Proactive Defense Approach for Cyber–Physical Fusion-Based Power Distribution Systems in the Context of Attacks Targeting Link Information Systems Within Smart Substations
Abstract
1. Introduction
2. Scenario Generation Method Considering External Uncertainties
2.1. CGAN Based on Wasserstein Distance
2.2. Scenario Reduction Method Based on the IK-Means Method
3. Active Defense Strategy for Cyber–Physical Integrated Power Distribution Systems
3.1. Analysis of the Information System Attack Process
3.2. Fixed–Flexible Adjustable Resource Response Strategy
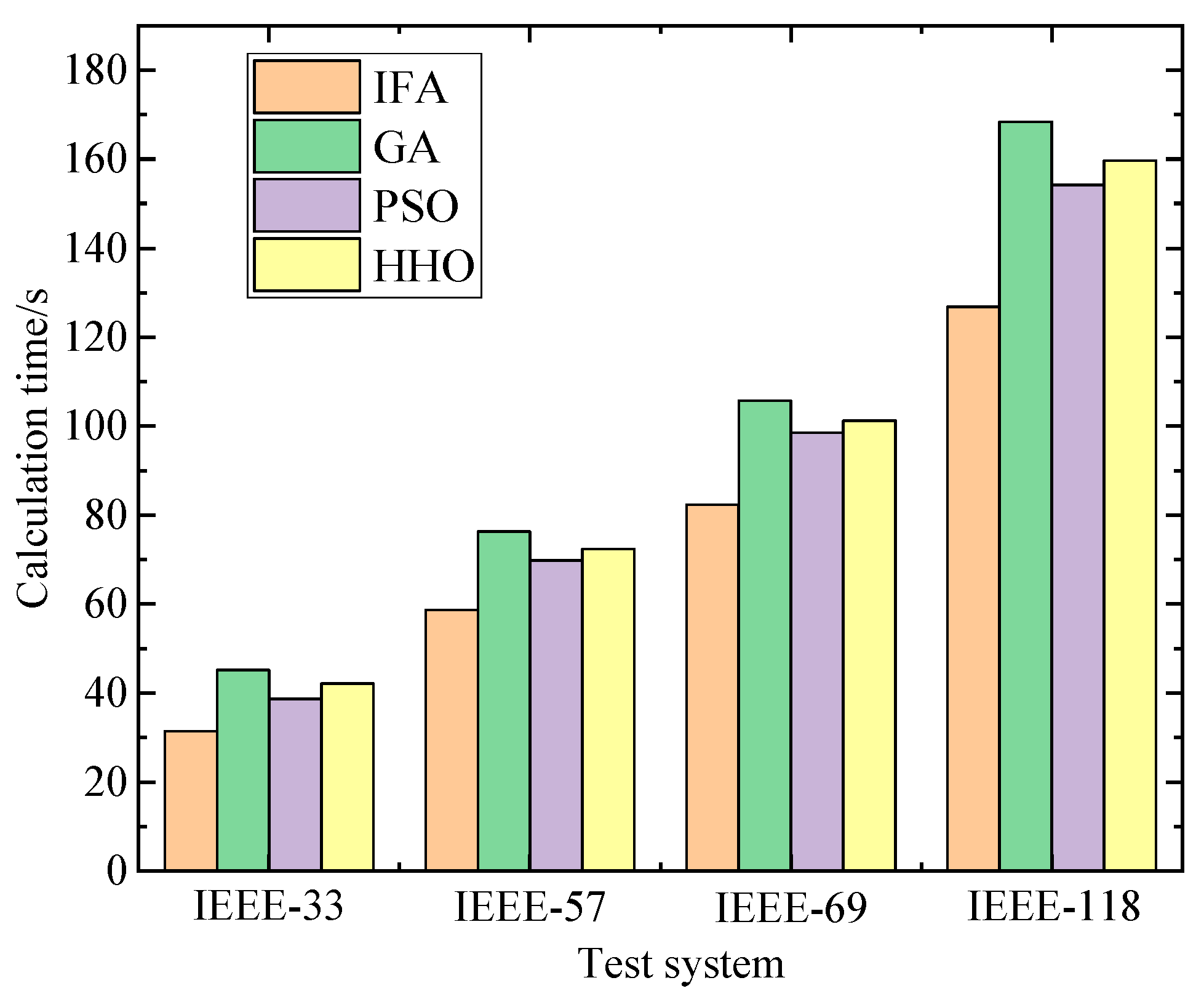
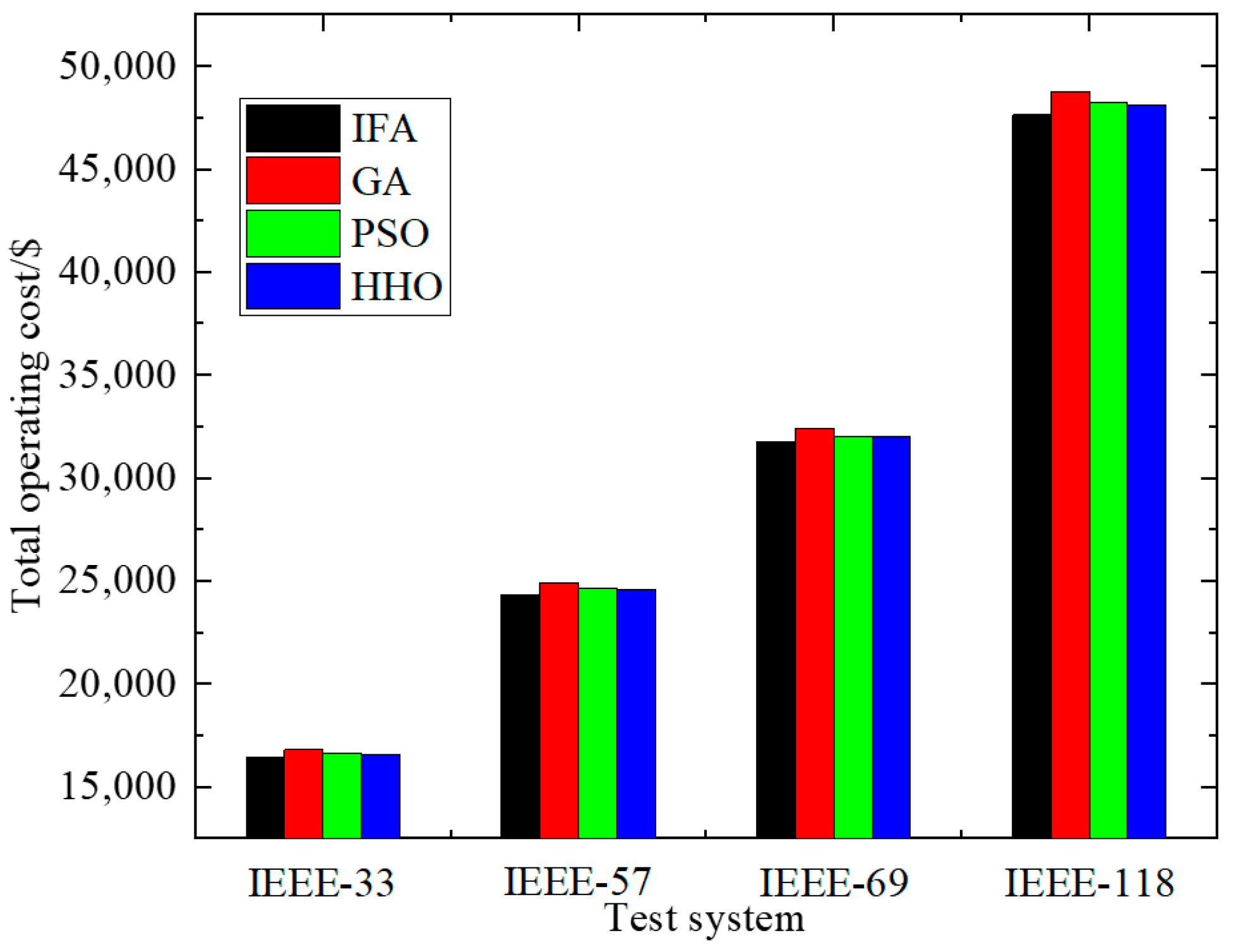
4. Solution Method Based on an Improved Firefly Algorithm
5. Case Study
5.1. The Introduction of the Testing System
5.2. Analysis of Typical Scenario Generation Results
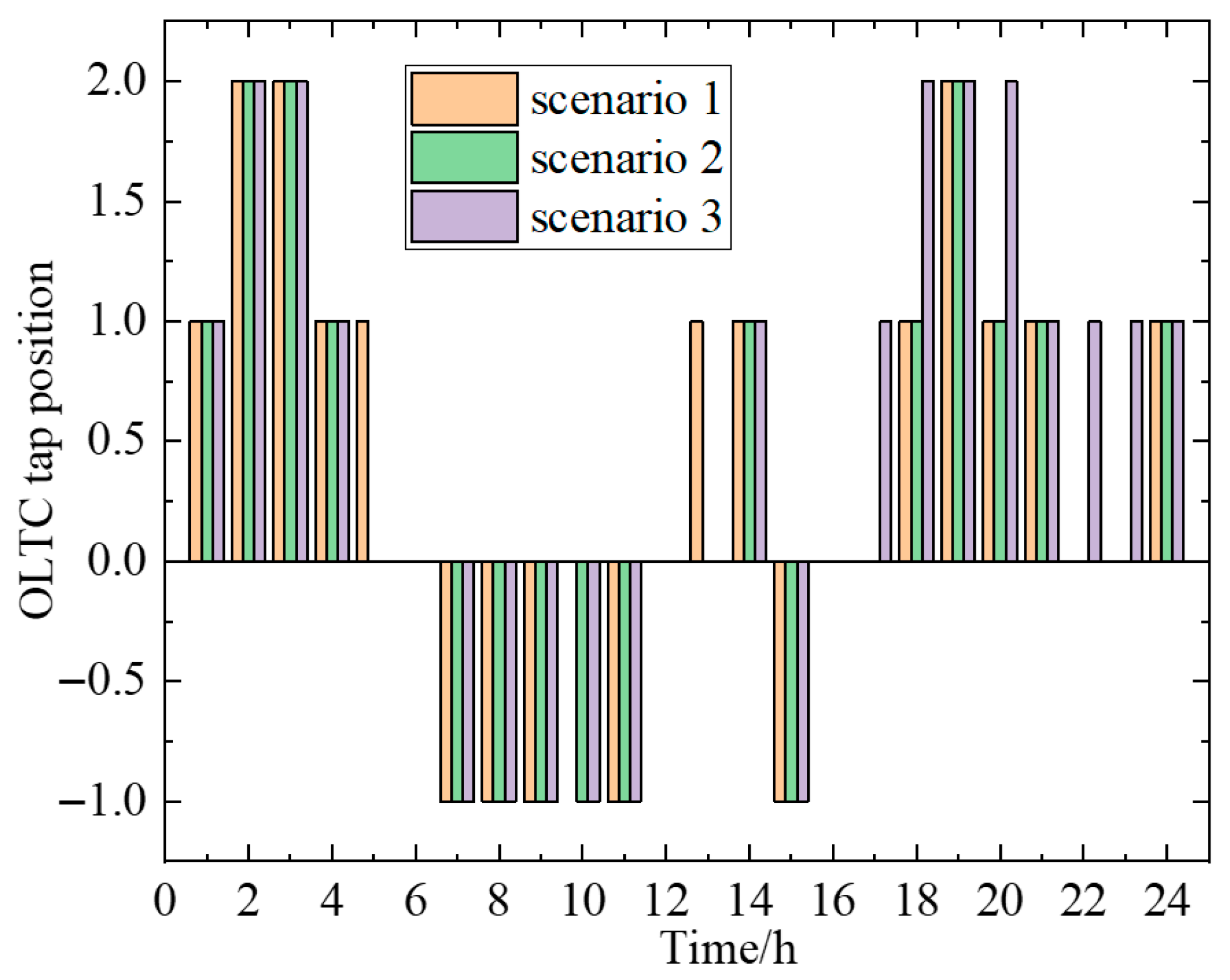
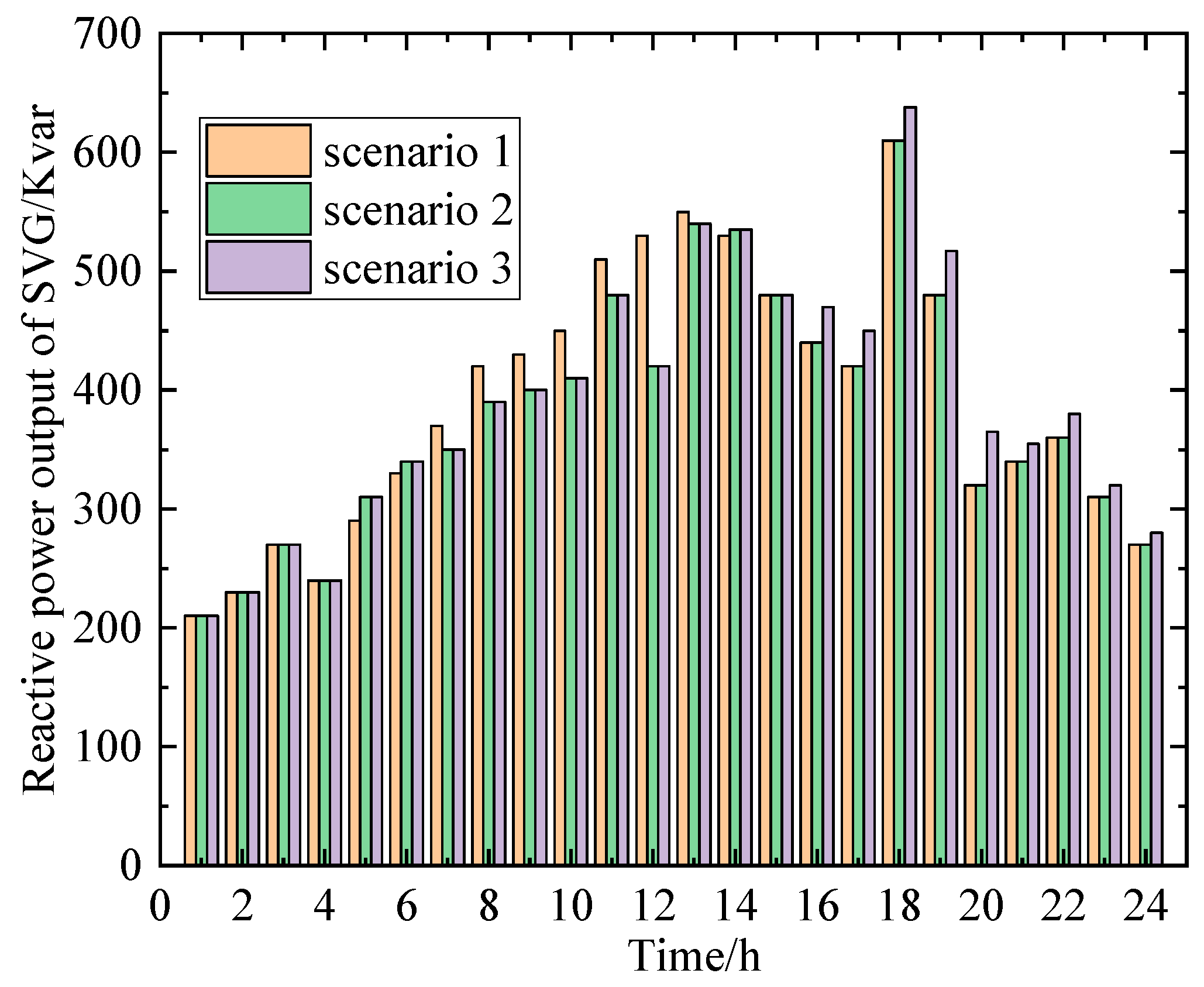
5.3. Analysis of Fixed Resource Response Under Deliberate Attacks
- Scenario 1: Normal operation.
- Scenario 2: Subject to an information attack from 5:00 to 9:00, resulting in a 20% reduction in renewable energy output.
- Scenario 3: Subject to an information attack from 16:00 to 20:00, leading to a 20% decrease in load power.
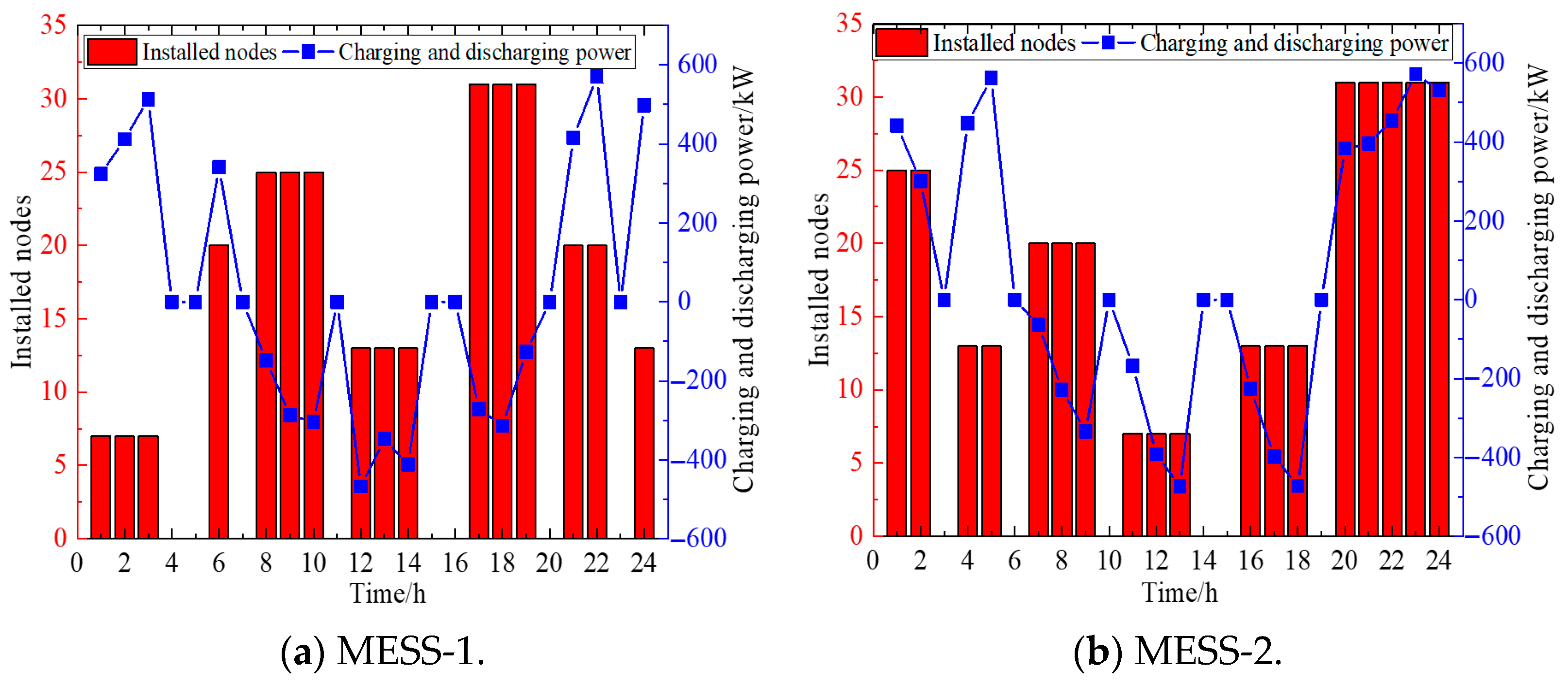
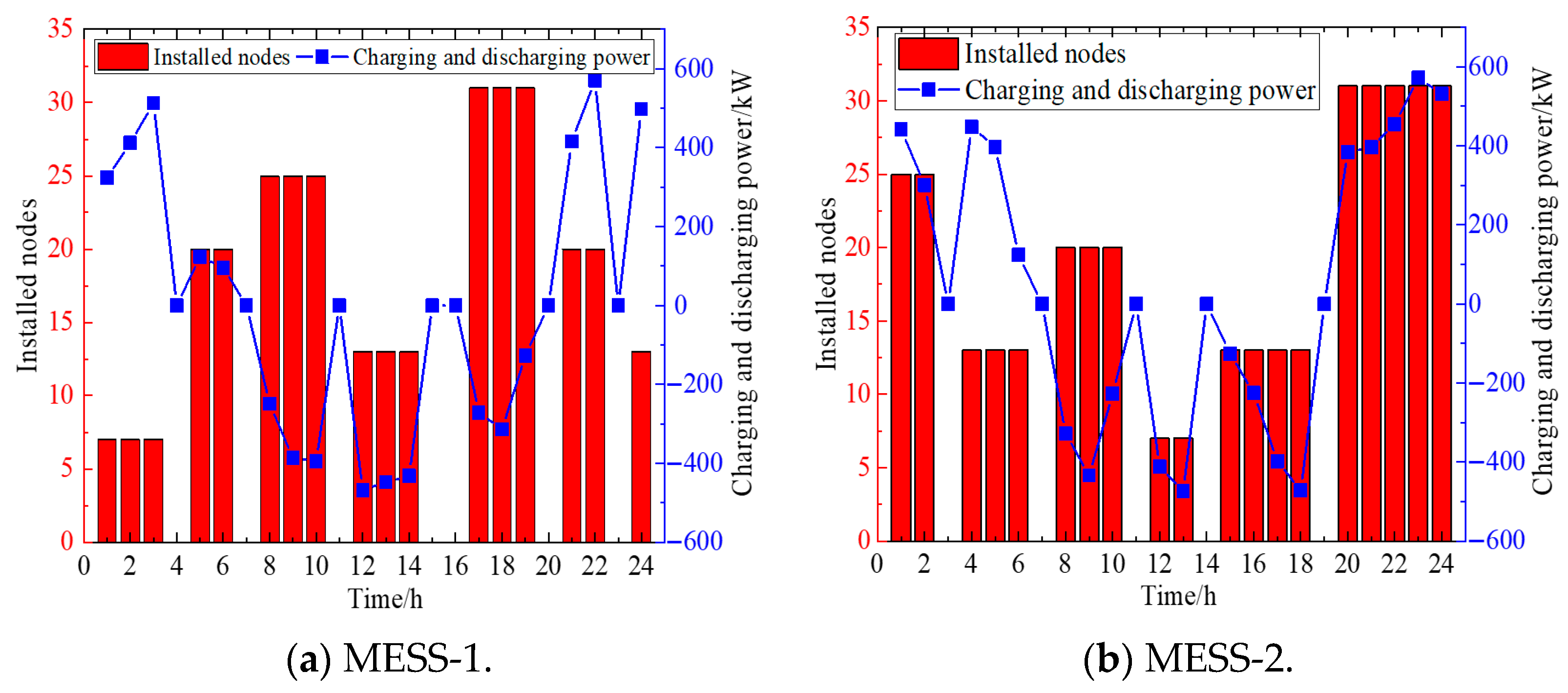
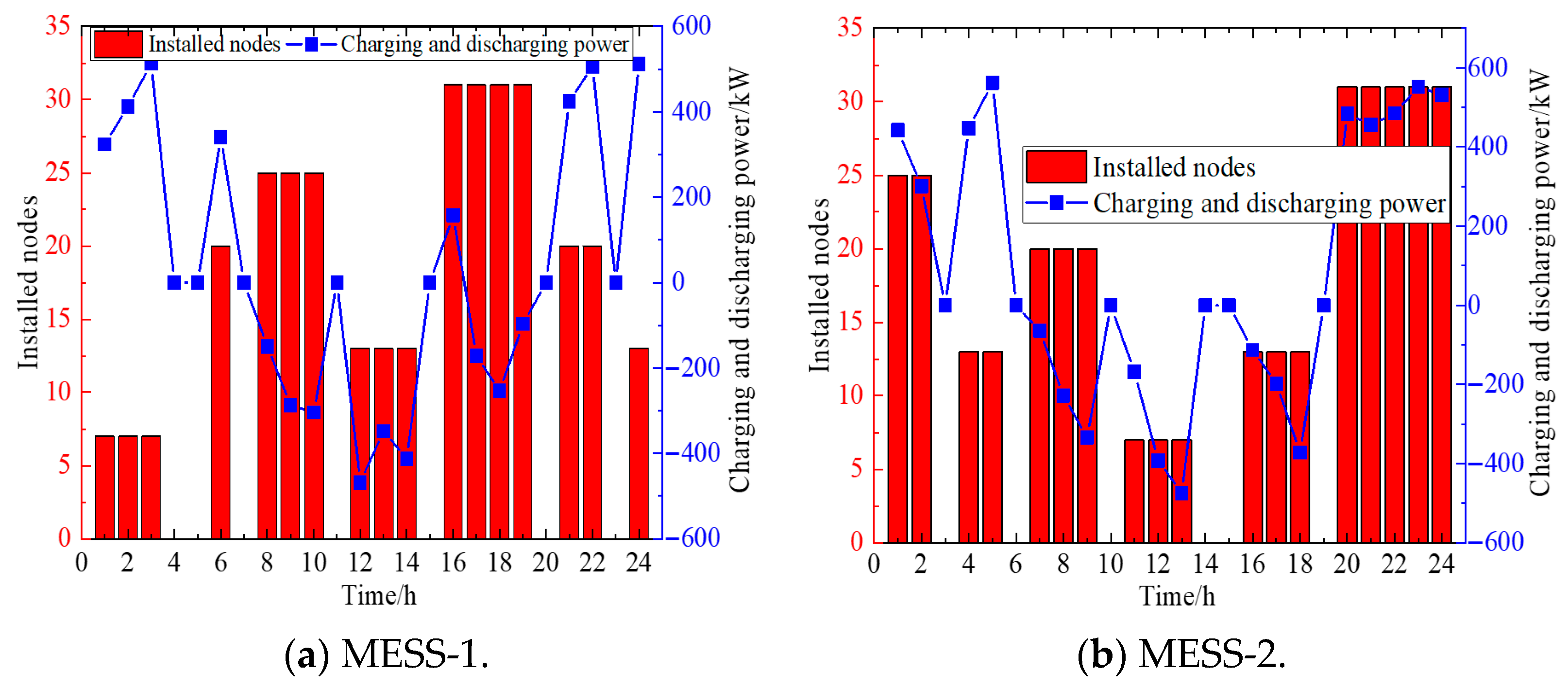
5.4. Analysis of Flexible Resource Response Under Deliberate Attacks
5.5. Analysis of System Recovery Effectiveness
5.6. Discussion on the Extensibility of the Method
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Sun, C.; Su, Q.; Li, J. Secure Tracking Control and Attack Detection for Power Cyber-Physical Systems Based on Integrated Control Decision. IEEE Trans. Inf. Forensics Secur. 2025, 20, 968–979. [Google Scholar] [CrossRef]
- Chen, L.; Zhang, X.; Xiao, F. A Stability Condition for Asynchronous and Aperiodic Sampled-Data Cyber-Physical Systems Under DoS Attacks. IEEE Trans. Ind. Cyber-Phys. Syst. 2025, 3, 397–407. [Google Scholar] [CrossRef]
- Yang, L.; Cao, X.; Zhou, Y.; Lin, Z.; Zhou, J.; Guan, X.; Wu, Q. Frequency-Constrained Coordinated Scheduling for Asynchronous AC Systems under Uncertainty via Distributional Robustness. IEEE Trans. Netw. Sci. Eng. 2025, 1–18. [Google Scholar] [CrossRef]
- Zhang, H.; Chen, C.; Lei, S.; Bie, Z. Resilient distribution system restoration with communication recovery by drone small cells. IEEE Trans. Smart Grid 2022, 14, 1325–1328. [Google Scholar] [CrossRef]
- Ye, Z.; Chen, C.; Liu, R.; Wu, K.; Bie, Z.; Lou, G.; Gu, W.; Yuan, Y. Boost distribution system restoration with emergency communication vehicles considering cyber-physical interdependence. IEEE Trans. Smart Grid 2022, 14, 1262–1275. [Google Scholar] [CrossRef]
- Wang, C.; Yan, M.; Pang, K.; Wen, F.; Teng, F. Cyber-physical interdependent restoration scheduling for active distribution network via ad hoc wireless communication. IEEE Trans. Smart Grid 2023, 14, 3413–3426. [Google Scholar] [CrossRef]
- Sun, X.; Chen, J.; Zhao, H.; Zhang, W.; Zhang, Y. Sequential disaster recovery strategy for resilient distribution network based on cyber–physical collaborative optimization. IEEE Trans. Smart Grid 2022, 14, 1173–1187. [Google Scholar] [CrossRef]
- Xu, L.; Guo, Q.; Sheng, Y.; Muyeen, S.M.; Sun, H. On the resilience of modern power systems: A comprehensive review from the cyber-physical perspective. Renew. Sustain. Energy Rev. 2021, 152, 111642. [Google Scholar] [CrossRef]
- Tian, M.; Dong, Z.; Gong, L.; Wang, X. Coordinated repair crew dispatch problem for cyber–physical distribution system. IEEE Trans. Smart Grid 2022, 14, 2288–2300. [Google Scholar] [CrossRef]
- Su, Q.; Sun, J.; Li, J. Node Recovery Optimization of Cyber–Physical Power Systems Based on an SEIRD Epidemic Model. IEEE Internet Things J. 2025, 12, 11011–11022. [Google Scholar] [CrossRef]
- Haridas, R.; Sharma, S.; Bhakar, R.; Gu, C. A Novel Integrated Load Redistribution Attack Model to Induce Cascading Failures in Cyber Physical Systems. IEEE Trans. Ind. Cyber-Phys. Syst. 2025, 3, 454–463. [Google Scholar] [CrossRef]
- Haque, K.A.; Sun, S.; Huo, X.; Goulart, A.E.; Davis, K.R. Scalable Discrete Event Simulation Tool for Large-Scale Cyber-Physical Energy Systems: Advancing System Efficiency and Scalability. IEEE Access 2025, 13, 101900–101921. [Google Scholar] [CrossRef]
- Presekal, A.; Ştefanov, A.; Semertzis, I.; Palensky, P. Spatio-Temporal Advanced Persistent Threat Detection and Correlation for Cyber-Physical Power Systems Using Enhanced GC-LSTM. IEEE Trans. Smart Grid 2025, 16, 1654–1666. [Google Scholar] [CrossRef]
- Wang, Y.; Li, J.; Qiu, J.; Chen, Y. Adaptive Early Warning Method of Cascading Failures Caused by Coordinated Cyber-Attacks. CSEE J. Power Energy Syst. 2025, 11, 406–423. [Google Scholar] [CrossRef]
- Yu, X.; Liu, N.; Xue, Y. The Role of Cyber-Physical-Social Systems in Smart Energy Future. IEEE Trans. Ind. Cyber-Phys. Syst. 2024, 2, 35–42. [Google Scholar] [CrossRef]
- Yang, Y.; Zhang, P.; Wang, C.; Zhao, Z.; Lai, L.L. State Transition Modeling Method for Optimal Dispatching for Integrated Energy System Based on Cyber—Physical System. J. Mod. Power Syst. Clean Energy 2024, 12, 1617–1630. [Google Scholar] [CrossRef]
- Qin, P.; Fu, Y.; Wu, K.; Zhang, J.; Wu, X.; Zhao, X. Packet Routing and Energy Cooperation for RTU Satellite-Terrestrial Multi-Hop Network in Remote Cyber-Physical Power System. IEEE Trans. Netw. Sci. Eng. 2024, 11, 3585–3597. [Google Scholar] [CrossRef]
- Davarikia, H.; Barati, M. A tri-level programming model for attack-resilient control of power grids. J. Mod. Power Syst. Clean Energy 2018, 6, 918–929. [Google Scholar] [CrossRef]
- Xiang, Y.; Zhang, X.; Shi, D.; Diao, R.; Wang, Z. Robust Optimization for Transmission Defense Against Multi-Period Attacks with Uncertainties. Int. J. Electr. Power Energy Syst. 2020, 121, 106154. [Google Scholar] [CrossRef]
- Ruan, Z.; Lv, L.; Liu, Y.; Yang, J.; Liu, J.; Ni, W. Research on Multi-Objective Defense Strategies for Power CPS Based on Pareto Optimality. J. Electr. Power Syst. Autom. 2019, 31, 36–42. [Google Scholar]
- Yang, Y.; Lan, S.; Qin, Z.; Liu, H. Network-Physical Coordinated Attacks in Cyber-Physical Power Systems. Electr. Power Autom. Equip. 2020, 40, 97–103. [Google Scholar]
- Zhang, J.; Wu, J.; Qi, X.; Yang, X.; Sun, L. Cascading Failure Analysis and Risk Assessment of CPPS Based on Network Dependency. Power Syst. Prot. Control 2023, 51, 164–171. [Google Scholar]
- Zhang, Y.; Liu, W.; Liu, G.; Huang, S. Modeling and Vulnerability Analysis of Cyber-Physical Power Systems Considering Topological Correlation and Dual Coupling. Proc. CSEE 2021, 41, 5486–5500. [Google Scholar]
- Available online: https://www.kaggle.com/datasets/PROPPG-PPG/hourly-weather-surface-brazil-southeast-region (accessed on 15 August 2023).
- Available online: https://gitcode.com/open-source-toolkit/8a397 (accessed on 14 September 2018).
- Lin, Y.; Luo, H.; Chen, Y.; Yang, Q.; Zhou, J.; Chen, X. Enhancing Participation of Widespread Distributed Energy Storage Systems in Frequency Regulation Through Partitioning-Based Control. Prot. Control Mod. Power Syst. 2025, 10, 76–89. [Google Scholar] [CrossRef]
- Wang, Y.; Li, L.; Chang, L.; Guan, J.; Peng, H.; Wu, B. Conditional Scenario Generation Method of New Energy Prediction Error Based on GMM. In Proceedings of the 2025 8th International Conference on Energy, Electrical and Power Engineering (CEEPE), Wuxi, China, 25–27 April 2025; pp. 394–399. [Google Scholar] [CrossRef]
- Wu, Q.; Lu, T.; Ding, Z.; Shi, L.; Xu, Y.; Xu, X. Automatic Completion Method of Power Missing Data in Distribution Network Based on GCN-VAE Model. In Proceedings of the 2024 China International Conference on Electricity Distribution (CICED), Hangzhou, China, 12–13 September 2024; pp. 1117–1121. [Google Scholar] [CrossRef]
- Huo, Y.; Yang, J.; Qu, J.; Zhang, C.; Zhou, L.; Zhao, W.; Jiang, H.; Wu, Z.; Dai, J.; Duan, W.; et al. Lightweight Data-Driven Planning Method of Hybrid Energy Storage Systems in the New Power System. IEEE Trans. Ind. Appl. 2025, 61, 4792–4800. [Google Scholar] [CrossRef]
- Chen, S.; Chen, W.; Lin, J.; Chen, L. Modeling and Optimal Operation of Mobile Energy Storage Units Considering the Operation Safety of the Distribution Networks. In Proceedings of the 2024 4th Power System and Green Energy Conference (PSGEC), Shanghai, China, 22–24 August 2024; pp. 1243–1247. [Google Scholar] [CrossRef]
- Wang, Z.; Li, X.; Xia, Y.; Zhao, T.; Xia, X.; Li, Y. Power System Evolutionary Planning Based on LHS-kmeans Method for Generating Future Load Scenarios. In Proceedings of the 2021 3rd International Conference on Smart Power & Internet Energy Systems (SPIES), Shanghai, China, 25–28 September 2021; pp. 381–385. [Google Scholar] [CrossRef]
- Wang, B.; Xu, Z.; Guan, X. Robust Load Frequency Control for Uncertainties Multi-Area Power Systems with Couplings of Systems Dynamics and Reconfigurable Communication Networks. IEEE Trans. Power Syst. 2025, 40, 2584–2599. [Google Scholar] [CrossRef]
- Stecher, J.; Kiltz, L.; Graichen, K. Generalized Tolerance Optimization for Robust System Design by Adaptive Learning of Gaussian Processes. IEEE Access 2025, 13, 68959–68983. [Google Scholar] [CrossRef]
- Liu, S.; Zenelis, I.; Li, Y.; Wang, X.; Li, Q.; Zhu, L. Markov Game for Securing Wide-Area Damping Control Against False Data Injection Attacks. IEEE Syst. J. 2021, 15, 1356–1365. [Google Scholar] [CrossRef]
- Cao, Y.; Zhou, B.; Chung, C.Y.; Zhou, K.; Zhu, L.; Shuai, Z. Resilience-Oriented Coordinated Topology Reconfiguration of Electricity and Drainage Networks with Distributed Mobile Emergency Resources. IEEE Trans. Smart Grid 2025, 16, 786–800. [Google Scholar] [CrossRef]
- Xu, H.; Yu, T.; Ren, C.; He, S. Finite-Time Decentralized Sliding Mode Control for Interconnected Systems and Its Application to Electrical Power Systems: A GA-Assisted Design Method. IEEE Trans. Circuits Syst. I Regul. Pap. 2024, 71, 2835–2847. [Google Scholar]
- Butti, O.S.T.A.; Burunkaya, M.; Rahebi, J.; Lopez-Guede, J.M. Optimal Power Flow Using PSO Algorithms Based on Artificial Neural Networks. IEEE Access 2024, 12, 154778–154795. [Google Scholar] [CrossRef]
- Wang, X.; Wang, S.; Ren, J.; Jing, W.; Shi, M.; Zheng, X. A Novel Harmonic Detection Method for Microgrids Based on Variational Mode Decomposition and Improved Harris Hawks Optimization Algorithm. IEEE Access 2024, 12, 60797–60807. [Google Scholar] [CrossRef]






| Data Set | Method | DBI | SC | RMSE |
|---|---|---|---|---|
| Wind power data | CGAN | 0.82 | 0.76 | 0.045 |
| K-means | 1.25 | 0.62 | 0.078 | |
| GMM | 1.03 | 0.68 | 0.065 | |
| VAE | 0.95 | 0.71 | 0.058 | |
| PV data | CGAN | 0.78 | 0.79 | 0.032 |
| K-means | 1.18 | 0.59 | 0.085 | |
| GMM | 0.97 | 0.65 | 0.061 | |
| VAE | 0.89 | 0.73 | 0.049 |
| Method | Economic Cost/USD | Average Voltage Deviation/p.u. | Total load Shedding Amount/MW |
|---|---|---|---|
| Our proposed method | 16,324 | 0.02 | 0.21 |
| Method considering only fixed resources [29] | 14,526 | 0.06 | 0.82 |
| Method considering only flexible resources [30] | 15,331 | 0.04 | 0.54 |
| No defense strategy implemented | 13,168 | 0.08 | 1.03 |
| Method | Renewable Energy Accommodation Rate/% | Average Voltage Deviation/p.u. | Total Load Shedding Amount/MW |
|---|---|---|---|
| The proposed method | 96.8 | 0.02 | 0.21 |
| K-means clustering [31] | 94.3 | 0.06 | 0.581 |
| Robust optimization [32] | 91.7 | 0.07 | 0.92 |
| Number of Scenarios | Economic Cost/USD | Computational Time/s |
|---|---|---|
| 5 | 16,324 | 157 |
| 10 | 16,117 | 324 |
| 15 | 15,923 | 473 |
| 20 | 15,804 | 668 |
| Metric | The Proposed Method | Traditional Robust Optimization Method | Distributed Defense Method Based on Multi-Agent Systems | Self-Recovery Strategy |
|---|---|---|---|---|
| Economic Cost/USD | 16,425 | 18,547 | 17,175 | 18,854 |
| Renewable Energy Accommodation Rate/% | 96.8 | 91.7 | 93.5 | 85.2 |
| Voltage Fluctuation Value/p.u. | 0.02 | 0.07 | 0.05 | 0.10 |
| Load Shedding Amount/MW | 0.21 | 0.92 | 0.65 | 1.50 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Y.; He, X.; Cheng, Z.; Wang, B.; Che, J.; Zou, H. Proactive Defense Approach for Cyber–Physical Fusion-Based Power Distribution Systems in the Context of Attacks Targeting Link Information Systems Within Smart Substations. Processes 2025, 13, 3269. https://doi.org/10.3390/pr13103269
Wang Y, He X, Cheng Z, Wang B, Che J, Zou H. Proactive Defense Approach for Cyber–Physical Fusion-Based Power Distribution Systems in the Context of Attacks Targeting Link Information Systems Within Smart Substations. Processes. 2025; 13(10):3269. https://doi.org/10.3390/pr13103269
Chicago/Turabian StyleWang, Yuan, Xingang He, Zhi Cheng, Bowen Wang, Jing Che, and Hongbo Zou. 2025. "Proactive Defense Approach for Cyber–Physical Fusion-Based Power Distribution Systems in the Context of Attacks Targeting Link Information Systems Within Smart Substations" Processes 13, no. 10: 3269. https://doi.org/10.3390/pr13103269
APA StyleWang, Y., He, X., Cheng, Z., Wang, B., Che, J., & Zou, H. (2025). Proactive Defense Approach for Cyber–Physical Fusion-Based Power Distribution Systems in the Context of Attacks Targeting Link Information Systems Within Smart Substations. Processes, 13(10), 3269. https://doi.org/10.3390/pr13103269






