Adaptive Control for Constrained Nonlinear Systems Under Deception Attacks and Actuator Saturation
Abstract
1. Introduction
- To handle sensor deception attack while enforcing state constraints, a modified coordinate transformation is proposed, upon which a BLF structure is constructed. Compared with existing BLF-based methods [21,34], the proposed approach preserves both state constraint satisfaction and BLF feasibility even when state measurements are corrupted—an interdependent issue not sufficiently addressed in prior works.
- Unlike previous research that investigates actuator saturation [27] and controller deception attacks [22] separately, this work analyzes their compounded influence within a unified BLF framework. An adaptive decoupling-compensation strategy is developed to mitigate these effects separately, thereby enhancing robustness under adversarial actuator conditions.
Notations
2. Problem Formulation
3. Main Results
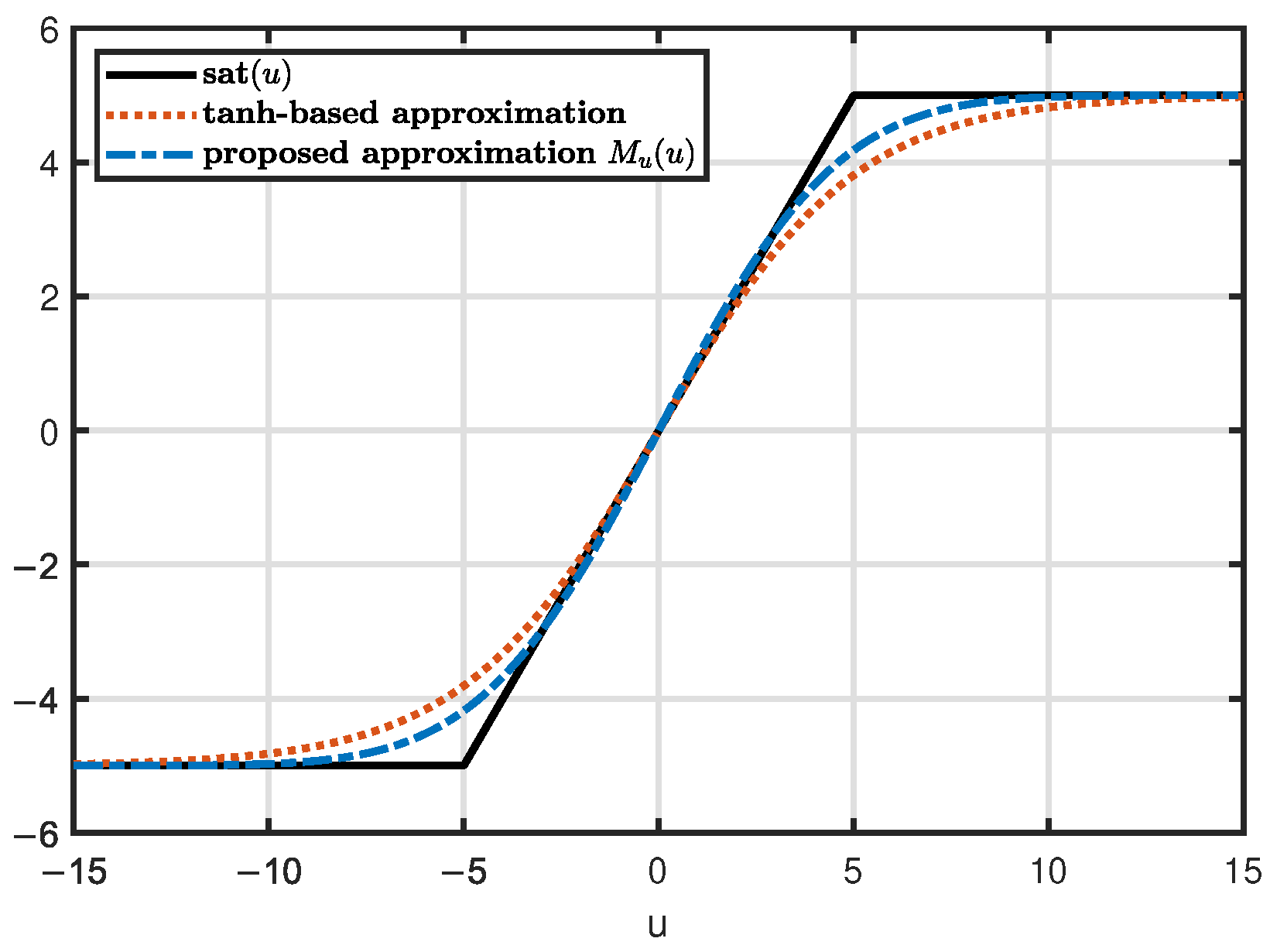
3.1. Saturation Approximation
3.2. Modified Transformations
3.3. Barrier Lyapunov Function
3.4. Controller Design
- Step 1:
3.5. Stability Analysis
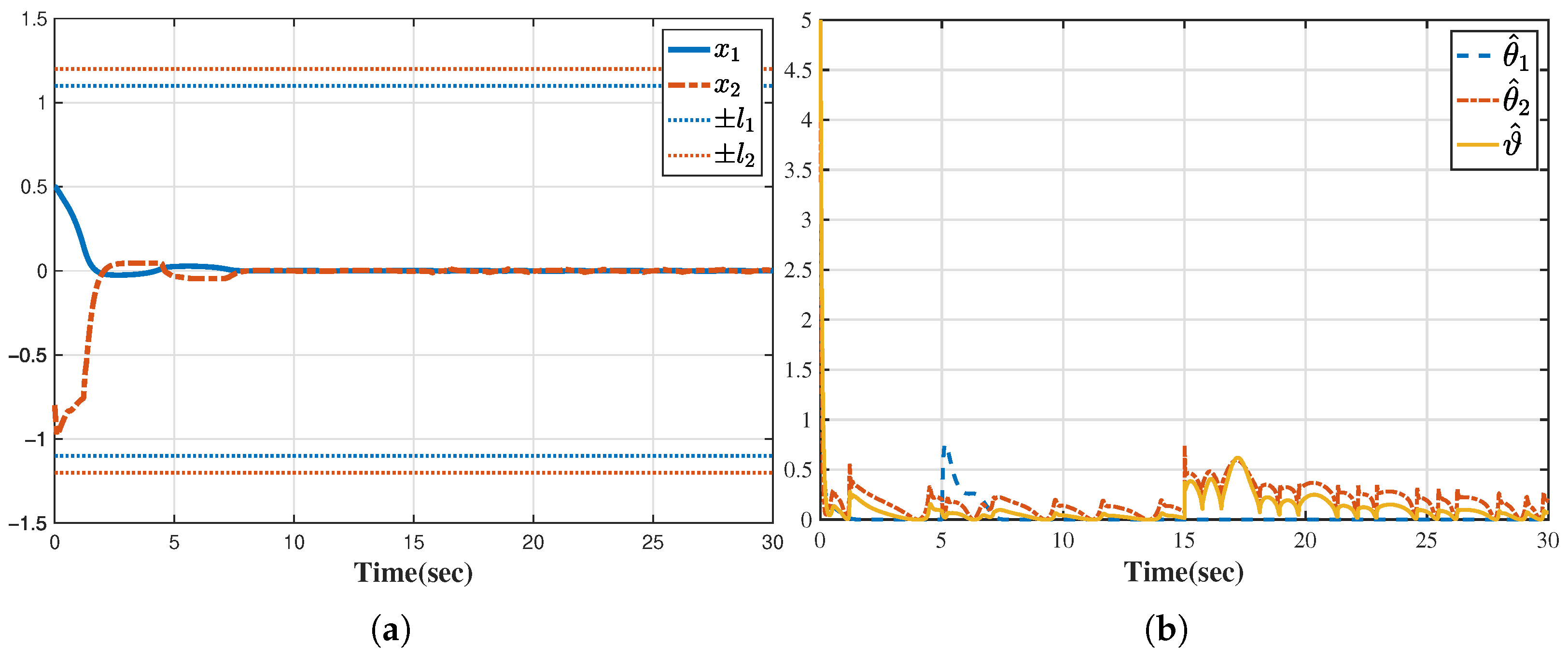
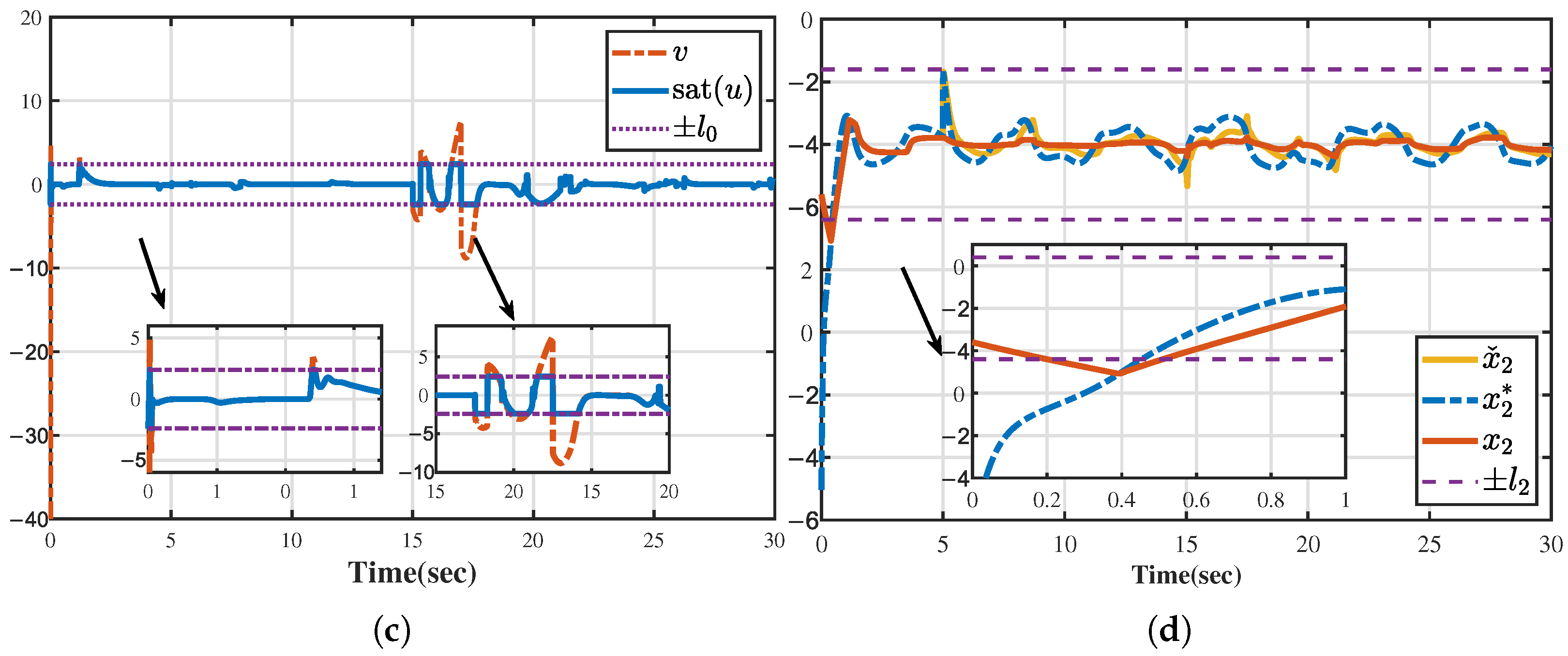
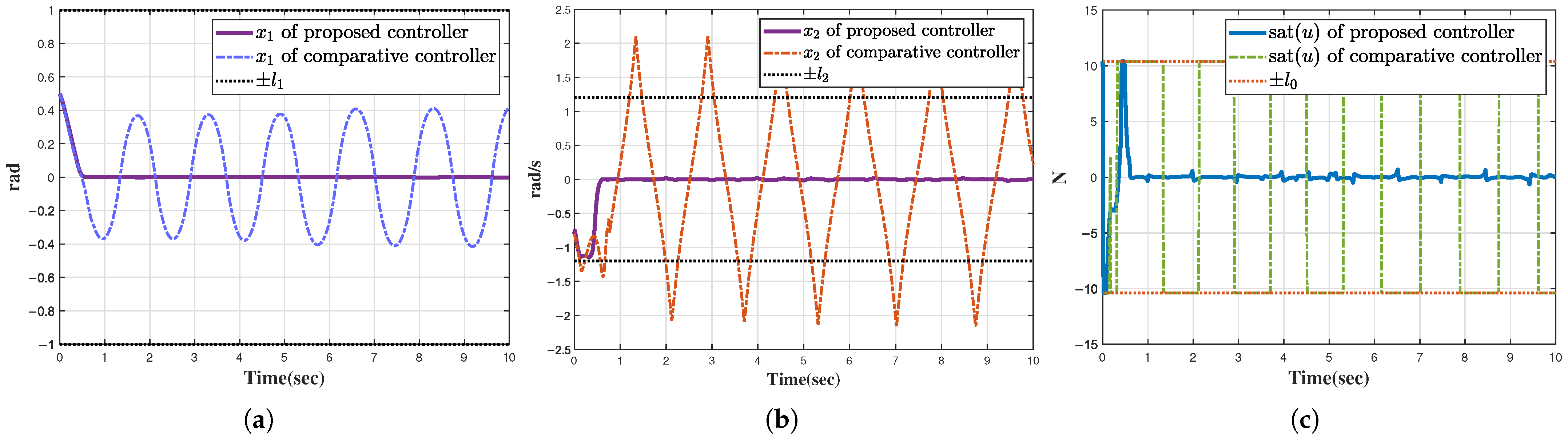
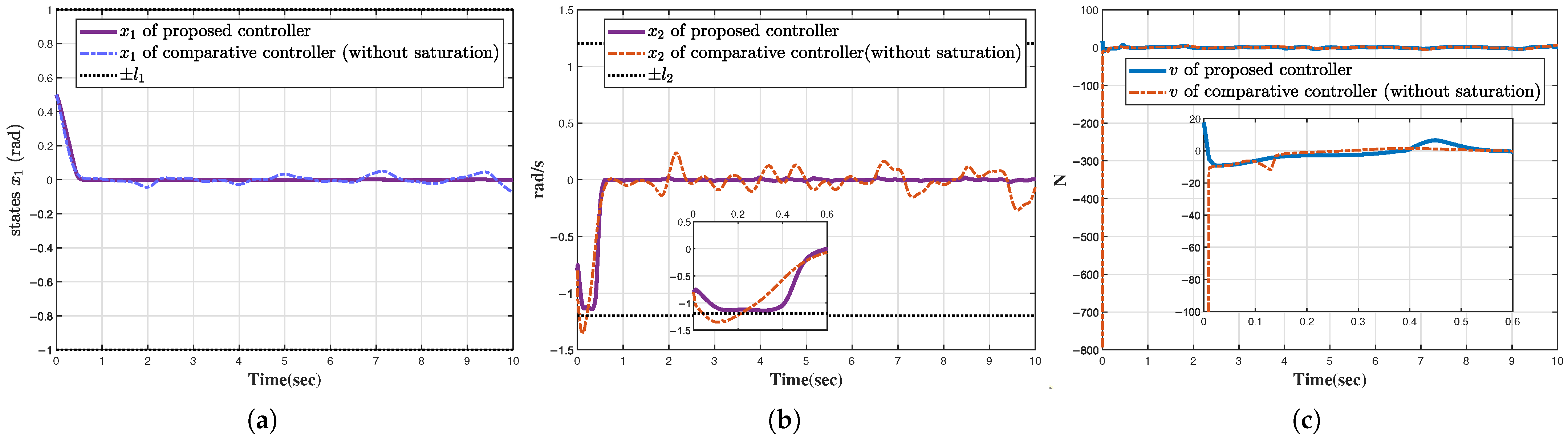
4. Simulations
| Algorithm 1 Adaptive Controller Implementation |
|
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Useful Lemmas
References
- Zhao, D.; Wang, Z.; Wei, G.; Han, Q.-L. A dynamic event-triggered approach to observer-based PID security control subject to deception attacks. Automatica 2020, 120, 109128. [Google Scholar] [CrossRef]
- Hu, L.; Wang, Z.; Han, Q.L.; Liu, X. State estimation under false data injection attacks: Security analysis and system protection. Automatica 2018, 87, 176–183. [Google Scholar] [CrossRef]
- Yang, Y.; Huang, J.; Su, X.; Deng, B. Adaptive control of cyber-physical systems under deception and injection attacks. J. Frankl. Inst. 2021, 358, 6174–6194. [Google Scholar] [CrossRef]
- Wang, X.; Zhao, P. An adaptive control scheme against state-dependent sensor attacks and input-dependent actuator attacks in cyber-physical systems. IET Control Theory Appl. 2023, 17, 1061–1072. [Google Scholar] [CrossRef]
- Ren, X.; Yang, G. Adaptive control for nonlinear cyber-physical systems under false data injection attacks through sensor networks. Int. J. Robust Nonlinear Control 2019, 30, 65–79. [Google Scholar] [CrossRef]
- Yang, Y.; Huang, J.; Su, X.; Wang, K.; Li, G. Adaptive control of second-order nonlinear systems with injection and deception attacks. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 574–581. [Google Scholar] [CrossRef]
- Yoo, S. Neural-network-based adaptive resilient dynamic surface control against unknown deception attacks of uncertain nonlinear time-delay cyber-physical systems. IEEE Trans. Neural Netw. Learn. Syst. 2020, 31, 4341–4353. [Google Scholar] [CrossRef]
- Wang, X.; Zhou, Y.; Yang, L. Event-triggered cooperative adaptive neural control for cyber-physical systems with unknown state time delays and deception attacks. IEEE Trans. Syst. Man Cybern. Syst. 2023, 53, 3540–3552. [Google Scholar] [CrossRef]
- Wang, H.; Wang, Y.; Zhuang, G.; Xia, J. Dynamic event-based prescribed-time practical consensus for nonlinear multi-agent systems under DoS and deception attacks. Nonlinear Dyn. 2025, 116, 16629–16642. [Google Scholar] [CrossRef]
- Ju, Z.; Zhang, H.; Tan, Y. Deception attack detection and estimation for a local vehicle in vehicle platooning based on a modified UFIR estimator. IEEE Internet Things J. 2020, 7, 3693–3705. [Google Scholar] [CrossRef]
- Wang, H.; Ren, Y.; Fang, Y. An optimal attack strategy based on adversary-modified historical innovations. IEEE Internet Things J. 2024, 11, 33337–33345. [Google Scholar] [CrossRef]
- Wittenmark, B. Adaptive dual control methods: An overview. IFAC Proc. Vol. 1995, 28, 67–81. [Google Scholar] [CrossRef]
- Lei, W.; Li, C.; Chen, M.Z.Q. Robust adaptive tracking control for quadrotors by combining PI and self-tuning regulator. IEEE Trans. Control Syst. Technol. 2019, 27, 2663–2671. [Google Scholar] [CrossRef]
- Lovi, A.; Fidan, B.; Nielsen, C. Multiple model reference adaptive control with blending for nonsquare multivariable systems. IEEE Trans. Autom. Control 2025, 70, 5780–5791. [Google Scholar] [CrossRef]
- Chu, H.; Yi, B.; Zhang, G.; Zhang, W. Performance improvement of consensus tracking for linear multiagent systems with input saturation: A gain scheduled approach. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 734–746. [Google Scholar] [CrossRef]
- Cao, N.; Lynch, A.F. Inner-outer loop control for quadrotor UAVs with input and state constraints. IEEE Trans. Control Syst. Technol. 2016, 24, 1797–1804. [Google Scholar] [CrossRef]
- Tee, K.; Ge, S.; Tay, E. Barrier Lyapunov functions for the control of output-constrained nonlinear systems. Automatica 2009, 45, 918–927. [Google Scholar] [CrossRef]
- He, W.; Chen, Y.; Yin, Z. Adaptive neural Network control of an uncertain robot with full-state constraints. IEEE Trans. Cybern. 2016, 46, 620–629. [Google Scholar] [CrossRef]
- Song, Y.; Zhou, S. Tracking control of uncertain nonlinear systems with deferred asymmetric time-varying full state constraints. Automatica 2018, 98, 314–322. [Google Scholar] [CrossRef]
- Yuan, X.; Yang, B.; Pan, X.; Zhao, X. Fuzzy control of nonlinear strict-feedback systems with full-state constraints: A new barrier function approach. IEEE Trans. Fuzzy Syst. 2022, 30, 5419–5430. [Google Scholar] [CrossRef]
- Yuan, X.; Chen, B.; Lin, C. Neural adaptive fixed-time control for nonlinear systems with full-state constraints. IEEE Trans. Cybern. 2023, 53, 3048–3059. [Google Scholar] [CrossRef]
- Cuan, Z.; Ding, D.; Liu, X.; Wang, Y. Adaptive fuzzy control for state-constrained nonlinear cyber-physical systems with unmodeled dynamics against malicious attacks. IEEE Trans. Ind. Cyber-Phys. Syst. 2023, 1, 56–65. [Google Scholar] [CrossRef]
- Liu, Z.; Tang, J.; Zhao, Z.; Zhang, S. Adaptive neural network control for nonlinear cyber-physical systems subject to false data injection attacks with prescribed performance. Philos. Trans. R. Soc. A Math. Phys. Eng. Sci. 2021, 379, 20200372. [Google Scholar] [CrossRef]
- Dong, S.; Li, Y. Adaptive fuzzy event-triggered formation control for nonholonomic multirobot systems with infinite actuator faults and range constraints. IEEE Internet Things J. 2024, 11, 1361–1373. [Google Scholar] [CrossRef]
- Zhao, K.; Song, Y. Removing the feasibility conditions imposed on tracking control designs for state-constrained strict-feedback systems. IEEE Trans. Autom. Control 2019, 64, 1265–1272. [Google Scholar] [CrossRef]
- Chen, M.; Ge, S.; Ren, B. Adaptive tracking control of uncertain MIMO nonlinear systems with input constraints. Automatica 2011, 47, 452–465. [Google Scholar] [CrossRef]
- Wen, C.; Zhou, J.; Liu, Z.; Su, H. Robust adaptive control of uncertain nonlinear systems in the presence of input saturation and external disturbance. IEEE Trans. Autom. Control 2011, 56, 1672–1678. [Google Scholar] [CrossRef]
- Fan, Y.; Yang, C.; Li, Y. Fixed-time neuro-optimal adaptive control with input saturation for uncertain robots. IEEE Internet Things J. 2024, 11, 28906–28917. [Google Scholar] [CrossRef]
- Ma, J.; Ge, S.; Zheng, Z.; Hu, D. Adaptive NN control of a class of nonlinear systems With asymmetric saturation actuators. IEEE Trans. Neural Netw. Learn. Syst. 2015, 26, 1532–1538. [Google Scholar] [CrossRef] [PubMed]
- Li, Y.; Tong, S.; Li, T. Composite adaptive fuzzy output feedback control design for uncertain nonlinear strict-feedback systems with input saturation. IEEE Trans. Cybern. 2015, 45, 2299–2308. [Google Scholar] [CrossRef]
- Zhou, Q.; Wang, L.; Wu, C.; Li, H.; Du, H. Adaptive fuzzy control for nonstrict-feedback systems with input saturation and output constraint. IEEE Trans. Syst. Man Cybern. Syst. 2017, 47, 1–12. [Google Scholar] [CrossRef]
- Wu, Y.; Xie, X. Robust adaptive control for state-constrained Nonlinear Systems with Input Saturation and Unknown Control Direction. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 1192–1202. [Google Scholar] [CrossRef]
- Zhao, N.; Tian, Y.; Zhang, H.; Herrera Viedma, E. Learning-based adaptive fuzzy output feedback control for MIMO nonlinear systems with deception attacks and input saturation. IEEE Trans. Fuzzy Syst. 2024, 32, 2850–2862. [Google Scholar] [CrossRef]
- Gao, Y.; Niu, B.; Chen, W.; Wang, H.; Mu, C.; Wen, G. Adaptive control of constrained nonlinear CPSs under deception attacks through sensor and actuator networks. IEEE Trans. Circuits Syst. II Express Briefs 2024, 71, 1241–1245. [Google Scholar] [CrossRef]
- Wei, W.; Zhang, W. Command-filter-based adaptive fuzzy finite-time output feedback control for state-constrained nonlinear systems with input saturation. IEEE Trans. Fuzzy Syst. 2022, 30, 4044–4056. [Google Scholar] [CrossRef]
- Deng, H.; Krstic, M. Output-feedback stochastic nonlinear stabilization. IEEE Trans. Autom. Control 1999, 44, 328–333. [Google Scholar] [CrossRef]
- Lin, W.; Qian, C. Adaptive control of nonlinearly parameterized systems. In Proceedings of the 40th IEEE Conference on Decision and Control (Cat. No. 01CH37228), Orlando, FL, USA, 4–7 December 2001; Volume 5, pp. 4192–4197. [Google Scholar] [CrossRef]
- Sun, Z.; Zhou, C.; Liu, Z.; Meng, Q. Fast finite-time adaptive event-triggered tracking for uncertain nonlinear systems. Int. J. Robust Nonlinear Control 2020, 30, 7806–7821. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, S.; Zhao, P.; Li, M. Adaptive Control for Constrained Nonlinear Systems Under Deception Attacks and Actuator Saturation. Mathematics 2025, 13, 3508. https://doi.org/10.3390/math13213508
Zhang S, Zhao P, Li M. Adaptive Control for Constrained Nonlinear Systems Under Deception Attacks and Actuator Saturation. Mathematics. 2025; 13(21):3508. https://doi.org/10.3390/math13213508
Chicago/Turabian StyleZhang, Shixuan, Ping Zhao, and Muyu Li. 2025. "Adaptive Control for Constrained Nonlinear Systems Under Deception Attacks and Actuator Saturation" Mathematics 13, no. 21: 3508. https://doi.org/10.3390/math13213508
APA StyleZhang, S., Zhao, P., & Li, M. (2025). Adaptive Control for Constrained Nonlinear Systems Under Deception Attacks and Actuator Saturation. Mathematics, 13(21), 3508. https://doi.org/10.3390/math13213508





