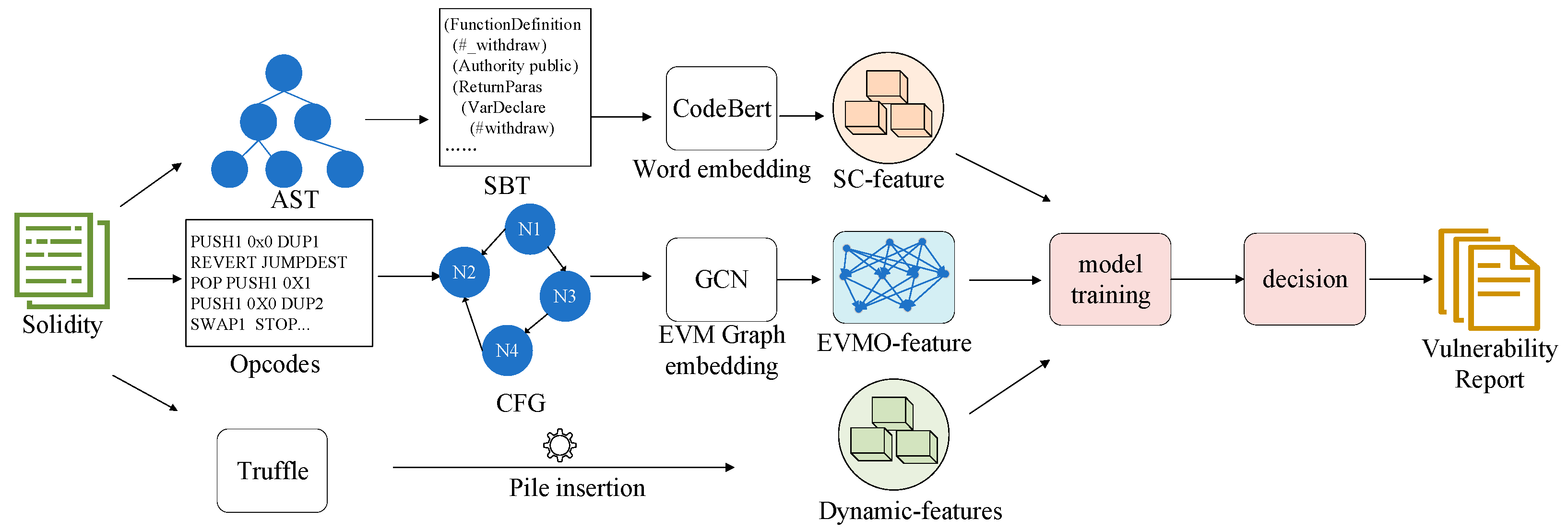
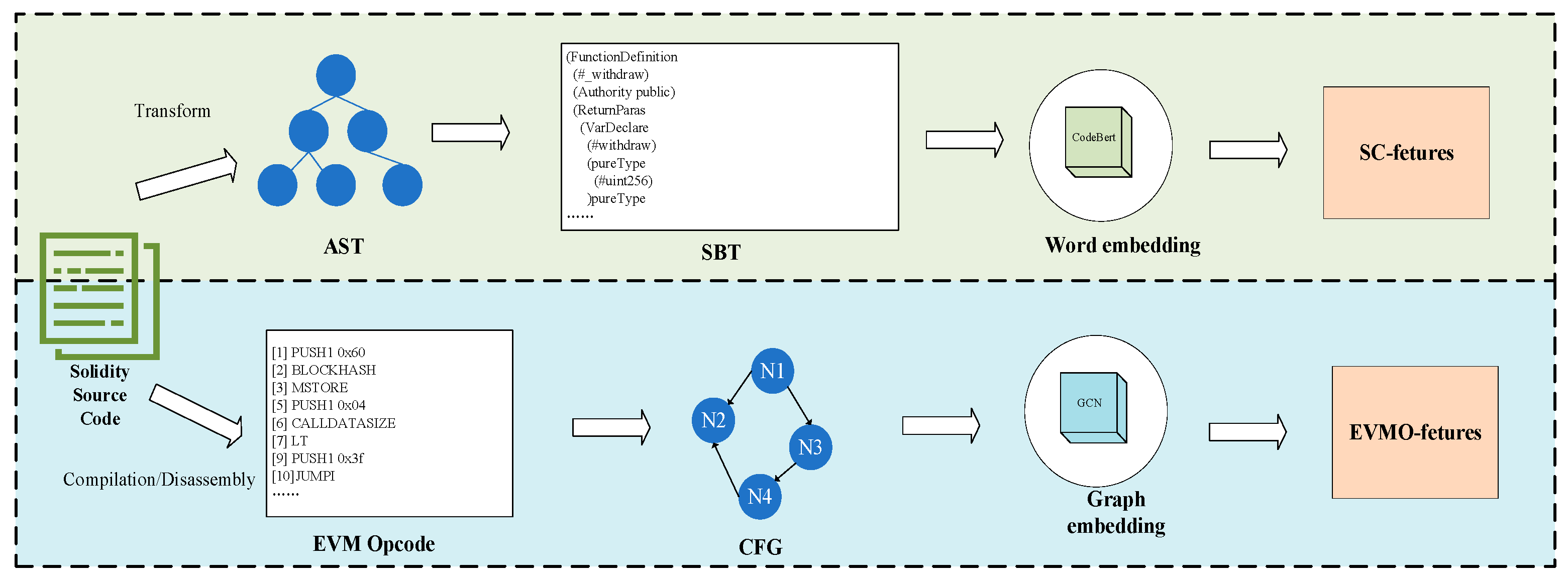
3.2. Extracting Static Features of Smart Contracts
As shown in
Figure 4, in this section we will demonstrate how to conduct data preprocessing and obtain features from the SC layer and EVMO layer. We will further elaborate on how to combine these features for smart contract vulnerability detection.
3.2.1. Source Code Layer
Smart contract source code is inherently unstructured, requiring the extraction of structural features for improved contract detection [
29,
30]. Hu et al. [
31] introduced the Structure-Based Traversal (SBT) method, which involves transforming the AST into a specialized format through a comprehensive traversal. In the SBT representation, “type” signifies structural information, “value” represents lexical information, and brackets indicate the hierarchical structure. Previous studies [
32,
33,
34] have illustrated the effectiveness of SBT in preserving both the code’s structural and lexical aspects. Consequently, we treat the SBT sequence as a modality of the AST, employing the SBT method to encapsulate the overall semantic information, including both structural and lexical elements.
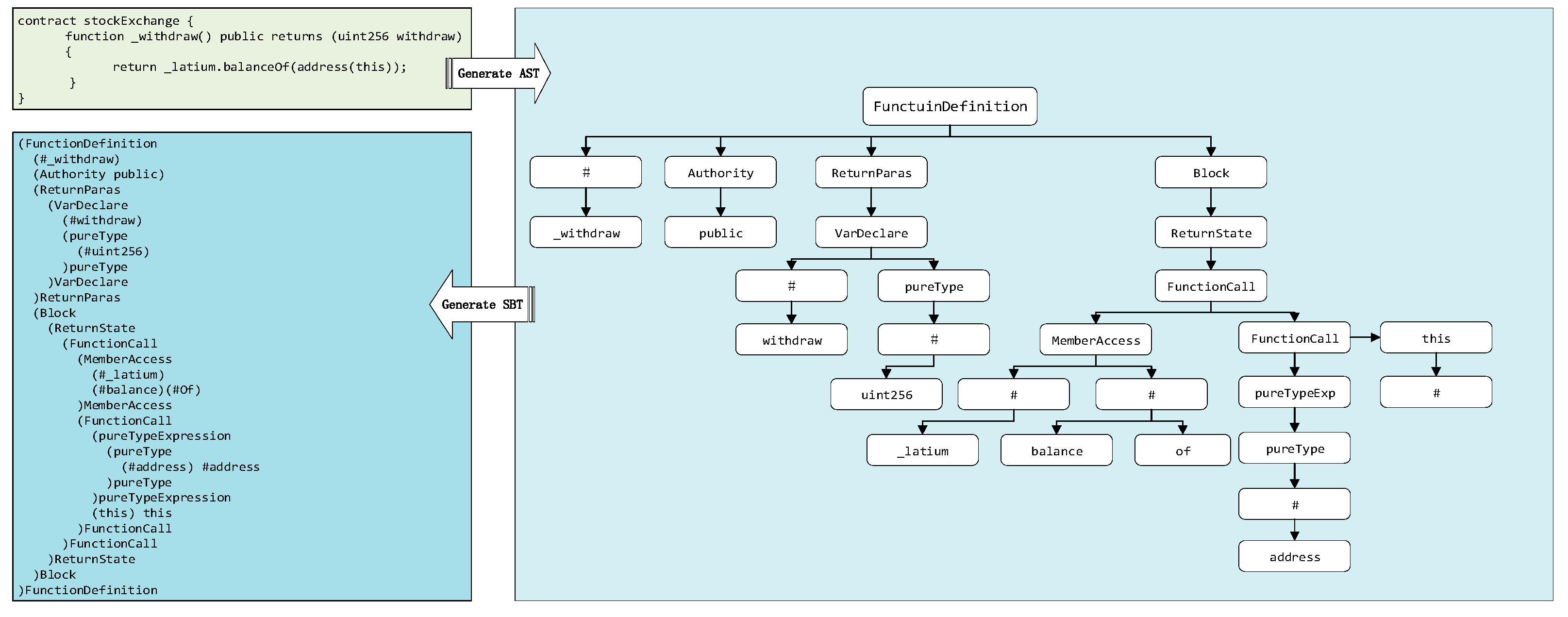
Using
Figure 5 as an illustration, our initial step involves employing the open-source parsing tool, tree-sitter-solidity (
https://github.com/JoranHonig/tree-sitter-solidity, accessed on 12 September 2023), to parse the source code and generate an AST. Subsequently, we utilize the SBT method to transform this AST into an SBT sequence. In the provided figure, consider the StockExchange contract that defines a function named “withdraw”. Non-leaf nodes are denoted by type (e.g., the root node of the contract is FunctionDefinition), and various elements such as variables, function names—return value names are represented by “#”. Leaf nodes correspond to values associated with each type.
For the initialization of the word-embedding matrix, two primary approaches are considered: random values or pretrained vectors obtained from models like CodeBERT [
35], Word2Vec [
22], GloVe [
36], FastText [
37], ELMo [
38], etc. While many methods are originally designed for natural language text, audio, video sequences, or knowledge graphs, CodeBERT stands out as a pretrained model uniquely suited for handling bimodal data, accommodating both natural language text and programming languages.
In the context of SBT, which incorporates distinctive tokens (e.g., ModifierDefinition, ModifierInvocation, SimpleName, FunctionDefinition), the construction of the SBT corpus requires the inclusion of these additional tokens. Subsequently, the SBT word-embedding matrix is formed based on this corpus and in conjunction with CodeBERT.
3.2.2. EVM Opcode Layer
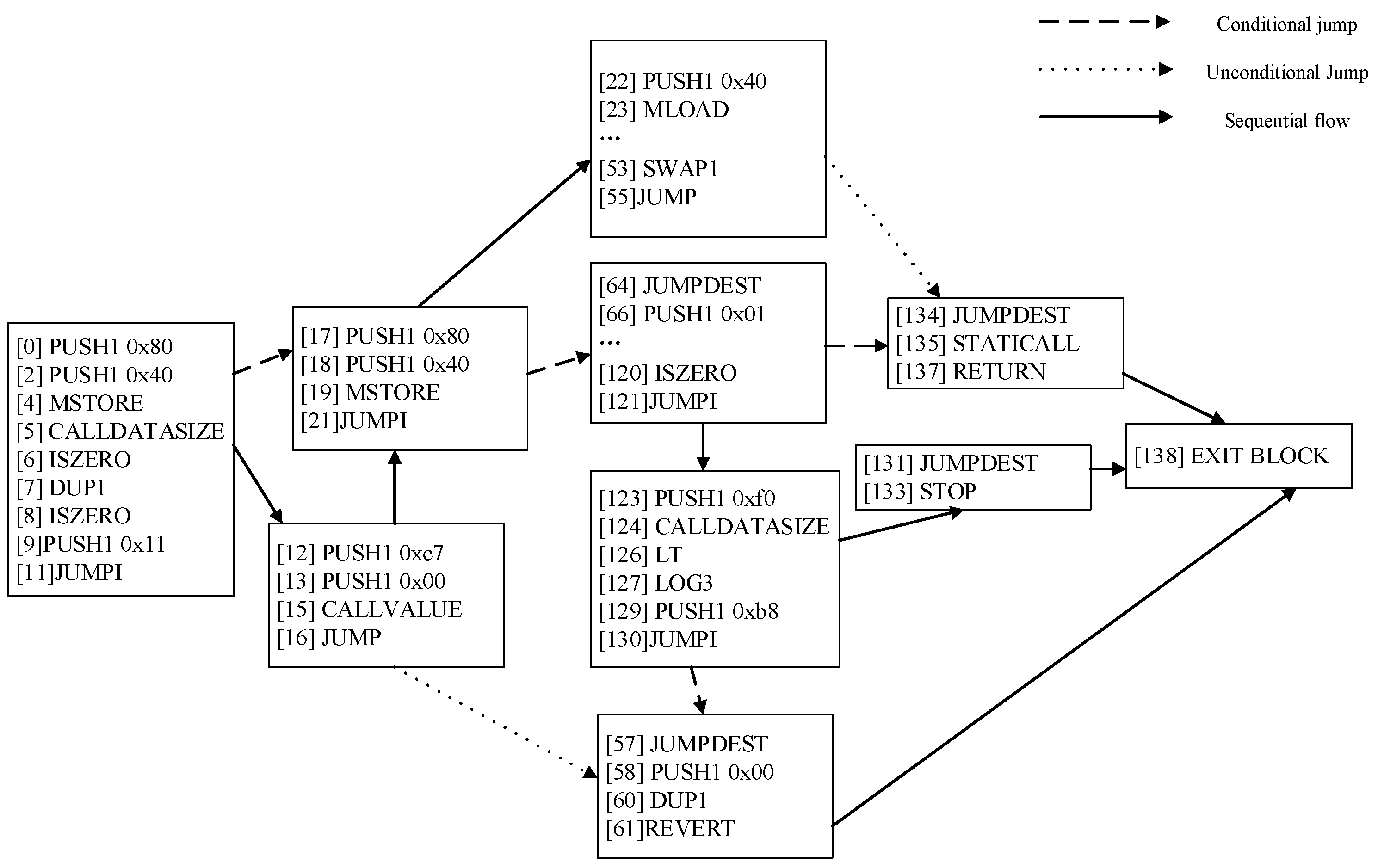
To enhance the representation of the binary code in smart contracts, a CFG is utilized, encompassing both data dependency and control relationships. The construction of the CFG entails a sequential process: initially compiling the source code of the contract and subsequently decompiling the bytecode to produce EVM opcode instructions along with their corresponding parameters. The illustrated process of compiling source code into opcodes is presented in
Figure 6.
The CFG is structured with basic blocks, each comprising instructions and their respective parameters. Basic blocks initiate with non-branching instructions and conclude with branching or terminating instructions (e.g., STOP, JUMP, JUMPI, RETURN, REVERT, SELF-DESTRUCT, etc.). The process involves decompiling the contract bytecode to form basic blocks. The interconnection of these blocks is established by parsing branching instructions (JUMP and JUMPI) within each block, forming the control flow graph of the targeted contract. Nodes within the contract and the edges between them constitute the CFG. The CFG representation is further characterized by two types of basic jumps: unconditional jumps, occurring when a JUMP opcode immediately follows a PUSH opcode, and conditional jumps, arising when a JUMPI opcode immediately follows a PUSH opcode. The resulting CFG is illustrated in
Figure 7.
Because nodes are closely related to each other in time, rather than isolated, in order to capture the semantic dependencies between nodes, we constructed three types of edges: conditional jump edges, unconditional jump edges, and sequential flow edges. Each node represents a basic block, and we used the set to represent all nodes in the CFG. The call relationships between nodes are considered as edges, and we used the set to represent all edges in the CFG.
Nodes within the CFG exhibit close temporal interrelations rather than isolation. To capture semantic dependencies between nodes, three types of edges are constructed: conditional jump edges, unconditional jump edges, and sequential flow edges. Each node corresponds to a basic block, denoted collectively as the set , representing all nodes in the CFG. The call relationships among nodes are portrayed as edges, forming the set , which encapsulates all edges in the CFG.
Following node partitioning and edge construction, achieving standardization of opcodes is essential for expressing the semantic information of the smart contract in the bytecode control flow graph. Uniform labels were assigned to the data following different opcodes to ensure consistency. The specific label for each dataset depends on the corresponding opcode. In alignment with the research by Zhang et al. [
5], we categorized the opcodes into six types based on the operand’s nature: arithmetic, block, logic, memory, storage, and bitwise. Refer to
Table 1 for the detailed classification.
Certain opcodes are succeeded by numbers indicating the byte length of the current operation data. Despite these length specifications, the precise length of the operation data corresponding to the opcode does not impact the semantic analysis of the bytecode. Therefore, it is crucial to simplify opcodes with operand lengths of this kind to maintain semantic consistency. Additionally, opcodes like DUP, POP, and SWAP, which directly manipulate stack data in the Ethereum Virtual Machine, have no practical impact on the semantics of smart contracts. Consequently, we opted to remove them. Refer to
Table 2 for examples of opcodes after normalization.
Various graph-based embedding methods, such as DeepWalk [
39], Node2Vec [
40], and GCNs (Graph Convolutional Networks) [
41], have been developed. In relevant studies, experimental results have indicated that GCNs, when applied to process smart contract graphs, adeptly integrate information from neighboring nodes. This integration allows node representations to comprehensively encompass the entire graph structure, rather than relying solely on local information from adjacent nodes. Moreover, a GCN has the capability to preserve the relative positions of nodes in the graph, maintaining the topological structure between nodes. This preservation of topological relationships is crucial for smart contract vulnerability detection, given that vulnerabilities are often closely tied to how nodes are interconnected. Consequently, we opt to utilize a GCN for embedding in the EVM opcode layer.
In the context of graph representation, if we denote the CFG as G, it can be expressed as
, where V represents nodes and E represents edges. By training the CFG using a GCN, we can derive embedded features for the graph. Each layer of the neural network can be represented by the following non-linear function:
where L is the number of layers in the network; the input layer is
, where X is the feature matrix; the output layer is
, where
is the node-level output;
represents the differentiable function of the neural network;
is the adjacency matrix of
. A GCN for graph classification utilizes both the intrinsic features of nodes and the structural information of the graph. The learning strategy is as follows:
represents the supervised loss for nodes with labels in the graph and is the loss introduced by the graph structural information. is a weight coefficient, and the ideal value for it is . is the node feature matrix and denotes the Laplacian operator of the graph.
Through the embedding process of the Graph Convolutional Neural Network, we can map the control flow graph of the smart contract to a low-dimensional vector space, enabling subsequent analysis and task processing in this vector space.
3.3. Extracting Dynamic Features of Smart Contracts
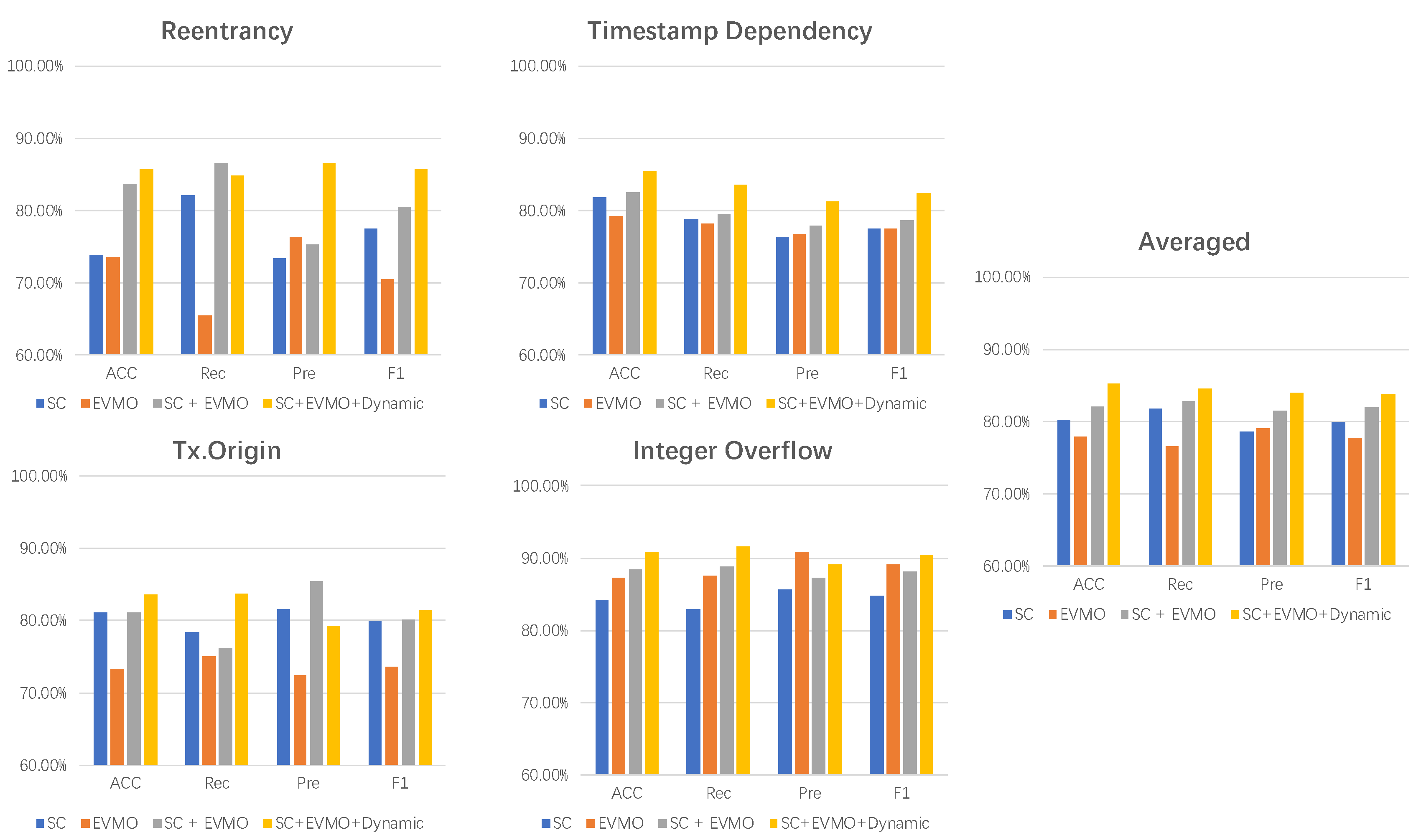
Dynamic detection of contract vulnerabilities involves the execution of the contract. In this paper, a dynamic detection pattern for vulnerabilities is designed. During runtime, the system examines the currently executing opcode, determines its type, detects the values of crucial variables in the stack based on this type, and then matches them with the designed dynamic pattern and critical variables. This process is conducted to assess whether the current smart contract exhibits a specific type of characteristic.
Transferring ether to an Ethereum contract account triggers the execution of the contract account’s fallback function. When sending Ether, the contract executes its corresponding fallback function. If a transfer operation is initiated to the address of an attacker’s contract, forcing the execution of the attacker contract’s fallback function, and if the fallback function contains a callback to the attacker’s own code, it leads to the execution of the contract “re-entering” itself. This type of contract vulnerability is known as a reentrancy vulnerability.
The distinctive characteristic of a reentrancy vulnerability is the sequence of transferring ether followed by the update of the contract state. To identify this vulnerability, we initially examine whether the currently executed opcode is CALL. Verification involves checking if the memory contains the address parameter of this opcode and if the position containing the amount parameter is not empty. A positive result indicates that the CALL opcode has indeed transferred ether to an external address, and we duly recorded this operation. Subsequently, we ascertained if the currently executed opcode is SSTORE. The presence of the SSTORE opcode signals the conclusion of the transfer operation and the impending update of the contract state, which prompted us to record this operation as well. Finally, we analyzed the sequence of CALL opcode occurrences in comparison to that of SSTORE occurrences. This sequence delineates the order of the transfer and contract state update. If the CALL opcode precedes the SSTORE opcode, it implies that the contract may be vulnerable to reentrancy attacks.
When smart contracts use block timestamps as triggering conditions for executing certain critical operations, a timestamp dependency vulnerability may arise. For instance, if the timestamp of a future block is used as a seed to generate a random number determining the winner of a game, a miner can exploit the vulnerability by freely setting the timestamp of future blocks within a short timeframe to manipulate the game’s outcome and gain illicit benefits. Attackers first analyze the target contract, identifying dependencies on timestamps within it. They then look for conditions in the contract that can be manipulated, such as controlling certain inputs or executing specific operations. These conditions may impact the logic related to timestamps. Once manipulable conditions are found, attackers execute malicious logic, potentially leveraging timestamps to carry out the attack.
The design concept of the dynamic pattern for timestamp dependency vulnerability is based on a scenario where the current contract uses a timestamp and transfers non-zero ether during execution. Firstly, it can be checked if operations related to the timestamp, such as TIMESTAMP, NUMBER, DIFFICULTY, etc., are called during execution. If these operations are not found, the contract will not be susceptible to timestamp dependency attacks. Next, it can be checked whether ether is sent via ‘send’, and verified if the contract has transactions with external addresses. If there is only a timestamp dependency without any loss of assets, the contract is considered safe. Finally, the operand at the corresponding position when executing the CALL opcode can be examined to ensure that the amount of ether transferred is not zero.
The tx.origin vulnerability is a type of smart contract security issue involving the misuse of the tx.origin variable. Attackers may exploit the tx.origin to carry out an attack, where tx.origin is a variable provided in Ethereum contracts to obtain the initiator of the transaction (original sender). After identifying the use of tx.origin in the target contract, attackers create a malicious contract and initiate a transaction through other legitimate contracts or external accounts while calling the target contract. In this transaction, the attacker sets their own address as that of a legitimate user. As the target contract uses tx.origin to verify the caller’s identity instead of msg.sender, the attacker successfully passes the verification and executes malicious logic.
One characteristic of the tx.origin vulnerability is the use of the tx.origin function to retrieve the calling information at the bottom of the stack. The detection pattern for tx.origin can be designed to check if the currently executed opcode is ORIGIN. If this opcode is not present during the contract execution process, then the contract will not be susceptible to tx.origin vulnerability attacks.
The smart contract integer overflow vulnerability is a security issue involving potential overflow situations during integer operations in a contract. Integer overflow occurs when the integer type (e.g., uint) in the contract exceeds the range defined for it during an operation. Attackers may exploit this overflow phenomenon to cause unexpected results, such as incorrect fund transfers or state modifications. Attackers achieve this by sending specific inputs or executing particular operations that cause the integer value in the contract to exceed its defined range, for instance, by using a sufficiently large value in an addition operation to cause overflow. Due to integer overflow, the computed result may become negative or wrap around to a smaller positive number. This can lead to failed conditional checks or erroneous fund transfers in the contract, granting the attacker undue privileges or assets.
The detection pattern for integer overflow vulnerabilities can be designed to check if the currently executed opcode is ADD, SUB, MUL, or DIV. Then, it can monitor the operands in the stack before the execution of the opcode. For each operand, it checks if its range could potentially lead to an integer overflow. For instance, if the operand is a 32-bit integer, it verifies if it falls within an acceptable range. Finally, it performs the actual check for integer overflow by comparing the value of the operand with the maximum and minimum values of its data type. If the operand exceeds the valid range, an overflow may occur.
Truffle is a popular Ethereum smart contract development framework. As shown in
Figure 8, We extracted its dynamic features by executing smart contracts within this framework. Executing a contract requires providing a set of inputs that conform to the specified parameter types and quantity. Based on the parameter types and quantity, input data is generated. Combined with the dynamic patterns designed above, we can monitor the specific type of the currently executed opcode and selectively obtain the operand at the corresponding position in the stack. Extracting dynamic features using dynamic patterns requires instrumenting the virtual machine at runtime. This is achieved by obtaining the value of key variables or the value at a specific position in the stack. The specific process of extracting dynamic features from smart contracts is shown in Algorithm 1.
| Algorithm 1: Dynamic feature extraction for smart contracts |
| Input: |
| prog: A Smart Contract Opcodes: |
| Output: |
| output: A Smart Contract Opcodes: |
| Begin |
| Let output be a list |
| if prog.has(CALL) && prog.has(SSTORE) && indexof(CALL) && indexof(SSTORE) then |
| update output |
| end if |
| if prog.has(Timestamp opcodes) && prog.CALL.hasDestination() && prog.CALL.ether !=0 then |
| update output |
| end if |
| if prog.has(Integer overflow) then |
| update output |
| end if |
| if prog.has(ORIGIN) then |
| update output |
| end if |
| return output |
| end |
For patterns closely associated with specific vulnerabilities, we utilized one-hot vectors to represent each pattern. The vulnerability detection patterns designed in this paper encompass four types. Consequently, we employ four binary flags for encoding, appending a binary digit (0/1) to each vector to indicate whether the tested function contains that pattern. In this approach, the one-hot vector for each smart contract signifies its dynamic features.