Optimized Intrusion Detection in the IoT Through Statistical Selection and Classification with CatBoost and SNN
Abstract
1. Introduction
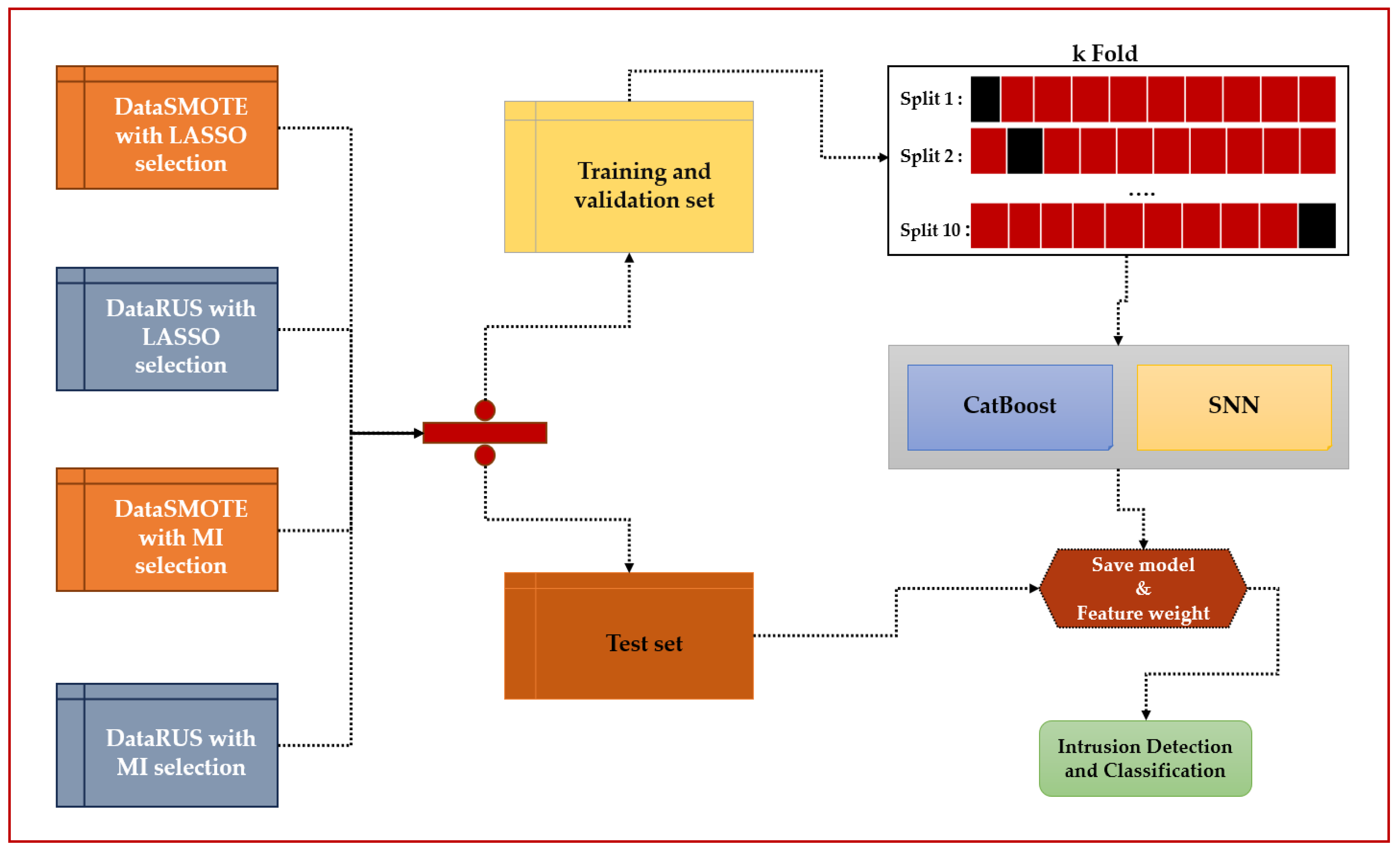
- Combining two class rebalancing methods (SMOTE and RUS) with two feature selection methods (LASSO and Mutual Information) to identify the most discriminative attributes.
- Generating four distinct datasets (SMOTE + LASSO, SMOTE + Mutual Information, RUS + LASSO, RUS + Mutual Information) to assess the combined impact of rebalancing and feature selection.
- Evaluating each dataset with two complementary classifiers: CatBoost and SNN.
- Conducting a systematic comparison of all configurations to determine the best trade-off between accuracy, recall, F1-score, and robustness against class imbalance.
2. Literature Review
3. Materials and Proposed Method
3.1. Materials
- Processor: Intel Core i5-8130U, 2.20 GHz
- Memory: 16 GB RAM
- Storage: SSD
- Operating system: Windows 11, 64-bit
3.1.1. Simple Neural Network (SNN)
- Architecture and hyperparameters:
- ✓
- Input layer: dimension = number of selected features
- ✓
- Hidden layer 1: 256 neurons, ReLU activation, Dropout 0.3
- ✓
- Hidden layer 2: 128 neurons, ReLU activation, Dropout 0.3
- ✓
- Output layer: num_classes neurons, softmax implicit via CrossEntropyLoss
- Hyperparameters:
- ✓
- Optimizer: Adam, learning rate = 0.001
- ✓
- Loss function: CrossEntropyLoss
- ✓
- Batch size: 128
- ✓
- Epochs: 100
- ✓
- Random seed: 42
- ✓
- Implementation: PyTorch version 2.8
3.1.2. CatBoost
- Configuration:
- ✓
- Objective: MultiClass
- ✓
- Random seed: 42
- ✓
- Validation: Stratified 10-fold cross-validation
- ✓
- Other hyperparameters: default settings optimized for classification tasks
- ✓
- Implementation: CatBoost Python version 3.10 library, CPU optimized
3.2. Dataset
- Mirai: botnet attack
- Scan: port scanning
- DoS: denial of service
- MITM ARP Spoofing: man-in-the-middle attack
- Normal: legitimate activity
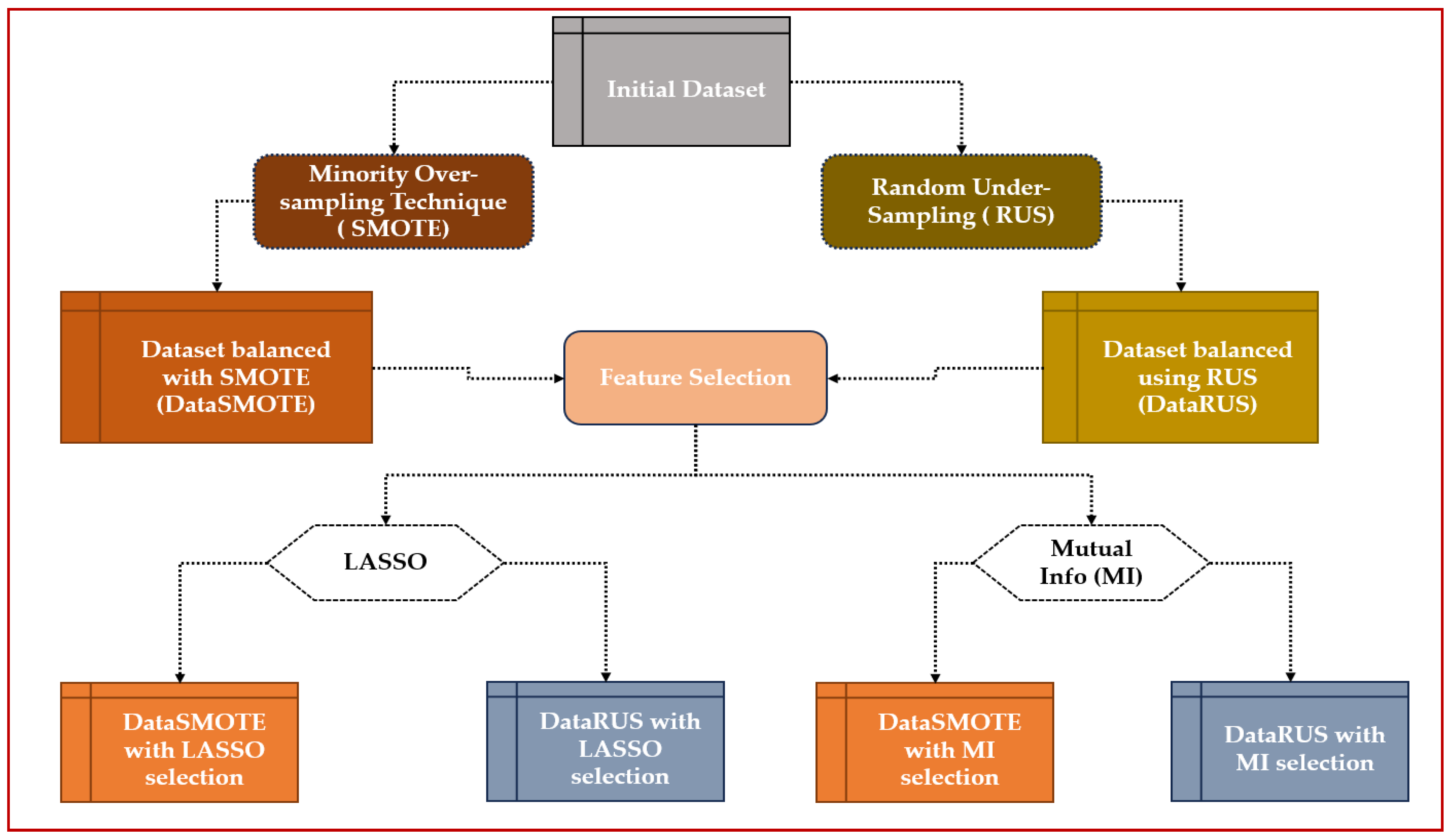
3.3. Proposed Methods
- Rebalancing classes
- ✓
- SMOTE (Synthetic Minority Over-sampling Technique)
- ✓
- Random Under-Sampling (RUS)
- Selection of characteristics
- ✓
- LASSO (Least Absolute Shrinkage and Selection Operator)
- ✓
- Mutual Information (MI)
- Creation of final datasets
- ✓
- DataSMOTE with LASSO selection
- ✓
- DataSMOTE with mutual information selection
- ✓
- DataRUS with LASSO selection
- ✓
- DataRUS with mutual information selection
- ✓
- 80% dedicated to training and validation, to build and optimize the models;
- ✓
- 20% reserved for final testing, ensuring independent and impartial performance evaluation.
- ✓
- It provides a more robust and stable estimate of model performance.
- ✓
- It facilitates comparison between different algorithm configurations.
- ✓
- In this context, two distinct algorithms were implemented:
- ✓
- CatBoost, recognized for its effectiveness in processing categorical data and its ability to reduce overfitting through gradient boosting;
- ✓
- SNN (Shallow Neural Network), an artificial neural network with a reduced architecture, allows nonlinear relationships between variables to be captured without requiring excessive model depth.
4. Experimental Results
4.1. Evaluation Metrics
- Accuracy is a performance metric that indicates how well the system correctly classifies data into the correct categories.
- Precision indicates the proportion of correctly identified attack instances among all predicted attacks. It is defined as:
- Recall is the ability of a classifier to determine true positive results.
- F1 score is the weighted average of precision and recall.
- Matthews correlation coefficient (MCC) is used in machine learning as a measure of classification quality.
- The Mean Squared Error of an estimator measures the average of the squared errors, i.e., the mean square difference between the estimated values and the actual value.
- Confidence interval (CI) is an interval estimate of the value of an unknown parameter (e.g., a proportion, a mean, the accuracy of a classifier). It indicates a range of acceptable values for this parameter, calculated from the observed data.
4.2. Overall Model Performance
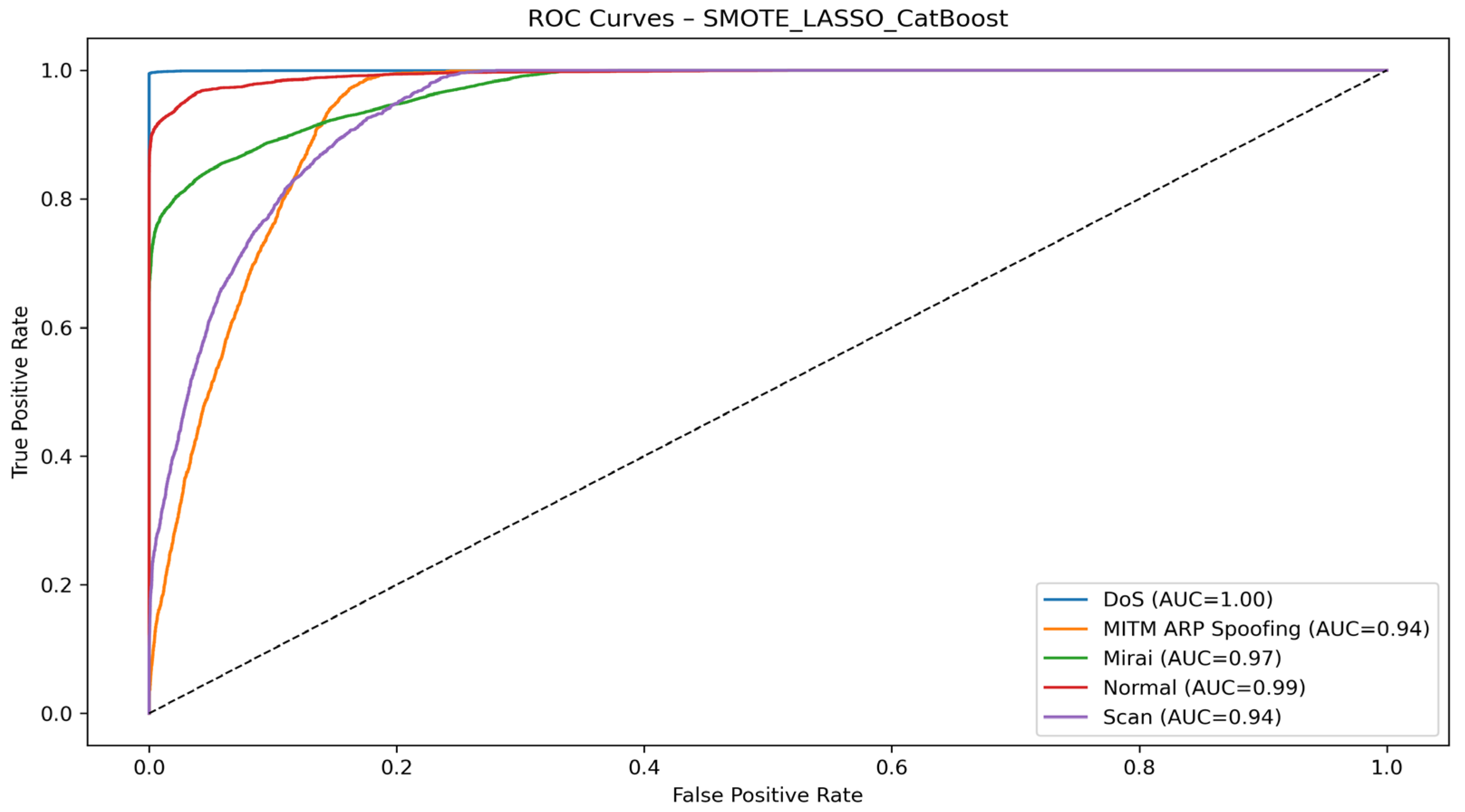
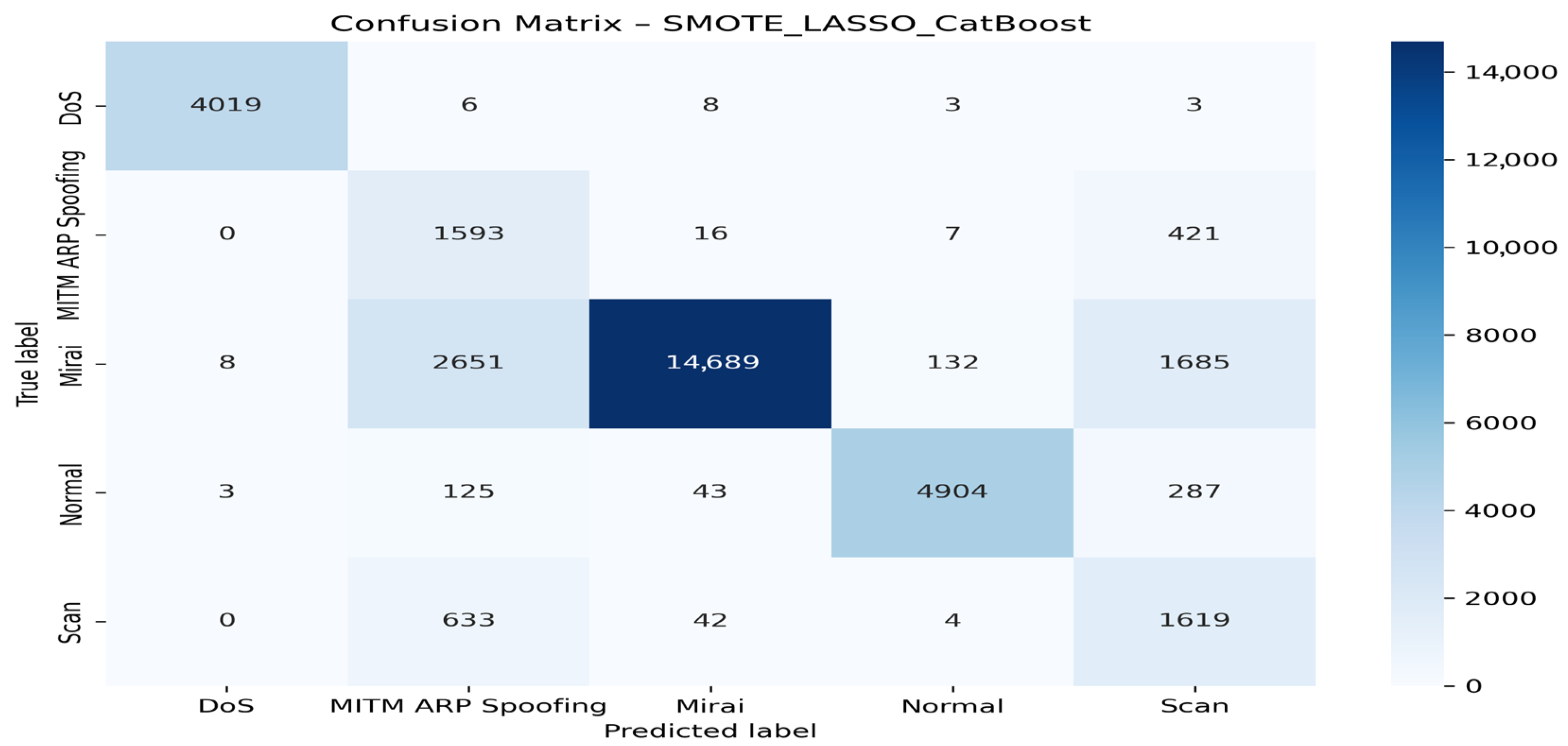
- Case 1: SMOTE + LASSO + CatBoost
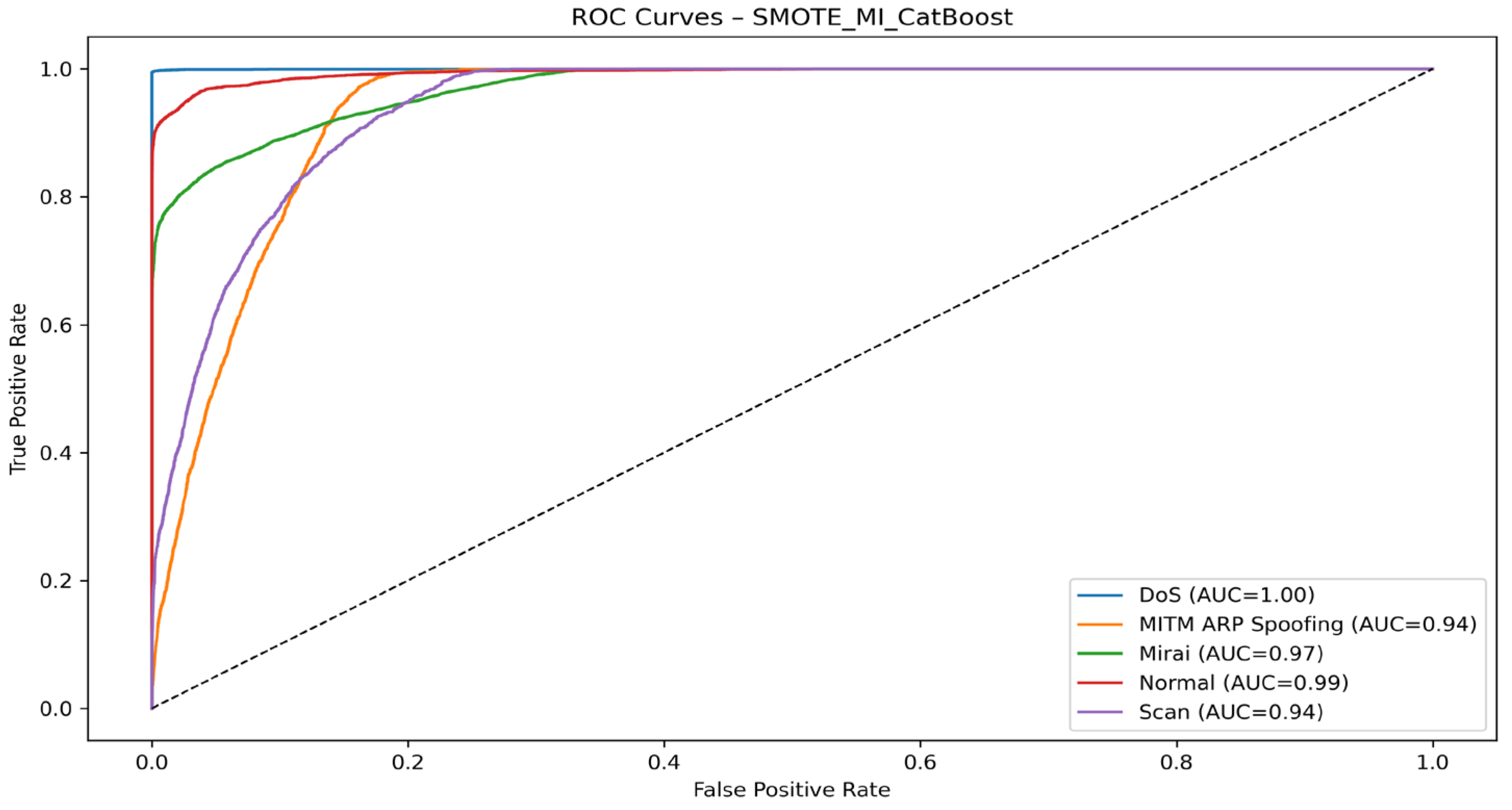
- Case 2: SMOTE + MI + CatBoost
- Case 3: RUS + LASSO + CatBoost
- Case 4: RUS + MI + CatBoost
- Case 5: SMOTE + LASSO + SNN
- Case 6: SMOTE + MI + SNN
- Case 7: RUS + LASSO + SNN
- Case 8: RUS + MI + SNN
4.3. 95% Confidence Intervals for Performance Metrics of CatBoost and SNN Models
- The SMOTE + LASSO and SMOTE + MI configurations achieve the highest accuracy and F1-score intervals, confirming the robustness of performance across all validation folds.
- The precision ranges are particularly high ([90.36–91.12]%), highlighting CatBoost’s ability to limit false positives.
- The difference between RUS and SMOTE is small but significant, indicating a slight advantage for oversampling methods for this dataset.
- The SMOTE + LASSO and SMOTE + MI configurations offer higher intervals for accuracy and F1-score, showing the positive effect of oversampling for simple networks.
- Accuracy is slightly lower than that of CatBoost, indicating greater variability in false positives for SNN.
- The intervals are broader than those of CatBoost, indicating greater variability across validation splits and less stable results.
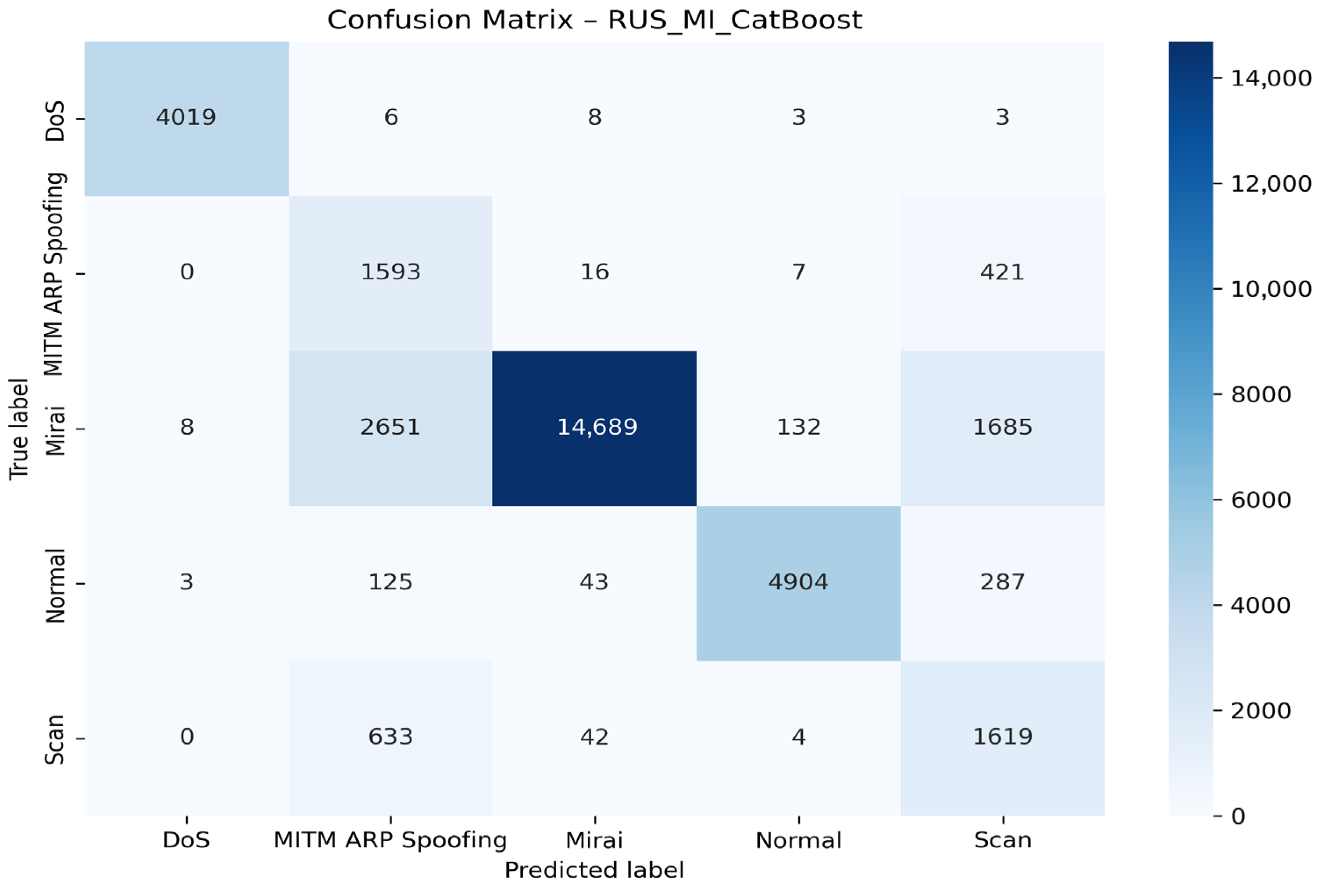
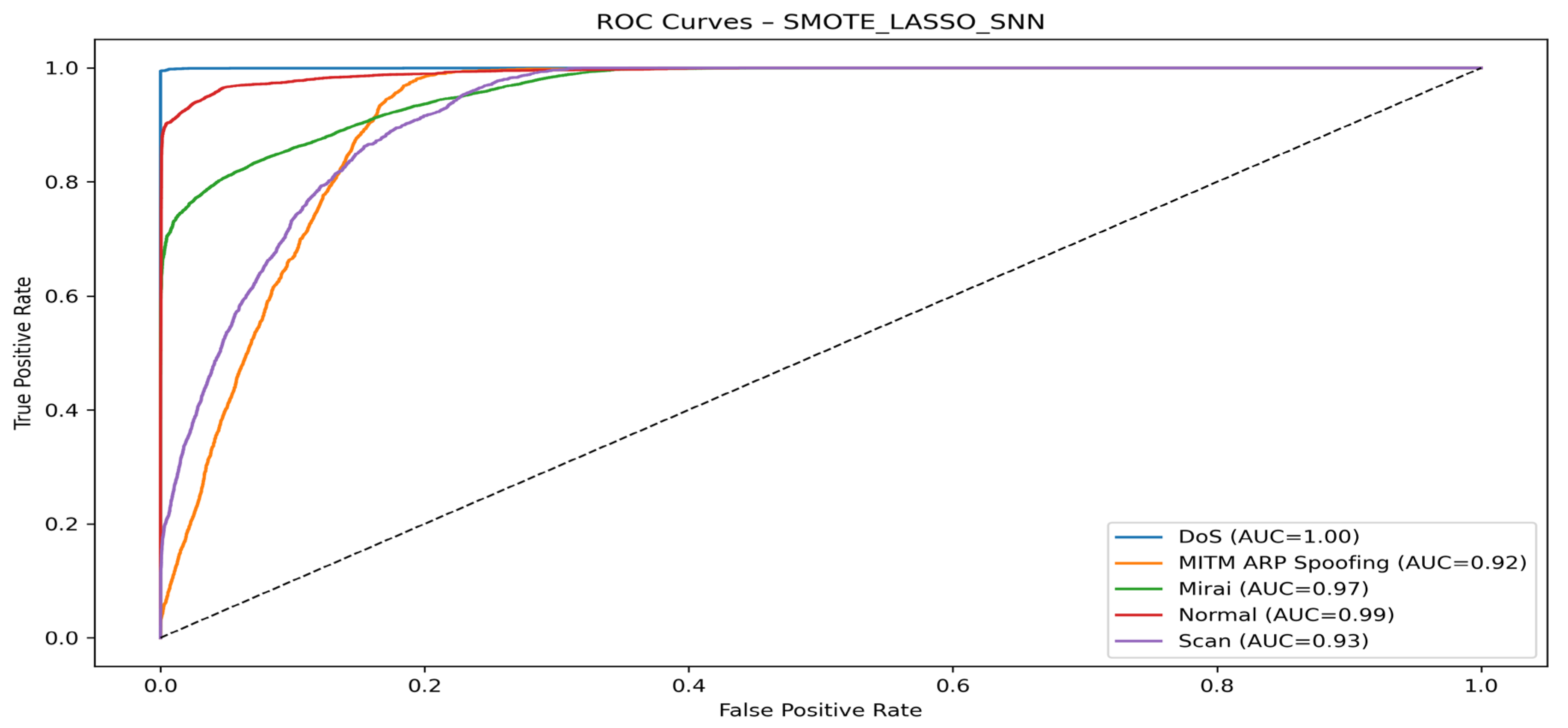
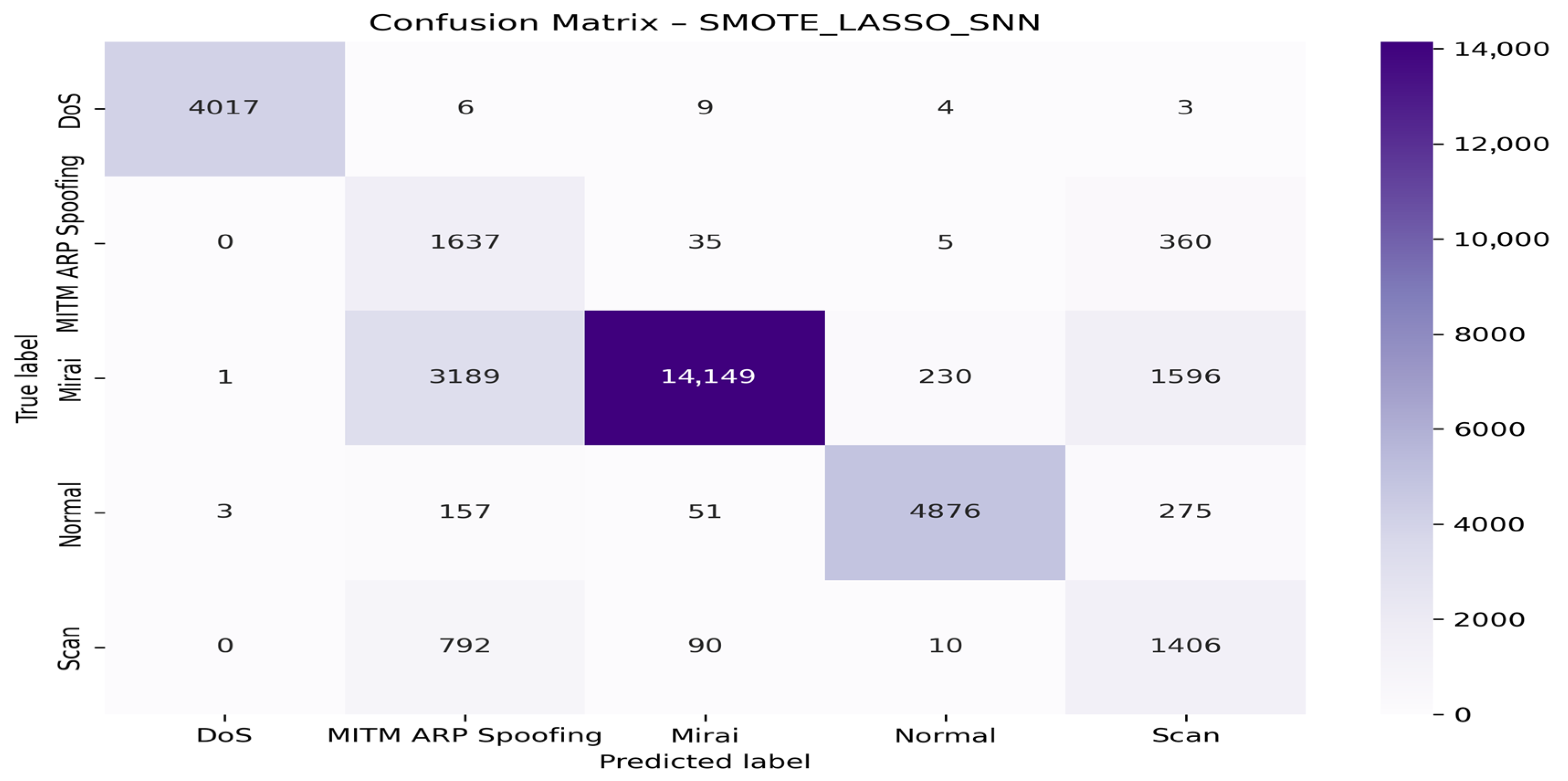
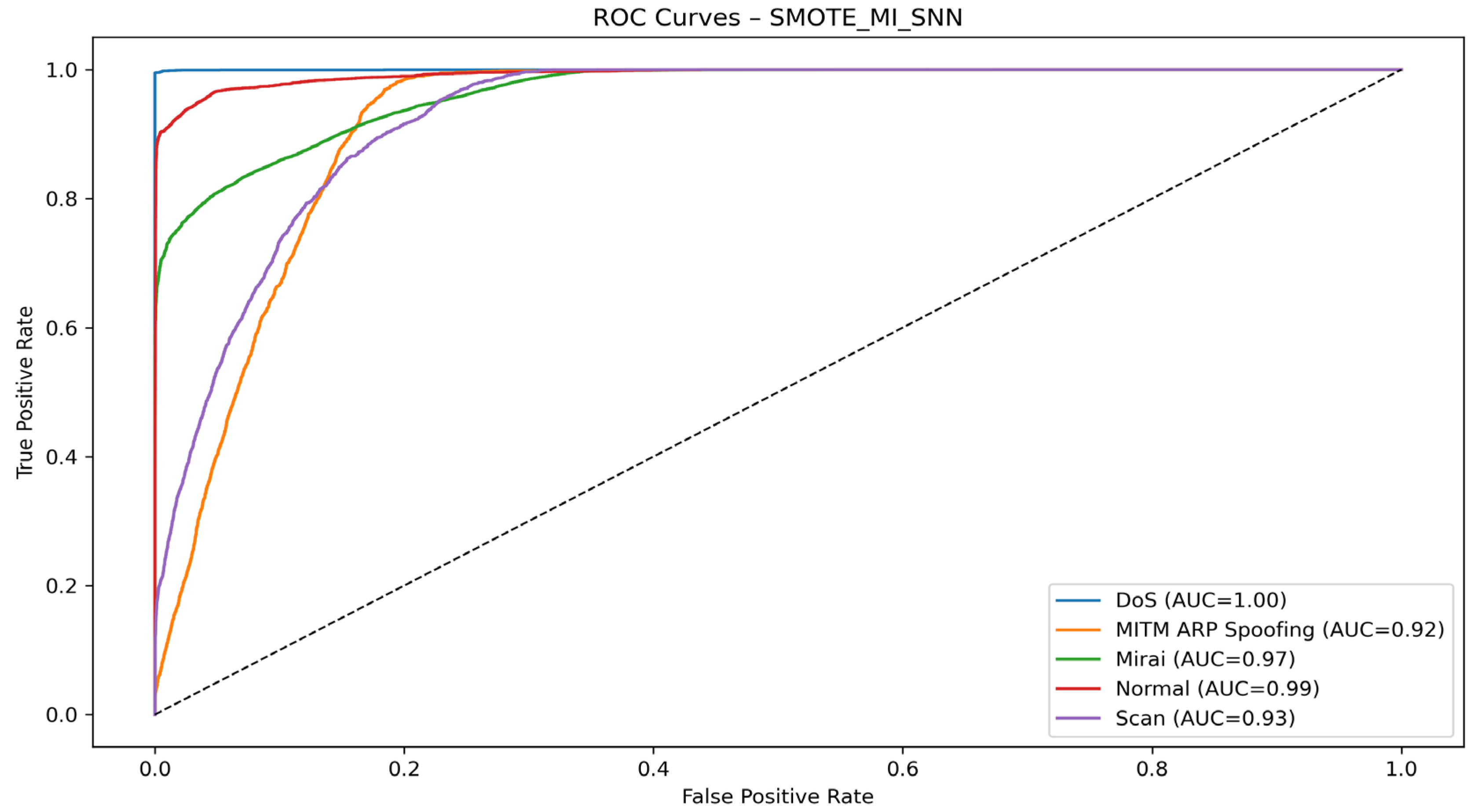
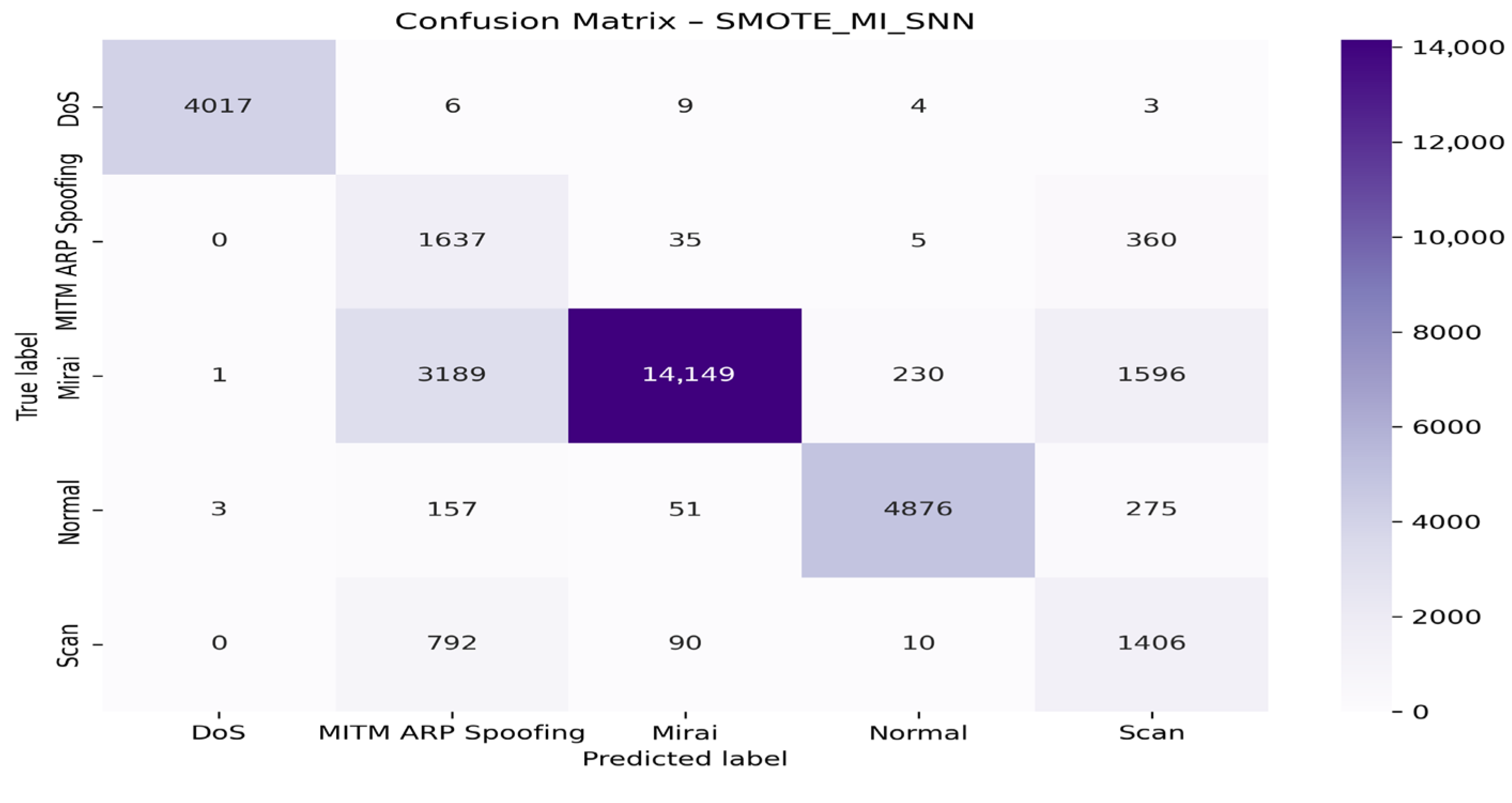
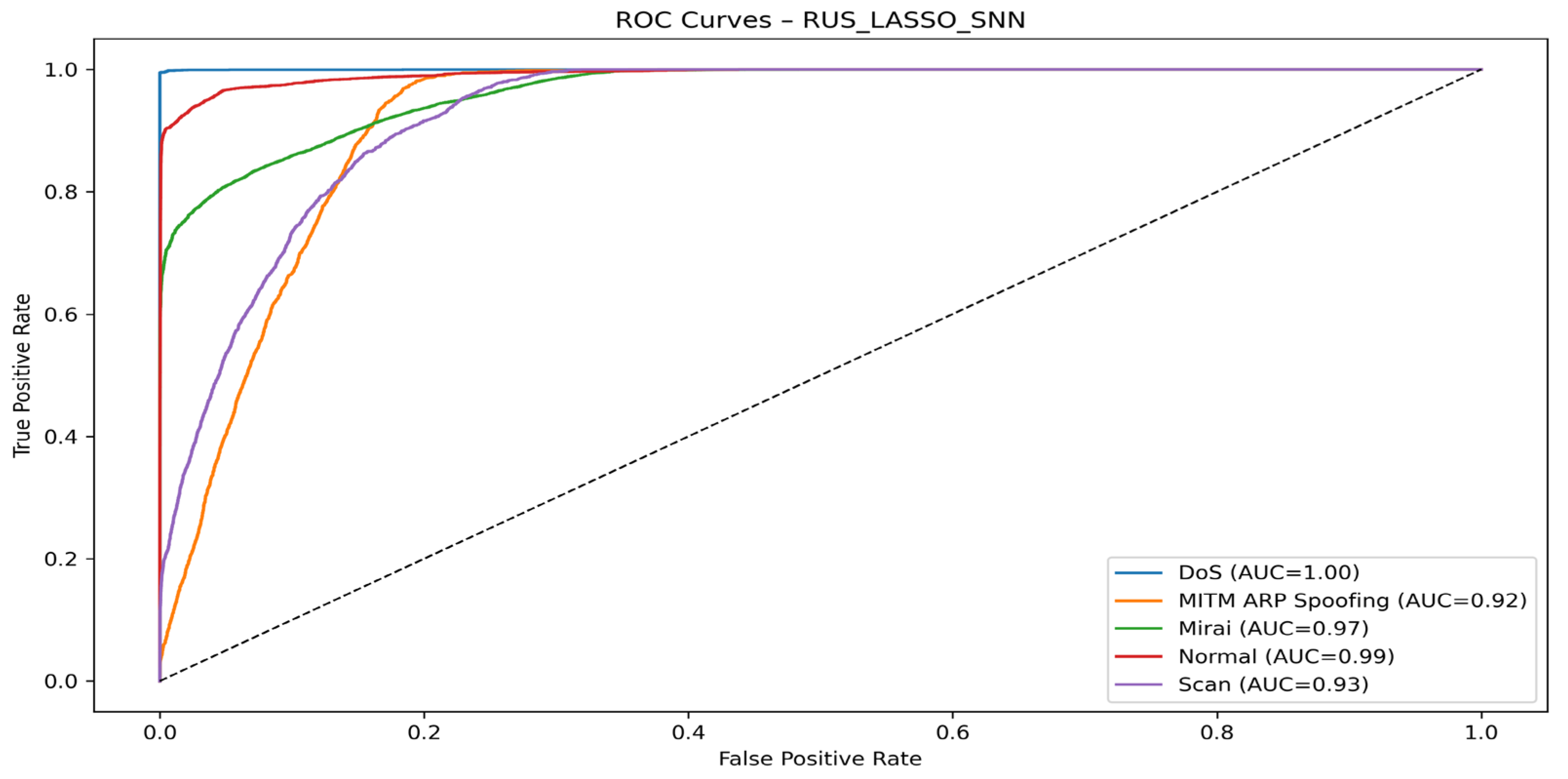
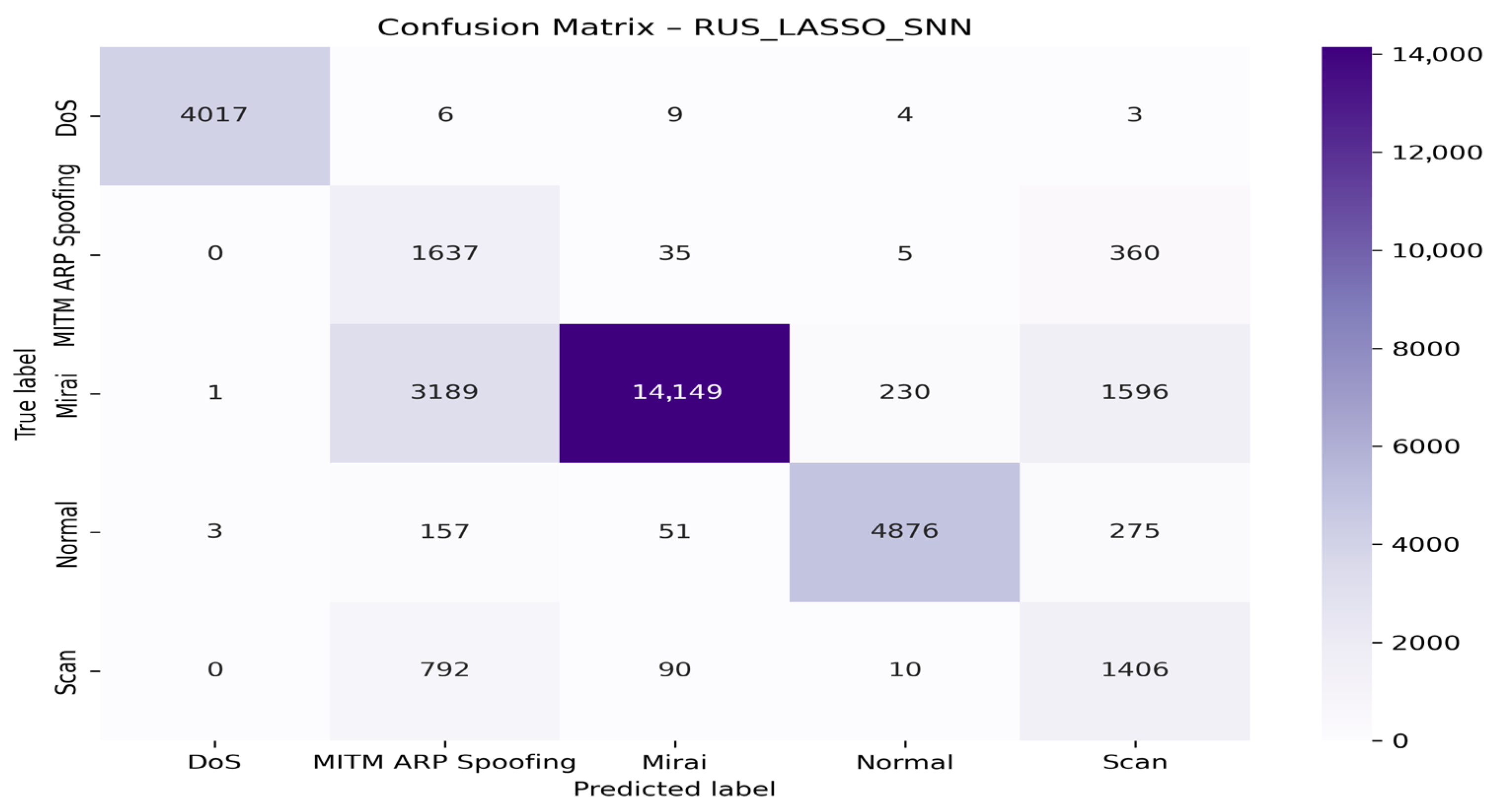
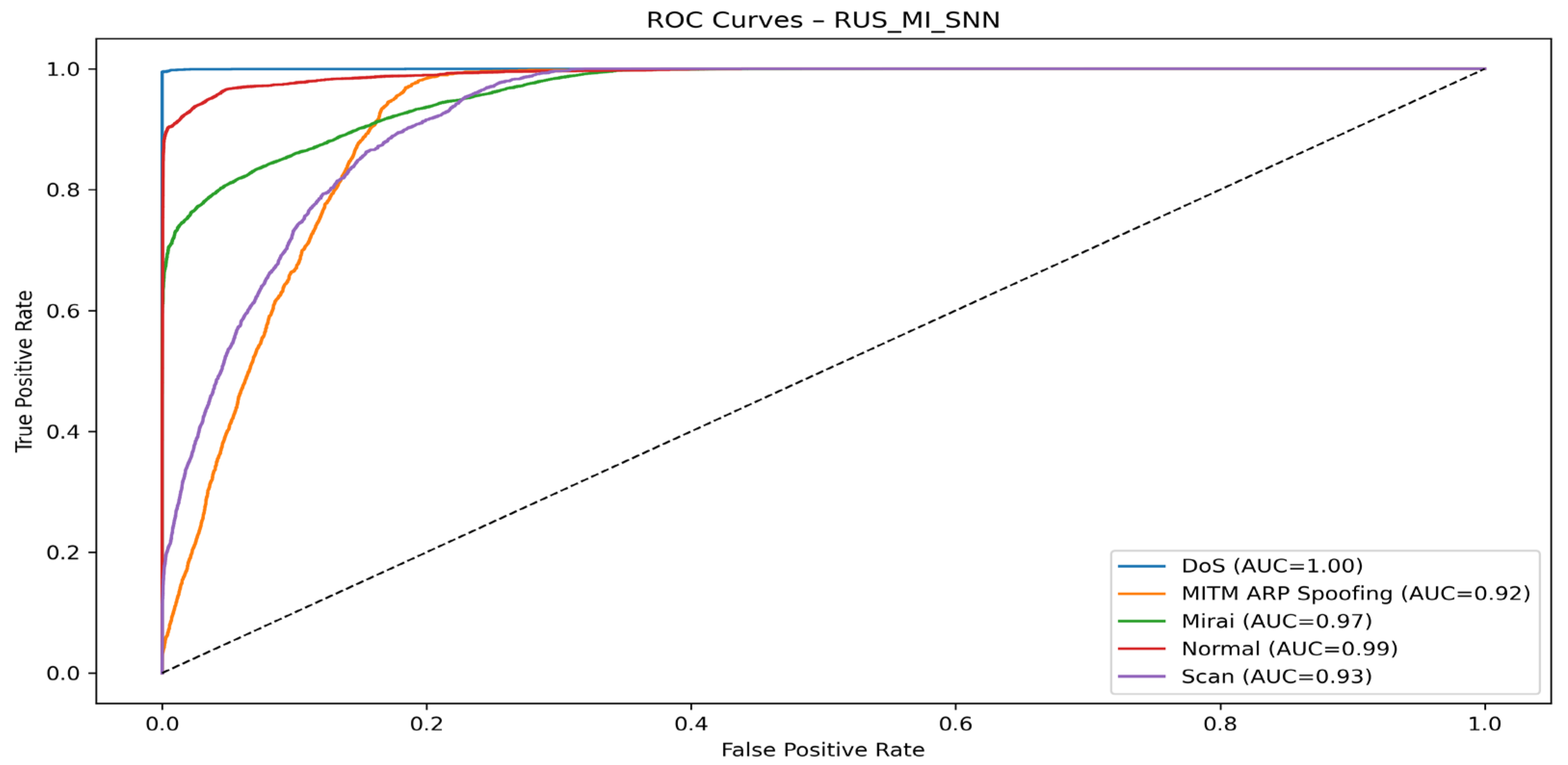
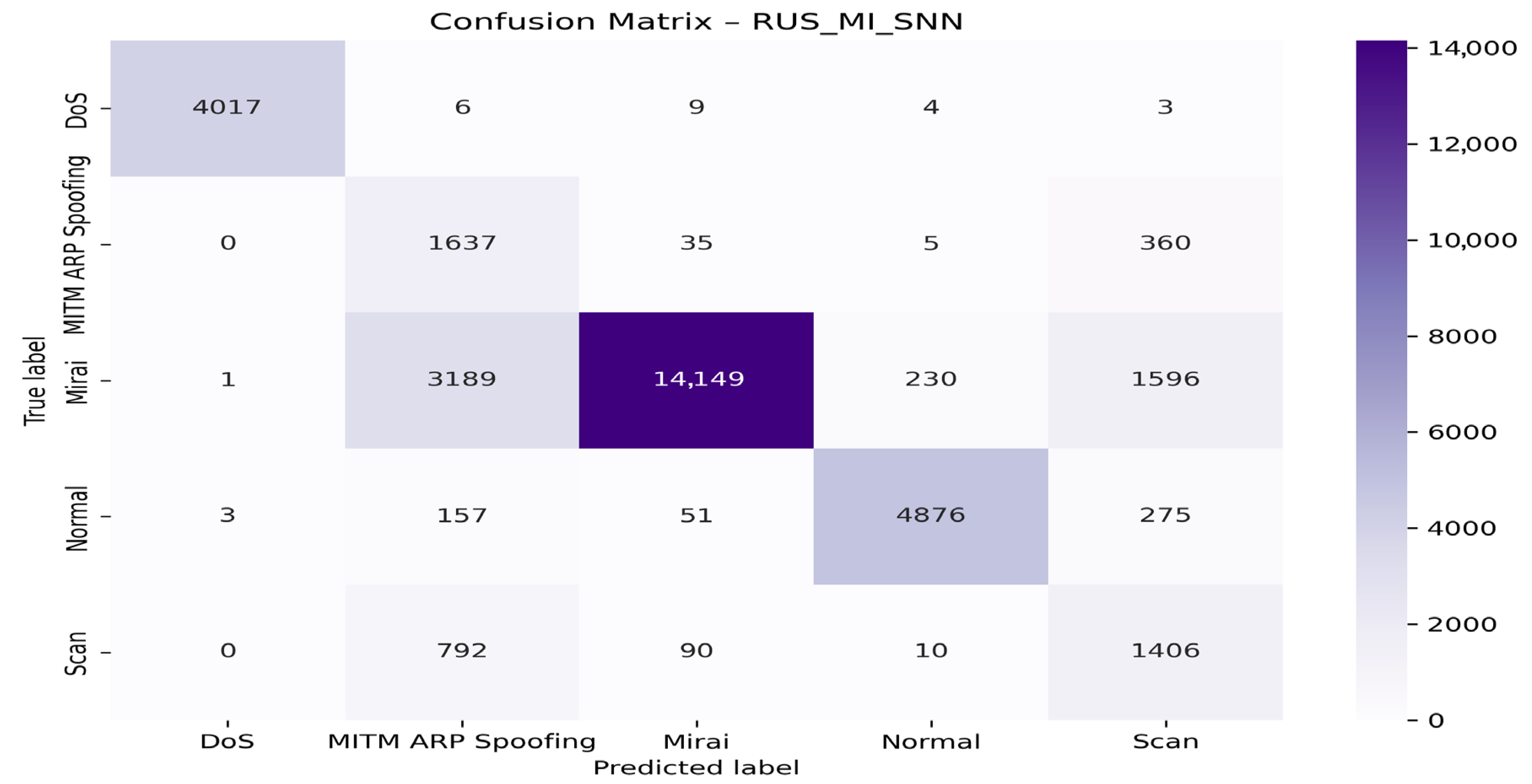
4.4. Visualization of Model Graphs
- With the CatBoost algorithm
- With the SNN algorithm
5. Discussion
6. Comparison with Existing Approaches
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ullah, S.; Ahmad, J.; Khan, M.A.; Alkhammash, E.H.; Hadjouni, M.; Ghadi, Y.Y.; Saeed, F.; Pitropakis, N. A New Intrusion Detection System for the Internet of Things via Deep Convolutional Neural Network and Feature Engineering. Sensors 2022, 22, 3607. [Google Scholar] [CrossRef]
- Awajan, A.A. A Novel Deep Learning-Based Intrusion Detection System for IoT Networks. Computers 2023, 12, 34. [Google Scholar] [CrossRef]
- Prisca, R. Ecosystème IoT. Available online: https://www.objetconnecte.com/les-connexions-iot-mondiales-devraient-depasser-40-milliards-dici-2034/ (accessed on 25 August 2025).
- Lionel, S.V. Number of Internet of Things (IoT) Connections Worldwide from 2022 to 2023, with Forecasts from 2024 to 2034. Statista, 2025. Available online: https://www.statista.com/statistics/1183 (accessed on 25 August 2025).
- Hela, M.; Abir, H.K.; Lamia, C.F. A Comprehensive Survey on Intrusion Detection based Machine Learning for IoT Networks. ICST Trans. Secur. Saf. 2021, 21, e3. [Google Scholar] [CrossRef]
- Rahman, M.M.; Shakil, S.A.; Mustakim, M.R. A survey on intrusion detection system in IoT networks. Cyber Secur. Appl. 2025, 3, 100082. [Google Scholar] [CrossRef]
- Zhukabayeva, T.; Zholshiyeva, L.; Mardenov, Y.; Buja, A.; Khan, S.; Alnazzawi, N. Real-Time Detection and Response to Wormhole and Sinkhole Attacks in Wireless Sensor Networks. Technologies 2025, 13, 348. [Google Scholar] [CrossRef]
- Javed, M.; Tariq, N.; Ashraf, M.; Khan, F.A.; Asim, M.; Imran, M. Securing Smart Healthcare Cyber-Physical Systems against Blackhole and Greyhole Attacks Using a Blockchain-Enabled Gini Index Framework. Sensors 2023, 23, 9372. [Google Scholar] [CrossRef]
- Kikissagbe, B.R.; Adda, M. Machine Learning-Based Intrusion Detection Methods in IoT Systems: A Comprehensive Review. Electronics 2024, 13, 3601. [Google Scholar] [CrossRef]
- Dritsas, E.; Trigka, M. A Survey on Cybersecurity in IoT. Future Internet 2025, 17, 30. [Google Scholar] [CrossRef]
- Gyamfi, E.; Jurcut, A. Intrusion Detection in Internet of Things Systems: A Review on Design Approaches Leveraging Multi-Access Edge Computing, Machine Learning, and Datasets. Sensors 2022, 22, 3744. [Google Scholar] [CrossRef]
- Lubaba, R.; Majed, A.; Abdullah, A.; Shtwai, A.; Binbusayyis, A.; Bukhari, S.A.C. Analysis of dimensionality reduction techniques on Internet of Things data using machine learning. Sustain. Energy Technol. Assess. 2022, 52, 102304. [Google Scholar] [CrossRef]
- Adedeji, K.B.; Abu-Mahfouz, A.M.; Kurien, A.M. DDoS Attack and Detection Methods in Internet-Enabled Networks: Concept, Research Perspectives, and Challenges. J. Sens. Actuator Netw. 2023, 12, 51. [Google Scholar] [CrossRef]
- Mawahib, S.A.B.; Nithinsha, S.; Preethi, R.; Najla, B.; Niyasudeen, F.; Jezna, A.J.P. Enhancing IoT Network Attack Detection with Ensemble Machine Learning and Efficient Feature Extraction. J. Inf. Syst. Eng. 2025, 10, 20. [Google Scholar]
- Hancock, J.T.; Khoshgoftaar, T.M. CatBoost for big data: An interdisciplinary review. J. Big Data 2020, 7, 94. [Google Scholar] [CrossRef] [PubMed]
- Yan, L.; Yu, Z. The Difference of Simple Neural Networks in Testing Penetration Speed. Contemp. Educ. Front. 2025, 3, 275–286. [Google Scholar] [CrossRef]
- Aghware, F.O.; Ogala, J.O. Jamming and anti-jamming solutions for 5G and IoT. Dutse J. Pure Appl. Sci. 2024, 10, 335–342. [Google Scholar] [CrossRef]
- Buiya, M.R.; Laskar, A.N.; Islam, M.R.; Sawalmeh, S.K.S.; Roy, M.S.R.C.; Roy, R.E.R.S.; Sumsuzoha, M. Detecting IoT cyberattacks: Advanced machine learning models for enhanced security in network traffic. J. Comput. Sci. Technol. Stud. 2024, 6, 142–152. [Google Scholar] [CrossRef]
- Jaigirdar, F.T.; Rudolph, C.; Anwar, M.; Tan, B. Empowering End-Users with Cybersecurity Situational Awareness: Findings from IoT-Health Table-Top Exercises. J. Cybersecur. Priv. 2025, 5, 49. [Google Scholar] [CrossRef]
- Thawait, N.K. Machine learning in cybersecurity: Applications, challenges and future directions. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2024, 10, 16–27. [Google Scholar] [CrossRef]
- Alobaid, A.; Talal, B.; Maher, A. Disruptive attacks on artificial neural network: A systematic review of attack techniques, detection methods, and protection srategies. Intell. Syst. Appl. 2025, 26, 200529. [Google Scholar] [CrossRef]
- Alromaihi, N.; Rouached, M.; Akremi, A. Design and Analysis of an Effective Architecture for Machine Learning Based Intrusion Detection Systems. Network 2025, 5, 13. [Google Scholar] [CrossRef]
- Kouassi, B.M.; Monsan, V.; Ballo, A.B.; Kacoutchy, J.A.; Mamadou, D.; Adou, K.J. Application of the learning set for the detection of jamming attacks in 5g mobile networks. Int. J. Adv. Comput. Sci. Appl. 2023, 14, 715–723. [Google Scholar] [CrossRef]
- Neto, E.C.P.; Dadkhah, S.; Ferreira, R.; Zohourian, A.; Lu, R.; Ghorbani, A.A. CICIoT2023: A Real-Time Dataset and Benchmark for Large-Scale Attacks in IoT Environment. Sensors 2023, 23, 5941. [Google Scholar] [CrossRef] [PubMed]
- Pastukh, A.; Tikhvinskiy, V.; Devyatkin, E.; Kulakayeva, A. Sharing Studies between 5G IoT Networks and Fixed Service in the 6425–7125 MHz Band with Monte Carlo Simulation Analysis. Sensors 2022, 22, 1587. [Google Scholar] [CrossRef] [PubMed]
- Al Sawafi, Y.; Touzene, A.; Hedjam, R. Hybrid Deep Learning-Based Intrusion Detection System for RPL IoT Networks. J. Sens. Actuator Netw. 2023, 12, 21. [Google Scholar] [CrossRef]
- Milajerdi, S.M.; Eshete, B.; Gjomemo, R.; Venkatakrishnan, V.N. Propatrol: Attack investigation via extracted high-level tasks. In International Conference on Information Systems Security; Springer International Publishing: Cham, Switzerland, 2018; pp. 107–126. [Google Scholar]
- Ianni, M.; Masciari, E. Scout: Security by computing outliers on activity logs. Comput. Secur. 2023, 132, 103355. [Google Scholar] [CrossRef]
- Jiang, H.; Algatt, S.; Ahammad, P. A recommender system for efficient discovery of new anomalies in large-scale access logs. arXiv 2016, arXiv:1610.08117. [Google Scholar] [CrossRef]
- Tayebi, M.; El Kafhali, S. Performance Analysis of Recurrent Neural Networks for Intrusion Detection Systems in Industrial-Internet of Things. Franklin Open 2025, 12, 100310. [Google Scholar] [CrossRef]
- Musthafa, M.B.; Huda, S.; Kodera, Y.; Ali, M.A.; Araki, S.; Mwaura, J.; Nogami, Y. Optimizing IoT Intrusion Detection Using Balanced Class Distribution, Feature Selection, and Ensemble Machine Learning Techniques. Sensors 2024, 24, 4293. [Google Scholar] [CrossRef]
- Benmalek, M.; Seddiki, A. Particle swarm optimization-enhanced machine learning and deep learning techniques for Internet of Things intrusion detection. Data Sci. Manag. 2025; in press. [Google Scholar] [CrossRef]
- Samir, F.; Fouzi, S. Smart Intrusion Detection in IoT Edge Computing Using Federated Learning. Rev. D’intelligence Artif. 2023, 37, 1133–1145. Available online: http://iieta.org/journals/ria (accessed on 22 August 2025).
- Nur, A.A.; Muhammad, S.M.P.; Aniza, M.D.; Adam, J. An Investigation of SMOTE Based Methods for Imbalanced Datasets with Data Complexity Analysis. Available online: https://www.ieee.org/publications/rights/index.html (accessed on 22 August 2025).
- Haseeb, A.; Mohd, N.M.S.; Kashif, H.; Arshad, A.; Ayaz, U.; Arshad, M.; Rashid, N.; Muzammil, K. A review on data preprocessing methods for class imbalance problem. Int. J. Eng. Technol. 2019, 8, 390–397. Available online: https://www.sciencepubco.com/index.php/ijet/article/view/29508 (accessed on 22 August 2025).
- Ernesto, C.; David, D.G.; Danae, C. Neural lasso: A unifying approach of lasso and neural networks. Int. J. Data Sci. Anal. 2025, 20, 1485–1495. [Google Scholar] [CrossRef]
- Gilberto, C.; Gabriel, M.F.F.; Thomas, M.L. Mutual Information as a General Measure of Structure in Interaction Networks. Entropy 2020, 22, 528. [Google Scholar] [CrossRef]
- Raneem, Q.; Al-Zoubi, A.M.; Faris, H.; Almomani, I. A Multi-Layer Classification Approach for Intrusion Detection in IoT Networks Based on Deep Learning. Sensors 2021, 21, 2987. [Google Scholar] [CrossRef]
- Wongvorachan, T.; He, S.; Bulut, O. A Comparison of Undersampling, Oversampling, and SMOTE Methods for Dealing with Imbalanced Classification in Educational Data Mining. Information 2023, 14, 54. [Google Scholar] [CrossRef]
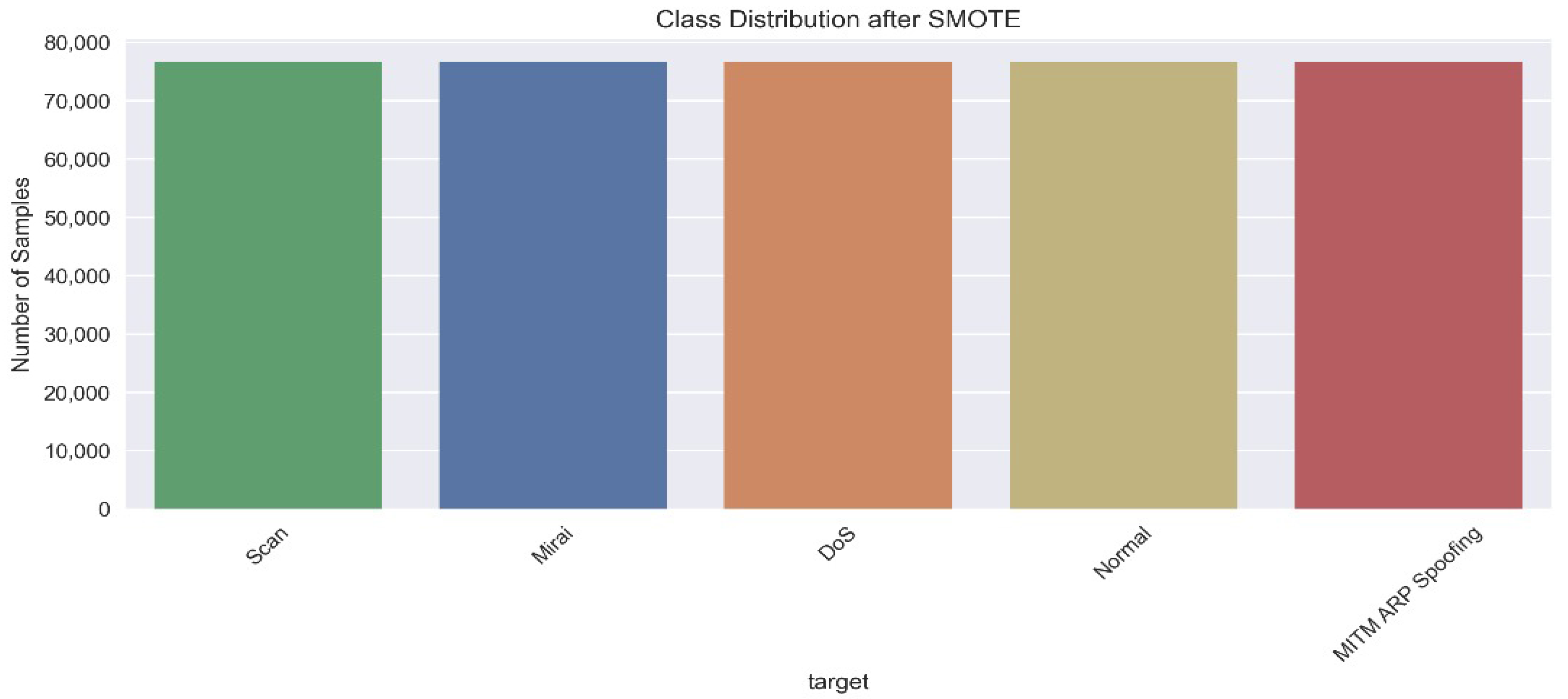
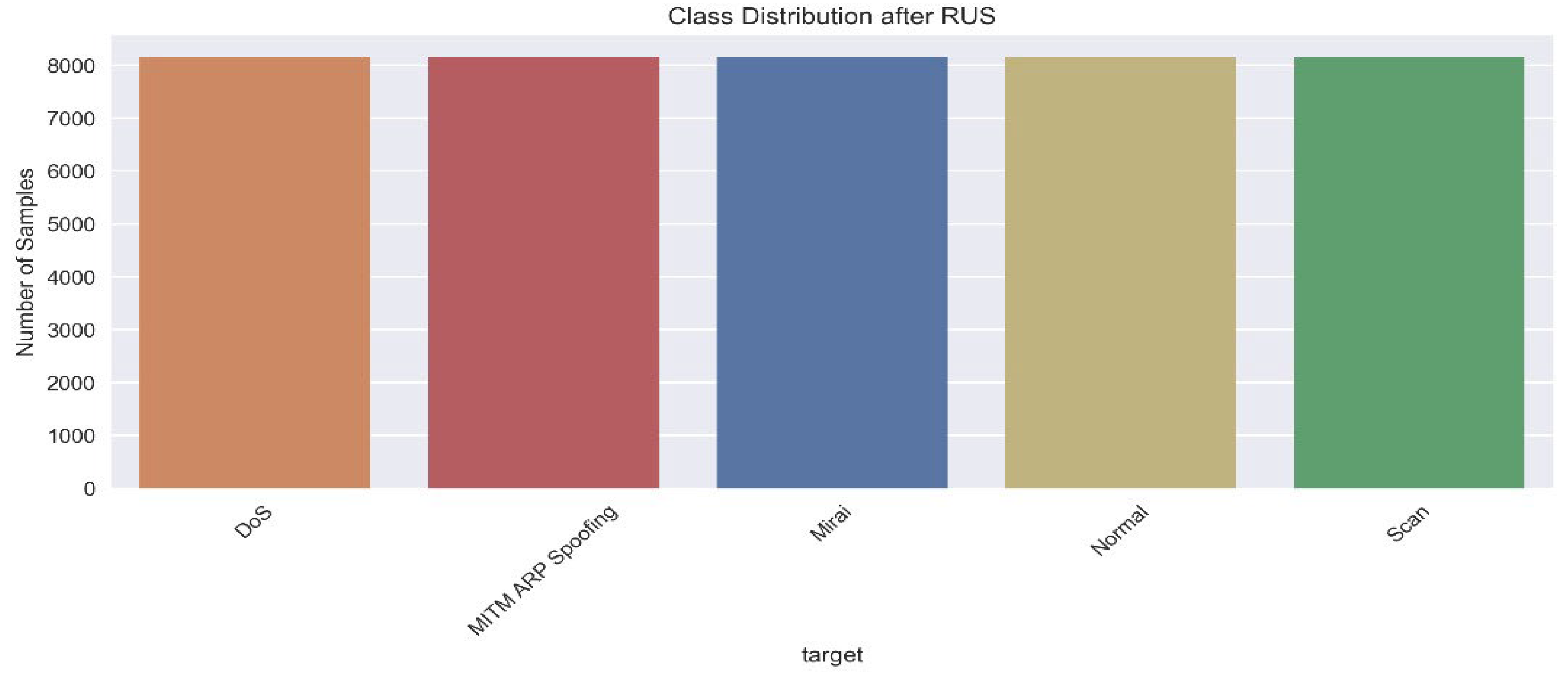
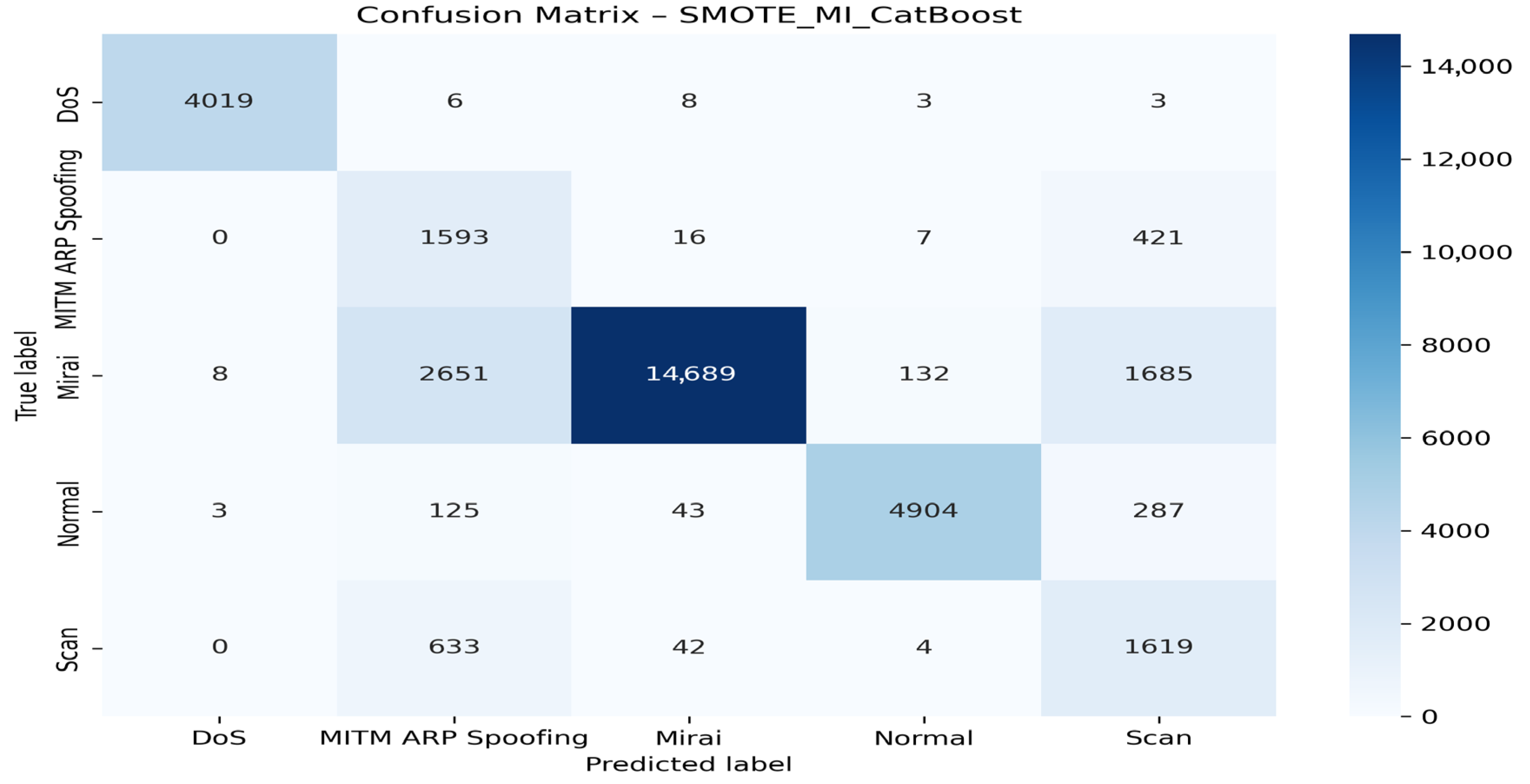
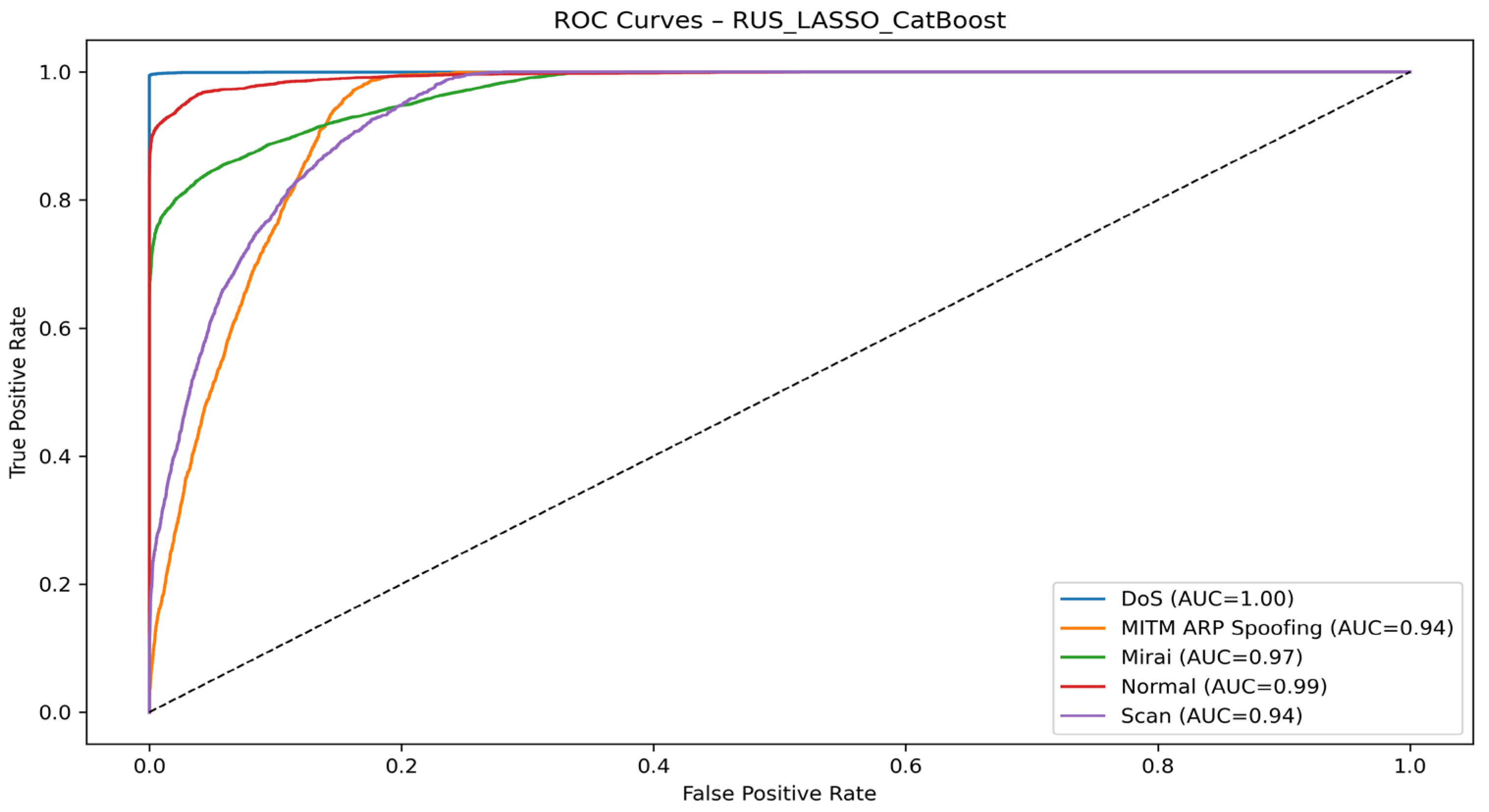
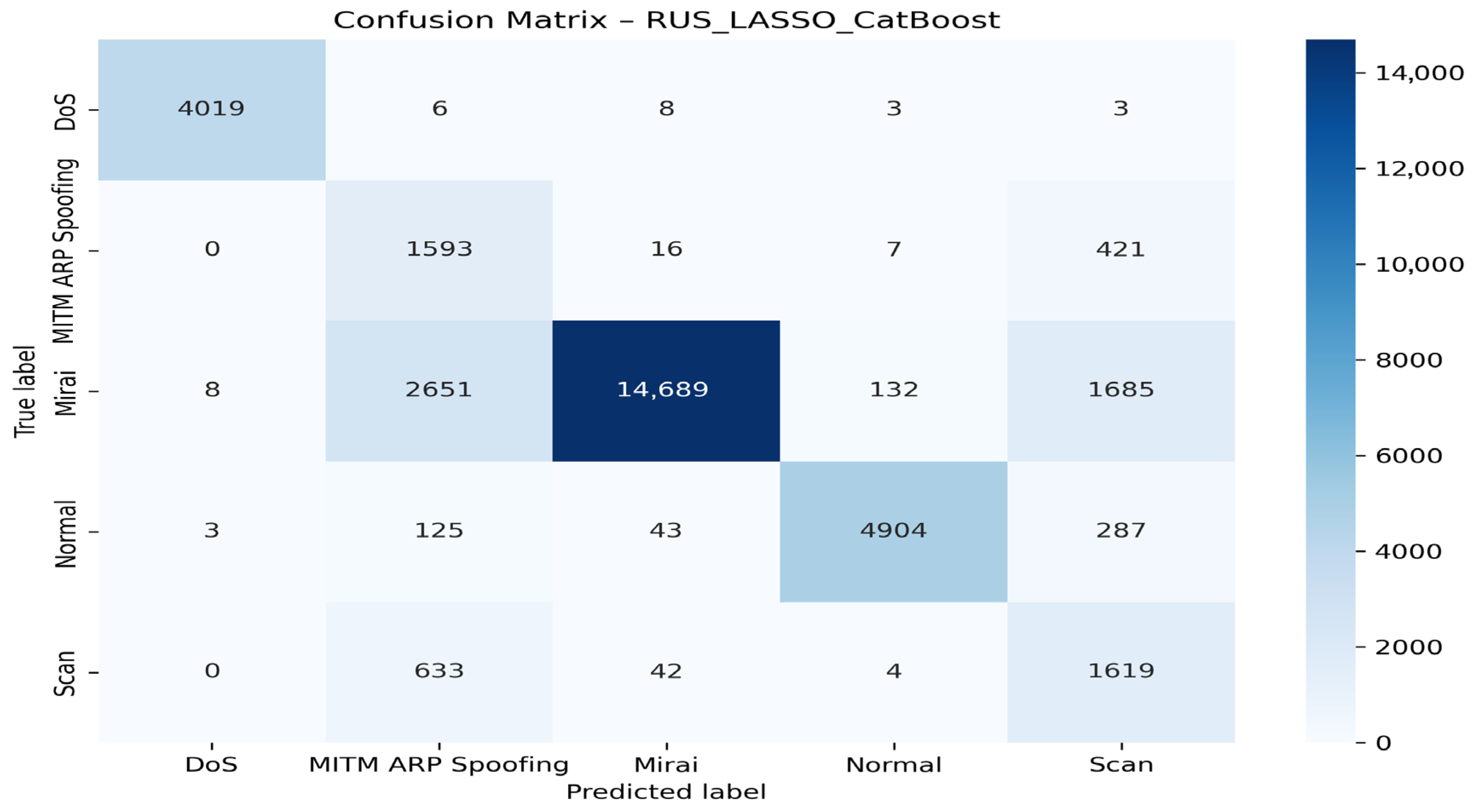
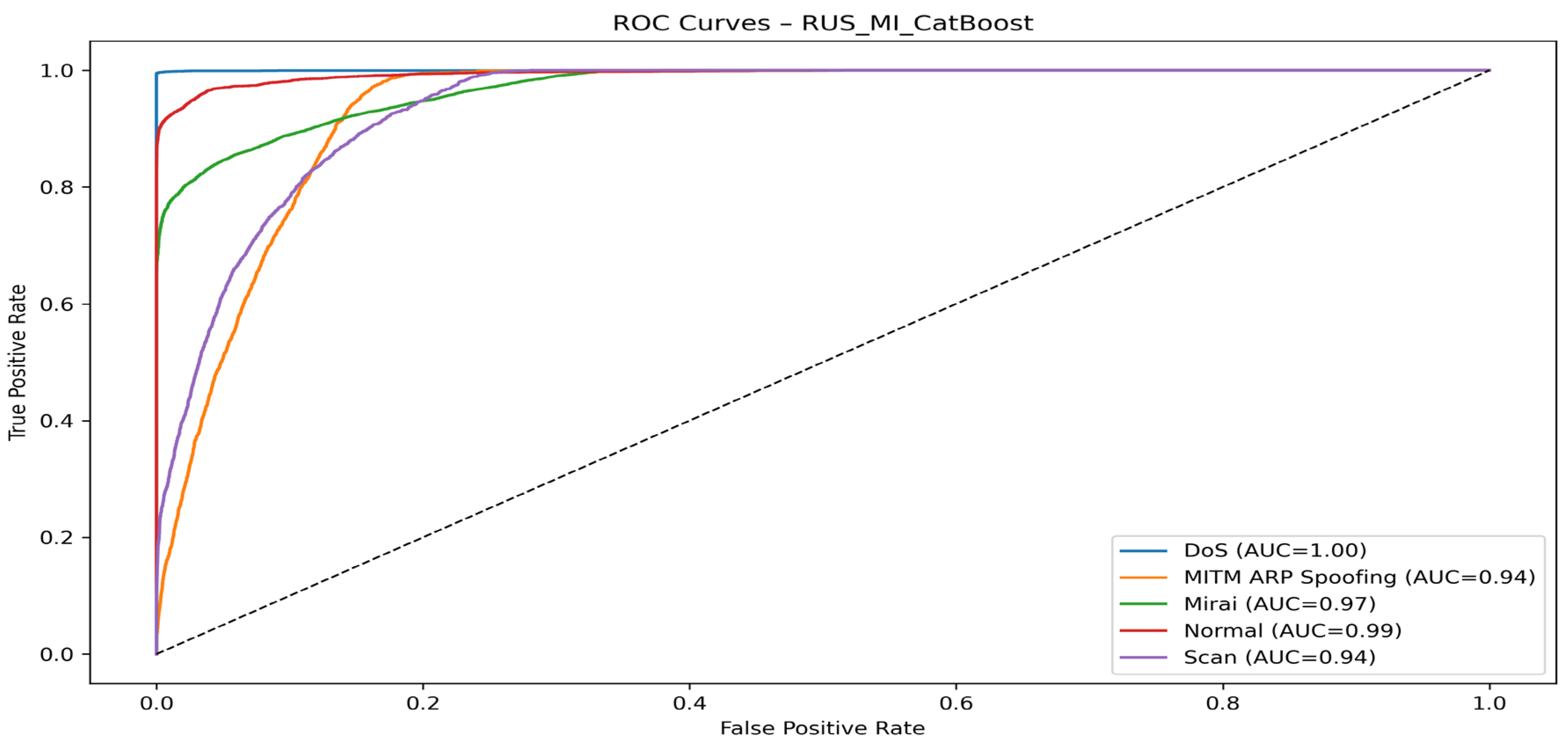
| Authors | Models Used | Dataset(s) | Main Metrics | Limitations |
|---|---|---|---|---|
| Buiya et al. [18] | Logistic Regression, Random Forest | IoT dataset (benign & malicious traffic) | RF > higher accuracy, better attack detection | Underrepresentation of some attacks → incomplete detection |
| Jaigirdar et al. [19] | Security-metadata–centered approach | Simulated IoT healthcare use cases | Improved awareness and risk management | Results based on simulations → low validity in real-world conditions |
| Thawait [20] | Theoretical analysis + anomaly inference algorithm | No solid experimental validation | Discussion on adversarial attacks, data poisoning, privacy, etc. | Too theoretical, limited experimentation, and few real datasets |
| Alobaid et al. [21] | Comparative study on ANN (DNN, CNN, GNN, SNN) | Review 2019–2024 | In-depth analysis of attacks and defense strategies | No direct experimentation, more oriented toward research directions |
| Alromaihi et al. [22] | XGBoost, Stacking, other ML models | CIC-MalMem-2022, CIC-IDS-2018, CIC-IDS-2017 | XGBoost → accuracy ~99.7–99.9%, very fast detection | Limited to known threats → poor adaptability to novel attacks |
| Kouassi B. et al. [23] | Hybrid ML model for jamming detection | Simulated 5G data | Accuracy: 99.46–99.72% for jamming detection | Only addresses jamming attacks; other 5G threats are not covered |
| Neto et al. [24] | Creation of a comprehensive dataset (33 attacks) | New IoT dataset (105 devices) | Wide IoT attack coverage, valuable research resource | Focused on dataset construction, no direct model testing |
| Pastukh et al. [25] | Simulation-based analysis (5G spectrum sharing) | 6425–7125 MHz band | Recommendations on protection distances and frequency offsets | Purely theoretical and regulatory → no practical attack detection |
| Al Sawafi et al. [26] | Hybrid IDS (supervised + semi-supervised DL) | IoTR-DS (based on RPL) | Accuracy: 98% (known), 95% (unknown); F1: 92%/87% | No analysis of computational costs or scalability for constrained IoT env. |
| Milajerdi et al. [27] | ProPatrol: leveraging natural compartmentalization of sensitive applications to group audit events | Kernel audit logs | Reduces dependency explosion, enables faster root-cause identification, system overhead < 2% | Limited generalization, scalability issues, and weak integration into heterogeneous IoT environments |
| Ianni & Masciari [28] | Compact encoding based on prime numbers + hierarchical outlier detection | Activity logs | Efficient detection of malicious behaviors | Complex to manage with large-scale activities, dependent on detection thresholds, and limited validation |
| Jiang et al. [29] | Helios: non-standard recommendation system using categorical combinations and rank statistics | Large-scale access logs | Rapid detection of unknown/novel anomalies, explanatory visualizations for experts | Performance dependent on label quality, high cost for very large datasets, limited robustness testing |
| Tayebi et al. [30] | RNN, LSTM, GRU, BiLSTM, BiGRU, DNN (+ attention) | IoT dataset | Enriched DNN → best overall performance, F1 > 0.94 | DNN models too heavy, not optimized for constrained IoT deployment |
| Musthafa et al. [31] | SVM + bagging, LSTM + stacking (ANOVA feature) | UNSW-NB15, NSL-KD | Accuracy: 96.92% and 99.77%; very low overfitting (0.33%, 0.04%) | Limited to two older benchmark datasets |
| Benmalek et al. [32] | rank statistics SVM, KNN, CatBoost, NB, CNN, LSTM + PSO | RT_IoT2022 | PSO → better feature selection, significant performance improvement | Requires scalability testing and validation in real IoT environments |
| Models | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) | AUC (%) | MCC (%) | MSE (%) |
|---|---|---|---|---|---|---|---|
| SMOTE + LASSO + CatBoost | 82.43 | 90.76 | 82.43 | 85.08 | 97.20 | 76.00 | 30.82 |
| SMOTE + MI + CatBoost | 82.43 | 90.72 | 82.43 | 85.06 | 97.00 | 76.22 | 29.57 |
| RUS + LASSO + CatBoost | 81.39 | 90.66 | 81.39 | 84.24 | 96.80 | 76.67 | 29.23 |
| RUS + MI + CatBoost | 81.57 | 90.69 | 81.57 | 84.38 | 96.80 | 76.76 | 29.02 |
| Models | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) | AUC (%) | MCC (%) | MSE (%) |
|---|---|---|---|---|---|---|---|
| SMOTE + LASSO + SNN | 80.87 | 89.84 | 80.87 | 83.67 | 96.6 | 78.40 | 27.71 |
| SMOTE + MI + SNN | 80.55 | 90.31 | 80.55 | 83.58 | 97.0 | 77.40 | 28.41 |
| RUS + LASSO + SNN | 78.61 | 90.12 | 78.61 | 81.96 | 96.0 | 77.60 | 28.54 |
| RUS + MI + SNN | 79.20 | 89.57 | 79.20 | 82.40 | 96.0 | 77.30 | 28.32 |
| Models | Classes | Precision (%) | Recall (%) | F1-Score (%) | AUC (%) |
|---|---|---|---|---|---|
| SMOTE + LASSO + CatBoost | DoS | 99.85 | 99.55 | 99.70 | 100.0 |
| MITM ARP Spoofing | 32.20 | 77.71 | 45.53 | 94.00 | |
| Mirai | 98.78 | 78.34 | 87.38 | 97.00 | |
| Normal | 98.17 | 91.50 | 94.72 | 99.00 | |
| Scan | 42.47 | 70.53 | 53.74 | 95.00 | |
| RUS + LASSO + CatBoost | DoS | 99.78 | 99.50 | 99.64 | 100.00 |
| MITM ARP Spoofing | 31.68 | 78.20 | 45.10 | 94.00 | |
| Mirai | 99.31 | 74.43 | 86.38 | 97.00 | |
| Normal | 96.91 | 97.31 | 94.03 | 99.00 | |
| Scan | 40.13 | 70.63 | 51.18 | 94.00 | |
| SMOTE + MI + CatBoost | DoS | 99.83 | 99.55 | 99.69 | 100.00 |
| MITM ARP Spoofing | 32.25 | 77.61 | 45.56 | 94.20 | |
| Mirai | 98.73 | 78.30 | 87.34 | 97.20 | |
| Normal | 98.06 | 91.51 | 94.67 | 99.70 | |
| Scan | 43.63 | 70.89 | 53.60 | 95.00 | |
| RUS + MI + CatBoost | DoS | 99.80 | 99.50 | 99.65 | 100.00 |
| MITM ARP Spoofing | 32.98 | 78.20 | 45.39 | 94.00 | |
| Mirai | 99.30 | 76.70 | 86.55 | 97.00 | |
| Normal | 97.00 | 91.40 | 94.11 | 99.00 | |
| Scan | 40.29 | 70.76 | 51.34 | 94.00 |
| Models | Classes | Precision (%) | Recall (%) | F1-Score (%) | AUC (%) |
|---|---|---|---|---|---|
| SMOTE + LASSO + SNN | DoS | 99.95 | 99.31 | 99.63 | 100.00 |
| MITM ARP Spoofing | 31.29 | 74.03 | 44.00 | 94.00 | |
| Mirai | 98.45 | 76.06 | 85.83 | 97.00 | |
| Normal | 95.51 | 91.74 | 93.57 | 99.00 | |
| Scan | 38.70 | 69.36 | 50.67 | 95.00 | |
| RUS + LASSO + SNN | DoS | 99.90 | 99.50 | 99.68 | 100.00 |
| MITM ARP Spoofing | 27.35 | 77.76 | 40.47 | 94.00 | |
| Mirai | 98.44 | 72.83 | 83.72 | 97.00 | |
| Normal | 95.33 | 90.53 | 90.52 | 99.00 | |
| Scan | 38.02 | 63.19 | 47.47 | 94.00 | |
| SMOTE + MI + SNN | DoS | 99.90 | 99.48 | 99.69 | 100.00 |
| MITM ARP Spoofing | 29.70 | 81.25 | 43.50 | 93.00 | |
| Mirai | 98.77 | 75.66 | 85.56 | 97.00 | |
| Normal | 97.16 | 91.29 | 94.13 | 99.00 | |
| Scan | 40.61 | 64.06 | 75.40 | 94.00 | |
| RUS + MI + SNN | DoS | 99.99 | 99.48 | 99.71 | 100.00 |
| MITM ARP Spoofing | 28.23 | 80.41 | 41.79 | 92.00 | |
| Mirai | 98.56 | 73.82 | 84.41 | 96.00 | |
| Normal | 94.81 | 90.92 | 92.82 | 99.00 | |
| Scan | 46.90 | 60.00 | 46.91 | 93.00 |
| Models | IC 95% Accuracy | IC 95% F1-Score | IC 95% Precision | IC 95% Recall |
|---|---|---|---|---|
| SMOTE + LASSO + CatBoost | [82.10, 82.76] | [84.80, 85.36] | [90.40, 91.12] | [82.10, 82.76] |
| SMOTE + MI + CatBoost | [82.10, 82.76] | [84.78, 85.34] | [90.36, 91.08] | [82.10, 82.76] |
| RUS + LASSO + CatBoost | [81.10, 81.68] | [83.90, 84.58] | [90.20, 91.12] | [81.10, 81.68] |
| RUS + MI + CatBoost | [81.28, 81.86] | [84.06, 84.70] | [90.28, 91.10] | [81.28, 81.86] |
| Models | IC 95% Accuracy | IC 95% F1-Score | IC 95% Precision | IC 95% Recall |
|---|---|---|---|---|
| SMOTE + LASSO + SNN | [80.80, 81.34] | [83.10, 84.24] | [88.80, 89.90] | [80.80, 81.34] |
| SMOTE + MI + SNN | [80.38, 80.72] | [83.00, 83.70] | [89.70, 90.30] | [80.38, 80.72] |
| RUS + LASSO + SNN | [78.30, 78.92] | [81.30, 82.50] | [89.80, 90.20] | [78.30, 78.92] |
| RUS + MI + SNN | [78.65, 79.75] | [81.80, 83.00] | [89.30, 90.00] | [78.65, 79.75] |
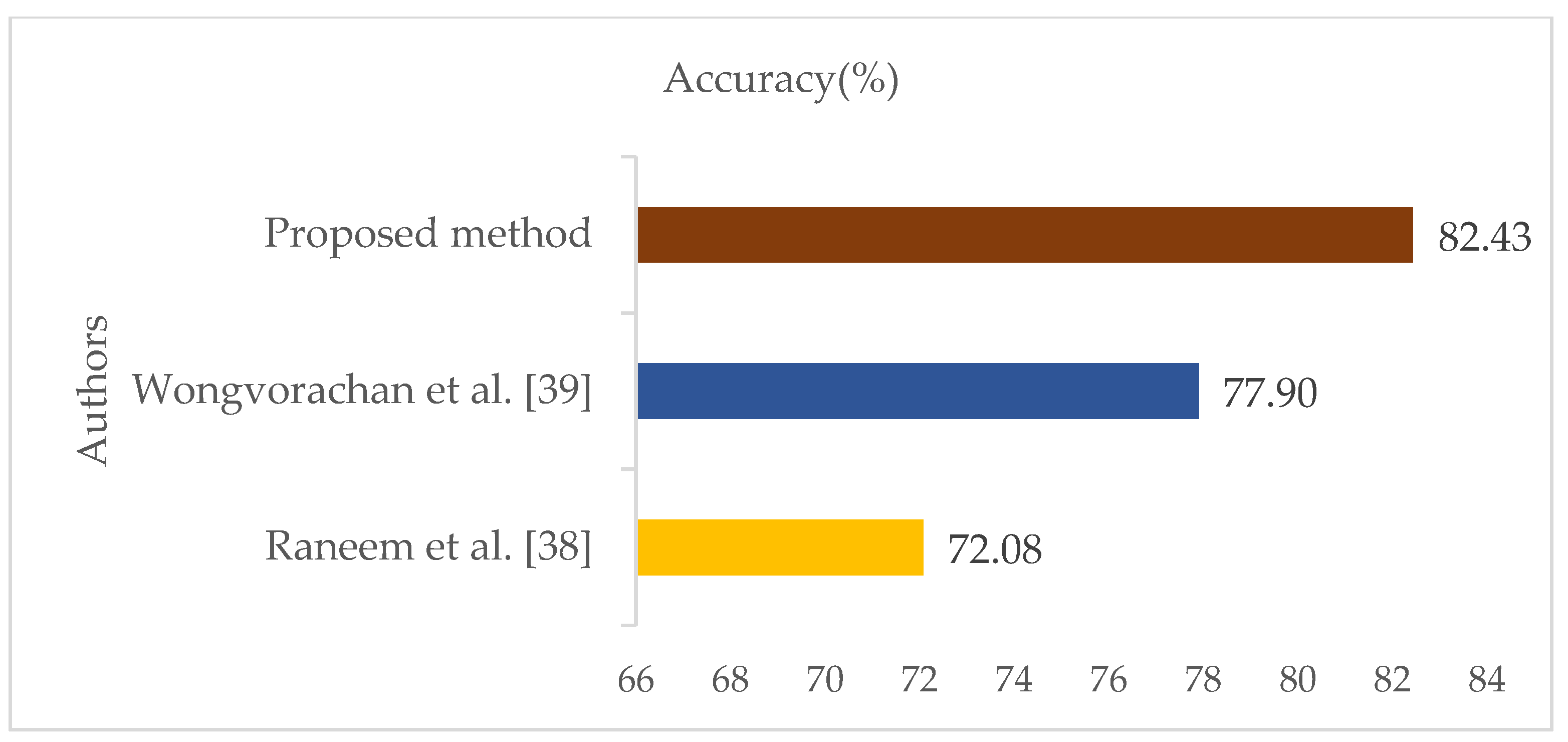
| Authors | Years | Methods | Pre-processing | Datasets | Accuracy (%) |
|---|---|---|---|---|---|
| Raneem et al. [38] | 2021 | SMOTE + SLFN + LSTM (SSL) | Oversampling by label Undersampling | IoTID20 | 72.08 |
| Wongvorachan et al. [39] | 2023 | SMOTE + NC + RUS (SNR) | imbalance learning | IoTID20 | 77.90 |
| Proposed method | 2025 | SMOTE + LASSO + CatBoost (SLC) | balancing techniques | IoTID20 | 82.43 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kouassi, B.M.; Ballo, A.B.; Ayikpa, K.J.; Mamadou, D.; Diabagate, Y. Optimized Intrusion Detection in the IoT Through Statistical Selection and Classification with CatBoost and SNN. Technologies 2025, 13, 441. https://doi.org/10.3390/technologies13100441
Kouassi BM, Ballo AB, Ayikpa KJ, Mamadou D, Diabagate Y. Optimized Intrusion Detection in the IoT Through Statistical Selection and Classification with CatBoost and SNN. Technologies. 2025; 13(10):441. https://doi.org/10.3390/technologies13100441
Chicago/Turabian StyleKouassi, Brou Médard, Abou Bakary Ballo, Kacoutchy Jean Ayikpa, Diarra Mamadou, and Youssouf Diabagate. 2025. "Optimized Intrusion Detection in the IoT Through Statistical Selection and Classification with CatBoost and SNN" Technologies 13, no. 10: 441. https://doi.org/10.3390/technologies13100441
APA StyleKouassi, B. M., Ballo, A. B., Ayikpa, K. J., Mamadou, D., & Diabagate, Y. (2025). Optimized Intrusion Detection in the IoT Through Statistical Selection and Classification with CatBoost and SNN. Technologies, 13(10), 441. https://doi.org/10.3390/technologies13100441