Correlations in Quantum Network Topologies Created with Cloning
Abstract
1. Introduction
2. Approximate Quantum Cloning Machines
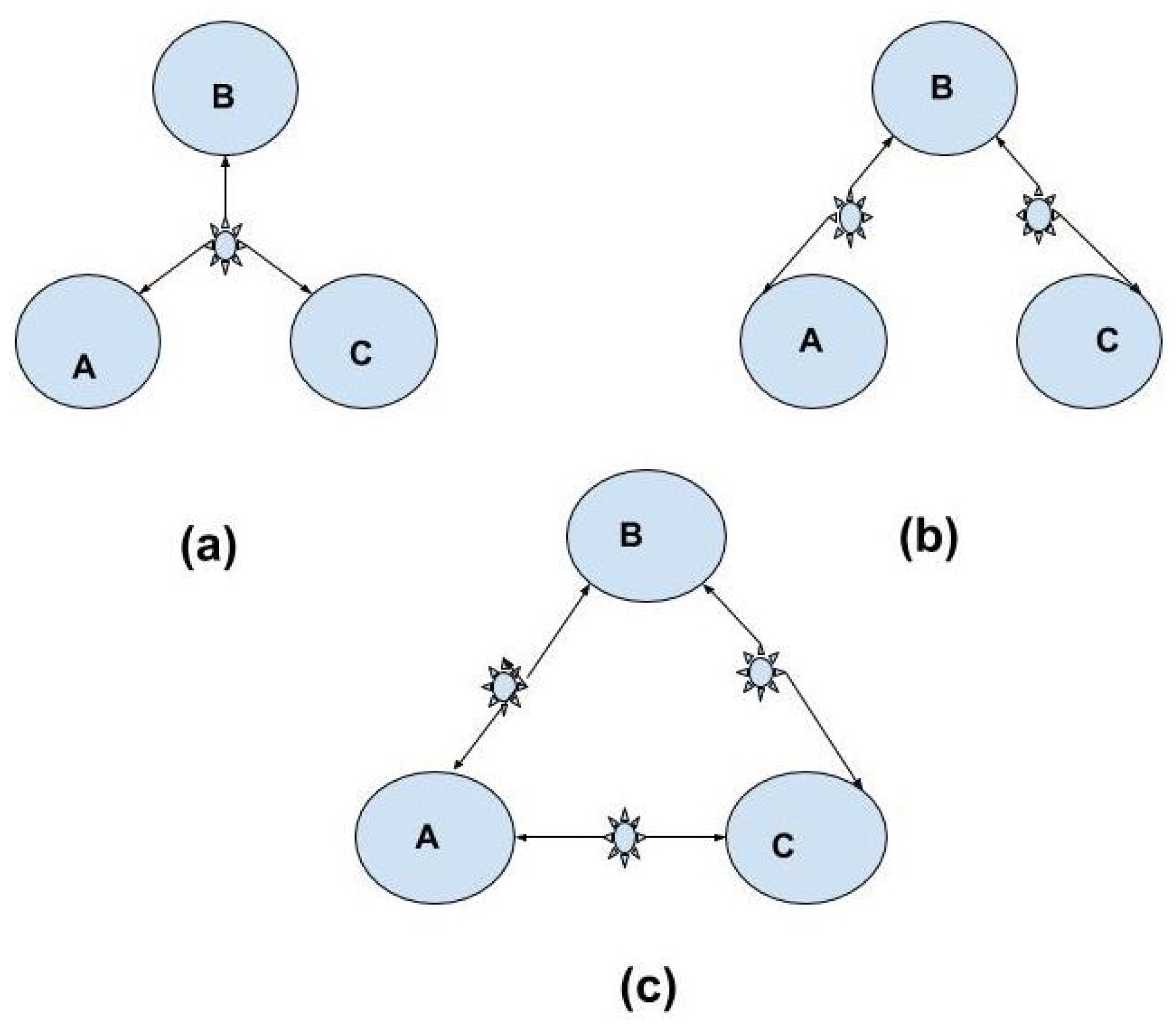
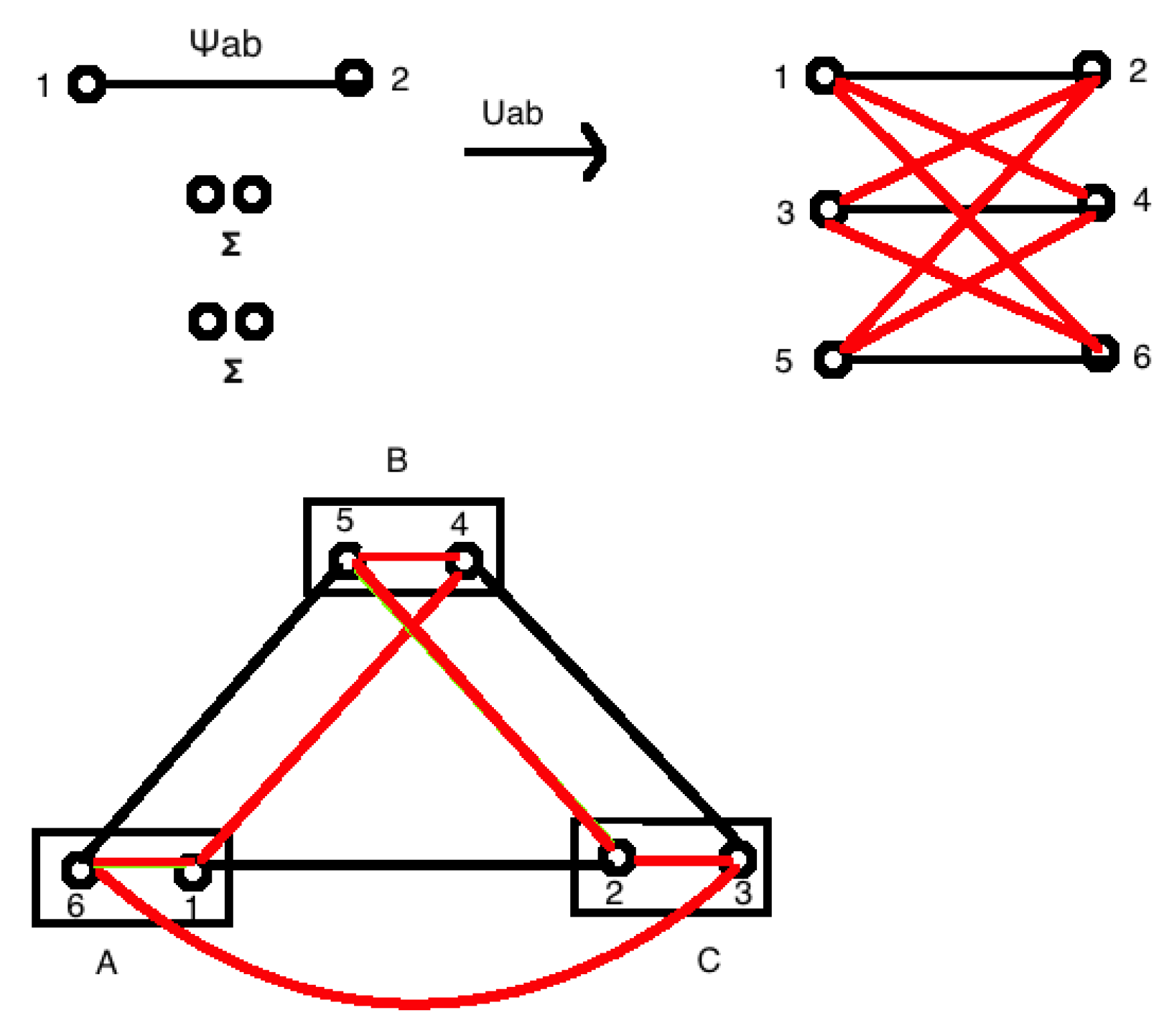
3. Three-Party Quantum Networks and Bounds and the Quantum Finner Inequalities
- For three observers, we can have three inequivalent networks. The first of the kind, shown in Figure 1a, is of a single common source communicating a quantum state to each of these three observers. We can see that any possible distribution can be obtained in this case. In fact, it is enough to restrict ourselves to classical sources here. The set of possible attainable distributions is nothing but the whole probability simplex with the normalization condition .
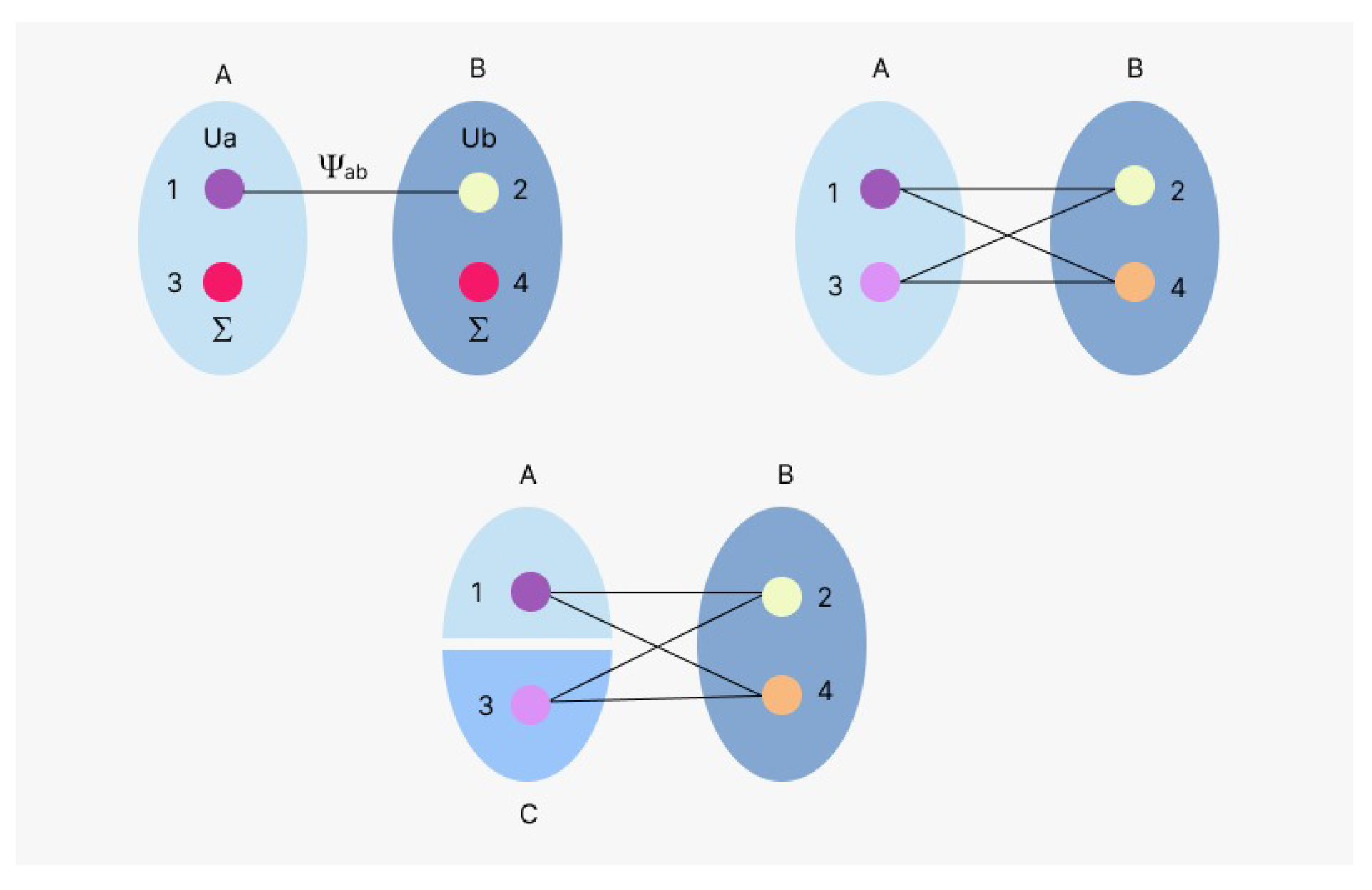
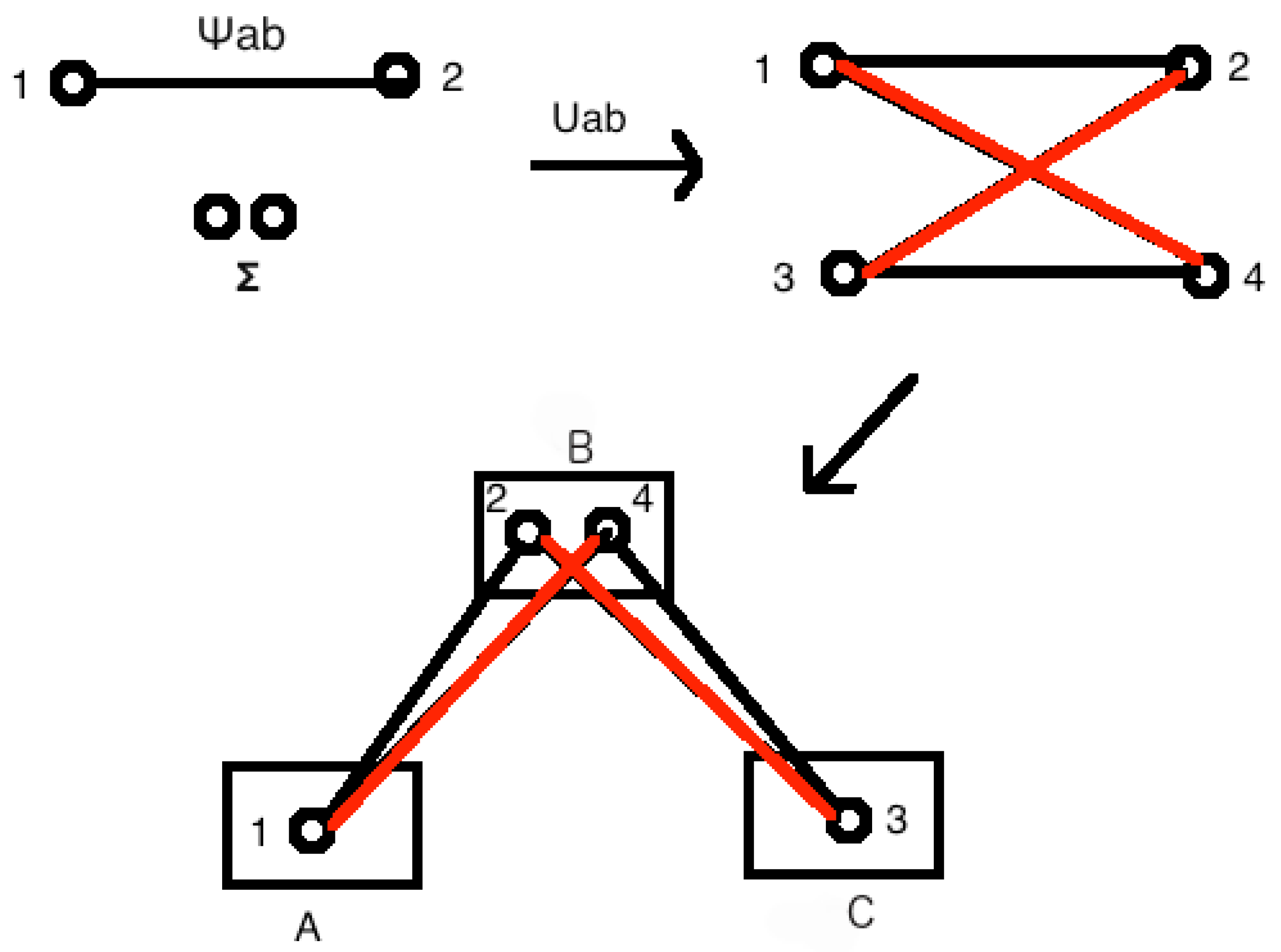
- Next, we consider the case when the triangle network is created by two independent sources, as in Figure 1b. One of the sources distributes a common state to the parties A and B while the other gives it to B and C. This is called a bi-local network. The interesting part of this network is that observers A and C are initially independent; however, they can be made to be correlated to each other through B. If we remove the node B from the network, these two become completely independent. To test the independence, we have the following condition [63]:
- Lastly, we have the most interesting and challenging three party network which is the triangle network [see Figure 1c]. This can be obtained from bilocal network by adding a source connecting A and C. Because of this additional source, there is no need for the independence condition as it no longer holds.
4. Three Party Networks by Cloning
4.1. Three Copies of Single Qubit
4.2. Local Cloning of Entangled Pair: Bi-Local Network
4.3. Bi-Local Network: Non Local Cloning
4.4. Triangle Network: Non Local Cloning
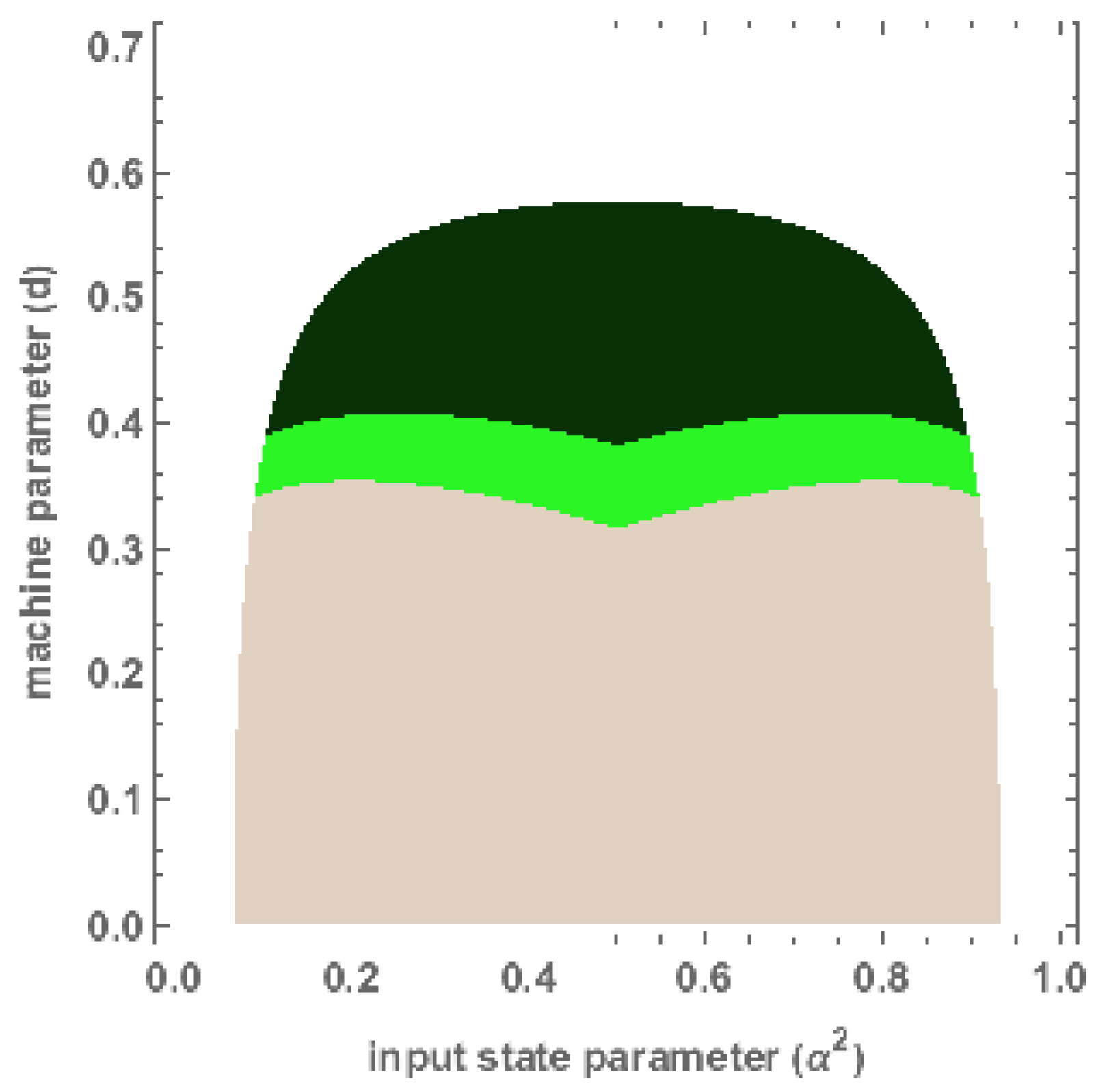
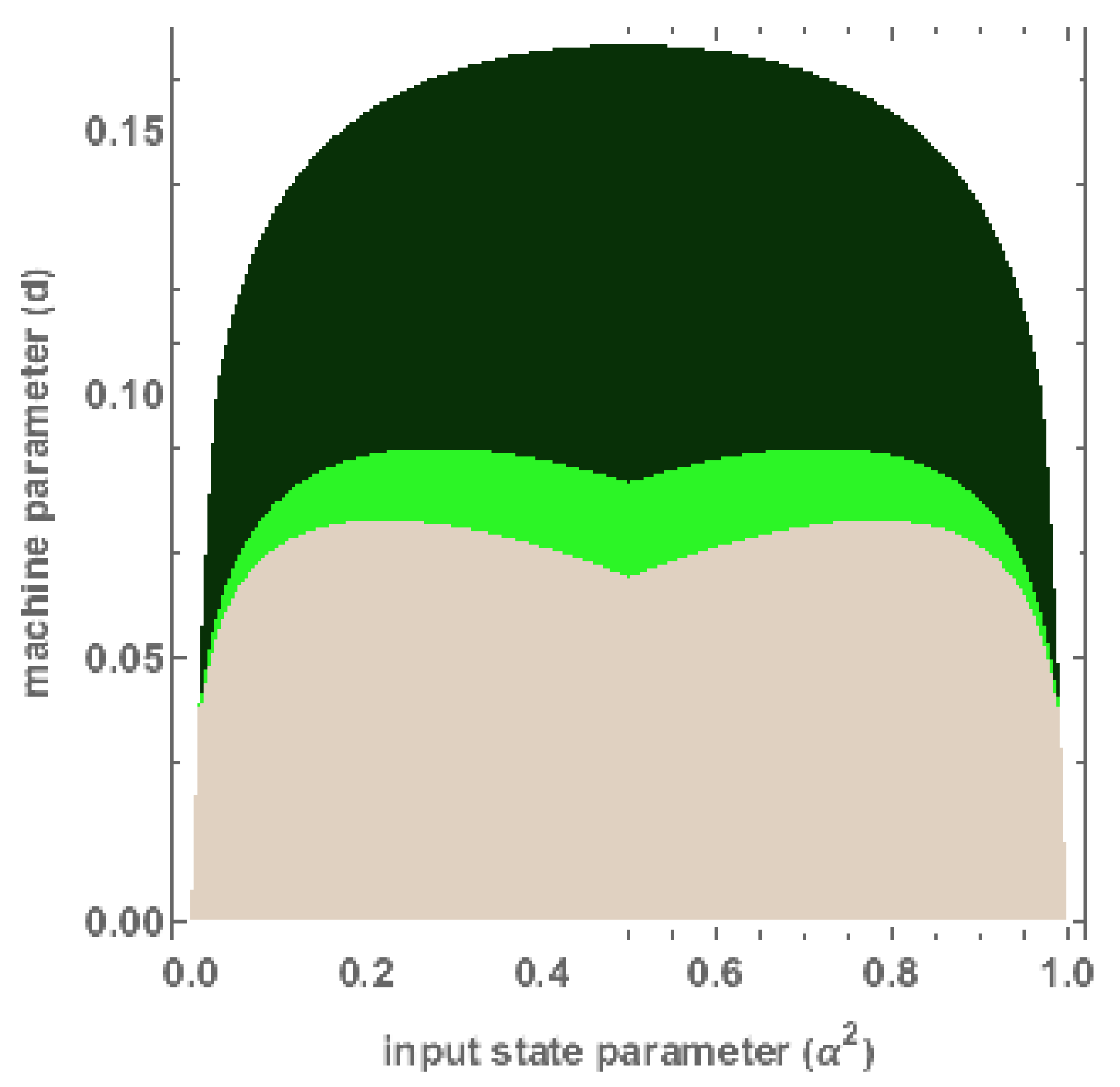
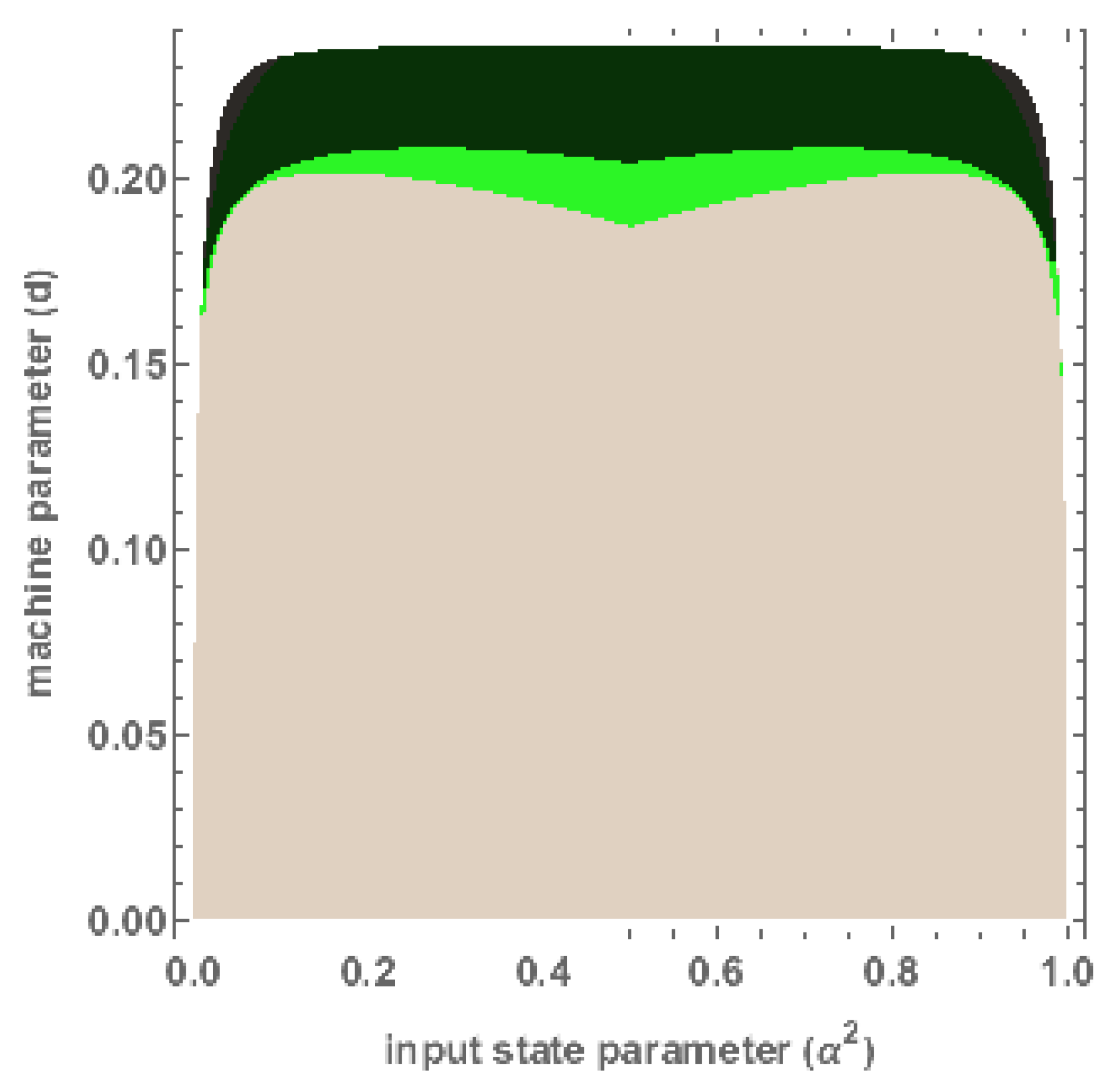
5. Witnessing Entanglement in Triangle Networks
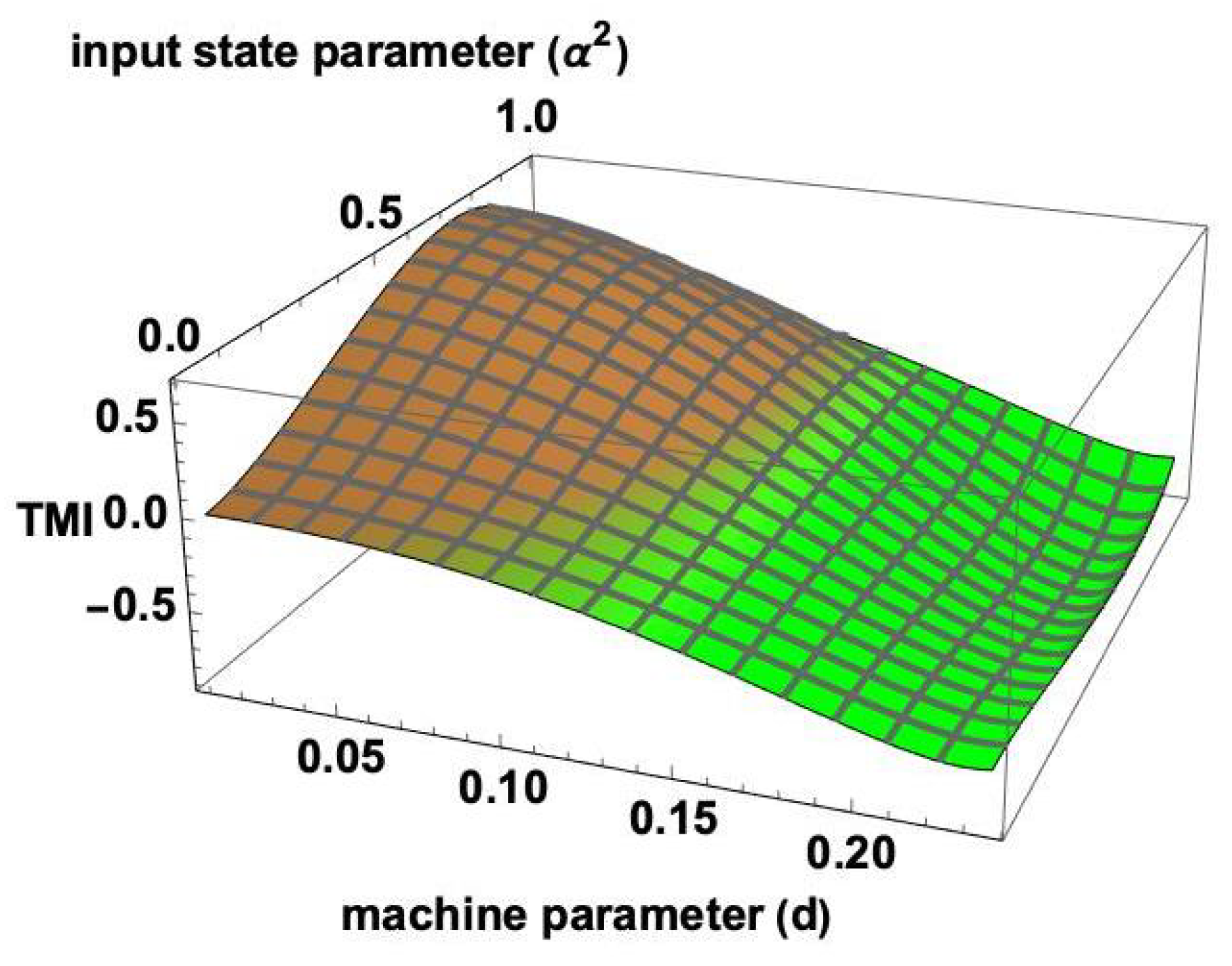
- = 0 for any . Here, I represents tripartite mutual information given byIntuitively, this means that there is no shared classical mutual information within the subsets of the quantum states owned by the parties A, B, and C, respectively.
- Let be an entanglement measure that is additive on tensor products and monogamous. For any , we have that holds for all the bi-partitions , , and . The intuition here is that the entanglement on the bi-partition should be equal to the sum of the entanglement in the reduced states, i.e., and .
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Einstein, A.; Podolsky, B.; Rosen, N. Can Quantum-Mechanical Description of Physical Reality Be Considered Complete? Phys. Rev. 1935, 47, 777. [Google Scholar] [CrossRef]
- Heisenberg, W. Über den anschaulichen Inhalt der quantentheoretischen Kinematik und Mechanik. Z. Phys. 1927, 43, 172. [Google Scholar] [CrossRef]
- Nielsen, M.A.; Chuang, I.L. Quantum computation and quantum information. Phys. Today 2001, 54, 60. [Google Scholar]
- Bell, J.S. On the einstein podolsky rosen paradox. Phys. Phys. Fiz. 1964, 1, 195. [Google Scholar] [CrossRef]
- Horodecki, R.; Horodecki, P.; Horodecki, M.; Horodecki, K. Quantum entanglement. Rev. Mod. Phys. 2009, 81, 865. [Google Scholar] [CrossRef]
- Henderson, L.; Vedral, V. Classical, quantum and total correlations. J. Phys. Math. Gen. 2001, 34, 6899. [Google Scholar] [CrossRef]
- Ollivier, H.; Zurek, W.H. Quantum discord: A measure of the quantumness of correlations. Phys. Rev. Lett. 2001, 88, 017901. [Google Scholar] [CrossRef] [PubMed]
- Bera, A.; Das, T.; Sadhukhan, D.; Roy, S.S.; De Sen, A.; Sen, U. Quantum discord and its allies: A review of recent progress. Rep. Prog. Phys. 2017, 81, 024001. [Google Scholar] [CrossRef]
- Baumgratz, T.; Cramer, M.; Plenio, M.B. Quantifying coherence. Phys. Rev. Lett. 2014, 113, 140401. [Google Scholar] [CrossRef]
- Greenberger, D.M.; Horne, M.A.; Zeilinger, A. Going beyond Bell’s theorem. In Bell’s Theorem, Quantum Theory and Conceptions of the Universe; Springer: Berlin/Heidelberg, Germany, 1989; pp. 69–72. [Google Scholar]
- Chakrabarty, I.; Agrawal, P.; Pati, A.K. Quantum dissension: Generalizing quantum discord for three-qubit states. Eur. Phys. J. 2011, 65, 605–612. [Google Scholar] [CrossRef]
- Wehner, S.; Elkouss, D.; Hanson, R. Quantum internet: A vision for the road ahead. Science 2018, 362. [Google Scholar] [CrossRef] [PubMed]
- Biamonte, J.; Faccin, M.; De Domenico, M. Complex networks from classical to quantum. Commun. Phys. 2019, 2, 1–10. [Google Scholar] [CrossRef]
- Chiribella, G.; D’Ariano, G.M.; Perinotti, P. Theoretical framework for quantum networks. Phys. Rev. A 2009, 80, 022339. [Google Scholar] [CrossRef]
- Perseguers, S.; Lewenstein, M.; Acín, A.; Cirac, J.I. Quantum random networks. Nat. Phys. 2010, 6, 539–543. [Google Scholar] [CrossRef]
- Kozlowski, W.; Wehner, S. Towards large-scale quantum networks. In Proceedings of the Sixth Annual ACM International Conference on Nanoscale Computing and Communication, Dublin, Ireland, 25–27 September 2019; pp. 1–7. [Google Scholar]
- Perseguers, S.; Lapeyre, G., Jr.; Cavalcanti, D.; Lewenstein, M.; Acín, A. Distribution of entanglement in large-scale quantum networks. Rep. Prog. Phys. 2013, 76, 096001. [Google Scholar] [CrossRef]
- Kimble, H.J. The quantum internet. Nature 2008, 453, 1023. [Google Scholar] [CrossRef]
- Simon, C. Towards a global quantum network. Nat. Photonics 2017, 11, 678. [Google Scholar] [CrossRef]
- Renou, M.O.; Bäumer, E.; Boreiri, S.; Brunner, N.; Gisin, N.; Beigi, S. Genuine quantum nonlocality in the triangle network. Phys. Rev. Lett. 2019, 123, 140401. [Google Scholar] [CrossRef]
- Sazim, S.; Chakrabarty, I. A study of teleportation and super dense coding capacity in remote entanglement distribution. Eur. Phys. J. D 2013, 67, 174. [Google Scholar] [CrossRef]
- Li, C.; Li, T.; Liu, Y.X.; Cappellaro, P. Effective routing design for remote entanglement generation on quantum networks. arXiv 2020, arXiv:2001.02204. [Google Scholar] [CrossRef]
- Zukowski, M.; Zeilinger, A.; Horne, M.A.; Ekert, A.K. “Event-ready-detectors” Bell experiment via entanglement swapping. Phys. Rev. Lett. 1993, 71, 4287–4290. [Google Scholar] [CrossRef] [PubMed]
- Branciard, C.; Gisin, N.; Pironio, S. Characterizing the nonlocal correlations created via entanglement swapping. Phys. Rev. Lett. 2010, 104, 170401. [Google Scholar] [CrossRef] [PubMed]
- Branciard, C.; Rosset, D.; Gisin, N.; Pironio, S. Bilocal versus nonbilocal correlations in entanglement-swapping experiments. Phys. Rev. A 2012, 85, 032119. [Google Scholar] [CrossRef]
- Chaves, R.; Fritz, T. Entropic approach to local realism and noncontextuality. Phys. Rev. A 2012, 85, 032113. [Google Scholar] [CrossRef]
- Tavakoli, A.; Skrzypczyk, P.; Cavalcanti, D.; Acín, A. Nonlocal correlations in the star-network configuration. Phys. Rev. A 2014, 90, 062109. [Google Scholar] [CrossRef]
- Fritz, T. Beyond Bell’s theorem: Correlation scenarios. New J. Phys. 2012, 14, 103001. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G. Quantum crytography. In Proceedings of the IEEE International Conference on Computers, Systems, and Signal Processing, Bangalore, India, 9–12 December 1984; pp. 175–179. [Google Scholar]
- Shor, P.W.; Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 2000, 85, 441. [Google Scholar] [CrossRef]
- Ekert, A.K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 1991, 67, 661. [Google Scholar] [CrossRef]
- Hillery, M.; Bužek, V.; Berthiaume, A. Quantum secret sharing. Phys. Rev. A 1999, 59, 1829. [Google Scholar] [CrossRef]
- Sazim, S.; Chiranjeevi, V.; Chakrabarty, I.; Srinathan, K. Retrieving and routing quantum information in a quantum network. Quant. Inf. Proc. 2015, 14, 4651–4664. [Google Scholar] [CrossRef]
- Adhikari, S.; Chakrabarty, I.; Agrawal, P. Probabilistic secret sharing through noisy quantum channels. arXiv 2010, arXiv:1012.5570. [Google Scholar]
- Ray, M.; Chatterjee, S.; Chakrabarty, I. Sequential quantum secret sharing in a noisy environment aided with weak measurements. Eur. Phys. J. D 2016, 70, 114. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G.; Crépeau, C.; Jozsa, R.; Peres, A.; Wootters, W.K. Teleporting an unknown quantum state via dual classical and Einstein-Podolsky-Rosen channels. Phys. Rev. Lett. 1993, 70, 1895. [Google Scholar] [CrossRef] [PubMed]
- Horodecki, R.; Horodecki, M.; Horodecki, P. Teleportation, Bell’s inequalities and inseparability. Phys. Lett. A 1996, 222, 21–25. [Google Scholar] [CrossRef]
- Bennett, C.H.; Wiesner, S.J. Communication via one-and two-particle operators on Einstein-Podolsky-Rosen states. Phys. Rev. Lett. 1992, 69, 2881. [Google Scholar] [CrossRef]
- Nepal, R.; Prabhu, R.; Sen De, A.; Sen, U. Maximally-dense-coding-capable quantum states. Phys. Rev. A 2013, 87, 032336. [Google Scholar] [CrossRef]
- Bose, S.; Vedral, V.; Knight, P.L. Multiparticle generalization of entanglement swapping. Phys. Rev. A 1998, 57, 822. [Google Scholar] [CrossRef]
- Chatterjee, S.; Sazim, S.; Chakrabarty, I. Broadcasting of quantum correlations: Possibilities and impossibilities. Phys. Rev. A 2016, 93, 042309. [Google Scholar] [CrossRef]
- Sharma, U.K.; Chakrabarty, I.; Shukla, M.K. Broadcasting quantum coherence via cloning. Phys. Rev. A 2017, 96, 052319. [Google Scholar] [CrossRef]
- Jain, A.; Chakrabarty, I.; Chatterjee, S. Asymmetric broadcasting of quantum correlations. Phys. Rev. A 2019, 99, 022315. [Google Scholar] [CrossRef]
- Mundra, R.; Patel, D.; Chakrabarty, I.; Ganguly, N.; Chatterjee, S. Broadcasting of quantum correlations in qubit-qudit systems. Phys. Rev. A 2019, 100, 042319. [Google Scholar] [CrossRef]
- Deutsch, D.; Ekert, A.; Jozsa, R.; Macchiavello, C.; Popescu, S.; Sanpera, A. Quantum privacy amplification and the security of quantum cryptography over noisy channels. Phys. Rev. Lett. 1996, 77, 2818. [Google Scholar] [CrossRef]
- Wootters, W.K.; Zurek, W.H. A single quantum cannot be cloned. Nature 1982, 299, 802–803. [Google Scholar] [CrossRef]
- Pati, A.K.; Braunstein, S.L. Impossibility of deleting an unknown quantum state. Nature 2000, 404, 164. [Google Scholar] [CrossRef] [PubMed]
- Patel, D.; Patro, S.; Vanarasa, C.; Chakrabarty, I.; Pati, A.K. Impossibility of cloning of quantum coherence. arXiv 2018, arXiv:1806.05706. [Google Scholar] [CrossRef]
- Chakrabarty, I. Impossibility of partial swapping of Quantum Information. Int. J. Quant. Inf. 2007, 5, 605–609. [Google Scholar] [CrossRef]
- Pati, A.K.; Sanders, B.C. No-partial erasure of quantum information. Phys. Lett. A 2006, 359, 31–36. [Google Scholar] [CrossRef]
- Modi, K.; Pati, A.K.; Sen, A.; Sen, U. Masking quantum information is impossible. Phys. Rev. Lett. 2018, 120, 230501. [Google Scholar] [CrossRef]
- Bužek, V.; Hillery, M. Quantum copying: Beyond the no-cloning theorem. Phys. Rev. A 1996, 54, 1844. [Google Scholar] [CrossRef]
- Gisin, N.; Massar, S. Optimal quantum cloning machines. Phys. Rev. Lett. 1997, 79, 2153. [Google Scholar] [CrossRef]
- Bužek, V.; Hillery, M. Universal optimal cloning of arbitrary quantum states: From qubits to quantum registers. Phys. Rev. Lett. 1998, 81, 5003. [Google Scholar] [CrossRef]
- Bruß, D.; DiVincenzo, D.P.; Ekert, A.; Fuchs, C.A.; Macchiavello, C.; Smolin, J.A. Optimal universal and state-dependent quantum cloning. Phys. Rev. A 1998, 57, 2368. [Google Scholar] [CrossRef]
- Cerf, N.J. Pauli cloning of a quantum bit. Phys. Rev. Lett. 2000, 84, 4497. [Google Scholar] [CrossRef] [PubMed]
- Cerf, N.J. Asymmetric quantum cloning in any dimension. J. Mod. Opt. 2000, 47, 187. [Google Scholar] [CrossRef]
- Scarani, V.; Iblisdir, S.; Gisin, N.; Acin, A. Quantum cloning. Rev. Mod. Phys. 2005, 77, 1225. [Google Scholar] [CrossRef]
- Adhikari, S.; Choudhury, B.S.; Chakrabarty, I. Broadcasting of inseparability. J. Phys. A 2006, 39, 8439. [Google Scholar] [CrossRef]
- Shukla, M.K.; Chakrabarty, I.; Chatterjee, S. Broadcasting of correlations via orthogonal & non-orthogonal state dependent cloners. arXiv 2019, arXiv:1904.12899. [Google Scholar]
- Cerf, N.J.; Bourennane, M.; Karlsson, A.; Gisin, N. Security of quantum key distribution using d-level systems. Phys. Rev. Lett. 2002, 88, 127902. [Google Scholar] [CrossRef]
- Ghiu, I. Asymmetric quantum telecloning of d-level systems and broadcasting of entanglement to different locations using the “many-to-many” communication protocol. Phys. Rev. A 2003, 67, 012323. [Google Scholar] [CrossRef]
- Renou, M.O.; Wang, Y.; Boreiri, S.; Beigi, S.; Gisin, N.; Brunner, N. Limits on correlations in networks for quantum and no-signaling resources. Phys. Rev. Lett. 2019, 123, 070403. [Google Scholar] [CrossRef]
- Kraft, T.; Designolle, S.; Ritz, C.; Brunner, N.; Gühne, O.; Huber, M. Quantum entanglement in the triangle network. arXiv 2020, arXiv:2002.03970. [Google Scholar] [CrossRef]
- Christandl, M.; Winter, A. “Squashed entanglement”: An additive entanglement measure. J. Math. Phys. 2004, 45, 829–840. [Google Scholar] [CrossRef]
- Cerf, N.J.; Adami, C. Negative entropy and information in quantum mechanics. Phys. Rev. Lett. 1997, 79, 5194. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shukla, M.K.; Huang, M.; Chakrabarty, I.; Wu, J. Correlations in Quantum Network Topologies Created with Cloning. Mathematics 2023, 11, 2440. https://doi.org/10.3390/math11112440
Shukla MK, Huang M, Chakrabarty I, Wu J. Correlations in Quantum Network Topologies Created with Cloning. Mathematics. 2023; 11(11):2440. https://doi.org/10.3390/math11112440
Chicago/Turabian StyleShukla, Manish Kumar, Minyi Huang, Indranil Chakrabarty, and Junde Wu. 2023. "Correlations in Quantum Network Topologies Created with Cloning" Mathematics 11, no. 11: 2440. https://doi.org/10.3390/math11112440
APA StyleShukla, M. K., Huang, M., Chakrabarty, I., & Wu, J. (2023). Correlations in Quantum Network Topologies Created with Cloning. Mathematics, 11(11), 2440. https://doi.org/10.3390/math11112440



