Abstract
In a blockchain network, a rule set called consensus mechanism is used to create and finalize a block. In a proof-of-stake (PoS), consensus-based blockchain network, nodes become validators, minters, or stakeholders’ nodes to complete the consensus mechanism. In these networks, when a node becomes a validator node, its details need to be saved because the details of the validators are used in the network for many important decisions, such as selecting block proposers for the consensus process. In this paper, we present Sea Shield, which uses a validator chain to save a node’s information when it becomes a validator or leaves its responsibility as a validator in the PoS-based blockchain network. The validator chain is a blockchain that can run with the main chain of a PoS-based blockchain. The internal features of the validator chain are similar to those of the blockchain. We designed and simulated a consensus mechanism to create and finalize the block for the validator chain with no forks. We present a process by which a node may join or unjoin as a validator in a PoS-based blockchain network to improve the overall security of the main chain-consensus process.
1. Introduction
Digital ledgers have been stored in databases for many years. The method for keeping a ledger in a database has changed over time. To cope with the limitations of traditional database systems, new technologies have emerged. Blockchain is a new technology that saves data in a decentralized manner. Blockchain technology plays a significant role in improving many systems such as cryptocurrency [1], supply chain [2], e-voting [3], Metallurgical and Machine-building tasks [4], autonomous decentralized online social networks [5], health care [6], and Privacy-preserving decentralized learning [7]. The core feature of this technology is to save data by creating timestamp blocks in peer-to-peer networks. There is no central authority in the blockchain network to create blocks because blockchain technology works in a decentralized network, that is why every blockchain network uses a consensus algorithm to create blocks in the network, such as delegated proof of work (DPoW) [8], proof of stake (PoS) [9], practical Byzantine fault tolerance (PBFT) [10], and tendermint [11]. Many consensus algorithms are available in the literature. Currently, the most appropriate consensus algorithm is determined and adopted by a system according to its requirements and network type. There are four different types of blockchain networks available: (1) public permissionless such as Ethereum [12], (2) public permissioned, for example, Corda [13], (3) private permissionless like an LTO network [14], and (4) private permissioned such as Hyperledger Fabric [15].
With time, blockchain consensus algorithms have been customized and evolved according to application requirements. Satoshi Nakamoto was the first to use the proof-of-work (PoW) algorithm in Bitcoin cryptocurrency [16]. The major benefit of this algorithm is its high immutability, temper resistance, and high security; however, the algorithm consumes very high energy to complete its computation. Because of these limitations, many other consensus algorithms have been proposed to cope with the problems of PoW, such as PoV [17]. This consensus method involves a decentralized voting settlement between consortium members to reach an agreement. In comparison to the fully decentralized PoW consensus, this consensus employs a separate voting and supervisory principle to decrease transaction verification time and to enhance reliability and security. The participants allocated four security identities to take part in the voting procedure. Unlike PoW, using the proof-of-vote consensus removes the necessity for third-party mediators in the submission or validation of generated blocks. The other presented solution is the proof-of-stake (PoS) algorithm in the literature. The PoS algorithm does not consume high energy, but it has drawbacks; therefore, many different PoS-based consensus mechanisms have been proposed in the literature. According to the PoS algorithms presented in the literature, Xiao et al. [18] classified four different classes of PoS-based algorithms: chain-based PoS [9], committee-based PoS [19], BFT-based PoS [11], and delegated PoS [20].
In PoS, blockchain network nodes are required to become validator nodes because the validator nodes are those who complete the consensus process in the network. To be a validator node, all PoS-based consensus algorithms use any amount or token-stacking system in the network. The nodes become validators after the coin/token stacking in the network. Later, the network and other nodes of the network use the staking information of the validators, such as the amount, staking time, or any extra information (as per consensus) during the consensus process, for example, to select the next block proposer using staking value and age. Moreover, staking information is also required if forgery is found in the block and the system needs to punish the validator because some of the PoS-based blockchains are using slashing mechanisms [21] to prevent forgery and to improve security.
Validators are a very important part of the PoS-based blockchain because their information cannot be modified, changed, or deleted, and should be accessible to all after they become validators in the system. Traditional database systems do not offer all of the required features, but the blockchain technology itself provides the required features. The key features of this technology are trust, transparency, and immutability [22]. Therefore, we propose a Sea Shield that uses a validator chain based on blockchain technology, with a consensus mechanism to save validator information. The purpose of the validator chain is to save the information of the nodes when they become validators in the network and when they leave the validators’ responsibility in the network. We designed a consensus by using the concept of practical byzantine fault tolerance (PBFT) to improve the proof-of-stake (PoS), algorithm-based blockchain safety.
Our major contributions to this paper are as follows:
- The nodes’ information, when join and unjoin in the network as a validator, is the critical aspect of PoS-based blockchain network, and we have not found any solution in the literature that saved the PoS-based blockchain network’s nodes information securely. Therefore, we introduce Sea Shield, a blockchain technology consensus that uses a validator chain. The internal features of the validator chain are similar to those of any other blockchain.
- If the staking information is not saved securely, the whole PoS blockchain network safety would be at risk. So, the presented consensus mechanism creates and finalizes blocks for the validator chain with no forks [23] in a decentralized public-permissioned blockchain network.
- We discuss the block structure of the validator chain for both the join and unjoined mechanisms of the validator.
- We evaluate the performance of the Sea Shield through simulation. The results show that the validator chain operates securely with fork control in a malicious environment.
The rest of the paper is organized as follows: Section 2 provides a short review of the blockchain internal structure, forking problem, consensus algorithms related to this paper, and significance of the study; Section 3 describes the complete mechanism of the proposed Sea Shield when join/unjoin is a validator; Section 4 presents the algorithm with an explanation of the complete process flow of the Sea Shield; Section 5 shows the experiment and evaluation details of the simulation work; and Section 6 discusses the performance of the presented Sea Shield through a comparative analysis of the inside consensus characteristics. Finally, Section 7 concludes the study and discusses the limitations, and future work.
2. Preliminaries
2.1. General Blockchain Internal Structure
A blockchain consists of interconnected timestamp blocks in a peer-to-peer network. The blocks hold information according to the type of blockchain network. Blockchain is a digital ledger that can hold any type of data. Every block in a blockchain is a timestamp that is attached in chronological order. A timestamp is generally present in the header of the block. The first block is called the genesis block, and its block number in the chain is zero. The interconnected block mechanism, also called chaining in the blockchain, and is obtained using the cryptographic hash function [24]. Figure 1 shows the general chaining of the blocks in the blockchain. Every block has its previous block hash in the header, such that it creates a digital chain structure. Every node in the blockchain maintains a copy of its ledger. When a new block is created, it is broadcast to the entire network and every node updates its ledger by adding new blocks.
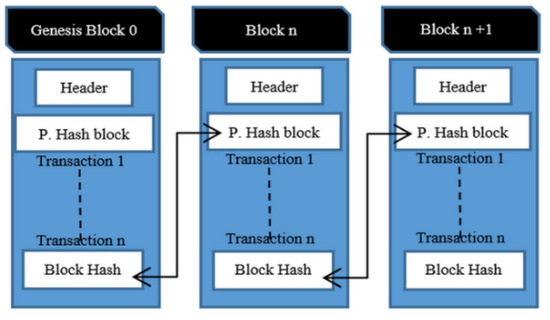
Figure 1.
Chaining of blocks in blockchain network.
2.2. Fork
A fork occurs when a linear blockchain ledger is split into two or more chains. In blockchain networks, forks occur for many reasons, such as adding new functionality, changing rule sets, addressing security risks, and resolving disagreements within the community on two blocks of the same height as Bitcoin and Ethereum [25,26]. This also occurs because of the blockchain consensus mechanism, such as in Bitcoin, when two valid blocks are pointing to a similar, previous block and are created and broadcasted simultaneously to the network, and then a fork appears in the blockchain network. Figure 2 illustrates the forking issue in the blockchain network.
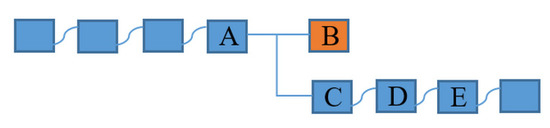
Figure 2.
Forking in blockchain.
The next block is created after the fork resolves the issue because it will point to one of the two blocks as the previous block in its block, such that block D points to block C. Most of the blockchains follow the longest chain rule [27] in the network. The longest chain is the one that has maximum details of the events that occur in the network. Here, +++A, C, D, E++ are considered the valid chain or the longest chain in the network. Block B is called the orphan block in the Bitcoin blockchain and the resources invested in the block are wasted. The transactions in the block also become stuck in the block because they are no longer part of the blockchain anymore.
2.3. Consensus Mechanism
Due to the unavailability of a central authority or third-party validation, the blockchain used a consensus mechanism to create and finalize the block in the network. We have many different consensuses in the literature, here we are going to discuss a few consensuses relevant to this paper. The proposed consensus uses the concept of BFT and PoS algorithms.
2.3.1. Practical Byzantine Fault Tolerance (Pbft)
Castro et al. presented an algorithm that solved the old Byzantine fault problem [10]. The algorithm works effectively under one-third of the malicious nodes’ environment. The algorithm is designed to tolerate one-third of the faulty nodes in a network. There are five steps in the algorithm for completing a request. The proposed algorithm follows the master/server concept. By some rules, one becomes a master and others become servers. In the first step, called the request step, the master server receives a transaction from any client and timestamps the transaction. In step two, called the pre-prepare step, the master server generates the order number and sends it to the other server nodes. In the third step, called the prepare step, if the master server receives accept messages from 2f + 1 nodes, the transaction is entered into the commit step. In the commit step, if the master receives commit messages from more than 2f + 1 server nodes, then the master considers the transaction accepted by other server nodes. The reply is the last step, in which the master responds to all server nodes to confirm the transaction. The Steller consensus [28] is an example of the PBFT consensus algorithm. The PBFT concept is used by many others in their own ways, such as Ant share. [29] used PBFT and proposed a consensus-delegated Byzantine fault tolerance [30].
2.3.2. Proof of Stake (Pos)
Many PoS consensus algorithms have been proposed in the literature. We describe the PoS algorithms, that is, how they work, and use staking in the consensus process.
Chain-Based Pos
Chain-based PoS is an alternative consensus to PoW. King et al. first proposed this consensus to reduce energy usage [31]. First, they were the Bitcoin developers. It operates under the Nakamoto consensus [16] framework. The longest chain rule, block validation rule set, gossip protocol [32] for message broadcasting, and probabilistic finality are used. In a chain-based PoS, there is a minter who solves the hashing puzzle [33] only once for a clock tick because the difficulty [34] decreases, according to the minter’s stake value. If the minter has a high stake value, then the difficulty of the hashing puzzle is considerably reduced for it and the expected number of hashing attempts to solve the puzzle would also be less. The consensus achieved a good reduction in energy consumption. Peercoin [31] and Nxt [35] are good examples of this type of PoS. Despite all of the good parameters, it also has some disadvantages, such as only the rich have the power to become a block proposer again and again, which leads to centralization issues in the network. There is also a security threat because only money is required to invest in a system to take control of a network whereas in PoW, money, hardware, electricity, and expertise are all required to interrupt the system.
Committee-Based Pos
A committee-based PoS does not depend on hashing puzzles such as chain-based PoS. This mechanism generates a committee of stakeholders, based on their stake values to create blocks. In this type of consensus mechanism, a multiparty computation (MPC) [36] scheme is generally used to create committees. The MPC takes stake values from the network as input and releases a list as the output of stakeholders through random selection. The stakeholders generate the blocks according to the MPC release list. The longest chain rule and probabilistic finality are perceived in this type of PoS consensus mechanism. Many consensuses use this type of PoS, such as snow-white [37] and chain of activity [19]. Kiayias et al. presented the protocol Ouroboros [38], in which they used time slots to produce blocks. They elected a leader for every slot to produce blocks. To improve security, every block producer considers the last three blocks of the chain as transient. This consensus improves decentralization, but it has its drawbacks. The block producer is susceptible to intentional attackers; this problem was solved by Ouroboros Praos [39].
Bft-Based Pos
Like other PoS-based consensus’, in BFT-based PoS consensus, the coin or token stacking mechanism has been used as a block producer in the network. The Byzantine fault tolerance (BFT)-based PoS uses many types of block-proposing mechanisms such as round robin [40] and committee election to produce blocks in the network. The check-pointing mechanism [41] replaces the longest chain rule in the BFT-based PoS to stabilize the main chain. The BFT-based PoS uses an additional layer for block finality. Consensus does not use the longest chain rule for probabilistic block finality. The BFT-based consensus has a fast and deterministic block finality. The BFT layer improves the liveness of the network, and the consensus can tolerate malicious nodes in the network. Many consensus mechanisms use BFT-based PoS concepts such as Tendermint [42], Algorand [43], and Casper FFG [44]. However, there are also disadvantages to using Bft-based PoS, such as an algorithm proposed by Kwon et al., that used a coin staking system to become a block producer in the system [11]. Because of the many block producers, consensus used the round robin algorithm to select a block proposer for the current round. They used Bft layers for block finalization because the extra layer of Bft in consensus, throughput has decreased. It increases block creation time and the communication message overhead of the consensus as well.
Delegated Pos (Dpos)
Delegated PoS is a partial member of a committee-based PoS because the committee is selected by the stakeholders to complete the consensus in the network through the voting process. In the DPoS, consensus members are called delegates. The election process is used to select delegates from among all stakeholders. The selected delegates proposed blocks in the network. Commonly used cases of DPoS are Bitshare [45], STEEM [46], LISK [47], and EOS.IO [48]. The DPoS is designed to reduce the number of consensus members so that messaging overhead can be controlled during the consensus. However, DPoS has many limitations as well. There are many works presented in the literature that try to improve DPoS, such as Yinghui et al., who presented an election mechanism to improve Dpos [49]. The algorithm used two election processes, one to elect the representative and the second to select the final winner and to reach a consensus. The algorithm is designed to improve the decentralization of the DPoS-based blockchain network. Qian et al. presented reputation-DPoS to improve the security of the DPoS consensus mechanism [50]. In the proposed model, nodes are divided according to their trust states. The algorithm only selects high-quality nodes to participate in the consensus algorithm. The selected consensus improves the security and efficiency of the algorithm. They introduced an improved incentive method by using reputation and tokens to attract voters. By using this algorithm, fair nodes will be selected. Nodes received votes and rewards on behalf of their behavior in the consensus.
2.4. Significance of the Study
The staking details of validators are very important. In a majority of PoS-based blockchain networks, block producers are the core part of the consensus. At some point, blockchain network security relies on their hand. They produce blocks and verify transactions in the network. The selection of block producers is mostly held by using their stake details. These details are a very critical part of the complete consensus process. We have seen that coin/amount staking plays a very important role in all PoS-based consensus mechanisms, such as in Table 1, which describes the staking amount requirements in the system. Therefore, the stacking details should not be tempered, altered, or deleted from the network. The details should also be available to all required ones. Hence, we present Sea Shield as a blockchain use case that uses a validator chain with a consensus mechanism. The proposed consensus mechanism saves the node’s information with all of the staking details when joining/unjoining as a validator in the network by a process flow. The join and unjoin process of the nodes as validators in the Sea Shield is completely transparent and the details are known by all of the nodes in the network. Normal computing environment infrastructure emphasizes confidentiality and integrity whereas blockchain is designed to offer integrity and availability on a decentralized distributed system. We used blockchain technology to save records because security in the blockchain is based on ensuring that data are protected from alteration. To restrict the data from modification, the technology copies the data to as many locations as possible so that the modification of all copies becomes infeasible. The validator chain works similarly to other blockchains. This is mainly the use case of blockchain technology. Figure 3 shows the chain of blocks for the validator blockchain.

Table 1.
The use of staking amount information in the PoS-Based blockchain network.
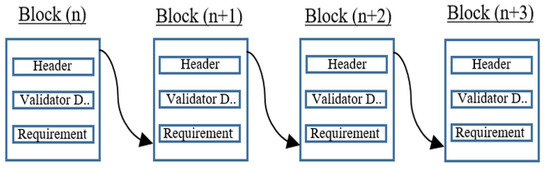
Figure 3.
Validator blockchain.
3. Proposed Consensus
The proposed consensus has two parts:
- 1.
- The Joining mechanism
This part contains the process of a node becoming a validator and the block structure joining as a validator in the validator blockchain.
- 2.
- The unjoin mechanism
This section illustrates the unjoin process of the validator from the network as well as the block structure for unjoin as a validator.
3.1. The Joining Mechanism
We designed the process for the PoS-based public permission blockchain system, in which anyone can join the network and create transactions; however, to participate in the block creation and finalization process, the node first needs to become a validator node. We presented a mechanism by which a node can become a validator node. When a node wants to become a validator node in the network, it must follow the joining mechanism. Figure 4 shows the process flow of the joining mechanism of a node to become a validator in the network.
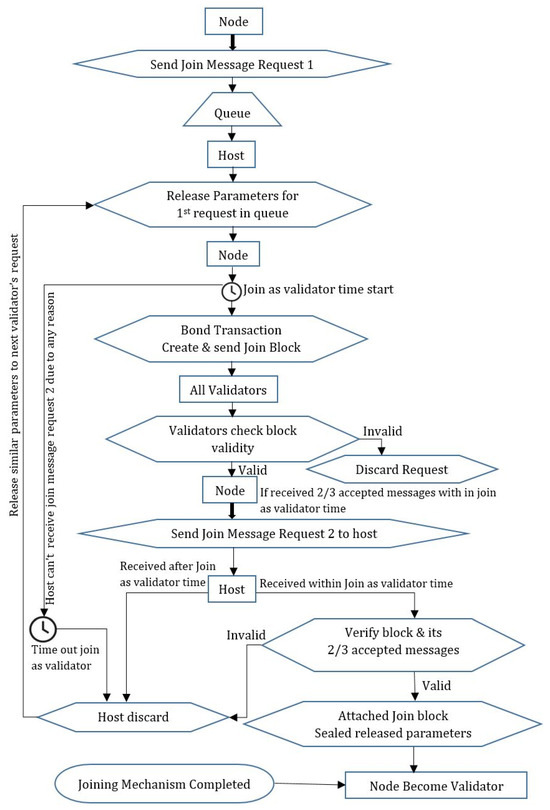
Figure 4.
Joining mechanism to be a validator in the network.
The node first generates a join message request 1 and sends it to the network host to start the joining mechanism. We use the term network host to refer to any person, software, or moderator running the blockchain network. All requests received by the host are saved in the queue maintained by the host. When the host is free, it responds to a request. The host generates and broadcasts the following parameters for the requested node:
- 1.
- Validator Number
An ID is assigned to the node by the host node. If the node is new and was never a validator node, the network host assigns a unique ID to the node as a validator number. If the node completes the join process as a validator and becomes a validator in the network, the validator ID assigned by the network host to the node would be sealed from the network. The network will not assign this ID to any other node, insofar as the node leaves the validator’s responsibility with an unjoin mechanism. If the existing validator leaves its validator’s responsibility, it becomes a normal node by unjoining. Subsequently, the same node returns to become a validator node in the network, and the network assigns a similar validator ID to the node that was first assigned to it.
- 2.
- Date Time (h)
This is the date and time when the network host generates a block number for the node.
- 3.
- Hash (n − 1): (Previous block hash)
It is the hash [24] of the latest block of the validator chain that the network host releases to the node so that the node may use it as the previous block hash in the block.
- 4.
- Total Validators Count
It is the total validator of the network immediately before the node’s request is received by the network host.
- 5.
- Block Number (n)
It is a serial number assigned by the network host to the node’s block as per the chain of the validator. The network host generates this node’s block number by increasing the last validator’s chain block number by one.
After releasing the parameters to the node and broadcasting them in the network, the hosts wait time has started. The host does not release any parameters to any requests until the request being processed has finished its joining process or the join-as-validator time duration allocated to this request has ended. Every network has a specified set of pre-defined time durations for the joining mechanism called join-as-validator time. The join-as-validator time starts after the node receives parameters from the host. The node must finish its joining mechanism within the join-as-validator time, otherwise after the join-as-validator time the network host discards the node’s request and releases all generated parameters, except the Date Time (h), to the next node’s request in the queue.
The next requested node receives a similar Validator Number, Block Number (n), Total Validators, and Hash (n − 1) but the recent Date Time (h). The Date Time (h) is always the time when the network host releases the parameters to the node.
After receiving the required parameters from the host, the node actively creates a validator block for the validator chain to join as a validator in the network. Two parameters are required to create a validator block i.e., a bond transaction and extra bonding time commitment.
3.1.1. Bond Transaction
A node must conduct a bond transaction and broadcast it on the network. The node can use any amount greater than the minimum amount set by the network for bond transactions. The network decides the minimum transaction amount that a node can perform to be a validator. This is a special bond transaction, and the amount used in the bond transaction cannot be used further by the node, as long as the node remains a validator node in the network. When a node wants to use its bonded stakes, it must first leave its validator responsibility in the network and become a normal node, then it may use its bonded stake.
3.1.2. Extra Bonding Time
Extra bonding time is the time duration that is committed by a node and is broadcasted with the transaction. When a validator wants to leave the validator’s responsibility in the network, the validator must pass an extra bonding time duration plus the network default bonding time duration to leave the validator’s responsibility. The network default bonding time duration is the time duration that the network sets for every validator in the network. The significant extra bonding time duration commitment makes a validator more trustworthy by other validators because if the validator performed any forgery during the consensus process, it could easily be punished by the network. The network imposes a penalty on the validator. Due to the penalty, the validator can completely lose its stake or be deducted, depending on the forgery size and network rule.
After completing the bond transaction, the validator can create a validator block. The validator block contains the following parameters:
- 1.
- Header
Block Number (n), Block Hash (n), Block Status, Hash (n − 1), Date Time (b).
- 2.
- Validator details
Node Identity, Validator Number, Date Time (h), Validator Status, Reactivation Number, Total Validators.
- 3.
- Requirement
Extra Bonding Time(m), Transaction, Date Time (t), Stake Value, Wallet Proof.
Where the Block Number, Hash (n − 1), Validator Number, Date Time (h), and Total Validators Count are issued by the host. Block Hash (n) contains the hash of the current block. Block Status shows the block is created for “join as validator”. Date Time (b) is the date and time when a node creates a block, and Node Identity is the identity of the node in the network, such as its wallet address [51] or any other address. Wallets are used to store the user’s credentials and all of the account-related information of the user. In the blockchain, the wallets keep track of all assets of the user. It also holds the private [52] and public [53] user keys. Validator Status shows the validator’s current status; the block is for the joining mechanism whose status is active. Extra Bonding Time (m) is the extra time duration (in minutes) committed by a node in the block. A Transaction is a bond transaction from node. Date Time (t) is the date time of the bond transaction performed by a node to become a validator. Stake Value is a bond transaction amount, and Wallet Proof is proof of the transaction from the node’s wallet. The reactivation number is for the validators that were once validators but left their validators responsibility by performing the unjoin mechanism. If that node creates a block for the join mechanism as the validator, it inserts its total number of unjoins as validator counts in the reactivation number in the block. For a new node that first creates a block for the join mechanism as a validator, its reactivation number would be zero. If the old validator wants to rejoin the validator’s responsibility, it must fulfill the complete joining mechanism again to become a validator in the network, except for the validator number. The node uses its old validator number to create a new block for the join mechanism. Figure 5 presents the block structure in which the node is used to create the new join block for the validator’s chain to become a validator in the network.
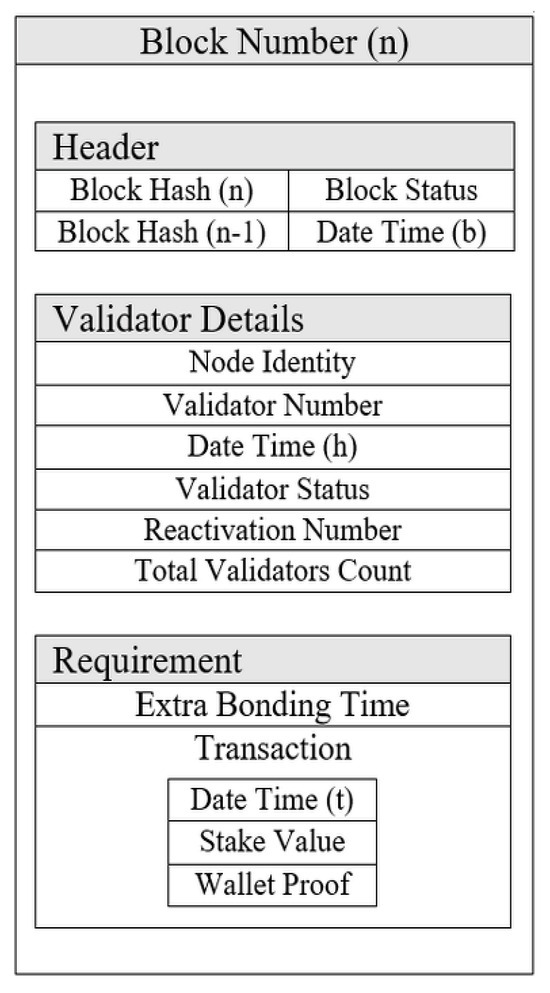
Figure 5.
Block structure of join as validator block for validator’s chain.
After creating a validator block, the validator digitally signs [54] the block by itself and broadcasts the block to all validators/nodes of the network. The validators of the network, after receiving the block, send an acceptance message with a digital signature to the node if the transaction and other information are valid. When a node has received acceptance messages from two-thirds of the total network validators, the node immediately informs the network host by sending join message request 2, The join message request 2 is a combination of a join block and proof of a two-thirds acceptance message for its block for the validator chain. After receiving the valid proof of a two-thirds acceptance message for the valid node block within the join as validator time, the network host attaches the node’s validator block to the validator chain and shares the validator chain ledger with the node.
After the join block is added to the validator chain by the network host, the joining mechanism of a node to become a validator node in the network ends. The node has now become a validator node in the network and can participate in the network as a validator such as in the consensus mechanism for the block creation process of the main chain. The network host generates new parameters for the next node’s parameters request after the completion of the joining mechanism of the current node’s request, which seals the parameters released to this node and updates the total validator count by increments of one in the network for the next nodes.
3.2. The Unjoin Mechanism
When a node wants to leave the validator’s responsibility in the network, it must follow the unjoin mechanism. To start the unjoin mechanism, the validator creates an unjoin message request 1 and sends it to the host and all validators/nodes of the network. The validator may send the unjoin request 1 at any time to the host but the host will only respond to the request after every 20 block creation cycles in the network until all requests are waiting in the unjoin_queue. A network may set any time duration to respond to unjoin requests; in our work, we set a 20-block creation cycle as the time duration. The validator may cancel its request before the host responds because the request becomes permanent after the host’s acknowledgment. The host collects all unjoin requests received from the validators during the last 20 block creation cycles. Before the start of the 21st block creation cycle or after every 20th block creation cycle of the network, the host acknowledges all of the requested validators that sent an unjoin request so that they can start their unjoin process. Once the host has sent an acknowledgment to the unjoin request, the validator cannot participate in any network process as a validator. The network host restricts the validators from participating in the consensus process as block producers or in the election process that had already requested to unjoin, by removing their IDs from the total validators list of the network at the time of sending an acknowledgment of their unjoin request.
After receiving an acknowledgment from the network host, the validators begin completing the first requirement of the unjoin mechanism, which is passed the bonding time duration in the network. The passing of the bonding time of a validator in the network starts with the receiving time of its acknowledgment from the network host. Bonding time is a combination of two types of time: the default time duration for unjoining as a validator from the network and extra bonding time duration that is committed by every validator at the time of becoming a validator in a join as a validator block. The validators must pass the default time duration plus extra bonding time duration in the network to leave their responsibilities as validators. The system has set the default, pre-specified time duration for validators to pass before unjoining the network as validators because the extra bonding time is committed by the validators themselves, so it can be more or less; however, the network requires that the validator remains in the network for longer after the unjoin request so that if they committed any forgery, the network could punish them. Therefore, the default unjoin time of the network should be greater than a 20-block creation cycle time.
Default Unjoin time ≥ 20 block creation cycle
After passing the bonding time in the network, the validator creates an unjoin message request 2 and sends it to the host and other validators to inform them of the completion of their bonding time. Unjoin message request 2 comprises (Bonding time start + total bonding time duration + Bonding time end). If the host is free, it responds to the validator’s request at the same time; otherwise, it maintains the queue to respond to the validator’s request. The host entertains each validator’s request by the receiving time either joining as a validator or unjoining as a validator, the host maintains the queue in FIFO (first in first out) fashion and responds with respect to the message arrival time of the requests. Figure 6 shows the process flow of requests received by the host during the join and unjoin mechanisms.
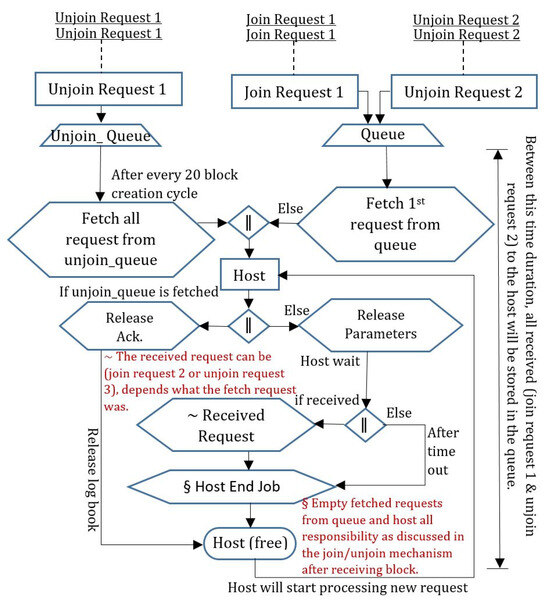
Figure 6.
Data flow diagram of all join/unjoin mechanism requests received by the host.
When receiving an unjoin message request 2, the host checks the validity of the unjoin message request 2. If the message is worthy, the host generates and releases the unjoin block parameters to the validators that completed their bonding time in the network and also broadcasts it to the network. After the releasing parameters were released, the host wait time began. During the host wait time, the host does not release the join/unjoin block parameter to anyone else. The host wait time will be over with the completion of the unjoin-as-validator time or the completion of this unjoin-request process. The parameters for the unjoined block from the host to the validators are as follows:
- 1.
- Block Number (n)
It is the block number issued by the host to the validator to create an unjoined validator block.
- 2.
- Date Time (h)
It is the date and time when the host creates the block number.
- 3.
- Hash (n − 1)
It is the hash of the last block in the validator chain. The final block can be any joined or unjoined validator block. This hash is used as the previous block hash in the next block creation.
- 4.
- Total Validators Count
It is the total validator number of the network.
- 5.
- Bonding Date Time Start
It is the date and time when the host sent an acknowledgment of unjoin message request 1 to the validator to begin passing its bonding time in the network.
- 6.
- Date Time (r2)
This is the received date and time of an unjoin message request 2 to the host from the validator.
- 7.
- Penalty
Penalty contains the total penalty imposed on the validators from the network during their time in the network as validators.
The pre-specified amount of time, called the unjoin-as-validator, has been allocated to the validator that receives parameters from the network to complete an unjoin block creation and obtain two-thirds of the accepted messages for its block from the validators of the network. The unjoin-as-validator time began after the validator received the parameters from the network host. After receiving the parameters from the host, the validator performs the transaction to release its bonded stake from the network and broadcasts it in the network. This is a special transaction because in normal transactions the sender performs the transaction, but in this case the receiver (validator) creates the transaction on behalf of the network host. In this transaction, only dummy values are shown because the network will only release the stake value to the validator after the successful completion of the unjoin mechanism. The special transaction is designed to control forgery in unjoin block creation and improve security. After the transaction, the validator creates an unjoined block. The unjoined block contains the following parameters:
- 1.
- Header
Block Number (n), Block Hash (n), Block Status, Hash (n − 1), Date Time (b).
- 2.
- Validator details
Node Identity, Validator Number, Date Time (h), Validator Status, Closing Number, Penalty, Total Validators Count.
- 3.
- Requirement
Bonding Date Time Start, Default Time Duration for Unjoining, Extra Bonding Time(m), Date Time (r2), Stake Release Transaction, Date Time (t), Stake Value, Wallet Proof.
Where Block Number (n), Date Time (h), Hash (n − 1), Total Validators Count, Bonding Date Time Start, Date Time (r1), Date Time (r2), and Penalty Detail are released by the host to the validator. Block Hash (n) contains the hash of the current block, Block Status shows the block is created for a “unjoin as validator” purpose. Date Time (b) is the date time of unjoin block creation, Node Identity is the wallet identity of the node in the network, Validator Number is the same validator number issued from the host at the time of creating the join validator block, and Validator Status is “inactive” because it is unjoined as a validator block. The Closing Number holds the “total number of unjoin” in the network of this validator, the Default Time Duration for unjoining is set by the network for every unjoin validator, Extra Bonding Time (m) is the committed time in minutes from the validator in the join block, and Stake Release Transaction is the transaction that causes the validator to release its stake from the network. Date Time (t) is the time of the stake release transaction, Stake Value is the bonded stake amount from the validator when it becomes a validator, and Wallet Proof is the proof of the stake release transaction from a node. Figure 7 shows the block structure for the unjoin mechanism that uses the validator to create the unjoin block.
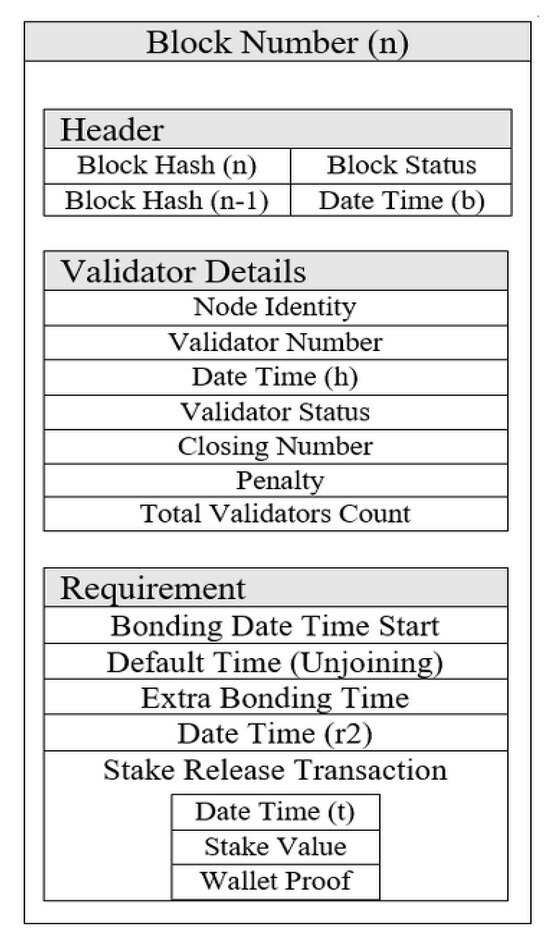
Figure 7.
Block structure of unjoin as validator block for validator’s chain.
After creating the unjoined block, the validator broadcasts this block to the network. If the block is valid, the other validators/nodes send the accepted messages to the sender validators. When the validator receives two-thirds of the accepted messages from the other validators, it informs the host by sending an unjoin message request 3. Unjoin message request 3 comprises (unjoin block and proof of two-thirds of the accepted messages for unjoin block). If the host receives an unjoin message request 3 within the unjoin-as-validator time and unjoin message request 3 (the unjoin block and two-thirds of the accepted messages) is also valid, then the host unjoins the validator from the network and releases its stake value. The host updates the total validator count in the network and uses this block as the previous block for the creation of the next block in the network. The network seals the parameters issued to the validator, which were used to create an unjoined block. The network will not use these parameters again for any other validators in the network. If the specified time has ended and the validator does not complete the unjoin mechanism for any reason, the host discards the validator’s request and releases the parameters to the next validator’s request in the queue.
If the host discards the validator’s request due to a time out, the validator will have to complete the whole process again. The validator may restart the unjoin mechanism by creating a new unjoin message request 1 to the network. Figure 8 shows the complete unjoining mechanism of a validator that leaves the network or becomes a common node in the network.
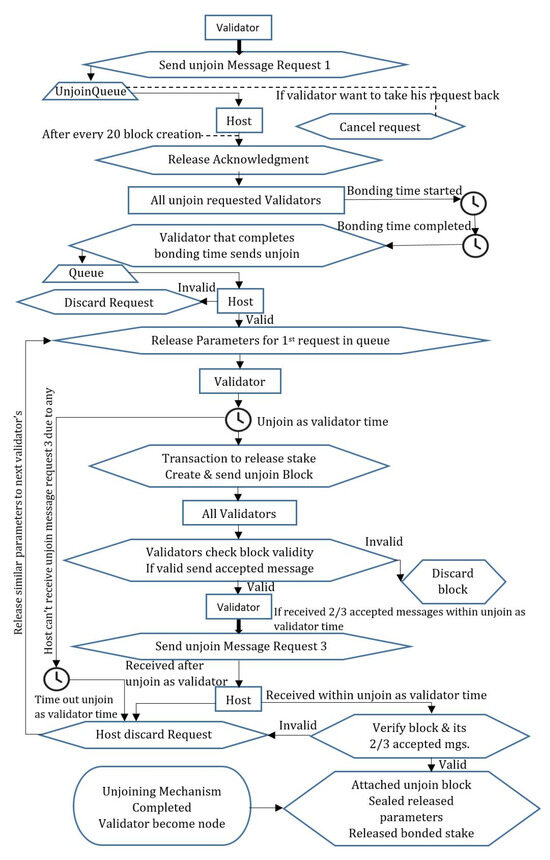
Figure 8.
Unjoining mechanism of a validator in the network.
The network host should work with honesty because the network host plays an important role in the join and unjoin mechanism of the validator, and validators are the main part of the block creation process of the PoS blockchain network, which is why their join and unjoin process is also very important. The network host maintains all of the received join and unjoin requests from the validators to create a log. The request log contains join message requests 1 and 2 and unjoin message requests 1, 2, and 3 of the validators during the last 20-block creation cycle. The network host creates and releases the request log to the entire network after every 20-block creation cycle. The request log is released to the whole nodes of the network. The request log allows the network’s validators to observe the network host’s working process. If any node in the network has any complaint, it can also raise its complaint against the host. If the node has found discrimination from the host for any reason, for example, a node wants to become a validator node and requests the host for the release of parameters for the join block and the node does not receive the acknowledgment of time from the host, the node would see the log of the details showing that the host is not occupied and that its request is also present in the log, it may raise its voice against the host by showing proof of its request. If the node sees the log and the host is occupied by a long queue or its request is missing from the log for any reason, then the node may send its request again to the host.
4. The Proposed System Algorithm
The proposed algorithm is written in the form of an event. To describe an event, an upon rule set is used. An upon rule set works when messages arrive and the associated conditions with upon become true. The algorithm shows the basic process flow of the proposed join and unjoin mechanism for implementation. The events are written based on node-initiated messages. We discussed the algorithm concisely because it has already been briefly discussed in the above sections.
4.1. Explanation
Algorithm 1 represents the complete Sea Shield mechanism. We used this algorithm for the implementation. Algorithm 1 calls the function the join/unjoin mechanism, which is discussed later.
| Algorithm 1 Sea Shield complete mechanism |
| Initialization |
|
4.1.1. Initialization
The starting nine lines are for the algorithm initialization. We have only provided the required initialization to explain the process flow. Phasec represents all of the join/unjoined phases. Node_list shows the list of nodes in the network. The wallet presents all transaction details of all nodes. ValidatorsNodeIDList shows the details of all the active or inactive validator IDs with their corresponding node IDs in the network. CurrentValidatorsList only has active validators of the network. We provide the join_as_validator time, unjoin_as _validator time, default bonding time, and penalty amount to the algorithm because these are the network inputs.
4.1.2. Start Mechanism
Lines 10 to 17 were written for the startup of the process. To start the mechanism, we generate the node list and the wallet list in line 11 and create connections for the network nodes in line 12. Lines 13 to 15 were written to run the join mechanism multiple times. Line 16 executes the unjoin mechanism, and Line 17 resets all parameters for the network.
4.2. Join Mechanism
We divided the join mechanism into three algorithms for better understanding. Algorithm 2 presents the complete join request 1 phase of the join mechanism, Algorithm 3 presents the entire join request 2 phase of the join mechanism, and Algorithm 3 presents the functions used by both of the join mechanism algorithms. Because it is one function, JoinMechansim, we discuss its entirety below; however, we distribute the explanation of Algorithms 2 and 3 for a better understanding. Lines 18 to 83 explain the join mechanism of the node, which is called in line 14. The joint mechanism is expressed in the form of functions. Three functions are written to execute the mechanism: JoinMechansim, CreateJoinBlock, and Discard request. JoinMechansim calls for the other two functions.
| Algorithm 2 Join mechanism (phase ← Join Request 1) |
|
- 1.
- Algorithm 2 Explanation
In lines 19–21, any random node from the network broadcasts join request 1 to the host. In lines 22 to 34, upon receiving a request from the node and if the host is free, the host broadcasts the parameters to the join request node. In lines 35 to 40, upon receiving the parameters from the host, the join mechanism broadcasts the parameters to the join request node. In lines 35 to 40, upon receiving parameters from the host, the join request node first creates a bond transaction and broadcasts it to the whole network. Second, it creates a block by calling the function CreateJoinBlock, and broadcasts it to the network. In lines 41 to 44, upon receiving a valid transaction and block, the network nodes broadcast an accept message to the join request node. In lines 45 to 48, if the join request nodes receive two-thirds of the accept messages, they will send join request 2 to the host.
| Algorithm 3 Join mechanism (phase ← Join Request 2) |
|
- 2.
- Algorithm 3 Explanation
In lines 49–66, upon receiving join request 2 to the host, the host accepts the block if the received request is valid and also reaches within join as its validator time, otherwise the host discards the request by calling the function DiscardRequest. In lines 67 and 68, the host discards the join request and frees itself, and it will only execute if the current process time exceeds the join as the validator time.
- 3.
- Algorithm 4 Explanation
Algorithm 4 contains the body of function CreateJoinBlock, and function DiscardRequest that is used by Algorithms 2 and 3 respectively. In lines 69–79 the join block is created with the digital signature. In lines 80–83 the function discard the request.
| Algorithm 4 Sea Shield join mechanism (functions) |
|
4.3. Unjoin Mechanism
We split the unjoined mechanism into four algorithms to clearly understand its functionality. Algorithm 5 presents the thorough unjoin request 1 phase of the unjoin mechanism, Algorithm 6 describes the complete unjoin request 2 phase of the unjoin mechanism, Algorithm 7 shows the complete process of unjoin request 3 of the unjoin mechanism, and Algorithm 8 describes the functions used by other algorithms of the unjoin mechanism. We describe the function unJoinMechansim sequentially because it is a function. For a clearer understanding, we present the explanation of Algorithms 5, 6, and 7 separately. We have not described Algorithm 8 separately because it contains functions that are called by other unjoin algorithms, and their explanations are already present there.
| Algorithm 5 Unjoin mechanism (phase ← Unjoin Request 1) |
|
- 1.
- Algorithm 5 Explanation
Lines 84–153 present the unjoin mechanism, which is called in line 16. The unjoin mechanism also has three functions: unjoinMechansim, createUnjoinBlock, and DiscardUnjoinRequest. The unjoinMechansim function calls the other two functions in it. In lines 85 to 89, multiple validators send an unjoin request 1 to the network and host. In lines 90–95, the host receives an unjoin request 1 and saves it in the unjoin queue. If the block creation reaches 20, the host releases an acknowledgment to all unjoin request validators and broadcasts the logbook to all networks. In lines 96–99, upon receiving an acknowledgment, the nodes begin passing their bonding time. After completion of the bonding time, the validator sends an unjoin request 2 to the host.
| Algorithm 6 Unjoin mechanism (phase ← Unjoin Request 2) |
|
- 2.
- Algorithm 6 Explanation
In lines 100 to 112, if the host is free, the host releases the unjoin parameters to the first received unjoin request 2. In lines 113–120, having received unjoin parameters from the host, the validator first creates and broadcasts an unjoin bond transaction. Second, the validator creates an unjoin block by calling the function CreateUnJoinBlock from algorithm 8 lines 144 to 150 and broadcasts it to the network. In lines 121 to 129, upon receiving a valid unjoin block and bond transaction, the network nodes send an accept message to the unjoin validator, and if the validator receives a two-thirds accept message, the validator generates an unjoin request 3 to the host.
| Algorithm 7 Unjoin mechanism (phase← Unjoin Request 3) |
|
- 3.
- Algorithm 7 Explanation
In lines 130–141, the unjoin block is accepted by the host if the host receives a valid message request 3 within the unjoin as the validator time; otherwise, the host discards the unjoin process by calling the function DiscardUnjoinRequest from Algorithm 8 lines 151 to 153. In lines 142 and 143, if the host does not receive unjoin request 3 and unjoin as the validator time exceeds, the host discards the unjoin request process and frees itself.
| Algorithm 8 Sea Shield unjoin mechanism (functions) |
|
5. Experiment and Evaluation
As per the literature, we have three generations of blockchains. The first generation includes Bitcoin [16], LiteCoin [55], and others; however, it has its limitations. To cope with first-generation blockchain limitations, the second generation has evolved. It includes Ethereum [12], Tezos [56], EOS [48], and other blockchain platforms. The second generation uses pre-written programmed logic to create and manage their data. The second generation works well; however, when users or transactions increase, a critical performance drop is observed. That is why the third blockchain generation is initiated.
The third generation is called heterogeneous blockchains. The third-generation platforms contain constructors that allow users to create and run their blockchains with expanded options. Heterogeneous networks, such as Cosmos [21], Polkadot [57], and Avalanche [58], create a global network that is more efficient in terms of throughput than previous generations. The platform allows the communication of a specialized blockchain with multiple other blockchain networks as required. The validator chain may support a POS-based consensus.
- 1.
- Implementation
We designed an asynchronous heterogeneous network model [59] for implementation. Asynchronous means that there is no assumption of timing. Any node can generate a join or unjoin request message at any time in the network. The system is based on Byzantine fault tolerance; the network may live under malicious nodes. To evaluate the mechanism, we implemented a prototype on C#. All cryptographic functions are generated using standard cryptography algorithms, such as (RSA [60] used to create digital signatures, encryption, decryption, and key generation) and the SHA-256 algorithm [24], for entirely hashing operations, where every single node is connected to two other nodes in the system for message propagation.
We use exponential distribution [61] to calculate the propagation delay in our broadcast. Algorithm 9 presents the function ExponentialDis for calculating the propagation delay. We input a maximum value of 1.5 and a minimum value of 0 to the function to obtain a new value for a delay during each broadcasting. We used 100 samples to calculate the average mean propagation delay. The average mean propagation delay used in broadcasting was 0.2 milliseconds. We set (join and unjoin as validator) time as (total_number_of_node + 200) seconds for the test runs.
| Algorithm 9 Calculation for propagation delay |
|
- 1.1.
- System Configuration
Sea shield is based on a PoS-Pbft design that does not require heavy machinery to run. Table 2 shows the system configuration of the machine that is used to execute the simulation environment.

Table 2.
System configuration used for simulator implementation.
- 1.2.
- Network Size
Network size generally refers to the number of nodes attached in the system. We used a number of nodes in the range of 0 to 150 for the test run of the simulator for collecting results.
- 1.3.
- Minimum Node Requirement
Our simulation operates at a minimum of five nodes. The network must have five or more nodes in the system to execute the block creation process because to finalize the block, the join/unjoin request sender node requires two-thirds of the total nodes’ accepted messages.
- 1.4.
- Number of Transaction
The block will contain only one transaction, either join or unjoin. The network may set the block size as per their requirement. We generated random transactions for our simulation.
- 1.5.
- Node Behavior
We evaluated and noted the behavior of our simulator with normal nodes under normal conditions and with malicious node activity under different conditions.
- 2.
- Evaluation
The simulator operates under 35 different conditions to analyze the join and unjoin mechanisms and their security. Below, we discuss the conditions in summary (join/unjoined together):
- 1.
- All nodes of the network do not receive join/unjoin parameters from the network or the host does not send join/unjoin parameters to all nodes.
Result: The node that did not receive the join/unjoin parameters from the host discards the block received from the node. To accept a block, a node must receive parameters from the host before receiving the block from the node. The node matches the parameters sent by the host to the network from block parameters. Therefore, the node cannot manipulate the block parameters.
- 2.
- The nodes receive a forged transaction stake value in the transaction with the correct wallet proof in the network. Alternatively, we forged stake values with the wrong wallet proof.
Result: Every node verifies the transaction from its wallet by using a zero-knowledge proof [62]. If the transaction is not valid, the node will reject the transaction.
- 3.
- Transaction received with backdate or time; change bond transaction creation time.
Result: Every node checks whether the bond creation time is backdated/time or when the node rejects the transaction.
- 4.
- The node submitted a late join request 2 or unjoin request 3 to the network/administrator/host.
Result: The host rejects the request of the node if the allocated “join/unjoin as validator time” exceeds.
- 5.
- Nodes received a bond stake value that is different in the block from a transaction.
Result: The bond stake value in the transaction and block should be similar; nodes that find different values will reject the block.
- 6.
- The host received join request 2 or unjoin request 3 from a node with all the required proof within the allocated “join/unjoin as validator time”, although the host does not receive a block or transaction from the node during block creation.
Result: The host validates the block, and if everything is correct, the host updates the ledger.
- 7.
- Only the host received the correct block, and all nodes received a forged block, a block having manipulated the bond stake value.
Result: The host validates and accepts the block, but all other nodes reject the block, and the block creator does not obtain a two-thirds accepted message for the block. The node will not provide an accepted message proof to the host. After allocating the join/unjoin time as the validator, the host rejects the request and releases similar parameters for the next request.
- 8.
- Nodes received a block with changed extra bond time.
Result: Nodes received an extra bond time with a transaction message as well, and they compared the extra bond time of transactions and blocks. If the block does not contain a similar time commitment, it is rejected by the node. The node validates the block by comparing the digital signature with the block hash. If the block matches the digital signature, it is considered unforged and created by the block creator. Under this condition, if nodes find different extra bonding times in the block from a verified transaction, the node may report a forgery complaint against the block creator to create a forged block.
- 9.
- A transaction with extra bonding time is not received by all nodes of the network for any reason.
Result: Nodes that do not receive transactions reject the block, if two-thirds of the nodes receive the transaction and give an accepted message to this block, then the block is accepted. In this condition, the nodes that reject the block will ask the host to send the last block if they remove the block from their ledger, because the ledger is sequential, and the next block they receive from the network contains a block number (n + 2).
- 10.
- The host does not receive two-thirds proof or less than two-thirds proof in join message request 2 or in unjoin message request 3 from the nodes.
Result: If the received join request 2 or unjoin request 3 from the node does not contain two-thirds proof, the host will reject the request and will release similar parameters to the next join/unjoin request.
- 11.
- The request logbook is not sent to all nodes, or all nodes do not receive a request logbook from the host.
Result: After every 20-block creation cycle, the host releases an acknowledgment of all unjoin request and then releases a request logbook in the network that contains all received requests between the last 20-block creation cycle. If the node does not receive the request logbook from the host, it can request the host to send the request logbook. The request logbook for nodes is very important because it is needed for the verification of unjoin transactions and blocks. When a node receives an unjoined transaction from a validator, it first verifies its ID in the request log from the host because before an unjoin transaction the validator must be acknowledged by the host on request 1. The transaction will only be accepted when a recent logbook from the host contains an unjoin request 1 from the validator to the host.
- 12.
- The validator sends an unjoin message request 2 to the host without completing the bonding time.
Result: If the host receives an unjoin message request 2 from the validator, it must verify the request before accepting it. The host accepts the unjoin message request 2 if the committed bonding time from the node has been completed in the network after receiving the acknowledgment from the host on request 1. If the validator has passed that time in the network, then unjoin request 2 is accepted and proceeded by the host; otherwise, the request is rejected and discarded by the host and the validator needs to restart from request 1 if it still wants to leave the validator responsibility in the network.
- 13.
- Validator sends cancellation request of its unjoin message 1 to the host.
Result: The host cancels the unjoin message request 1 if the acknowledgment has not been sent by the host. Once the host releases acknowledgment on unjoin message request 1, the unjoin request cannot be reverted or canceled.
- 14.
- Block received with manipulated closing number, penalty amount, bonding time, unjoin request 1 date time or unjoin request 2 date time.
Result: The node verifies all of these details in the block from the unjoined parameters received from the host. The node may also confirm the closing number and bonding time from the validator chain and unjoin request1 date time from the request log. If the data do not match, the block is rejected by the node. The node verifies the block creator by verifying the digital signature of the block. If the block hash and digital signature match the node, this may raise complaints against the block creator to create a forged block; otherwise, it is considered a network attack, and the block creator is not responsible for the manipulated data in the block.
- 15.
- Node sends an unjoin transaction or block without completing its bonding time.
Result: When the node receives an unjoined transaction or block from the validator, it first verifies its completion of the bonding time. The start of bonding time is presented in the request log by subtracting the current time. If the required bonding time is not completed, the node rejects the block or transaction.
- 16.
- Ultimately block rejection.
There are two reasons:
Result: If the node receives a block that contains the transaction and for any reason, the transaction is already rejected by the node, the received block will also be rejected by the node.
Result: Every node that receives the block first verifies the correctness of the block by comparing the block hash with a digital signature. If the block hash does not match the digital signature the block is rejected.
6. Discussion
6.1. Comparative Analysis of the Inside Characteristics of the Consensus
The comparative analysis of consensus with other blockchains is a good source for understanding the internal features of a consensus. Therefore, we performed a comparative analysis using a blockchain trilemma to review the internal characteristics of the Sea Shield. The blockchain trilemma is a tradeoff between three properties: security, scalability, and decentralization of blockchain technology. In the literature, subcategories are available for the blockchain trilemma. Stefanoz et al. [63] presented the presto framework in relation to the blockchain trilemma through which consensus can be compared and understood. This framework is based on optimality, stability, efficiency, robustness, and persistence. Figure 9 shows the framework in relation to blockchain trilemma and its subcategories for Sea Shield comparison. We chose the sub-categories of the presto framework related to our consensus. We described (1) Optimality as Liveness and Safety, (2) Robustness as Fault Tolerance and Resilience to Attack, (3) Stability as Block Proposer, Transaction Pool, Incentive, Fairness, and Decentralization, (4) Persistence as Fork Control and Governance, and (5) Efficiency as Communication Message Overhead, and Throughput.
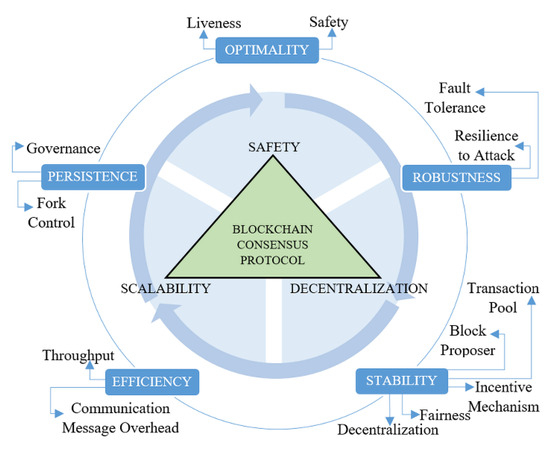
Figure 9.
Comparison framework in relation to blockchain trilemma with its subcategories.
- 1.
- OPTIMALITY
- Liveness:
Some consensus mechanisms such as PBFT [10] use the concept of Byzantine fault tolerance (BFT) to achieve liveness. Similarly, we also use the concept of Byzantine fault tolerance to create join and unjoin blocks, because the design ensures the liveness of the network. In this design, the network node reaches a consensus even in the presence of malicious actors. The consensus requires a minimum of five nodes to run. Because to create a block, the node requires two-thirds of the total network nodes’ response. The Sea- Shield also uses the host concept. To maintain the liveness of the network, the host must be responsive and perform adequately. Otherwise, the liveness of the network may come in a risky state.
- Safety:
We have applied blockchain technology to keep a record of the validator’s information secure; however, security issues are present in both traditional computing environments and blockchain. The same attack is possible in both environments but in a different manner. A few attacks are discussed below:
1. Denial of service: In a traditional computing environment when a system cannot respond to the user due to received requests higher than the target or its capacity, this is called a denial of service attack. In the blockchain, when more transactions are produced and submitted by users to crash the blockchain network, this is considered a denial of service (DoS) attack. In Sea Shield, this attack is not possible because a transaction is performed after receiving the host parameters, and the host does not release multiple parameters at similar times. Even now, if the user or multiple users create an excessive transaction it would be of no use because the only one that uses this transaction in the block is itself and if multiple forged blocks are created without host parameters it can slow down the process; however, later the system can recover from it because every block has its digital signature and nodes to verify every block by its signature and host parameters, so if such situations happen, the network nodes will reject all forged blocks and a penalty will be applied on those nodes.
2. Intentional Misuse: Both traditional and blockchain environments encounter this type of attack. In traditional networks, internal users or clients attack the system intentionally to obtain benefits. In blockchain, this type of attack occurs as in Bitcoin [16]. If more than 50% of the network processing power is controlled by one entity or a single group, it can weaken the network by creating and obtaining incentives for their block from the network. This attack can also weaken the Sea Shield if more than two-thirds of nodes of the network become faulty and accept blocks with forged transactions. However, if any of the nodes or host finds forgery, the block can be rejected because the transaction has a wallet proof, and the wallet proof can be verified by anyone through zero-knowledge proof in the network.
3. Endpoint Security: Traditional infrastructure and blockchain environments are quite different, but both face endpoint security issues. In traditional infrastructure, endpoint security is the process of securing all the points that are connected to the network, such as user devices, servers, tablets, and virtual environments, from malware, spyware, and computer viruses in many ways, such as using antivirus or more. In a blockchain environment, nodes are considered endpoints because they interact with the blockchain environment to input data such as creating transactions and achieving consensus. Like other blockchains, the Sea Shield also reduces security issues by using public key cryptography and decentralization. Nodes use keys to digitally sign transactions and blocks, which is why the security of the keys should be high. Keys can be stolen and used to perform malicious activities in the network; therefore, keys should not be in emails, computers, or inside files. We suppose that cloud protection is a good solution for securing keys. There are many cloud security services available in the web market for eliminating endpoint security risks, such as CASB products [64].
- 2.
- ROBUSTNESS
- Fault Tolerance:
There are many blockchains in the literature, but all cannot achieve consensus in the presence of malicious nodes. To work with faulty nodes, the BFT design is considered the best, which is why several algorithms use the BFT design to obtain block finalization, such as Algorand [43] and PBFT [10]. The Sea Shield is based on the BFT design. In the BFT design, positive response of two-thirds of the nodes can lead to achieving consensus in the network. In the Sea Shield, to confirm the join and unjoin blocks, the node needs to receive two-thirds acceptance from the other nodes of the network, if the remaining one-third of the nodes have become faulty and do not respond, even so a block will be created. The total fault tolerance of the Sea Shield is 33%. The network may work under one-third of faulty nodes.
- Resilience to Attack:
In this mechanism, there is the concept of a penalty for nodes that are found guilty by the network. If forgery is reported against the node for creating a forged join block and the network finds it guilty, then the network can punish the node by imposing a penalty on it or removing it from the network. If the validator creates a forged unjoin block and the network finds it, then the host can impose a penalty, which can be deducted from the stake amount of the validator. Attacking the Sea Shield blockchain is difficult because, like other blockchains like Bitcoin [16], it also uses different types of cryptography, such as public-key cryptography, zero-knowledge proof, and hash functions. The wallet proof is also cryptographically hashed; we used a zero-knowledge proof to verify the transaction.
- 3.
- STABILITY
- Block Proposer:
PBFT or other blockchain algorithms such as Tendermint [11] require a block proposer to create a block for the blockchain. Sea Shield does not require an additional block proposer selection algorithm or round to select a block proposer for the validator chain. The nodes or validators of the network itself create a block according to their requirements. In other blockchains, the finalization of transactions is pending, which is why continuous block production is necessary for the stability of the network. However, the Sea Shield is a special purpose blockchain and it does not require continuous block production because there are no extra transactions.
- Transaction Pool:
Sea Shield does not require a transaction pool like other Cosmos [21] because there are no additional transactions in the block; the only transaction that is present in the block is created by the block creator itself.
- Incentive Mechanism:
1. Transaction Fees: In other blockchains, such as Bitcoin [16], anyone generates a transaction and attaches fees to the transaction to make it more attractive to the block creator. Mostly, the block creator takes transactions into their blocks according to the fees attached to them. In Sea Shield, there is no transaction fee because the block creators are the ones that generate transactions and create a block with its transaction.
2. Block Proposer Reward: To maintain the stability of the network, almost every blockchain provides incentives to block proposers to obtain attention of nodes toward the consensus process. Sea Shield does not need to incentivize block proposers because if nodes want to obtain a block proposer incentive of the main blockchain, they have to become validators first, and to become a validator they need to create a join block, or if they are required to take their stake back, they have to create an unjoin block for itself.
3. Block Validation Reward: To further stabilize the network, the Sea shield blockchain network provides an incentive to the first two-third nodes that validate the join/unjoin block and send an accept message to the block creator. To customize similarly to other blockchains DPoS [20], the Sea Shield validator may share its block reward for creating a block in the main blockchain with the nodes that give it an accept message to its join block. The Sea Shield incentive mechanism can be customized according to the needs of the main chain.
- Fairness:
To achieve fairness, we broadcast the request logbook of the host so that all nodes know about the operation of the host. Join blocks, unjoin blocks, and accept messages are digitally signed by creators using public-key cryptography. The digital signature provides authentication, integrity, and nonrepudiation of the received blocks and messages. The nodes have an open right to accept or reject the created block for the validator chain, as in other blockchains like Bitcoin [16]. Unjoin request 1, join parameters, and unjoin parameters are broadcast to the entire network so that every node knows the status of the validator’s node. Sea Shield observes complete transparency; data stored in the blockchain can be accessible to all and its integrity can be verified.
- Decentralization:
The Sea Shield design is ideal for a public permission blockchain network. This type of network is typically developed mostly within one industry or between several companies that have mutually agreed upon it, such as Quorum [65]. In Sea Shield, every node is equally privileged; we have a concept of the host in the mechanism, any node or software or moderator can be the host and fulfill the responsibility. Host work is open to everyone in the network. The host activity is monitored by nodes and if the host does any forgery network, its members may change it. The host is only responsible for releasing join/unjoin parameters, but the decision of the new block is taken by the nodes of the network.
- 4.
- PERSISTENCE
- Fork Control:
The validator chain retains all the staking information of a validator, and we have already discussed the importance of this data in the blockchain network in Section 2. Sea Shield does not allow a fork in the validator chain as in other blockchains like Bitcoin [16] because we cannot lose any validator’s information due to the fork. The forking issue has already been discussed in other blockchain networks in Section 2. Every accepted validator’s information as a block must be part of everyone in the validator chain. The replicated ledger should be similar to a network. To control for the forking issue, we compromise on time because it is not a main chain. We prioritize linearity and security over high throughput for this chain. We slowed down the consensus process by introducing a wait time for the host. We also do not want a quick process for the join/unjoin validator mechanism because of security issues. Our main focus is to keep our blockchain ledger linear and secure for everyone. Below are the two situations that may appear in the network and how the validator chain deals with these conditions:
Condition 1: If the validators of the network receive multiple blocks with a similar block number for the validator chain, the validators will discard all similar blocks and only keep a block that has the latest Date Time (h) in between all similar blocks for the validator chain. The latest Date Time (h) shows that the host released the parameters to the next request and discarded the previously released request. Therefore, the block created based on the previously dated time (h) parameters should also be discarded.
Reason: This occurs when the network host releases parameters to the node or validators upon its request to create a block for the validator chain. By using these parameters, nodes or validators create the block and broadcast it to the network but the node/validator cannot receive a two-thirds acceptance message for the block or, for any reason, cannot complete the join/unjoin mechanism within the join/unjoin as the validator time. In this condition, the network host discards the node’s request and re-issues these parameters, except the Date Time (h), to the next request in the queue. The next requested node/validator creates a block using these parameters and broadcasts it to the network.
Condition 2: If a validator directly receives, for example, block (4) after block (2), as shown in Figure 10, this means that block (3) is missing, and the validator does not receive block (3) for the validator chain. The validator must ask block (3) from the network to maintain its validator chain ledger.
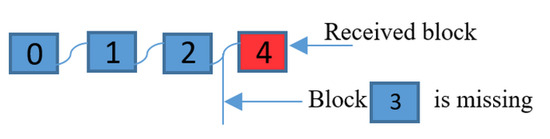
Figure 10.
Validator chain with missing block.
Reason: The blocks are created using a sequential block number from the network host. The network host does not generate block number four without creating block number three. As discussed above, the network host repeatedly releases similar parameters to the nodes until any node creates and finalizes a block with the network’s host-released parameters.
- Governance:
We suppose that open governance or off-chain governance would be suitable for the Sea Shield. There are several governance models in the literature [66]. In open governance, network members choose the team by mutual concern, and the team sets the rules for the network. In off-chain governance, decisions are not made in a traditional formal format. The stakeholders use many ways to communicate, such as social media, conferences, and events, to decide on the new rule set. The Sea Shield implementer may need to set rules for join as validator time, unjoin as validator time, default bonding time, penalty amount, and incentive amount.
- 5.
- EFFICIENCY
- Communication Message Overhead:
1. Join Mechanism: Sea Shield used the concept of PBFT for block creation and finalization. The communication overhead of the PBFT algorithm is discussed in Section 2. The PBFT consensus algorithm has quadratic message complexity. The message complexity of the Sea Shield join mechanism is O(N2). In terms of the joining node, the total required communication message in the join mechanism sent and received by the node is ((5 + 2N) + 2N), where N represents the message broadcast to all networks in which 5 + 2N is required and 2N represents extra layers for security. A total of four messages are received from others while ((3 + 1N) + (1N)) is sent by the join node, in which (3 + 1N) is required and 1N is an extra layer for security. There are two required overall network broadcasting messages, one from the join request node to all network nodes, and one from all network nodes to the join request node to complete the joining mechanism. Figure 11 shows two extra layers for security, and the join mechanism can be completed without broadcasting these two messages. We apply these two broadcasts to improve the overall consensus mechanism security. The host sends join parameters to all network nodes because the network nodes compare the received join parameters from the host to the join block. Except for the date parameter, all join parameters are also available in the last block of the validator chain, and the nodes also need to be verified. The join request node broadcasts bond transactions to all network nodes, although a similar transaction is present in the join block. We applied these layers to reduce the security risks. The nodes verify the transaction from the wallet proof and then verify the block transaction to its already received verified transaction. It is also possible that the join request node directly sends a block with the transaction, and all network nodes verify the transaction from the wallet proof. This is a customizable use case, and both extra layers can be removed according to the network requirements. This is mostly dependent on the data sensitivity of the main chain.

Figure 11.
Communication message overhead diagram of join mechanism.
2. Unjoin Mechanism: The message complexity of the Sea shield unjoin mechanism is O(N2). In relation to the unjoin validator node, the required total communication message in the unjoin mechanism is ((7 + 3N) + 3N), where N represents the total message broadcast, in which (7 + 3N) is required and +3N is an extra layer to increase security. A total of four messages are received from others to unjoin the validator, while ((4 + 1N) + 2N) is sent by the unjoin request validator, in which (4 + 1N) is required and 2N is an extra layer for to increase safety. There are three required messages that should be broadcast to the whole network, such as request logbook from the host, block from unjoin request validator, and accept messages from all network nodes. In Figure 12, there are three extra layers for security shown. These layers were applied to improve the security of the unjoined mechanism. The purpose of the unjoin parameters from the host and unjoin transaction from the unjoin request validator broadcasted to the whole network is the same as the join mechanism, and we have already discussed this. The unjoin request node broadcasts unjoin request 1 to all network nodes so that everyone in the network knows that it will soon leave the network. The network node requires these details to verify the unjoin transaction because unjoin request 1 must be received before receiving the unjoin transaction. This broadcasting can be omitted because an unjoin request 1 of the node is also present in the host request logbook, and the host already releases this request book to the entire network after acknowledging the unjoin received requests. We discussed five extra layers of communication messages overhead in the Sea Shield. The Sea Shield user may remove these extra layers, according to the required safety level. We applied these layers to ensure the security of the Sea Shield because the main chain can improve itself in terms of throughput by using its secure mechanism.
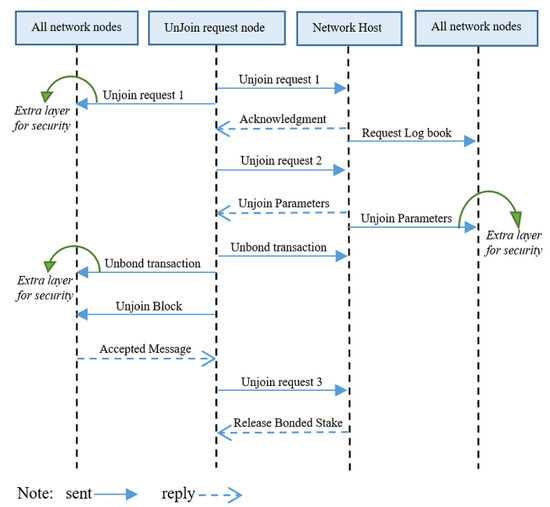
Figure 12.
Communication message overhead diagram of unjoin mechanism.
- Throughput:
We have already discussed the block creation process of the join and unjoin mechanisms. Based on our simulation results, the average join block creation time is 3.4 s when the number of nodes is five; likewise, the average block creation time of an unjoin block is 12.1 s when the number of nodes is 20. We tested unjoin block creation with a minimum of 20 nodes because we discussed that a validator can unjoin itself after a 20-block creation cycle in the network. The time of block creation gradually increased with an increase in the number of nodes in the network. Figure 13 and Figure 14 show the block creation times of the joined and unjoined block, respectively.
Figure 13.
The Sea Shield average join block creation time with respect to the number of nodes.
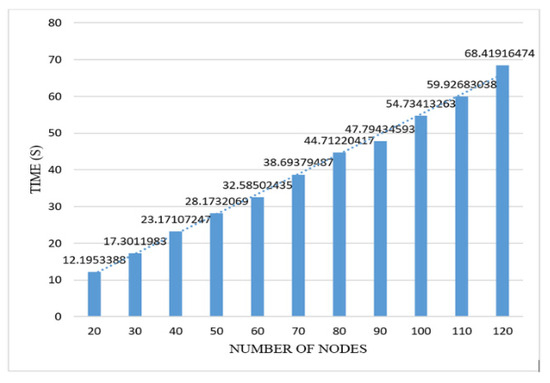
Figure 14.
The Sea Shield average unjoin block creation time with respect to the number of nodes.
We calculated the confidence level considering an alpha value of 95%. Considering the confidence interval values, the results are ensuring that the 95% of samples are in the range from 3.43571127 ± 0.215138962 for join block creation when the number of nodes is five to 12.1953388 ± 0.326131099 for unjoin block creation when the number of nodes is twenty and so on. Figure 15 and Figure 16 show the block creation time with the error bar of the joined and unjoined block, respectively.
Figure 15.
The Sea Shield average join block creation time with error bar.
Figure 16.
The Sea Shield average unjoin block creation time with error bar.
The average block creation time of the Sea Shield is 11.7 s on 20 nodes. Figure 17 shows a comparative analysis between the average join block creation time, average unjoin block creation time, and average block creation time. We observed that the average block creation time increases with an increase in the number of nodes in the network.
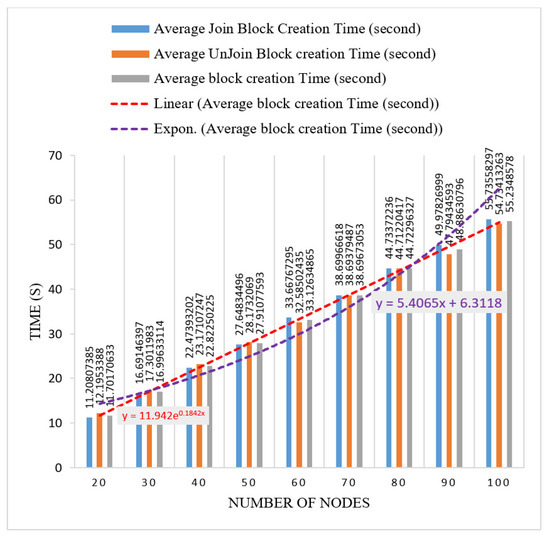
Figure 17.
The Sea Shield average block creation time compared to join and unjoin block creation time with respect to number of nodes.
We did not control the node number/validator number in our consensus because of security and decentralization; who is becoming a validator and leaving its responsibility as a validator in the network should be known by everyone in the network, which is why they all respond to block creation. Blockchain technology is used by different industries according to their needs, if they want to reduce or fix the block creation time, they can modify the mechanism according to their data sensitivity. The network can reduce or fix the total node number using the aging technique to control the time increment of block creation due to increasing node numbers. A group of two-thirds of the most senior nodes in the network will respond to the join and unjoin blocks, which will reduce the communication overhead and block creation time of the mechanism, and the final created block will be broadcasted to the entire network. The network determines the time duration for the node to become a senior node in the network.
We discussed an extra layer of security in the communication message overhead. We analyzed the effect of the extra broadcasting layer on block creation time. In join block creation, the host broadcasts the join parameters to all nodes, and the join request node broadcasts bond transactions to all nodes. We removed these extra layers and noted their effect on the join block creation time.
We observed a decrease of 0.00432474 s time duration in the join block creation time without broadcasting join parameters by the host to all when the system has five nodes and a decrease of 0.00088374 s time duration in the join block creation time without broadcasting bond transactions by joining the request node to all five nodes.
Figure 18 shows a comparison between the average join block creation time when the host does not send join parameters to all and when the join request node does not send bond transactions to all with the average join block creation time. We removed the extra layers of security and observed a decrease in time; the total decrease in time was 0.00520848 s in the average join block creation on five nodes. Figure 19 shows a comparison between the average join block creation time and the join block creation time without broadcasting both extra layers of security. Similarly, we observed the unjoined block creation time without an extra layer for security. We have removed the broadcasting unjoin parameters by the host to all in unjoin block creation, and a decrease of 0.09326934 s was observed while the number of nodes in the system was 30. We also removed broadcasting of unjoin bond transactions to all by a node in unjoin block creation and a decrease of 0.07465962 s was observed while the number of nodes in the system was 30. We also removed the broadcasting of unjoin bond transactions to all by a node in unjoin block creation, and a decrease of 0.07465962 s was observed, while the number of nodes was 30.
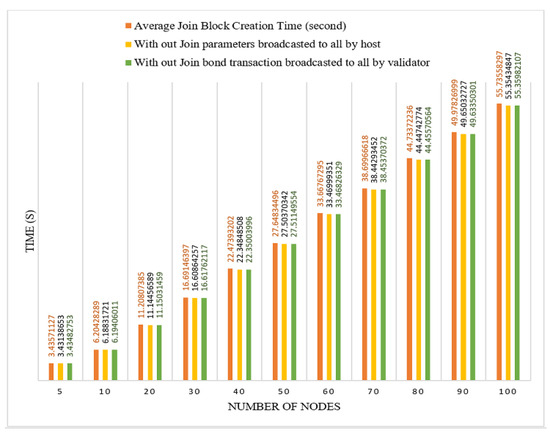
Figure 18.
The Sea Shield average join block creation time compared with the average join block creation time without broadcasting join parameters to all by host and the average join block creation time without broadcasting bond transaction to all by join node with respect to number of nodes.
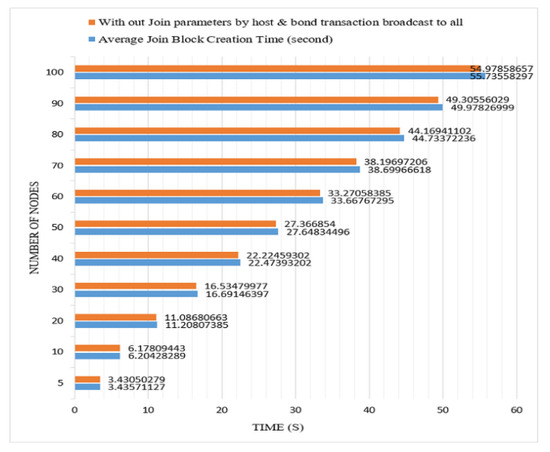
Figure 19.
The Sea Shield average join block creation time compared with the average join block creation time without broadcasting join parameters by the host to all and without broadcasting bond transaction to all by join node with respect to number of nodes.
Figure 20 shows the comparison between three unjoin block creation times, unjoin block creation time without broadcasting unjoin request 1, unjoin block creation time without broadcasting unjoin bond transactions, and broadcasting unjoin parameters by the host. After removing all extra layers of broadcasting in unjoin block creation, we observed the total time taken for average unjoin block creation was 17.13 s on 30 nodes. Figure 21 shows a comparison between the average unjoined block creation time and the unjoined block creation time without any extra broadcasting layers.
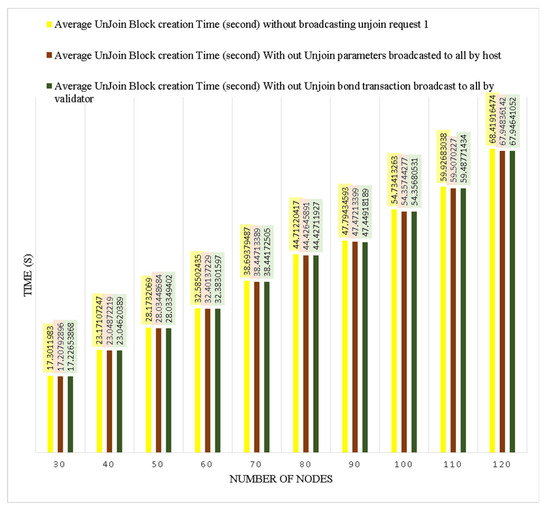
Figure 20.
The Sea Shield average unjoin block creation time without broadcasting unjoin request 1 compared with the average unjoin block creation time without broadcasting unjoin parameters by host to all, and without broadcasting unjoin bond transaction to all by unjoin request node with respect to number of nodes.
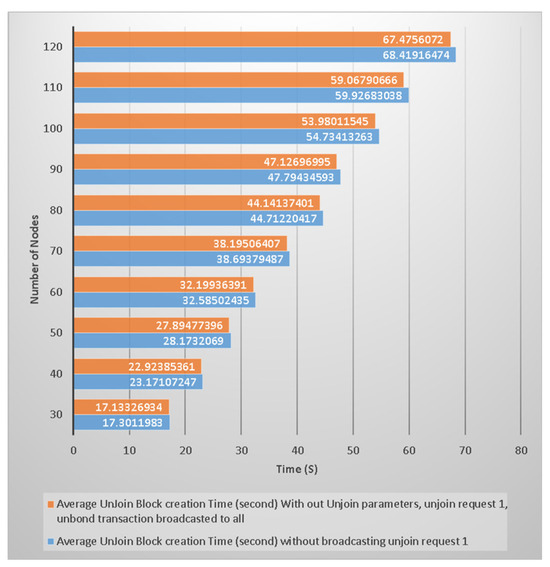
Figure 21.
The Sea Shield average unjoin block creation time without broadcasting unjoin request 1 compared with the average unjoin block creation time without broadcasting unjoin parameters by the host to all and without broadcasting unjoin bond transaction to all by unjoin request node and unjoin request 1 by node with respect to number of nodes.
The Sea Shield block creation was based on the BFT concept. We compared the Sea Shield block creation time (with all security layers) with the PBFT-based consensus using a simulation. The block creation time of other PBFT-based consensus on simulation was affected by the number of transactions in the block; Figure 22 shows that PBFT consensus block creation time increases with the increment of transactions in the block. However, the Sea Shield block creation time was not affected by the number of transactions in the block because the Sea Shield does not contain extra transaction numbers in the block.
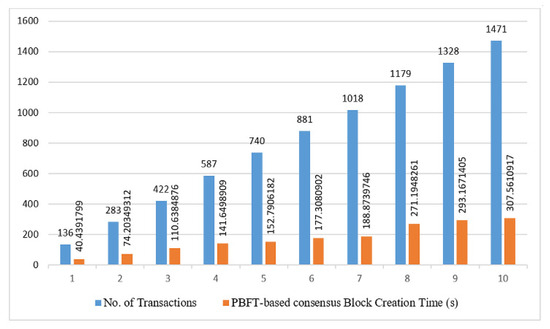
Figure 22.
The PBFT-based consensus block creation time with different numbers of transactions.
We developed a simulation environment for the Sea Shield with two numbers of connections, where every node is connected to two or more nodes to send or receive messages. We also observed that the number of connections affects the total block creation time of PBFT consensus during simulation. We compared the PBFT-based consensus with two connections and the PBFT-based consensus with connected to all other nodes. Figure 23 shows the block creation time of PBFT-based consensus with a different number of connections. The Sea Shield took 11.70170633 s to create an average block on 20 nodes with two connections while other PBFT-based consensus took 0.302378774 s with two connections and 3.014170098 s when connected to all on 20 nodes. The Sea Shield took a little more time in seconds than the other PBFT-based consensus.
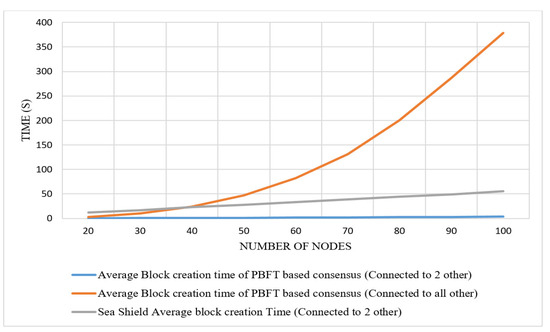
Figure 23.
The comparison of Sea Shield average block creation with other PBFT-based consensus.
6.2. Comparative Analysis with Another PBft-Based Consensus
We have discussed the internal characteristics of Sea Shield in terms of security, decentralization, and scalability. Table 3 presents the comparative analysis of the Sea Shield with another PBFT-based consensus. The internal characteristics are almost the same as those of the PBFT-based consensus, except for the transaction verification speed, block creation speed, and incentive mechanism.

Table 3.
Comparative analysis of Sea Shield with another Pbft-based consensus.
- Impact on another blockchain network upon using Sea Shield:
Storage: Every network uses some traditional storage for saving the nodes staking information. We introduced Sea Shield, which used blockchain technology rather than using a traditional computing environment to store information. There is no additional storage required for using Sea Shield in the network.
Incentive Mechanism: Every blockchain needs an incentive mechanism to stabilize the network. We have seen in the incentive mechanism that there is no need for a block reward in the Sea Shield. There will be no additional pressure on the network to use Sea Shield in terms of an incentive mechanism.
Computation: The design of the Sea Shield is based on PoS and PBFT. There is no need for additional computation and heavy machinery to run Sea Shield. However, network latency may be affected due to using an additional validator chain.
7. Conclusions
We present Sea Shield, a special purpose consensus to save the node’s information in a validator chain, without forking, when a node becomes a validator/stakeholder and when the validator leaves its responsibility in a PoS-based blockchain network. The design of the consensus is to ensure the security of the overall blockchain. The Sea Shield can be customized and aligned with any current PoS-based blockchain. We compromise on time over security for the Sea Shield because we want a validator to go through a long procedure to join and unjoin itself so that the main blockchain security will not be compromised.
7.1. Limitations
Sea Shield can handle any number of users; however, the design of Sea Shield is ideal when the number of users is finite because it uses the concept of host wait. Therefore, if the number of requests becomes very high, it can collude the system. To maintain the liveness of the system, the host must be active and responsive.
7.2. Future Work
The presented work can be improved in the future in terms of scalability. In the future, we will develop an improved blockchain consensus for the main chain to create and finalize blocks and use Sea Shield to improve its overall security.
Author Contributions
Writing—original draft, S.N.; Supervision, S.U.-J.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was partly supported by Institute of Information & communications Technology Planning & Evaluation (IITP) grant funded by the Korea government (MSIT) (No.RS-2022-00155885, Artificial Intelligence Convergence Innovation Human Resources Development (Hanyang University ERICA)) and the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (NRF-2023R1A2C1006390).
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare no conflicts of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
References
- Yuan, Y.; Wang, F.-Y. Blockchain and cryptocurrencies: Model, techniques, and applications. IEEE Trans. Syst. Man Cybern. Syst. 2018, 48, 1421–1428. [Google Scholar] [CrossRef]
- Menon, S.; Jain, K. Blockchain technology for transparency in agri-food supply chain: Use cases, limitations, and future directions. IEEE Trans. Eng. Manag. 2021, 71, 106–120. [Google Scholar] [CrossRef]
- Hjálmarsson, F.Þ.; Hreiðarsson, G.K.; Hamdaqa, M.; Hjálmtýsson, G. Blockchain-based e-voting system. In Proceedings of the 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 2–7 July 2018; pp. 983–986. [Google Scholar]
- Snegireva, D.A. Blockchain System Prototype for the Tasks of Metallurgical and Machine-Building Enterprises. In Proceedings of the 2021 International Conference on Quality Management, Transport and Information Security, Information Technologies (IT&QM&IS), Yaroslavl, Russia, 6–10 September 2021; pp. 106–111. [Google Scholar]
- Chen, N.; Cho, D.S.-Y. A blockchain based autonomous decentralized online social network. In Proceedings of the 2021 IEEE International Conference on Consumer Electronics and Computer Engineering (ICCECE), Guangzhou, China, 15–17 January 2021; pp. 186–190. [Google Scholar]
- Theodouli, A.; Arakliotis, S.; Moschou, K.; Votis, K.; Tzovaras, D. On the design of a blockchain-based system to facilitate healthcare data sharing. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 1374–1379. [Google Scholar]
- Xu, M.; Zou, Z.; Cheng, Y.; Hu, Q.; Yu, D.; Cheng, X. SPDL: Blockchain-secured and Privacy-preserving Decentralized Learning. arXiv 2022, arXiv:2201.01989. [Google Scholar]
- Kara, M.; Laouid, A.; Bounceur, A.; Lalem, F.; AlShaikh, M.; Kebache, R.; Sayah, Z. A Novel Delegated Proof of Work Consensus Protocol. In Proceedings of the 2021 International Conference on Artificial Intelligence for Cyber Security Systems and Privacy (AI-CSP), El Oued, Algeria, 20–21 November 2021; pp. 1–7. [Google Scholar]
- Bentov, I.; Lee, C.; Mizrahi, A.; Rosenfeld, M. Proof of activity: Extending bitcoin’s proof of work via proof of stake [extended abstract] y. ACM SIGMETRICS Perform. Eval. Rev. 2014, 42, 34–37. [Google Scholar] [CrossRef]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance. OsDI 1999, 99, 173–186. [Google Scholar]
- Kwon, J. Tendermint: Consensus without mining. Draft. v. 0.6 Fall 2014, 1, 1–11. [Google Scholar]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Brown, R.G.; Carlyle, J.; Grigg, I.; Hearn, M. Corda: An Introduction. R3 CEV 2016, 1, 14. [Google Scholar]
- LTO network, Blockchain for Decentralized Workflows. 2018. Available online: https://ltonetwork.com/documents/LTO%20Network%20-%20Technical%20Paper.pdf (accessed on 2 October 2023).
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. In Proceedings of the EuroSys’18: Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 4, 15. [Google Scholar]
- Li, K.; Li, H.; Hou, H.; Li, K.; Chen, Y. Proof of Vote: A High-Performance Consensus Protocol Based on Vote Mechanism & Consortium Blockchain. In Proceedings of the 2017 IEEE 19th International Conference on High Performance Computing and Communications; IEEE 15th International Conference on Smart City; IEEE 3rd International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Bangkok, Thailand, 18–20 December 2017; pp. 466–473. [Google Scholar]
- Xiao, Y.; Zhang, N.; Lou, W.; Hou, Y.T. A survey of distributed consensus protocols for blockchain networks. IEEE Commun. Surv. Tutor. 2020, 22, 1432–1465. [Google Scholar] [CrossRef]
- Bentov, I.; Gabizon, A.; Mizrahi, A. Cryptocurrencies without Proof of Work. In International Conference on Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2016; pp. 142–157. [Google Scholar]
- Wan, S.; Li, M.; Liu, G.; Wang, C. Recent advances in consensus protocols for blockchain: A survey. Wirel. Netw. 2020, 26, 5579–5593. [Google Scholar] [CrossRef]
- Kwon, J.; Buchman, E. Cosmos whitepaper. Netw. Distrib. Ledgers 2019, 27, 1–32. [Google Scholar]
- Naz, S.; Lee, S.U.-J. Why the New Consensus Mechanism is Needed in Blockchain Technology? In Proceedings of the 2020 Second International Conference on Blockchain Computing and Applications (BCCA), Antalya, Turkey, 2–5 November 2020; pp. 92–99. [Google Scholar]
- Yiu, N.C. An overview of forks and coordination in blockchain development. arXiv 2021, arXiv:2102.10006. [Google Scholar]
- Sobti, R.; Geetha, G. Cryptographic hash functions: A review. Int. J. Comput. Sci. Issues 2012, 9, 461. [Google Scholar]
- Shahsavari, Y.; Zhang, K.; Talhi, C. A Theoretical Model for Fork Analysis in the Bitcoin Network. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 237–244. [Google Scholar]
- Vujičić, D.; Jagodić, D.; Ranđić, S. Blockchain Technology, Bitcoin, and Ethereum: A Brief Overview. In Proceedings of the 2018 17th International Symposium Infoteh-Jahorina (Infoteh), East Sarajevo, Bosnia and Herzegovina, 21–23 March 2018; pp. 1–6. [Google Scholar]
- Seike, H.; Aoki, Y.; Koshizuka, N. Fork Rate-Based Analysis of the Longest Chain Growth Time Interval of A PoW Blockchain. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 253–260. [Google Scholar]
- Mazieres, D. The stellar consensus protocol: A federated model for internet-level consensus. Stellar Dev. Found. 2015, 32, 1–45. [Google Scholar]
- What is Antshares (ANS) and Blockchain. Available online: https://cryptopapers.info/assets/pdf/antshares.pdf (accessed on 3 October 2023).
- Wang, Q.; Li, R.; Chen, S.; Xiang, Y. Formal security analysis on dBFT protocol of NEO. Distrib. Ledger Technol. Res. Pract. 2023, 2, 1–19. [Google Scholar] [CrossRef]
- Saldamli, G.; Upadhyay, C.; Jadhav, D.; Shrishrimal, R.; Patil, B.; Tawalbeh, L.A. Improved gossip protocol for blockchain applications. Clust. Comput. 2022, 25, 1915–1926. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and privacy on blockchain. ACM Comput. Surv. 2019, 52, 1–34. [Google Scholar] [CrossRef]
- Fullmer, D.; Morse, A.S. Analysis of Difficulty Control in Bitcoin and Proof-of-Work Blockchains. In Proceedings of the 2018 IEEE Conference on Decision and Control (CDC), Miami, FL, USA, 17–19 December 2018; pp. 5988–5992. [Google Scholar]
- King, S.; Nadal, S. Ppcoin: Peer-to-peer crypto-currency with proof-of-stake. Self-Publ. Pap. 2012, 1, 1–6. [Google Scholar]
- Zhao, W. On Nxt Proof of Stake Algorithm: A Simulation Study. IEEE Trans. Dependable Secur. Comput. 2022, 20, 3546–3557. [Google Scholar] [CrossRef]
- Rabin, T.; Ben-Or, M. Verifiable Secret Sharing and Multiparty Protocols with Honest Majority. In Proceedings of the Twenty-First Annual ACM Symposium on Theory of Computing, Seattle, WA, USA, 14–17 May 1989; pp. 73–85. [Google Scholar]
- Daian, P.; Pass, R.; Shi, E. Snow White: Robustly Reconfigurable Consensus and Applications to Provably Secure Proof of Stake. In Proceedings of the Financial Cryptography and Data Security: 23rd International Conference, FC 2019, Frigate Bay, St. Kitts and Nevis, 18–22 February 2019; Revised Selected Papers 23. Springer: Berlin/Heidelberg, Germany, 2019; pp. 23–41. [Google Scholar]
- Kiayias, A.; Russell, A.; David, B.; Oliynykov, R. Ouroboros: A Provably Secure Proof-of-Stake Blockchain Protocol. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2017; pp. 357–388. [Google Scholar]
- David, B.; Gaži, P.; Kiayias, A.; Russell, A. Ouroboros Praos: An Adaptively-Secure, Semi-Synchronous Proof-of-Stake Blockchain. In Proceedings of the Advances in Cryptology–EUROCRYPT 2018: 37th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tel Aviv, Israel, 29 April–3 May 2018; Proceedings, Part II 37. Springer: Berlin/Heidelberg, Germany, 2018; pp. 66–98. [Google Scholar]
- Panda, S.K.; Bhoi, S.K. An effective round robin algorithm using min-max dispersion measure. arXiv 2014, arXiv:1404.5869. [Google Scholar]
- Korkmaz, K.; Bruneau-Queyreix, J.; Mokthar, S.B.; Réveillère, L. Dandelion: Multiplexing byzantine agreements to unlock blockchain performance. arXiv 2021, arXiv:2104.15063. [Google Scholar]
- Buchman, E.; Kwon, J.; Milosevic, Z. The latest gossip on BFT consensus. arXiv 2018, arXiv:1807.04938. [Google Scholar]
- Gilad, Y.; Hemo, R.; Micali, S.; Vlachos, G.; Zeldovich, N. Algorand: Scaling Byzantine Agreements for Cryptocurrencies. In Proceedings of the 26th Symposium on Operating Systems Principles, Shanghai, China, 28–30 October 2017; pp. 51–68. [Google Scholar]
- Buterin, V.; Griffith, V. Casper the friendly finality gadget. arXiv 2017, arXiv:1710.09437. [Google Scholar]
- Larimer, D. Delegated proof-of-stake (dpos). Bitshare Whitepaper 2014, 81, 85. [Google Scholar]
- Steem an Incentivized Blockchain-Based Public Content Platform, June 2018. Available online: https://steem.com/steem-whitepaper.pdf (accessed on 1 September 2023).
- Kordek, M.; Beddows, O. White paper: Lisk. Technical Report. 2016. Available online: https://whitepaperdatabase.com/lisk-lsk (accessed on 26 October 2023).
- Xu, B.; Luthra, D.; Cole, Z.; Blakely, N. EOS: An architectural, performance, and economic analysis. Retrieved June 2018, 11, 2019. [Google Scholar]
- Luo, Y.; Chen, Y.; Chen, Q.; Liang, Q. A New Election Algorithm for DPos Consensus Mechanism in Blockchain. In Proceedings of the 2018 7th International Conference on Digital Home (ICDH), Guilin, China, 30 November–1 December 2018; pp. 116–120. [Google Scholar]
- Hu, Q.; Yan, B.; Han, Y.; Yu, J. An improved delegated proof of stake consensus algorithm. Procedia Comput. Sci. 2021, 187, 341–346. [Google Scholar] [CrossRef]
- Suratkar, S.; Shirole, M.; Bhirud, S. Cryptocurrency Wallet: A Review. In Proceedings of the 2020 4th International Conference on Computer, Communication and Signal Processing (ICCCSP), Chennai, India, 28–29 September 2020; pp. 1–7. [Google Scholar]
- Aydar, M.; Cetin, S.C.; Ayvaz, S.; Aygun, B. Private key encryption and recovery in blockchain. arXiv 2019, arXiv:1907.04156. [Google Scholar]
- Hellman, M.E. An overview of public key cryptography. IEEE Commun. Mag. 2002, 40, 42–49. [Google Scholar] [CrossRef]
- Pooja, M.; Yadav, M. Digital signature. International Journal of Scientific Research in Computer Science. Eng. Inf. Technol. 2018, 3, 71–75. [Google Scholar]
- Ahamad, S.; Nair, M.; Varghese, B. A Survey on Crypto Currencies. In Proceedings of the 4th International Conference on Advances in Computer Science, AETACS, Delhi, India, 13–14 December 2013; pp. 42–48. [Google Scholar]
- Allombert, V.; Bourgoin, M.; Tesson, J. Introduction to the Tezos Blockchain. In Proceedings of the 2019 International Conference on High Performance Computing & Simulation (HPCS), Dublin, Ireland, 15–19 July 2019; pp. 1–10. [Google Scholar]
- Burdges, J.; Cevallos, A.; Czaban, P.; Habermeier, R.; Hosseini, S.; Lama, F.; Alper, H.K.; Luo, X.; Shirazi, F.; Stewart, A.; et al. Overview of polkadot and its design considerations. arXiv 2020, arXiv:2005.13456. [Google Scholar]
- Tanana, D. Avalanche Blockchain Protocol for Distributed Computing Security. In Proceedings of the 2019 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Sochi, Russia, 3–6 June 2019; pp. 1–3. [Google Scholar]
- A Comparison of Heterogeneous Blockchain Networks. 19 March 2022. Available online: https://medium.com/@arikan/a-comparison-of-heterogeneous-blockchain-networks-4bf7ff2fe279 (accessed on 1 October 2023).
- Milanov, E. The RSA Algorithm. 2009, pp. 1–11. Available online: https://sites.math.washington.edu/~morrow/336_09/papers/Yevgeny.pdf (accessed on 3 October 2023).
- Exponential Distribution. Available online: https://en.wikipedia.org/wiki/Exponential_distribution (accessed on 3 October 2023).
- Sun, X.; Yu, F.R.; Zhang, P.; Sun, Z.; Xie, W.; Peng, X. A survey on zero-knowledge proof in blockchain. IEEE Netw. 2021, 35, 198–205. [Google Scholar] [CrossRef]
- Leonardos, S.; Reijsbergen, D.; Piliouras, G. Presto: A systematic framework for blockchain consensus protocols. IEEE Trans. Eng. Manag. 2020, 67, 1028–1044. [Google Scholar] [CrossRef]
- Endpoint Security Risks—Associated with New Blockchain Technology. 2021. Available online: https://www.cloudcodes.com/blog/endpoint-security-risks-due-to-blockchain.html (accessed on 3 October 2023).
- Quorum Whitepaper. 2018. Available online: https://github.com/ConsenSys/quorum/blob/master/docs/Quorum%20Whitepaper%20v0.2.pdf (accessed on 5 October 2023).
- Blockchain Governance: What Is It, What Types Are There and How Does It Work in Practice? 2023. Available online: https://watsonlaw.nl/en/blockchain-governance-what-is-it-what-types-are-there-and-how-does-it-work-in-practice/ (accessed on 3 October 2023).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).