Advanced Security Framework for Internet of Things (IoT)
Abstract
:1. Introduction
1.1. Data Security in IoT
1.2. Data Integrity in the IoT
1.3. Data Confidentiality in the IoT
1.4. Data Validity in the IoT
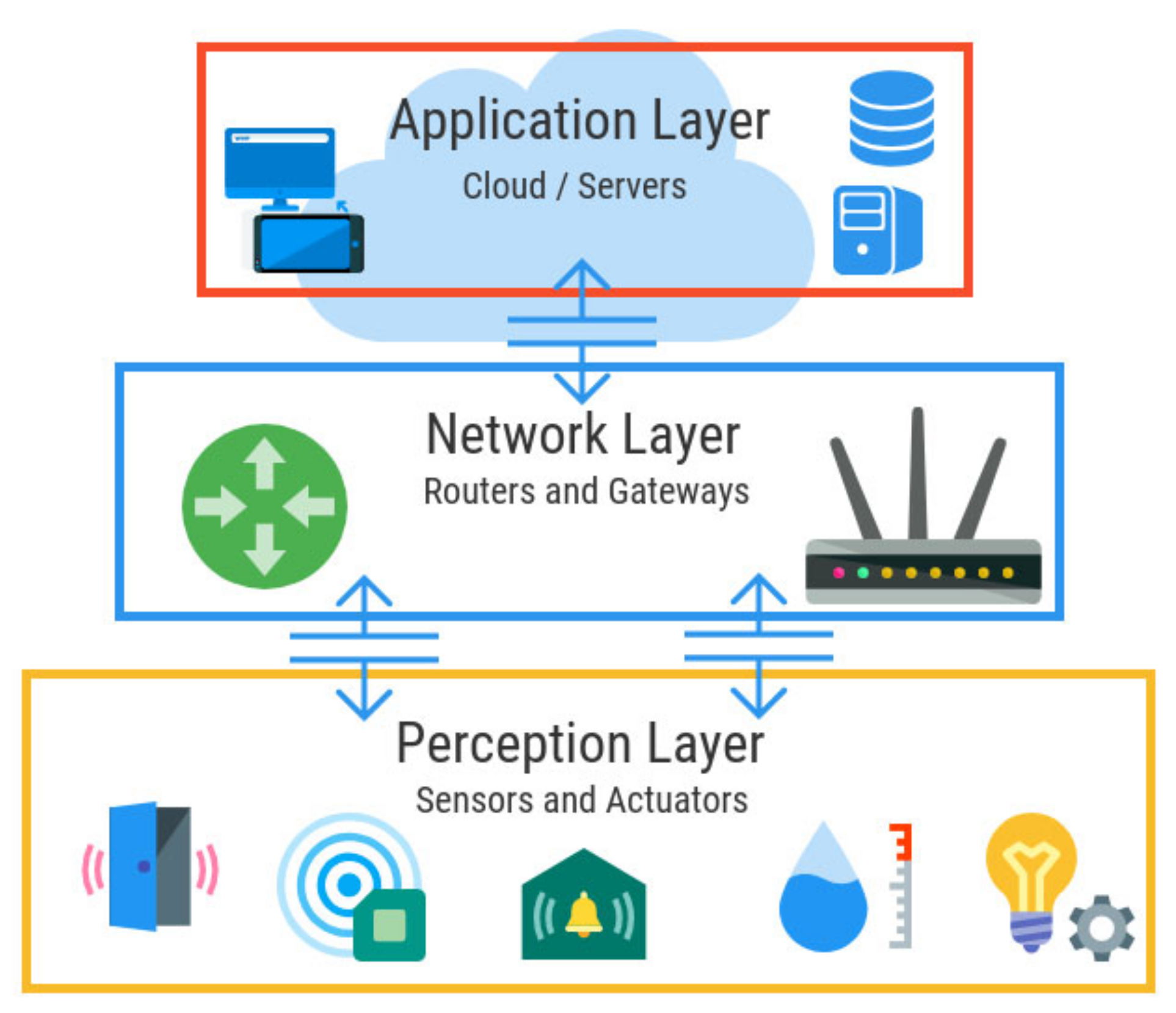
1.5. Current IoT Security Framework
- It consists of sensors, actuators, and other embedded systems [15].
- Fog set of connections: A class of exchange ideas, technologies, and protocols by several IoT policies with the prerequisite to expand and enforce an entire confidence policy [16].
- Core Complex: It provides a set of connection center platforms and IoT devices. The issues at this time are individuals confronted with conventional fundamental networks [17]. The measureless number of endpoints act together and get by to create a considerable precautions burden. Thus, based on the suggestions made in previous research papers, the current study proposes a security framework for the IoT in terms of data confidentiality, availability, and integrity.
1.6. Motivation of This Study
1.7. Contribution of This Study
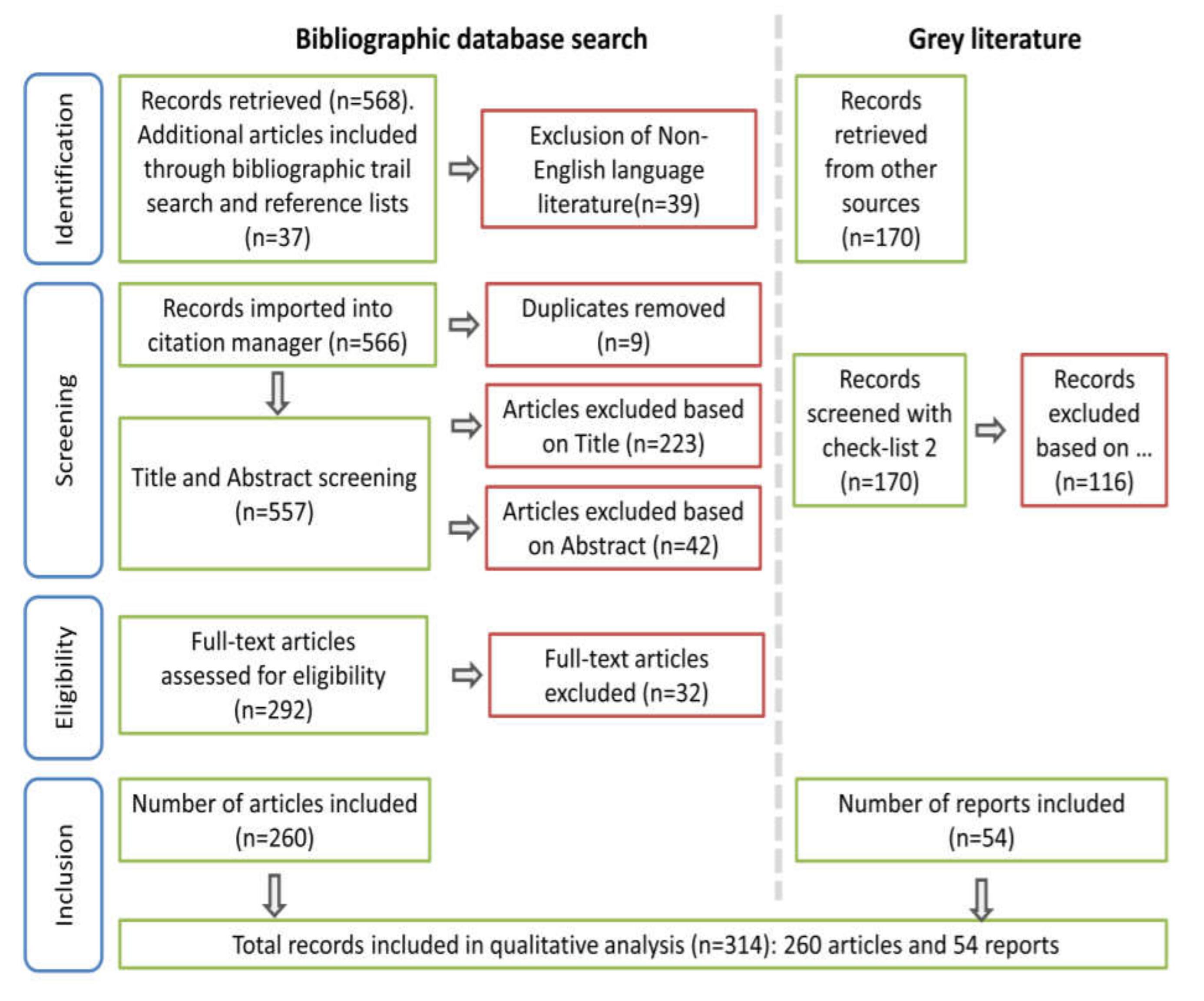
2. Literature Review and the Selection Criteria
2.1. Selection of Relevant Studies
2.2. Evaluation
2.3. Analysis and Synthesis
3. Reporting and Discussion of the Results
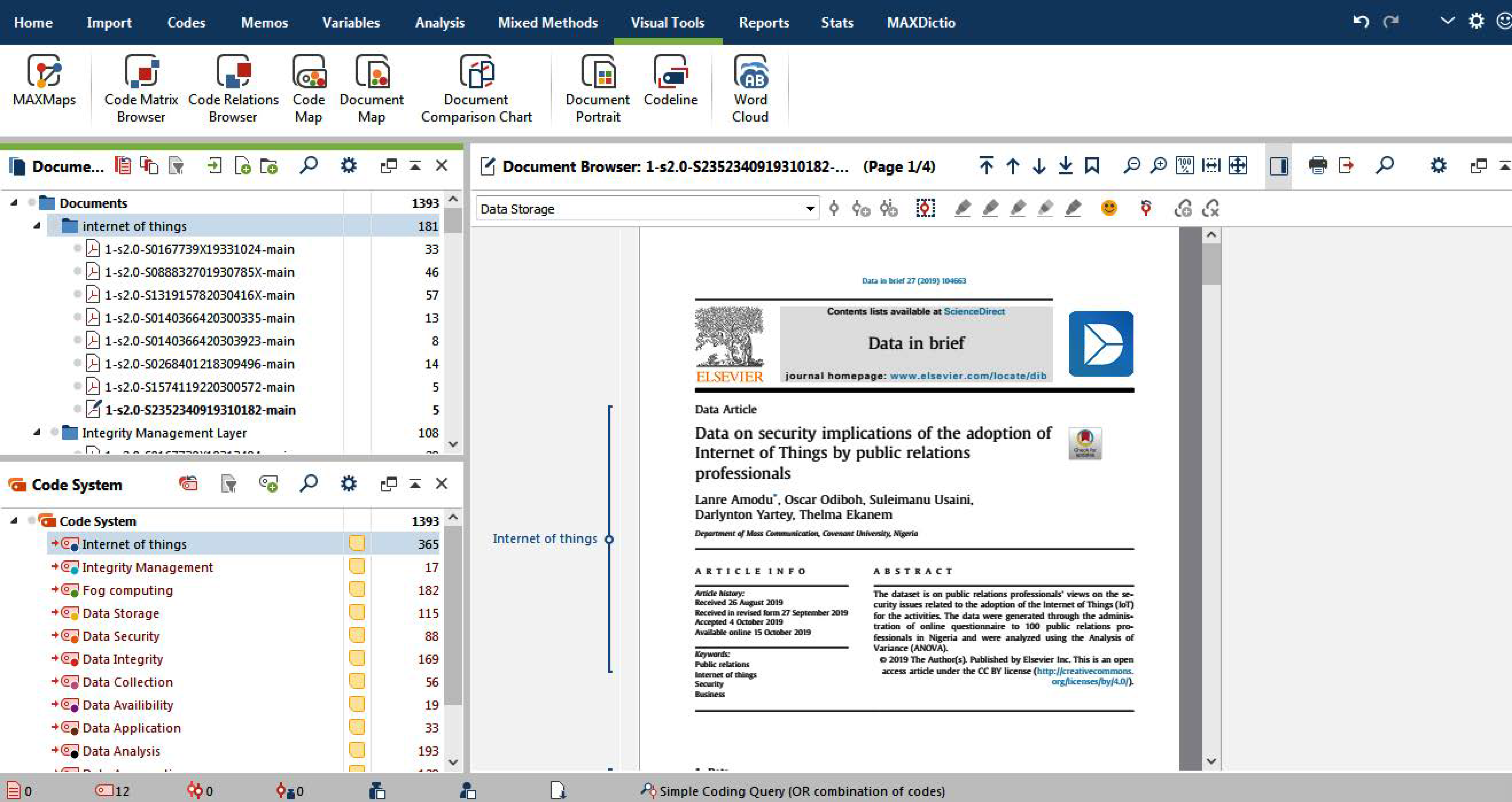
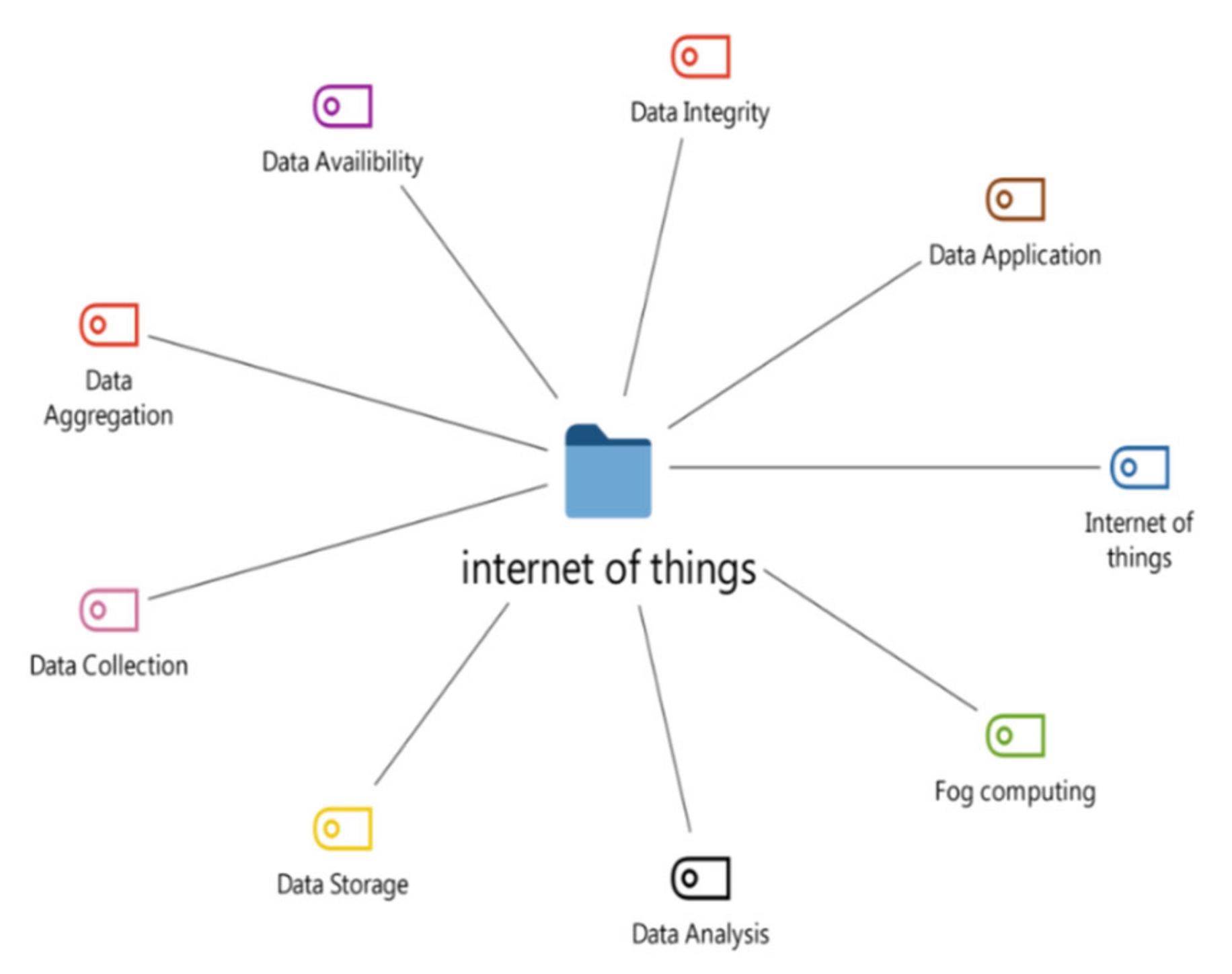
3.1. Auto Codes Results from SLR
3.2. The Codes Cloud
3.3. Word Frequencies
3.3.1. Data Confidentiality
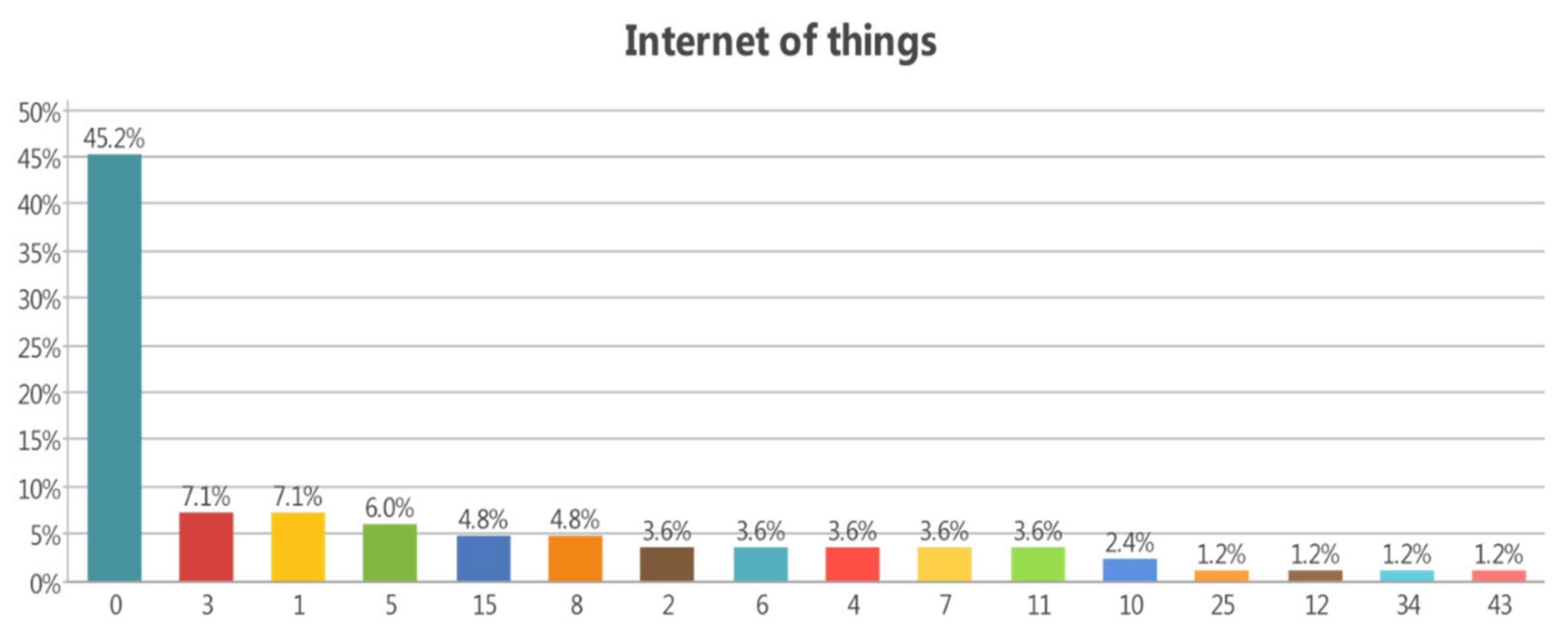
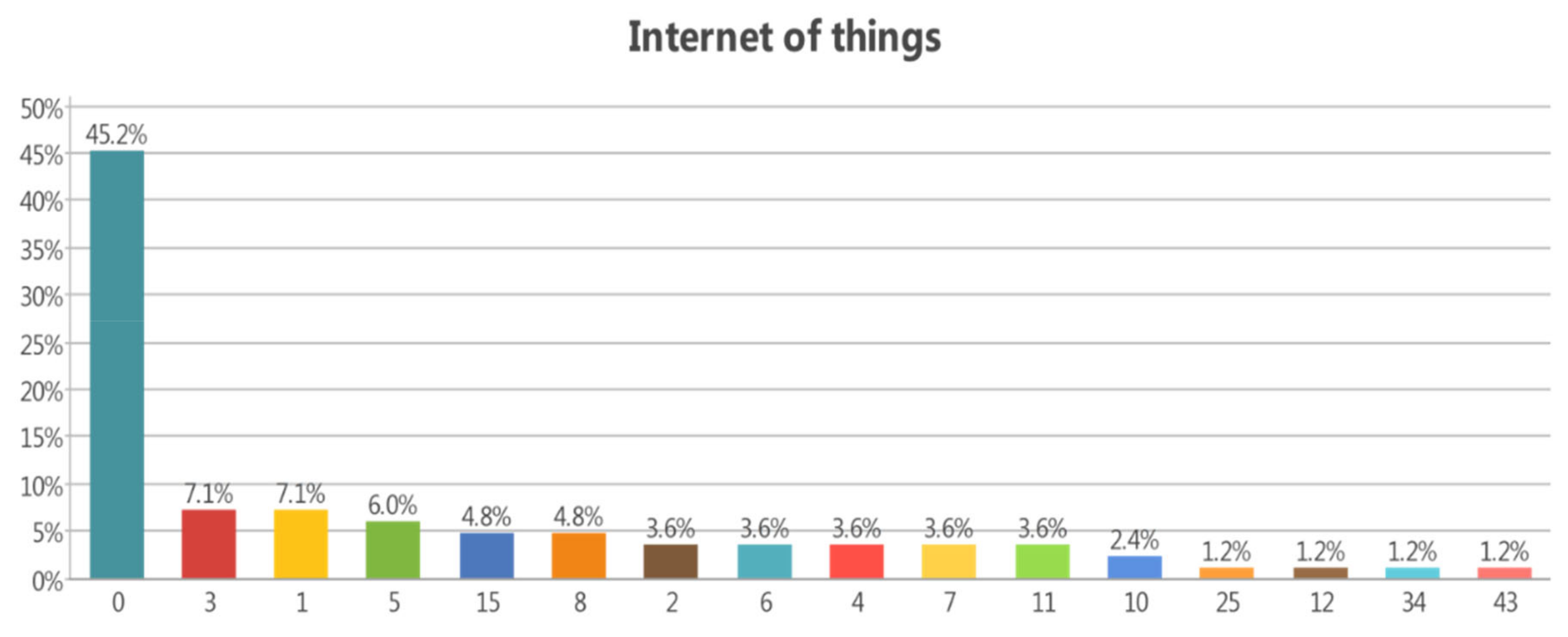
3.3.2. Internet of Things
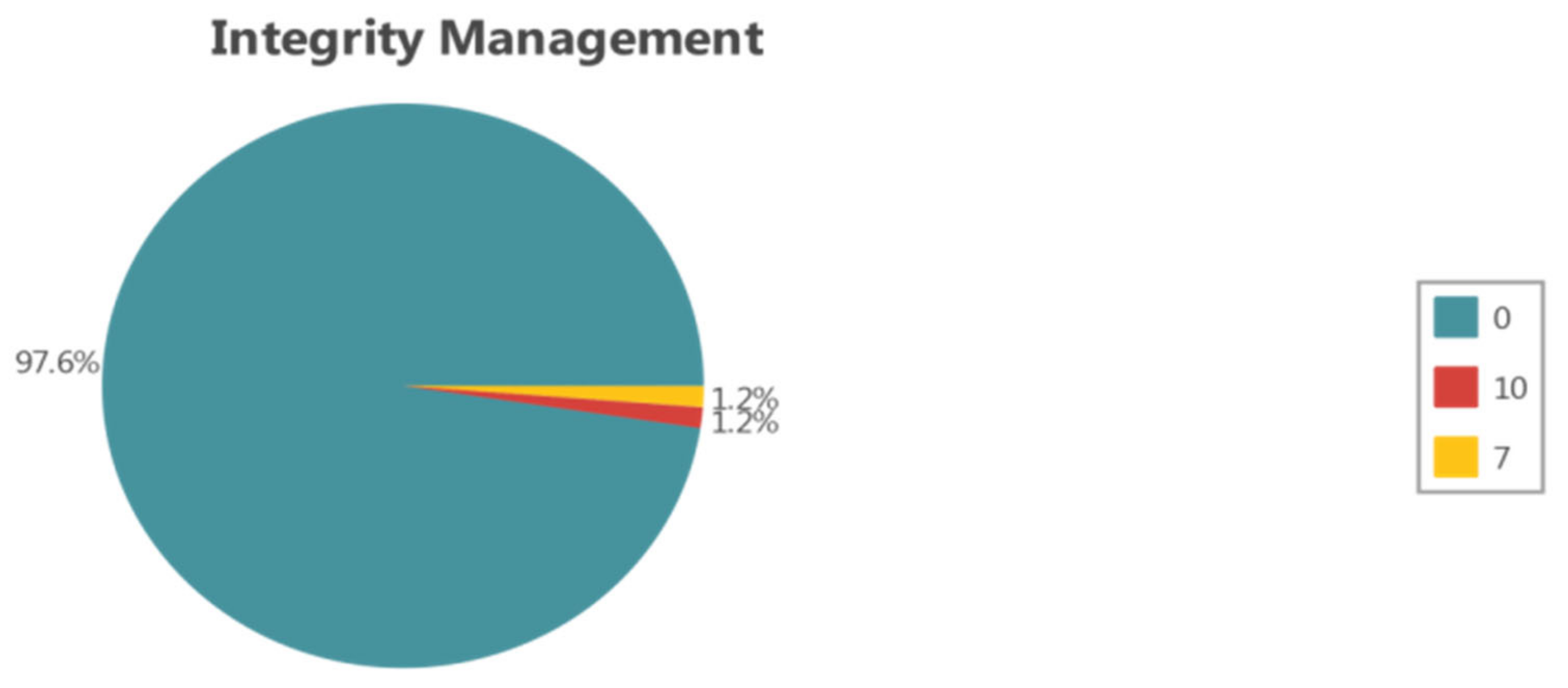
3.3.3. Integrity Management Layer
3.3.4. Fog Computing Layer
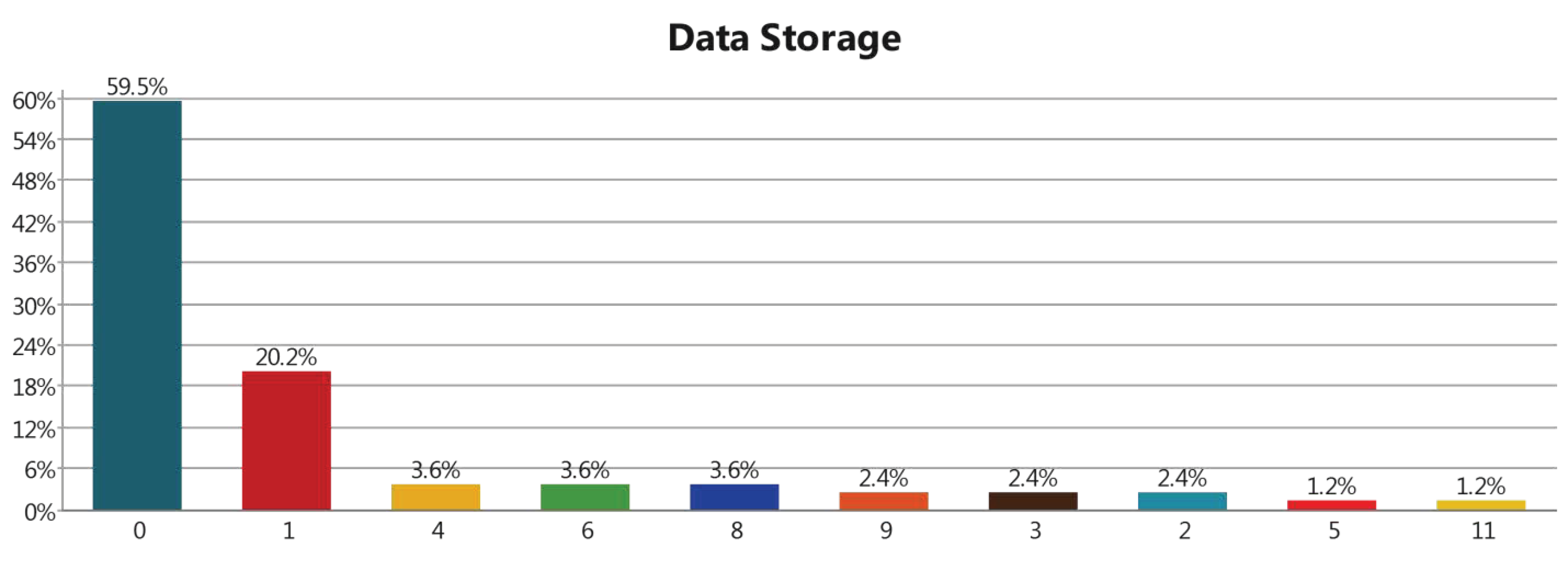
3.3.5. Data Storage Layer
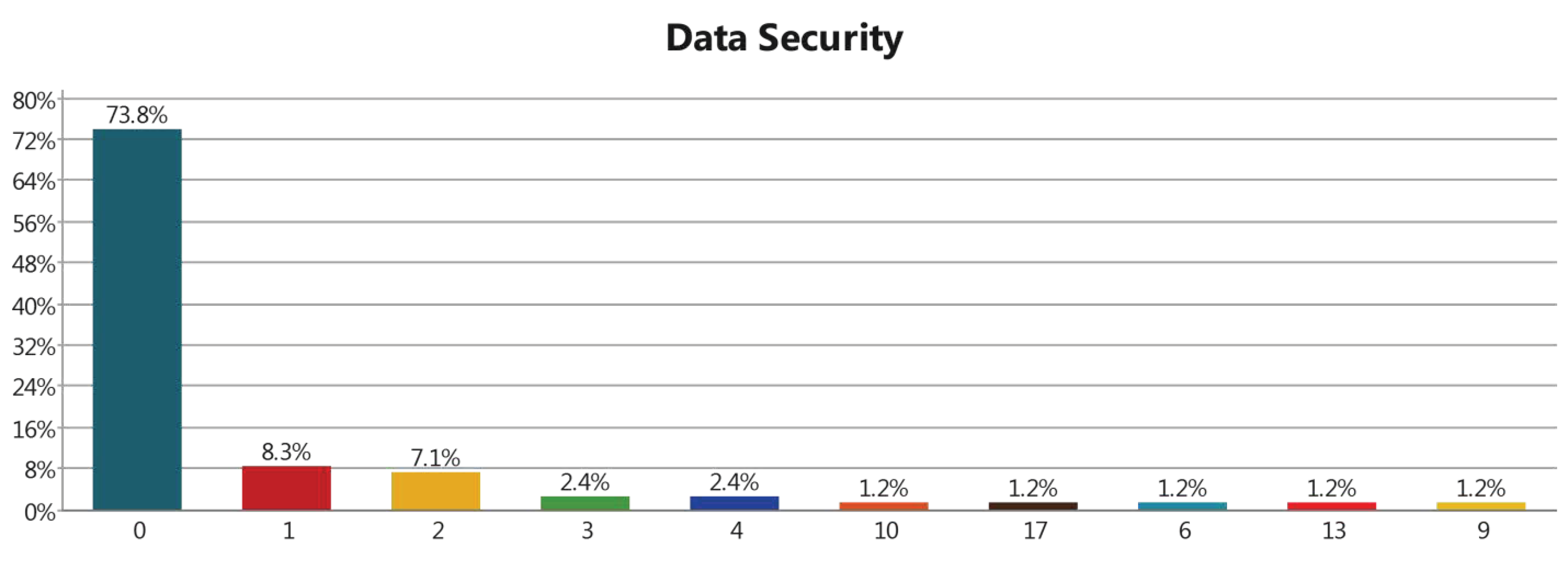
3.3.6. Data Security Layer
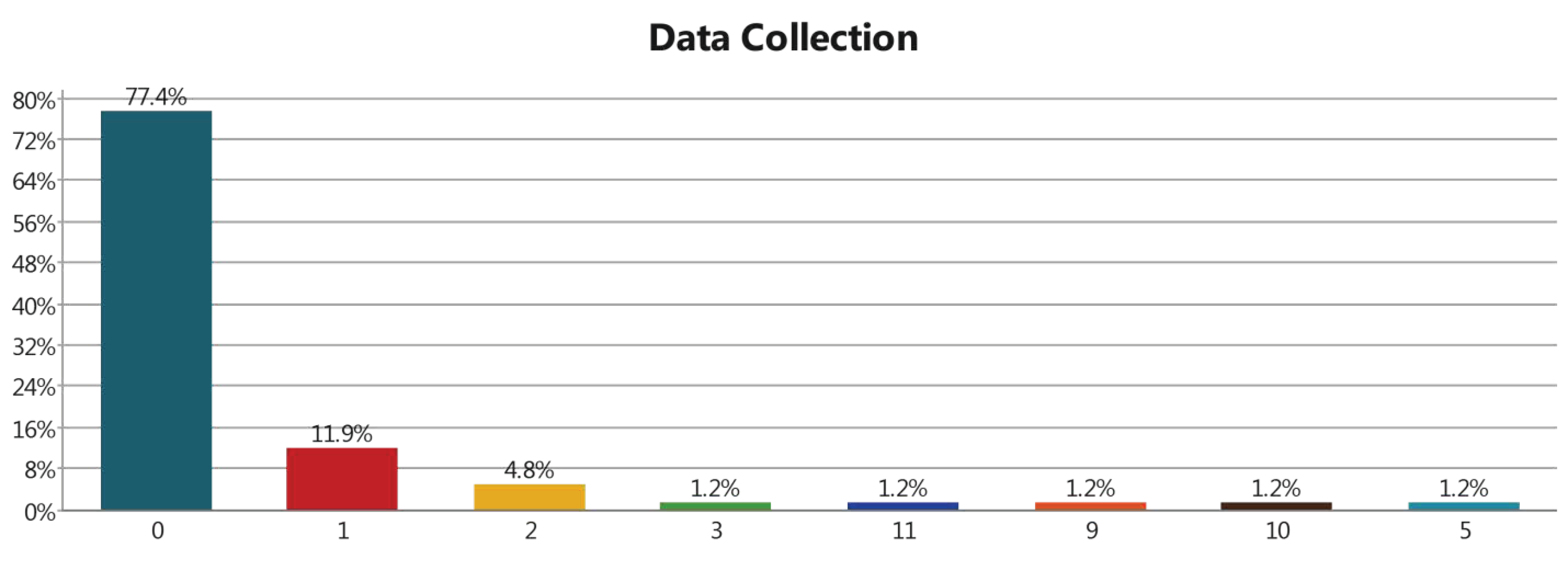
3.3.7. Data Collection Layer
3.3.8. Data Availability Layer
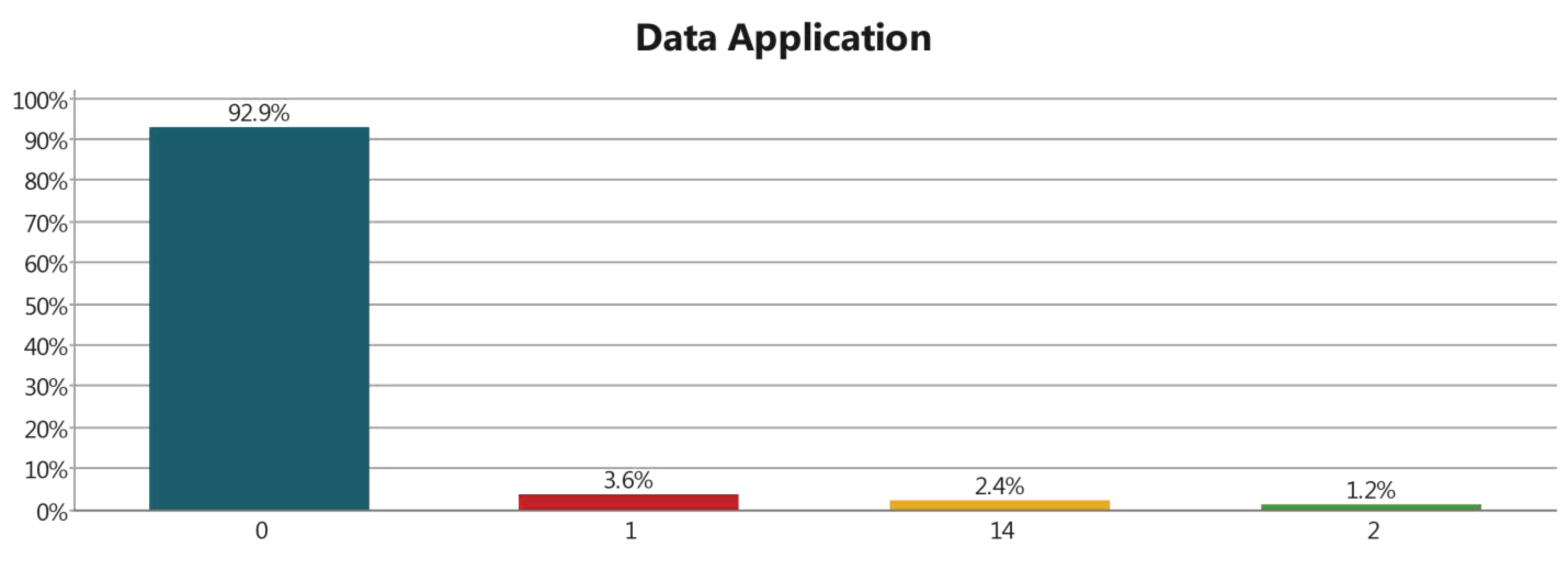
3.3.9. Data Application Layer
3.3.10. Data Analysis Layer
3.3.11. Data Aggregation Layer
4. Qualitative Model
5. Findings and Implications of This Study
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Amin, F.; Abbasi, R.; Rehman, A.; Choi, G.S. An Advanced Algorithm for Higher Network Navigation in Social Internet of Things Using Small-World Networks. Sensors 2019, 19, 2007. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Qian, Y.; Jiang, Y.; Chen, J.; Zhang, Y.; Song, J.; Zhou, M.; Pustišek, M. Towards decentralized IoT security enhancement: A blockchain approach. Comput. Electr. Eng. 2018, 72, 266–273. [Google Scholar] [CrossRef]
- Khattak, H.A.; Shah, M.A.; Khan, S.; Ali, I.; Imran, M. Perception layer security in Internet of Things. Futur. Gener. Comput. Syst. 2019, 100, 144–164. [Google Scholar] [CrossRef]
- Amin, F.; Choi, G.S. Hotspots Analysis Using Cyber-Physical-Social System for a Smart City. IEEE Access 2020, 8, 122197–122209. [Google Scholar] [CrossRef]
- Kumar, N.M.; Mallick, P.K. The Internet of Things: Insights into the building blocks, component interactions, and architecture layers. Procedia Comput. Sci. 2018, 132, 117–119. [Google Scholar] [CrossRef]
- Sun, W.; Cai, Z.; Li, Y.; Liu, F.; Fang, S.; Wang, G. Security and Privacy in the Medical Internet of Things: A Review. Secur. Commun. Netw. 2018, 2018, 5978636. [Google Scholar] [CrossRef]
- Jose, D.V.; Vijyalakshmi, A. An Overview of Security in Internet of Things. Procedia Comput. Sci. 2018, 143, 744–748. [Google Scholar] [CrossRef]
- Yang, A.; Li, Y.; Kong, F.; Wang, G.; Chen, E. Security Control Redundancy Allocation Technology and Security Keys Based on Internet of Things. IEEE Access 2018, 6, 50187–50196. [Google Scholar] [CrossRef]
- Chen, K.; Zhang, S.; Li, Z.; Zhang, Y.; Deng, Q. Internet-of-Things security and vulnerabilities: Taxonomy, challenges, and practice. J. Hardw. Syst. Secur. 2018, 2, 97–110. [Google Scholar] [CrossRef]
- Javaid, U.; Aman, M.N.; Sikdar, B. Blockpro: Blockchain based data provenance and integrity for secure IoT environments. In Proceedings of the ACM Blocksys 2018, New York, NY, USA, 4 November 2018; pp. 13–18. [Google Scholar]
- El-Hajj, M.; Chamoun, M.; Fadlallah, A.; Serhrouchni, A. Analysis of authentication techniques in Internet of Things (IoT). In Proceedings of the 2017 1st Cyber Security in Networking Conference (CSNet), Rio de Janeiro, Brazil, 18–20 October 2017; pp. 1–13. [Google Scholar]
- Huang, Q.; Yang, Y.; Wang, L. Secure Data Access Control with Ciphertext Update and Computation Outsourcing in Fog Computing for Internet of Things. IEEE Access 2017, 5, 12941–12950. [Google Scholar] [CrossRef]
- Sahmim, S.; Gharsellaoui, H. Privacy and security in internet-based computing: Cloud computing, internet of things, cloud of things: A review. Procedia Comput. Sci. 2017, 112, 1516–1522. [Google Scholar] [CrossRef]
- Meddeb, M.; Dhraief, A.; Belghith, A.; Monteil, T.; Drira, K.; Alahmadi, S. Cache Freshness in Named Data Networking for the Internet of Things. Comput. J. 2018, 61, 1496–1511. [Google Scholar] [CrossRef]
- Angin, P.; Mert, M.B.; Mete, O.; Ramazanli, A.; Sarica, K.; Gungoren, B. A Blockchain-Based Decentralized Security Architecture for IoT. In Proceedings of the International Conference on Internet of Things, Seattle, WA, USA, 25–30 June 2018. [Google Scholar] [CrossRef]
- Aman, M.N.; Sikdar, B.; Chua, K.C.; Ali, A. Low Power Data Integrity in IoT Systems. IEEE Internet Things J. 2018, 5, 3102–3113. [Google Scholar] [CrossRef]
- Amin, F.; Choi, G.S. Advanced Service Search Model for Higher Network Navigation Using Small World Networks. IEEE Access 2021, 9, 70584–70595. [Google Scholar] [CrossRef]
- Colicchia, C.; Strozzi, F. Supply chain risk management: A new methodology for a systematic literature review. Supply Chain. Manag. Int. J. 2012, 17, 403–418. [Google Scholar] [CrossRef]
- Dziopa, F.; Ahern, K. A systematic literature review of the applications of Q-technique and its methodology. Eur. J. Res. Methods Behav. Soc. Sci. 2011, 7, 39–55. [Google Scholar] [CrossRef]
- Si, K.; Wolfson, C.; Fi, B. A multidisciplinary systematic literature review on frailty: Overview of the methodology used by the Canadian Initiative on Frailty and Aging. BMC Med. Res. Methodol. 2009, 9, 68–72. [Google Scholar]
- Liu, C.; Yang, C.; Zhang, X.; Chen, J. External integrity verification for outsourced big data in cloud and IoT: A big picture. Future Gener. Comput. Syst. 2015, 49, 58–67. [Google Scholar] [CrossRef]
- Farooq, M.U.; Waseem, M.; Khairi, A.; Mazhar, P.S. A critical analysis on the security concerns of internet of things (IoT). Int. J. Comput. Appl. 2015, 111, 1–6. [Google Scholar]
- Amin, F.; Lee, W.-K.; Mateen, A.; Hwang, S.O. Integration of Network science approaches and Data Science tools in the Internet of Things based Technologies. In Proceedings of the 2021 IEEE Region 10 Symposium (TENSYMP), Jeju, Korea, 23–25 August 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Atlam, H.F.; Walters, R.J.; Wills, G.B. Fog computing and the internet of things: A review. Big Data Cogn. Comput. 2018, 2, 10. [Google Scholar] [CrossRef] [Green Version]
- Hameed, K.; Khan, A.; Ahmed, M.; Reddy, A.G.; Rathore, M.M. Towards a formally verified zero watermarking scheme for data integrity in the Internet of Things based-wireless sensor networks. Futur. Gener. Comput. Syst. 2018, 82, 274–289. [Google Scholar] [CrossRef]
- Bin Qaim, W.; Ometov, A.; Molinaro, A.; Lener, I.; Campolo, C.; Lohan, E.S.; Nurmi, J. Towards Energy Efficiency in the Internet of Wearable Things: A Systematic Review. IEEE Access 2020, 8, 175412–175435. [Google Scholar] [CrossRef]
- Navas, R.E.; Cuppens, F.; Cuppens, N.B.; Toutain, L.; Papadopoulos, G.Z. MTD, Where Art Thou? A Systematic Review of Moving Target Defense Techniques for IoT. IEEE Internet Things J. 2020, 8, 7818–7832. [Google Scholar] [CrossRef]
- Valadares, D.C.G.; Will, N.C.; Caminha, J.; Perkusich, M.B.; Perkusich, A.; Gorgonio, K.C. Systematic Literature Review on the Use of Trusted Execution Environments to Protect Cloud/Fog-Based Internet of Things Applications. IEEE Access 2021, 9, 80953–80969. [Google Scholar] [CrossRef]
- Amjad, A.; Azam, F.; Anwar, M.W.; Butt, W.H. A Systematic Review on the Data Interoperability of Application Layer Protocols in Industrial IoT. IEEE Access 2021, 9, 96528–96545. [Google Scholar] [CrossRef]
- Reilly, E.; Maloney, M.; Siegel, M.; Falco, G. A smart city IoT integrity-first communication protocol via an ethereum blockchain light client. In Proceedings of the SERP4IoT, Colocated with the 44th ACM/IEEE International Conference on Software Engineering ICSE 2022, Marrakech, Morocco, 19 May 2022; pp. 15–19. [Google Scholar]
- Amin, F.; Ahmad, A.; Sang Choi, G.S. Towards Trust and Friendliness Approaches in the Social Internet of Things. Appl. Sci. 2019, 9, 166. [Google Scholar] [CrossRef] [Green Version]





Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ali, A.; Mateen, A.; Hanan, A.; Amin, F. Advanced Security Framework for Internet of Things (IoT). Technologies 2022, 10, 60. https://doi.org/10.3390/technologies10030060
Ali A, Mateen A, Hanan A, Amin F. Advanced Security Framework for Internet of Things (IoT). Technologies. 2022; 10(3):60. https://doi.org/10.3390/technologies10030060
Chicago/Turabian StyleAli, Abid, Abdul Mateen, Abdul Hanan, and Farhan Amin. 2022. "Advanced Security Framework for Internet of Things (IoT)" Technologies 10, no. 3: 60. https://doi.org/10.3390/technologies10030060
APA StyleAli, A., Mateen, A., Hanan, A., & Amin, F. (2022). Advanced Security Framework for Internet of Things (IoT). Technologies, 10(3), 60. https://doi.org/10.3390/technologies10030060






