Abstract
This contribution applies tools from the information theory and soft computing (SC) paradigms to the embedding and extraction of watermarks in aerial remote sensing (RS) images to protect copyright. By the time 5G came along, Internet usage had already grown exponentially. Regarding copyright protection, the most important responsibility of the digital image watermarking (DIW) approach is to provide authentication and security for digital content. In this paper, our main goal is to provide authentication and security to aerial RS images transmitted over the Internet by the proposal of a hybrid approach using both the redundant discrete wavelet transform (RDWT) and the singular value decomposition (SVD) schemes for DIW. Specifically, SC is adopted in this work for the numerical optimization of critical parameters. Moreover, 1-level RDWT and SVD are applied on digital cover image and singular matrices of LH and HL sub-bands are selected for watermark embedding. Further selected singular matrices and are split into non-overlapping blocks, and diagonal positions are used for watermark embedding. Three-level symmetric encryption with low computational cost is used to ensure higher watermark security. A hybrid grasshopper–BAT (G-BAT) SC-based optimization algorithm is also proposed in order to achieve high quality DIW outcomes, and a broad comparison against other methods in the state-of-the-art is provided. The experimental results have demonstrated that our proposal provides high levels of imperceptibility, robustness, embedding capacity and security when dealing with DIW of aerial RS images, even higher than the state-of-the-art methods.
Keywords:
aerial images; RDWT–SVD; digital image watermarking; random key; grasshopper; bat; hybrid optimization MSC:
68U10; 68T20
1. Introduction
The widespread use of the Internet and ever-evolving telecommunications technologies has led to an increase in the sharing of multimedia content, such as audio, video and images. The revolution of social networks, electronic health care systems, electronic commerce and the IoT has further accelerated the exchange of multimedia content through the Internet. Moreover, specific remote sensing (RS) tasks involving aerial images are largely known of, e.g., the transmission of aerial RS images for tracking weather, volcanic eruptions, disaster management and growth of cities or forests, among others [1]. RS images contain sensitive data; therefore, it is necessary to ensure their authenticity and provide copyright protection. There is a high possibility that these contents can be easily hacked and manipulated by unauthorized users. Furthermore, illegal distribution of RS images should be prevented. Therefore, the authenticity, integrity and confidentiality of images is very important. This issue can be addressed by using the digital image watermark (DIW) approach [2]. DIW is the process where a watermark such as text or an image is embedded in a cover image to get a watermarked image. Features such as robustness and imperceptibility are important for efficient watermarking schemes. The term imperceptibility represents the visual quality of the image. If the original and embedded images are the same in terms of visual perception, then it is very unnoticeable. Robustness refers to similarity between the original and extracted watermark images [3].
However, it is very difficult to maintain all of these features (i.e., imperceptibility, robustness and embedding capacity) in a single watermark scheme, and there is always a trade-off between them. To face this, an optimal scaling factor () should be used in the embedding process in order to obtain quality DIW results. In the last decade, an approach called soft computing (SC) [4] has emerged to tackle with the latter issue by proposing near-optimal solutions to complex optimization problems. In particular, nature inspired optimization (NIO) algorithms have become a viable solution to tackle with this problem due to their successful results [5,6]. Our proposal makes use of SC paradigm to derive near-optimal solutions for the scaling factor. Watermark security is also one of the important features to look for in a DIW scheme. The watermark can be embedded in the spatial or spectral domain. During streaming, the security of the watermark is also crucial. To ensure high security, researchers have suggested hashing, compression, Arnold maps and chaotic maps techniques. However, these techniques are either less secure or have high computational costs for encryption and decryption tasks [7].
In the existing literature, limited research has been done to address issues related to the copyright protection, authentication and security problems of remote sensing images. The proposed scheme aims to address the latter limitations of the current DIW method for aerial RS images by providing high imperceptibility, robustness and security with the optimal computational cost. Here, a 3-level watermark security scheme is proposed to achieve high watermark security with a low computational cost. Furthermore, a grasshopper–BAT (G-BAT) hybrid NIO algorithm is proposed for the optimal computation of the scaling factor to balance the trade-off between watermarking characteristics.
The structure of the paper is as follows. Section 2 provides a brief review of the state-of-the-art of DIW, describing several of the contributions and limitations of the current methods in the field. This discussion is followed by the motivation and contribution of the proposed scheme. The proposed scheme is described in detail in Section 3, and Section 4 is focused on its experimental evaluation. Finally, Section 5 provides relevant comments on the results reported as a conclusion and outlines work that may be carried out in the future.
2. Literature Review
As stated, the DIW scheme came into being and has been widely used to secure the copyright of one’s content, such as images, text, audio and video. The initial DIW schemes that exist focused primarily on imperceptibility and robustness by incorporating watermarking in the spatial and spectral domains. In particular, the schemes proposed in [8,9,10] used the spatial domain in order to embed the watermark in the image. In the spatial domain, embedding can be done directly by using pixel values of the image. This gives us high imperceptibility and less robustness. The majority of the researchers proposed methods dealing with DIW from the frequency domain for the watermark embedding [10,11,12,13] to ensure higher robustness and imperceptibility. Furthermore, to increase the imperceptibility and robustness of the watermark scheme, hybrid transformations are suggested [14,15,16,17,18]. For the secure transmission of aerial images in remote sensing applications, some researchers proposed the DIW schemes [19,20,21,22,23]. In order to incorporate a watermark in satellite images, the DIW approach suggested in [19] used a degradation and restoration model and a chaotic map for watermark security.
Furthermore, [20] describes a DWT transform scheme for watermarking remote sensing images. To secure the watermark in this scheme, Arnold cat maps are used. For secure transmission of compressive remote sensing images, a hybrid LWT–Hadamard–ternary watermark sequence DIW scheme is suggested in [21].
A DIW scheme propped in [22] employs a hybrid DWT–HD–SVD transform to safeguard the copyright of landside images. The ideal embedding factor is discovered using particle swarm optimization (PSO) and the firefly optimization approach. Additionally, the step space filling curve-based approach is used to achieve security. The DIW approach suggested in [23] used the scale-invariant feature and wavelet transform to include aerial images for copyright protection.
To balance the trade-offs in the watermark features, a scaling factor (i.e., ) is used for the watermark embedding process. Some of the researchers used a constant scaling factor to optimize all the images [10], which may not work effectively for all kinds of imaging modalities. Therefore, optimization of scaling factor plays a crucial role in the entire DIW process. Specifically, the DIW algorithms proposed in [14,15,16,18] adopted the use of NIO algorithms for scale factor optimization. Nevertheless, despite the good performances of these methods, the results in terms of imperceptibility and robustness can be improved. On the other hand, NIO algorithms alone are not very effective at balancing the exploration and exploitation of algorithm search behavior. Thus, there is a need to develop hybrid optimization algorithms to properly balance the search behavior. Additionally, the security of the watermark has not been given much importance by the field. The methods proposed in [10,15,17,23] have less focus on watermark security, and the schemes proposed in [14,16,19,20,21] used chaotic maps and Arnold maps for watermark security. However, these methods are less secure methods. It is suggested to use a pseudo-random key for watermark encryption in [18], but the computational cost of the key generation process is high. Therefore, developing high security approaches with lower computational costs is both a challenging and needed task.
Motivation and Contributions:
A review of these watermark schemes revealed that the majority of existing DIW schemes have less efficacious embedding scaling factors and overlooked watermark security. To address the security issue, a 3-level watermark security scheme is proposed in this paper to achieve high watermark security with low computational cost, tackling aerial RS images. Furthermore, our proposal is based on the design of a hybrid optimization algorithm for the optimal computation of the scaling factor by using a NIO algorithm, i.e., G-BAT. An outline of the main contribution of our work is as follows:
I. Higher security with low computational cost: Three levels of watermark security, i.e., shuffling, substitution and partitioning, are suggested in the proposed scheme to ensure high watermark security with low computational cost. At the 1st level, row-column-zigzag (RCZ) shuffling is applied to obtain a shuffled watermark. Then, using the Lehmer Random Number Generator (LRNG), substitution is performed on the RCZ random watermark to obtain an encrypted watermark. An additional encrypted watermark is divided into odd and even position pixels for embedding.
II. Scaling factor optimization using hybrid G-BAT: Scale factor optimization using a hybrid NIO-based G-BAT algorithm to balance trade-offs in watermark features and to balance exploration and exploitation search behavior of watermarks.
III. High imperceptibility and robustness: Employment of a hybrid RDWT–SVD transformation for high imperceptibility and robustness. Due to its change-invariant nature, RDWT is resistant to geometric attacks. SVD, on the other hand, is resistant to filtering and noise attacks.
IV. Application area: The proposed DIW scheme is used to address security concerns in the transmission of digital images of aerial RS images over the Internet. Furthermore, it combats various threats in the transmission of RS images, such as copyright protection, copy control and unauthorized access.
3. Materials and Methods
A hybrid RDWT–SVD based DIW scheme is proposed for secure transmission of aerial RS images through digital communications channels. The proposed scheme ensures high robustness, imperceptibility, security and embedding capacity. Section 3.1, Section 3.2, Section 3.3 and Section 3.4 are devoted to elucidate the proposed scheme.The flowchart of the proposed scheme is provided in Figure 1.
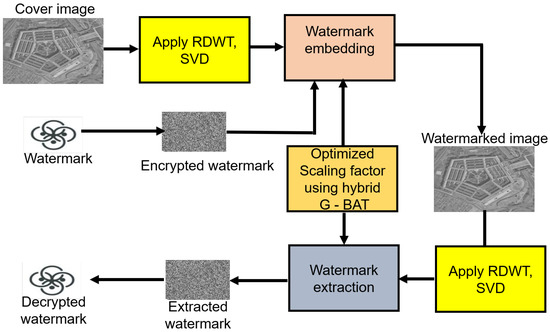
Figure 1.
Flowchart of the proposed scheme.
3.1. Watermark Embedding
A cover image (C) of size and a binary watermark (W) of size are considered in the suggested scheme. First, 1-level RDWT is applied on C to decompose it into four sub-bands: LL, LH, HL and HH. Sub-bands LH and HL are chosen for watermark embedding, as they undergo less distortions due to embedding than LL and HH. Since RDWT is shift invariant and avoids downsampling in its sub-bands, each sub-band is of the same size as C. RDWT is more reliable in conveying watermarks with a high embedding capacity by this property. However, it is more vulnerable to noise and filtering attacks. To mitigate this pitfall, the proposed scheme employs a hybrid RDWT-SVD algorithm. SVD is applied on LH and HL, which decomposes into , , , , and sub-matrices, respectively. and represent the column and row orthogonal matrices; and represents singular diagonal matrices. Since the tiny fluctuation in singular values is unlikely to impact the image’s visual perception, the watermark is embedded by altering these singular values that show high robustness. Therefore, and matrices are selected and partitioned into non-overlapping blocks (, ) for embedding. To ensure high imperceptibility and robustness, it uses an optimized scaling factor (); an encrypted even () and odd () watermark are embedded using Equations (1) and (2) into diagonal positions of and , respectively. The process of watermark encryption as elucidated in Section 3.3 and scaling factor optimization using G-BAT is described in Section 3.4. Finally, inverse SVD and RDWT are applied to get watermarked image ().
where k = 1, 2 and 3; and is optimized scaling factor.
The proposed watermark embedding, encryption and scaling factor optimization are shown in Figure 2. The process of watermark extraction is explained in detail in the next Section 3.2.
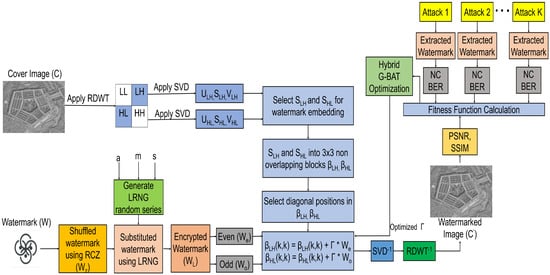
Figure 2.
Block diagram for watermark encryption and embedding.
3.2. Watermark Extraction
The proposed DIW scheme is blind, as the original image is not required for watermark extraction. The secret keys (, , , a, m, s) are used in the proposed scheme to extract the watermark from the watermarked image. The watermark extraction process is the reverse of the embedding process. For watermark extraction, RDWT is applied on the watermarked image to obtain sub-bands , , and . On sub-bands and , the SVD transform is applied, and it further decomposes into , and ; and , and . Select and and and singular arrays and split them into non-overlapping blocks ( and ; and , and respectively). The encrypted and are extracted from and using Equations (3) and (4).
where k = 1, 2 and 3; and is the optimized scaling factor.
The block diagram for watermark extraction and decryption is shown in Figure 3. The extracted and are decrypted using a decryption approach, as explained in Section 3.3.2, to obtain the watermark image (). The following subsections describe the watermark encryption and decryption process.
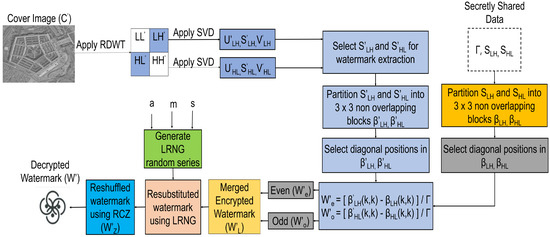
Figure 3.
Block diagram for watermark extraction and decryption.
3.3. Watermark Encryption and Decryption
In the transmission of images over the Internet, ensuring the security of the watermark, is very important. In the proposed scheme, the security of the watermark is achieved by using a symmetric cryptographic approach. The proposed scheme ensures watermark security at 3 levels: (1) RCZ shuffle, (2) LRNG substitution and (3) odd-even partitioning.
3.3.1. Watermark Encryption
Shuffling is done along the rows and columns and in a zigzag pattern (RCZ). The Lehmer Random Number Generator (LRNG) is used for the substitution process. Finally, the resulting encrypted watermark is divided into two parts. To secure the watermark, the RCZ is used in conjunction with the LRNG. This provides the encrypted watermark image, which is split into odd and even pixels and embedded in the cover image. In the RCZ shuffling process, initially the shuffling is done along the rows, followed by the columns, and then in a zigzag fashion. The procedural steps for watermark encryption are explained in Algorithm 1, and the 3-level encryption process is explained next.
| Algorithm 1: Algorithm for watermark encryption. |
| Require: Watermark image (W) Ensure: Even () and Odd () watermarks
|
Initially, in row shuffling, even rows, i.e., row ith, are shuffled into row th, as shown in Figure 4a. Furthermore, similarly, odd rows, i.e., row ith, are shuffled into row th to get . Similarly, in column shuffling, odd and even columns are shuffled into ; i.e., column jth is shuffled into column th, as shown in Figure 4b, to get . In zigzag shuffling, shuffling starts from the position pixel in the upper left corner of the image and traverses the zigzag path at , as shown in Figure 4c. The pixels that have been traversed are stored in the one-dimensional array, which is then converted to the 2D array for a mixed watermark (). Furthermore, is substituted using a binary random key () generated from LRNG.
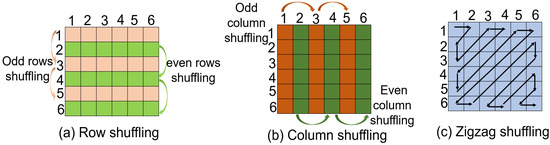
Figure 4.
RCZ shuffling.
LRNG is a pseudo-random number generator used to generate decimal random numbers within a given range. The generation of random series uses LRNG as mentioned in [24]. After generation of the LRNG random string, each member of the string is converted to an equivalent 8-bit binary format to generate a binary random key () of size equal to the size of W. Then, is combined with to get encrypted W (). Additionally, is divided into even () and odd () position pixels of size ()/2 using Equations (5) and (6).
where is the size of .
The process of watermark encryption is elucidated with an example in Figure 5a. The process of watermark decryption is explained in the next sub-section.
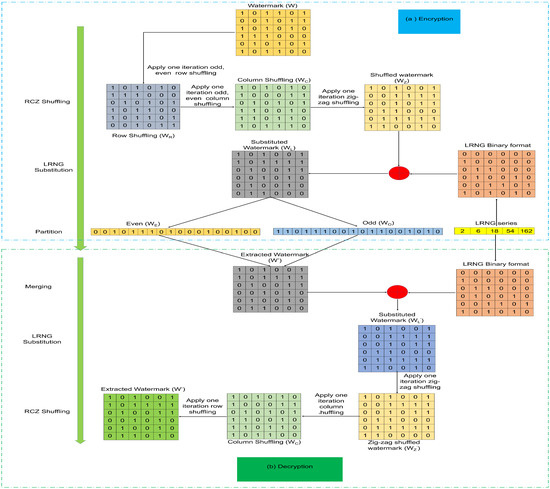
Figure 5.
Three-level watermark encryption and decryption process.
3.3.2. Watermark Decryption
Watermark decryption is a reverse process to watermark encryption. First, the extracted even () and odd () position pixels are merged to obtain an encrypted watermark (). The process of extracting and from is explained in Section 3.2. More LRNG random strings are generated using secret keys (a, m, s) and convert them to the equivalent binary format (). Next, we XOR between and to get an encrypted watermark of level 1st (). Furthermore, we apply the RCZ process to get the original watermark (). The watermark decryption process is clarified with an example in Figure 5b.
3.4. Scaling Factor Optimization Using Hybrid G-BAT
DIW characteristics such as imperceptibility, robustness and embedding capacity are always trade-offs in designing a DIW scheme. A good DIW scheme must achieve a balance between the latter three traits. The balancing of these three features is aided by the scaling factor (i.e., ), and using a suitable scaling factor is critical for retrieving quality DIW outcomes. The majority of the researchers recommended using optimization algorithms to find the optimum scaling factor. Specifically, the NIO algorithms, such as evolutionary algorithms (i.e., GA, DE and JAYA) and swarm intelligence (PSO, ABC, grasshopper, Bat, firefly), have been suggested in the last few years. However, a good balance of exploration and exploitation of search behavior for NIO is also critical. In our proposed scheme, a hybrid grasshopper–BAT (G-BAT) optimization algorithm is adopted to reconcile the search behaviors of exploration (search agents are encouraged to move abruptly) and exploitation (search agents tend to move abruptly).
The grasshopper optimization (GO) algorithm is a simple and fast swarm intelligence-based NIO algorithm that mimics the behavior of grasshoppers [25]. In terms of search behavior, GO strikes a good balance between exploration and exploitation, and also avoids getting stuck in local optima. As well as its advantages, it also has some limitations: grasshoppers reach their comfort zones faster, but the swarm does not join a key point, which results in low search accuracy and premature convergence [26]. To address the shortcomings of the GO algorithm and improve convergence rates and search accuracy, the proposed scheme integrates GO with the BAT algorithm. BAT is also a swarm intelligence optimization algorithm based on NIO [27]. The unique feature of the BAT algorithm is that it balances exploration and exploitation behavior through echolocation frequency tuning control and auto-zoom capability. It also has the advantage of requiring parameter control rather than the fixed and preset algorithmic dependent parameters used by many NIO algorithms, allowing automatic switching from exploration to exploitation to reach the optimal solution. Table 1 shows the basic parameters for the optimization of the hybrid G-BAT [28], and Figure 6 shows the flowchart representation for the hybrid G-BAT.

Table 1.
List of basic parameters for hybrid G-BAT.
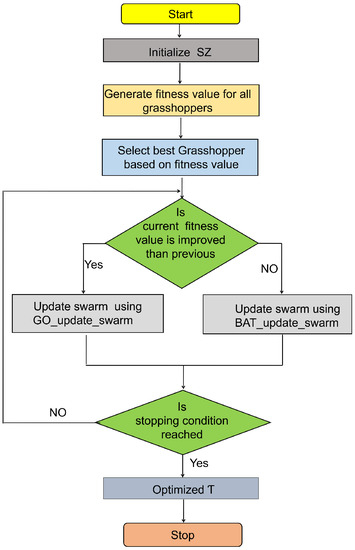
Figure 6.
Flowchart of scaling factor () optimization using G-BAT.
The fitness function used for scaling factor () optimization, as shown in Equation (7).
where PSNR and SSIM are the imperceptibility metrics; NC and BER are robustness metrics; and is the chosen population value. K is the number of attacks. In the proposed scheme, an average of K = 6 attacks are considered for FF evaluation. To start the hybrid G-BAT, the swarm (grasshopper) is randomly generated using the swarm generation formula, as shown in Table 1. Then, using Equation (7), fitness values are calculated for all entries in the swarm, and the best grasshopper (minimum fitness value) is chosen for further processing. The position of a grasshopper is updated each time the fitness values of the current and previous grasshopper are compared. If the current fitness value improves over time, the proposed scheme updates the new swarm using GO optimization. BAT optimization, on the other hand, helps in upgrading new swarms. To achieve the best scaling factor (), GO and BAT are executed in parallel to encourage swarm information sharing, and as a result, improve search efficiency.
4. Experimental Results and Discussion
This section is devoted to reporting about the performance of the proposed DIW method. Specifically, our proposal is evaluated according to terms of imperceptibility, robustness and security. The experiments were carried out in the MATLAB 2014b environment. A cover image of size and a binary watermark of size were considered for the generation of experimental results. Aerial RS and general cover test images and watermark were taken from the USC-SIPI [29] and Kaggle [30] dataset, as shown in Figure 7 and Figure 8.

Figure 7.
Gray-scale cover images (1–6) with corresponding watermark images (a–f) and extracted watermark images (I–VI). Color cover images (7–12) with corresponding watermark images (g–l) and extracted watermark images (VII–XII) under zero attacks.
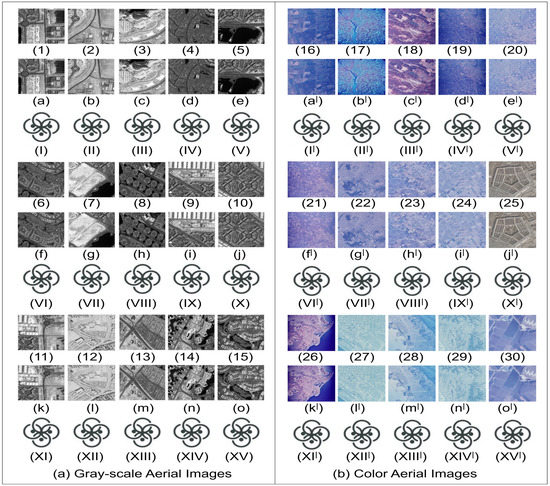
Figure 8.
Aerial images (gray-scale images (1–15), color images (16–30)) with corresponding watermarked images (gray-scale watermarked images (a–o), color watermarked images (a–o)) and extracted watermark images (I–XV,I–XV).
4.1. Imperceptibility Test
The visual quality of the original and embedded images is identical and is called imperceptibility. It is very important to maintain high imperceptibility for watermarked images. First, the imperceptibility performance of the proposed scheme for gray-scale cover images of different modalities is evaluated, as shown in Figure 7. Subjective analysis of the cover and the watermarked image in Figure 7 shows that both images are identical. Furthermore, the watermark extracted under zero attacks is clearly visible. In addition, the objective analysis of imperceptibility was performed using PSNR and SSIM. The relationships used for PSNR and SSIM are given in Equations (8) and (10), respectively.
where C and are cover and watermarked images; are the sizes of cover and watermarked images. and are means of C and : . is the variance of C and . is the covariance of C and .
The imperceptibility performance of the proposed scheme was analyzed for general images with random scale factor ( = 0.9); the scale factor was optimized using GO, BAT and the proposed hybrid G-BAT, and the corresponding PSNR and SSIM values are shown in Table 2. In Table 2, it can be seen that for all gray-scale and color cover images, the PSNR > exceeds the threshold value of 37 dB. Furthermore, SSIM is equal to the ideal value 1 using random and optimized using GO, BAT and hybrid G-BAT. The result presented in Table 2 indicates greater imperceptibility of the proposed scheme for general images.

Table 2.
PSNR and SSIM for general images (gray-scale and color) with random and optimized using GO, BAT and G-BAT.
In addition, the imperceptibility performance of our proposal was analyzed for 30 aerial images (gray-scale and color) with random and optimized by GO, BAT and G-BAT. The corresponding PSNR and SSIM values are presented in Table 3. In Table 3, it can be seen that PSNR and SSIM for the 30 aerial images using random and with GO, BAT and G-BAT are higher than the threshold values. With random , the proposed scheme shows the ideal value of PSNR for all the color images. The proposed DIW method also shows the ideal SSIM value for all the images with random and with optimized . Therefore, our proposal shows higher imperceptibility even if it uses random , and an ever higher value of PSNR for optimized , while keeping the SSIM value at 1 for all the images with different . Therefore, our method demonstrated high imperceptibility for both aerial RS and conventional images.

Table 3.
PSNR, SSIM, NC and BER (under zero attack) with random and optimized using GO, BAT and G-BAT for 30 aerial RS (gray-scale and color) images taken from USC-SIPI [29] and Kaggle [30] datasets.
4.2. Robustness Test
Robustness is another important requirement of the watermark scheme. Ideally, the original and extracted watermark should be identical. The robustness performance of the proposed scheme was analyzed using NC and BER metrics. The relationship between NC and BER is shown in Equations (11) and (12).
where W and are original and extracted watermarks.
where EB represents the number of incorrectly decoded bits in the extracted watermark, TB represents the total number of bits and the initial value of the counter = 0.
The robustness of our proposal was evaluated on 30 aerial RS images taken from the USC-SIPI [29] and Kaggle [30] datasets, as shown in Figure 8. The corresponding parameters NC, BER below zero random attacks and optimized (GA, BAT, G-BAT) are tabulated in Table 3. For the 30 aerial RS images, the proposed method shows a value of NC above the threshold and BER below the threshold with random and optimized . When compared to random and optimized , it can be observed that the robustness improves with optimized . NC values are highest and BER is lowest with optimized using the proposed G-BAT for all the aerial RS images. This observation demonstrates that greater robustness is achieved by using optimized using G-BAT.
In addition, the robustness performance of the proposed scheme (under zero attack) was analyzed for the general images shown in Figure 7 and the corresponding NC. The BER is tabulated in Table 4 with random , and with optimized using GO, BAT and hybrid G-BAT. In Table 4 it can be seen that, with random = 0.9 NC for all gray-scale and color images, the threshold value is above 0.7 [31], and the BER is less than the threshold value 0.5. To improve the robustness of the proposed scheme, the optimized was built using GO, BAT and NC. The BER values are tabulated in Table 4. With the use of GO, the robustness of BAT was improved over the random . For all gray-scale and color images, NC and BER with hybrid G-BAT are almost equal to the ideal value(s) of 1.0. As can be seen in Table 4, the proposed hybrid G-BAT improved the robustness performance (under zero attack) for gray-scale and color images from 0.92 to 0.99 and from 0.91 to 0.99, respectively. As can be seen in Table 2 and Table 3, using optimized shows a lower value PSNR than using random , and keeps PSNR higher than threshold value 37 dB and the corresponding NC. BER reached the ideal value (1.0), as shown in Table 3 and Table 4. Numerical comparisons of NC and BER for the 10 test aerial RS images with random and optimized are shown in Figure 9 and Figure 10, respectively. It can be seen that the hybrid G-BAT demonstrates greater robustness than the other optimized . Thus, as revealed in Table 2, Table 3 and Table 4 and Figure 9 and Figure 10, the hybrid G-BAT approach balances the trade-offs in the characteristics of DIW (i.e., imperceptibility and robustness).

Table 4.
NC and BER for normal (gray-scale and color images) images with random and with optimized using GO, BAT and G-BAT under zero attacks.
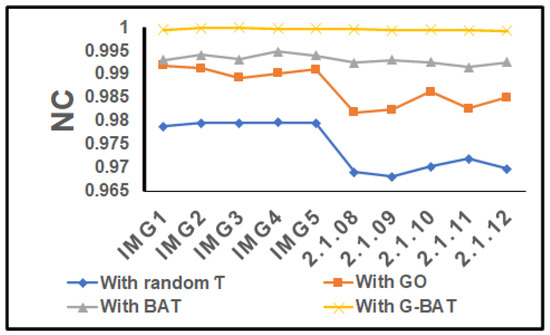
Figure 9.
NC for the 10 test aerial cover images with random , with GO, with BAT and with G-BAT under zero attacks.
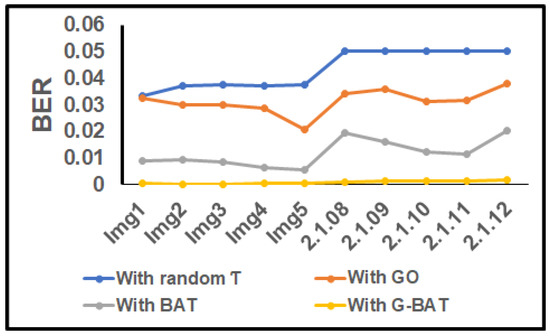
Figure 10.
BER for the 10 test aerial cover images with random , with Go, with BAT and with G-BAT under zero attacks.
The robustness performance of the proposed scheme under attacks was analyzed with random and with optimized using GO, BAT and G-BAT. The corresponding values of NC and BER are tabulated in Table 5 and Table 6. In Table 5 and Table 6 it can be seen that, under all attacks, G-BAT using optimized shows a higher value of NC and BER than considering random , or optimized with GO or BAT.

Table 5.
NC and BER for aerial RS images Img3 (taken from USC-SIPI [29]) under attacks with random and with optimized using GO, BAT and G-BAT.

Table 6.
NC and BER for Lena image under attacks with random and with optimized using GO, BAT and G-BAT.
In addition, the robustness of the proposed scheme was examined on three watermarked sampled aerial RS images against various image processing attacks, such as filtering attacks, sniffing attacks, compression and cut-off attacks with optimized using G-BAT. Our proposal is robust against filtering, noise and some geometric attacks, since its NC and BER values (see Table 7) are higher than threshold values for all images (Img1, 2.1.01, 2.1.02). The proposed method revealed limited robustness performance on rotation, clipping and scaling attacks with random . However, the robustness improves with optimized using the proposed hybrid G-BAT. This observation demonstrates the effectiveness of using our proposal using the hybrid G-BAT to achieve higher robustness against most attacks, and higher stealth performance. Therefore, our design of G-BAT shows more imperceptibility and robustness.

Table 7.
NC and BER for aerial RS images (Img1, 2.1.01, and 2.1.02) taken from USC-SIPI [29] and Kaggle [30] datasets under attacks with optimized using G-BAT.
4.3. Security Test
The security of the proposed encryption approach was tested using the correlation coefficient (CC) and entropy metrics [32] on five binary test images, and the experimental results are shown in Table 8. The value of CC between any two images is in the range from −1 to 1. If the value of CC is 1, it means that both images are identical, and if the value of CC is 0, it stands that both images are irrelevant. Otherwise, both images are negatively or positively correlated. In Table 8 it can be seen that, for all test images, the values of CC between the original encrypted images in the horizontal, vertical and diagonal directions are less than −0.6. The latter indicates that both the original and encrypted images are negatively correlated. When the value of CC between original and decrypted images is 1, it indicates that they are identical. Additionally, security performance is analyzed by entropy, as shown in Table 8. For all test images, the entropy value of the encrypted image is higher than that of the original image. This also indicates that the proposed method generates an encrypted image with different entropies. From the above discussion, it can be stated that the proposed 3-level encryption scheme generates stronger encryption images and decrypts successfully as well.

Table 8.
CC values between original watermark image (W) and encrypted images (EW). CC values between original image and decrypted images (DW) and entropies of original image and encrypted images (H—horizontal, V—vertical, D—diagonal).
4.4. Computational Time
Computational time is the amount of time required to complete an embedding and extraction process. Computational times for the embedding and extraction in seconds for different test images are tabulated in Table 9. In Table 9, it can be seen that the embedding and extraction times for all gray-scale images were less than 0.16 and 0.07 s, and for the color images they were less than 0.26 and 0.09 s, respectively. The variation in gray-scale and color images was minimal. Therefore, the computational time of our DIW method can be considered minimal, since the watermark was embedded and extracted in less than 0.3 and 0.09 s, respectively.

Table 9.
Embedding and extraction time (in seconds) of different test cover images.
4.5. Comparative Study
In this section, the performance of the proposed DIW method is compared against those considered state-of-the-art in terms of imperceptibility, robustness, embeddability and security: Ali and Nasab [14], Preethi and Kishore [15], Zhu et al. [16], Ali [17] and Singh et al. [18]. Ali and Nasab [14] proposed a SWT and SURF transformation method for robust image transmission. The Arnold map was suggested for security and BAT optimization for scaling factor optimization. An ABC optimization method was proposed by Preethi and Kishore [15] in the DWT+DCT domain for robust image transmission. The IWT+SVD hybrid was suggested by Zhu et al. [16]. In particular, GA is used to optimize the scaling factor and affine transformation for security. Ali [17] proposed the DWT+SVD DIW scheme for robust image transmission. Recently, Singh et al. [18] contributed a IWT+SVD method in the hybrid domain for robust image transmission. This latter scheme uses a pseudo-random key for encryption. A comparative overview against other state-of-the-art methods is explained in Table 10. In Table 10 it can be seen that the DIW scheme proposed in [15,17] has overlooked watermark security, and the schemes proposed in [14,16] uses the Arnold map and Affine transformations for safety. The Arnold map and affine transformations provide less security and can be easily cracked. The scheme proposed in [18] uses a pseudo-random key approach for encryption, and the key is generated with high computational cost. Our proposed scheme guarantees security at three levels, shuffling, substitution and partitioning, at a low computational cost. Compared to the state-of-the-art methods proposed in [14,15,16,17], our proposal of encryption scheme shows better watermark security. Compared to the scheme in [18], our scheme provides high security at a low computational cost. Moreover, the method proposed in this paper provides a higher incorporation capacity than all other next-generation schemes ([14,15,16,17,18]), as analyzed in Table 10.

Table 10.
Comparison analysis of our proposal against those considered the state-of-the-art.
Furthermore, the imperceptibility performance of our DIW method was tested with the comparison schemes for Lena and Baboon, as shown in Figure 11. The PSNR of the Lena and the Baboon images treated with the proposed method are higher than those of all tested schemes [14,15,16,17,18]. The robustness performance under zero attacks is shown in Figure 12. In Figure 12, it can be seen that the our DIW scheme has a higher NC than the scheme presented in [16], and it has an almost equal NC to the schemes of [14,15,16,18]. The additional robustness of our proposal was tested under different image processing attacks, such as Gaussian filter (GF), median filter (MF), sharpness (SHARP), salt and pepper noise (SP), histogram equivalent (HQ), gamma correction (GC) and JPEG compression (JPEG), as shown in Figure 13.
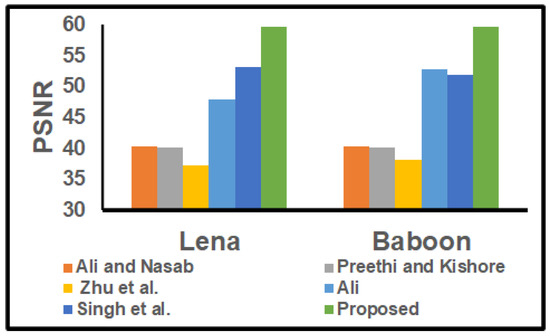
Figure 11.
PSNR comparison of our method against state-of-the-art methods for Lena and Baboon images.
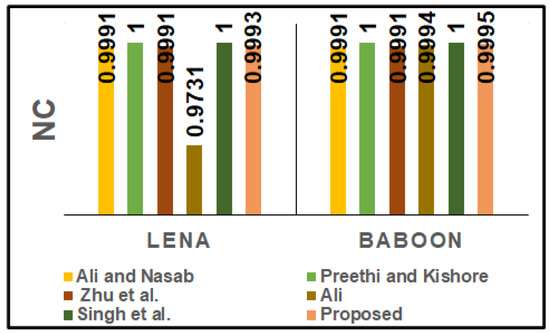
Figure 12.
NC comparison of our method against state-of-the-art methods for Lena and Baboon images under zero attacks.
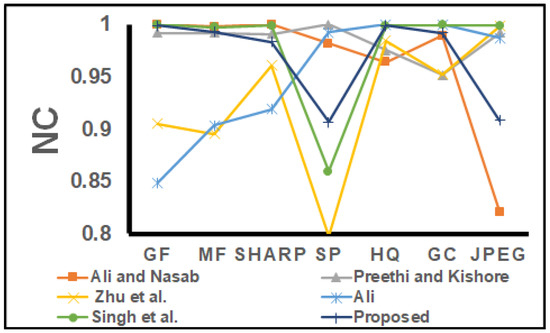
Figure 13.
Robustness comparison of our method against those in the state-of-the-art for the Lena image under attacks.
In Figure 13, it can be seen that the proposed method shows greater robustness when considering filter attacks (GF, MF, and SHARP) than the schemes in [16,17]. Additionally, it shows robustness performance almost equal to those of the schemes proposed in [14,15,18]. For JPEG attack, the proposed scheme had better performance than the schemes of [14], but lagged in comparison to the schemes presented in [15,16,17]. However, the proposed scheme had an NC ≈ 0.92, indicating higher robustness against JPEG attack. For noise attacks, the proposed scheme showed greater robustness than the schemes proposed in [16,18] and was almost equally robust as the schemes proposed in [14,15,17]. The proposed scheme showed limited performance against noise attacks, which can be seen as future work. For HQ and GC attacks, the proposed scheme is superior to the schemes in [14,15,16,18]. The comparative analysis revealed that the proposed scheme reports higher than or the same robustness as the other schemes. Furthermore, it revealed high imperceptibility, embedding ability and security compared to the other schemes ([14,15,16,17]).
The scheme of Singh et al. [18] showed higher imperceptibility, robustness and embedding capacity with an adaptively generated ISF scaling factor. Moreover, the authors suggested using NIO algorithms (GA, ABC and FO) to improve watermarking characteristics. The GA approach showed higher imperceptibility and robustness. For a fair comparison, in this paper, GA generated PSNR and NC values according to those in Singh et al. [18]. As shown in Figure 11 and Table 10, the PSNR and the embedding capacity of our proposed DIW method are higher than those of the scheme [18]. The computational times for the embedding and extraction process of Singh et al. [18] and our proposal for different images (Lena, Baboon and Koala) are analyzed next. The scheme of Singh et al. [18] achieved embedding times of (in seconds) 1.919606, 1.465614 and 1.378239 s for Lena, Baboon and Koala images, respectively, whereas our method took 0.150429, 0.269723, 0.240605 s. Likewise, the computational times by the method of Singh et al. [18] regarding extraction were 1.056093, 0.915152 and 0.98756 s, whereas our proposal achieved 0.055273, 0.095462 and 0.077382 s for the same images. From this, it can be seen that our proposal takes less time to embed and extract images for all those images. Therefore, the computational time reported by our hybrid G-BAT DIW method is lower than that of the GA-based method in [18]. Moreover, our method brings NC closer to the ideal value. From the above observations and discussions, it can be stated that the proposed scheme outperformed all the state-of-the-art methods in [14,15,16,17,18].
5. Conclusions and Future Work
In this article, a RDWT-SVD-based DIW scheme was proposed for secure transmission of aerial remote sensing images on the Internet. A hybrid G-BAT optimization algorithm was proposed for optimizing the scaling factor (). An optimized scaling factor was used as an embedding advantage for watermark embedding to balance the watermarking characteristics trade-off. Further, to ensure high watermark security at with little computation, a 3-level encryption approach was proposed. The performance of the proposed DIW scheme was analyzed with random , optimized (using NIO algorithms, i.e., GO and BAT) and optimized using the proposed hybrid G-BAT. Experimental results show that the proposed DIW scheme has superior imperceptibility and robustness with the obtained by G-BAT optimization. Thus, the proposed scheme effectively balances watermarking characteristics. It was observed that original and encrypted watermarks were highly uncorrelated, whereas original and decrypted watermarks were highly correlated, indicating higher watermark security. Furthermore, the performance of the proposed scheme has been compared with those of recent state-of-the-art DIW schemes. The proposed DIW scheme reported comparatively higher performance in terms of imperceptibility, robustness, security and embedding capacity. Experimental results and a comparative study validated the effectiveness of the proposed DIW scheme. It can be successfully used for for copyright protection, ownership verification, image authentication and image security when remote sensing images are transferred over the Internet. The proposed scheme has limited robustness against geometric attacks such as rotation and clipping attacks. Improving the robustness of the proposed scheme against geometric attacks could be seen as future research work.
Author Contributions
Conceptualization and methodology, K.J.D., P.S., H.K.T., J.S. and J.K.D.; software, K.J.D. and P.S.; validation and formal analysis, H.K.T., J.S., J.K.D. and A.R.-M.; investigation and resources, P.S., K.J.D. and M.V.J.K.; writing original draft preparation, P.S. and K.J.D.; writing review and editing, J.S., H.K.T., J.K.D. and A.R-M.; supervision, P.S., H.K.T., J.S. and M.V.J.K.; project administration, P.S., K.J.D. and H.K.T. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Jiang, H.; Peng, M.; Zhong, Y.; Xie, H.; Hao, Z.; Lin, J.; Ma, X.; Hu, X. A Survey on Deep Learning-Based Change Detection from High-Resolution Remote Sensing Images. Remote Sens. 2022, 14, 1552. [Google Scholar] [CrossRef]
- Evsutin, O.; Dzhanashia, K. Watermarking schemes for digital images: Robustness overview. Signal Process. Image Commun. 2022, 100, 116523. [Google Scholar] [CrossRef]
- Zainol, Z.; Teh, J.S.; Alawida, M. Alabdulatif A Hybrid SVD-based image watermarking schemes: A review. IEEE Access 2021, 9, 32931–32968. [Google Scholar]
- Gendreau, M.; Potvin, J.Y. (Eds.) Handbook of Metaheuristics; Springer: New York, NY, USA, 2010; Volume 2.9. [Google Scholar]
- Singh, O.P.; Singh, A.K.; Srivastava, G.; Kumar, N. Image watermarking using soft computing techniques: A comprehensive survey. Multimed. Tools Appl. 2021, 80, 30367–30398. [Google Scholar] [CrossRef]
- Khanduja, N.; Bhushan, B. Recent advances and application of metaheuristic algorithms: A survey (2014–2020). In Metaheuristic and Evolutionary Computation: Algorithms and Applications; Springer: Singapore, 2021; pp. 207–228. [Google Scholar]
- Shankar, R.; Vara Prasad, R.U.; Adiraju, R.V.; Krishna, R.V.; Nandan, D. A Review Paper Based on Image Security Using Watermarking. In Proceedings of the International Conference on Recent Trends in Machine Learning, IoT, Smart Cities and Applications, Hyderabad, India, 28–29 March 2021; Springer: Singapore, 2021; pp. 697–706. [Google Scholar]
- Su, Q.; Liu, D.; Yuan, Z.; Wang, G.; Zhang, X.; Chen, B.; Yao, T. New rapid and robust color image watermarking technique in spatial domain. IEEE Access 2019, 7, 30398–30409. [Google Scholar] [CrossRef]
- Abraham, J.; Paul, V. An imperceptible spatial domain color image watermarking scheme. J. King Saud. Univ.-Comput. Inf. Sci. 2019, 31, 125–133. [Google Scholar] [CrossRef]
- Kunhu, A.; Mansoori, S.A.; Al-Ahmad, H. A Novel Reversible Watermarking Scheme Based on SHA3 for Copyright Protection and Integrity of Satellite Imagery. Int. J. Comput. Sci. Netw. Secur. 2019, 19, 92–102. [Google Scholar]
- Mahmoud, K.; Datta, S.; Flint, J. Frequency Domain Watermarking: An Overview. Int. Arab J. Inf. Technol. 2005, 2, 33–47. [Google Scholar]
- Kang, X.; Chen, Y.; Zhao, F.; Lin, G. Multi-dimensional particle swarm optimization for robust blind image watermarking using intertwining logistic map and hybrid domain. Soft Comput. 2020, 24, 10561–10584. [Google Scholar] [CrossRef]
- Tewari, T.K.; Saxena, V. An improved and robust DCT based digital image watermarking scheme. Int. J. Comput. Appl. 2020, 3, 28–32. [Google Scholar] [CrossRef]
- Pourhadi, A.; Mahdavi-Nasab, H. A robust digital image watermarking scheme based on bat algorithm optimization and SURF detector in SWT domain. Multimed. Tools Appl. 2020, 79, 21653–21677. [Google Scholar] [CrossRef]
- Garg, P.; Kishore, R.R. An efficient and secured blind image watermarking using ABC optimization in DWT and DCT domain. Multimed. Tools Appl. 2021, 1–18. [Google Scholar]
- Zhu, T.; Qu, W.; Cao, W. An optimized image watermarking algorithm based on SVD and IWT. J. Supercomput. 2021, 78, 222–237. [Google Scholar] [CrossRef]
- Alzahrani, A. Enhanced Invisibility and Robustness of Digital Image Watermarking Based on DWT-SVD. Appl. Bionics Biomech. 2022, 2022, 5271600. [Google Scholar] [CrossRef] [PubMed]
- Singh, P.; Devi, K.J.; Thakkar, H.K.; Santamaría, J. Blind and Secured Adaptive Digital Image Watermarking Approach for High Imperceptibility and Robustness. Entropy 2021, 23, 1650. [Google Scholar] [CrossRef]
- Zhu, P.; Jiang, Z.; Zhang, J.; Zhang, Y.; Peng, W. Remote sensing image watermarking based on motion blur degeneration and restoration model. Optik 2021, 248, 168018. [Google Scholar] [CrossRef]
- Yuan, G.; Hao, Q. Digital watermarking secure scheme for remote sensing image protection. China Commun. 2020, 17, 88–98. [Google Scholar] [CrossRef]
- Tong, D.; Ren, N.; Zhu, C. Secure and robust watermarking algorithm for remote sensing images based on compressive sensing. Multimed. Tools Appl. 2019, 78, 16053–16076. [Google Scholar] [CrossRef]
- Mohan, A.; Anand, A.; Singh, A.K.; Dwivedi, R.; Kumar, B. Selective encryption and optimization based watermarking for robust transmission of landslide images. Comput. Electr. Eng. 2021, 95, 107385. [Google Scholar] [CrossRef]
- Hsu, P.H.; Chen, C.C. A robust digital watermarking algorithm for copyright protection of aerial photogrammetric images. Photogramm. Rec. 2016, 31, 51–70. [Google Scholar] [CrossRef]
- Mascagni, M.; Srinivasan, A. Algorithm 806: SPRNG: A scalable library for pseudorandom number generation. ACM Trans. Math. Softw. (TOMS) 2000, 26, 436–461. [Google Scholar] [CrossRef]
- Saremi, S.; Mirjalili, S.; Lewis, A. Grasshopper optimisation algorithm: Theory and application. Adv. Eng. Softw. 2017, 105, 30–47. [Google Scholar] [CrossRef] [Green Version]
- Ewees, A.A.; Elaziz, M.A.; Houssein, E.H. Improved grasshopper optimization algorithm using opposition-based learning. Expert Syst. Appl. 2018, 112, 156–172. [Google Scholar] [CrossRef]
- Yang, X.-S.; He, X. Bat algorithm: Literature review and applications. Int. J. Bio-Inspired Comput. 2013, 5, 141–149. [Google Scholar] [CrossRef] [Green Version]
- Yang, X.S. A New Metaheuristic Bat-Inspired Algorithm. In Nature-Inspired Cooperative Strategies for Optimization (NICSO 2010); Studies in Computational Intelligence; Springer: Berlin/Heidelberg, Germany, 2010; pp. 65–74. [Google Scholar]
- The USC-SIPI Image Database. Available online: https:/sipi.usc.edu/database/ (accessed on 20 January 2022).
- The Kaggle Image Database. Available online: https://www.kaggle.com/datasets (accessed on 20 January 2022).
- Rao, Y.R.; Prathapani, N.; Nagabhooshanam, E. Application of normalized cross correlation to image registration. Int. J. Res. Eng. Technol. 2014, 3, 12–16. [Google Scholar]
- Balaska, N.; Ahmida, Z.; Belmeguenai, A.; Boumerdassi, S. Image encryption using a combination of Grain-128a algorithm and Zaslavsky chaotic map. IET Image Process. 2020, 14, 1120–1131. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).