1. Introduction
Since the introduction of the first generation of wireless technology, the telecommunications industry has grown at an exponential rate. The industry’s growth can be attributed to an increase in customer demand for network services. Users requesting network services have a wide range of needs, including streaming videos and audio, sending and receiving multimedia files, and making online transactions. These services necessitate network providers providing high levels of QoS, while resourcefully consuming network resources.
In this regard, 5G networks use different kinds of technologies and Network Slicing to accommodate the varying needs of users. Network slicing is the rational division of a physical network structure into multiple autonomous virtual networks, each of which is designed to meet the needs of specific users. The use of radio resources is improved through network slicing, which ensures that only the resources required are readily available. Network slicing ensures that the networks make optimum use of network resources. In order to deliver acceptable QoS, mobility management is a major difficulty in 5G networks where continuous connectivity, smooth at cell borders, is anticipated.
The capacity to retain a link when a call shifts from one to another is known as mobility management. When the user moves from one region to another while a call is in progress, the network’s responsibility is to keep the call active, while shifting it from one to another cell. The process of transferring a call to a cell that supports a similar network is known as horizontal handoff, whereas the process of transferring a call to a cell that supports a different network is known as vertical handover. In 5G, calls can be reassigned to slices that support similar use cases in a procedure known as intra-slice handover, or to slices that support dissimilar use cases in a procedure known as inter-slice handover.
The 5G networks incorporate well-organized algorithms to guarantee that fewer calls are rejected or missed around handoffs and that the numeral of handoffs executed is reduced in order to provide smooth connectivity during a handover. For the purpose of giving significance to handoff calls and sustaining excellent QoS, the vertical handover algorithm employs distinct bandwidth reservation methods.
The origins of mobile communication can be traced back to Guglielmo Marconi’s pioneering effort in long-distance radio transmission. Since Guglielmo’s time, the technology behind mobile communication has advanced dramatically. The number of subscribers and mobile technologies has seen the most significant developments in wireless technologies [
1]. The following 2G networks were built on digital technologies such as Time Division Multiple Access. Then, 3G networks offered high data rates and multimedia features. After that, 4G network combined 3G and secure internet to enable wireless mobile internet.
The main goal of 5G networks is to provide high bandwidth, low latency, and always-on connectivity. The increased number of devices requesting services from wireless networks resulted in a rise in the number of wireless network research studies conducted in academia.
Wireless technology has progressed through multiple generations and continues to do so. The term “generation” refers to how the system evolves in terms of pace, technology, and frequency. Each generation is defined by its own set of capabilities, skills, and characteristics that set it apart from the one before it. The initial generation of wireless technology was known as 1G. Frequency reuse was the key technique underpinning 1G, and it was solely castoff voice conversations [
2].
Falowo et al. offered a JCAC algorithm. wherein call admission circumstances are made depending on the choices of the user [
3]. The proposed method was tested in scenarios where users paid the minimum for their favorite services. The method was simulated using a Markov Chain to see how effective it was in lowering service costs, and the results showed that the technique could reduce service costs significantly.
Chen et al. [
4] offered a Markov chain model and a sensitivity analysis-based, threshold-based call admission control system. The sensitivity evaluation is used to bind the number of recompilations that the algorithm performs, and the Markov model is utilized to find the best policy. The approach outperformed the guarded channel and complete sharing algorithms when tested in event-driven systems.
Alfoudi et al. presented modular mobility management, in which every slice has a unique module that levers its mobility needs and implements the slice mobility management policies [
5]. The suggested method is based on a joint abstraction that allows the slices to end up sharing resources. Every user is given a slice ID to help with continuous connectivity and when the user is transferred to another RAN, the slice ID is used to identify which slice provides the greatest service. User satisfaction is great and resource use is efficient.
Falowo et al. [
6] suggested an AJCAC system that can be utilized to improve system deployment, reduce call blocking and dropping probabilities and ensure that all allowed calls have their QoS needs met. The method was simulated, and the results were compared to those of a non-adaptive JCAC, revealing a 20% increase in system utilization.
Lee et al. used a distributed reinforcement learning approach in [
7], which allows the equipment to acquire the policies for optimal multi-connectivity configuration and choose the best RAT. The authors suggest a Q-learning-based method because of its capacity to learn the appropriate policy without prior knowledge of its surroundings. When implemented with learning, reinforcement learning algorithms take into account immediate costs, as well as future expenses. The algorithm was designed to find the best policy that reduces total cost.
The level of reference signal received power (RSRP) is monitored by users in reinforcement learning, and the strongest base station with the highest power is chosen. Simulations are used to assess the algorithm’s performance, which is then compared to that of a lone connection RAT selection method and a dual-link RAT selection algorithm [
7]. The effects demonstrated that the suggested reinforcement learning algorithm outperformed the single and dual connectivity algorithms, in terms of reliability and QoS. However, despite its benefits, the program’s most significant disadvantage was its difficult implementation.
Yajnanarayana et al. presented a reinforcement learning-based handover approach [
8]. The system employs a centralized reinforcement learning agent that handles network capacities from the user equipment and uses the data to determine the best handover choice in order to maximize lasting utility. The proposed scheme was assessed and related to conventional handover algorithms, with the findings indicating a 20 percent rise in the efficiency of creating the correct handover decision.
2. The 5G Networks
The 5G wireless network is the most recent and is an all-IP network that is expected to serve a variety of industries, including defense organizations, and medical and manufacturing industries [
9]. It is envisaged that 5G satisfies user QoS necessities in various applications, providing broad coverage so that users have a seamless connection, even at cell borders [
10]. The 5G system uses the network slicing method, which allows service providers to virtualize networks on a common infrastructure to freely deploy their services.
2.1. Network Slicing
The 5G network supports a wide range of use cases and offers tailored services among users to meet a variety of QoS criteria. In the context of 5G networks, network slicing is defined as a procedure in which network resources are packed and allotted in an isolated manner to distinct users with different requirements [
11]. A slice is a set of resources bundled to suit certain user needs in terms of the slice’s quality of service. The purpose of network slicing is to maximize resource deployment by only supplying resources on an on-demand basis.
The promoting feature of network slicing is network resource virtualization, which allows different service providers to share physical infrastructure in a versatile and dynamic way, permitting them to optimally use network resources. Since virtual networking is part of the Software Defined Networks, which intends to move present networks to a software-based model [
12], network slicing is expected to be more efficient. The 5G networks include specific slices designed for the network’s primary use cases, such as eMBB, uRLLC and mMTC. To provide users with the finest QoS and security, the slices are segregated from one another.
2.2. Use Cases of 5G Network
The ITU and 5GPPP have divided 5G network use cases into three major areas based on the demands of each use case. The use cases are divided into two categories: eMBB and mMTC. Each use case has its own set of needs that are unique to it.
2.2.1. Ultra-Reliable Low Latency Communication
The uRLLC slice is customized for mission-critical applications, such as those that demand small latency, high dependability, and security. Mission-critical applications demand a constant flow of information and are less patient with delays, the optimal latency is less than 1ms, and transmission rates are up to 10 Gbps. Telemedicine and self-driving cars are two examples of applications that can benefit from the uRLLC slice.
2.2.2. Enhanced Mobile Broadband
The eMBB slice is intended to address the shortcomings of preceding wireless network generations. The major purpose of eMBB is to improve connection at cell boundaries and deliver quicker, invariable networks with 1 Gbps speed and less than 1 ms latency. Augmented Reality, Virtual Reality and high-quality video streaming are examples of eMBB.
2.2.3. Massive Machine Type Communication
The mMTC slice is built to support a wide range of IoT devices. IoT gadgets are continually connected and their uplink is featured by low throughput and data transfer rate. Since IoT devices have minimal end-to-end latency requirements, the mMTC slice provides latency of less than 10 ms with the least bit rate of 0.5 Mbps. Smart home and smart city devices are examples of applications that can use the mMTC slice.
2.3. The 5G Network Slicing Enabling Technologies
Network slicing makes use of the following to create a communication service where slices may be produced periodically.
Software Defined Network: SDN is described by the physical structure that contains the network control plane and forwarding plane. The separation allows for more flexibility and provides a global perspective of the entire network, as well as means to respond to network changes [
13]. SDN is used to build a virtualized control plane that uses intelligent network management techniques to bridge the gap between network management and service allocation.
Containers: Containers are built on the concept of OS-level virtualization and are used instead of hypervisor-based virtual machines [
13]. It runs on the operating system and allows for greater application compactness. Containers include Dockers, Linux-Vserver, and OpenVZ. VMs and Containers are used in 5G networks to operate VNFs that are connected together, creating a 5G network slice.
Network Function Virtualization (NFV): NFV is a technique that can be cast off to virtualize network operations. Such as Virtual Private Networks and Firewalls on product hardware, breaking the old hardware–software paradigm [
13]. NFV transfers network functions to service providers, who run them on shared infrastructure, making it simple to manage the addition, removal, or update of functions for customers without having to physically visit their location. NFV ensures the performance of Virtual Network Functions (VNFs) operations in the context of 5G, including small latency and failure rate [
13].
Standard Interfaces, such as OpFlex [
14] and OpenFlow [
15], enable direct network control programming. The SDN controller dynamically manages the slices by combining slices that fit the identical context using a set of established rules.
Multiple Edge Computing (MEC): MEC is a technology that allows application and content providers to leverage cloud services at the mobile network’s edge [
16]. By processing data, MEC makes it possible to carry ultra-low latency to mission-critical applications. The deployment of MEC improves network resource utilization by hosting applications at the network edge.
Cloud Computing: Cloud computing is a term that describes the technology that is used to supply computer services via the internet, storage databases, and applications. According to Mujumbi et al. [
17], service providers can be classified as Infrastructure Providers or Service Providers. InPs’ main responsibility is to maintain cloud and lease services depending on usage. SPs are in charge of renting resources from InPs and assigning them to various users.
Network Hypervisors: This abstracts the physical infrastructure into virtual network slices.
Virtual Machines: Virtual Machines enable the virtualization of physical resources, agreeing the user to run a self-governing OS with functions segregated on the host, yet sharing crucial resources.
2.4. Network Slicing Challenges
The idea of network slicing is not without its drawbacks. Numerous difficulties are encountered as a result of the concept being a novel issue in academics and industry, resulting in disagreements over the best method to execute the technology.
Security: As 5G wireless networks deliver services to intelligent devices, new intelligent security procedures are required to protect the services from cyber-attacks, such as Denial of Service. Security can be achieved by network virtualization or through slice management security.
Mobility Management: Mobility management is accustomed to ensuring that ongoing calls are not disrupted while users move at different speeds. For applications that demand minimal latency, seamless and quick handover is a must. To execute seamless handover, it is necessary to maintain track of location and estimate the route most likely to be taken and time spent at a specific RAT. The deployment is difficult since it necessitates coordination among many MVNOs.
Resource Allocation: 5Gs is innovative, so it is challenging to assign network resources. The allocation mechanisms used in 5G are in charge of deciding which resources are instantiated, prioritizing slices, and permitting MVNOs to coordinate.
Isolation: Isolation in network slices refers to confirming that variations in one slice do not affect changes in other slices. As channel quality changes in an unpredictable manner, implementing isolation in network slices is tricky.
3. System Design
The sliced network design enables the establishment of logically distinct networks that share infrastructure, letting slices provide specific use cases. The developed method is based on the formulae and representations used by Falowo in [
18], and the handover decision algorithm is evaluated using a numerical technique, based on the Markov decision process. Our proposed scheme makes use of the network module developed in Matlab and Python to calculate the outputs and depict the graphs. The Operating System was the following: Windows 10, Processor: Intel
® Core™ i7-1265UL Processor, RAM: 16 GB DDR3, Storage: 500 GB SSD.
3.1. Network Model
Network slicing is a concept that permits many self-contained networks to be built on a maximum of a single shared infrastructure. Infrastructure Providers (InPs) are the owners of shared infrastructure and are responsible for supplying resources to tenants. Tenants receiving resources from InPs include Mobile Virtual Network Operators (MVNOs). In sliced networks, resource distribution is accomplished through a tiered approach that encompasses both InPs and MVNOs. They are positioned at distinct stages of the organization and have diverse resource allocation responsibilities. InPs distribute resources to MVNOs, who then distribute the resources to different slices.
A sliced network has the following three separate slices, each with its own set of needs: eMBB, mMTC, and uRLLC. The slices have resources allotted to them for their specialized use cases, but they are not responsible for taking any calls. The CAC algorithm is realized at the MVNO level, which is responsible for taking calls from various users. When a call is accepted to the eMBB slice in one MVNO it is then handed over to the eMBB slice in another MVNO or the uRLLC slices an MVNO.
Assumptions of Network Model
During the implementation of the network model, the following assumptions were made.
In order to maximize radio resource utilization, the MVNO gives all slices equal priority when allocating resources.
Users are prioritized at each slice based on their arrival time.
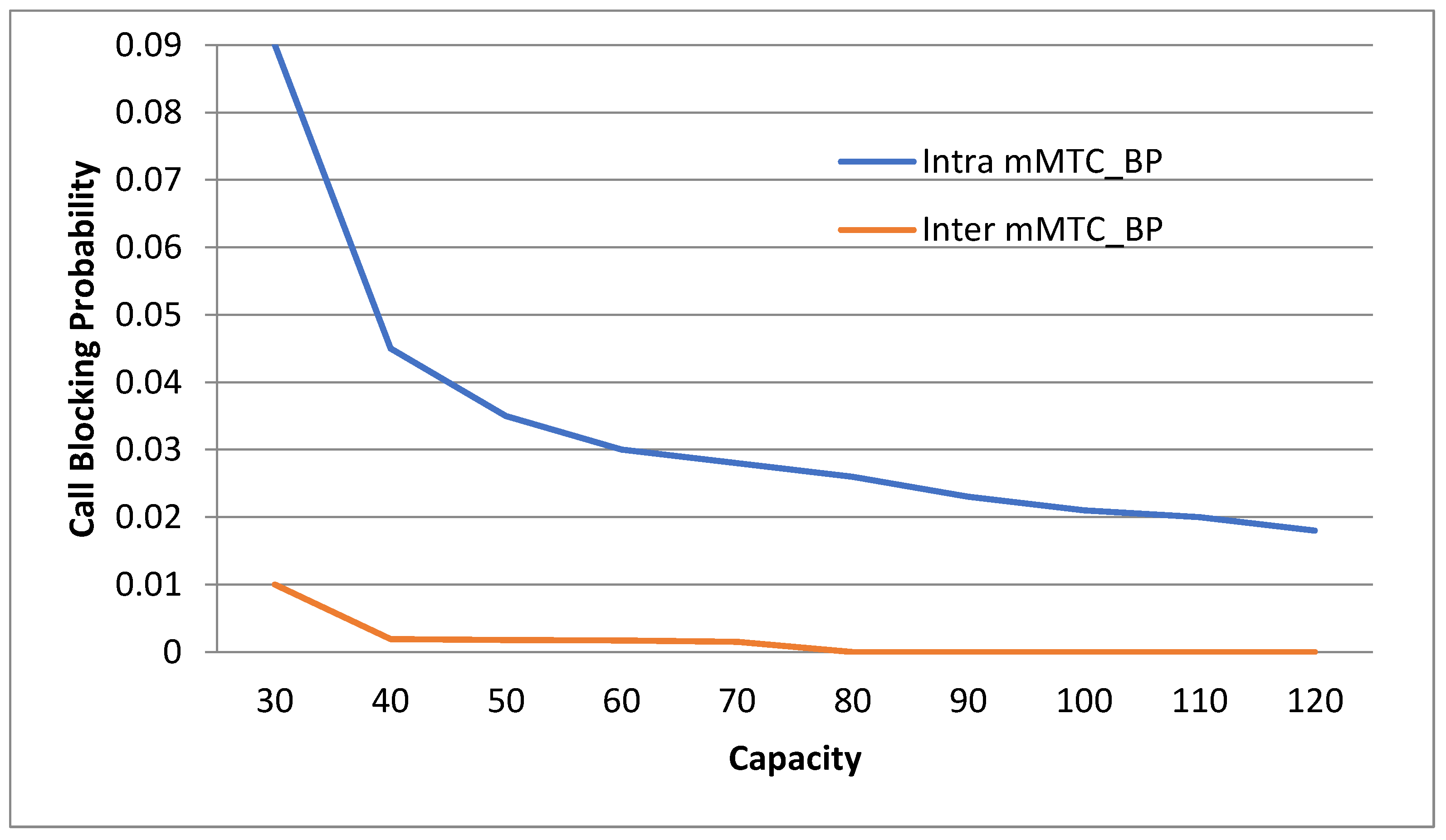
Since its UEs are not mobile, the mMTC slice does not support handoff calls.
In eMBB and uRLLC, handoff calls take precedence over new calls.
Each user has their own set of requirements.
In a slice, users are evenly dispersed.
3.2. Call Admission Control (CAC) Model
The following were the goals of the proposed CAC algorithm for sliced 5G networks:
Imagine an InP that provides the groundwork to a group of MVNOs, where M is the number of MVNOs:
Each MVNO has a total of Y
m slices, which is given by:
with every slice isolated from others in the same network. All call arriving processes are assumed to be Poisson processes.
A use case and capacity are assigned to each slice of the virtual network. The highest number of radio resources that the slice can give is referred to as the slice’s capacity. According to other studies, radio resources are supplied in terms of multiplexing techniques. Nevertheless, the capacity is obtainable in terms of Basic Bandwidth Units (BBUs) for the purposes of this study. A use case is a collection of services with comparable criteria, such as eMBB. The MVNO can take a call requesting services and assign it to a slice based on the call’s requirements. A video streaming device, for example, can issue a service request, and the MVNO admits it to the eMBB slice. The MVNO examines the slice conditions in terms of load during call admission.
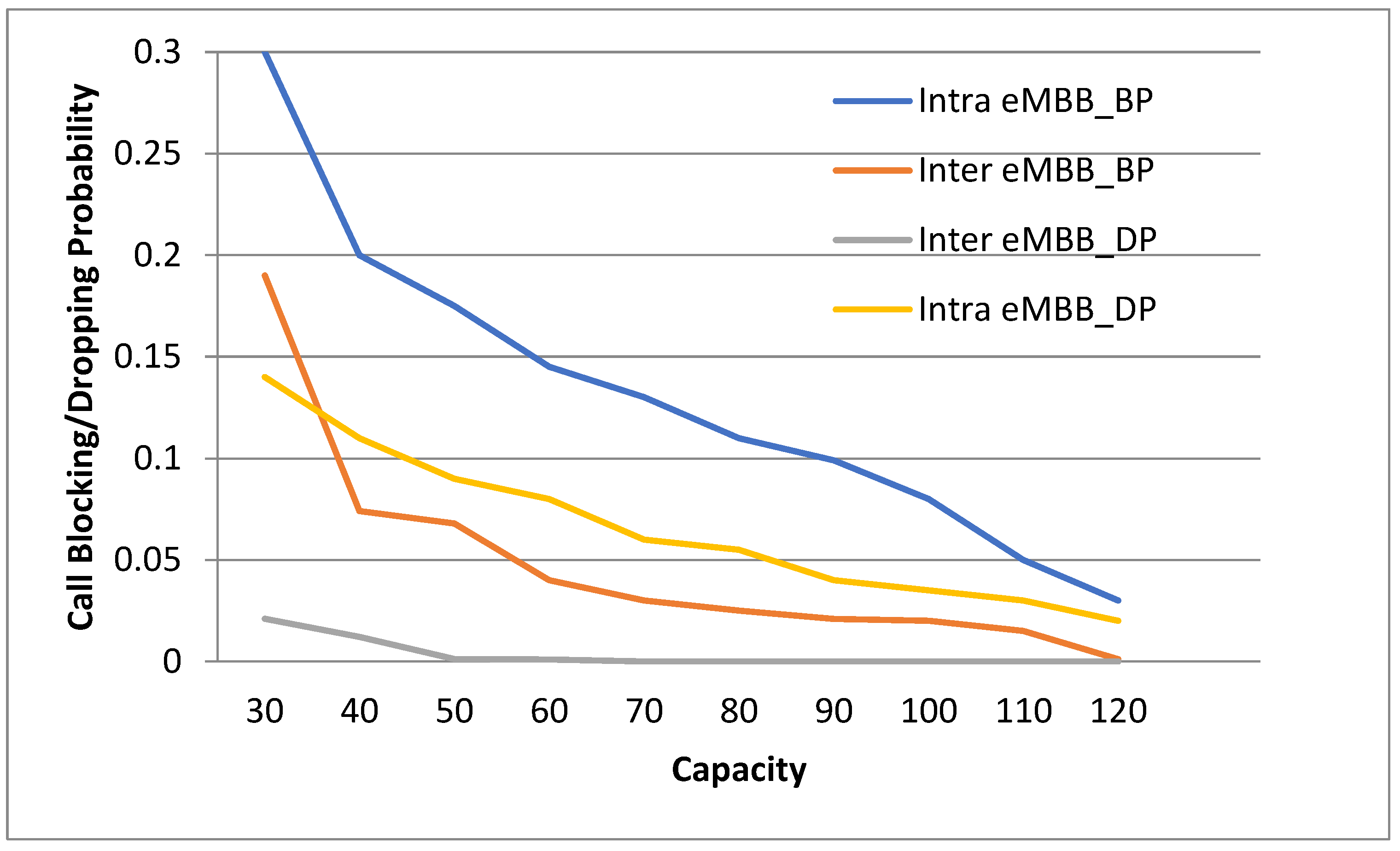
Inter-slice handover occurs when a call is transferred to a slice that supports distinct use cases, such as an eMBB call to an uRLLC slice, while intra-slice handover occurs when a call is transferred to a slice that supports the same use case, such as an mMTC call to an mMTC slice. As the qualifications for the uRLLC slice are stricter, they cannot be permitted any slices. Calls are conditioned for eMBB such that the uRLLC slice can be met; therefore, they can be passed to the uRLLC slice. Calls for the mMTC slice have a wide range of needs that can be met by both the eMBB and uRLLC slices; thus, they can be distributed to either. Calls are permitted to a slice only if the slice has sufficient radio resources to meet the call’s necessities without interfering with other permitted calls; otherwise, the call is forwarded to some other slice, blocked, or dropped.
The slice and use-case considered are shown in
Figure 1. The slices are mentioned as eMBB, mMTC and uRLLC, respectively.
Each slice y
m ∈ Y
m which fits to an MVNO, m, has a capacity signified by B
y, and the total capacity is:
Every slice has a group of users
. The users firmly rely on the slice given by:
Each user w∈ W demands a bandwidth of Bu when accepted to the slice, and the slice distributes a fraction Fy of its overall bandwidth to the subscriber. The likelihood of a subscriber w ∈ W pertaining to a slice y
m ∈ Y
m that belongs to MVNO m is based on the assumption that users are uniformly distributed:
As consumers are less tolerant of dropped handoff calls in slices that help them, handoff calls are given priority over new calls in slices that support them (eMBB and uRLLC).