A Secure Satellite Transmission Technique via Directional Variable Polarization Modulation with MP-WFRFT
Abstract
1. Introduction
- (1)
- In satellite communications, MQPSK modulation is commonly used but can lead to high BER and significant signal energy loss from the RF front-end power amplifier. To address these issues, polarization modulation (PM) can be employed. When the modulation order 2, the distance between adjacent constellation points in PM’s three-dimensional constellation is significantly larger, resulting in better BER performance compared to MQPSK. Additionally, PM is not affected by the nonlinear distortion of the power amplifier.
- (2)
- Currently, the MP-WFRFT secure transmission algorithm is increasingly utilized to enhance the anti-interception performance of communication systems. However, there is a lack of clear numerical analysis regarding its effectiveness in improving anti-interception performance in PM. In this paper, for the VPAPM scheme, the selection of horizontal and vertical direction parameters in the MP-WFRFT algorithm has varying impacts on the anti-interception performance.
- (3)
- Given the current challenges of poor anti-interception performance and low secrecy rates in satellite communication, relying on a single secure transmission technique is insufficient. While MP-WFRFT processes the signal from the perspective of the time-frequency transform domain, it lacks beam directivity in the air domain. In contrast, DM enhances anti-interception performance by leveraging the beam directivity of MIMO in the air domain, serving as a complementary approach to MP-WFRFT.
- (1)
- PM does not introduce additional distortions to amplitude and phase, offering enhanced immunity to interference. The paper proposes a VPAPM scheme, grounded in the fundamental principles of polarization modulation and variable polarization modulation, which effectively suppresses interference by leveraging polarization orthogonality. Additionally, the PAPM scheme is employed to enhance both the data transmission rate and the energy efficiency of the power amplifier.
- (2)
- Based on VPAPM modulation scheme, this study delves into the influence of MP-WFRFT scanning parameter periodicity on the anti-interception capabilities of satellite communication systems. As the results show, firstly, the anti-scanning capabilities of a single parameter in a scale vector vary from one another. Specifically, parameter shows no effect, is the most effective, is the second most effective, and is the least effective. Secondly, the direction outperforms the direction in terms of anti-interception capabilities.
- (3)
- This paper proposes directional variable polarization modulation with MP-WFRFT to improve the anti-interception capabilities of satellite communication systems. The analysis of performance simulation indicates that the fusion algorithm of MP-WFRFT and DM substantially improves the anti-interception performance compared to individual secure transmission methods, improving anti-interception performance by at least an order of magnitude at signal-to-noise ratio above 10 dB. Meanwhile, this also represents a substantial leap forward in the technology for secure satellite communications.
2. System Model
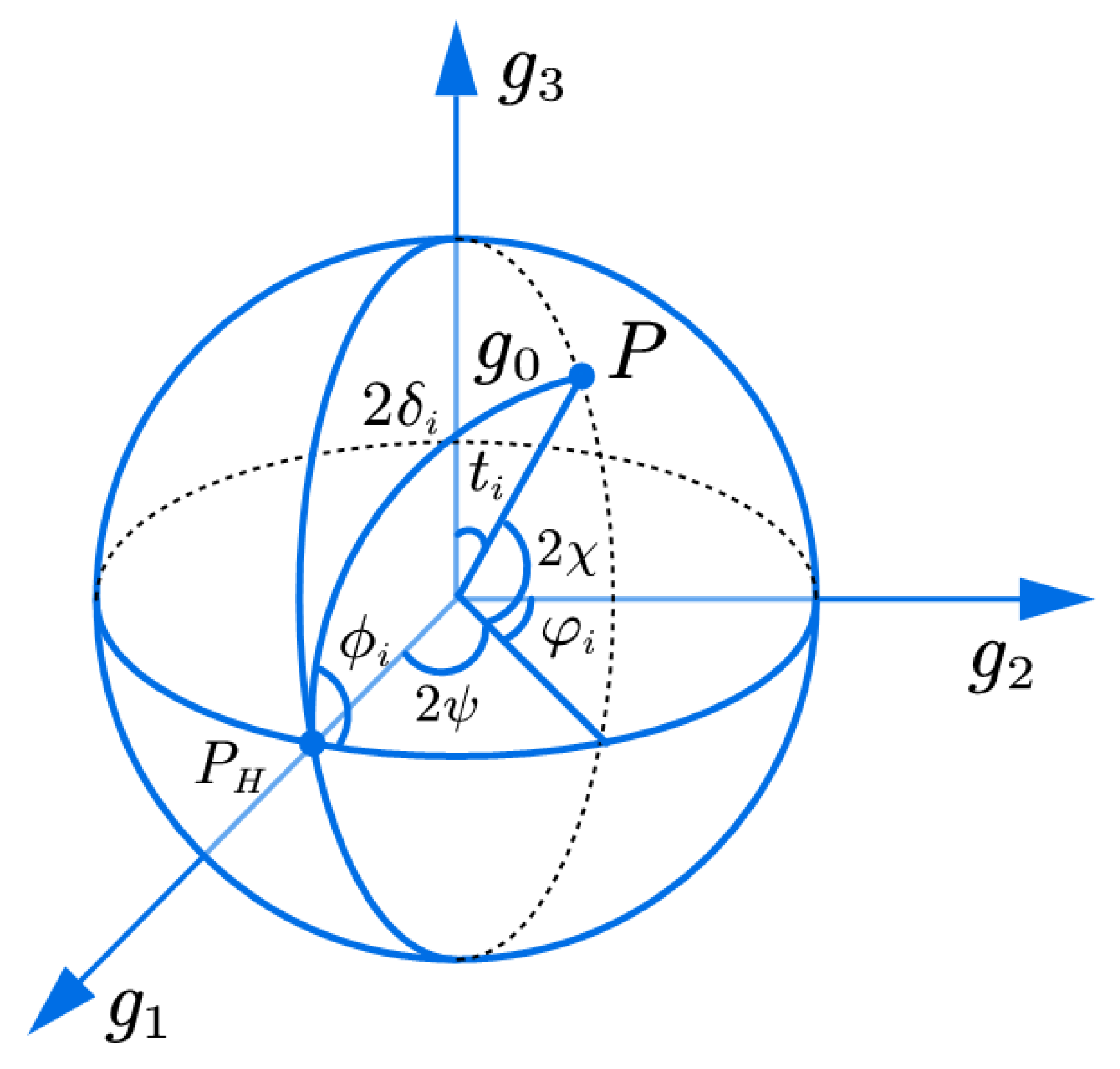
2.1. Polarization Modulation Model
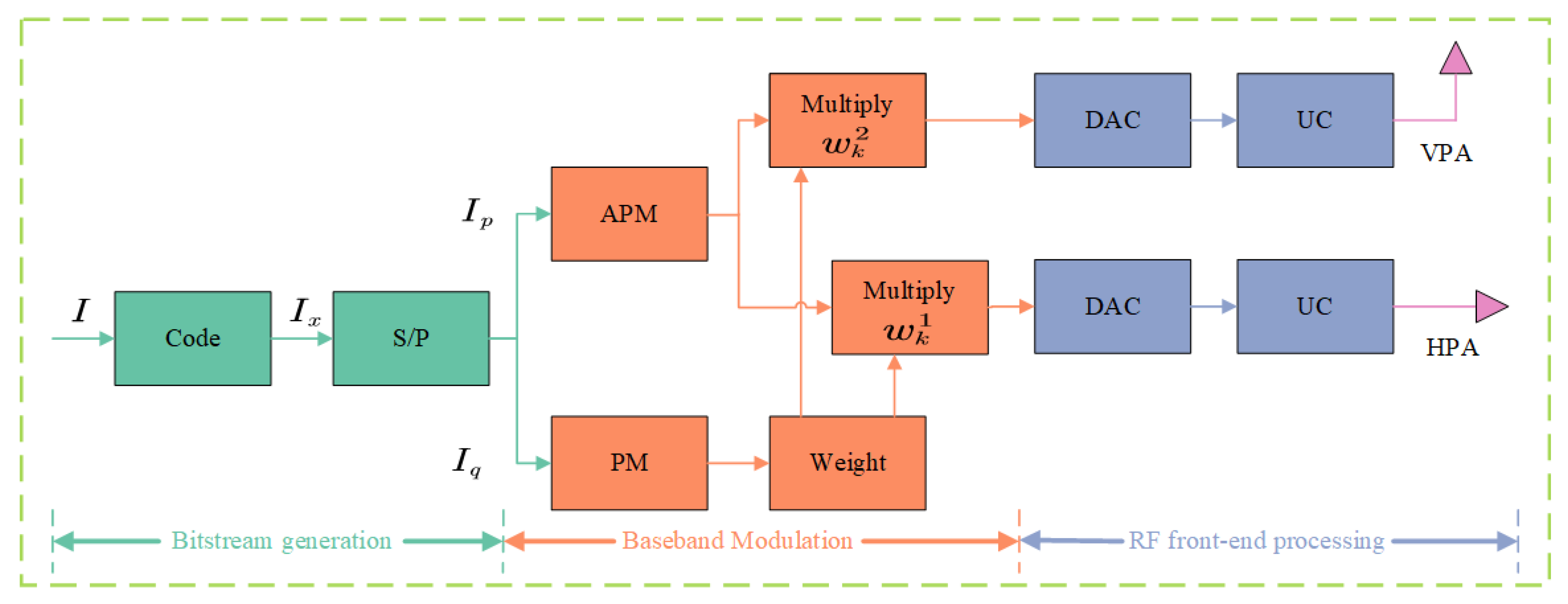
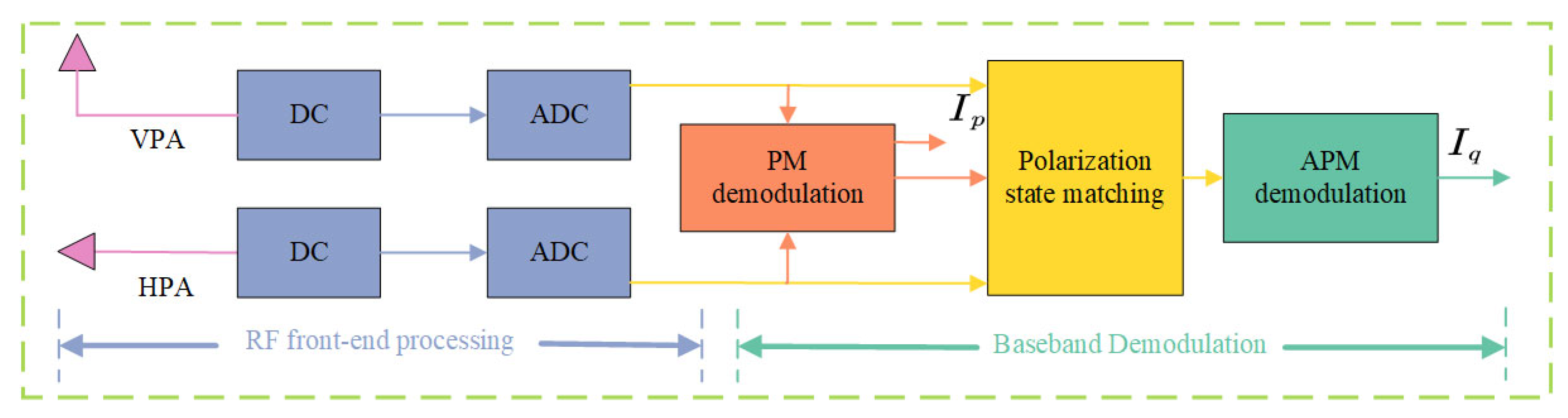
2.2. PAPM Modulation and Demodulation Model
2.3. Multi-Parameter Weighted-Type Fractional Fourier Transform Model
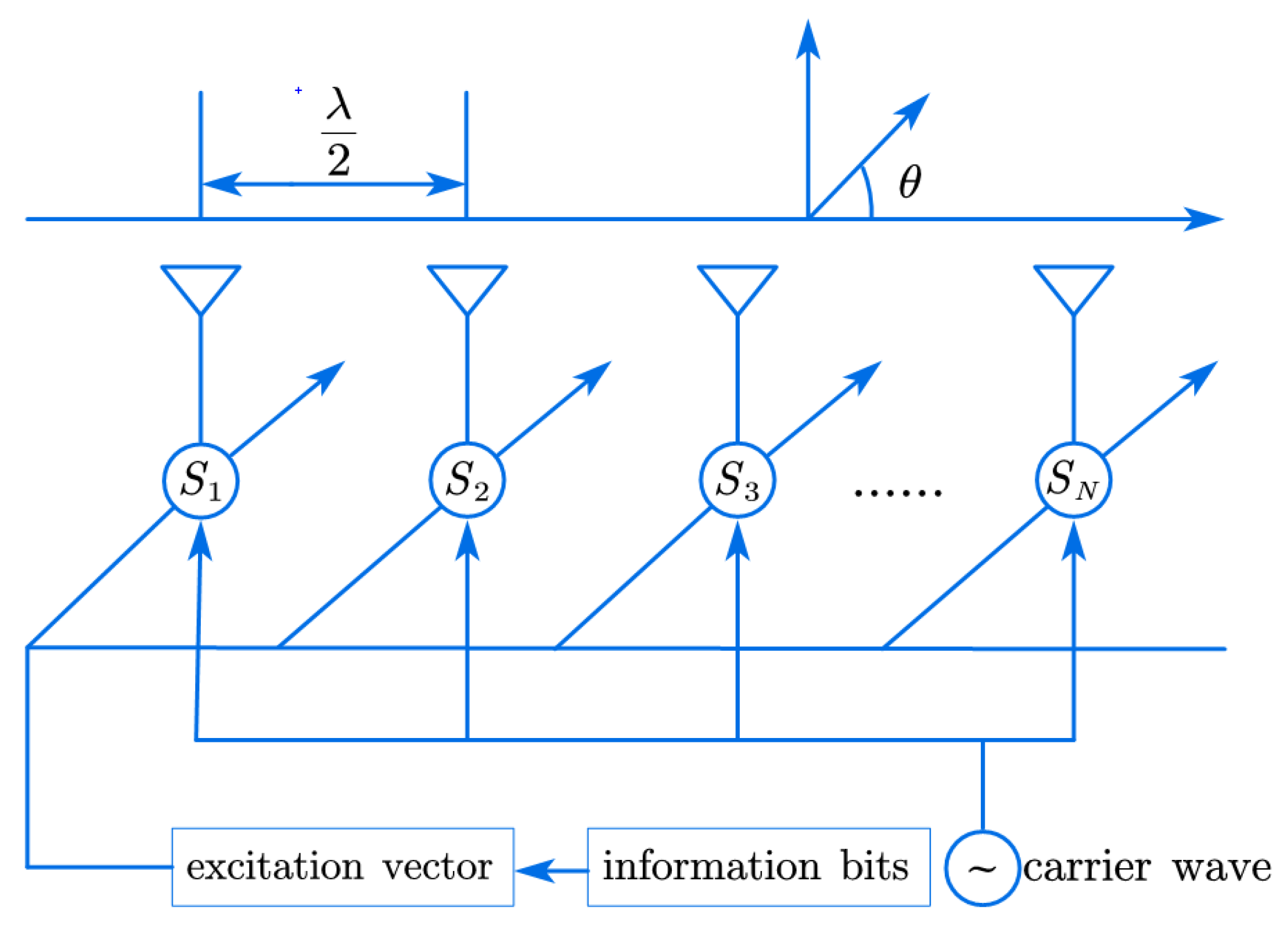
2.4. Directional Modulation Model
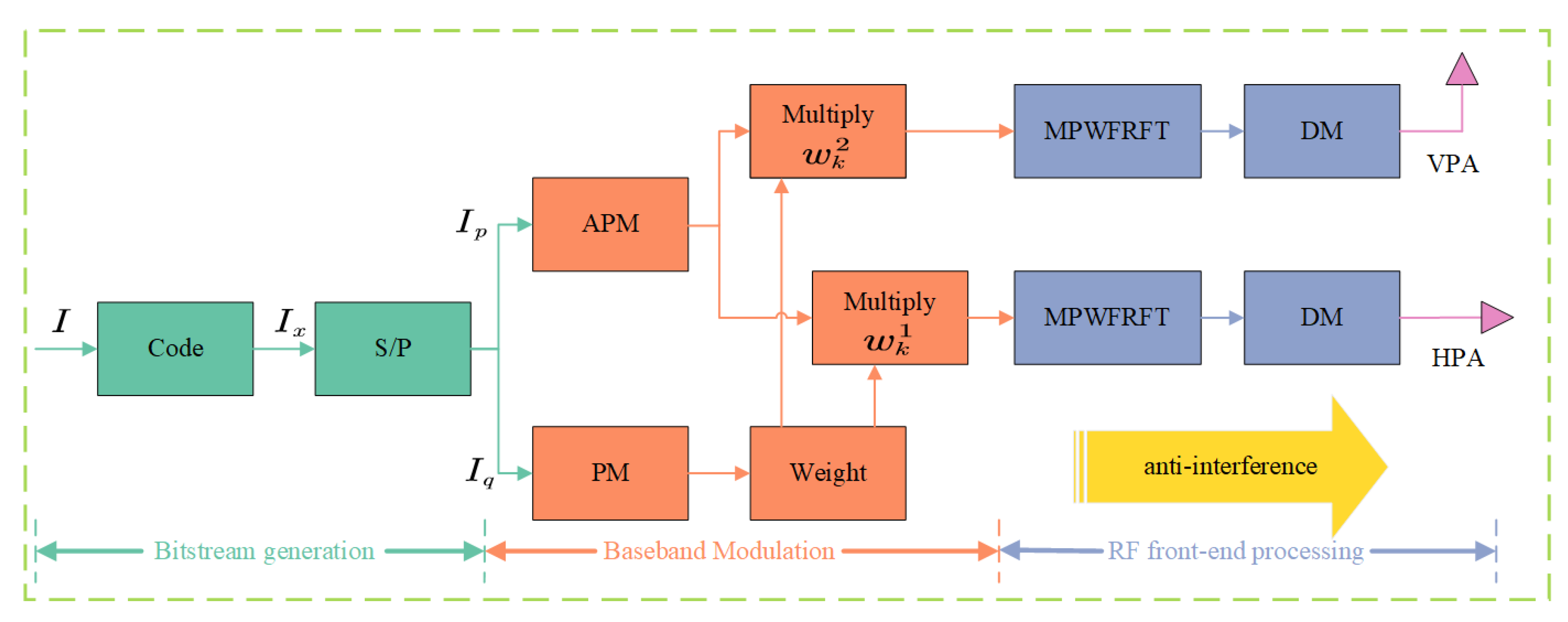
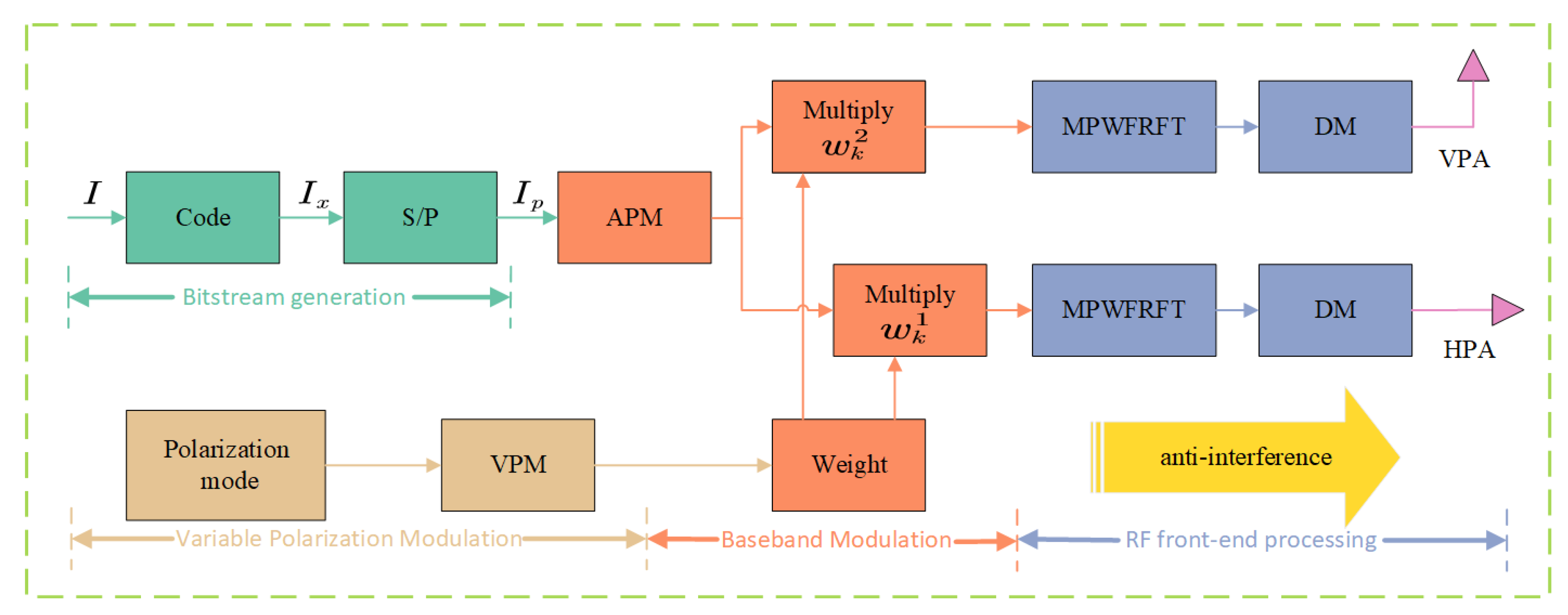
3. Proposed Solution
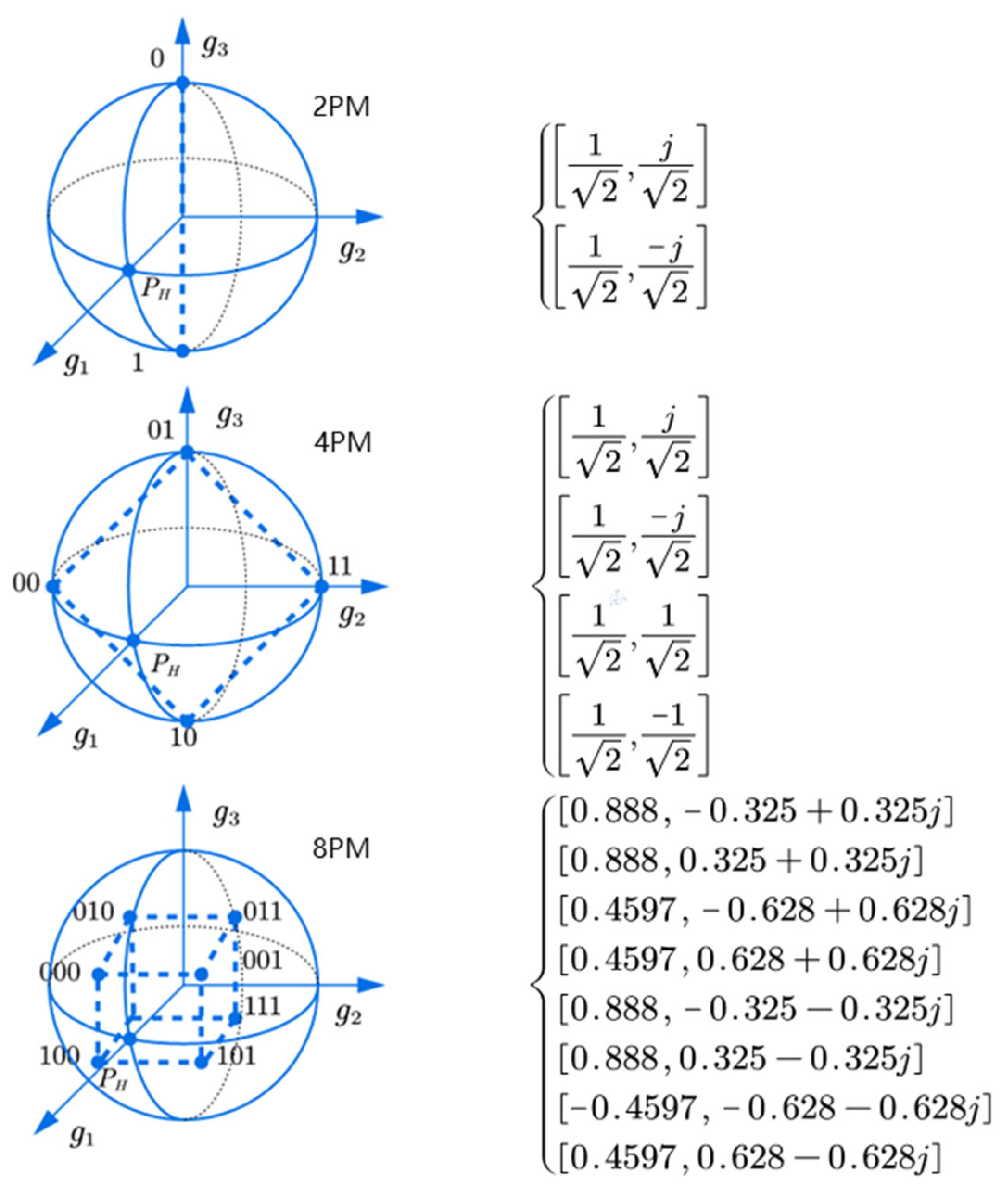
3.1. The Principle of Variable Polarization Modulation
3.2. Analyzing the Impact of MP-WFRFT Parameter Settings on BER Performance
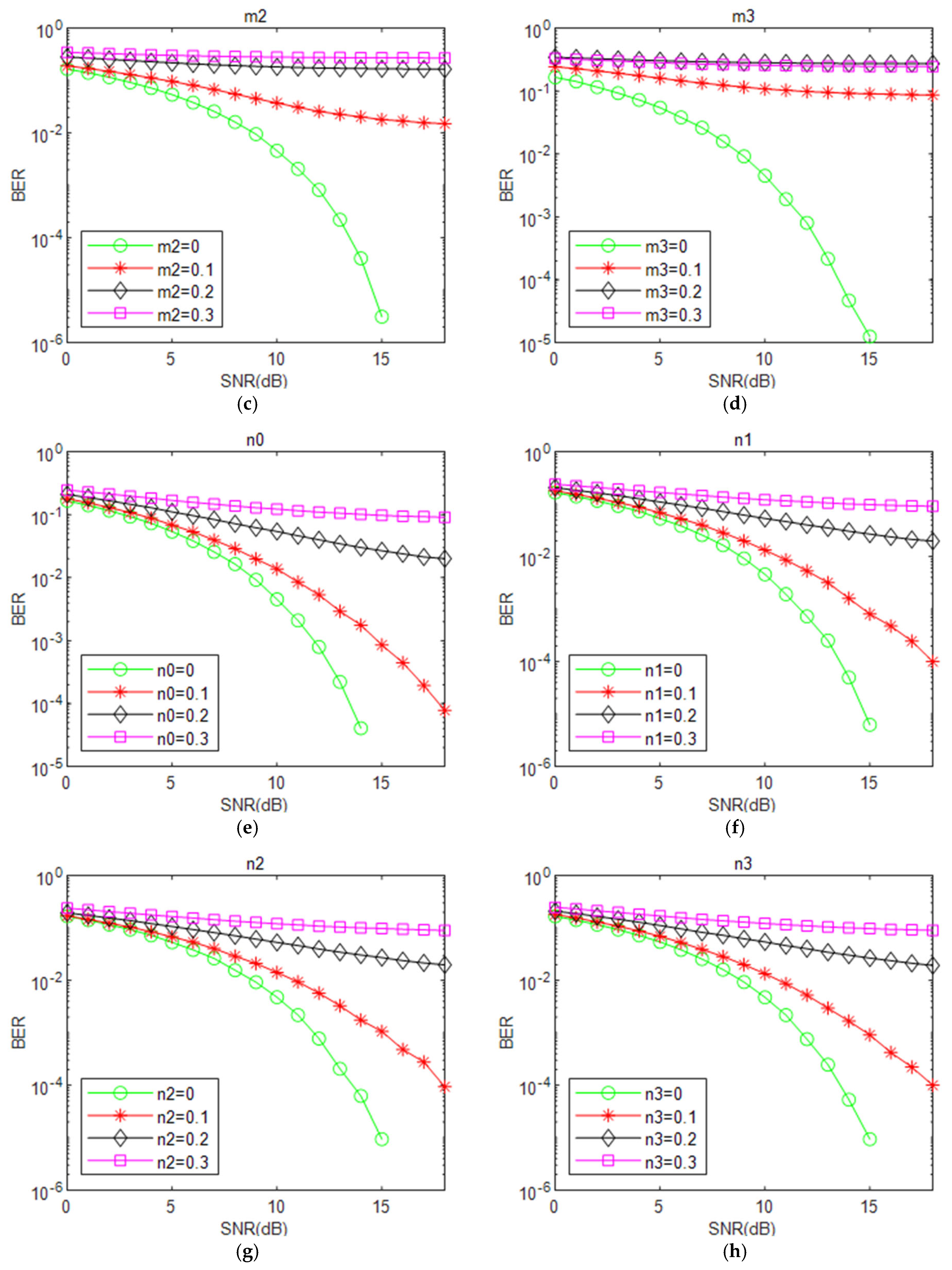
3.2.1. Analyzing the Impact of MP-WFRFT Scale Vector Parameter Settings on BER Performance
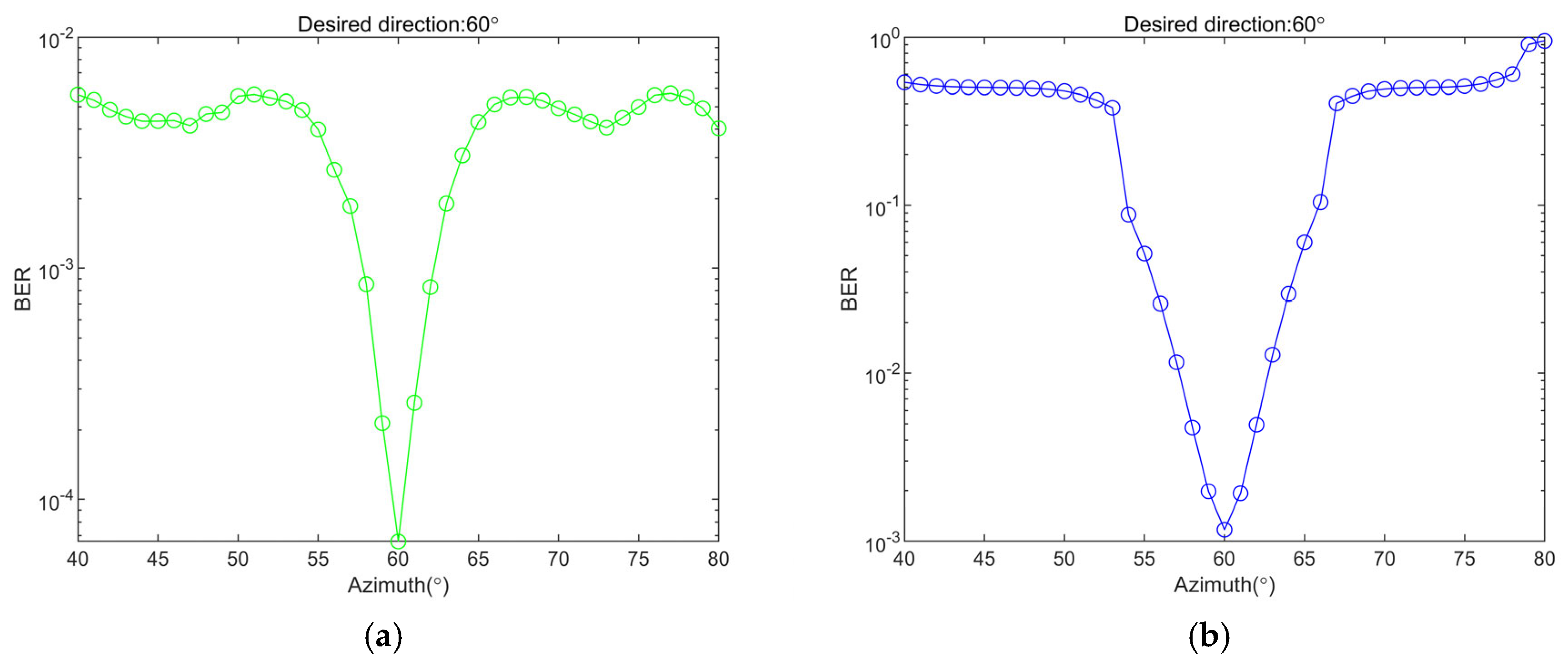
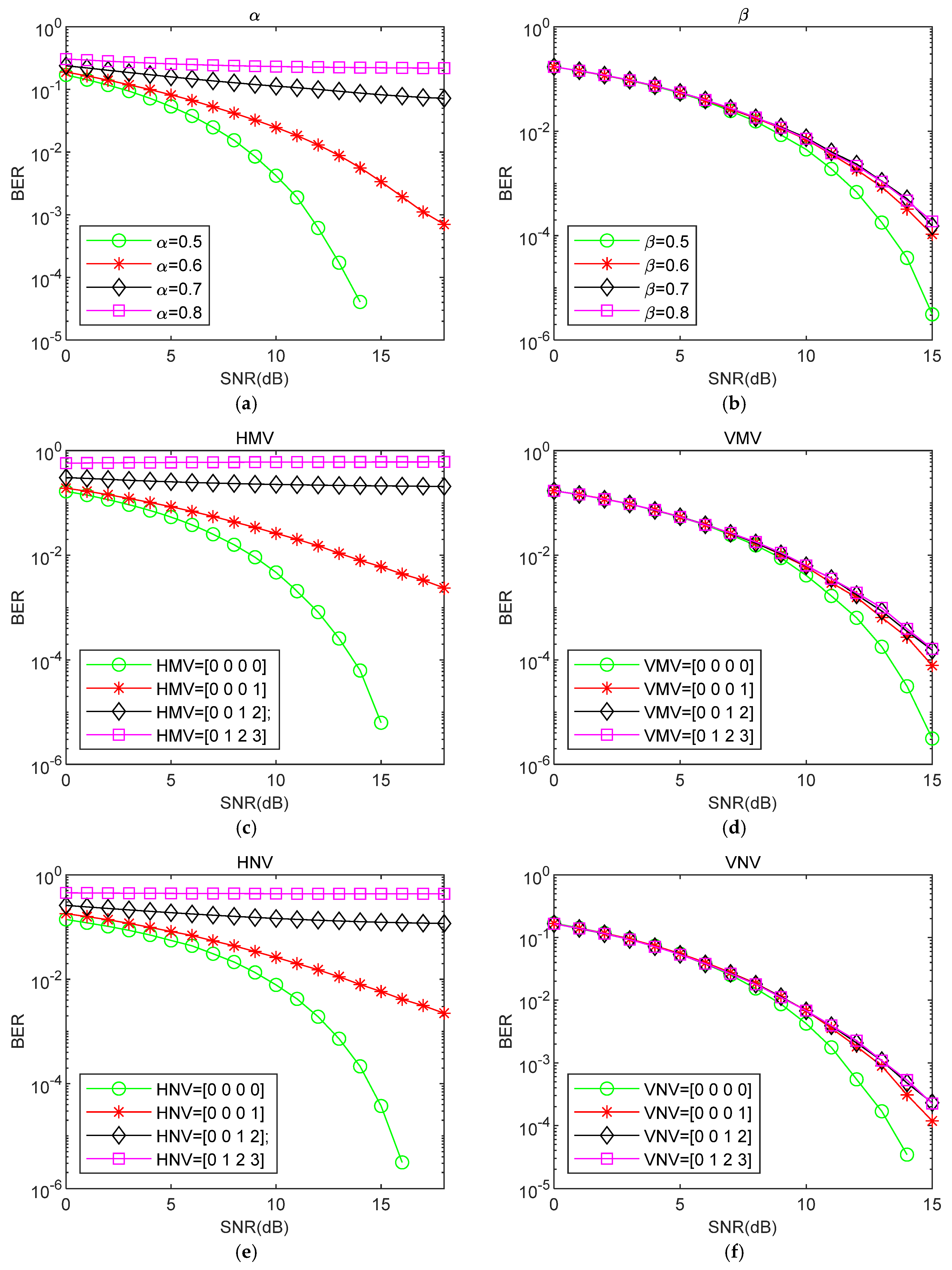
3.2.2. Analyzing the Impact of MP-WFRFT and Direction Parameter Settings on BER Performance
3.3. Proposing the Fusion of MP-WFRFT and DM Algorithms Based on the VPAPM Scheme
- The Principles of PAPM and VPAPM Schemes
- (1)
- The constellation points lie on the Poincare sphere, satisfying and .
- (2)
- The constellation structure maintains central symmetry.
- 2.
- Analyzing the BER Performance of MP-WFRFT and DM fusion algorithm
- (1)
- Simulation 1 (Obtaining ): Activate only the DM system (by setting the MP-WFRFT module to a passthrough mode). Simulate the BER for an eavesdropper at various offset angles (), yielding .
- (2)
- Simulation 2 (Obtaining ): Activate only the MP-WFRFT system (by setting the DM to an omnidirectional transmission mode). Simulate the BER for an eavesdropper using an incorrect security key (,), yielding .
- (3)
- Simulation 3 (Obtaining ): Run the complete, integrated system. Simulate an eavesdropper who is simultaneously at an incorrect angle and using an incorrect key, yielding .
- (4)
- Calculate k: Calculate the value of k over a large number of parameter points (different , , , etc.) using the formula .
- (1)
- Computational complexity: In MP-WFRFT, the complexity of computing the weight is , and that of the weighted sum is , while the fast Fourier transform (FFT) has a computational complexity of . As , . Consequently, the time complexity of MP-WFRFT is , primarily determined by the length of the discrete sequence. Moreover, both the time and space complexities of the DM algorithm are (where is the number of antenna elements), corresponding to linear complexity. Thus, it is evident that the integrated MP-WFRFT and DM algorithm exhibits a relatively low complexity, facilitating its practical implementation.
- (2)
- Power consumption: Increased digital processing and the need to drive a multi-element antenna array for DM will lead to higher power consumption. However, this is partially mitigated by one of the core components of our scheme. The use of PAPM is known to improve the power efficiency of the satellite’s high-power amplifier (HPA) by reducing the peak-to-average power ratio (PAPR) compared to that of some traditional modulation formats.
4. Simulation Experiment Results and Discussion
4.1. The Influence of the MP-WFRFT Algorithm on Signal Constellation Map Distribution
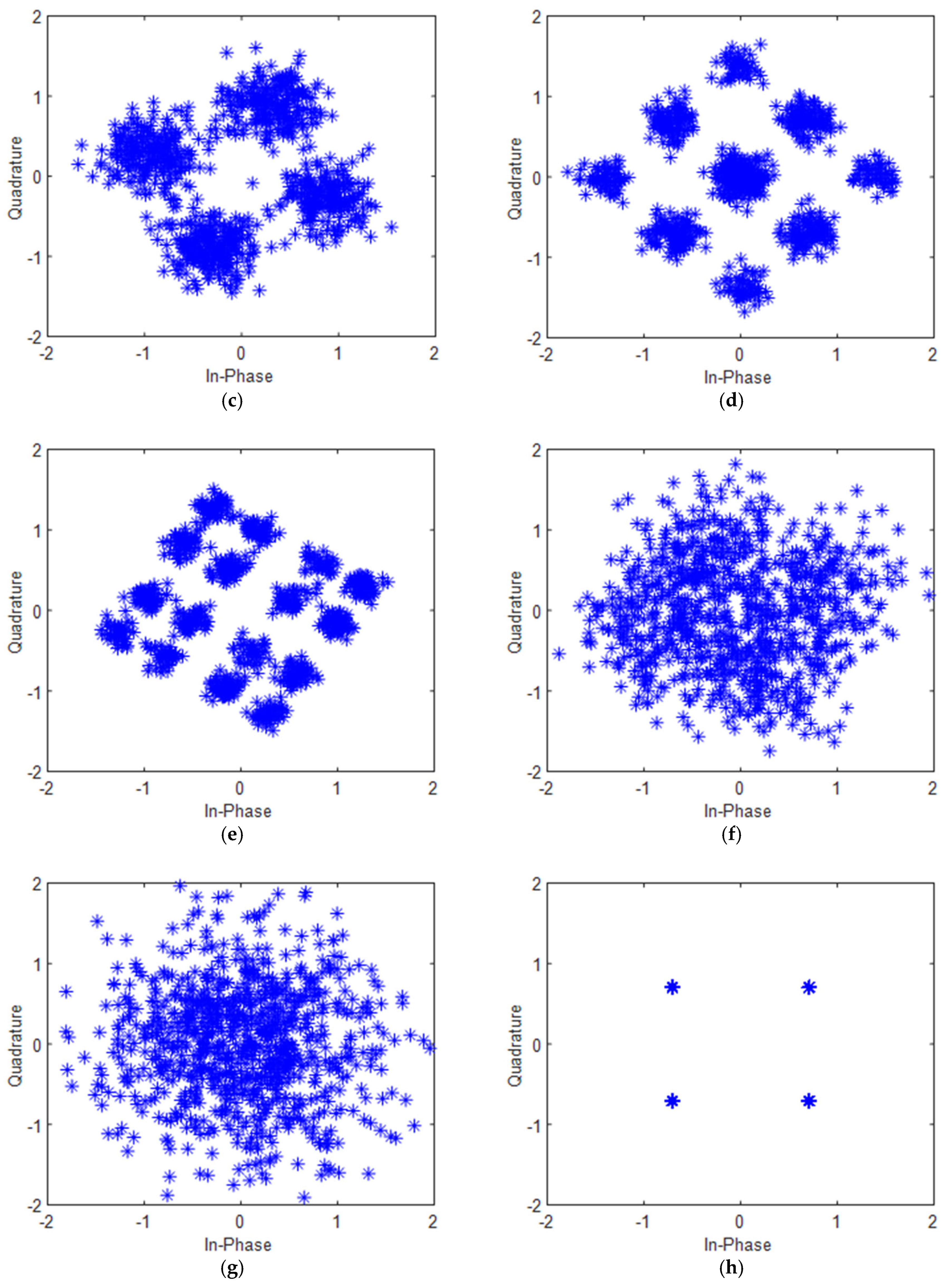
4.1.1. Parameter Scanning Characteristics of the MP-WFRFT Algorithm in Two-Dimensional Constellation Map
4.1.2. Parameter Scanning Characteristics of the MP-WFRFT Algorithm in Three-Dimensional Constellation Map
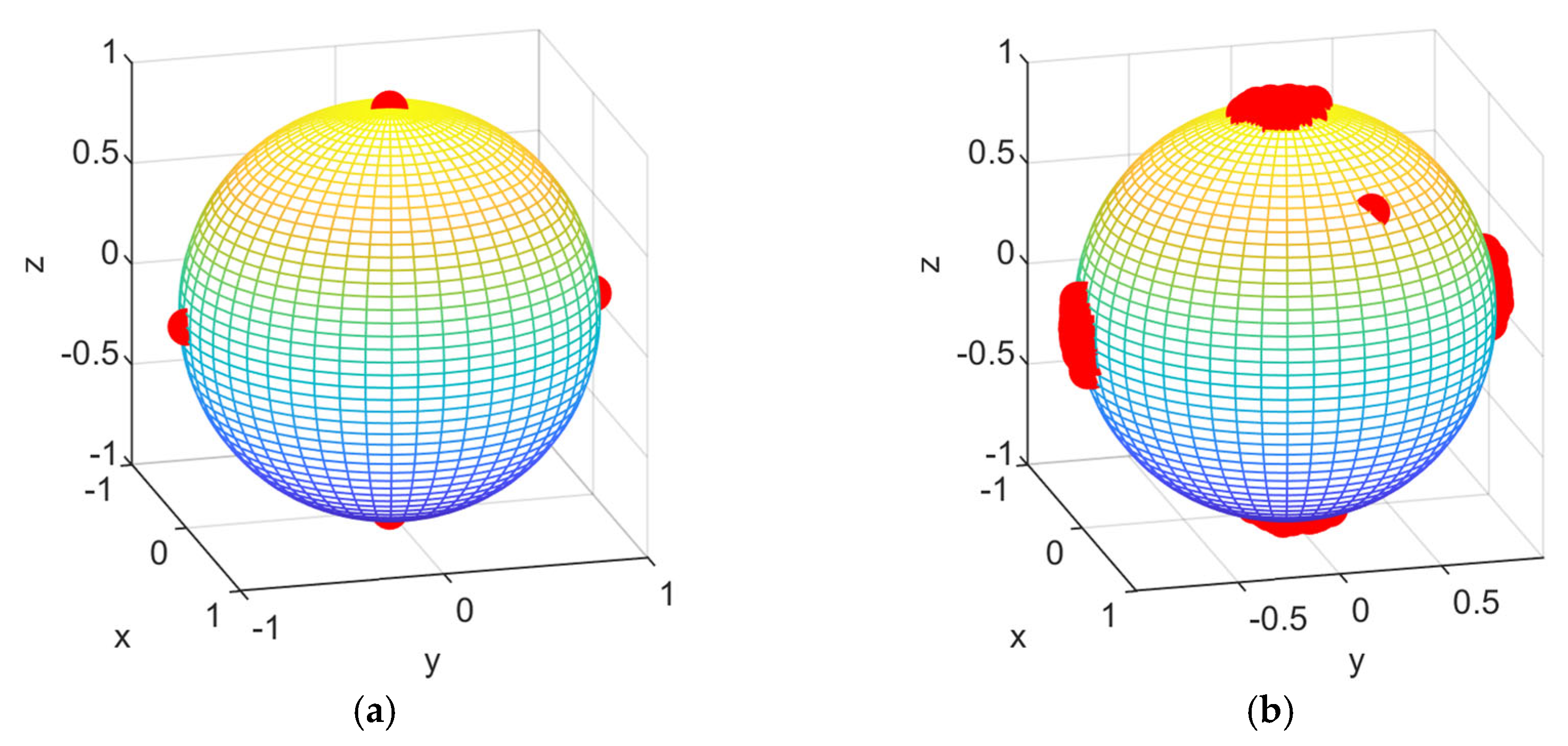
4.2. The Influence of DM on Conventional and Polarization Modulation
4.3. BER Performance Comparison of MP-WFRFT Parameters Based on the VPAPM Scheme
- (1)
- Changing the parameter in the horizontal and vertical directions has no impact on the BER performance of the received signal, as shown in Figure 12a.
- (2)
- From Figure 12b–d, it is observed that the BER performance for receiver is the best, followed by , while has the worst performance.
- (3)
- The effects of parameters , , , and on the BER performance at the receiver are nearly the same, as shown in Figure 12e–h.
4.4. Directional Variable Polarization Modulation with MP-WFRFT
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kua, J.; Loke, S.W.; Arora, C.; Fernando, N.; Ranaweera, C. A survey of next-generation computing technologies in space-air-ground integrated networks. ACM Comput. Surv. 2023, 56, 1–40. [Google Scholar]
- He, J.; Cheng, N.; Yin, Z.; Zhou, C.; Zhou, H.; Quan, W.; Lin, X.-H. Service-oriented network resource orchestration in space-air-ground integrated network. IEEE Trans. Veh. Technol. 2024, 73, 1162–1174. [Google Scholar] [CrossRef]
- Reddy, Y.M.; Raj, V.H.; Thethi, H.P.; Gupta, S.; Maan, P.; Ghani, R.H. Low earth orbit satellite networks: A new era in global communication. In Proceedings of the 2023 10th IEEE Uttar Pradesh Section International Conference on Electrical, Electronics and Computer Engineering (UP CON), Gautam Buddha Nagar, India, 1–3 December 2023; Volume 10. [Google Scholar]
- Shen, Z.; Jin, J.; Tan, C.; Tagami, A.; Wang, S.; Li, Q.; Zheng, Q.; Yuan, J. Internet of things in space: A review of opportunities and challenges from satellite-aided computing to digitally-enhanced space living. Sensors 2021, 21, 8117. [Google Scholar]
- Chai, F.; Zhang, Q.; Yao, H.; Xin, X.; Gao, R.; Guizani, M. Joint multi-task offloading and resource allocation for mobile edge computing systems in satellite IOT. IEEE Trans. Veh. Technol. 2023, 72, 7783–7795. [Google Scholar] [CrossRef]
- Li, X.; Lu, Z.; Yuan, M.; Liu, W.; Wang, F.; Yu, Y.; Liu, P. Tradeoff of code estimation error rate and terminal gain in SCER attack. IEEE Trans. Instrum. Meas. 2024, 73, 8504512. [Google Scholar] [CrossRef]
- Shen, N.; Chen, L.; Liu, J.; Wang, L.; Tao, T.; Wu, D.; Chen, R. A review of global navigation satellite system (GNSS)-based dynamic monitoring technologies for structural health monitoring. Remote Sens. 2019, 11, 1001. [Google Scholar] [CrossRef]
- Giordani, M.; Zorzi, M. Satellite communication at millimeter waves: A key enabler of the 6g era. In Proceedings of the 2020 International Conference on Computing, Networking and Communications (ICNC), Big Island, HI, USA, 17–20 February 2020; pp. 383–388. [Google Scholar]
- Wang, J.; Jiang, C.; Kuang, L. High-mobility satellite-UAV communications: Challenges, solutions, and future research trends. IEEE Commun. Mag. 2022, 60, 38–43. [Google Scholar] [CrossRef]
- Tedeschi, P.; Sciancalepore, S.; Di Pietro, R. Satellite-based communications security: A survey of threats, solutions, and research challenges. Comput. Networks 2022, 216, 109246. [Google Scholar] [CrossRef]
- Zou, Y.; Zhu, J.; Wang, X.; Hanzo, L. A survey on wireless security: Technical challenges, recent advances, and future trends. Proc. IEEE 2016, 104, 1727–1765. [Google Scholar] [CrossRef]
- Mukherjee, A.; Fakoorian, S.A.A.; Huang, J.; Swindlehurst, A.L. Principles of physical layer security in multiuser wireless networks: A survey. IEEE CST 2014, 16, 1550–1573. [Google Scholar] [CrossRef]
- Namias, V. The fractional order Fourier transform and its application to quantum mechanics. IMA J. Appl. Math. 1980, 25, 241–265. [Google Scholar] [CrossRef]
- McBride, A.C.; Kerr, F.H. On Namias’s fractional Fourier transforms. IMA J. Appl. Math. 1987, 39, 159–175. [Google Scholar] [CrossRef]
- Lohmann, A.W. Image rotation, Wigner rotation, and the fractional Fourier transform. J. Opt. Soc. Am. A-Opt. Image Sci. Vision. 1993, 10, 2181–2186. [Google Scholar] [CrossRef]
- Shih, C.-C. Fractionalization of Fourier transform. Opt. Commun. 1995, 118, 495–498. [Google Scholar] [CrossRef]
- Mei, L.; Sha, X.; Zhang, N. Research on the application of 4-weighted fractional Fourier transform in communication system. Sci. China-Inf. Sci. 2010, 53, 1251–1260. [Google Scholar] [CrossRef]
- Ding, B.; Mei, L.; Sha, X. Secure communication system based on alterable-parameter 4-weighted fractional Fourier transform. Inf. Technol. J. 2010, 9, 158–163. [Google Scholar] [CrossRef][Green Version]
- Fang, X.; Zhang, N.; Sha, X.; Chen, D.; Wu, X.; Shen, X. Physical layer security: A WFRFT-base cooperation approach. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017. [Google Scholar]
- Zhang, X.; Zhang, B.; Guo, D.; Wang, Y. Application of polarization modulation in satellite communication. In Proceedings of the 2017 First International Conference on Electronics Instrumentation Information Systems (EIIS), Harbin, China, 3–5 June 2017. [Google Scholar]
- Wei, D.; Feng, C.; Guo, C. A polarization-amplitude-phase modulation scheme for the power amplifier energy efficiency enhancement. In Proceedings of the 15th International Symposium on Wireless Personal Multimedia Communications, Taipei, Taiwan, 24–27 September 2012. [Google Scholar]
- Wei, D.; Zhang, M.; Fan, W.; Huang, W. A spectrum efficient polarized PSK/QAM scheme in the wireless channel with polarization dependent loss effect. In Proceedings of the 2015 22nd International Conference on Telecommunications, Sydney, NSW, Australia, 27–29 April 2015. [Google Scholar]
- Liu, F.; Wang, X.; Li, R.; Wang, B. Multilevel continuous polarization modulation with high spectral efficiency in the depolarization channels. IEEE Access. 2018, 6, 33002–33014. [Google Scholar] [CrossRef]
- Zhao, S.; Zeng, Z.; Feng, C.; Liu, F. Power amplifier energy efficiency enhancement via adaptive polarization-QAM modulation scheme in OFDM systems. IEEE Access. 2017, 5, 23751–23763. [Google Scholar] [CrossRef]
- DA, X.; Wang, H.; Luo, Z. Dual-polarized satellite security trans mission scheme based on double layer multi-parameter weighted-type fractional Fourier transform. J. Electron. Inf. Technol. 2019, 41, 1974–1982. [Google Scholar]
- Qiu, B.; Cheng, W.; Zhang, W. Decomposed and distributed directional modulation for secure wireless communication. IEEE Trans. Wirel. Commun. 2024, 23, 5219–5231. [Google Scholar] [CrossRef]
- Hafez, M.; Yusuf, M.; Khattab, T.; Elfouly, T.; Arslan, H. Secure spatial multiple access using directional modulation. IEEE Trans. Wirel. Commun. 2018, 17, 563–573. [Google Scholar] [CrossRef]
- Liu, F.; Wang, L.; Xie, J. Directional modulation technique for linear sparse arrays. IEEE Access. 2019, 7, 13230–13240. [Google Scholar] [CrossRef]
- Zhuang, Z.; Junshan, L.; Shilian, W.; Guojiang, X. Security-enhanced directional modulation based on two-dimensional M-WFRFT. China Commun. 2024, 21, 229–248. [Google Scholar] [CrossRef]
- Kalantari, A.; Soltanalian, M.; Maleki, S.; Chatzinotas, S.; Ottersten, B. Directional modulation via symbol-level precoding: A way to enhance security. IEEE J. Sel. Top. Signal Process. 2016, 10, 1478–1493. [Google Scholar] [CrossRef]
- Wang, W.-Q.; Zheng, Z. Hybrid MIMO and phased-array directional modulation for physical layer security in mmWave wireless communications. IEEE J. Sel. Areas Commun. 2018, 36, 1383–1396. [Google Scholar] [CrossRef]
- Shu, F.; Wu, X.; Li, J.; Chen, R.; Vucetic, B. Robust synthesis scheme for secure multi-beam directional modulation in broadcasting systems. IEEE Access. 2016, 4, 6614–6623. [Google Scholar] [CrossRef]
- Christopher, R.M.; Borah, D.K. Iterative convex optimization of multi-beam directional modulation with artificial noise. IEEE Commun. Lett. 2018, 22, 1712–1715. [Google Scholar] [CrossRef]
- Luo, Z.; Wang, H.; Lv, W. Directional polarization modulation for secure transmission in dual-polarized satellite MIMO systems. In Proceedings of the 2016 8th International Conference on Wireless Communications Signal Processing (WCSP), Yangzhou, China, 13–15 October 2016. [Google Scholar]
- Luo, Z.; Pei, Z.; Zou, B. Directional polarization modulation for secure dual-polarized satellite communication. In Proceedings of the 2019 International Conference on Communications, Information System and Computer Engineering (CISCE), Haikou, China, 5–7 July 2019. [Google Scholar]
- Collett, E. Field Guide to Polarization; SPIE Press: Bellingham, WA, USA, 2005. [Google Scholar]
- Brosseau, C. Fundamentals of Polarized Light: A Statistical Optics Approach; John Wiley: Hoboken, NJ, USA, 1998. [Google Scholar]





| Technique | Security Domain(s) | Key Space Size | Anti-Interception Gain | Limitations |
|---|---|---|---|---|
| (DM) [34,35] | Spatial | Low (direction) | Moderate | Susceptible to multi-antenna eavesdroppers |
| Artificial noise (AN) DM [26] | Spatial | Moderate (direction + AN) | High | Reduces power efficiency; AN can interfere with legitimate users |
| WFRFT-based security [25] | Time-frequency (TF) | High (transform orders/vectors) | High | No spatial security; susceptible to frontal attack at the correct location |
| Our proposed scheme | Multi-domain (spatial + TF Polarization) | Very high (combined keys) | Very high (synergistic) | Increased system complexity |
| Positive | MV | NV | Inverse | |
|---|---|---|---|---|
| (b) | 0.05 | [0 0 0 0] | [0 0 0 0] | (a) |
| (c) | 0.20 | [0 0 0 0] | [0 0 0 0] | (a) |
| (d) | 2.90 | [0 0 1.3 0] | [0 0 0 4.7] | (a) |
| (e) | 1.95 | [0 0 1 0] | [3.5 0 0 0] | (a) |
| (f) | 0.05 | [6 5 0 0] | [0 0 4 3] | (a) |
| (g) | 1.00 | [6 5 4 0] | [0 4 3 2] | (a) |
| …… | …… | …… | …… | (a) |
| (h) | 2.00 | [6 5 4 3] | [6 5 4 3] | (a) |
| Positive | MV1 | NV1 | MV2 | NV2 | Inverse | ||
|---|---|---|---|---|---|---|---|
| (b) | 0.05 | [0 0 0 0] | [0 0 0 0] | 0.05 | [0 0 0 0] | [0 0 0 0] | (a) |
| (c) | 0.20 | [0 0 0 0] | [0 0 0 0] | 0.20 | [0 0 0 0] | [0 0 0 0] | (a) |
| (d) | 0.30 | [6 0 0 0] | [0 5 0 0] | 0.30 | [6 0 0 0] | [0 5 0 0] | (a) |
| (e) | 0.40 | [6 5 0 0] | [0 0 4 3] | 0.40 | [6 5 0 0] | [0 0 4 3] | (a) |
| (f) | 1.00 | [6 5 4 0] | [0 4 3 2] | 1.00 | [6 5 4 0] | [0 4 3 2] | (a) |
| (g) | 1.50 | [6 5 4 3] | [6 5 4 3] | 1.50 | [6 5 4 3] | [6 5 4 3] | (a) |
| … | …… | …… | …… | …… | …… | …… | (a) |
| (h) | 2.00 | [0 0 0 0] | [0 0 0 0] | 2.00 | [0 0 0 0] | [0 0 0 0] | (a) |
| Situation | or | or | (°) | Curve |
|---|---|---|---|---|
| (a) | 0.50 | 0.50 | 54° | Green |
| (b) | 0.56 | 0.50 | 54° | Red |
| (c) | 0.58 | 0.50 | 54° | Yellow |
| (d) | 0.60 | 0.50 | 54° | Blue |
| (e) | 0.50 | 0.50 | 60° | Black |
| (f) | 0.56 | 0.50 | 60° | Purple |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hao, Z.; Lu, Z.; Li, X.; Zhao, X.; Li, Z.; Liu, X. A Secure Satellite Transmission Technique via Directional Variable Polarization Modulation with MP-WFRFT. Aerospace 2025, 12, 690. https://doi.org/10.3390/aerospace12080690
Hao Z, Lu Z, Li X, Zhao X, Li Z, Liu X. A Secure Satellite Transmission Technique via Directional Variable Polarization Modulation with MP-WFRFT. Aerospace. 2025; 12(8):690. https://doi.org/10.3390/aerospace12080690
Chicago/Turabian StyleHao, Zhiyu, Zukun Lu, Xiangjun Li, Xiaoyu Zhao, Zongnan Li, and Xiaohui Liu. 2025. "A Secure Satellite Transmission Technique via Directional Variable Polarization Modulation with MP-WFRFT" Aerospace 12, no. 8: 690. https://doi.org/10.3390/aerospace12080690
APA StyleHao, Z., Lu, Z., Li, X., Zhao, X., Li, Z., & Liu, X. (2025). A Secure Satellite Transmission Technique via Directional Variable Polarization Modulation with MP-WFRFT. Aerospace, 12(8), 690. https://doi.org/10.3390/aerospace12080690






