An Innovative Blockchain-Based Secured Logistics Management Architecture: Utilizing an RSA Asymmetric Encryption Method
Abstract
1. Introduction
1.1. Problem Contexts
1.2. Motivation
1.3. Contributions of This Study
- This study identified the kinds of cyber-attacks challenging smart logistics systems.
- A blockchain-based secured and efficient logistics management system architecture on a peer-to-peer decentralized network was proposed to secure and enhance the efficiency of the logistics management system.
- iAn innovative asymmetric RSA encryption method was deployed to enhance the security of the logistics system and provide privacy to customers’ private information.
- blockchain-based algorithms with specified smart contracts utilizing the Ethereum platform were proposed and implemented to address security issues and enhance the efficiency of the logistics system.
- Finally, security and privacy analyses were done to assess the security of the logistics system and the privacy of customers’ data. The latency and throughput of the proposed system were compared with a baseline system.
1.4. Paper Organization
2. Literature Review and Related Works
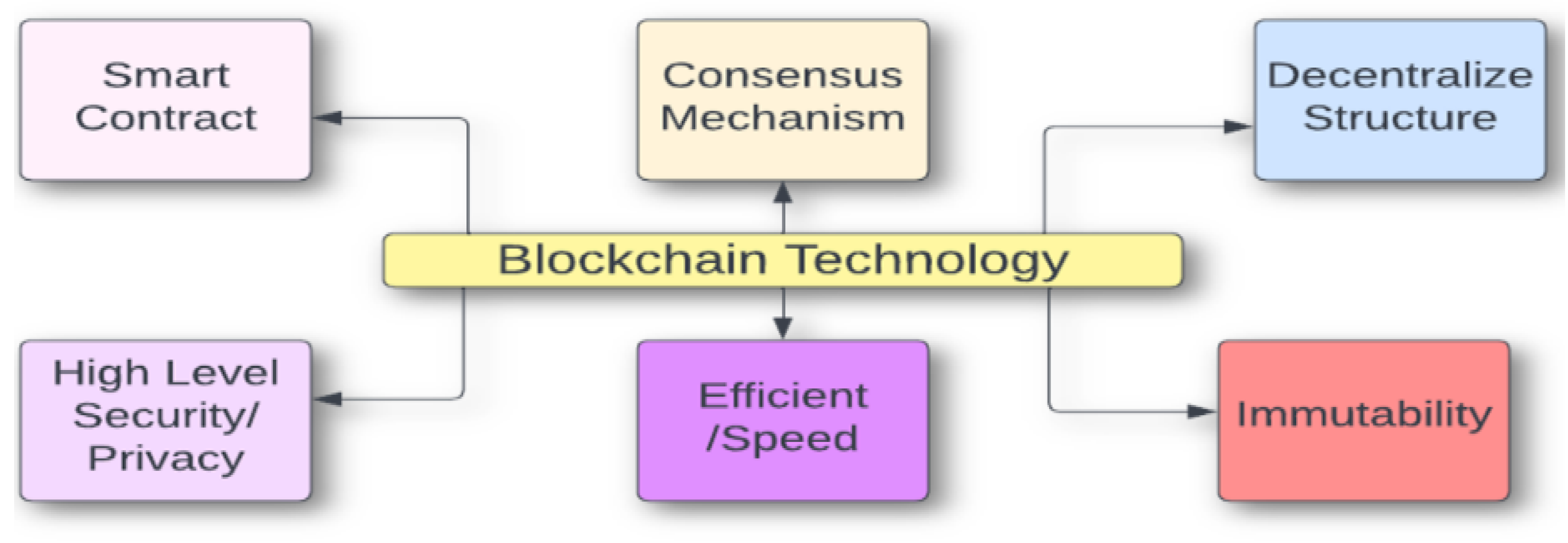
2.1. Blockchain Technology and Its Applications in Different Areas
2.2. Blockchain-Based Logistics Systems
2.3. Limitations of Existing Literature/Works
3. Definition of Smart Logistics Systems and Cyber-Attack Challenges
3.1. Smart Logistics Definition
- Fast Decision Support: This involves the utilization of big data analytics and artificial intelligence (AI) to automate fast decision support through a data-driven method.
- Seamless Information Transfer: IT systems are combined with cloud computing to provide users with fast access to data and information from several sources and to enable more flexible real-time production planning and scheduling.
- Automation with robotics: This is the development of smart/intelligent transportation systems that support or substitute human labor in manual processes.
- Connectivity and Identification: These refer to applications of IoT and smart sensor technologies that can uniquely identify goods, improving the tracking and tracing of goods both within and outside of the warehouse.
3.2. Kinds of Cyber-Attacks Challenging Smart Logistics Systems
- Computational Attack: In the logistics domain, smart contract computation performs the mathematical operations that typically establish interactions of smart contracts that facilitate business processes in a logistics application. The computational attack occurs when the smart contract transaction can accept any unauthorized input or data. In a computation attack, the adversary uses various techniques, such as smart contract overflow, etc., to compromise the logistics system’s functionality. Smart contract overflow occurs when more value is provided than the maximum value, 256 bits. An increase of 1 value would result in an overflow.
- Denial of Service Attack: This attack arises when malicious code is sent across a logistics network to breach the network communication, thereby creating an avenue to steal sensitive information. Most smart logistics systems are prone to this attack due to their centralized database system.
- Communication Attack: This kind of attack is sometimes perpetrated by an insider. The interchange of data between various parties (processes or persons) involved in logistics is handled by the communication process. An adversary engaging in a communication attack seeks to compromise the data transferred among numerous connected services. For instance, the attacker might tamper with input values for smart contracts or other components, violate the integrity of the communication by using a selective forward, and drop or insert fake information based on mining public contracts and the ledger.
- Password Attack: This attack refers to the stealing of identification information of legitimate logistics stakeholders to carry out nefarious activities.
3.3. Blockchain Innovations and Smart Contract
- Radical or Incremental Innovation: The ability of blockchain to improve existing processes or services
- Competent Innovation: The capability of blockchain to build on an existing system and replace the existing system
- Architectural or Component Innovation: blockchain innovates by changing how systems operate or how components interact.
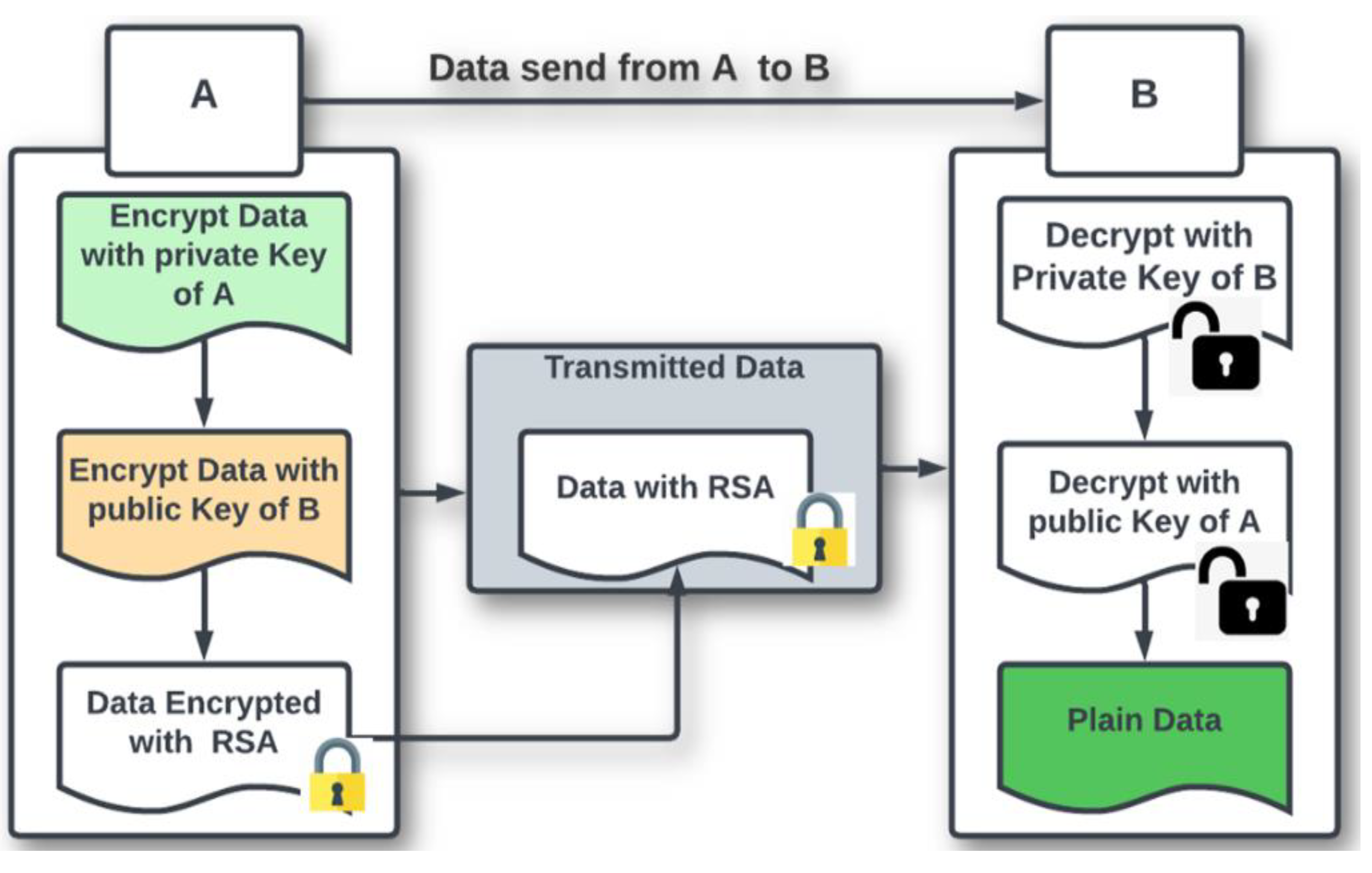
3.4. Security Protection Mechanism of Blockchain Using RSA Encryption
3.5. Advantages of RSA over ECC
- (a)
- ECC is sluggish at encryption and very fast at decryption,
- (b)
- RSA has proven to be quite successful at encrypting but not very efficient at decrypting.
- (c)
- RSA allows for the encryption of messages before transmitting. It also helps to certify the message so that the recipient will know that it has not been altered during transmission.
- (d)
- RSA is easier to implement than ECC.
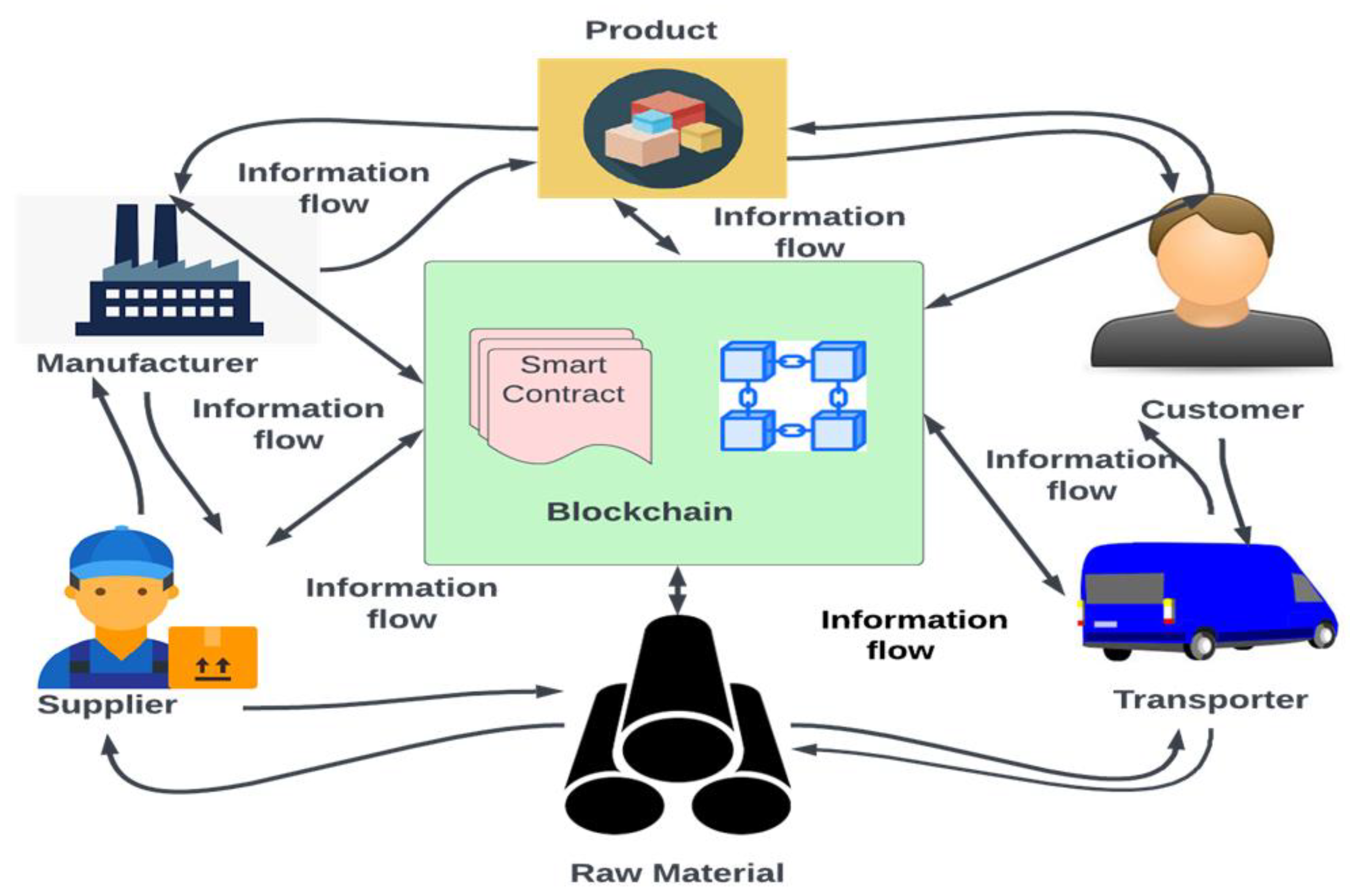
3.6. Blockchain-Based Logistics Management System
4. Proposed Methodology
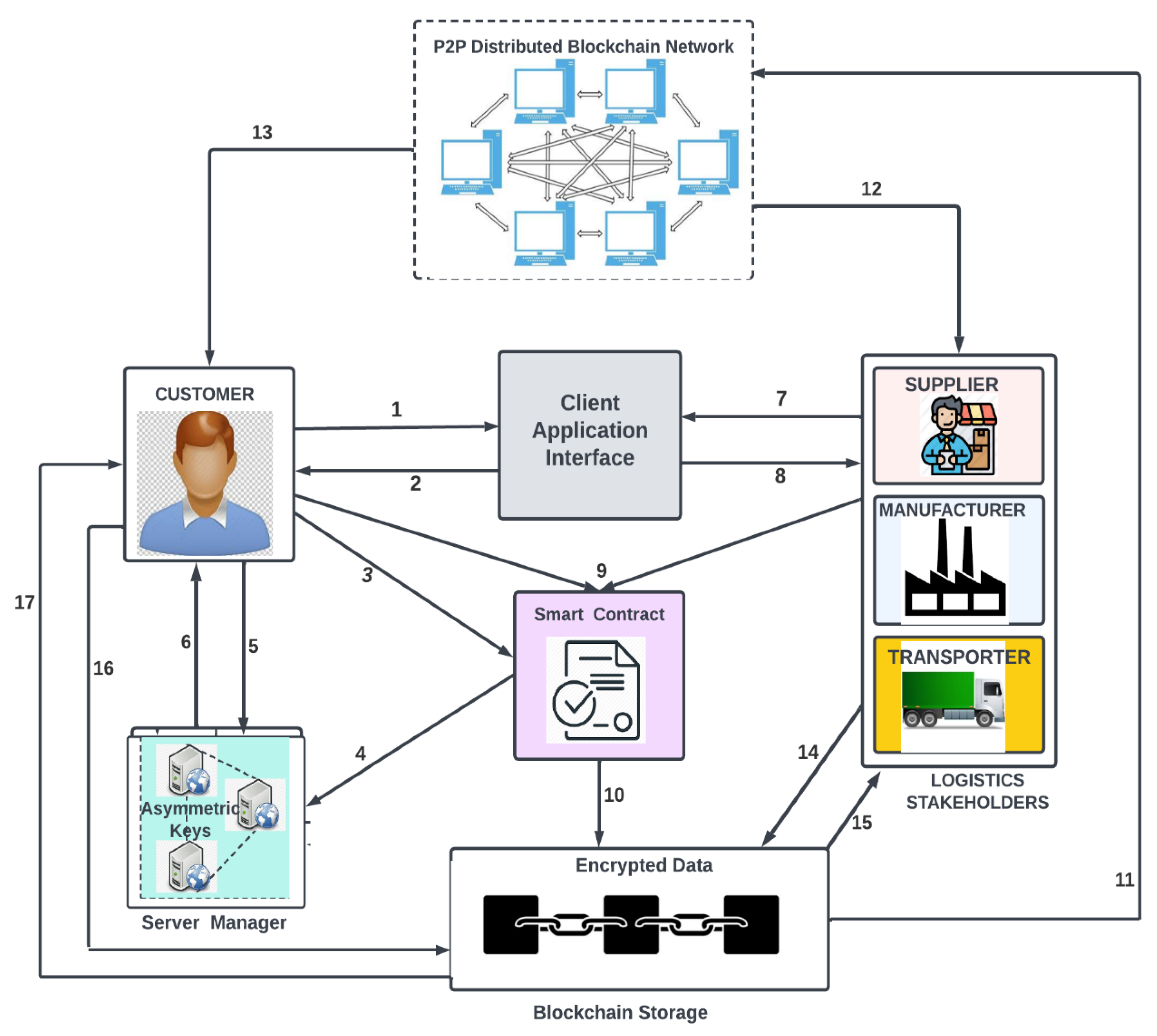
4.1. System Architecture
- The customer creates an account through the client application interface and is assigned user identification by the system
- Customer logs in to the system with the user identifications.
- The customer generates an asymmetric key through the smart contract.
- The generated encrypted key is validated and stored in the decentralized server. The decentralized server manager is used to store all the private keys,
- The customer can query for the asymmetric key.
- The feedback of the query is sent to the customer and it can be decrypted by the customer.
- The other logistics stakeholders (manufacturers, supplier, and transporters) with different roles and designations create accounts through the client application interface and are assigned user identifications.
- The stakeholders log in to the system with the user identification.
- The customers and other logistics stakeholders initiate a transaction such as a manufacturer adding products in the blockchain network, a customer purchasing products, product change of ownership. Customers encrypt personal data and transmit to the corresponding receiver (logistics stakeholder) using the customer’s private key and the receiver’s public key. The receiver will decrypt the data using the customer’s public key and the receiver’s private keys. This mechanism protects customers’ data from unnecessary access and verifies the message’s source.
- All the transactions that are executed by the smart contract are validated and recorded in the block once they pass the validation check. and then added to the blockchain. All transaction is completely secure because transactions are merely added to the previous hash with a time stamp.
- The stored information is broadcasted on the p2p distributed blockchain network. This process ensures that every transaction over the network is distributed to all system stakeholders
- The logistics stakeholders (manufacturers, suppliers, and transporter) connected to the network have access to updated information.
- The customer also has access to the updated distributed information on the blockchain network.
- The logistics stakeholders make queries from the blockchain repository.
- The quarried information is retrieved from the blockchain storage or repository and sent back to the corresponding entity.
- Customers make queries from the blockchain storage
- The information is retrieved from the blockchains repository and feedback is sent to the customer.
4.2. Specified Smart Contract
- Secured sharing of customer information among stakeholders with encryption and decryption using asymmetric encryption
- Creation of product records on the blockchain network,
- Validation check for stakeholders to perform a transaction
- Obtain the asymmetric keys from the server
- Purchase product, change of ownership, and delivery of the product
- A.
- Secured sharing of customer information among stakeholders using RSA asymmetric encryption and decryption method.
- Enc hash of (Cdata, CprivateKey) = SHA244
- The hash of (Cdata, RpublicKey) = SHA256
| Algorithm 1: Smart contract for secured sharing of customer data |
| 1: Input: (CprivateKey, CpublicKey, TprivateKey, TpublicKey, Cdata) 2: Output: Encryption and Decryption of Customer Data 4: Encrypt (hash of Cdata) using Cprivatekey = M 5: Encrypt (hash of Cdata) using Tpublickkey = X 6: if {(M, X) Enc} = (Cdata) Enc then 7: Transmit (Cdata) Enc to Tid 8: else 9: Declare Error Message and Return to none 10: end if 11: If (TprivateKey exists), then 12: Decrypt {(Cdata) Enc} using TprivateKey 13: Decrypt {(Cdata) Enc} using CpublicKey, 14: Acknowledge Cdata by Tid 15: else 16: Declare a message that the transporter does not exist 17: end if |
- B.
- Creation of product records on the blockchain network
| Algorithm 2: Smart contract for creation of product on blockchain network |
| 1: Inputs: Mprivate_key, PId, p_p 2: Output: Product created and out for sale 3: If (Mprivate_key and PId exist) then 4: create _product details 5: increment Product Count 6: update Product_Details 7: if else 8: Declare error message cannot create a product 9: end if 10: if (Mprivate_key = ProductOnwerid) then 11: Declare ProductforSale 12: if else 13: Declare error message that product owner is not correct 14: end if |
- C.
- Validation check for Stakeholders to perform a transaction
| Algorithm 3: Consensus algorithm for validation check for stakeholders |
| 1: Input: (CId, MId, SId, TId) 2: Output: Log in to the blockchain network 3: if (CId and Password are valid) then 4: Log in Customer to the blockchain Network 5: else 6: Declare customer does not exist and create a customer account 7: end if 8: if (MId and Password are valid) then 9: Log in Manufacturer to the blockchain Network 10: else 11: Declare Manufacturer does not exist and Create a Manufacturer account 12: end if 13: if (SId is valid) then 14: Log in Supplier to the blockchain Network 15: else 16: Declare Supplier does not exist and Create a Supplier account 17: end if 18: if (Tid is valid) then 19: Log in Transporter to the blockchain Network 20: else 21: Declare Transporter does not exist and Create a Transporter account 22: end if |
- D.
- Get the asymmetric keys from the server
| Algorithm 4: Smart contract for obtaining asymmetric key for customer |
| 1: Inputs: Cid, Cpublickey 2: Output: Asymmetric Key of Customer 3: if (Cid and CpublicKey exit) then 4: Get_asymmetrickey of Cid from the server 5: Encrypt (asymmetric key, Cpublickey) 6: Return as (asymmetric key) Enc 7: else 8: Return to None 9: end if |
- E.
- Purchase product, change of ownership, and delivery of the product
| Algorithm 5: Smart contract for purchase, transfer, and delivery of product |
| 1: Inputs: Selpublickey, Pid, BId, soldate, status,p_p 2: Output: Purchase And delivery of Product 3: if (Pid exists) then 4: if (product is available) then 5: Proceed with the purchase of the product 6: else 7: Report with a message that the product is not available 8: end if 9: end if 10: if (Selpublickey = productOnwerid) then 11: Proceed with payment for the product 12: else 13: Declare an error message that the seller is fake 14: end if 15: if (buyer account balance ≥ p_p), then 16 transfer funds from the buyer account to the seller account 17: update productOwnerId 18: update the ownership Address 19: Update Status to product successfully purchased 20: else 21: Report with error message insufficient fund 22: end if 23: if (product delivery date is in agreement with the buyer) then 24 if (Tid exists) then 25: Deliver product 26: Acknowledge delivery by the buyer 27 else 28: Reschedule delivery of the product 29: end if 30: end if |
4.3. Materials and Method
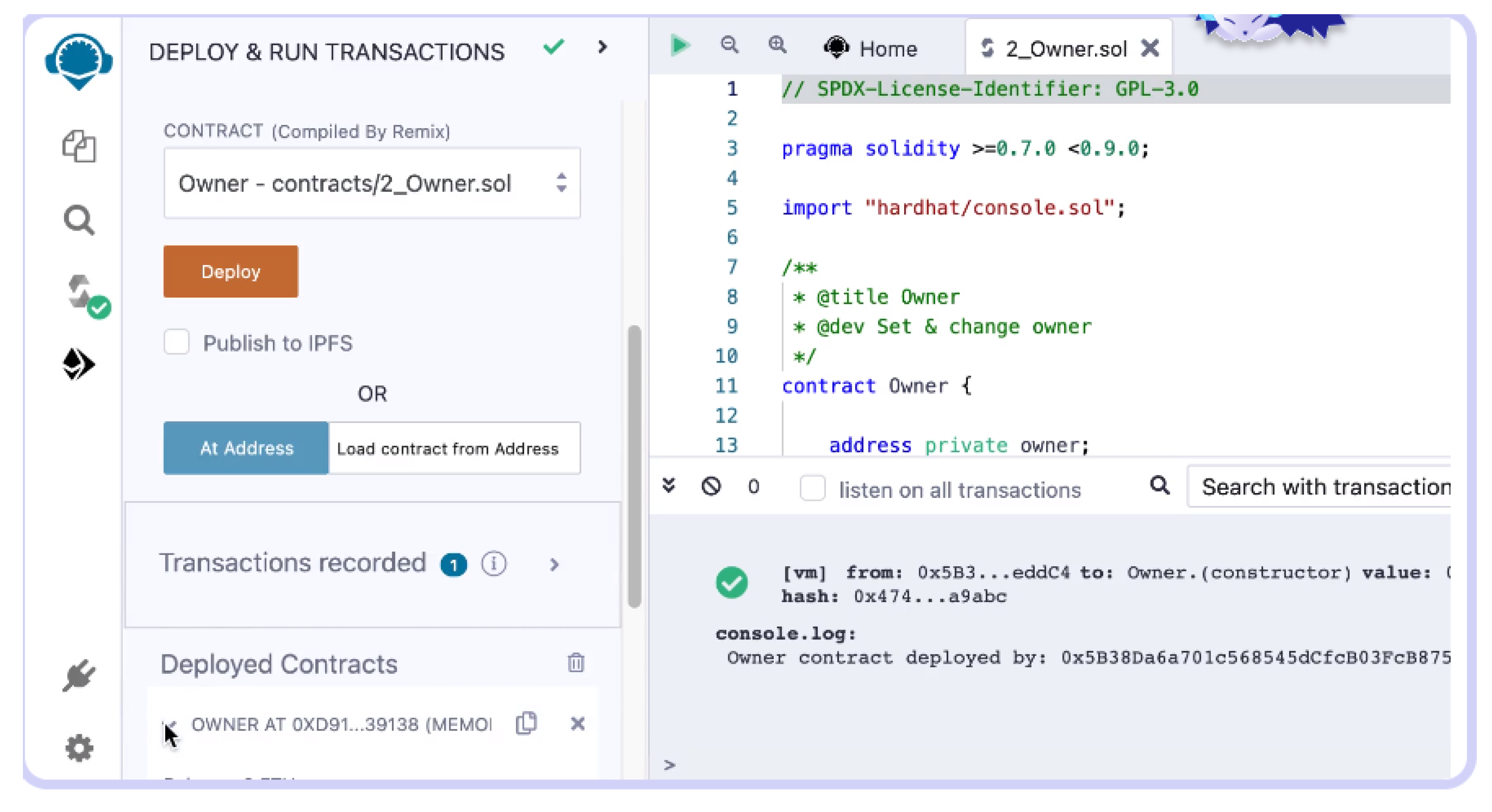
5. Proposed System Evaluation
5.1. Privacy Evaluation
5.2. Security Evaluation
5.3. Performance Evaluation
- tci: Is the transaction committed time,
- Ni: is the total number of transactions for the ith trial, and
- n: is the total number of trials run.
- tsi: Is the transaction submission time for the ith trial,
- tci: Is the transaction execution times for the ith trial,
- Ti: indicates how many transactions were submitted for the ith trial.
6. Results and Findings
6.1. Results
6.2. Findings
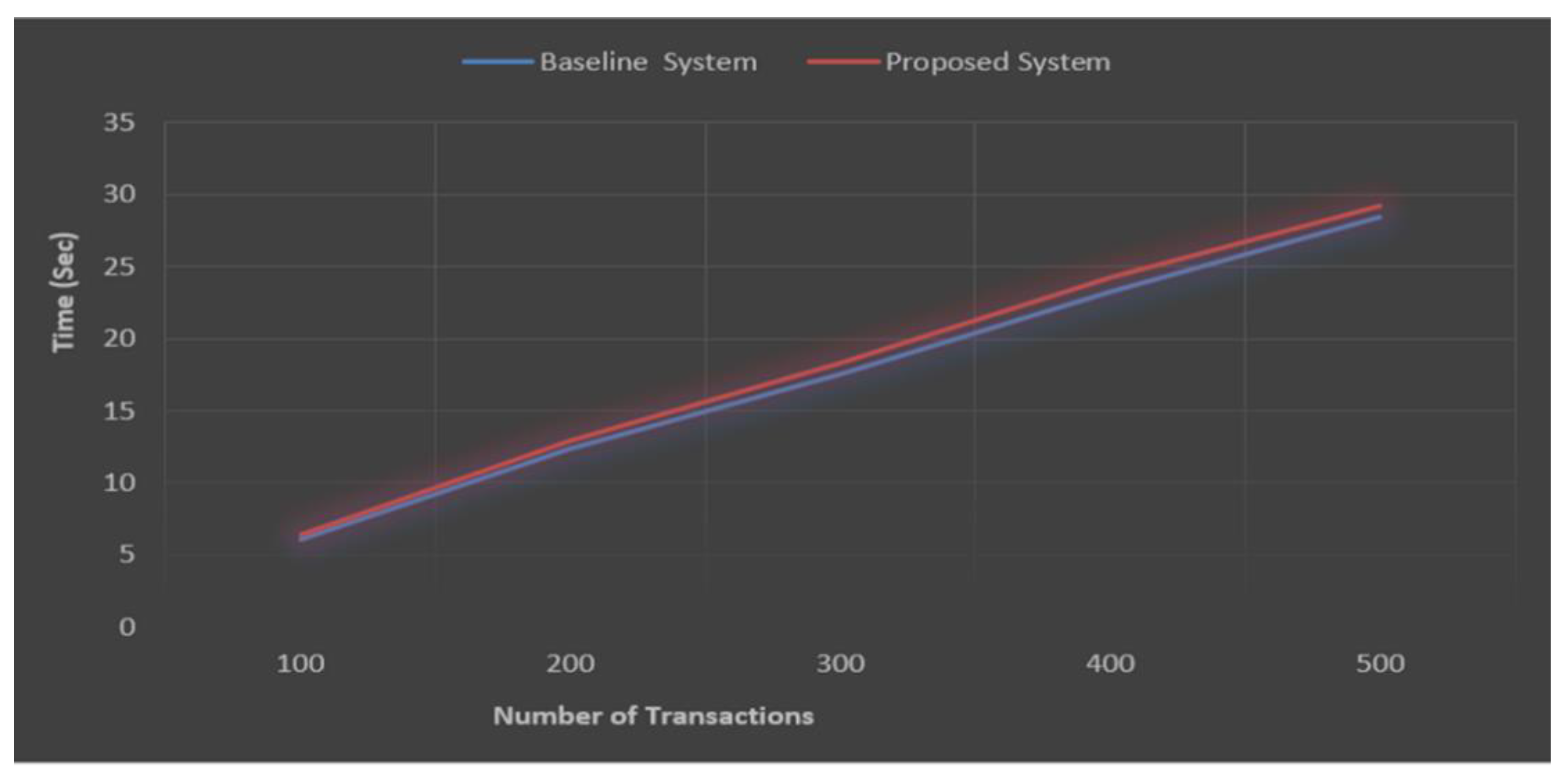
6.3. Comparison of Proposed System with Exiting System
7. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Panarello, A.; Tapas, N.; Merlino, G.; Longo, F.; Puliafito, A. Blockchain and IoT Integration: A Systematic Survey. Sensors 2018, 18, 2575. [Google Scholar] [CrossRef] [PubMed]
- Council of Supply Chain Management Professionals (CSCMP). Grants Regist. 2021, 303–304. [CrossRef]
- Akram, Asif, and Bross, Philipp Trust, Privacy, and Transparency with Blockchain Technology in Logistics. CIS Proceedings. 2018. Available online: https://aisel.aisnet.org/cgi/viewcontent.cgi?article=1021&context=mcis2018 (accessed on 24 September 2022).
- Rosenberger, P. Satoshi Nakamoto (Bitcoin and Blockchain), Blockchain Is a Peer 2 to-Peer-Distributed Decentralized network. In Bitcoin und Blockchain; Springer: Berlin/Heidelberg, Germany, 2018; pp. 25–34. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the 2017 IEEE 6th International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar] [CrossRef]
- Beck, R.; Stenum Czepluch, J.; Lollike, N.; Malone, S. Blockchain–the gateway to trust-free cryptographic transactions. In Proceedings of the Twenty-Fourth European Conference on Information Systems(ECIS), Istanbul, Turkey, 12 June 2016. [Google Scholar]
- Xiong, Z.; Yang, Z.; Niyato, D.; Wang, P.; Han, Z. When Mobile Blockchain Meets Edge Computing. IEEE Commun. Mag. 2017, 56, 33–39. [Google Scholar] [CrossRef]
- Shrestha, R.; Nam, S.Y. Regional Blockchain for Vehicular Networks to Prevent 51% Attacks. IEEE Access 2019, 7, 95033–95045. [Google Scholar] [CrossRef]
- Dunphy, P.; Petitcolas, P. A First Look at Identity Management Schemes on the Blockchain. IEEE Secur. Priv. 2018, 16, 20–29. [Google Scholar] [CrossRef]
- Sun, Y.; Zhang, L.; Imran, M.A. Blockchain-Enabled Wireless Internet of Things: Performance Analysis and Optimal Communication Node Deployment. IEEE Internet Things J. 2019, 6, 5791–5802. [Google Scholar] [CrossRef]
- Liu, C.H.; Wen, S. Blockchain-Enabled Data Collection and Sharing for Industrial IoT with Deep Reinforcement Learning. IEEE Trans. Ind. Inform. 2019, 15, 3516–3526. [Google Scholar] [CrossRef]
- Wan, J.; Li, J.; Imran, M.; Li, D. Fazal-e-Amin Based Solution for Enhancing Security and Privacy in Smart Factory. IEEE Trans. Ind. Inform. 2019, 15, 3652–3660. [Google Scholar] [CrossRef]
- Dinh, T.T.A.; Liu, R.; Zhang, M.; Chen, G.; Ooi, B.C.; Wang, J. Untangling Blockchain: A Data Processing View of Blockchain Systems. IEEE Trans. Knowl. Data Eng. 2018, 30, 1366–1385. [Google Scholar] [CrossRef]
- Shahzad, B.; Crowcroft, J. Trustworthy Electronic Voting Using Adjusted blockchain technology. IEEE Access 2019, 7, 24477–24488. [Google Scholar] [CrossRef]
- Imeri, A.; Khadraoui, D.; Agoulmine, N. Blockchain Technology for the Improvement of SCM and Logistics Services: A Survey. In Industrial Engineering in the Big Data Era. Lecture Notes in Management and Industrial Engineering; Calisir, F., Cevikcan, E., Camgoz, A.H., Eds.; Springer: Cham, Switzerland, 2019; pp. 349–361. [Google Scholar]
- IBM. Vaccine Distribution on Blockchain. 2020. Available online: https://www.ibm.com/blockchain/solutions/vaccine-distribution (accessed on 10 September 2022).
- Park, A.; Li, H. The Effect of Blockchain Technology on Supply Chain Sustainability Performances. Sustainability 2021, 13, 1726. [Google Scholar] [CrossRef]
- Muniandy, M.; Ern, O.; Tze, G. Implementation of Pharmaceutical Drug Traceability Using Blockchain Technology. 2019. Available online: http://eprints.intimal.edu.my/1308/1/vol.2019_035.pdf (accessed on 14 September 2022).
- Shahid, A.; Almogren, A.; Javaid, N.; Al-Zahrani, F.A.; Zuair, M.; Alam, M. Blockchain-Based Agri-Food Supply Chain: A Complete Solution. IEEE Access Inst. Electr. Electron. Eng. 2020, 8, 69230–69243. [Google Scholar] [CrossRef]
- Ugochukwu, N.A.; Goyal, S.B.; Arumugam, S. Blockchain-Based IoT-Enabled System for Secure and Efficient Logistics Management in the Era of IR 4.0. J. Nanomater. 2022, 1–10. [Google Scholar] [CrossRef]
- Musamih, A.; Salah, K.; Jayaraman, R.Y. Blockchain-Based Approach for Drug Traceability in Healthcare Supply Chain. IEEE Access. Inst. Electr. Electron. Eng. 2021, 9, 9728–9743. [Google Scholar] [CrossRef]
- Hackius, N.; Petersen, M. Blockchain in logistics and supply chain: Trick or treat? In Proceedings of the Hamburg international conference of Logistics (HICL), online, 12 October 2017; pp. 3–18. [Google Scholar]
- Önder, I.; Treiblmaier, H. Blockchain and tourism: Three research propositions. Ann. Tour. Res. 2018, 72, 180–182. [Google Scholar] [CrossRef]
- Ding, Y.; Jin, M.; Li, S.; Feng, D. Smart logistics based on the internet of things technology: An overview. Int. J. Logist. Res. Appl. 2020, 24, 323–345. [Google Scholar] [CrossRef]
- Aziz, M.F.; Khan, A.N.; Shuja, J.; Khan, I.A.; Khan, F.G.; Khan, A. A lightweight and compromise-resilient authentication scheme for IoTs. Trans. Emerg. Telecommun. Technol. 2019, 33, e3813. [Google Scholar] [CrossRef]
- Anwar, M. Connect2smallports Project: South Baltic Small Ports–Gateway to Integrated and Sustainable European Transport System: Project Brief and Updates on the Project Activities: Digital Audit. Blockchain Design Strategy. Call for Collaboration. Reports and Scientific Publications. 2019. Available online: http://urn.kb.se/resolve?urn=urn:nbn:se:bth-18763 (accessed on 2 October 2022).
- Cimini, C.; Lagorio, A.; Romero, D.; Cavalieri, S.; Stahre, J. Smart Logistics and the Logistics Operator 4.0. IFAC 2020, 53, 10615–10620. [Google Scholar] [CrossRef]
- Al-Farsi, S.; Rathore, M.M.; Bakiras, S. Security of Blockchain-Based Supply Chain Management Systems: Challenges and Opportunities. Appl. Sci. 2021, 11, 5585. [Google Scholar] [CrossRef]
- Sayeed, S.; Marco-Gisbert, H. On the effectiveness of control-flow integrity against modern attack techniques. In ICT Systems Security and Privacy Protection; Dhillon, G., Karlsson, F., Hedström, K., Zúquete, A., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 331–334. [Google Scholar] [CrossRef]
- Banerjee, M.; Lee, J.; Choo, K.K.R. A Blockchain future for the internet of things security: A position paper. Digit. Commun. Netw. 2018, 4, 149–160. [Google Scholar] [CrossRef]
- Rane, S.; Thakker, S. Green procurement process model based on Blockchain–IoT integrated architecture for a sustainable business. Manag. Environ. Qual. Int. J. 2019, 31, 741–763. [Google Scholar] [CrossRef]
- Korpela, K.; Hallikas, J.; Dahlberg, T. Digital supply chain transformation toward Blockchain integration. In Proceedings of the 50th Hawaii International Conference on System Sciences, Hilton Waikoloa Village, HI, USA, 4–7 January 2017; pp. 4182–4191. [Google Scholar]
- Amy, N. Quantum Computer Comes Closer to Cracking RSA Encryption Shor’s Algorithm Performed in a System less than Half the Size Experts Expected. 2016. Available online: https://spectrum.ieee.org/encryptionbusting-quantum-computer-practices-factoring-in-scalable-fiveatom-experiment (accessed on 30 September 2022).
- Toyoda, K.; Mathiopoulos, P.T.; Sasase, I.; Ohtsuki, T. A Novel Blockchain-Based Product Ownership Management System (POMS) for Anti-Counterfeits in the Post Supply Chain. IEEE Access 2017, 5, 17465–17477. [Google Scholar] [CrossRef]
- Du, M.; Chen, Q.; Xiao, J.; Yang, H.; Ma, X. Supply Chain Finance Innovation Using Blockchain. IEEE Trans. Eng. Manag. 2020, 67, 1045–1058. [Google Scholar] [CrossRef]
- Mohit, M.; Kaur, S.; Singh, M. Design and implementation of transaction privacy by ownership and traceability in the blockchain-based supply chain. Clust. Comput. 2021, 25, 2223–2240. [Google Scholar] [CrossRef]
- Ugochukwu, N.A.; Goyal, S.B. Logistics Management Using Blockchain: A Review of Literature and Research Agenda. IGI Global 2022, 122–144. [Google Scholar] [CrossRef]
- Ji, T.; Goyal, S.B.; Arumugam, S. A Regulated Anticounterfeiting Traceability Metamodel Based on Blockchain in Supply Chain in the Era of IR 4.0. J. Nanomater. 2022, 11, 4305966. [Google Scholar] [CrossRef]

| Notations | Meaning |
|---|---|
| Mid | Manufacturer unique identifier |
| Mprivatekey | Manufacturer private key |
| CId | Customer unique identifier |
| Cprivatekey | Customer private key |
| Cpublickey | Customer public key |
| Cdata | Customer data (name, address, mobile no, etc) |
| (Cdata) Enc | Encrypted customer data |
| SId | Supplier unique identifier |
| TId | Transporter unique identifier |
| Tpublickey | Transporter public key |
| Tprivatekey | Transporter private key |
| PId | Product unique identifier |
| P_P | Product Price |
| Enc | Encryption |
| Dec | Decryption |
| BId | The unique ID of the buyer of the product |
| SelId | The unique ID of the seller of the product |
| Selpublickey | Seller public key |
| Soldate | The date on which the purchase is being made. |
| RprivateKey | Receiver private key |
| RpublicKey | Receiver Public Key |
| S/No | Tools | Specifications |
|---|---|---|
| 1.0 | Solidity version, | 0.7.0 and more |
| 2.0 | REMIX IDE | Intel (R) Core (TM), i5—8250U |
| 3.0 | CPU, Windows 10 | 1.60 GHz, 8 GB of RAM, 64-bit OS |
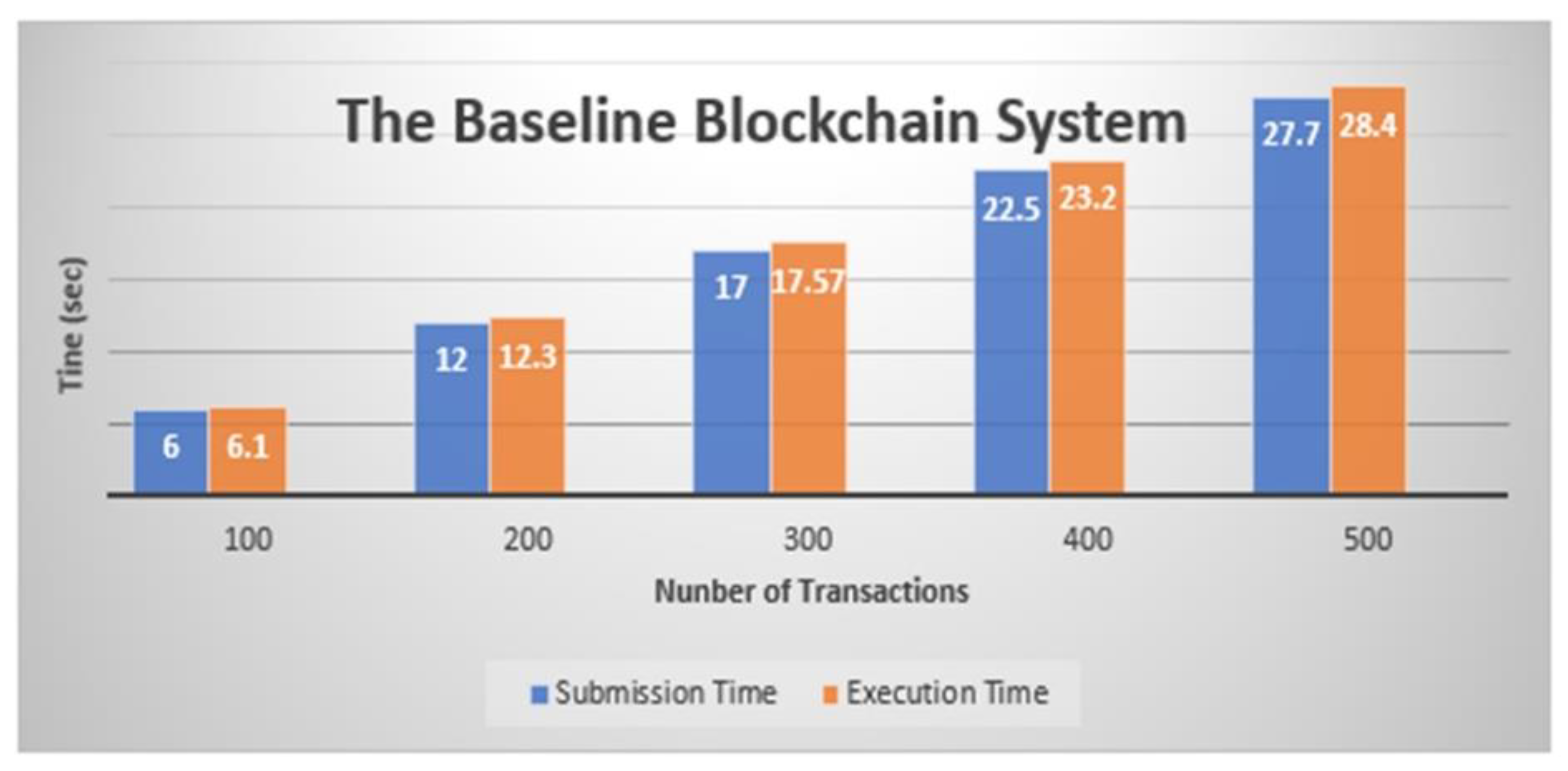
| No of Transactions | Submission Time (s) | Execution Time (s) |
|---|---|---|
| 100 | 6.0 | 6.1 |
| 200 | 12 | 12.3 |
| 300 | 17 | 17.57 |
| 400 | 22.5 | 23.2 |
| 500 | 27.7 | 28.4 |
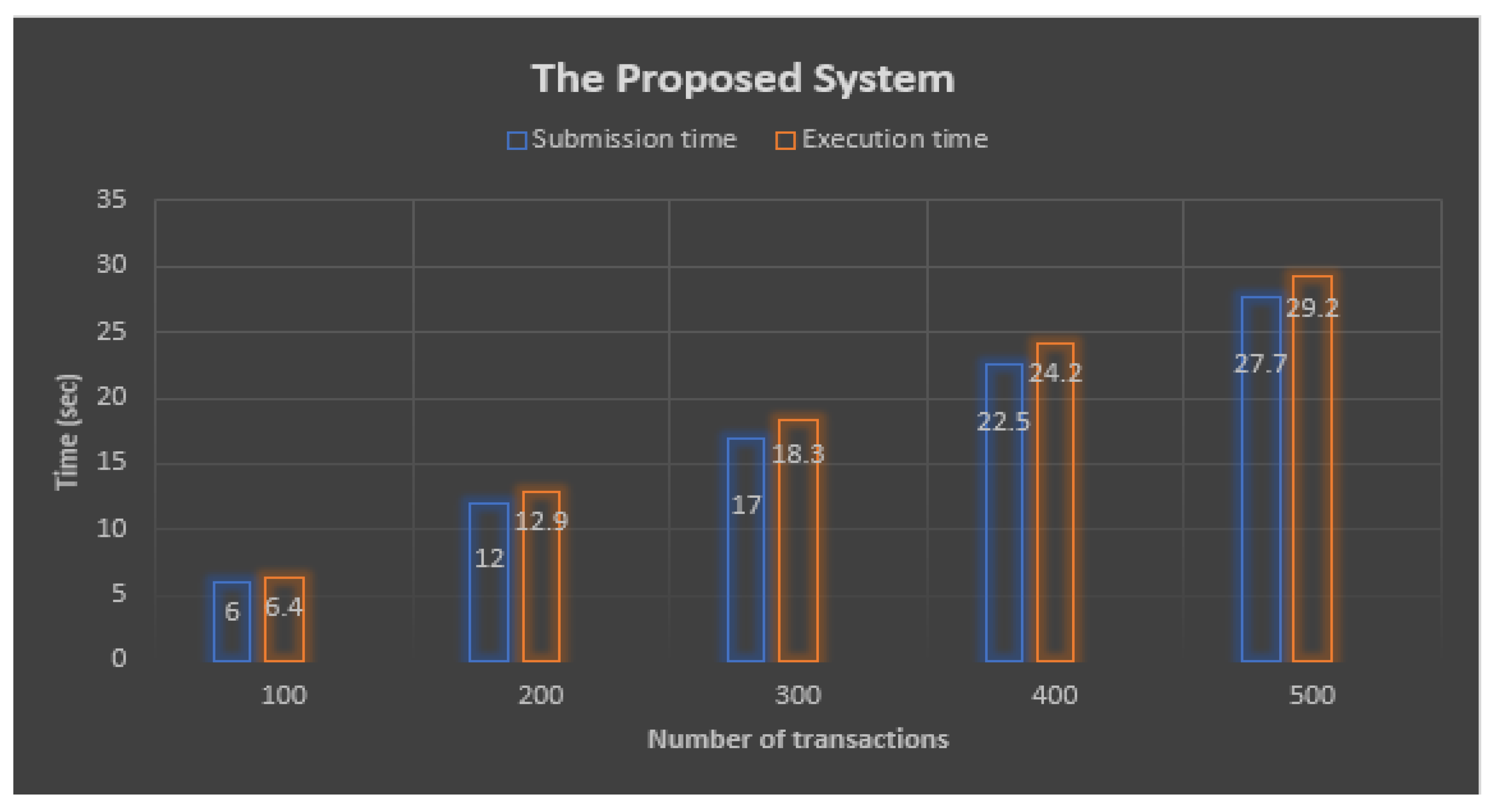
| No of Transactions | Submission Time (s) | Execution Time (s) |
|---|---|---|
| 100 | 6.0 | 6.4 |
| 200 | 12 | 12.9 |
| 300 | 17 | 18.3 |
| 400 | 22.5 | 24.2 |
| 500 | 27.7 | 29.2 |
| Authors | Blockchain Platforms | Encryption Method | Transaction Privacy and Security | Efficiency |
|---|---|---|---|---|
| [34] | Ethereum | none | low | low |
| [35] | Hyperledger fabric | Homomorphic encryption | high | high |
| [36] | Hyperledger sawtooth | Symmetric encryption | high | high |
| Proposed system | Ethereum | RSA Asymmetric encryption | very high | very high |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ugochukwu, N.A.; Goyal, S.B.; Rajawat, A.S.; Islam, S.M.N.; He, J.; Aslam, M. An Innovative Blockchain-Based Secured Logistics Management Architecture: Utilizing an RSA Asymmetric Encryption Method. Mathematics 2022, 10, 4670. https://doi.org/10.3390/math10244670
Ugochukwu NA, Goyal SB, Rajawat AS, Islam SMN, He J, Aslam M. An Innovative Blockchain-Based Secured Logistics Management Architecture: Utilizing an RSA Asymmetric Encryption Method. Mathematics. 2022; 10(24):4670. https://doi.org/10.3390/math10244670
Chicago/Turabian StyleUgochukwu, Nwosu Anthony, S. B. Goyal, Anand Singh Rajawat, Sardar M. N. Islam, Jiao He, and Muhammad Aslam. 2022. "An Innovative Blockchain-Based Secured Logistics Management Architecture: Utilizing an RSA Asymmetric Encryption Method" Mathematics 10, no. 24: 4670. https://doi.org/10.3390/math10244670
APA StyleUgochukwu, N. A., Goyal, S. B., Rajawat, A. S., Islam, S. M. N., He, J., & Aslam, M. (2022). An Innovative Blockchain-Based Secured Logistics Management Architecture: Utilizing an RSA Asymmetric Encryption Method. Mathematics, 10(24), 4670. https://doi.org/10.3390/math10244670







.png)

