A Secure Authentication Scheme with Local Differential Privacy in Edge Intelligence-Enabled VANET
Abstract
1. Introduction
- We propose a secure authentication scheme for edge intelligence-enabled VANET environments. The proposed scheme can provide a secure communication between edge nodes and vehicles using fuzzy extractors, biometric information, and ECC. To ensure the robust security for edge nodes, the proposed scheme utilizes PUF technology when generating the secret keys.
- We provide a secure data upload process using the session key and local differential privacy technology [6]. Thus, the proposed scheme can ensure secure message transmission and data collection through the encryption of de-identification data. This approach can provide secure and efficient data management for edge intelligence-enabled VANET environments.
- We compare the computation and communication overheads of the proposed scheme with the other related schemes using “Multiprecision Integer and Rational Arithmetic Cryptographic Library (MIRACL) software development kit (SDK) [13]”.
2. Related Works
3. Preliminaries
3.1. System Model
3.1.1. Trusted Authority
3.1.2. Cloud Server
3.1.3. Edge Node
3.1.4. Vehicle
3.2. Threat Model
- The adversary can reveal the verification table and try to compute sensitive parameters [30].
- The adversary can obtain secret parameters and try to disguise itself as a legitimate vehicle [31].
- The adversary can be a privileged insider to compute identity and password of vehicle.
- The adversary can perform various security attacks such as man-in-the-middle, ephemeral secret leakage, replay, and insider attacks.
3.3. Elliptic Curve Cryptography
- Elliptic curve discrete logarithm (ECDL) problem: A mathematical problem to compute when is given.
- Elliptic curve decisional Diffie–Hellman (ECDDH) problem: A mathematical problem to grant the equality of and when n, s, and t is allowed.
- Elliptic curve computational Diffie–Hellman (ECCDH) problem: A mathematical problem to compute when and are allowed.
3.4. Physically Unclonable Function
- PUF is a hardware circuit, which cannot replicate or interpret the detailed structure.
- Since PUF is implemented uniquely in each hardware, different outputs are produced even if the same input is input.
- The output value of PUF cannot be predicted.
- PUF is easy to implement and estimate.
3.5. Fuzzy Extractor
- : After executing the probability algorithm , we can obtain a string and helper string . We utilize as a secret parameter for the proposed scheme.
- : After conducting the deterministic algorithm with helper string , we can obtain the secret parameter .
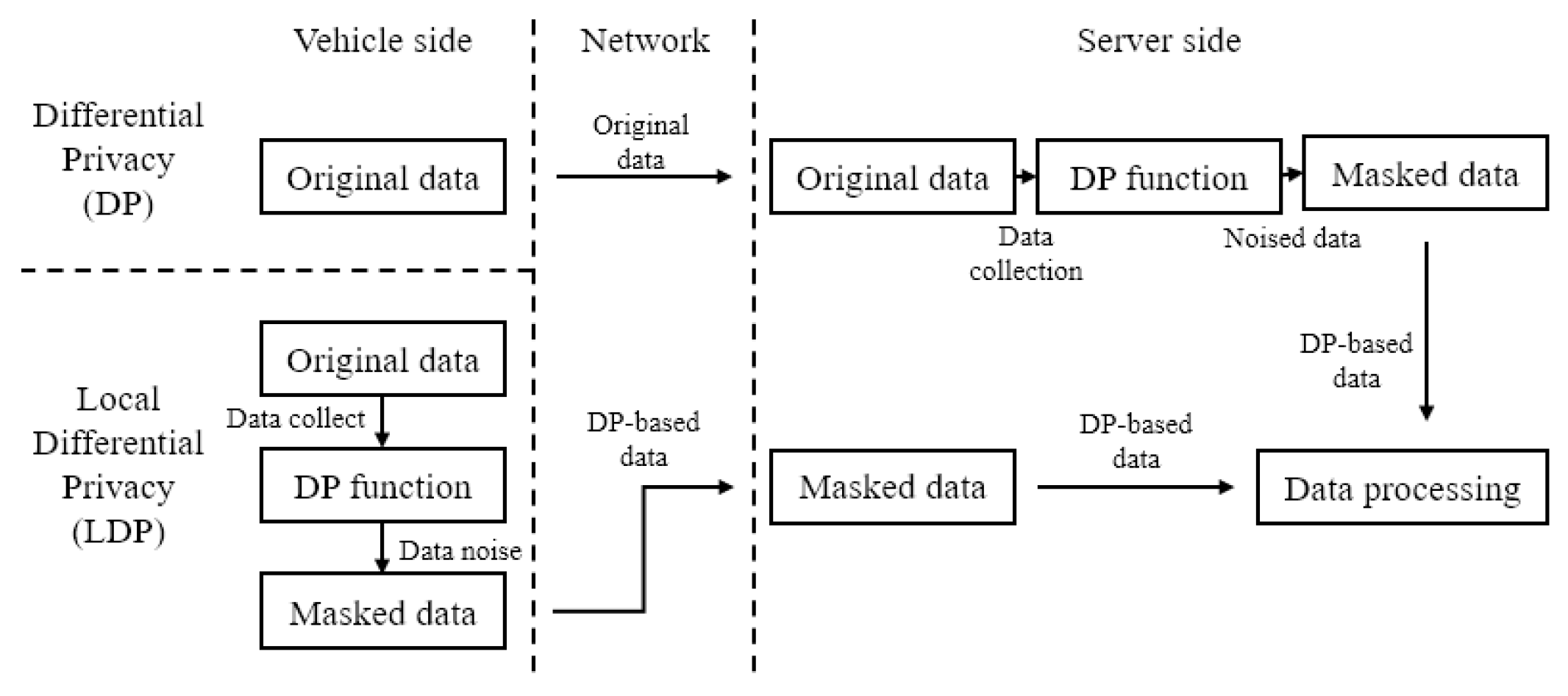
3.6. Local Differential Privacy
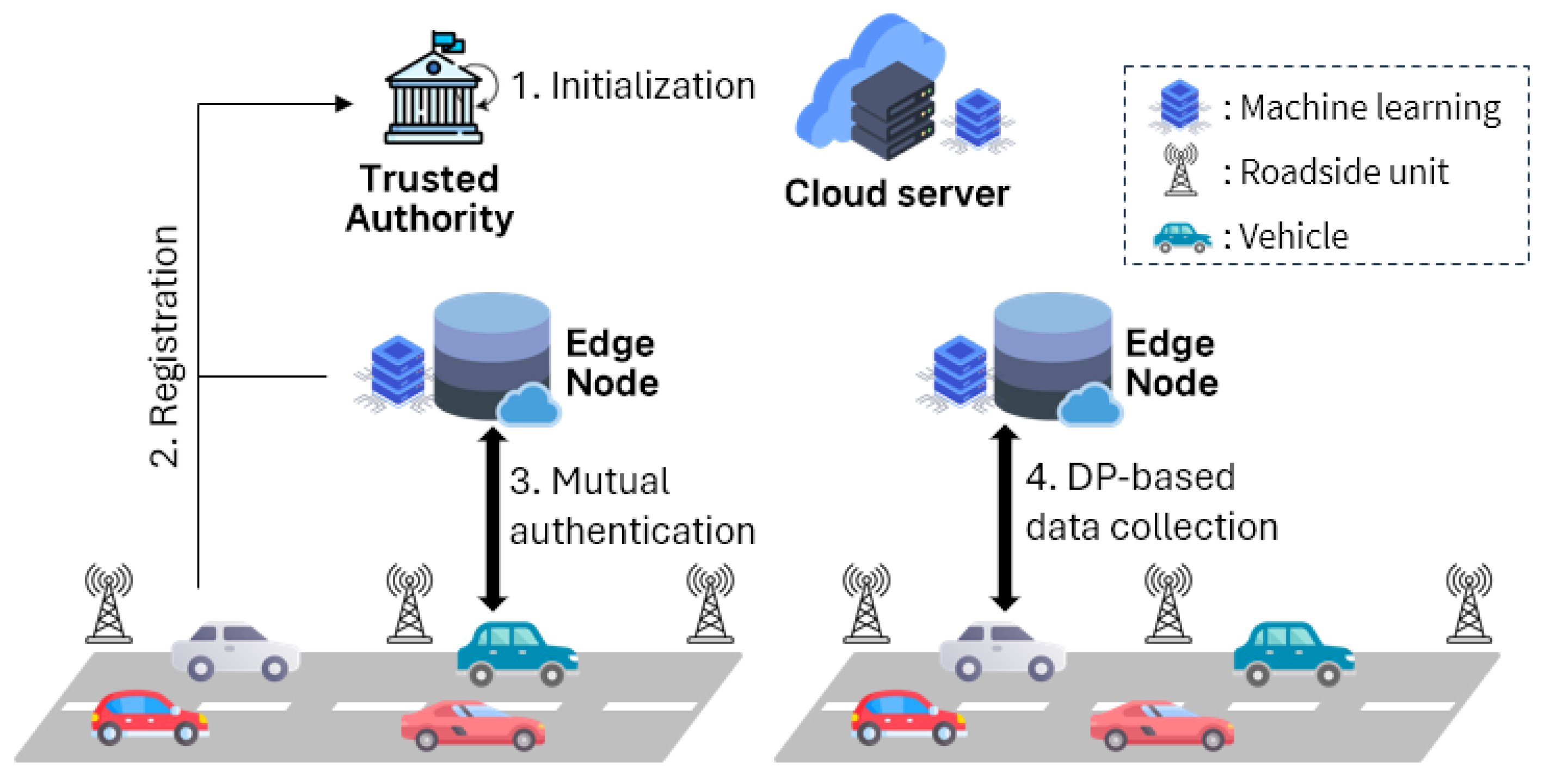
4. Proposed Scheme
4.1. Initialization Phase
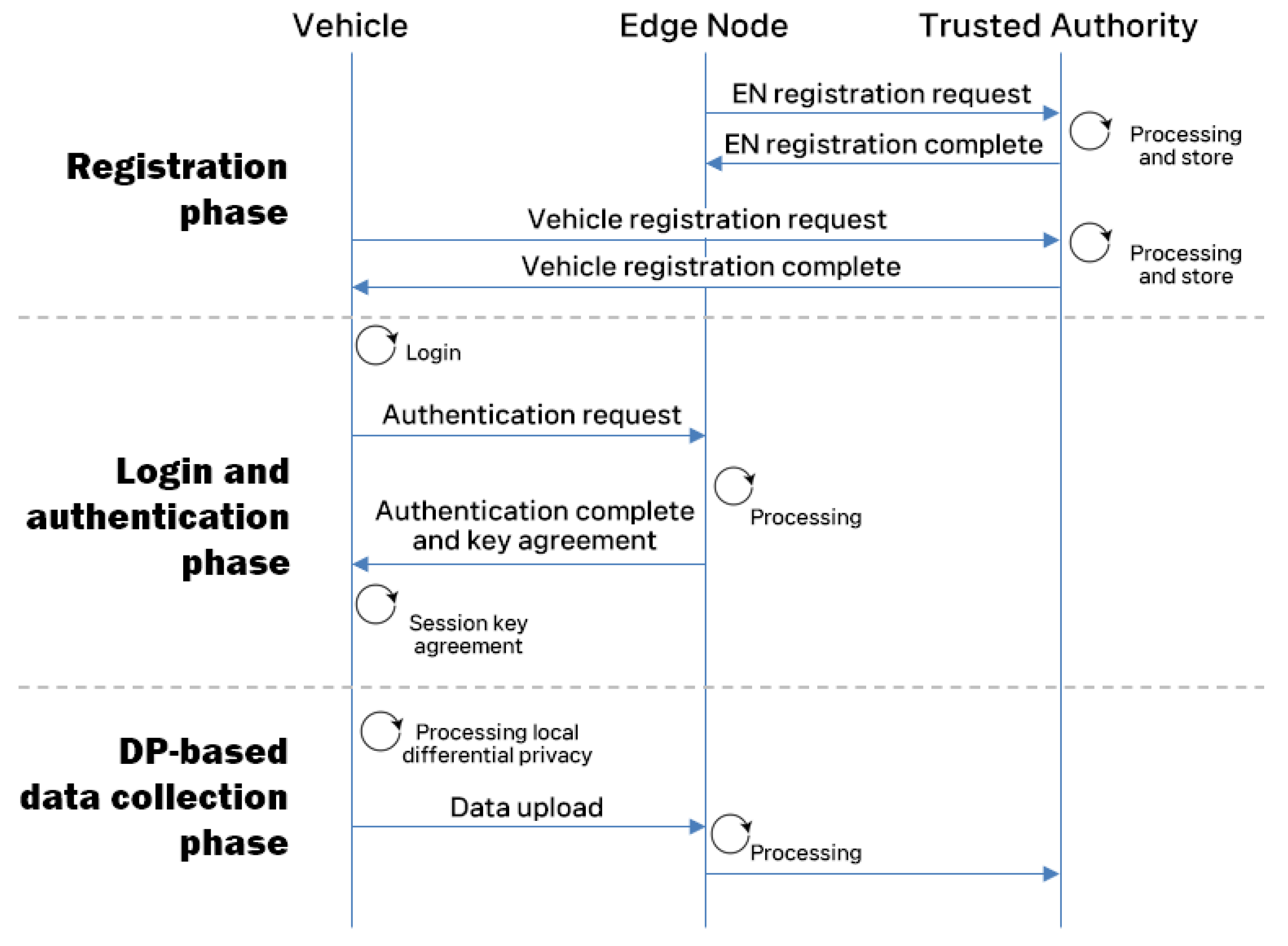
4.2. Registration Phase
4.2.1. Edge Node Registration
- RE1:
- To register in the proposed network system, the edge node selects its own identity and picks a random number . Then, computes and sends to the TA via a secure channel.
- RE2:
- TA first checks the validity of and generates . Then, TA computes and stores in its secure database. TA returns to through a secure channel.
- RE3:
- computes , using PUF function, using fuzzy extractor, and . keeps as a secret key and computes public key . stores in its database.
4.2.2. Vehicle Registration
- RV1:
- The user of a vehicle selects their own identity , password , and biometrics . Then, picks a random number and computes using fuzzy extractor, . sends a registration request message to the TA via a secure channel.
- RV2:
- TA checks the validity of and generates to compute , , and . TA stores and sends a return message to through a secure channel.
- RV3:
- computes its secret key and public key . Then, computes , , , , and . stores in its memory.
4.3. Login and Authentication Phase
| Algorithm 1: Login and authentication: Vehicle |
 |
| Algorithm 2: Login and authentication: Edge node |
 |
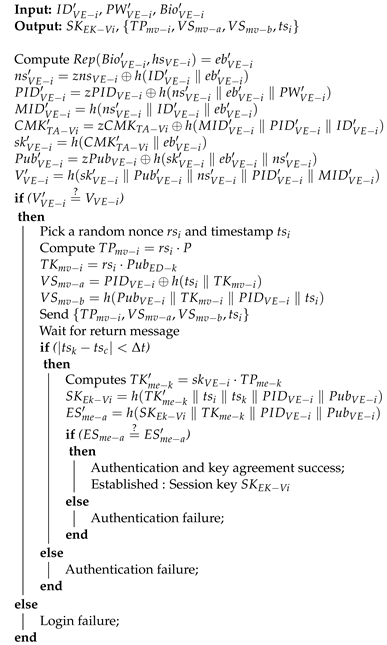
- LA1:
- inputs , , and biometrics . Then, computes using fuzzy extractor, , , , , and . If is equal to , picks a random nonce and timestamp . Then, computes , , , , and sends to the edge node through a public channel.
- LA2:
- checks the freshness of through the inequality . Then, computes , , , , , and retrieves . From that, checks the equality of and . If it is valid, generates and , and computes , , , and . sends to through a public channel.
- LA3:
- first check and computes , , and . If is equal to , the session key is completely established between and .
4.4. Differential Privacy-Based Data Collection Phase
- DC1:
- With the collected data , executes Laplace mechanism (, ) and obtains DP-based data . After that, generates a timestamp and computes , . sends to via an wireless open channel.
- DC2:
- checks the validity of and computes , . If is equal to , utilizes the DP-based data for various service improvement tasks.
5. Security Analysis
5.1. ROR Model
- : The adversary can collect messages transmitted through public channels using query.
- : The adversary can capture the vehicle and extract secret parameters using query.
- : This query represents a send event. Thus, the adversary can send messages to participant .
- : This is a test query to distinguish the session key and random number. If the query is executed, an unbiased coin is flipped. When the adversary obtains 0, the session key security can be achieved. However, the session key is not secure if the adversary obtains 1. Otherwise, the value is output.
Security Proof
5.2. Informal Analysis
5.2.1. Replay and Man-in-the-Middle Attacks
5.2.2. Impersonation Attacks
5.2.3. Insider Attacks
5.2.4. Privileged Insider Attacks
5.2.5. Verification Table Leakage Attacks
5.2.6. Ephemeral Secret Leakage (ESL) Attacks
5.2.7. Perfect Forward Secrecy
5.2.8. User Anonymity and Untraceability
5.2.9. Mutual Authentication
5.3. Scyther Tool
6. Performance Analysis
6.1. MIRACL Testbed
- Desktop environments: “Linux Ubuntu 20.04 LTS, Intel Core i3-8100 CPU @ 3.60 GHz, 16 GB RAM”
- Raspberry Pi environments: Raspberry Pi 4B (Quad-core ARM Cortex-A72 @ 1.5 GHz, 8 GB RAM)
6.2. Computational Overheads
6.3. Communication Overheads
6.4. NS-3 Simulation
- Scenario 1: 10 vehicles are placed in a single edge node’s service range.
- Scenario 2: 30 vehicles are placed in a single edge node’s service range.
- Scenario 3: 60 vehicles are placed in three edge nodes’ service range.
- Scenario 4: 90 vehicles are placed in three edge nodes’ service range.
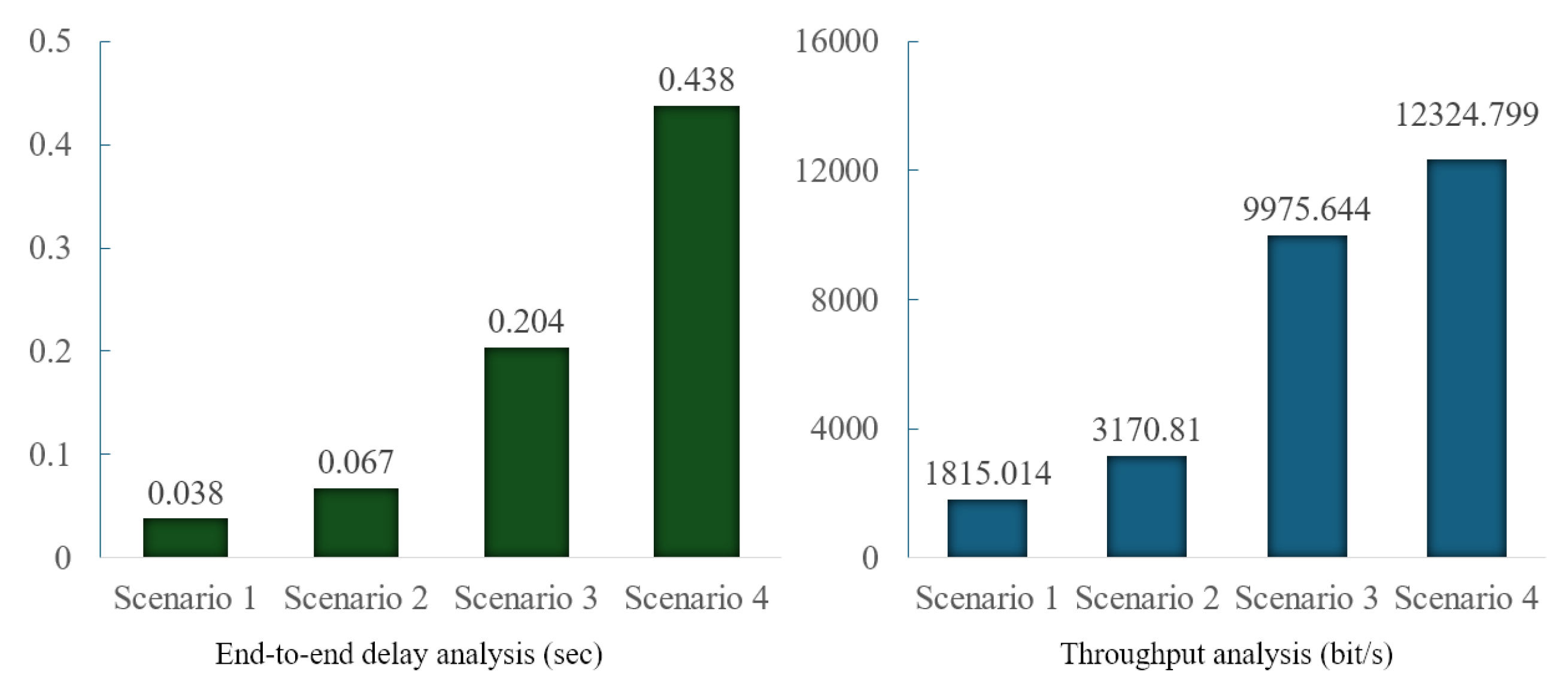
Throughput and End-to-End Delay Analysis
6.5. Security Features
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Liu, Y.; Peng, M.; Shou, G.; Chen, Y.; Chen, S. Toward edge intelligence: Multiaccess edge computing for 5G and Internet of Things. IEEE Internet Things J. 2020, 7, 6722–6747. [Google Scholar] [CrossRef]
- Plastiras, G.; Terzi, M.; Kyrkou, C.; Theocharides, T. Edge intelligence: Challenges and opportunities of near-sensor machine learning applications. In Proceedings of the 2018 IEEE 29th International Conference on Application-Specific Systems, Architectures and Processors (ASAP), Milan, Italy, 10–12 July 2018; pp. 1–7. [Google Scholar]
- Zhang, J.; Letaief, K.B. Mobile edge intelligence and computing for the internet of vehicles. Proc. IEEE 2019, 108, 246–261. [Google Scholar] [CrossRef]
- Balasubramanian, V.; Otoum, S.; Reisslein, M. VeNet: Hybrid stacked autoencoder learning for cooperative edge intelligence in IoV. IEEE Trans. Intell. Transp. Syst. 2022, 23, 16643–16653. [Google Scholar] [CrossRef]
- Haris, M.; Shah, M.A.; Maple, C. Internet of intelligent vehicles (IoIV): An intelligent VANET based computing via predictive modeling. IEEE Access 2023, 11, 49665–49674. [Google Scholar] [CrossRef]
- Dwork, C. Differential privacy. In Proceedings of the International Colloquium on Automata, Languages, and Programming, Venice, Italy, 10–14 July 2006; pp. 1–12. [Google Scholar]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Advances in Cryptology-EUROCRYPT 2004, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Public Key Cryptography—PKC 2005, Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 2005; pp. 65–84. [Google Scholar]
- Cremers, C.J. The Scyther Tool: Verification, Falsification, and Analysis of Security Protocols: Tool Paper. In Proceedings of the International Conference on Computer Aided Verification, Princeton, NJ, USA, 7–14 July 2008; pp. 414–418. [Google Scholar]
- Scyther Tool. Available online: https://people.cispa.io/cas.cremers/scyther/ (accessed on 5 July 2024).
- NS-3.29. Available online: https://www.nsnam.org (accessed on 5 July 2024).
- MIRACL Cryptographic SDK. Available online: https://github.com/miracl/MIRACL (accessed on 5 July 2024).
- Zhou, Z.; Chen, X.; Li, E.; Zeng, L.; Luo, K.; Zhang, J. Edge intelligence: Paving the last mile of artificial intelligence with edge computing. Proc. IEEE 2019, 107, 1738–1762. [Google Scholar] [CrossRef]
- Deng, S.; Zhao, H.; Fang, W.; Yin, J.; Dustdar, S.; Zomaya, A.Y. Edge intelligence: The confluence of edge computing and artificial intelligence. IEEE Internet Things J. 2020, 7, 7457–7469. [Google Scholar] [CrossRef]
- Qi, W.; Li, Q.; Song, Q.; Guo, L.; Jamalipour, A. Extensive edge intelligence for future vehicular networks in 6G. IEEE Wirel. Commun. 2021, 28, 128–135. [Google Scholar] [CrossRef]
- Gong, T.; Zhu, L.; Yu, F.R.; Tang, T. Edge intelligence in intelligent transportation systems: A survey. IEEE Trans. Intell. Transp. Syst. 2023, 24, 8919–8944. [Google Scholar] [CrossRef]
- Zhang, Y.; Huang, H.; Yang, L.X.; Xiang, Y.; Li, M. Serious challenges and potential solutions for the industrial internet of things with edge intelligence. IEEE Netw. 2019, 33, 41–45. [Google Scholar] [CrossRef]
- Li, Y.; Yu, Y.; Susilo, W.; Hong, Z.; Guizani, M. Security and privacy for edge intelligence in 5G and beyond networks: Challenges and solutions. IEEE Wirel. Commun. 2021, 28, 63–69. [Google Scholar] [CrossRef]
- Xu, D.; Li, T.; Li, Y.; Su, X.; Tarkoma, S.; Jiang, T.; Crowcroft, J.; Hui, P. Edge intelligence: Empowering intelligence to the edge of network. Proc. IEEE 2021, 109, 1778–1837. [Google Scholar] [CrossRef]
- Villar-Rodriguez, E.; Pérez, M.A.; Torre-Bastida, A.I.; Senderos, C.R.; López-de-Armentia, J. Edge intelligence secure frameworks: Current state and future challenges. Comput. Secur. 2023, 130, 103278. [Google Scholar] [CrossRef]
- Jia, X.; He, D.; Kumar, N.; Choo, K.K.R. A provably secure and efficient identity-based anonymous authentication scheme for mobile edge computing. IEEE Syst. J. 2019, 14, 560–571. [Google Scholar] [CrossRef]
- Bagga, P.; Das, A.K.; Wazid, M.; Rodrigues, J.J.; Choo, K.K.R.; Park, Y. On the design of mutual authentication and key agreement protocol in internet of vehicles-enabled intelligent transportation system. IEEE Trans. Veh. Technol. 2021, 70, 1736–1751. [Google Scholar] [CrossRef]
- Ke, C.; Zhu, Z.; Xiao, F.; Huang, Z.; Meng, Y. SDN-based privacy and functional authentication scheme for fog nodes of smart healthcare. IEEE Internet Things J. 2022, 9, 17989–18001. [Google Scholar] [CrossRef]
- Seifelnasr, M.; AlTawy, R.; Youssef, A.; Ghadafi, E. Privacy-preserving mutual authentication protocol with forward secrecy for IoT-edge-cloud. IEEE Internet Things J. 2023, 11, 8105–8117. [Google Scholar] [CrossRef]
- Yadav, A.K.; Shojofar, M.; Braeken, A. iVFAS: An improved vehicle-to-fog authentication system for secure and efficient fog-based road condition monitoring. IEEE Trans. Veh. Technol. 2024, 1–16. [Google Scholar] [CrossRef]
- Kumar, P.; Om, H. Multi-TA model-based conditional privacy-preserving authentication protocol for fog-enabled VANET. Veh. Commun. 2024, 47, 100785. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Advances in Cryptology—EUROCRYPT 2002, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 337–351. [Google Scholar]
- Oh, J.; Son, S.; Kwon, D.; Kim, M.; Park, Y.; Park, Y. Design of secure and privacy-preserving data sharing scheme based on key aggregation and private set intersection in medical information system. Mathematics 2024, 12, 1717. [Google Scholar] [CrossRef]
- Son, S.; Oh, J.; Kwon, D.; Kim, M.; Park, K.; Park, Y. A Privacy-preserving authentication scheme for a blockchain-based energy trading system. Mathematics 2023, 11, 4653. [Google Scholar] [CrossRef]
- Hou, W.; Sun, Y.; Li, D.; Guan, Z.; Liu, J. Lightweight and privacy-preserving charging reservation authentication protocol for 5G-V2G. IEEE Trans. Veh. Technol. 2023, 72, 7871–7883. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Park, K.; Lee, J.; Das, A.K.; Park, Y. BPPS: Blockchain-enabled privacy-preserving scheme for demand-response management in smart grid environments. IEEE Trans. Dependable Secur. Comput. 2023, 20, 1719–1729. [Google Scholar] [CrossRef]
- Park, K.; Park, Y. MIoT-CDPS: Complete decentralized privacy-preserving scheme for medical internet of things. Internet Things 2024, 27, 101250. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Boyko, V.; MacKenzie, P.; Patel, S. Provably secure password-authenticated key exchange using Diffie-Hellman. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Bruges, Belgium, 14–18 May 2000; pp. 156–171. [Google Scholar]


| Year | Scheme | Contributions | Limitations |
|---|---|---|---|
| 2019 | [22] |
|
|
| 2021 | [23] |
|
|
| 2022 | [24] |
|
|
| 2023 | [25] |
|
|
| 2024 | [26] |
|
|
| 2024 | [27] |
|
|
| - | Proposed |
| |
| Notation | Explanation |
|---|---|
| Real identity of vehicle and edge node | |
| Password of vehicle | |
| Biometric information of vehicle | |
| Pseudo identity of vehicle | |
| Helper string | |
| Random nonce | |
| Timestamp | |
| Public key of an entity m | |
| Secret key of an entity m | |
| Generation algorithm of fuzzy extractor | |
| Reproduce algorithm of fuzzy extractor | |
| PUF operator | |
| Session key | |
| · | Multiplication operator |
| ⊕ | XOR operator |
| Hash function | |
| Concatenation operator |
| Claim Event | Description |
|---|---|
| Aliveness | The entity is certain whether or not it is communicating with the other party. |
| Weak agreement | The entity is certain whether or not it is communicating with the other legitimate party. |
| Non-injective agreement | The entity is certain whether or not it is communicating with the other legitimate party, which exchanges the legal data. |
| Non-injective synchronization | The entity is certain whether or not it is communicating with the other legitimate party, which exchanges the legal data. Moreover, the messages are transmitted, following the rules of the protocol. |
| Notations | Max | Min | Average |
|---|---|---|---|
| ECC multiplication () | 3.018 ms | 2.003 ms | 2.265 ms |
| ECC addition () | 0.035 ms | 0.018 ms | 0.024 ms |
| AES encryption () | 0.007 ms | 0.003 ms | 0.004 ms |
| AES decryption () | 0.006 ms | 0.003 ms | 0.004 ms |
| Bilinear pairings () | 13.837 ms | 10.533 ms | 11.937 ms |
| Exponentiation () | 0.189 ms | 0.093 ms | 0.115 ms |
| Hash function () | 0.007 ms | 0.005 ms | 0.006 ms |
| Notations | Max | Min | Average |
|---|---|---|---|
| ECC multiplication () | 0.421 ms | 0.388 ms | 0.409 ms |
| ECC addition () | 0.006 ms | 0.002 ms | 0.006 ms |
| AES encryption () | 0.001 ms | 0.001 ms | 0.001 ms |
| AES decryption () | 0.001 ms | 0.001 ms | 0.001 ms |
| Bilinear pairings () | 2.735 ms | 2.015 ms | 2.253 ms |
| Exponentiation () | 0.052 ms | 0.033 ms | 0.041 ms |
| Hash function () | 0.002 ms | 0.001 ms | 0.002 ms |
| Schemes | Device | Infrastructure | Total Costs |
|---|---|---|---|
| Jia et al. [22] | 15.693 ms | ||
| Bagga et al. [23] | 13.053 ms | ||
| Ke et al. [24] | 33.346 ms | ||
| Seifelnasr et al. [25] | 26.431 ms | ||
| Yadav et al. [26] | 8.938 ms | ||
| Kumar and Om [27] | 11.367 ms | ||
| Proposed | 8.098 ms |
| Schemes | Total Communication Costs | Messages |
|---|---|---|
| Jia et al. [22] | 1504 bits | 2 |
| Bagga et al. [23] | 1856 bits | 3 |
| Ke et al. [24] | 992 bits | 2 |
| Seifelnasr et al. [25] | 3840 bits | 3 |
| Yadav et al. [26] | 1472 bits | 3 |
| Kumar and Om [27] | 2880 bits | 5 |
| Proposed | 1184 bits | 2 |
| Simulation Parameters | Details |
|---|---|
| Version of NS-3 | 3.29 |
| Version of OS | Ubuntu 16.04 LTS |
| Number of vehicles | 10, 30, 60, 90 |
| Number of edge nodes | 1, 3 |
| Propagation loss model | TwoRayGroundPropagationLossModel |
| Mobility model | RandomDirection2dMobilityModel |
| ConstantPositionMobilityModel | |
| Simulation area | 500 m × 500 m |
| Wireless channel bandwidth | 6 Mbps |
| Network | IEEE 802.11p |
| Routing protocol | Ad hoc On-demand Distance Vector |
| Simulation time | 300 s |
| Security Features | [22] | [23] | [24] | [25] | [26] | [27] | Proposed |
|---|---|---|---|---|---|---|---|
| F1 | ∘ | ∘ | ∘ | ∘ | ∘ | ∘ | ∘ |
| F2 | ∘ | ∘ | ∘ | ∘ | ∘ | ∘ | ∘ |
| F3 | ∘ | × | ∘ | ∘ | ∘ | ∘ | ∘ |
| F4 | − | − | − | − | − | ∘ | ∘ |
| F5 | ∘ | ∘ | ∘ | ∘ | − | − | ∘ |
| F6 | ∘ | ∘ | ∘ | ∘ | − | − | ∘ |
| F7 | × | ∘ | ∘ | ∘ | ∘ | ∘ | ∘ |
| F8 | × | ∘ | ∘ | ∘ | ∘ | ∘ | ∘ |
| F9 | ∘ | ∘ | ∘ | × | ∘ | ∘ | ∘ |
| F10 | × | ∘ | × | × | ∘ | ∘ | ∘ |
| F11 | × | × | ∘ | × | × | × | ∘ |
| F12 | ∘ | ∘ | ∘ | ∘ | ∘ | ∘ | ∘ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kwon, D.; Son, S.; Park, K.; Park, Y. A Secure Authentication Scheme with Local Differential Privacy in Edge Intelligence-Enabled VANET. Mathematics 2024, 12, 2383. https://doi.org/10.3390/math12152383
Kwon D, Son S, Park K, Park Y. A Secure Authentication Scheme with Local Differential Privacy in Edge Intelligence-Enabled VANET. Mathematics. 2024; 12(15):2383. https://doi.org/10.3390/math12152383
Chicago/Turabian StyleKwon, Deokkyu, Seunghwan Son, Kisung Park, and Youngho Park. 2024. "A Secure Authentication Scheme with Local Differential Privacy in Edge Intelligence-Enabled VANET" Mathematics 12, no. 15: 2383. https://doi.org/10.3390/math12152383
APA StyleKwon, D., Son, S., Park, K., & Park, Y. (2024). A Secure Authentication Scheme with Local Differential Privacy in Edge Intelligence-Enabled VANET. Mathematics, 12(15), 2383. https://doi.org/10.3390/math12152383








