Performance Enhancement of IEEE 802.15.6 Using Collision Avoidance Technique
Abstract
:1. Introduction
- Propose a mechanism to avoid homogeneous and heterogeneous collisions by controlling CW and prioritize channel access without collisions.
- Improve the energy efficiency, the throughput, and use of the channel.
- Develop an analytical model for both the IEEE 802.15.6 standard and the proposed mechanism.
- Implement a simulation model to test the effectiveness of the analytical model and compare the analytical results in terms of throughput, energy per bit, and normalized delay.
2. Background and Related Work
- Reduce collision probability by categorizing collisions into collisions among nodes of the same UP and collisions among/between different UPs.
3. Proposed Mechanism
3.1. Heterogeneous Collisions
- Successful transmission: When the backoff counter of a node becomes zero, the node waits some time as specified in equation 4, then it starts transmission. In addition, when the backoff counter of two or more nodes with different UPs becomes zero, the node with a higher UP starts transmission after waiting for its , as shown in Figure 1. In Figure 1, three nodes have UP 6, 5, and 0, along with a coordinator. Initially, the backoff counter of a node belongs to UP 6, 5, and 0 is set to 2, 3, and 3, respectively. After two backoff slots, the UP 6 backoff counter becomes zero. Thus, it starts transmission after waiting for its as given in Equation (4). The of any node is smaller than the backoff slot. After successful transmission by a node of UP 6, all the nodes resumes the process of backoff and decrements its backoff counter. Subsequently, the nodes with UPs 5 and 0 backoff counter becomes zero. Both the nodes must wait for their , but based on equation UPs have lower and start transmission. Node with UP 0 found the channel busy as it has bigger as compared to UP 5, so it does not transmit and choose its backoff counter again based on its current CW.
- Collision: Collision happens between nodes with similar UPs and zero backoff counter. In this mechanism, the collision is prevented by allowing transmission of the high priority node, whereas the low priority node enters the backoff stage.
- Backoff: The backoff counter is decremented if the channel is idle for the duration of a time, as given in Equation (3).
3.2. Homogeneous Collisions
4. Performance Analysis
4.1. Analytical Model of the IEEE 802.15.6
4.1.1. Throughput
4.1.2. Energy Efficiency
- : The amount of energy consumed when the channel is idle. All nodes decrement their backoff counters.
- : The energy consumed by a node with UP k during the successful transmission of a frame.
- : It is the energy consumed when a node overhears (receives) another successful transmission with a coordinator.
- : The amount of energy consumed during collisions and the intended node is involved.
- : The energy consumed during collisions between/among background nodes (unintended).
4.1.3. Normalized Average Delay
4.2. Analytical Model for the Proposed Mechanism
4.2.1. Throughput
4.2.2. Energy Efficiency
5. Results and Discussion
5.1. Simulation Configuration
- Scenario 1: There are three UPs (UP0, UP6, and UP7) and each UP has varying number of nodes, i.e., n = 2, 3, and 4. The value of performance factor .
- Scenario 2: There are 8 UP nodes and each UP has a single node and .
- Scenario 3: There are 8 UP nodes and each UP has a single node; however, we vary the performance factor from 1 to 8.
5.2. Analysis Validation
5.3. Performance Comparison
5.3.1. Throughput
5.3.2. Energy Efficiency
5.3.3. Normalized Average Delay
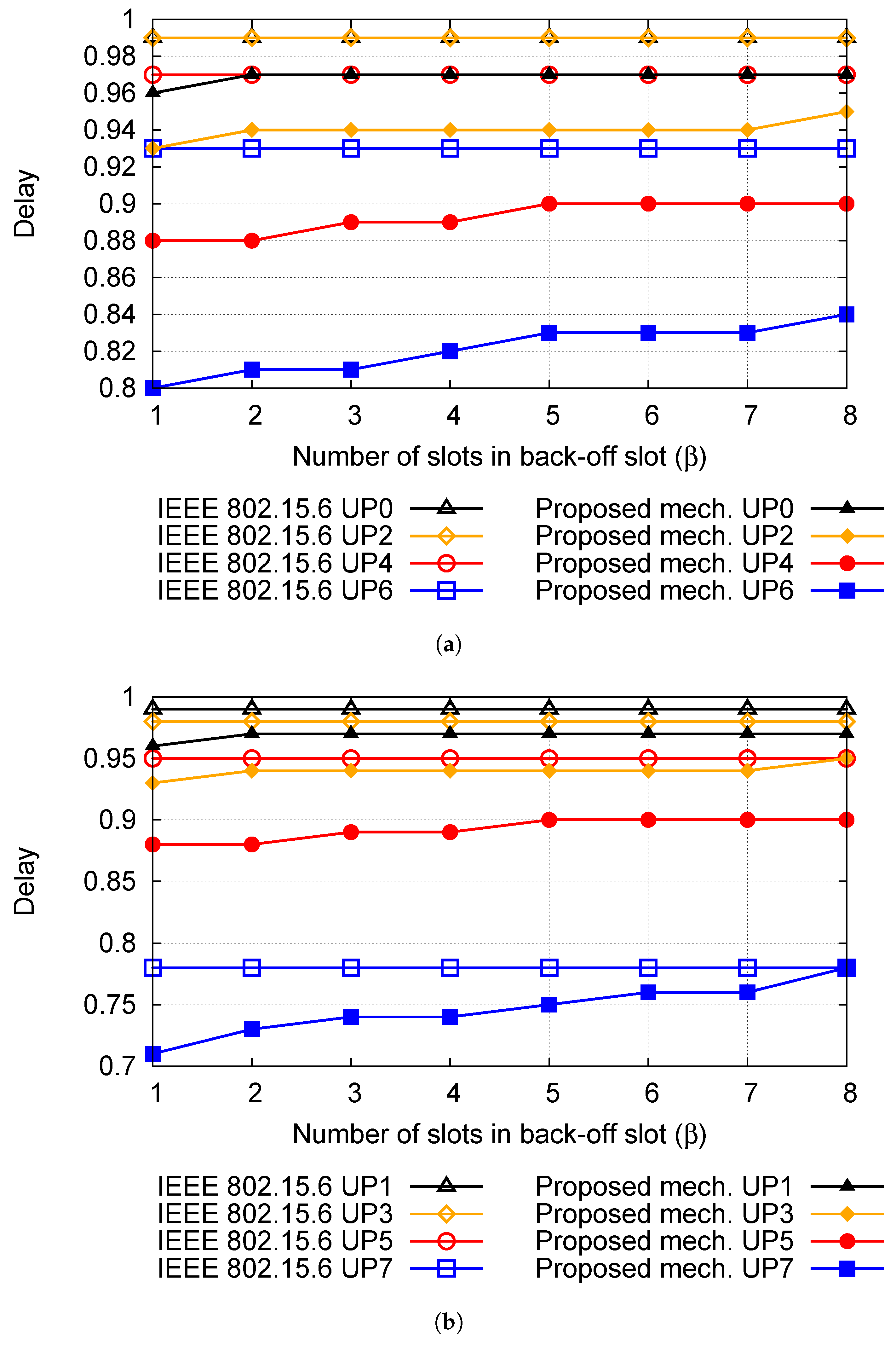
5.4. Effects of on the Performance
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ray, P.P. A survey on Internet of Things architectures. J. King Saud Univ. Comput. Inf. Sci. 2016, 30, 291–319. [Google Scholar] [CrossRef]
- Lee, S.K.; Bae, M.; Kim, H. Future of IoT networks: A survey. Appl. Sci. 2017, 7, 1072. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Alwan, A. Global Status Report on Noncommunicable Diseases 2010; World Health Organization: Geneva, Switzerland, 2011. [Google Scholar]
- Movassaghi, S.; Abolhasan, M.; Lipman, J.; Smith, D.; Jamalipour, A. Wireless body area networks: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 1658–1686. [Google Scholar] [CrossRef]
- Association, I.S. IEEE Standard for Local and Metropolitan Area Networks—Part 15.6: Wireless Body Area Networks. IEEE Stand. Inf. Technol. 2012, 802, 1–271. Available online: https://ieeexplore.ieee.org/document/6161600/ (accessed on 24 August 2018).
- Rashwand, S.; Mišić, J.; Khazaei, H. IEEE 802.15.6 under saturation: Some problems to be expected. J. Commun. Netw. 2011, 13, 142–148. [Google Scholar] [CrossRef]
- Fang, G.; Dutkiewicz, E. BodyMAC: Energy efficient TDMA-based MAC protocol for wireless body area networks. In Proceedings of the 2009 9th International Symposium on Communications and Information Technology, Icheon, Korea, 28–30 September 2009; pp. 1455–1459. [Google Scholar]
- Khan, P.; Ullah, N.; Alam, M.N.; Kwak, K.S. Performance analysis of WBAN MAC protocol under different access periods. Int. J. Distrib. Sens. Netw. 2015, 11, 102052. [Google Scholar] [CrossRef]
- Ullah, S.; Hassan, M.M.; Hossain, M.S.; Alelaiwi, A. Performance Evaluation of RTS/CTS Scheme in Beacon-Enabled IEEE 802.15.6 MAC Protocol for Wireless Body Area Networks. Sensors 2020, 20, 2368. [Google Scholar] [CrossRef]
- Ullah, S.; Mohaisen, M.; Alnuem, M.A. A review of IEEE 802.15.6 MAC, PHY, and security specifications. Int. J. Distrib. Sens. Netw. 2013, 9, 950704. [Google Scholar] [CrossRef]
- Marinkovic, S.; Spagnol, C.; Popovici, E. Energy-efficient TDMA-based MAC protocol for wireless body area networks. In Proceedings of the 2009 IEEE Third International Conference on Sensor Technologies and Applications, Athens, Greece, 18–23 June 2009; pp. 604–609. [Google Scholar]
- Goyal, R.; Bhadauria, H.; Patel, R.; Prasad, D. TDMA based delay sensitive and energy efficient protocol for WBAN. J. Eng. Sci. Technol. 2017, 12, 1067–1080. [Google Scholar]
- Ullah, F.; Abdullah, A.H.; Kaiwartya, O.; Kumar, S.; Arshad, M.M. Medium Access Control (MAC) for Wireless Body Area Network (WBAN): Superframe structure, multiple access technique, taxonomy, and challenges. Human-Centric Comput. Inf. Sci. 2017, 7, 34. [Google Scholar] [CrossRef] [Green Version]
- Wang, R.; Wang, H.; Roman, H.E.; Wang, Y.; Xu, D. A cooperative medium access control protocol for mobile clusters in wireless body area networks. In Proceedings of the 2013 First International Symposium on Future Information and Communication Technologies for Ubiquitous HealthCare (Ubi-HealthTech), Jinhua, China, 1–3 July 2013; pp. 1–4. [Google Scholar]
- Shakir, M.; Rehman, O.U.; Rahim, M.; Alrajeh, N.; Khan, Z.A.; Khan, M.A.; Niaz, I.A.; Javaid, N. Performance Optimization of Priority Assisted CSMA/CA Mechanism of 802.15.6 under Saturation Regime. Sensors 2016, 16, 1421. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Moulik, S.; Misra, S.; Chakraborty, C.; Obaidat, M.S. Prioritized payload tuning mechanism for wireless body area network-based healthcare systems. In Proceedings of the 2014 IEEE Global Communications Conference (GLOBECOM), Austin, TX, USA, 8–12 December 2014; pp. 2393–2398. [Google Scholar]
- Jacob, A.K.; Jacob, L. Energy efficient MAC for QoS traffic in wireless body area network. Int. J. Distrib. Sens. Netw. 2015, 11, 404182. [Google Scholar] [CrossRef] [Green Version]
- Zhou, J.; Guo, A.; T Nguyen, H.; Su, S. Intelligent management of multiple access schemes in wireless body area network. J. Netw. 2015, 10, 108–116. [Google Scholar] [CrossRef] [Green Version]
- Khan, P.; Ullah, N.; Ali, F.; Ullah, S.; Hong, Y.S.; Lee, K.Y.; Kim, H. Performance analysis of different backoff algorithms for WBAN-based emerging sensor networks. Sensors 2017, 17, 492. [Google Scholar] [CrossRef] [Green Version]
- Manna, T.; Misra, I.S. Implementation of energy efficient WBAN using IEEE 802.15.6 scheduled access MAC for e-healthcare. In Proceedings of the 2018 IEEE 10th International Conference on Communication Systems & Networks (COMSNETS), Bengaluru, India, 3–7 January 2018; pp. 267–274. [Google Scholar]
- Manna, T.; Misra, I.S. Performance analysis of scheduled access mode of the IEEE 802.15.6 MAC protocol under non-ideal channel conditions. IEEE Trans. Mob. Comput. 2019, 19, 935–953. [Google Scholar] [CrossRef]
- Sultana, N.; Huq, F.; Razzaque, M.A.; Rahman, M.M. Prioritized IEEE 802.15.6 MAC Protocol for Wireless Body Area Network. In Proceedings of the IEEE 2019 International Conference on Sustainable Technologies for Industry 4.0 (STI), Dhaka, Bangladesh, 24–25 December 2019; pp. 1–5. [Google Scholar]
- Saboor, A.; Ahmad, R.; Ahmed, W.; Kiani, A.K.; Alam, M.M.; Kuusik, A.; Le Moullec, Y. Dynamic Slot Allocation using Non Overlapping Backoff Algorithm in IEEE 802.15.6 WBAN. IEEE Sens. J. 2020. [Google Scholar] [CrossRef]
- Benmansour, T.; Ahmed, T.; Moussaoui, S.; Doukha, Z. Performance analyses of the IEEE 802.15.6 wireless body area network with heterogeneous traffic. J. Netw. Comput. Appl. 2020, 163, 102651. [Google Scholar] [CrossRef]
- Kim, B.S.; Sung, T.E.; Kim, K.I. An NS-3 Implementation and Experimental Performance Analysis of IEEE 802.15.6 Standard under Different Deployment Scenarios. Int. J. Environ. Res. Public Health 2020, 17, 4007. [Google Scholar] [CrossRef]
- Calì, F.; Conti, M.; Gregori, E. Dynamic tuning of the IEEE 802.11 protocol to achieve a theoretical throughput limit. IEEE/ACM Trans. Netw. 2000, 8, 785–799. [Google Scholar] [CrossRef] [Green Version]
- Syed, I.; Shin, S.H.; Roh, B.H.; Adnan, M. Performance Improvement of QoS-Enabled WLANs Using Adaptive Contention Window Backoff Algorithm. IEEE Syst. J. 2017, 12, 3260–3270. [Google Scholar] [CrossRef]
- Jung, B.H.; Akbar, R.U.; Sung, D.K. Throughput, energy consumption, and energy efficiency of IEEE 802.15.6 body area network (BAN) MAC protocol. In Proceedings of the 2012 IEEE 23rd International Symposium on Personal Indoor and Mobile Radio Communications (PIMRC), Sydney, NSW, Australia, 9–12 September 2012; pp. 584–589. [Google Scholar]
- Adnan, M.; Park, E.C. Hybrid control of contention window and frame aggregation for performance enhancement in multirate WLANs. Mob. Inf. Syst. 2015, 2015, 383081. [Google Scholar] [CrossRef]
- Adnan, M.; Park, E.C. Improving Energy Efficiency in Idle Listening of IEEE 802.11 WLANs. Mob. Inf. Syst. 2016, 2016, 6520631. [Google Scholar] [CrossRef]










| Traffic Type | User Priority | ||
|---|---|---|---|
| Background | 0 | 16 | 64 |
| Best effort | 1 | 16 | 32 |
| Excellent effort | 2 | 8 | 32 |
| Video | 3 | 8 | 16 |
| Voice | 4 | 4 | 16 |
| Network Control or medical data | 5 | 4 | 8 |
| High priority medical data | 6 | 2 | 8 |
| Emergency or medical implant event report | 7 | 1 | 4 |
| Parameters | Values | Parameter | Values |
|---|---|---|---|
| Payload size () | 100 bytes | Data Rate | 151.8 kbps |
| 0.0069 s | 0.0064 s | ||
| 267 W | 414 W | ||
| 393 W | 75 s | ||
| () | 252 s | () | 40 |
| Slot time () | 292 s |
| IEEE 802.15.6 MAC | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Throughput (Kbits/s) | Energy Efficiency ( J/bit) | Delay (Fraction) | ||||||||
| No. of nodes | n = 2 | n = 3 | n = 4 | n = 2 | n = 3 | n = 4 | n = 2 | n = 3 | n = 4 | |
| UP 0 | Simulation | 2.532 | 1.370 | 0.856 | 0.155 | 0.287 | 0.459 | 0.978 | 0.988 | 0.992 |
| Analysis | 2.502 | 1.393 | 0.926 | 0.138 | 0.267 | 0.412 | 0.978 | 0.988 | 0.992 | |
| 0.012 | 0.017 | 0.082 | 0.109 | 0.070 | 0.103 | 0.001 | 0.000 | 0.000 | ||
| UP 6 | Simulation | 10.207 | 5.461 | 3.382 | 0.039 | 0.073 | 0.117 | 0.910 | 0.952 | 0.970 |
| Analysis | 10.143 | 5.588 | 3.674 | 0.037 | 0.070 | 0.107 | 0.913 | 0.952 | 0.968 | |
| 0.006 | 0.023 | 0.086 | 0.047 | 0.040 | 0.084 | 0.002 | 0.000 | 0.002 | ||
| UP 7 | Simulation | 20.381 | 10.917 | 6.653 | 0.020 | 0.037 | 0.060 | 0.822 | 0.905 | 0.941 |
| Analysis | 19.845 | 11.000 | 7.184 | 0.021 | 0.037 | 0.057 | 0.829 | 0.905 | 0.938 | |
| 0.026 | 0.008 | 0.080 | 0.061 | 0.025 | 0.046 | 0.008 | 0.000 | 0.004 | ||
| Proposed Mechanism | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Throughput (Kbits/s) | Energy Efficiency ( J/bit) | Delay (Fraction) | ||||||||
| No. of nodes | n = 2 | n = 3 | n = 4 | n = 2 | n = 3 | n = 4 | n = 2 | n = 3 | n = 4 | |
| UP 0 | Simulation | 2.025 | 1.350 | 1.000 | 0.193 | 0.288 | 0.388 | 0.983 | 0.988 | 0.991 |
| Analysis | 2.302 | 1.266 | 0.882 | 0.198 | 0.302 | 0.406 | 0.980 | 0.989 | 0.992 | |
| 0.137 | 0.062 | 0.117 | 0.030 | 0.048 | 0.048 | 0.002 | 0.001 | 0.001 | ||
| UP 6 | Simulation | 9.179 | 5.782 | 4.105 | 0.043 | 0.067 | 0.095 | 0.921 | 0.950 | 0.965 |
| Analysis | 9.344 | 4.889 | 3.256 | 0.040 | 0.062 | 0.085 | 0.919 | 0.958 | 0.972 | |
| 0.018 | 0.154 | 0.207 | 0.061 | 0.082 | 0.099 | 0.001 | 0.008 | 0.008 | ||
| UP 7 | Simulation | 33.927 | 20.003 | 13.866 | 0.012 | 0.020 | 0.028 | 0.707 | 0.827 | 0.880 |
| Analysis | 33.136 | 18.856 | 13.017 | 0.014 | 0.021 | 0.029 | 0.714 | 0.837 | 0.888 | |
| 0.023 | 0.057 | 0.061 | 0.209 | 0.082 | 0.026 | 0.011 | 0.012 | 0.009 | ||
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Adnan, M.; Sallabi, F.; Shuaib, K.; Abdul-Hafez, M. Performance Enhancement of IEEE 802.15.6 Using Collision Avoidance Technique. J. Sens. Actuator Netw. 2020, 9, 33. https://doi.org/10.3390/jsan9030033
Adnan M, Sallabi F, Shuaib K, Abdul-Hafez M. Performance Enhancement of IEEE 802.15.6 Using Collision Avoidance Technique. Journal of Sensor and Actuator Networks. 2020; 9(3):33. https://doi.org/10.3390/jsan9030033
Chicago/Turabian StyleAdnan, Muhammad, Farag Sallabi, Khaled Shuaib, and Mohammed Abdul-Hafez. 2020. "Performance Enhancement of IEEE 802.15.6 Using Collision Avoidance Technique" Journal of Sensor and Actuator Networks 9, no. 3: 33. https://doi.org/10.3390/jsan9030033
APA StyleAdnan, M., Sallabi, F., Shuaib, K., & Abdul-Hafez, M. (2020). Performance Enhancement of IEEE 802.15.6 Using Collision Avoidance Technique. Journal of Sensor and Actuator Networks, 9(3), 33. https://doi.org/10.3390/jsan9030033








