1. Introduction
The issue of containment control of multi-agent systems (MASs) has been a hot topic of research in the field of control since it was first proposed by Ren Wei for its advantages in ensuring the safe operation of cooperative systems [
1,
2]. Sensor-equipped agents are able to detect information about obstacles during movement, and the leader agents in the system are able to form a dynamic safety zone accordingly. With the control protocol, all follower agents interact and converge to the safety zone and follow the leaders in their movements [
3,
4]. Theoretically, in many scenarios where containment control systems cooperate in collision avoidance, only the collision avoidance constraints of the leader agents have to be taken into account for achieving collision avoidance of the whole system. However, in the practical collision avoidance problem, due to the action of various collision avoidance algorithms, such as the artificial potential field (APF) method [
5,
6,
7], the movement directions of agents when avoiding obstacles is random, and inevitably, variations in the relative position of the leader agents will lead to variations in the positions of the follower agents as well, thus causing the possibility of collisions between the followers, greatly threatening the safe operation of the system. Therefore, when analysing the performance of the system, in addition to the convergence speed of the system, discussed in a general control problem in [
8], in the containment control problem, the possibility of collisions within the system are also considered. In order to lower the risk of collisions between follower agents in the system, the follower convergence positions should be dispersed as much as possible, so that a safe distance can be maintained between the follower agents during collision avoidance, even if the leader agents’ positions are constantly changing.
In the case of the study on containment control issues, it can be noted that the factors affecting the convergence position of the followers can be divided into two parts from a system topology perspective: the F2F network topology, and the L2F network topology. Algebraic connectivity, as an important indicator to measure the capacity of a system, represents the convergence speed of the system. Many existing papers have investigated the relationship between algebraic connectivity and system topology [
9,
10]. In the containment control problem, owning to the non-linear properties of the algebraic connectivity of the F2F network topology itself [
11,
12], and the influence of the L2F topology on the system, the dispersion of the follower convergence position in the system also shows non-linear features, thus becoming difficult to obtain a relatively accurate performance identification model of the containment control system by mere mathematical modelling.
Neural networks (NNs) are superior in processing such non-linear, sophisticated modelling issues. Based on network topology theory, they have the ability to process information in parallel distributions, as well as intelligent and adaptive learning features, and has been widely used in the analysis of non-linear problems [
13,
14]. It is clear from the previous analysis that the convergence position of a follower is determined by the F2F and L2F network topologies, and that these two quantities show some correlation in the sequence, so recurrent neural networks (RNNs) are suitable for modelling the sequence for this problem [
15]. For processing sequence data, the characteristics of RNNs are the ability to transfer data information horizontally between neurons and to achieve partial preservation of the dependencies between sequences, and thus are widely used in various sequence-related problems [
16,
17,
18]. Thus, based on RNN, the identification results of the performance of the containment control system can be determined as the algebraic connectivity of the F2F network and dispersion of follower convergence positions in the system. In the problem of distributed control of a multi-agent system, the system usually needs to be temporarily networked based on the cooperative task requirements. When the system is large in scale, the process of establishing a containment control system that can meet the performance level requirements while ensuring that the agents in system are sufficiently distributed is very complicated. The addition of RNNs will greatly improve the networking efficiency of the system by enabling prediction of the situation by the end of the whole system networking only using the local information of the agents as the input based on the trained system performance identification model.
Alongside methods on the control side, improving the efficiency of system networking can also be considered an important aspect of communication. The polymorphic network [
19], proposed by Wu Jiangxing et al., is a full-dimensional defined smart network [
20], whose fundamental idea is to develop an opening network structure that separates the technical institution from the physical platform, such that diverse network technologies can co-exist in it, while dynamically loading and operating in a supported environment, to achieve intelligent deployment of network technologies and make them adaptable to a variety of specialized application needs [
21,
22]. The clustering system with polymorphic network architecture guarantees the self-improvement and development of the various system and network tasks, while enabling the intelligent, efficient, secure and integrated deployment and management of the diverse network [
23]. Thus, the polymorphic network provides an efficient and secure base network for the networking environment of MASs with novel baseline services such as multimodal addressing, routing control, transmission modes, computational processing, and so on. As the problem of efficient integration of the polymorphic network and MAS communication involved requires more theoretical support for information and communication [
24], while this paper focuses on the analysis of system performance from the perspective of identification models, only discussing a feasible idea here, and does not elaborate on the details of the polymorphic network.
In summary, the purpose of this paper is to apply RNN to the distributed identification of the performance of MASs to explore the networking process only using local information to achieve the performance prediction of the whole system when the networking is completed. In this paper, an RNN-based performance identification model for multi-agent containment control systems is developed by simulating and sampling data from the multi-agent containment control system topology and using the sampled data as learning samples for the RNN. The training converged model is implemented to identify the performance of the containment control system during the networking process. The RNN-based performance identification model is compared with a traditional MLP-based performance identification model and the identification accuracy of the different models is discussed.
3. Methodology
Inspired by the biological nervous system, neural networks (NNs) have various of computational models abstracted by simulating the mechanisms by which the human brain’s nervous system processes complicated information from the outside world. They have the capability to process parallel distributed information, based on network topology theory, as well as features of intelligence and adaptive learning. The characteristics of NNs are the neurons in the chosen structure and the connections between them, the choice of the activation function and how the weights are calculated according to the selected method. Neural networks combine the operating mechanisms of biological NNs with mathematical statistical models which are trained to enable them to have some decision-making or predictive capability. In this section, two types of NNs, the MLP and the standard RNN, are introduced.
3.1. MLP
The multi-layer perceptron (MLP), as a feed-forward NN, evolved from the perceptron. Its basic model structure consists of an input layer, a hidden layer and an output layer, where each node is a neuron possessing a non-linear activation function except for the input layer, as well as the number of hidden layers depending on the specific problem requirements. Typically, with all layers of the MLP fully connected to the next layer, the input layer can be considered a fully connected to the hidden layer, and the hidden layer to the output layer can be considered a classifier. The general structure of the MLP is shown in
Figure 1. The input layer is composed of input neurons, in which every neuron is connected with at least one other neuron of the hidden layer.
The structure of the MLP shows that each neuron in the same hidden layer is not connected to each other and information cannot be transferred between these neurons; thus, the MLP is a memoryless network, which is unsatisfactory when it comes to describing data with dependencies between sequences.
3.2. Standard RNN
In the existing studies, many types of NNs, such as MLP and convolutional neural network(CNN), are based on the premise that the various elements in the NN are independent from each other, including the inputs and outputs. However, in reality, many elements are connected, and such models do not provide an appropriate description of the true relationship between these elements. In RNNs, the neurons of the hidden layer are interconnected, through which time series inputs can be passed sequentially through the neurons in the hidden layer; therefore, the correlation of long-term events can be considered.
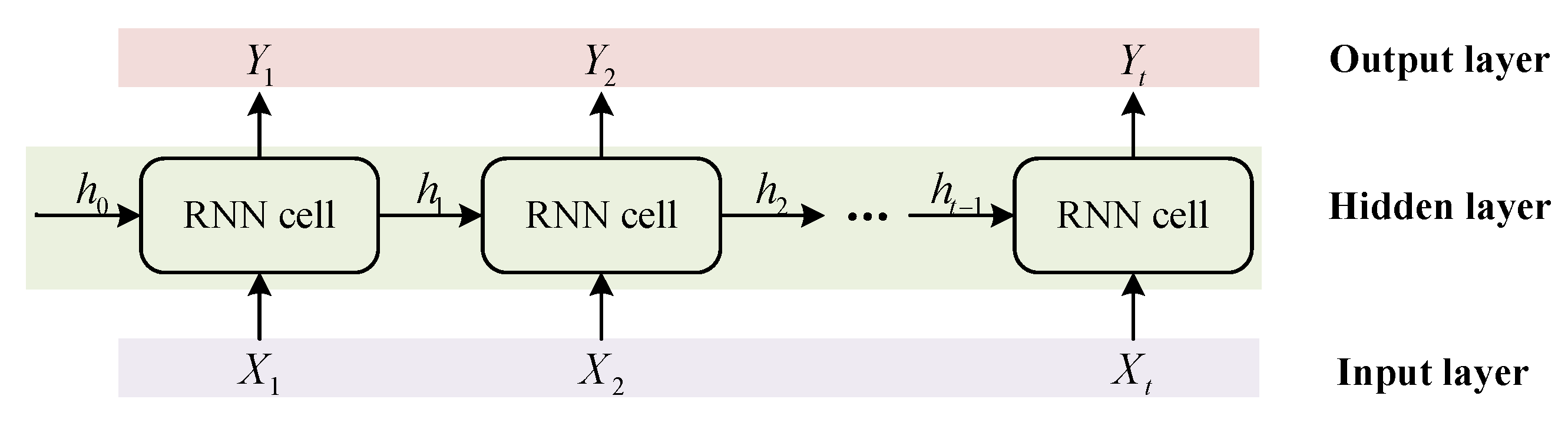
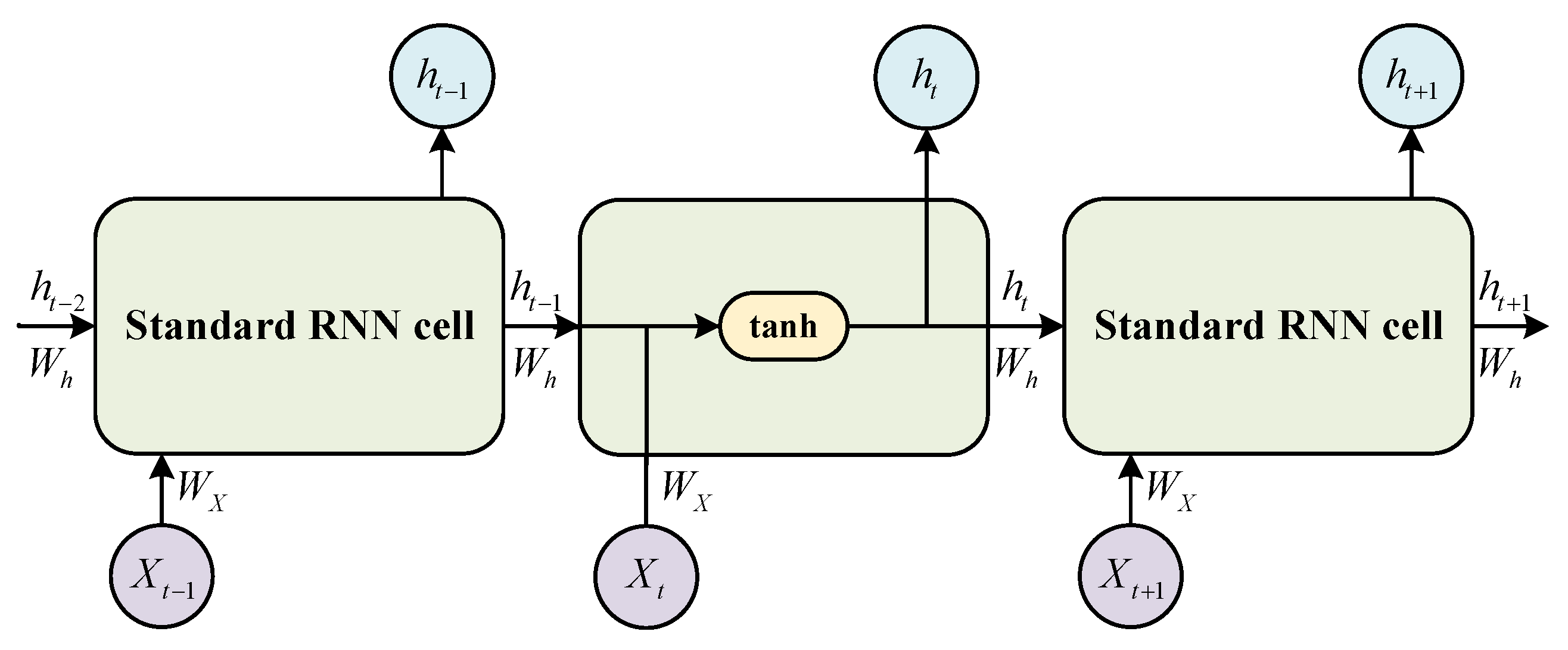
The structure of RNNs and standard RNN cells are shown in
Figure 2 and
Figure 3, where
denotes the input vector at time step
t,
denotes the hidden state output at time step
t, and
and
are the input and interconnected weight matrices for the output of the hidden layer, respectively.
Different from MLP cells, at time step t, the state output of a hidden layer cell is determined by at the prior time step , and then passed forward. This key design enables RNNs memorability.
4. Analysis of Multi-Agent Containment Control Systems Based on NN
In this section, the process of obtaining experimental data is described based on the multi-agent system containment control problem. As discussed previously, in terms of ensuring the system’s operational security and improving the efficiency of temporary networking, this paper explores the relationship between multi-agent containment control system topology and the dispersion of follower convergence locations in the system, as well as the forecasting of the whole system performance through the local information of nodes from the perspective of the distributed identification of the system. From Definition 3, it follows that in the containment control problems, holds when , where and denote the convex hull spanned by followers and leaders, respectively. To analyse the problem of multi-agent containment control on the basis of follower agent convergence in the two-dimensional plane, we define a function related to the convergence position to describe the dispersion of the follower convergence positions.
Definition 4. Let be a set in a real vector space , and be the gravity of the convex hull constructed by the follower converging positions. The dispersion of the follower convergence positions is denoted aswhere 4.1. Data
From the perspective of system topology, the degree metric of a node is very important as it represents the communication connectivity of the agents. As noted in [
27], nodes with more communication links hold a more important position in the system. Therefore, in the context of this paper, the following variables are chosen as indicators for the MAS performance identification model: the degree matrix of each node in the system (
D), the sum of degrees of the neighbour sets of each node (
), the sum of degrees of the neighbour set nodes of each node’s neighbours (
), the connection relationship matrix of the leader to follower agents (
), the algebraic connectivity of the F2F network (
), and the dispersion of follower convergence positions (
). The system topology studied in this paper is a hybrid form, comprising directed L2F topology and undirected F2F topology.
4.1.1. Network Topology of F2F
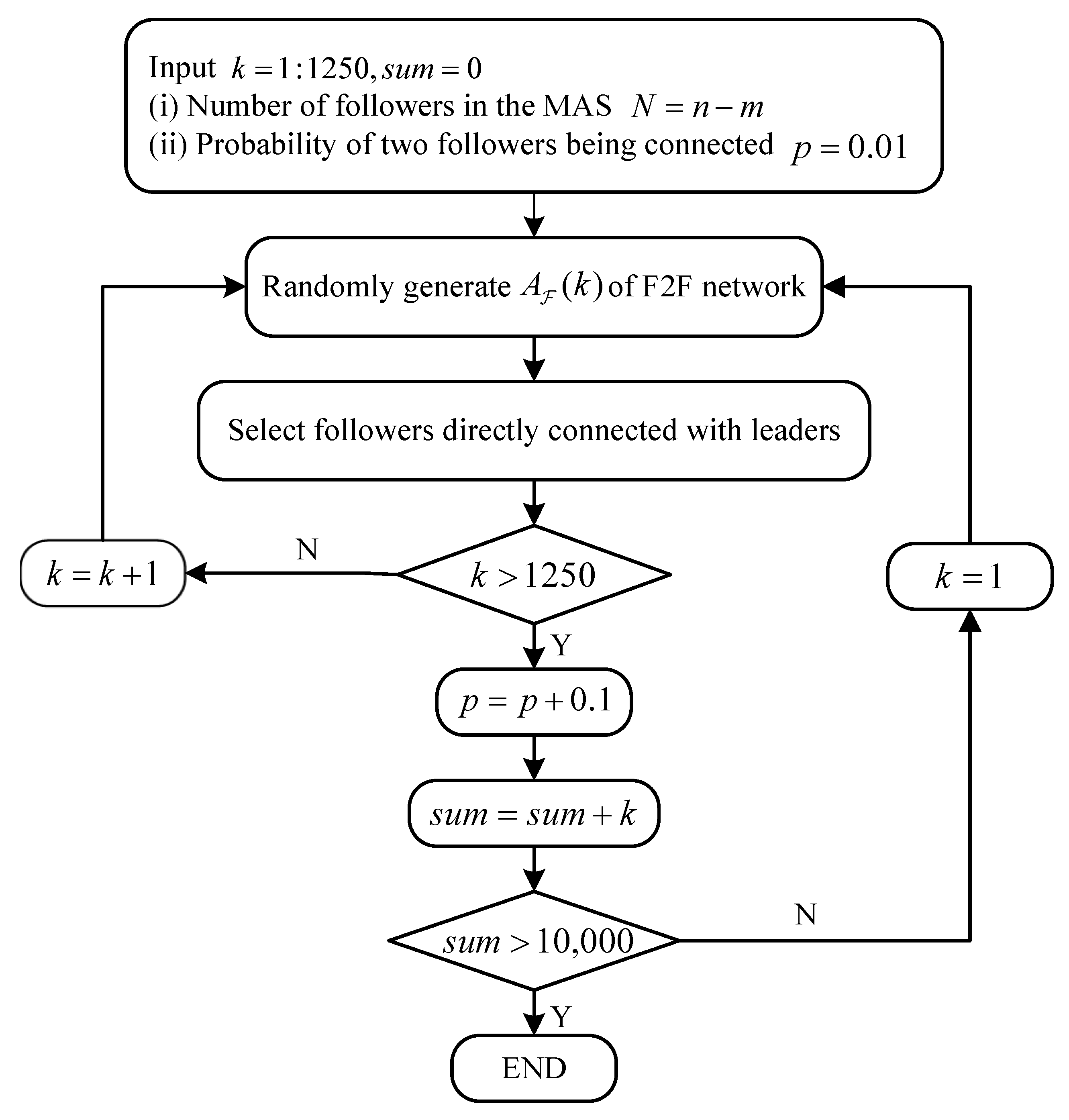
In this section, the direct simulation of Monte Carlo method (DSMC) is used to simulate the F2F topology in the containment control problem. The principle of simulating the adjacency matrix is based on algebraic graph theory, whereby communication links between real agents are replaced with finite numbers of randomly generated zeros and ones. The number 1 means that the two agents are connected while 0 means that they are not connected. In order to make the simulation stochastic, the following assumption is required.
Assumption A1. In a containment system, the probability that agents i and j are connected is p ().
In the experiment 10,000 simulations of
are performed with DSMC. A flow chart of the algorithm is shown in
Figure 4. The aim of setting the connectivity probability
p is to make the simulation sufficiently random, and simultaneously obtain as many types of topology as possible. The NN trained with these data will be more accurate in forecasting the system performance.
4.1.2. Network Topology of L2F
The F2F network is obtained in
Section 4.1.1. The follower agents that leaders directly communicate with are selected based on the system topology to obtain the containment system topology. In this paper, the algorithm for the selection of the follower agents is as follows:
Consider a containment control system with m leaders and followers, where the agent l has a set of active neighbours .
Step 1: The degree of each node is calculated and the r nodes with the smallest degree is selected as the set of alternative follower nodes ().
A situation may arise where there are several nodes with the same degree in the alternative node set, such that the number of nodes in the node set is greater than m. Further selection based on the alternative node set is then required to determine the follower agents with which the leaders directly communicates with. This is why Step 2 and 3 are necessary.
Step 2: Nodes with the smallest degree are selected as a priority. For follower nodes with the same degree, the sum of the degrees of each follower node in its neighbour set () are calculated, and the nodes with the largest sum of degrees of the neighbour set nodes are selected as the followers that the leader directly communicates with.
Step 3: According to the selection results of Steps 1 and 2, the sum of degrees of the neighbour set nodes calculate for each node’s neighbours (), and the node with the largest sum is selected as the followers that the leader directly communicates with.
Step 4: The leader and follower agents selected by the algorithm above are connected, generating the L2F network topology which in turn gives the complete topology of the multi-agent containment control system.
4.1.3. Calculation of the Relevant Indicators of System Performance
In this study the relevant computational indicators of system performance are the algebraic connectivity of the F2F network topology (calculated by algebraic graph theory) and the dispersion of follower convergence positions in the system (calculated using Definition 2).
4.1.4. Dataset for NN Training
In addition to investigating the relationship between the multi-agent containment control system topology and the dispersion of follower convergence positions in the system, in order to highlight the efficiency advantages of distributed identification in the process of system networking, all global information about the system, i.e., the whole system topology of the underlying F2F network, was hidden when constructing the dataset for the NN, and only local information about each agents is reserved, i.e., the sensing of the follower agents to the neighbour set of followers and the sensing of the leader agents to their directly communicating followers. Thus, in the dataset the local information of the agents in each system can be represented by a matrix of the following form
where
represents the input to the NN where the first row composed of ones and zeros describes the connection relationship between the leader and follower agents in the system,
indicates that the leader is connected to the
ith follower while 0 denotes no connection. The remaining three rows are vectors transformed from the node degree relativity matrix,
denotes the degree of the
ith follower,
denotes the sum of degrees of the neighbour set of the
ith follower, and
denotes the sum of degrees of the neighbour set nodes of the
ith follower’s neighbours.
The output of the NN
, i.e., the two performance indicators of the multi-agent containment control system in this study, can be expressed in the form of a vector as follows
4.2. Data Pre-Processing
The pre-processing of original data is divided into two parts:
- (1)
Removal of unconnected system topology data.
Since simulating the matrix by DSMC is completely random, a small probability of connectivity between agents is likely to lead to disconnection of the F2F network. In the context of this paper’s problem, there is no research significance in this part of the data. Since the F2F network is undirected, it can be directly determined whether the system is connected by calculating the algebraic connectivity of the system topology through algebraic graph theory.
- (2)
Data normalization.
In NN training, data normalization is essential [
28]. Different evaluation indicators as inputs often have different magnitudes and dimensions, which may affect the results of the NN training; hence, the purpose of normalization is to eliminate the effect of magnitude gaps between the input data. The normalized indicators are all of the same order of magnitude, speeding up the convergence of the model and minimizing errors in the training process [
29]. The min–max normalization method is used to normalize all data within the range of 0 to 1. The formula for normalization is given by
where
x represents the original data,
represents the normalized data, and
and
are the minimum and maximum values of the entire original data set, including data from the training and test sets, respectively.
4.3. Development and Implementation of the System Models Using NN
Keeping the simulation method of the containment control system topology as described in
Section 4.1 unchanged, two types of distributed identification models of system performance are proposed and investigated. The inputs to the models are the local information from agents and the outputs are the performance indicators of the systems. In each system, only the number of input features is different, all other features remain the same. According to the information range for identifying the system performance, two types of identification models were proposed, one only based on the node itself and the neighbour set nodes, and the other based on the node itself, the neighbour set nodes and the neighbour set nodes of its neighbours. Details of the variables in the two models are given in
Table 1.
The forecasting model for system performance identification was created using a portion of the pre-processed data from
Section 4.2 as the training dataset. The size of the dataset for the models is shown in
Table 2, where
denotes the number of connected system topologies and
denotes the number of follower agents in the containment control system.
In this study, a two-layer feed-forward network with sigmoid activation functions for the hidden layer neurons and linear activation functions for the output layer neurons is chosen. When training the NN, the network weights are updated by the Levenberg–Marquart (LM) backpropagation algorithm, possessing the fastest training speed for medium-sized NN training. The coefficient of determination (
) and RMSE are employed to assess the forecasting performance with the following equations
where
denotes the
ith forecasting value,
denotes the corresponding true value,
denotes the mean of the true values, and
denotes the total number of samples.
The parameters selected for NN training based on the models employed are given in
Table 3. Training of the NN was implemented in the MATLAB programming environment.
4.4. Results and Discussions
In this subsection, the performance of the multi-agent containment control system is investigated using two NN models, MLP and standard RNN, and the two types of distributed identification models for the system performance proposed in
Section 4.3 are compared. In order to assess the forecasting performance of the distributed system identification models based on NNs, two system identification models are trained with MLP and standard RNN, and the system performance indicators (
and
) are forecasted through test sets with the parameters given in
Table 3. To enhance the forecasting accuracy of the model, data for the learning and testing sets are determined separately by random sampling before the training starts. Measurements of the forecasting performance for the identification models based on the two NNs for the system are given in
Table 4.
In the context of multi-agent containment control system performance identification, compared to the MLP-based model, the proposed standard RNN-based Model 2 performed well in terms of prediction accuracy at the cost of a larger CPU training time. The standard RNN-based Model 2 had a greater prediction accuracy than the two MLP-based models, increasing the
of the two indicators to 0.9639 and 0.9453 and decreasing the
to 0.0389 and 0.0400, respectively, as shown in
Table 4. Furthermore, compared to the two MLP-based models, the CPU training time of the proposed standard RNN-based Model 2 increased by 4 and 2 times, respectively.
4.4.1. System Performance Forecasting with Model 1
Depending on the range of required information for distributed system identification, two system identification models are proposed in
Section 4.3, i.e., one only based on the node itself and the neighbour set nodes, and the other based on the node itself, the neighbour set nodes and the neighbour set nodes of its neighbours. System identification also includes the process of selecting leaders which directly communicate with followers based on the followers’ local information, as described in
Section 4.1.
In this study, the containment control system is composed of 12 agents with 3 leaders, and the F2F network consisting of 9 follower agents. The position vectors of the three static leaders with fixed positions are
,
and
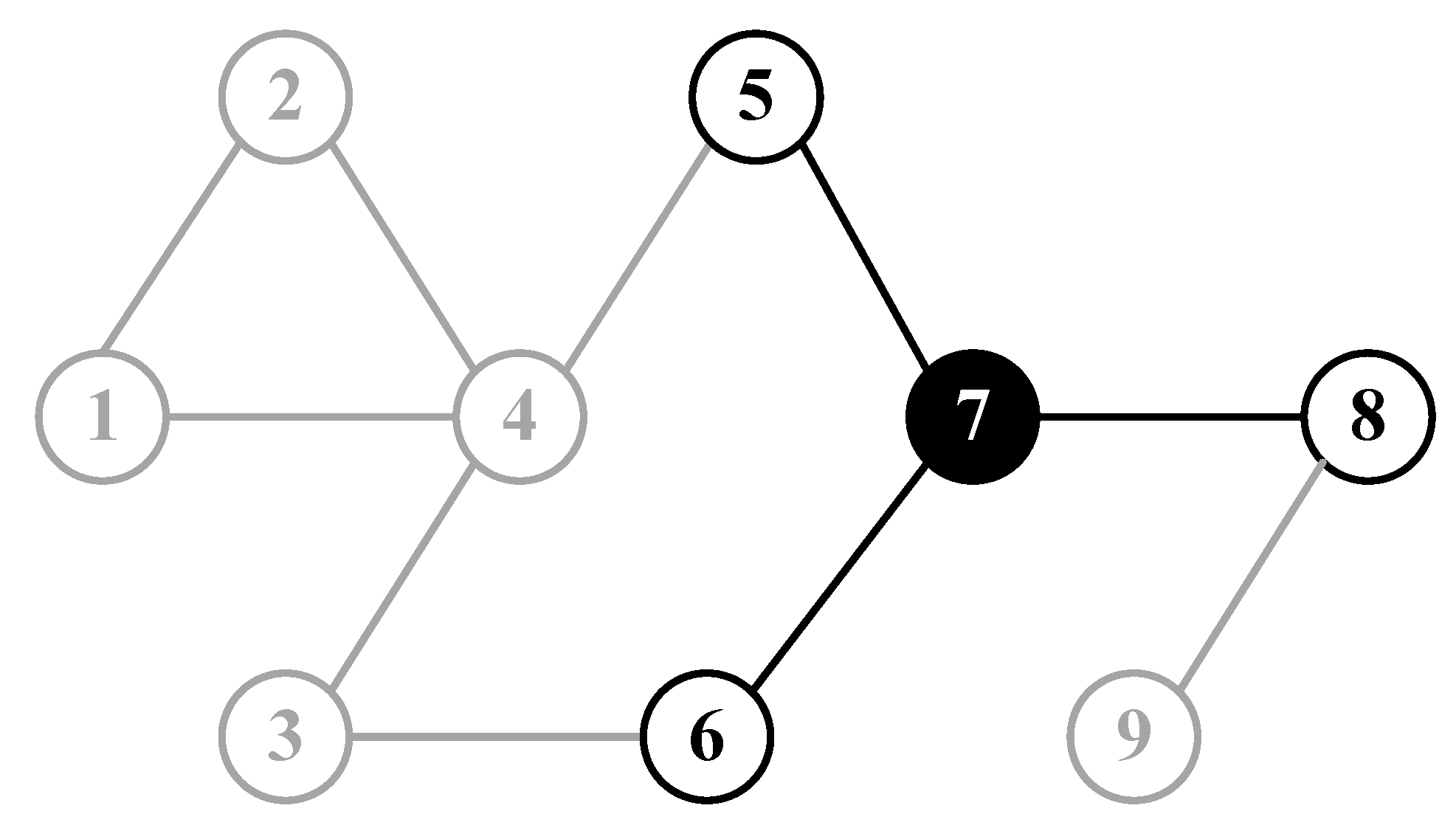
. Take node 7 for example, in Model 1, the range of identification information of node 7 is shown in
Figure 5, including its own information about itself (agent 7) and information about the neighbour set (agent 5, 6 and 8). The input matrix
corresponding to this system is as follows
where the first row denotes the communication links from leaders to followers, i.e., leader 1 (agent 10) connects to follower 1 (agent 1), leader 2 (agent 11) connects to follower 5 (agent 5) and leader 3 (agent 11) connects to follower 9 (agent 9).
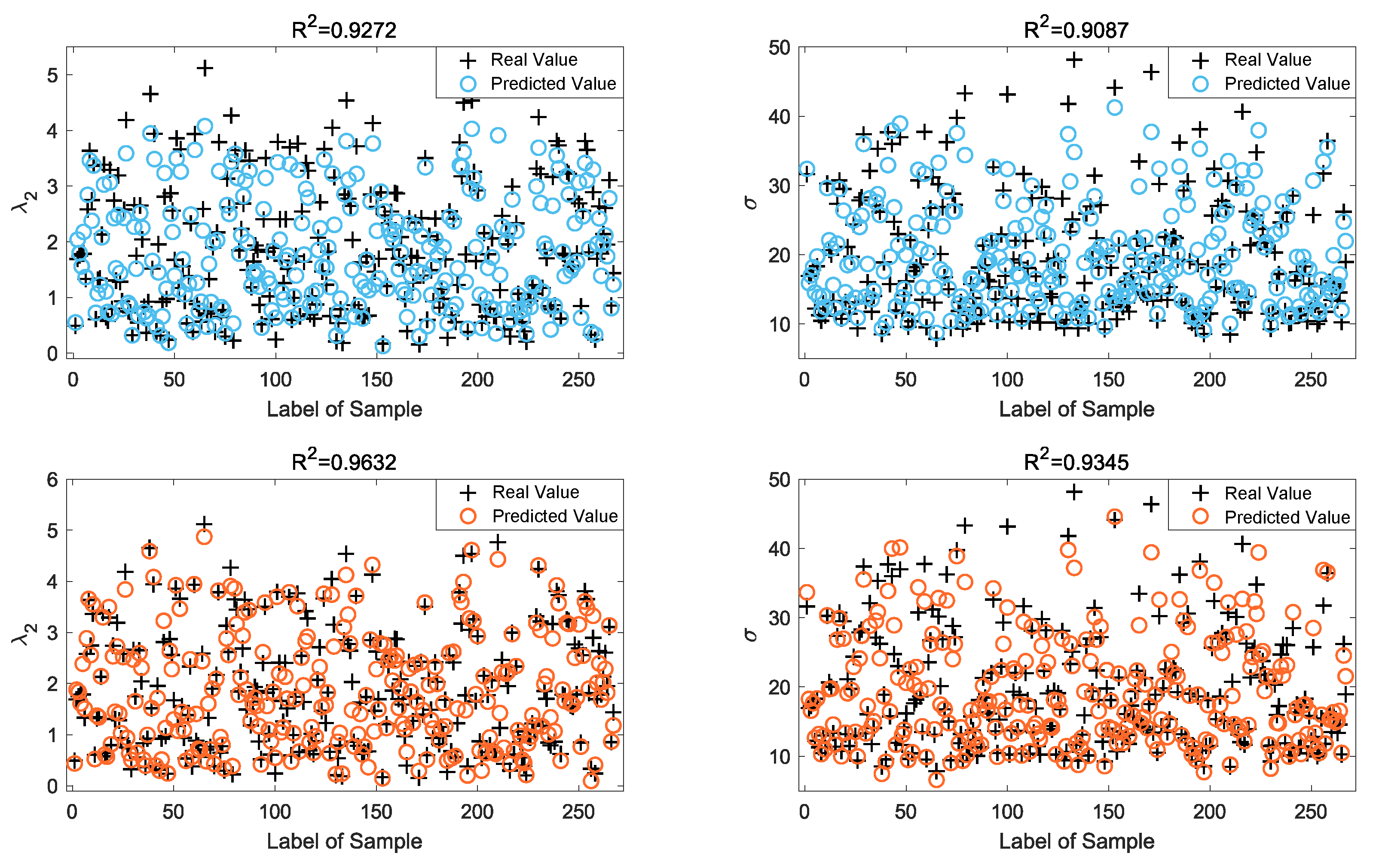
A total of 5340 sets of randomly generated sample data from the containment control system topology after pre-processing are employed in this paper. The scatter plots of the experimental samples of the testing dataset and the predicted values of
and
are shown in
Figure 6, where the upper two figures are the MLP forecasting results and the lower two figures are the standard RNN forecasting results. The results of the system performance identification denoted by the predicted values are evaluated by
and RMSE, as seen in
Table 4. It is clear that the model outperforms in terms of in-sample predictions of system performance,
and
, and for Model 1, the standard RNN performs better than the MLP in system performance identification.
4.4.2. System Performance Forecasting with Model 2
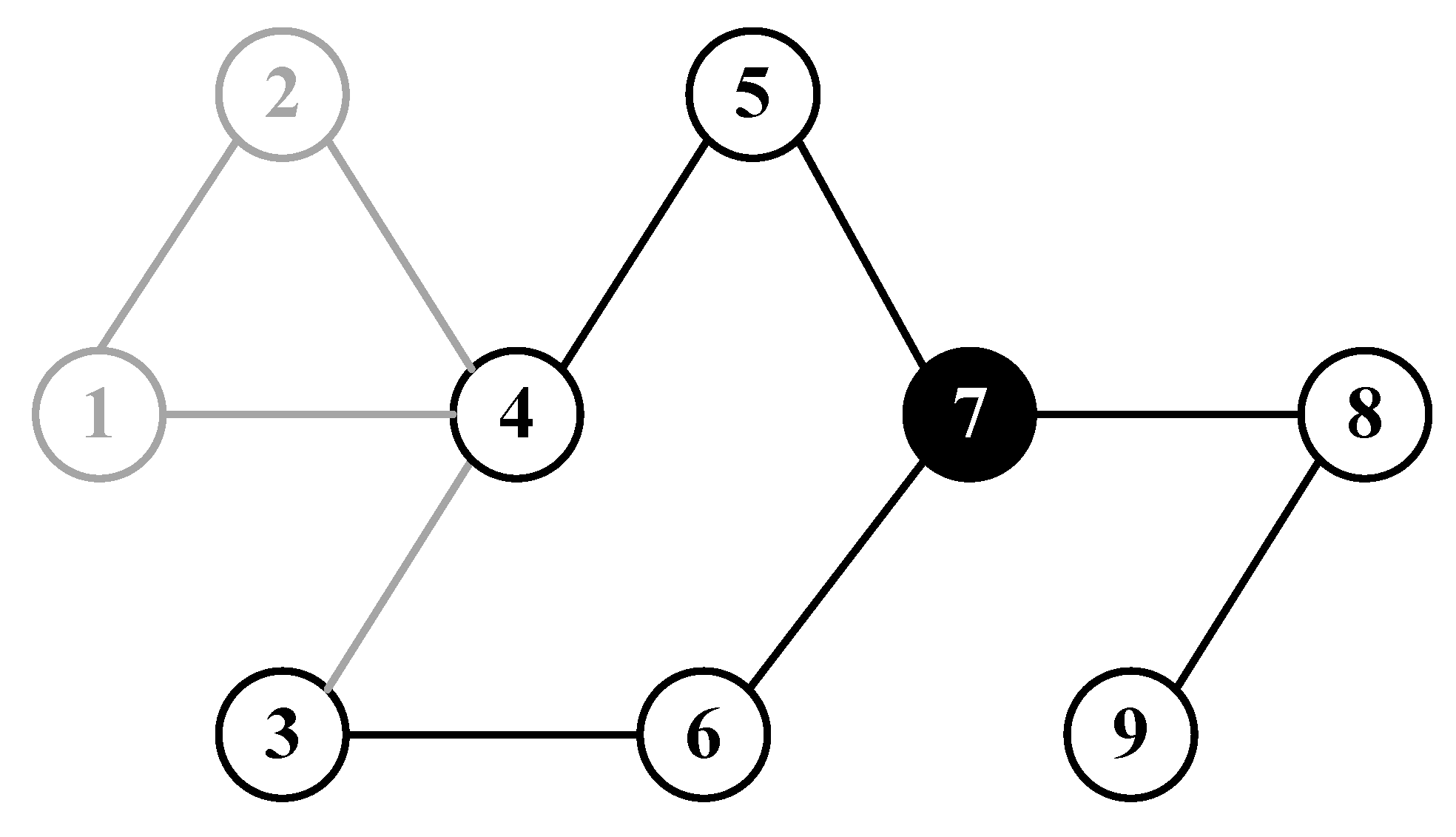
Similarly, the containment control system is composed of 12 agents with 3 leaders, and the F2F network consisting of 9 follower agents. Take node 7 for example, in Model 2, the range of identification information of node 7 is shown in
Figure 7, including information about its own (agent 7), information about the neighbour set (agent 5, 6 and 8), and information about the neighbour set nodes of its neighbours (agent 4, 3 and 9).
where the first row denotes the communication links from leaders to followers, i.e., leader 1 (agent 10) connects to follower 1 (agent 1), leader 2 (agent 11) connects to follower 5 (agent 5) and leader 3 (agent 11) connects to follower 9 (agent 9).
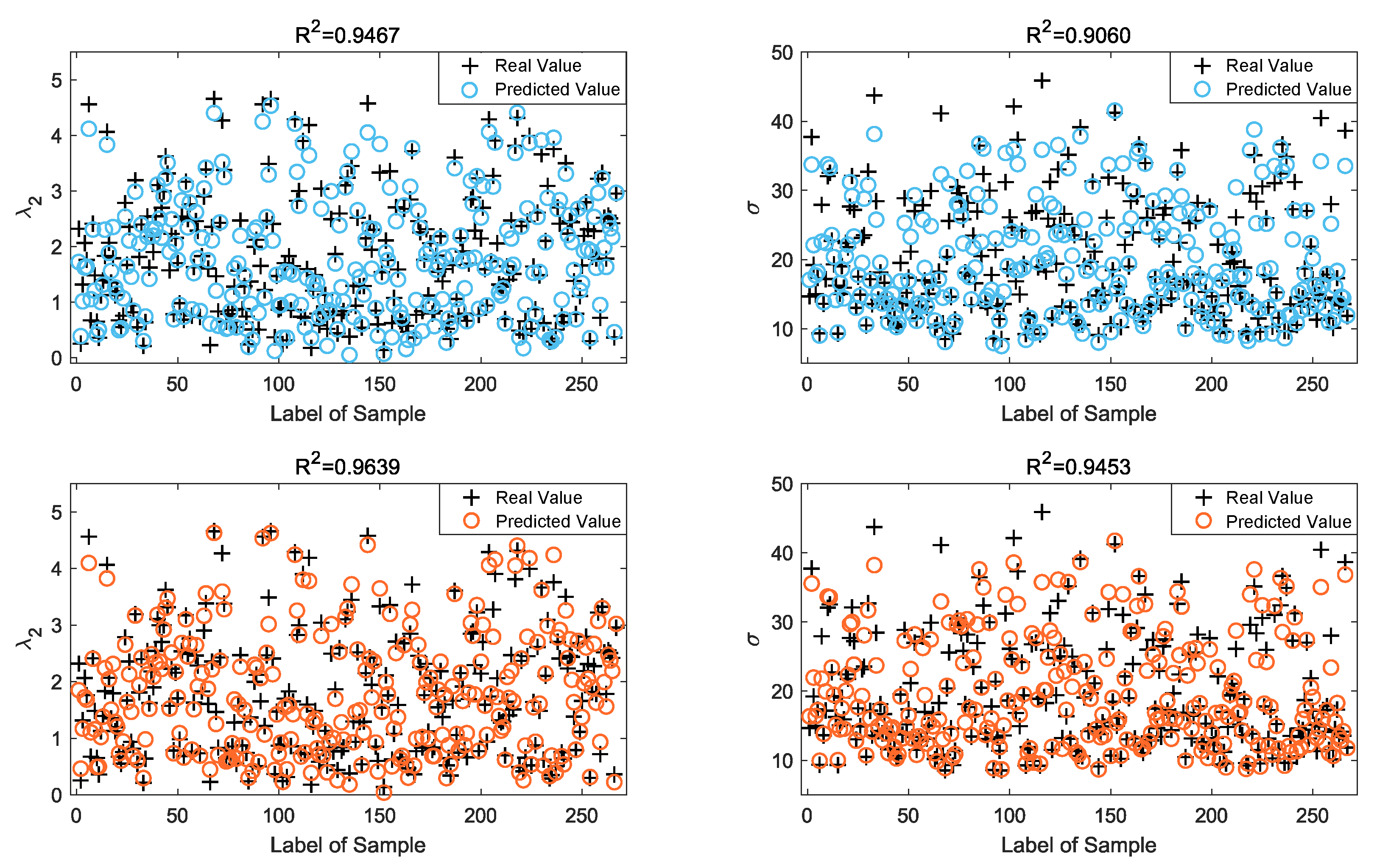
A total of 5340 sets of randomly generated sample data of the containment control system topology after pre-processing are employed in this paper. The scatter plots of the experimental samples of the testing dataset and the predicted values of
and
are shown in
Figure 8, where the upper two figures are the MLP forecasting results and the lower two figures are the standard RNN forecasting results. The results of system performance identification denoted by the predicted values are evaluated by
and RMSE, as seen in
Table 4. It is clear that the model outperformed in terms of in-sample prediction of system performance,
and
. For Model 2, the standard RNN performs better than the MLP, and the forecasting performances of both types of NNs based on Model 2 are better than Model 1.
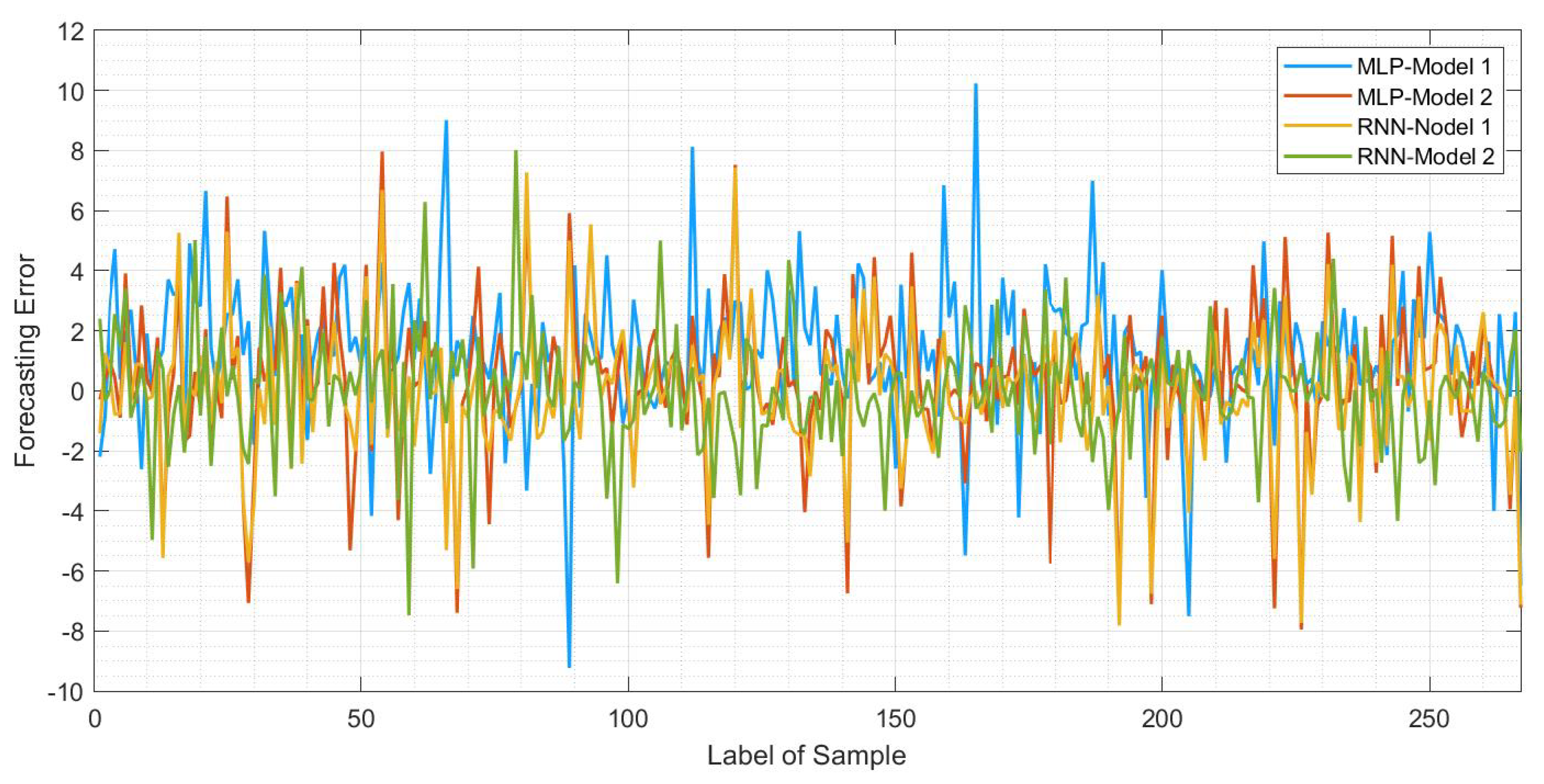
Forecasting error curves of the follower convergence positions
by four types of models for system performance identification are shown in
Figure 9, with 267 samples included in the forecasting. It shows that each model gives a better forecasting accuracy than the other models in specific cases, resulting from the strong non-linearity of the system topology and the algebraic connectivity. From the experiments the results show that the standard RNN-Model 2 has the smaller errors in most cases, but it can only ensure the accuracy of the forecasting in a limited range as there are still some points where the errors increase suddenly.
Figure 8 shows that the prediction of the model is accurate only in a relatively limited range,
and
, beyond which the error tends to increase. Therefore, further development of the model is necessary to improve its forecasting accuracy, and optimize and supplement the sample datasets.
4.4.3. Limitations
The potential limitations of the study can be considered from the aspect of practical applications.
Figure 6 and
Figure 8 show that when
increases to a certain level, such as beyond
, the forecasting accuracy error tends to increase. This is the limitation when applying our research to practical containment problems, because in practice a greater
is preferred as the followers are more dispersed in the convex hull spanned by followers, and the risk of collisions between followers is lower. In this paper, the prediction accuracy is not yet guaranteed over these large ranges. Such a limitation would not affect the generalizability or validity of the results in this paper, but in further research, based on the forecasting accuracy of
for greater ranges, there is still a requirement to make some improvements to the performance identification model.
4.4.4. Suggestions and Recommendations
The further developments and optimizations suggested to improve the accuracy of the model identification include:
- (1)
Optimization of the extraction methods for containment control system features. As shown here, the L2F networks are constructed according to certain F2F network to obtain the complete containment control system topologies; therefore, all works extracting system feature information are based on these. The aim of this construction is to describe the containment control system from the perspective of graph theory. There might be better ways to construct the L2F network topology and extraction methods for containment control system features.
- (2)
Modelling systems based on better-performing NNs or hybrid NNs. Two identification models based on two types of relatively simple NNs are verified in this paper. The prediction results are still partly inaccurate due to the disadvantages of MLP and RNNs; therefore, some better-performing NNs and hybrid NNs such as LSTM, GRU, and their hybrid forms, may improve the accuracy of model identification.
The second point is feasible but the first point might not be that easy. This is because when extracting the features of a containment control system, how the connections from leaders to followers affect the final converging positions of the followers is hard to identify due to the coupling of and when calculating the follower converging positions. Therefore, this would be a great challenge to implement.
The generalization of the findings to different containment control system types and scales is good and the proposed RNN-based model could be applied effectively to other MASs with similar characteristics. In this paper, a method to simulate a certain scale of containment control system and a method to extract the system information to form a new matrix based on an F2F network topology are provided. These methods could be applied to any system scale in which the communication links could be represented with a topology construction. Containment control problems are relatively unique issues because of the effect of leaders on followers. When applied to other MASs with similar characteristics, the proposed RNN-based model would be more simple without the need to consider the leader to follower communication links. In summary, the proposed standard RNN-Model2 is able to forecast the performance of distributed system identification based on the local information of the agents, greatly facilitating the system’s networking efficiency when applied to large-scale unmanned system networking.
5. Conclusions
NNs are powerful tools for coping with non-linear, complex modelling problems and have unique advantages in model identification, forecasting and control of complex systems. In this research, two types of system performance identification models based on two types of NNs, MLP and standard RNN, were developed for a multi-agent containment control system, according to the range of information required for identification, and the identification results of these models were then compared. The results show that the RNN-based model is overall more accurate than the MLP-based model for the performance identification of the multi-agent containment control system. Although this study was conducted for a containment control system with 12 agents, the proposed standard RNN-based Model 2 could be applied to various types and scales of containment control systems based on the local information of the agents to precisely forecast the results of distributed system identification. However, to further improve the accuracy of the model identification more in-depth development of the model is required, as well as optimization and supplementation of the dataset samples. By applying this RNN-based system performance identification model to the networking process of large-scale systems, the goal of improving the efficiency of system networking could be achieved by only using local information to forecast the performance of the whole system when the networking is completed. This study may also provide solutions to other model identification problems concerning MASs cooperative networking.