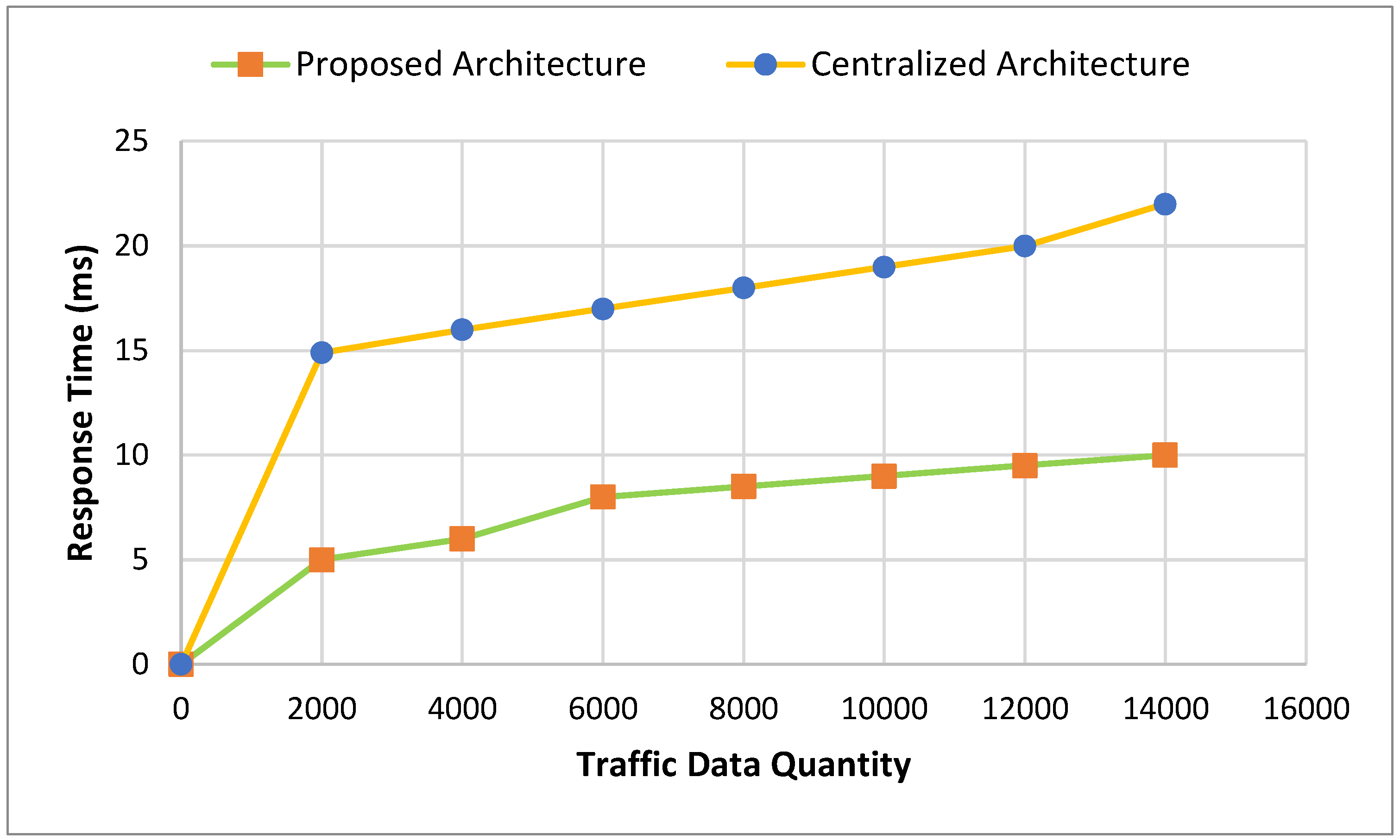
4.3. Blockchain Framework Performance in Smart Homes
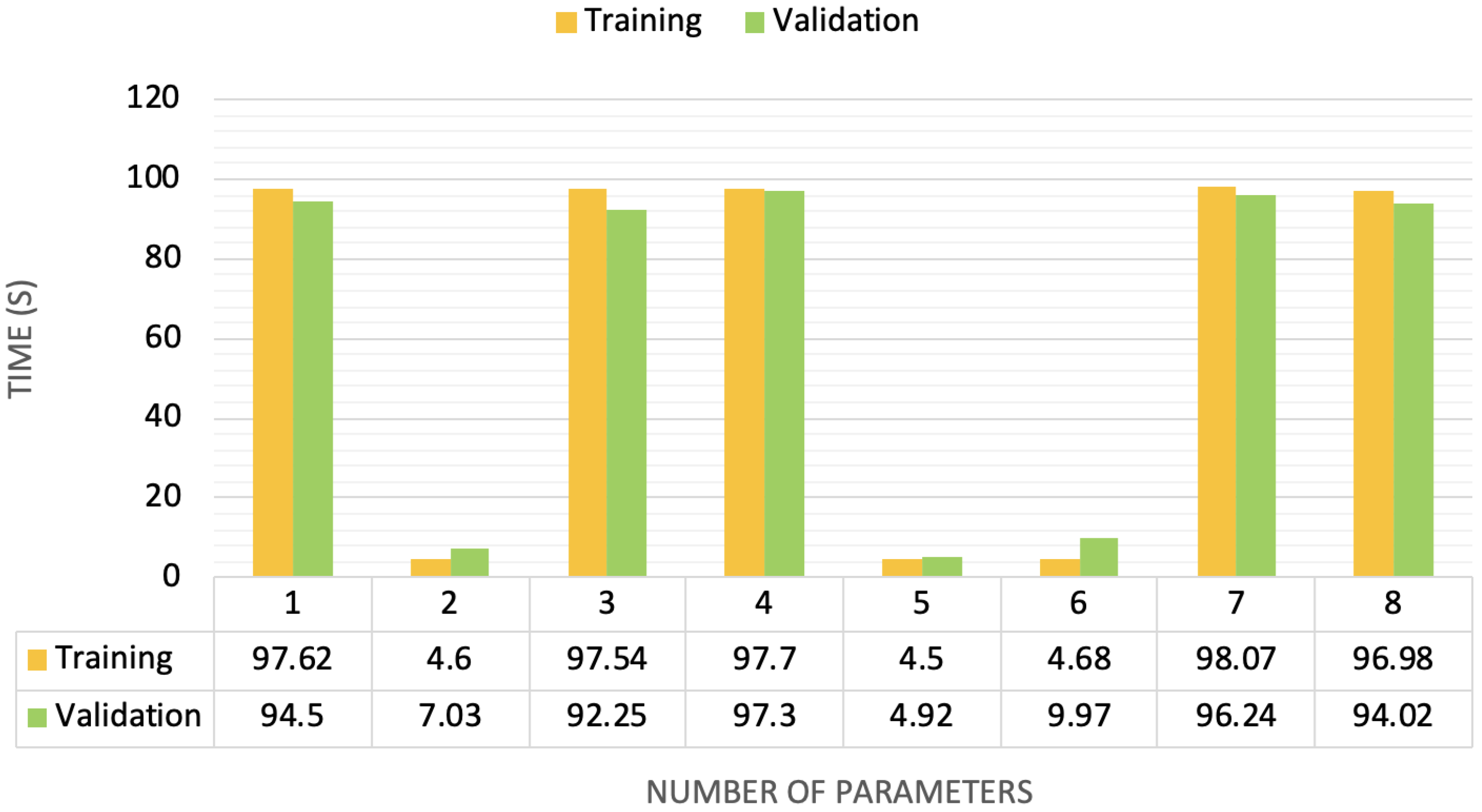
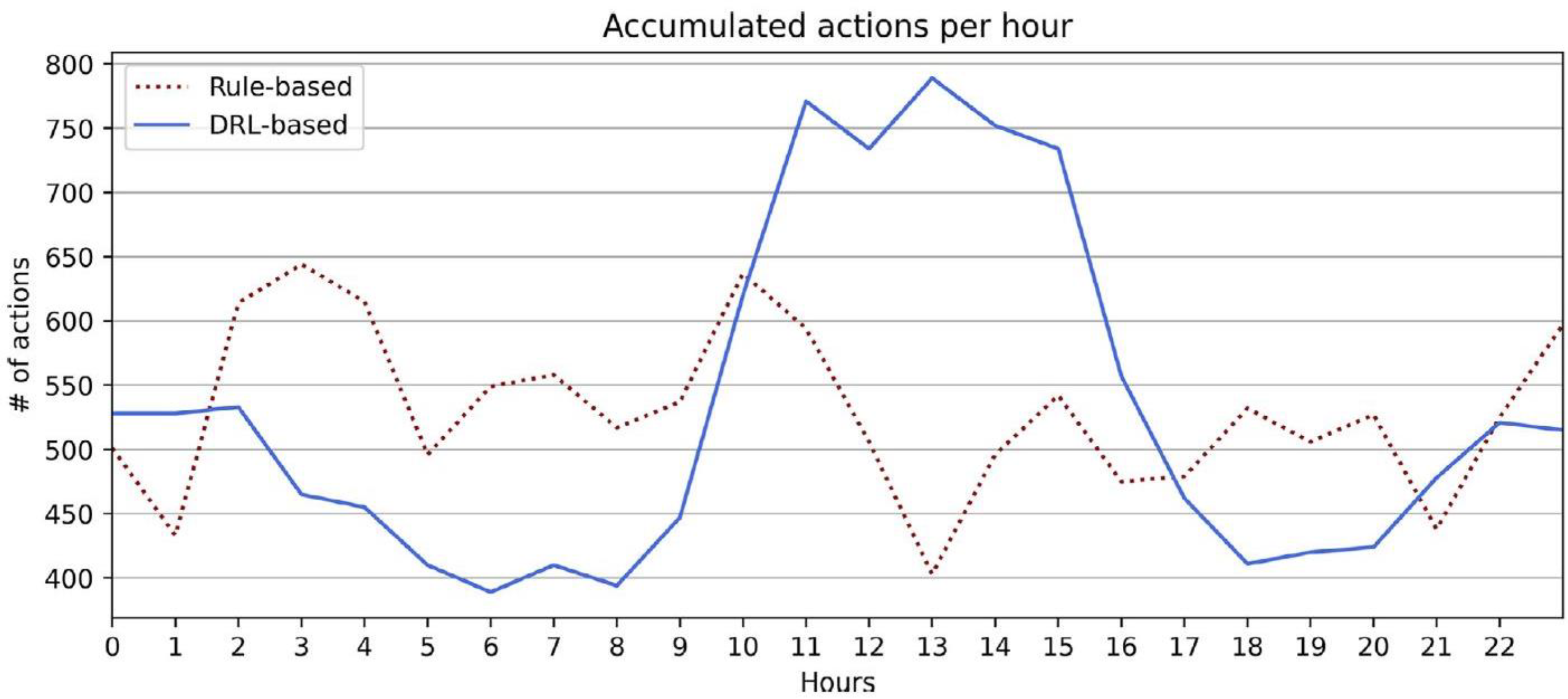
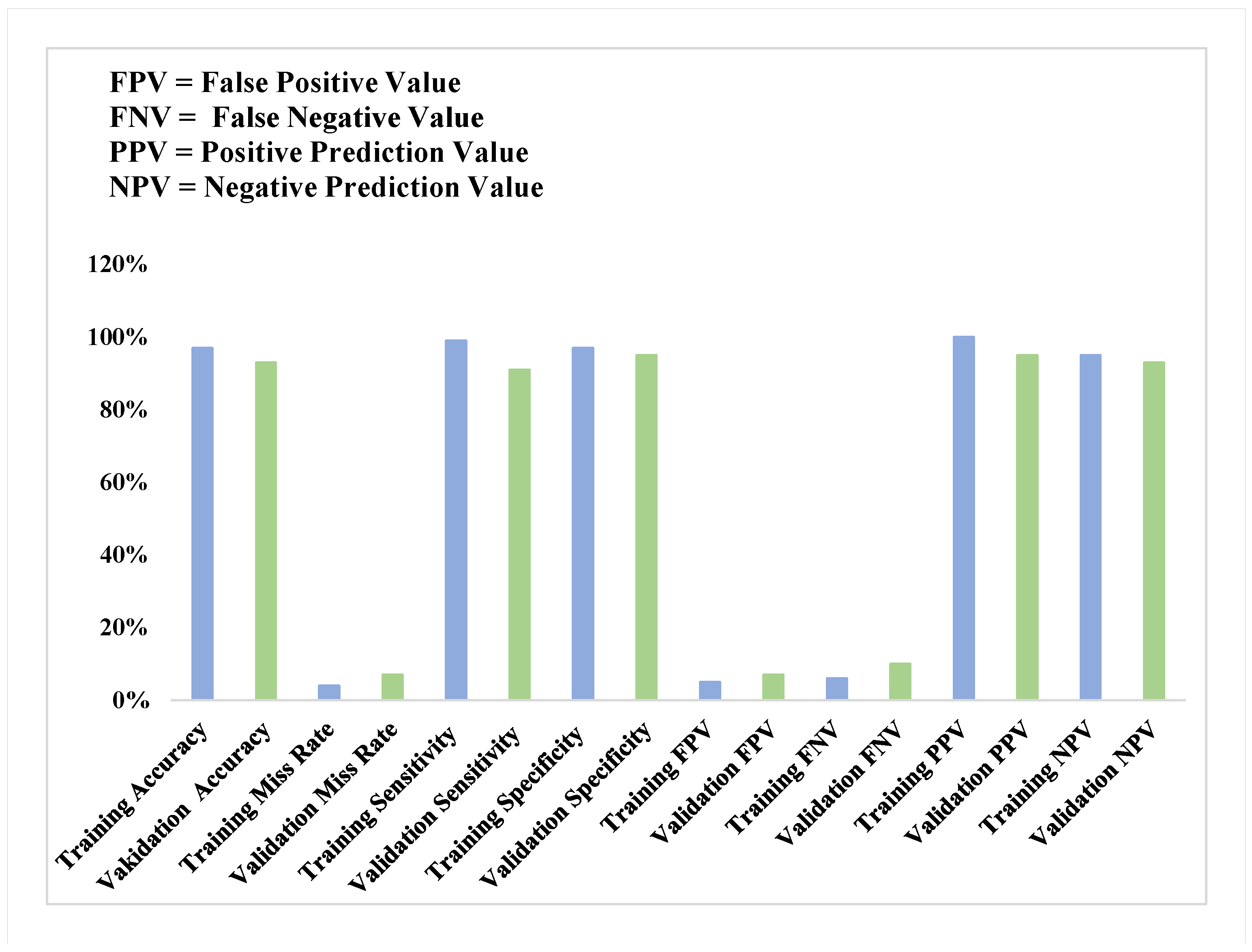
4.4. Deep Reinforcement Learning Performance in Smart Homes
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Alam, M.R.; St-Hilaire, M.; Kunz, T. Peer-to-peer energy trading among smart homes. Appl. Energy 2019, 238, 1434–1443. [Google Scholar] [CrossRef]
- Rivera, J.; Meulen, R. Competition Is Increasing to Be the IoT Gateway to the Connected Home. Gartner. 2015. Available online: https://www.gartner.com/en/newsroom/press-releases/2015-08-06-gartner-says-competition-is-increasing-to-be-the-iot-gateway-to-the-connected-home (accessed on 6 August 2015).
- Shouran, Z.; Ashari, A.; Priyambodo, T. Internet of things (IoT) of smart home: Privacy and security. Int. J. Comput. Appl. 2019, 182, 3–8. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT security: An exhaustive survey on IoT vulnerabilities and a first empirical look on internet-scale IoT exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Sovacool, B.K.; Martiskainen, M.; Del Rio, D.D.F. Knowledge, energy sustainability, and vulnerability in the demographics of smart home technology diffusion. Energy Policy 2021, 153, 112196. [Google Scholar] [CrossRef]
- Ullah, F.; Al-Turjman, F. A conceptual framework for blockchain smart contract adoption to manage real estate deals in smart cities. Neural Comput. Appl. 2021, 1–22. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Sikdar, B.; Choo, K.K.R. Consumer IoT: Security vulnerability case studies and solutions. IEEE Consum. Electron. Mag. 2020, 9, 17–25. [Google Scholar] [CrossRef]
- Khattak, H.A.; Shah, M.A.; Khan, S.; Ali, I.; Imran, M. Perception layer security in Internet of Things. Future Gener. Comput. Syst. 2019, 100, 144–164. [Google Scholar] [CrossRef]
- Woodier, J.R.; Zingerle, A. The internet and cybersecurity: Taking the virtual fight to cybercrime and cyberwarfare. In Handbook of Terrorism and Counter Terrorism Post 9/11; Edward Elgar Publishing, 2019; Available online: https://www.elgaronline.com/view/edcoll/9781786438010/9781786438010.00011.xml (accessed on 4 December 2019).
- Touqeer, H.; Zaman, S.; Amin, R.; Hussain, M.; Al-Turjman, F.; Bilal, M. Smart home security: Challenges, issues and solutions at different IoT layers. J. Supercomput. 2021, 1, 37. [Google Scholar]
- Tzezana, R. Scenarios for crime and terrorist attacks using the internet of things. Eur. J. Future Res. 2016, 4, 1–7. [Google Scholar] [CrossRef] [Green Version]
- Li, T.; Xiao, Y.; Song, L. Integrating Future Smart Home Operation Platform With Demand Side Management via Deep Reinforcement Learning. IEEE Trans. Green Commun. Netw. 2021, 5, 921–933. [Google Scholar] [CrossRef]
- Geneiatakis, D.; Kounelis, I.; Neisse, R.; Nai-Fovino, I.; Steri, G.; Baldini, G. Security and privacy issues for an IoT based smart home. In Proceedings of the 2017 40th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 22–26 May 2017; IEEE: New York, NY, USA, 2017; pp. 1292–1297. [Google Scholar]
- Abdullah, T.A.; Ali, W.; Malebary, S.; Ahmed, A.A. A review of cyber security challenges attacks and solutions for Internet of Things based smart home. Int. J. Comput. Sci. Netw. Secur. 2019, 19, 139. [Google Scholar]
- Verma, A.; Prakash, S.; Srivastava, V.; Kumar, A.; Mukhopadhyay, S.C. Sensing, controlling, and IoT infrastructure in smart building: A review. IEEE Sens. J. 2019, 19, 9036–9046. [Google Scholar] [CrossRef]
- Brotsis, S.; Limniotis, K.; Bendiab, G.; Kolokotronis, N.; Shiaeles, S. On the suitability of blockchain platforms for IoT applications: Architectures, security, privacy, and performance. Comput. Netw. 2021, 191, 108005. [Google Scholar] [CrossRef]
- Tao, M.; Zuo, J.; Liu, Z.; Castiglione, A.; Palmieri, F. Multi-layer cloud architectural model and ontology-based security service framework for IoT-based smart homes. Future Gener. Comput. Syst. 2018, 78, 1040–1051. [Google Scholar] [CrossRef]
- Burhan, M.; Rehman, R.A.; Khan, B.; Kim, B.S. IoT elements, layered architectures and security issues: A comprehensive survey. Sensors 2018, 18, 2796. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kamran, M.; Khan, H.U.; Nisar, W.; Farooq, M.; Rehman, S.U. Blockchain and Internet of Things: A bibliometric study. Comput. Electr. Eng. 2020, 81, 106525. [Google Scholar] [CrossRef]
- Özyılmaz, K.R.; Yurdakul, A. Iot Blockchain integration: A Security Perspective. In Security Analytics for the Internet of Everything; 2020; p. 29. Available online: https://www.taylorfrancis.com/chapters/edit/10.1201/9781003010463-3/iot-blockchain-integration-kaz (accessed on 4 September 2021).
- Baucas, M.J.; Gadsden, S.A.; Spachos, P. IoT-based Smart Home Device Monitor Using Private Blockchain Technology and Localization. arXiv 2021, arXiv:2103.15896. [Google Scholar]
- Spathoulas, G.; Negka, L.; Pandey, P.; Katsikas, S. Can Blockchain Technology Enhance Security and Privacy in the Internet of Things? In Advances in Core Computer Science-Based Technologies; Springer: Berlin, Germany, 2021; pp. 199–228. [Google Scholar]
- Alam, S.R.; Jain, S.; Doriya, R. Security threats and solutions to IoT using Blockchain: A Review. In Proceedings of the 2021 5th International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 25–27 May 2021; IEEE: New York, NY, USA, 2021; pp. 268–273. [Google Scholar]
- Rathee, G.; Balasaraswathi, M.; Chandran, K.P.; Gupta, S.D.; Boopathi, C. A secure IoT sensors communication in industry 4.0 using blockchain technology. J. Ambient. Intell. Humaniz. Comput. 2021, 12, 533–545. [Google Scholar] [CrossRef]
- Shahbazi, Z.; Byun, Y.C. Improving the Product Recommendation System based-on Customer Interest for Online Shopping Using Deep Reinforcement Learning. Soft Comput. Mach. Intell. 2021, 1, 31–35. [Google Scholar]
- Shahbazi, Z.; Byun, Y.C. Integration of Blockchain, IoT and Machine Learning for Multistage Quality Control and Enhancing Security in Smart Manufacturing. Sensors 2021, 21, 1467. [Google Scholar] [CrossRef] [PubMed]
- Kumar, P.; Chouhan, L. A secure authentication scheme for IoT application in smart home. Peer-to-Peer Netw. Appl. 2021, 14, 420–438. [Google Scholar] [CrossRef]
- Alani, S.; Mahmood, S.N.; Attaallah, S.Z.; Mhmood, H.S.; Khudhur, Z.A.; Dhannoon, A.A. IoT based implemented comparison analysis of two well-known network platforms for smart home automation. Int. J. Electr. Comput. Eng. 2021, 11, 442–450. [Google Scholar] [CrossRef]
- Rastogi, R.; Jain, R.; Jain, P. IoT Applications in Smart Home Security: Addressing Safety and Security Threats. In Artificial Intelligence Paradigms for Smart Cyber-Physical Systems; IGI Global, 2021; pp. 251–277. Available online: https://www.igi-global.com/chapter/iot-applications-in-smart-home-security/266143 (accessed on 4 September 2021).
- Reyes-Campos, J.; Alor-Hernández, G.; Machorro-Cano, I.; Olmedo-Aguirre, J.O.; Sánchez-Cervantes, J.L.; Rodríguez-Mazahua, L. Discovery of Resident Behavior Patterns Using Machine Learning Techniques and IoT Paradigm. Mathematics 2021, 9, 219. [Google Scholar] [CrossRef]
- Jafari, S.; Shahbazi, Z.; Byun, Y.C. Improving the Performance of Single-Intersection Urban Traffic Networks Based on a Model Predictive Controller. Sustainability 2021, 13, 5630. [Google Scholar] [CrossRef]
- Cvitić, I.; Peraković, D.; Periša, M.; Gupta, B. Ensemble machine learning approach for classification of IoT devices in smart home. Int. J. Mach. Learn. Cybern. 2021, 1–24. [Google Scholar] [CrossRef]
- Shahbazi, Z.; Byun, Y.C. A framework of vehicular security and demand service prediction based on data analysis integrated with blockchain approach. Sensors 2021, 21, 3314. [Google Scholar] [CrossRef]
- Javed, A.R.; Fahad, L.G.; Farhan, A.A.; Abbas, S.; Srivastava, G.; Parizi, R.M.; Khan, M.S. Automated cognitive health assessment in smart homes using machine learning. Sustain. Cities Soc. 2021, 65, 102572. [Google Scholar] [CrossRef]
- Kaya, M.M.; Taşkiran, Y.; Kanoğlu, A.; Demirtaş, A.; Zor, E.; Burçak, İ.; Nacak, M.C.; Akgül, F.T. Designing a Smart Home Management System with Artificial Intelligence & Machine Learning. 2021. Available online: https://www.researchgate.net/profile/Mehmet-Muecahit-Kaya/publication/349869633_Designing_a_Smart_Home_Management_System_with_Artificial_Intelligence_Machine_Learning/links/604506e392851c077f241fd2/Designing-a-Smart-Home-Management-System-with-Artificial-Intelligence-Machine-Learning.pdf (accessed on 7 March 2021).
- Abbas, A.F.; Abdullah, M.Z. Design and Implementation of Tracking a user’s Behavior in a Smart Home. IOP Conf. Ser. Mater. Sci. Eng. 2021, 1094, 012008. [Google Scholar] [CrossRef]
- Elsayed, N.; Zaghloul, Z.S.; Azumah, S.W.; Li, C. Intrusion Detection System in Smart Home Network Using Bidirectional LSTM and Convolutional Neural Networks Hybrid Model. arXiv 2021, arXiv:2105.12096. [Google Scholar]
- Bokka, R.; Sadasivam, T. Deep Learning Model for Detection of Attacks in the Internet of Things Based Smart Home Environment. In Proceedings of the International Conference on Recent Trends in Machine Learning, IoT, Smart Cities and Applications, Hyderabad, India, 28–29 March 2021; Springer: Berlin, Germany, 2021; pp. 725–735. [Google Scholar]
- Suman, S.; Etemad, A.; Rivest, F. Potential Impacts of Smart Homes on Human Behavior: A Reinforcement Learning Approach. arXiv 2021, arXiv:2102.13307. [Google Scholar]
- Shahbazi, Z.; Byun, Y.C. Smart Manufacturing Real-Time Analysis Based on Blockchain and Machine Learning Approaches. Appl. Sci. 2021, 11, 3535. [Google Scholar] [CrossRef]
- Varshney, G.; Gupta, H. A security framework for IOT devices against wireless threats. In Proceedings of the 2017 2nd International Conference on Telecommunication and Networks (TEL-NET), Noida, India, 10–11 August 2017; IEEE: New York, NY, USA, 2017; pp. 1–6. [Google Scholar]
- Lazaroiu, C.; Roscia, M. Smart district through IoT and blockchain. In Proceedings of the 2017 IEEE 6th International Conference on Renewable Energy Research and Applications (ICRERA), San Diego, CA, USA, 5–8 November 2017; IEEE: New York, NY, USA, 2017; pp. 454–461. [Google Scholar]
- Aggarwal, S.; Chaudhary, R.; Aujla, G.S.; Jindal, A.; Dua, A.; Kumar, N. Energychain: Enabling energy trading for smart homes using blockchains in smart grid ecosystem. In Proceedings of the 1st ACM MobiHoc Workshop on Networking and Cybersecurity for Smart Cities; 2018; pp. 1–6. Available online: https://dl.acm.org/doi/abs/10.1145/3214701.3214704 (accessed on 25 June 2018).
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, Big Island, HI, USA, 13–17 March 2017; IEEE: New York, NY, USA, 2017; pp. 618–623. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. LSB: A Lightweight Scalable Blockchain for IoT security and anonymity. J. Parallel Distrib. Comput. 2019, 134, 180–197. [Google Scholar] [CrossRef]
- Zhou, Y.; Han, M.; Liu, L.; Wang, Y.; Liang, Y.; Tian, L. Improving iot services in smart-home using blockchain smart contract. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; IEEE: New York, NY, USA, 2018; pp. 81–87. [Google Scholar]
- Jamil, F.; Kim, D. Enhanced Kalman filter algorithm using fuzzy inference for improving position estimation in indoor navigation. J. Intell. Fuzzy Syst. 2021, 40, 8991–9005. [Google Scholar] [CrossRef]
- Jamil, F.; Cheikhrouhou, O.; Jamil, H.; Koubaa, A.; Derhab, A.; Ferrag, M.A. PetroBlock: A blockchain-based payment mechanism for fueling smart vehicles. Appl. Sci. 2021, 11, 3055. [Google Scholar] [CrossRef]
- Chandramohan, J.; Nagarajan, R.; Satheeshkumar, K.; Ajithkumar, N.; Gopinath, P.; Ranjithkumar, S. Intelligent smart home automation and security system using Arduino and Wi-fi. Int. J. Eng. Comput. Sci. (IJECS) 2017, 6, 20694–20698. [Google Scholar]
- Lin, H.; Bergmann, N.W. IoT privacy and security challenges for smart home environments. Information 2016, 7, 44. [Google Scholar] [CrossRef] [Green Version]
- Sivaraman, V.; Gharakheili, H.H.; Vishwanath, A.; Boreli, R.; Mehani, O. Network-level security and privacy control for smart-home IoT devices. In Proceedings of the 2015 IEEE 11th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Abu Dhabi, United Arab Emirates, 19–21 October 2015; IEEE: New York, NY, USA, 2015; pp. 163–167. [Google Scholar]
- Jamil, F.; Iqbal, N.; Ahmad, S.; Kim, D. Peer-to-Peer Energy Trading Mechanism based on Blockchain and Machine Learning for Sustainable Electrical Power Supply in Smart Grid. IEEE Access 2021, 9, 39193–39217. [Google Scholar] [CrossRef]
- Han, D.; Kim, H.; Jang, J. Blockchain based smart door lock system. In Proceedings of the 2017 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 18–20 October 2017; IEEE: New York, NY, USA, 2017; pp. 1165–1167. [Google Scholar]
- Xu, Q.; He, Z.; Li, Z.; Xiao, M. Building an ethereum-based decentralized smart home system. In Proceedings of the 2018 IEEE 24th International Conference on Parallel and Distributed Systems (ICPADS), Singapore, 11–13 December 2018; IEEE: New York, NY, USA, 2018; pp. 1004–1009. [Google Scholar]
- Singh, S.; Ra, I.H.; Meng, W.; Kaur, M.; Cho, G.H. SH-BlockCC: A secure and efficient Internet of things smart home architecture based on cloud computing and blockchain technology. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719844159. [Google Scholar] [CrossRef]
- Mohanty, S.N.; Ramya, K.; Rani, S.S.; Gupta, D.; Shankar, K.; Lakshmanaprabu, S.; Khanna, A. An efficient Lightweight integrated Blockchain (ELIB) model for IoT security and privacy. Future Gener. Comput. Syst. 2020, 102, 1027–1037. [Google Scholar] [CrossRef]
- Lee, Y.; Rathore, S.; Park, J.H.; Park, J.H. A blockchain-based smart home gateway architecture for preventing data forgery. Hum. Centric Comput. Inf. Sci. 2020, 10, 1–14. [Google Scholar] [CrossRef]
- She, W.; Gu, Z.H.; Lyu, X.K.; Liu, Q.; Tian, Z.; Liu, W. Homomorphic consortium blockchain for smart home system sensitive data privacy preserving. IEEE Access 2019, 7, 62058–62070. [Google Scholar] [CrossRef]
- Chen, Y.; Norford, L.K.; Samuelson, H.W.; Malkawi, A. Optimal control of HVAC and window systems for natural ventilation through reinforcement learning. Energy Build. 2018, 169, 195–205. [Google Scholar] [CrossRef]
- Wei, T.; Wang, Y.; Zhu, Q. Deep reinforcement learning for building HVAC control. In Proceedings of the 54th Annual Design Automation Conference 2017, Austin, TX USA, 18–22 June 2017; pp. 1–6. [Google Scholar]
- Nagy, A.; Kazmi, H.; Cheaib, F.; Driesen, J. Deep reinforcement learning for optimal control of space heating. arXiv 2018, arXiv:1805.03777. [Google Scholar]
- Wang, Y.; Velswamy, K.; Huang, B. A long-short term memory recurrent neural network based reinforcement learning controller for office heating ventilation and air conditioning systems. Processes 2017, 5, 46. [Google Scholar] [CrossRef] [Green Version]
- Gao, G.; Li, J.; Wen, Y. Energy-efficient thermal comfort control in smart buildings via deep reinforcement learning. arXiv 2019, arXiv:1901.04693. [Google Scholar]




| Authors | Building Block | Type of Blockchain | Confidentiality | Integrity | Scalability |
|---|---|---|---|---|---|
| [41] | Physical layer Sensors wifi Bluetooth Distributed ledger | Public | Yes | Yes | No |
| [42] | Distributed ledger Smart contract PoW PoS | Public | Yes | No | Yes |
| [43] | Pow Minor node Normal node | Public Private | Yes | No | Yes |
| [44] | Minor smart home Backup drive | Public | Yes | No | Yes |
| [53] | Data storage Pow Control module | Public | Yes | Yes | No |
| [46] | Smart contract Local minor IoT devices | Private | Yes | Yes | Yes |
| [54] | Ethereum | Private | Yes | No | No |
| [55] | Cloud network Smart contract | Consortium | Yes | No | Yes |
| [56] | Ethereum Cryptography Consensus algorithm | Public | Yes | Yes | No |
| [57] | Gateway of smart home Ethereum | Private | Yes | No | No |
| [58] | Nodes Encryption | Consortium | Yes | Yes | No |
| Sectors | Opportunities | Problems | Answers |
|---|---|---|---|
| IoT | - Increasing the network IoT devices - Connection management between devices - Developing the IoT devices based on decentralized architecture - Data transaction security - smart home devices data collection facilitating | - Increasing the capacity of process - Necessity of high power consumption - Increasing the problem of copy right for data ownership | - Cloud computing development for related data using interoperability. - Managing social network using hierarchical processing - Identify the ownership based on management plan |
| Financial transaction | - Using digital currency between various nodes - Using cryptocurrency for speed up the financial transaction - Security improvement by transaction tracing - Electricity cost reduction compare to real-time environment | - Require a suitable cryptocurrency - Improving the transaction security because of the attack possibility - Need for flexibility addressing | - Avoid the increasing in huge amount by managing the cryptocurrency |
| Smart contract | - Using the decentralized node for simplifying financial transactions - Maximizing the security - defining the way to pay to consumers digital incentives - Inspire the consumers for participation in programs | - Lack of standard protocols, contracts and interface - Monitoring contracts require high resources | - Providing the draft of standard contract. - Based on the value of contract embedding the security - Applying the authorization and for standard security |
| Component | Description |
|---|---|
| Memory | 32 GB |
| CPU | Intel(R) Core(TM) i7-8700@3.20 GHz |
| Python | 3.6.2 |
| Operating System | Ubuntu Linux 18.04.1 LTS |
| Docker Engine | Version 18.06.1-ce |
| Docker Composer | Version 1.13.0 |
| Blockchain framework | Ethereum |
| Machine learning algorithm | Deep Reinforcement Learning |
| DRL Model (80% Training Data) | ||
|---|---|---|
| Sample (M = 150.317) | Output (Y0, Y1) | |
| Expected output (X0,X1) | Normal (Y0) | Attack (Y1) |
| X0 = 79.465 Normal | 76.477 | 2.988 |
| X1 = 70.852 Attack | 3.531 | 67.321 |
| Decision Tree | ||
| X0 = 63.586 Normal | 59.521 | 4.065 |
| X1 = 86.731 Attack | 2.320 | 84.411 |
| ANN | ||
| X0 = 60.719 Normal | 57.430 | 3.289 |
| X1 = 89.598 Attack | 2.060 | 87.538 |
| SVM | ||
| X0 = 58.952 Normal | 54.211 | 4.741 |
| X1 = 91.365 Attack | 1.742 | 89.623 |
| DRL Model (20% Validation Data) | ||
|---|---|---|
| Sample (M = 33.886) | Output (Y0, Y1) | |
| Expected output (X0,X1) | Normal (Y0) | Attack (Y1) |
| X0 = 10.931 Normal | 10.348 | 583 |
| X1 = 22.955 Attack | 909 | 22.046 |
| Decision Tree | ||
| X0 = 9.820 Normal | 9.126 | 694 |
| X1 = 24.066 Attack | 1.020 | 23.046 |
| ANN | ||
| X0 = 8.719 Normal | 7.920 | 799 |
| X1 = 25.167 Attack | 1.560 | 23.607 |
| SVM | ||
| X0 = 8.210 Normal | 7.711 | 499 |
| X1 = 25.676 Attack | 1.626 | 24.050 |
| Algorithm | NSL-KDD | KDD-CUP-99 |
|---|---|---|
| Decision tree | 79.04 | 81.15 |
| ANN | 80.05 | 89.40 |
| SVM | 70.60 | 90.85 |
| DRL | 96.92 | 97.04 |
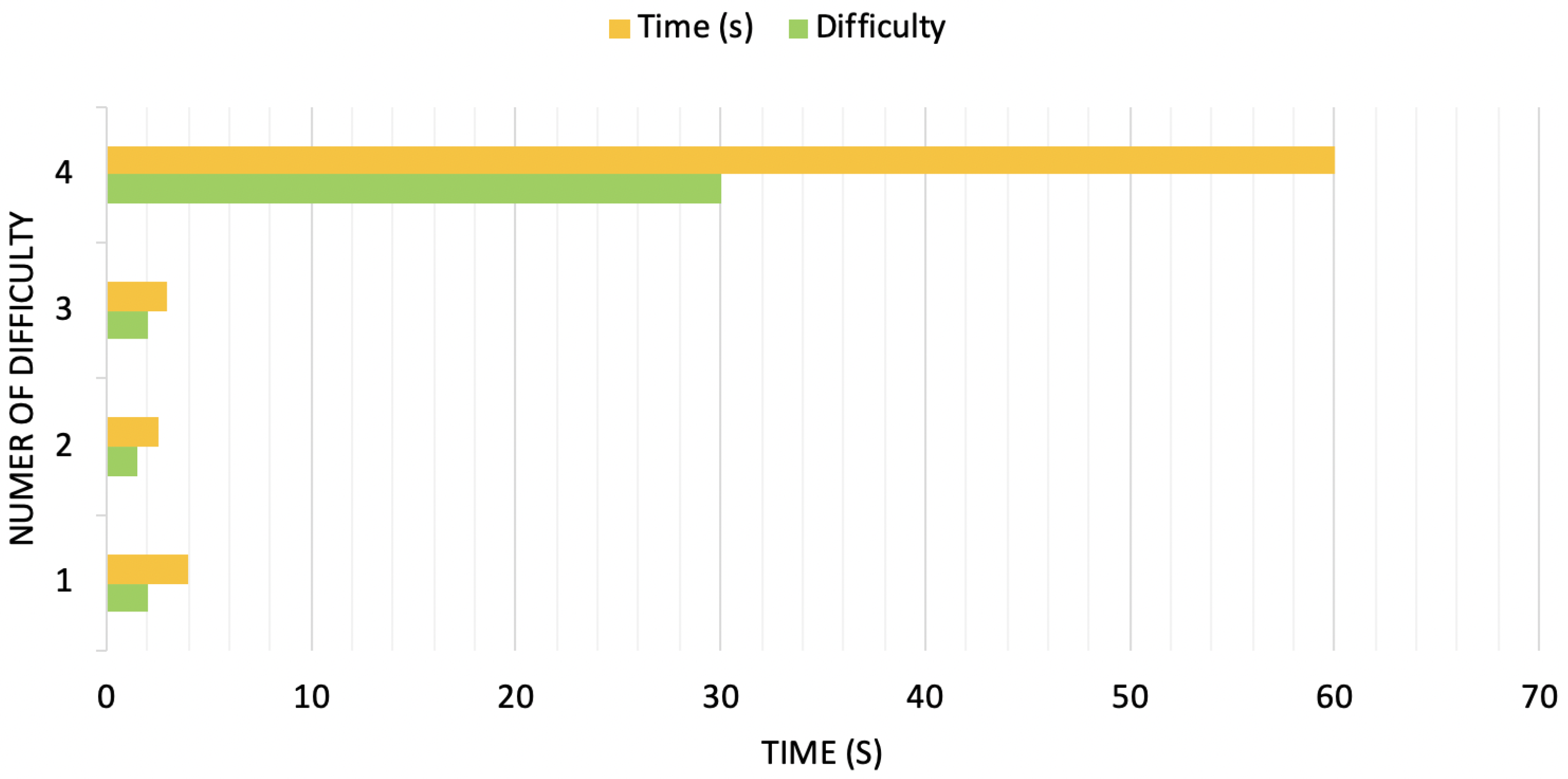
| Difficulty | Mining Time (S) |
|---|---|
| 1 | 0.5 |
| 2 | 0.22 |
| 3 | 0.3 |
| 4 | 60 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shahbazi, Z.; Byun, Y.-C.; Kwak, H.-Y. Smart Home Gateway Based on Integration of Deep Reinforcement Learning and Blockchain Framework. Processes 2021, 9, 1593. https://doi.org/10.3390/pr9091593
Shahbazi Z, Byun Y-C, Kwak H-Y. Smart Home Gateway Based on Integration of Deep Reinforcement Learning and Blockchain Framework. Processes. 2021; 9(9):1593. https://doi.org/10.3390/pr9091593
Chicago/Turabian StyleShahbazi, Zeinab, Yung-Cheol Byun, and Ho-Young Kwak. 2021. "Smart Home Gateway Based on Integration of Deep Reinforcement Learning and Blockchain Framework" Processes 9, no. 9: 1593. https://doi.org/10.3390/pr9091593
APA StyleShahbazi, Z., Byun, Y.-C., & Kwak, H.-Y. (2021). Smart Home Gateway Based on Integration of Deep Reinforcement Learning and Blockchain Framework. Processes, 9(9), 1593. https://doi.org/10.3390/pr9091593








