1. Introduction
The no-slip condition is the standard boundary condition in mathematical fluid flow models. It expresses the fact that a fluid adheres to the surface
S, i.e., the velocity
on
S. Nevertheless, in many situations a motion of the fluid on
S such as a slip along impermeable
S or a leak through semipermeable
S can be observed. The Navier slip condition is the simplest one [
1]:
, where
is the adhesive coefficient,
,
denotes the shear stress, and the tangential component of
u, respectively. From its form we see that the fluid starts to slip whenever
. However, this is not the case, in general. For example, a water drop on an inclined plane which is coated by a non-wetting (hydrophobic) material (teflon, e.g.,) slips only if the angle inclination reaches a specific value. Similarly, a leak of a fluid through semipermeable
S may occur only if the magnitude of the stress vector
(or some of its components) on
S attains a certain critical value. The true slip or leak boundary conditions should reflect this threshold behavior. To this end one can use tools of convex analysis and write them in a compact form as inclusions for set-valued mappings, defined by the subgradient of appropriate convex functionals [
2]. The overview of different threshold slip laws is presented and discussed in [
3]. Since “slip” in fluid mechanics is a synonym for “friction” in solid mechanics (in particular in contact mechanics), it is not surprising that friction and slip models use the same terminology. The weak form of mathematical models under threshold slip or leak conditions leads to a variational inequality type problem, intricacy of which depends on the used law. The simplest one is the threshold slip and leak condition of the Tresca type defined by:
and
respectively, where
g is an a-priori given threshold bound,
stands for the absolute value of a real number or the Euclidean norm in (
1) for 3D problems. The Stokes system under (
1) and (
2) has been studied by Fujita [
4,
5] and by Roux [
6] who considered more general slip models, in which the bound
g may depend on
. Despite the fact that the mathematical analysis of this class of problems began relatively late (compared with friction problems of contact mechanics), a lot of theoretical papers on this topic has appeared during past twenty years. Results have been extended to other fluid models and slip conditions such as the steady and unsteady Stokes and Navier–Stokes equations, Coulomb’s type friction law [
7,
8,
9,
10,
11] and the references therein. The Signorini unilateral boundary conditions [
12]:
with given
g,
is another type of conditions which leads to an inequality formulation. The authors used (
3) in [
13,
14] as the artificial outflow conditions prescribed on a part of the boundary to model the blood flow in large arteries.
One of difficulties we face in numerical solution of variational inequalities is the fact that problems are generally nonsmooth and consequently, appropriate computational methods have to be used [
15,
16]. For the Stokes or Navier–Stokes system with slip or leak conditions nonsmoothness is caused by the presence of the nondifferentiable functional
j whose subgradient defines (
1) or (
2). In the case of the Signorini conditions nonsmoothness is due to the kinematical constraint
on
S which imposes additional restrictions on the set of admissible velocity fields. The velocity–pressure formulation of such problems is discretized using a pair of finite element spaces satisfying the Babuska–Brezzi condition [
17,
18]. One way to handle the nondifferentiable term
j, the kinematical constraint in (
3), is to use a regularization of
j and a smooth penalization of the constraint, respectively in order to transform originally the nonsmooth problem into a sequence of smooth ones, which can be solved by standard methods. The regularization of
j has been used in [
19], and the penalty method in [
13]. Another and the most frequent way of releasing constraints and the nonsmooth character of mathematical models is based on a dualization approach. In the case of the Stokes and Navier–Stokes system, this leads to the weak velocity–pressuretype formulation which is enhanced by the additional Lagrange multipliers. The resulting weak formulation is formally the same as the Karush–Kuhn–Tucker conditions in saddle point problems. The majority of papers devoted to the convergence/error analysis of this class of problems uses just the dualization approach [
20,
21,
22,
23,
24,
25,
26,
27]. Moreover, there exists a wide range of numerical methods for efficient computational realization of the resulting algebraic models [
16].
The present paper is devoted to computational aspects of the Stokes problem with threshold leak conditions. We use the dual strategy, i.e., the velocity component is eliminated from an appropriate mixed finite element discretization of 2D and 3D problems. Our aim is to develop efficient algorithms for solving resulting algebraic systems which are satisfied by the dual variables, namely by the discrete pressure, shear and the normal stress on
S, in our case. Let us note that this approach is frequently used in contact problems of solid mechanics. However, its simple transfer to problems of fluid mechanics is not possible due to the presence of the incompressibility condition prescribed in the whole computational domain. The modified path–following (PF) variant of the interior point method has been used in [
27] for solving 2D Stokes system with threshold slip conditions, and in [
28] for 3D problems. In addition, the latter paper uses also the semi-smooth Newton (SSN) and compares it with the PF method. Although numerical experiments demonstrated the scalable behavior of both approaches, the SSN method turned out to be more efficient because of its simpler implementation. Similar numerical tests and comparisons of SSN and PF will be done in the present paper. It is hard to predict the computational efficiency in advance, since the discrete threshold leak conditions in 2D and 3D problems always lead to simple box constraints unlike the separable spherical constraints in the case of the threshold slip in 3D. Another important feature is the fact that the dual algebraic formulations involve relatively a small number of constrained unknowns. This excludes the efficient use of some types of algorithms such as strictly feasible minimization methods based on an active-set strategy [
29]. It has been found in [
27] for 2D problems that they are less efficient than the PF method. The inefficiency is more significant for large-scale 3D problems. The main benefit of this work is an application of dual strategies for solving the problem. The methods presented in this paper may be easily modified for parallelization based on the FETI domain decomposition technique [
30].
The paper is organized as follows. In
Section 2 we present the classical and several weak formulations of the problem. The mixed finite element approximation based on the P1-bubble/P1 finite element pair is introduced in
Section 3. The resulting algebraic problems are starting point for constructing of algorithms in
Section 4. Finally,
Section 5 contains results of numerical experiments, including the problems with non-unique solutions. Concluding remarks are summarized in
Section 6.
The following notation is used in the paper: , integer, stands for the Sobolev space of functions defined in which are together with their generalized derivatives up to order k square integrable in a domain . The scalar product in will be denoted by . denotes the set of non-negative functions from . If is a part of the boundary of then is the trace space on of functions belonging to . The space of matrices is denoted by , is the space of p-dimensional vectors, and denotes the non-negative orthant of . Bold characters are used for vectors and matrices. By we denote the zero matrix, or vector. Further stands for the identity matrix. The scalar product of two vectors , is denoted by . If , are two matrices then (summation convention is used). Caligraphic symbols will be used for index sets, for instance: and . If and , then stands for the matrix given by the rows of whose indices belong to . If is symmetric, positive definite with the smallest, and largest eigenvalues , respectively, then the spectral condition number of is . The indicator matrix of a subset is the diagonal matrix , where for and if . Finally, the symbol stands for the Euclidean norm in , .
2. Setting of the Problem
The aim of this section is to recall the classical formulation of the Stokes system with leak boundary conditions and to present several weak formulations of this problem together with main existence/uniqueness results.
Let
,
be a bounded domain with the Lipschitz boundary
which is decomposed into two nonempty, nonoverlapping parts
and
S both open in
. The
classical formulation of the problem reads as follows: find the velocity vector
and the pressure
satisfying the following system of differential equations and boundary conditions:
Here is the viscosity of the fluid, , denote an external force, and a nonnegative leak threshold, respectively. Further is the symmetric part of the gradient of u, n stands for the unit, outward normal vector to , , is the normal, and the tangential component of u on , respectively. Similarly, is the normal component of the stress vector on . It is worth noticing that unlike the shear stress , the normal component depends explicitly on the pressure p. The boundary conditions on S express the fact that there is no slip along S and the fluid can escape from only if the threshold g is attained, i.e., . In addition, the sign of is opposite to the one of .
Remark 1. The last two conditions in (4) can be written in the following equivalent way: where the symbol ∂ stands for the subgradient of convex functions.
To present variational formulations of (
4) we shall need the following function spaces and forms:
and
By the
weak velocity–pressure formulation of (
4) we call a problem of finding a pair
such that
From Green’s formula with an appropriate choice of test functions
v one can verify that the classical and weak velocity–pressure formulations are equivalent for sufficiently smooth solutions
([
5]).
Restricting to test functions
we arrive at the
weak velocity formulation of (
4):
which is equivalent to the following minimization problem:
where
Problem (
8) is the variational inequality of the second kind and it has a unique solution
u [
15].
The following existence/uniqueness result has been established in [
4,
5].
Theorem 1. Problem (6) has a solution for any and . The velocity vector u is unique. If there is a set , such that on ω then the pressure p is unique, as well, otherwise p is determined up to constants c satisfying a.e. on S. Remark 2. If, besides Γ and S there is a portion , , where the value of σ is prescribed, i.e., given, then also p is unique.
Remark 3. It has been shown in [5] that, if p is not unique, then the range of the admissible constants c satisfying a.e. on S is the interval , where , , provided that the solution is smooth enough. The last formulation presented in this section is the variant of the velocity–pressure formulation (
6) in which the Lagrange multipliers are used to release the no-slip condition
on
S and to regularize the nonsmooth term
j. To this end we shall need the following trace spaces:
and their duals
,
. If
is the domain with a smooth boundary
, e.g.,), then
and
.
Remark 4. If the solution is sufficiently smooth, then the normal and shear components of σ on S have been defined pointwisely at the beginning of this section. If no regularity assumptions are imposed on then and have to be understood as elements of and , respectively, defined bywhere the stands for the duality pairings. It is easy to see that the right hand sides of (9) and (10) depend only on , and on S, respectively, since solves the Stokes system in a weak sense. Moreover, belongs to and it satisfies the last two conditions on S in (4). Indeed, The duality pairing is defined by the -scalar product in this case.
Finally, let
be a closed, convex subset of
. To derive the new formulation we use the saddle-point approach. It holds:
where
is the Lagrangian. Suppose there exists a saddle-point
of
on
Q:
that holds for every
.
It is known (see [
2]) that the necessary and sufficient condition for
to be a saddle-point of
on
Q is the satisfaction of the Karush–Kuhn–Tucker conditions:
It is easy to see that
satisfies the Stokes system and the boundary conditions on
, i.e.,
solves (
6). Moreover,
,
is the corresponding shear, and normal stress on
S, respectively. The opposite assertion is also trivial: if
is a solution to (
6), then the quadruplet
solves (
11), where
,
is the corresponding shear, and normal stress on
S, respectively.
Theorem 2. A couple solves (6) if and only if the quadruplet is a solution to (11). Proof is straightforward. For more details we refer to [
31].
Remark 5. In the discrete counterpart of the problem we shall use the following more general form instead of j: Then the weak formulation (6) is modified as follows: find a pair such that The function characterizes pore opening. The respective leak condition reads as Therefore the substitution transforms the leak condition (13) formally into (5) so that all results of this section remain valid also for problem (12). 3. Mixed Finite Element Method and Algebraic Formulations
In this section we present the algebraic form of the problem, which will be used in the subsequent parts of the paper for numerical solution. It is based on the discretization of the velocity–pressure formulation (
12) by a mixed finite element method. Next we shall suppose that
is a polygonal
, or polyhedral
domain. If not, then
is approximated by them. Let
,
be finite element approximations of
,
, and
, respectively, such that the bilinear form
b satisfies the Babuska–Brezzi condition:
where
does not depend on the discretization parameter
h.
The mixed finite element approximation of (
12) reads as follows:
In computations we use the P1-bubble/P1 finite element pair [
32] on a regular partition
of
into triangles, tetrahedras for
, and 3, respectively. On
we define the finite element spaces:
where
,
are the spaces of polynomials of degree one and of bubble functions of degree three (
) and four (
) on
, respectively.
The algebraic counterpart of (
14) reads as follows:
with
where the absolute value is understood componentwisely,
,
with
being the number of nodes belonging to
. Here,
,
stand for the number of the finite element nodes of
in
, and
, respectively, while
denotes the number of the triangles/tetrahedras in
. Further,
is a symmetric, positive definite diffusion matrix,
is a full row-rank divergence matrix, and
is a vector of nodal forces. The unit outward, normal vector at the
i-th node of
defines nonzero entries in the
i-th row of the matrix
. For
, the tangential vector defines nonzero entries in the
i-th row of the matrix
. For
, there are two mutually orthonormal tangential vectors that define nonzero entries in the
i-th rows of the matrices
. In this case,
.
Denote
that is the local index set of the nodes belonging to
. The algebraic version
of
j introduced above is the result of numerical integration, assuming that
. For
we use the following integration formula on the triangular element
with the vertices
:
where
,
is the centre of gravity of
, and
is the
i-th component of
. Summing up (
17) over all
we arrive at:
where
and
is the number of the triangles
sharing
as the common vertex. In the same way we get:
where
. We proceed analogously for
when
is a line segment,
, and
Thus problem (
15) can be written in the following equivalent form:
where
and
It is easy to show that the first component
in (
20) solves the discrete velocity formulation being the algebraic version of (
8):
where
Formulation (
22) is not suited for direct computations, as the constraints in
can be hardly handled for large-scale problems. Moreover, the function
is nondifferentiable caused by the term
jh. To overcome these difficulties, we will use the dual formulation of (
22) and derive the discrete counterpart of (
11).
We introduce three Lagrange multipliers:
to regularize
,
,
to release the discrete stick, and incompressibility conditions, respectively and denote
. Let
where
is the
i-th component of
. The term
can be written as follows:
Thus:
where the Lagrangian
associated with the velocity Formulation (
22) is defined for
by:
Until now, the velocity vector
incorporates
bubble components. These components are usually eliminated before the computational process [
33]. In our case, we perform this elimination in a saddle-point formulation for
, which leads to the reduced Lagrangian
defined by:
To simplify notation here and in what follows, we use the same symbols for the corresponding matrices and vectors before and after the elimination of the bubble components. The dimensions of the reduced matrices are:
,
,
,
, and
. Note that these matrices preserve the same properties as before the elimination, especially, the expression (
21) remains valid with
being symmetric, positive definite. The presence of the symmetric, positive semidefinite matrix
and of the vector
is due to this elimination. Note that
has the defect one and the eigenvector whose all components are equal to 1 corresponds to zero eigenvalue.
The new saddle-point formulation of (
22) reads as follows:
or, equivalently,
where
.
Remark 6. Here, , , are the discrete counterparts of (see Remark 5), , and p, respectively. The change of the sign at and is for convenience of readers. One can see at a glance that the dual Hessian will be positive definite, as introduced bellow is assembled from matrices without any negative signs.
Now we eliminate the unknown
. Denoting
, the first equation in (
24) yields
. Inserting
into the first inequality in (
23), we arrive at the dual formulation of (
22):
where
,
with
being symmetric, positive definite provided that
from Remark 2 is nonempty, and
. In what it follows we will assume that
is non-singular. The case
will be discussed in Example 3.
It should be noted that (
25) is more convenient for numerical solution unlike (
22) as the function
is differentiable (quadratic) and the feasible set 𝕏 is defined by the box constraints. The solution to (
25) may be computed by an appropriate algorithm of the constrained minimization. Another way how to solve our problem originates from (
24) but with the algebraic leak boundary conditions expressed by projections on appropriate convex sets. The resulting system of nonsmooth algebraic equations can be solved by the nonsmooth Newton type method.
5. Numerical Experiments
The computations were performed by the supercomputer Salomon at IT4I VŠB-TUO [
40]. The Salomon cluster consists of 1009 compute nodes. Each node is a powerful x86-64 computer with Intel Xeon E5-2680v3 processors equipped with 24 cores and at least 128 GB RAM. All codes are implemented in Matlab R2020a. The velocity component is eliminated in both algorithms by solving auxiliary linear systems involving
or
with the preliminary Cholesky factorization realized by the Matlab function
chol. We use
Algorithm PF with
,
,
,
,
,
,
,
. These values turned out to be optimal, as it follows from the tests in [
34].
Algorithm SSN uses
,
, and
. The termination tolerance
leads to the relative residua of order
. In the tables below the numbers
,
of the outer iterations, and the matrix-vector multiplications by
or
, respectively, are monitored. Note that
determines overall complexities of computations. The partitions
of
are generated by Iso2mesh toolbox and ANSYS software [
41,
42]. As we have already mentioned, the finite element spaces use P1-bubble/P1 element pairs on
. The resulting mesh will be characterized by values of the parameters
,
,
introduced in
Section 3. The stiffness matrices are assembled by the vectorized code [
33,
43]. To guarantee the uniqueness of the solution to (
4) we will consider that
is decomposed into three non-overlapping and non-empty parts
,
S, and
open in
(see Remark 2). Nevertheless, one example and comments when
will be presented, as well. Finally note that all physical quantities are considered in the SI system so that the units of
g and
are
and
, respectively.
Example 1. (Square in 2D). Let
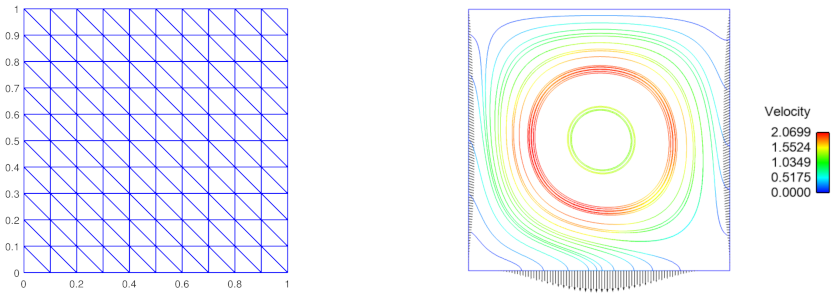
. To construct the triangulation
we first cut
into small squares and then each square into two triangles, see
Figure 1(left). The decomposition of
is defined as follows:
,
,
, where
,
. Further
in
,
,
on
,
on
,
, and
on
S (see Remark 5), where
, and
Note that
satisfies the homogeneous Dirichlet boundary condition on
. Data are chosen in such a way that both, leak and no leak zones appear on
S.
Figure 1 (right) presents the streamlines of the computed solution. One can see that the leak on
S generates the fluid suction on
.
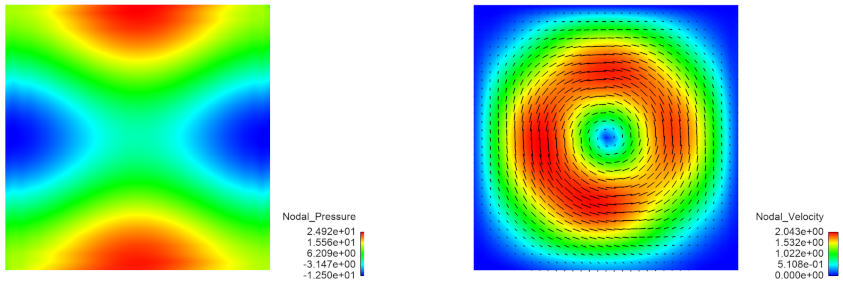
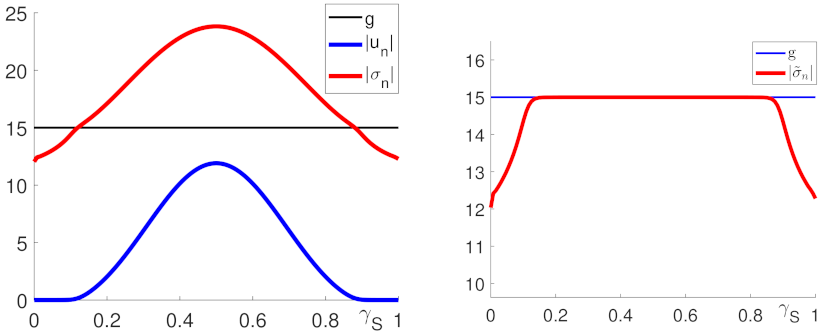
Figure 2 shows the pressure and velocity distribution in
. The magnitudes of the normal velocity
and of the normal stress
on
S are seen in
Figure 3 (left), while
is depicted in
Figure 3 (right). In the tables below the values
,
, and CPU time (in seconds) for different finite element meshes with increasing
,
, and
, and different values of
g are compared. The computational complexities for
are shown in
Table 1. The analogous characteristics for
(leak everywhere) and
(no leak) are summarized in
Table 2 and
Table 3, respectively. In view of the values of
, one can see that both algorithms are scalable. The computations without preconditioning are considerably less efficient as it is seen from
Table 4.
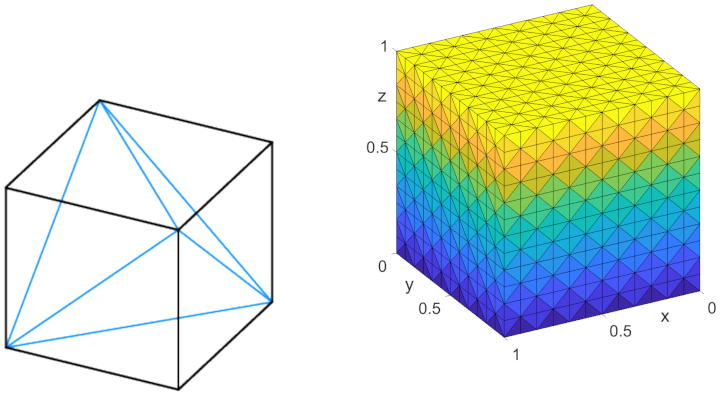
Example 2. (Cube in 3D). Let
. To construct the partition
we first cut
into small cubes and then each cube is split into five tetrahedras, see
Figure 4. The partition of
into
,
S, and
is defined as follows:
,
,
, where
,
,
,
,
,
. Further
in
,
,
on
,
on
,
, and
, where
, and
Again,
satisfies the homogeneous Dirichlet boundary condition on
and data are chosen in such a way that both, leak and no leak zones appear on
S.
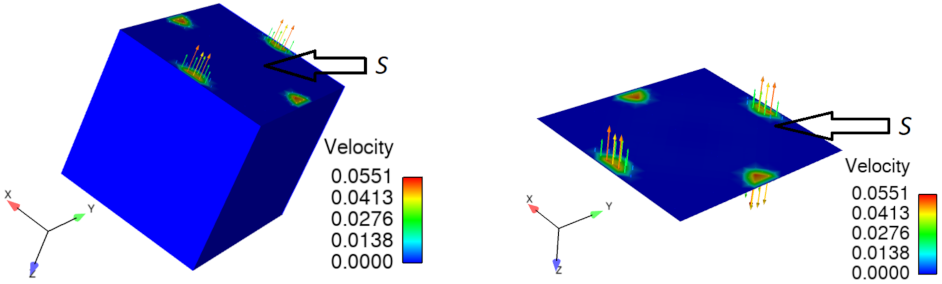
Figure 5 shows the distribution of the velocity field on
S and
. One can see the leak zone in the middle of
S and the fluid suction on
. The same suction effect appears on
. The normal stress
and
on
S are seen in
Figure 6. In
Table 5,
Table 6,
Table 7 and
Table 8 we summarize analogous characteristics as in Example 1. The conclusions are also analogous, i.e., both algorithms turn out to be scalable also in 3D and the preconditioner plays an important role. Notice that the numbers
of the matrix-vector multiplications are lower compared to 2D case.
Example 3. (Cube in 3D, non-unique solution). We change the partition of
from Example 2 as follows:
,
, and
. Let us remind that, if
, the pressure might be non-unique depending on the choice of
g. Next we suppose that
g is constant and
on
S. To establish the critical value of
g we use the Stokes system with the homogeneous Dirichlet data prescribed on the whole boundary
. Assuming that its solution is smooth enough,
, where
is the corresponding normal stress. However since the whole procedure is applied to the finite element discretization, the regularity assumption is superfluous. For given physical data and the partition
characterized by the parameters
the value
. It is easy to show that if
, the problem has a unique solution with both, leak and no-leak zones on
S. If
, the solution is not unique and only no-leak zone appears on
S. The behavior of the algorithms for different
g is summarized in
Table 9. One can see that both algorithms are stable in all cases. The table presents also the values
and
computed for the respective
g. One can easily check that
for
, while
if
. The distribution of the velocity field on
S for
is seen from
Figure 7. Note that the matrix
used in (
25), especially its part
, has not the full row-rank due to
. Consequently,
and
for
are singular with the defect one and the eigenvector whose all components are equal to 1 corresponds to the zero eigenvalue. The matrix
of the inner linear systems in
Algorithm PF is regularized by adding the diagonal matrix
to
as seen from (
31) (there are non-zero diagonal entries on the level of
). Analogously, the matrix
in
Algorithm SSN is regularized by adding
to
(see (
41)) and by the choice of the active set
. These heuristic arguments show that the matrices of the solved linear systems can be regularized by the construction of the algorithms. Finally note that the condition number bounds of the preconditioned Schur complements (
32) and (
42) are no longer valid. Nevertheless, the preconditioners can still be used and play the same important role as in the previous examples.
Example 4. (3D branched tube). Let
be the branched tube as in
Figure 8, where the partition
and the partition of the boundary
is also depicted. This tube may represent a final part of the capillary in the human body. On
we prescribe the input velocity
,
with
,
while
consists of two outputs of the tube with the natural outflow condition
. The leak condition is prescribed on
. Further
in
,
, and
. The partition
is characterized by the following values of the parameters:
,
, and
. The behavior of
Algorithm PF and
Algorithm SSN for different
g is reported in
Table 10. The distribution of the velocity and the pressure for three selected
g is depicted in
Figure 9. Almost all liquid leak through the wall at the vicinity of
for the smallest value
can be observed, see
Figure 9 (top). The leak through the wall is minimal for
, see
Figure 9 (bottom). The pressure is also growing for higher values of
g. The zoomed parts of the velocity fields near
and
are depicted in
Figure 10 (the velocity distribution inside the tube looks like the Poiseuille distribution). We used the reorthogonalization technique of the descent vectors inside the CGM solver [
44] that increases considerably efficiency of computations; compare
Table 10 with
Table 11.