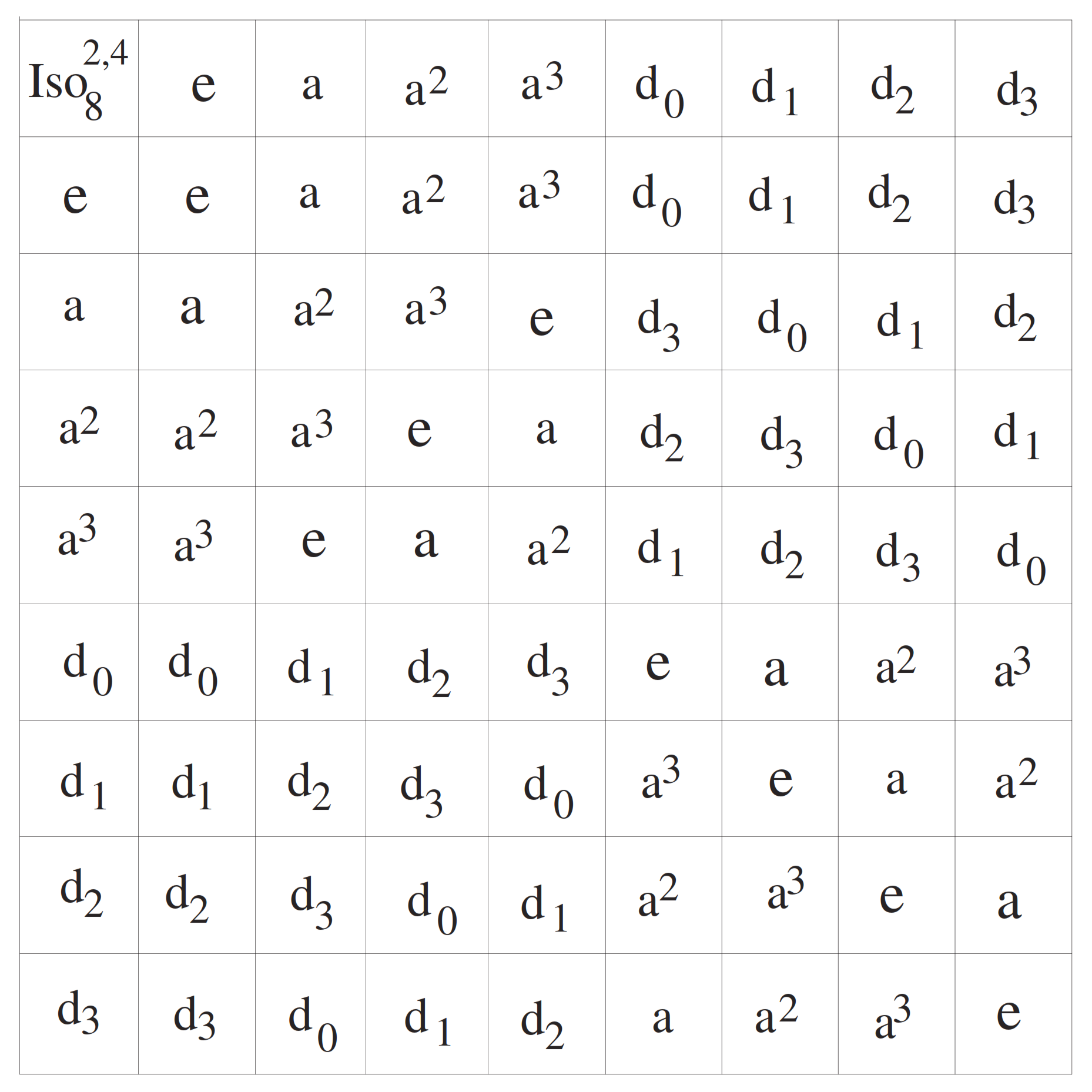1. Introduction
Let
(
resp.) represent the set of integers (
resp. natural numbers), and
be the
n times Cartesian product of
,
. Besides, let
(
resp.) be the set of even (
resp. odd) natural numbers. Digital geometry mainly deals with discrete objects in
from the viewpoints of digital
k-curve and digital
k-surface theory, where the
k-adjacency means the digital
k-connectivity of
(see (1) in
Section 2). Indeed, a digital image
,
, can be considered to be a digital graph on
with a certain
k-adjacency of
or a discrete topological subspace on
with a
k-adjacency relation of
(for details see
Section 2). They are indeed equivalent to each other. This kind of consideration facilitates our recognition of some discrete objects in a modern smart electronic device. For instance, a smart computer screen, being finite pixels, can be assumed to be a set followed from these two approaches among others. In addition, there are also further many types of approaches of studying digital objects in
. Hence, many works taking these approaches include the papers [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17,
18,
19]. Besides, some studies related to nonlinearizable action of dihedral groups on affine space [
20], free actions on
-trees [
21], and a group of paths in
[
22] were done. In addition, there are some researches on the fixed point property related to two-dimensional polyhedra [
23] and fixed point sets of circle action [
24]. Hereinafter, for convenience, for
with
, we follow the notation
[
13]. Besides, in the present paper we call
a digital image or a digital object in
.
One important thing to note is that the current approach in a digital topological setting plays an important role in applied mathematics as well as applied sciences. Hence, based on this approach, let
, the present paper explores some new structures and features associated with the fixed point sets by the
-actions on a digital image
(see Definition 10) and further, examines if alignments of fixed point sets by the
-actions are 2-connected or perfect (see Definition 11). In particular, these actions include fixed point and fixed point free ones [
25] and further, these are discrete groups or monoid ones.
The recent papers [
7,
8,
26] studied the set of cardinalities of fixed point sets of all
k-continuous self-maps of
, denoted by
in the present paper (or
in [
26]). Motivated by this approach, this paper further investigates some more important features of
. The obtained results give us some big advantages of recognizing the sizes or volumes of the fixed points sets by the
-actions on
. The papers [
7,
8] also characterized the set
with 2-adjacency which is referred to as “an alignment of fixed point sets” (see Definition 10) [
8]. Since the present paper indeed deals with two kinds of algebraic structures,
and
, the usage of the notations
and
can finally avoid a certain possible confusion among fixed point sets derived from these two actions on
.
The algebraic structure of
is essential for exploring fixed point sets of the
-actions on
in a
setting, where
is a category consisting of the set of digital images (or digital objects)
and the set of digitally
k-continuous maps (for details see
Section 2). Thus, they play important roles in studying fixed point theory [
27] and group theory in a
setting. Using these structures, we further investigate some properties of the
-action on
and explore a certain condition that makes the alignment of fixed point sets by the
-action perfect (for details see Definitions 10 and 11), where for a digital object
we say that
is perfect if it is equal to
(see Definition 11). Papers [
7,
8] have also explored some alignments of fixed point sets that are 2-connected (or perfect). Since an existence of a perfect alignment of fixed point sets depends on the situation, we strongly need to examine if
is perfect, which can play an important role in digital topology and many areas of applied sciences [
8]. Indeed, this kind of approach gives us to efficiently characterize the fixed point sets of
.
The present paper investigates various properties of
and
related to fixed point sets in the category
(for details see
Section 5). Let
be a simple closed
k-curve with
l elements in
(for more details see the property (2)). Then, based on the minimal simple closed
k-curve
in
, it turns out that either
or
is the secondary to the minimal simple closed
k-curve
in
depending on both the “
k-adjacency” and the dimension “
n” [
8]. Naively, while there is
, neither
nor
exists, where
. Meanwhile,
exists if
and
(for more details see the property (2) in the present paper or the property of (2) of [
8]). Considering a digital wedge
whose digital
k-fundamental group is an infinite cyclic group or a trivial group depending on the number
l, a recent paper mentioned that in the case
,
is 2-connected (or perfect) (see Definition 11) if and only if
, where the term “perfect“ means that
. Besides, a recent paper further developed a certain condition of which
is perfect. In addition, in the case
, the study of
was also proceeded [
8]. This kind of study can be substantially helpful to study fixed point theory and
k-homotopy theory in a digital topological setting. Since the present paper deals with many properties related to the digital topological property, let us recall the property in advance. Hereafter, as usual, we say that a digital topological invariant is a property of a digital image
which is invariant under digital
k-isomorphisms. In other words, a property of digital images is a digital topological property if whenever a digital image
possesses that property every digital image
k-isomorphic to
has that property.
Based on this approach, we may pose the following queries.
- (●1)
How can we characterize the group ?
- (●2)
Given , what group is isomorphic to ?
- (●3)
After proceeding with the -action on , how can we characterize the fixed point sets by the -action ?
- (●4)
What are the fixed point sets of an -action on ?
- (●5)
Given with a certain hypothesis, , how can we formulate ?
After developing many new tools, we will address all of these issues in this paper.
The rest of the paper is organized as follows:
Section 2 provides various concepts needed for this study and deals with some properties of them.
Section 3 develops the group structure of
. Besides, we prove that
is isomorphic to the standard dihedral group
with
elements.
Section 4 deals with some fixed point sets of an
-action on the given digital image
.
Section 5 explores various properties of
, where
. Indeed, the study of this kind of a digital wedge remains open.
Section 6 concludes the paper with some remarks and a further work. In this paper the notation “
” is used for introducing a new terminology. In addition, we will use the notation
to indicate the cardinality of a set
X.
2. Preliminaries
Rosenfeld [
17,
18] called the pair
a digital image (or digital object), where
with digital
k-connectivity,
. Motivated by these
k-adjacency relations for low dimensional digital images, a paper [
5] initially developed the generalized version of them for high dimensional digital images
,
. Indeed, this approach is essential for studying many digital objects from the viewpoint of digital topology such as digital products with normal adjacencies [
5] and their applications [
28,
29]. More explicitly, the following
k-adjacency relations of
were taken in [
5,
28] for studying
.
For a natural number
t,
, distinct points
are
-adjacent if at most
t of their coordinates differ by
and the others coincide. According to this statement, the
-adjacency relations of
, were formulated [
5,
28]), as follows:
Using a digital
k-adjacency of
, it turns out that a digital image
is a digital space [
30]. In this paper
is assumed in
, with one of the
k-adjacency of (1). The following terminology and notions [
5,
7,
17,
18,
29] will be often used later.
Given a digital image
with
, by a
k-path with
elements in
X, we mean the sequence
such that
and
are
k-adjacent if
[
13]. Using this approach, we can also represent the concept of
k-connectedness, as follows [
13].
We say that
is
k-connected if for any distinct points
there is a
k-path
in
X such that
and
(for more details see [
7]).
By a simple
k-path, we mean a finite set
such that
and
are
k-adjacent if and only if
[
13]. In particular, if
and
, then the length of this set
is denoted by
.
We say that a simple closed
k-curve (or simple
k-cycle) with
l elements in
, denoted by
[
5,
13],
, is a set
such that
and
are
k-adjacent if and only if
. In particular, as mentioned in the previous part, in this paper we use the notation
to abbreviate
.
More precisely, for
, no
exists, according to the notion of
(see also (2) below), we observe the following properties [
8]. The number
l of
depends on the
k-adjacency of
in (1), i.e.,
of (1) (for more details, see the property (2) of [
8] and several examples in
Figure 1 and
Figure 2).
For instance, we can consider the following digital objects: , , , and . However, in neither nor exists. Besides, in neither nor exists.
Given
, by the
k-component of
, we mean the maximal
k-connected subset of
containing the point
x [
13].
For a
k-connected digital image
, the paper [
5] already established a certain metric on
(for more details see [
5,
7]). Thus, given a digital image
on
, we obtain [
5,
29] that for a point
,
This set is called a digital
k-neighborhood of
with radius 1 [
5]. As another approach for the digital
k-neighborhood of
with radius
in (3) using a special kind of metric on
was established in the papers [
5,
7]. The digital
-continuity of a map
in [
18] can be represented, as follows:
Proposition 1. [4,6] A function is (digitally) -continuous if and only if for every , . In Proposition 1, in the case
, the map
f is called a “
k-continuous” map to abbreviate the
-continuity of Proposition 1. Using the presentation of the
k-continuity from Proposition 1, let us recall the category
DTC consisting of the following two pieces of data [
5], called the digital topological category.
The set of , where , as objects of DTC;
for every ordered pair of objects , the set of all -continuous maps between them as morphisms of DTC.
In
DTC, in the case
, we will particularly use the notation
DTC(k) [
29].
The recent paper studied the following property of digital continuity of a set , which can play an important role in digital topology.
Theorem 1. [8] Given a set , let us consider the two digital connectivities of X such as and with (see the property of (1)). Naively, we can assume the two digital images and . Further consider a -continuous self-map of and a -continuous self-map of . Then, neither of them implies the other. In order to discuss some errors in the literature written by L. Boxer [
31], we need to recall the following. We say that a nonempty digital image
has the almost fixed point property (
AFPP for brevity) if every
k-continuous self-map
f of
has a point
such that
or
is
k-adjacent to
x[
18]. Then, a paper [
18] proved that a digital screen
has the
AFPP. Motivated by this research, the paper [
7] has generalized it as follows:
Theorem 2. [7] For , the n-dimensional digital cube with k-adjacency on has the AFPP if and only if . Indeed, this assertion is correct. Moreover, this fact plays an important role in digital geometry. A paper [
31] also agrees that this assertion holds. Despite this fact, Boxer [
31] mentions that the proof of this theorem in [
7] has some errors or unclear. However, it is clear that Boxer’s argument is false. More explicitly, let us set the false straightfoward more precisely, as follows:
As for this comment on the page 362 of the paper [
31], we now state that Boxer’s argument is false because he seems to read Han’s proof in [
7] incorrectly.
- (1)
The proof of this theorem in [
7] is correct. More explicitly, as we can see the proof in [
7] as well as Theorem 1 above, given a set
X in
, Han [
7] does not say that every 6-continuous map implies an 18-continuous map. As mentioned in Theorem 1, for instance, given a set
X in
, assume a 6-continuous self-map of
and an 18-continuous self-map of
. Then, in general, neither of them implies the other (for more details, see Figure 2 in [
8]). Indeed, although every 6-continuous map need not imply 18-continuous, depending on the situation, a certain 6-continuous map can be an 18-continuous map. For instance, given the set
and the given maps
g of (7),
h of (8), and
r of (9) in [
7], the composite
in the proof of Theorem 2 in [
7] is clearly 18-continuous. Indeed, Example 3.1 of [
31] is not related to Han’s assertion in [
7] (for more details see the proof of [
8] and Figure 2 of [
8]).
- (2)
Boxer [
31] also incorrectly argues about Han’s second proof in [
7] related to Theorem 2. Since the method of suggesting a counterexample againt a certain assertion is obviously a kind of typical proof, Han’s proof taken in [
7] can be acceptable because the counterexample considered in
can be enough to prove Theorem 2. Besides, a paper [
7] further explains an
n-dimensional case.
To classify digital images
[
6], we often use the notion of a
-isomorphism (or
k-isomorphism) as in [
6], as follows:
Definition 1. [6] (-homeomorphism in [32]) Consider two digital images and in and , respectively. Then, a map is called a -isomorphism if h is a -continuous bijection and further, is -continuous. Then, we use the notation . In the case , we use the notation to abbreviate . The notion of (strict) digital wedge (or one point union of two digital images was initially proposed in [
5,
33]. Given two digital images
and
, a
digital wedge (or one point union of digital images), denoted by
, is defined [
5,
33] as the union of the digital images
and
, where
- (1)
is a singleton, say .
- (2)
and
are not
k-adjacent, where two subsets
A and
B of
is
k-adjacent if
and there are at least two points
and
such that
a is
k-adjacent to
b [
13].
- (3)
is k-isomorphic to and is k-isomorphic to (see Definition 1).
In view of this process, we may finally consider
to be a digital object
using these
and
. In this paper we only deal with this digital wedge which is quite different from the typical one point union in classical topology [
34].
In digital topology, we are strongly required to follow this digital wedge
. If we do not follow this approach, we will get some big difficulties in proceeding with further works in digital topology. Meanwhile, in the case of
and
such that
, the compatible
k-adjacency of
was also established. More precisely, for
, since no
exists, given
such that
and
, depending on the numbers
, we can consider many types of
(for more details, see the property (4) of [
8]).
Based on the pointed digital
k-homotopy in [
9,
10,
11] (see also [
32]), the concept of
k-homotopy relative to a subset
is established, as follows:
Definition 2. [5,32] Let and be a digital image pair and a digital image in and , respectively. Let be -continuous functions. Suppose there exist and a function such that - (●1)
for all and ;
- (●2)
for all , the induced function given by for all is -continuous;
- (●3)
for all , the induced function given by for all is -continuous.
Then, H is said to be a -homotopy between f and g [32]. - (●4)
Furthermore, for all , for all and for all [5].
Then, we call H a -homotopy relative to A between f and g, and f and g are said to be -homotopic relative to A in Y, in symbols [29]. In Definition 2, in the case
and
, we call a
k-homotopy to abbreviate
-homotopy. In addition, if
, then we say that
F is a pointed
-homotopy at
[
32]. When
f and
g are pointed
-homotopic in
Y, we use the notation
. In the case
and
,
f and
g are said to be pointed
k-homotopic in
Y and we take the symbol
to abbreviate
. If, for some
,
is
k-homotopic to the constant map in the space
X relative to
, then
is said to be
pointed k-contractible [
32]. Indeed, taking this approach, the concept of strong
k-deformation retract was developed in [
29].
Based on this
k-homotopy, the notion of digital homotopy equivalence firstly introduced in [
35] (see also [
36]), as follows:
Definition 3. [35] (see also [36]) Given two digital images and , if there are k-continuous maps and such that the composite is k-homotopic to and the composite is k-homotopic to , then the map is called a k-homotopy equivalence and is denoted by . Besides, is said to be k-homotopy equivalent to or is the same k-homotopy types with . If the identity map is k-homotopy equivalent to a certain constant map , we say that is k-contractible. Based on the several concepts such as a digital
k-homotopy class [
9,
10,
11], a Khalimsky operation of two
k-homotopy classes [
9], a trivial extension [
32], the paper [
32] defined the digital
k-fundamental group, denoted by
. Also, we have the following: If
X is pointed
k-contractible, then it is clear that
is a trivial group [
32]. A recent paper written by the present author recently proposed the most simplified axiom for a digital covering space. Using the homotopy lifting theorem [
4] and the unique digital lifting theorem [
5] in digital covering theory [
5], we obtain the following [
5,
29,
33]:
Theorem 3.
- (1)
For a non-k-contractible , is an infinite cyclic group [5]. - (2)
Given , is trivial if and only if [5,32]. Namely, is k-contractible if and only if . - (3)
For non-k-contractible , is a free group generated by two generators with infinite orders, i.e., is isomorphic to the free group [5].
This result is essential to characterizing an alignment of fixed point sets in
Section 5. Regarding Theorem 3, for instance,
has the trivial group and further,
also has the trivial group,
[
4,
5,
32]. Hence, we have
and
which are infinite free groups with two generators. In other words,
is isomorphic to the infinite cyclic group
and each
and
is isomorphic to the free group with two generators,
. In view of Theorem 3, we obtain the following:
Remark 1. For a given , we obtain the following:
- (1)
is an infinite cyclic group with an infinite order if and only if .
- (2)
is an infinite cyclic group with an infinite order if and only if .
Theorem 4. [7] A k-isomorphism preserves a k-homotopy, k-contractibility, and a k-homotopy equivalence. Corollary 1. A -isomorphism preserves a -homotopy and a -homotopy equivalence, and it transforms -contractibility into -contractibility.
3. Characterizations of : Is Isomorphic to the Dihedral Group
This section focuses on characterizing a group of the set of all self-
k-isomorphisms of
, denoted by
, i.e., an automorphism group of
in a
setting. Given a digital image
, the computation of
is a very important step for the self-
k-isomorphisms classifications of digital images. Indeed, the group
is also essential for studying fixed points of continuous self-maps of digital images
(see
Section 5).
Comparing with the group of the set of homeomorphisms for typical topological spaces, a digital topological analogue of it has its own features. Hence, motivated by the research of the group of the set of self-homeomorphisms of a topological space [
37], given a finite digital image
, we firstly need to characterize a group structure of the set of self-
k-isomorphisms of
X. Based on this work (see Remark 2 and Theorem 5), we further apply this structure to the fields of group theory, homotopy theory, fixed point theory (see
Section 5) and applied sciences.
In particular, given
, we will intensively explore some properties of
Namely, we will prove that the group has two generators and with orders l and 2, respectively, such that (or ). After recognizing some strong relationships between and the standard dihedral group with respect to the multiplication tables and the sizes of them, we prove that they are isomorphic to each other.
Given a digital image , we define the following:
Definition 4. For , let be the set . Consider the function composition, denoted by “”, as a binary operation on .
Then, we obviously obtain the following:
Lemma 1. is a group.
Proof. It is obvious that forms a group with the function composition for a group operation. Then, we clearly observe that the identity map is the identity element of the group. □
We will often use the notation instead of which is the finite cyclic group with the operation “”, as usual.
Remark 2. Let be a simple k-path which is not a singleton. Then, is isomorphic to the finite cyclic group .
Proof. Let be a simple k-path on such that . Then, we have the typical identity map and further, another self-k-isomorphism h of X such that , which completes the proof. □
It is important to recognize and understand certain key features of
. Hence, for any
, we now intensively explore some properties of
. Before studying this issue, let us recall some properties of the dihedral group
with
elements,
. To be precise,
indeed consists of two generators
r and
s with order
l and 2, respectively, such that
. Indeed,
is produced by
symmetries from a regular
l-gon in
[
38]. Namely, “
” and “
" represent the rotations and the reflections of this regular
l-gon, respectively.
Based on this geometric definition of
, to make a good combination between this geometric definition for
and that of
with respect to relations of the two groups,
, we recall
, as follows:
The relation “
” in (4) can be equivalently considered as “
”, “
”, or “
”. However, for convenience in the paper we will follow the relation taken in (4). Furthermore, the equation
has strong advantages in comparing
and
, we certainly follow the equality. This presentation of (4) indeed plays an important role in making a good combination between
and
. Motivated by this approach, let us move onto the study of rotations and reflections of
formulating
. For convenience, firstly reshape
into like a (digital) rectangle or a virtual
l-gon (need not be regular) on
up to
k-isomorphism (see
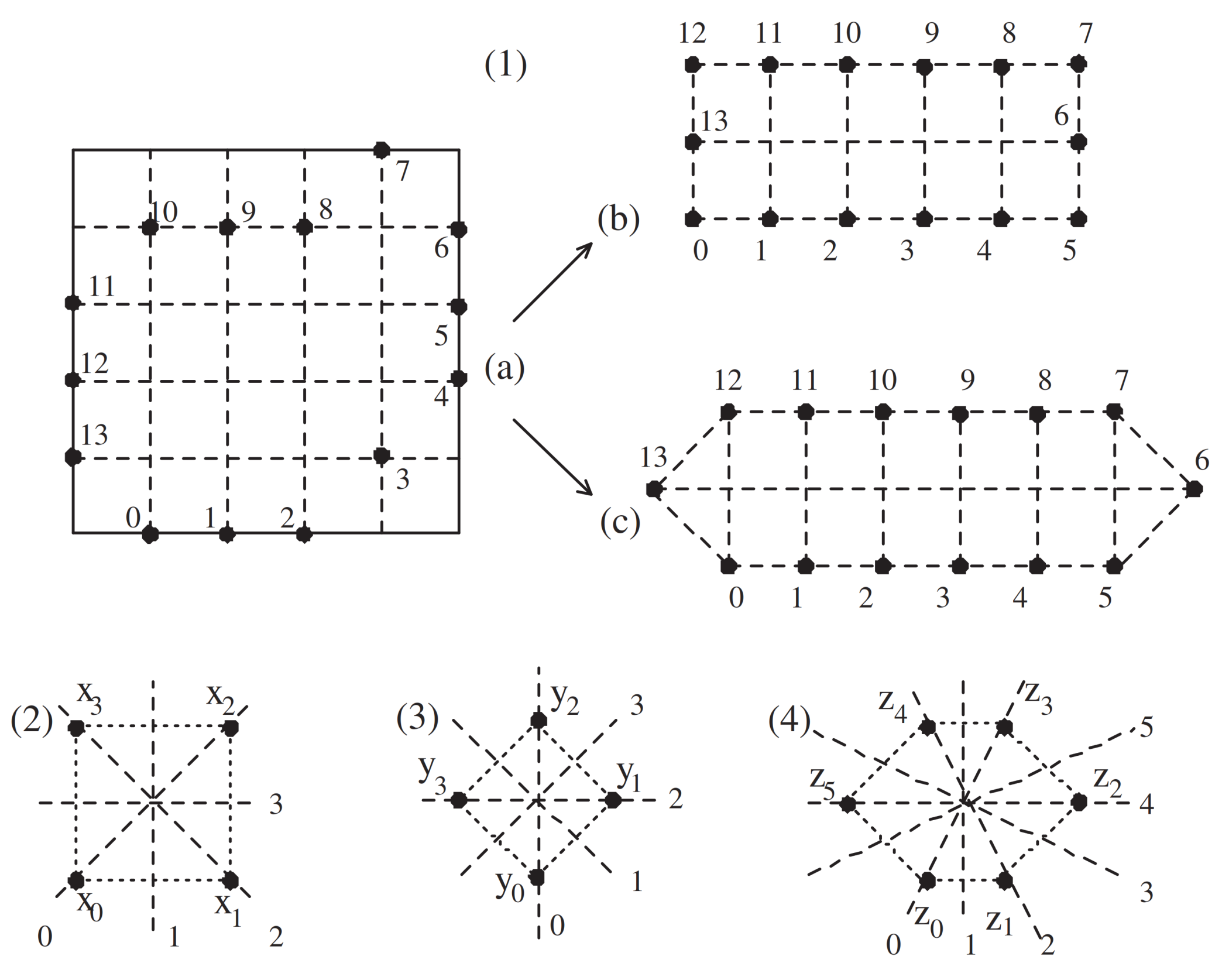
Figure 1(1) and
Figure 2). One important thing to note is that this reshaped object need not be a regular
l-gon. According to the number
l of
, based on the reshaped object from
, we can efficiently consider special kinds of rotations and reflections (or symmetries, or diagonal like flips) of
(see
Figure 1(1) and
Figure 2). Indeed, this kind of consideration can be acceptable because a digital
-isomorphism
induces a group isomorphism
(for details see Theorem 6 and Corollary 2). Furthermore, these rotations and symmetries are different from those related to a regular
l-gon with some angle producing a traditional dihedral group
as mentioned above (for details see Remark 3). Based on a self-
k-isomorphism of
,
is produced by
l rotations of
and
l reflections of
. Hence, our work that is strongly involved in
related to the presentation of
in (4). Indeed, owing to a
k-isomorphism of
and the reshaped simple closed 4- or 8-curve with
l elements in
, the current rotations should proceed with special types of rotations with some angles depending on the situation (see
Figure 1(1)(a)–(c) and
Figure 2) or special kinds of symmetries with some different angles depending on the situation (see
Figure 1(4)).
The next theorem plays an important role in establishing many results later.
Theorem 5. Given , is isomorphic to the dihedral group .
When proving the assertion, we will count on both l rotational symmetries and l reflection symmetries which are slightly different from those associated with the typical dihedral group with respect to the angles associated with the rotations and the reflections (for details see Remark 3).
Proof. (Case 1) Let us consider the case .
(Case 1-1) [l rotational symmetries of with respect to the k-isomorphism of ]
Let us consider the following self-k-isomorphism of as l rotational symmetries.
With
, for
, assume the map
Based on (5), we obtain the set
Then, further consider the function composition for
A as a binary operation on
A, denoted by ∘. Next, we may consider the set
A in (6) with the operation “∘” to be a cyclic group with a generator
. Namely, using the following operation,
we finally recognize that the pair
is equivalent to the cyclic group
with degree
l. Indeed,
is a cyclic subgroup of
such that
.
(Case 1-2) [l reflection symmetries of with respect to the k-isomorphism of ]
Based on the reshaped digital-based rectangle or a virtual
l-gon (see
Figure 1(1)), according to the reflections (diagonal like flips with some angles) of
up to
k-isomorphism (see the picture in
Figure 1(2)–(4)), we obviously have only
l types of self-
k-isomorphisms of
. For convenience, we may admit
l types of certain reflection symmetries using some diagonal-like flips with some angles. These angles need not be constant, which is quite different from the geometric definition of
. Indeed, we only need take the reflections of
as
k-isomorphisms of
, as follows (see
Figure 1(2)–(4)):
Then, it is clear that the map
in (7) is a self-
k-isomorphism of
because the generator
is termed by “diagonal flip”. Then, owing to the reflection
from (7), we obtain the paired set
, where
Owing to (8), we observe the property
Besides, the cosets
and
, exhaust all of the set
,
, and
(see the multiplication table for the elements of
in
Figure 3 and
in
Figure 4). Hence,. due to (6) and (8), it turns out that the elements
and
are generators for the group
with
elements because the element
has the order
l and each
has the order 2 and further,
. At the moment, let us explore the relation among elements of
from (6) and (7) (see the multiplication tables for
in
Figure 3 and
in
Figure 4), as follows: For
, the following properties are obtained (see
Figure 3 and
Figure 4).
The order of the elements of
denoting the composition is right to left, as usual. Eventually, owing to the properties (9), the group
has the following presentation.
Naively, it is clear that
is a finite group whose degree is equal to
. Comparing the properties of (4) and those of (10), it is obvious that they are equivalent. In view of the group presentation of
, owing to the property
, we see that
is not abelian. Indeed, since
has the property of (10) and
has the same size as
with respect to their multiplication tables (see the tables in
Figure 3 and
Figure 4), we can establish a homomorphism from
to
which leads to an isomorphism because they have the same order
and same numbers of generators with same orders. Writing down an explicit homomorphism from
to
, we now prove an isomorphism between
of (4) and
of (10) in the following way: consider the map
defined by
which leads to a homomorphism from
to
. Let us now check if
h is surjective. Since each element of
has the form
which is mapped by the established-map
h, this mapping of
h is eventually a surjection to lead to an isomorphism between
and
.
(Case 2) Let us consider the case .
(Case 2-1) [l rotational symmetries of with respect to the k-isomorphism of ]
Using the methods referred to in (5) and (6), given the assumption, we obtain
l rotations of
(see
Figure 2(b)), which completes the proof.
(Case 2-2) [l reflection symmetries of with respect to the k-isomorphism of ]
Indeed, the
l reflection symmetries of
,
, are similarly considered to those of
,
, as stated in (Case 1-2) (see (7)). However, as compared with the reflections referred to in (7), the current reflections are slightly different from the reflections referred to in (6) because of the odd number of
l (compare
Figure 1(2)–(4) and
Figure 2(c)). □
Based on Theorem 5, let us now compare a geometric definition of and that of .
Remark 3. [Comparison a geometric definition of and that of ]
- (1)
As for the rotations r producing , first of all, recall the geometric definition producing stated in (4). Meanwhile, as to the rotations of , the element (see (6)) is termed the rotation or the generator of the cyclic piece of (see (6)). However, there are some difference between and with respect to the angles of the rotations. To be precise, let be a regular l-gon with vertex on the plane. In the case , with P, the rotation r proceeds evenly over angle. Namely, each of the vertices on P is transformed in terms of the one click counterclockwise movement on P by a constant angle.
Meanwhile, in the case , the element α is a self-k-isomorphism of being mapped as in (5). Thus, we may recognize as one click movement of points of in the counterclockwise direction (see the map in (5) and Figure 2(b) as an example). However, in light of these rotations, , is equivalent (not equal) to because . Meanwhile, unlike (see (4)), the rotation α need not proceed evenly over a certain angle on the plane, which is a slightly different from the rotation r of . - (2)
Comparing and , we see only one difference between them with respect to the reflection angle (see Figure 1 (4) and Figure 2(c)).
Example 1. is isomorphic to the dihedral group .
(Case 1) [Rotation as an 8-isomorphism of ]
Let us consider the following self-map
of
defined in the following way (see
Figure 1 (4)). For instance, consider six rotations of
(see
Figure 1 (4)), as follows: For
,
Then, the map
of
is a self-8-isomorphism of
. From (12), we obtain the pair
, where
which makes
the cyclic group
with
. Then, we clearly obtain
.
(Case 2) [Some reflections (diagonal like flips) of ]
Based on the reshaped digital-based rectangle (see
Figure 1(1)(a) → (b) or (c) as an example) according to the 8-isomorphism of
, we obviously have only six types of reflections as self-8-isomorphisms of
(see the picture in
Figure 1(4)). To be precise, we may represent these reflections more precisely in the following way (see
Figure 1(4)).
Then, it is clear that the maps
in
are self-8-isomorphisms of
. Thereby, owing to (13) and (14), we obtain the pair
, where (see
Figure 1(4))
Then, it is clear that
. Besides, owing to the partition of
by the set
, we see that
. In particular, in
, after carefully examining the relationships among the elements of
, we observe the following: For
,
With the dihedral group
of (4) in mind, using the properties in (16), using the properties from (13) and (15), we finally have the presentation, as follows:
Comparing the relation of (4) and that of (16) and further, taking a look at the multiplication table in
Figure 4, we conclude that
is isomorphic to
. However, as already stated in the proof of Theorem 5,
is not equal to
. More precisely, we now establish the following map
as referred in the proof of Theorem 5. Indeed, since
has two generators with the property (17) and it has the same size as
. By mapping
and
, we finally have an isomorphism between them (see the multiplication table in
Figure 4).
Using a method similar to the process of Example 1, we obtain the following:
Example 2. (1) is isomorphic to the dihedral group .
(2) is isomorphic to the dihedral group .
Theorem 6. A k-isomorphism between and implies an isomorphism between and .
Proof. Let be a k-isomorphism.
Consider
. Then, we obtain the composite
. Thus, let us now define the map
Then, for any , we clearly obtain and further, using the property of (18), we observe that is a bijection, which completes the proof. □
By Theorem 6, we obtain the following because the identity obviously implies an isomorphism between and , as follows:
Corollary 2. In a setting, is isomorphic to if and only if .
According to Theorems 5 and 6, it is clear that depends on the number l. Thus, for a -isomorphism between and we obtain the following:
Corollary 3. Given two digital images , is isomorphic to if and only if .
4. Fixed Points Sets of an -Action on and an -Action on
Given a digital image and , for , we use the notation , where is the set of self-k-continuous maps of .
Definition 5. Given a digital image , we use the notation Let us now prove that is a digital topological invariant, as follows:
Proposition 2. In a setting, is a digital topological invariant.
Proof. Let be a k-isomorphism. Then, it suffices to prove that is equal to . More explicitly, consider an arbitrary . Then there is a set such that , where for any and a certain we have the property . Then we need to prove that the number t belongs to . Furthermore, using a method similar to this approach above, we need to prove that any element s in also belongs to .
As mentioned above, given a number
, take the set
such that
, where for a certain
we obtain that any
has the property
. Since
h is a
k-isomorphism, we have
. By (18), take
. Then, we clearly obtain
. Then, for
, let
. Since we obtain
Let us now put
, which implies that
so that
Similarly, for any
, let us put
. Then, using a method similar to the process of (19), for any
, after putting
, we obtain
which implies that
Due to the properties of (20) and (21), we obtain that is equal to . □
By Theorem 6 and Proposition 2, we obtain the following:
Corollary 4. Consider two digital images which are -isomorphic. Then is equal to .
Since both and play important roles in digital geometry, let us characterize the set of cardinalities of the fixed sets of self-k-continuous maps of them.
Lemma 2. Given with , .
Proof. With the hypothesis, consider
. By Theorem 5, it is clear that
in (6) or
in (8) (see
Figure 1).
(Case 1) Assume in (6). Then we obtain .
(Case 2) Assume in (6). Then we have .
(Case 3) Assume in (8). Then we obtain . □
Unlike the above case of , for an odd number (see also the property (2)), we obtain the following:
Lemma 3. Given with , .
Proof. In the case of
, the proof of
is proceeded by using a method similar to the proofs of the Cases 1 and 2 stated in the proof of Lemma 2. However, unlike the Case 3 referred to in the proof of Lemma 2, in the case that
f is a reflection of
, as shown in
Figure 2(c), we obtain
. □
Based on the properties from Lemmas 2 and 3, we obtain the following:
Theorem 7. Given with , .
Proof. Using Theorem 5 and Lemmas 2 and 3, we need to consider the following several cases.
(Case 1) Making the part or of remained, we consider a certain symmetry of referred to in (6). More explicitly, we first consider to obtain .
Second, as another case, after fixing (resp.) of , we further consider a certain symmetry of the part (resp.) introduced in (8) to obtain .
(Case 2) Fixing the point in and using the property (8), we further consider the reflection of both and on themselves respectively to obtain .
(Case 3) Fixing the point in and exchanging the points of and those of under a k-isomorphism to obtain . □
Unlike the case of of stated in Theorem 7, using a method similar to the proof of Theorem 7, we obtain the following:
Corollary 5. Given with and , .
Proof. The assertion of is proved by using the methods referred to in the cases of Theorem 7. However, since , we cannot further proceed with the process of Case 3 of the proof of Theorem 7. □
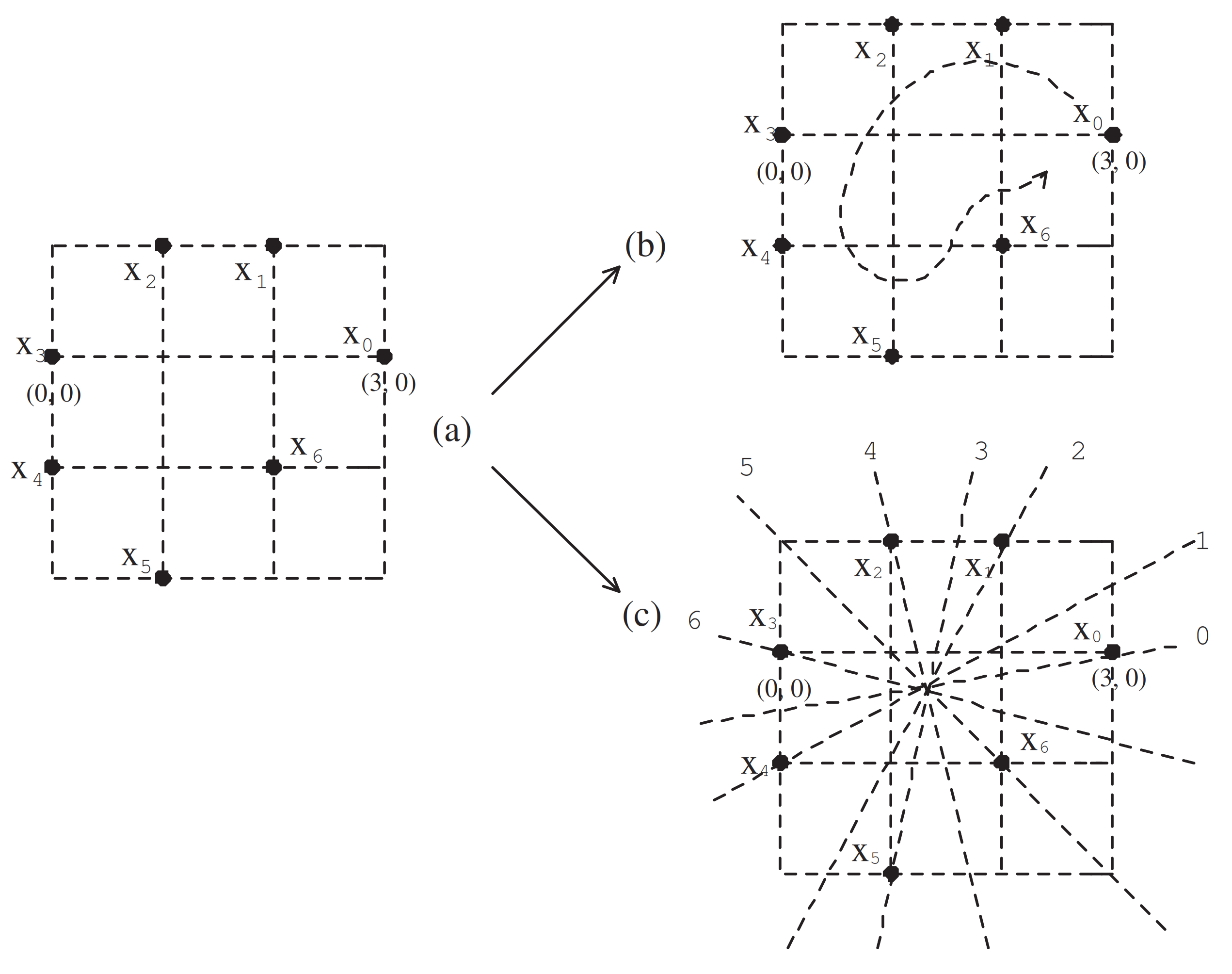
Let us now consider the cases
or
. Without loss of generality, we may consider the case
(see
Figure 5b), as follows:
Theorem 8. Given with , .
Proof. Using a method similar to the proof of Theorem 7, we complete the proof. To guarantee this approach, for instance, given
in
Figure 5b, we obtain
. □
Let us now investigate for the case of .
Theorem 9. Given with , we obtain the following:
- (1)
if .
- (2)
if .
Proof. Using Theorem 5 and Lemmas 2 and 3, we need to consider the following cases.
- (1)
In the case of , making the part of remained, we consider a certain symmetry of used in the Case 2 of the proof of Theorem 5. Then we first consider to obtain .
Second, we can consider a certain symmetry of referred to in (8) to obtain .
Third, making the point in fixed and using the property referred to in the Case 2 of the proof of Theorem 5 (see also the property (8)), we map the points of onto those of under a k-isomorphism to obtain .
Fourth, making the point in
fixed and exchanging the points of
and those of
under a
k-isomorphism, we obtain
. To support this process, for instance, given
in
Figure 5a, we obtain
.
- (2)
In the case of , using a method similar to the proof of the above Case 1 and the proof of Corollary 5, we complete the proof. For instance, we obtain .
□
Let us now recall the notion of digital -imbedding to study some generalized versions of Theorems 7–9 and Corollary 5.
Definition 6. [39] Consider two digital images and such that there is an arbitrary -isomorphism . Then, is said to be a digital topological imbedding into with respect to the -isomorphism h or the map h is called a digital topological -imbedding from into . Definition 7. In Definition 6, as to for X and for Y, if , then is said to be a strictly digital topological imbedding into with respect to the -isomorphism h. In particular, in the case with the same k-adjacency of both X and , a digital topological imbedding is simply understood to be an inclusion .
Based on the concept of the digital topological imbedding above, let us now make the digital wedge more generalized, as follows:
Definition 8. [39] Given two digital images in and in , where and , take and . Then, we define a digital wedge of and in with a k-adjacency of , where , denoted by , as one point union of the certain digital images and in satisfying the following properties. - (W1)
There are the following digital topological imbeddings, such that the set is assumed with the k-adjacency and further,
- (W2)
is a singleton, say ,
- (W3)
and are not k-adjacent, and
- (W4)
as for the subsets , the following properties hold. In view of this feature, we may consider to be which is one point union of and with k-adjacency.
As mentioned in [
39], given
, not every
always exists in
with a certain
k-adjacency of
, where
. For instance, given
and
, no
exists in
for any
k-adjacency, where
. However, given
and
, we can consider
in
with 26-adjacency, i.e.,
(see
Figure 5b). Based on the generalized digital wedge from Definition 8, we obtain the following:
Theorem 10. Given with , we obtain the following:
- (1)
if .
- (2)
if .
Proof. Using certain methods similar to the proofs of (1) and (2) of Theorem 7 and the proof of Corollary 5, we complete the proof. □
Theorem 11. Given with , we obtain the following:
- (1)
if .
- (2)
if .
Proof. Using certain methods similar to the proofs of (1) and (2) of Theorem 9, we complete the proof. □
Theorem 12. Given with , .
Proof. Using a certain method similar to the proof of Theorem 8, we complete the proof. □
Remark 4. In view of Lemmas 2 and 3 and Theorems 7–10, and Corollary 5, for , we observe that each depends on the numbers .
5. Conditions Being the Perfectness of
As for the study of some properties of
, we have recently studied the following cases,
[
39] and
(or
) [
39]. Thus, for the case of
, the study of
still remains. This section explores certain conditions which make
perfect. Based on the study of
[
8], and the property of (2), where
, this section investigates some digital topological properties of
, where
. Since
is
k-isomorphic to
and an alignment of fixed point sets is a digital topological invariant (see Proposition 3), we obtain
Furthermore, given a digital image , after studying -action on a digital object , we investigate certain properties of fixed point sets of by the -action on . Regarding this approach, we count on certain roles of and that are involved in the perfectness of (see Definition 11). Indeed, the study of still remains open. Up to now, it turns out that digital fundamental groups of and are strongly related to the digital topological features of alignments of fixed point sets of them (see Theorem 13). Given , we use the notation .
Definition 9. [26] Given a digital image , we say Given
, for
, we define
. As a generalization of
[
8,
26], the following is defined.
Definition 10. Given a digital object , we say that the digital image is an alignment of the set of cardinalities of fixed point sets of maps in , where . Then, we call (or for brevity) an alignment of fixed point sets of according to .
In view of Definition 10, it is clear that is a special case of stated in Definition 9. Using Lemma 4, we obtain the following:
Proposition 3. [26] The quantity is a digital topological invariant. Definition 11. [8] Given , if , then (or for brevity) is said to be perfect. Remark 5. In view of Lemmas 2 and 3 and Theorems 7–12, we observe that each , , is a proper subset of .
We now explore some conditions supporting perfectness of an alignment of fixed point sets.
Lemma 4.
- (1)
In the case is k-contractible, is perfect [8]. - (2)
In the case is not k-contractible, is not perfect [8]. - (3)
Given , [26].
Regarding Lemma 4, we also need to remind that not every
k-contractible digital image
has a perfect
[
26]. However, by Lemma 4, it is clear that the
k-contractibility of
implies the perfectness of
and the converse also holds [
8]. This section is based on the studies of some digital topological properties of
in [
8] and the perfectness of it associated with the number
l, where
[
8]. One important thing to note is that we need to recall that the digital
k-fundamental group of
is trivial or an infinite cyclic group with an infinite order depending on the number
l (see Theorem 3). For instance,
is
k-contractible [
5], and if
, then
is not
k-contractible [
5] (see also Theorem 3).
In view of Theorems 3–5, since the number
l of
strongly influences some digital topological properties of
. In particular, depending on the number
l (even or odd), many digital topological properties of
are determined. A recent paper [
26] only proposed the property referred to in Lemma 4(3). In view of the property of (2), we need the following result improving the assertion of [
26] (see Lemma 4(3)).
Lemma 5. [8] Given with , . Theorem 13. Given , , if is isomorphic to an infinite cyclic group such that or trivial, then is perfect.
Proof. (Case 1) Let us consider the case that
is trivial. Then, by Theorem 3, owing to the
k-homotopic property of
, by the properties
and
of Definition 2, it is clear that each
and
are
k-contractible. Thus, by Theorem 3, we have only the case
. Then, by Lemma 4, we obtain
which proves the perfectness of
.
(Case 2) Let us consider the case that is isomorphic to an infinite cyclic group. Then, without loss of generality we may replace by or (see (22)), where .
Without loss of generality, we may take .
(Case 2-1) Let us assume
. Owing to the part
of
, if
, by Lemma 4(3), we obtain [
8]
which implies the perfectness of
because
.
(Case 2-2) Let us assume
. Owing to the part
of
, if
, by Lemma 5, we obtain [
8]
which implies the perfectness of
because
. □
Since the perfectness of
depends on the numbers
and
, the paper [
8] investigated various properties of
,
,
, and so on.
As mentioned in the earlier part, sinc also plays a crucial role in digital and computational topology. Let us explore an alignment of fixed point sets of . Let us now explore for the case .
Theorem 14. In the case , has three 2-components. Namely, , where .
Proof. Regarding
, though there are several cases of self-
k-continuous maps of
we have the following four cases.
First, from (a) we obtain the following:
Second, from (b) we have the following:
Third, from (c) and (d), the following is obtained.
Hence based on these three quantities as subsets of
, we obtain
For instance, in the case
, we obtain
Thus, in view of these calculations and by the property in (23), in the case
, we can conclude that
has three 2-components. Furthermore, we have the formula representing (23) in the following way. If
, then we obtain
where
. □
Example 3. . Thus, we see that the alignment has three 2-components.
Based on Theorems 13 and 14, we obtain the following:
Theorem 15. Assume . Then, .
Proof. Using a method similar to the approach taken in (23), regarding
, it is sufficient to consider the following
k-continuous self-maps
f of
such that
First of all, from (a) above and Lemma 4, since
has the cardinality
, we obtain
Second, from (b) above, we have
Third, from (c) and (d) above, we obtain
Owing to the hypothesis “
,
”, and the Properties (24)–(26), we conclude that
which completes the proof.
For instance, in the case
and
, we obtain
□
Example 4.(1) .
(2) .
As shown in (1) and (2) above, we observe that these alignments consist of three 2-components.
In view of Proposition 3, we obtain the following:
Corollary 6. Given a digital image , the perfectness of is a digital topological invariant.