Case Study on Privacy-Aware Social Media Data Processing in Disaster Management
Abstract
1. Introduction
2. Fundamentals
2.1. Social Media and Disaster Management
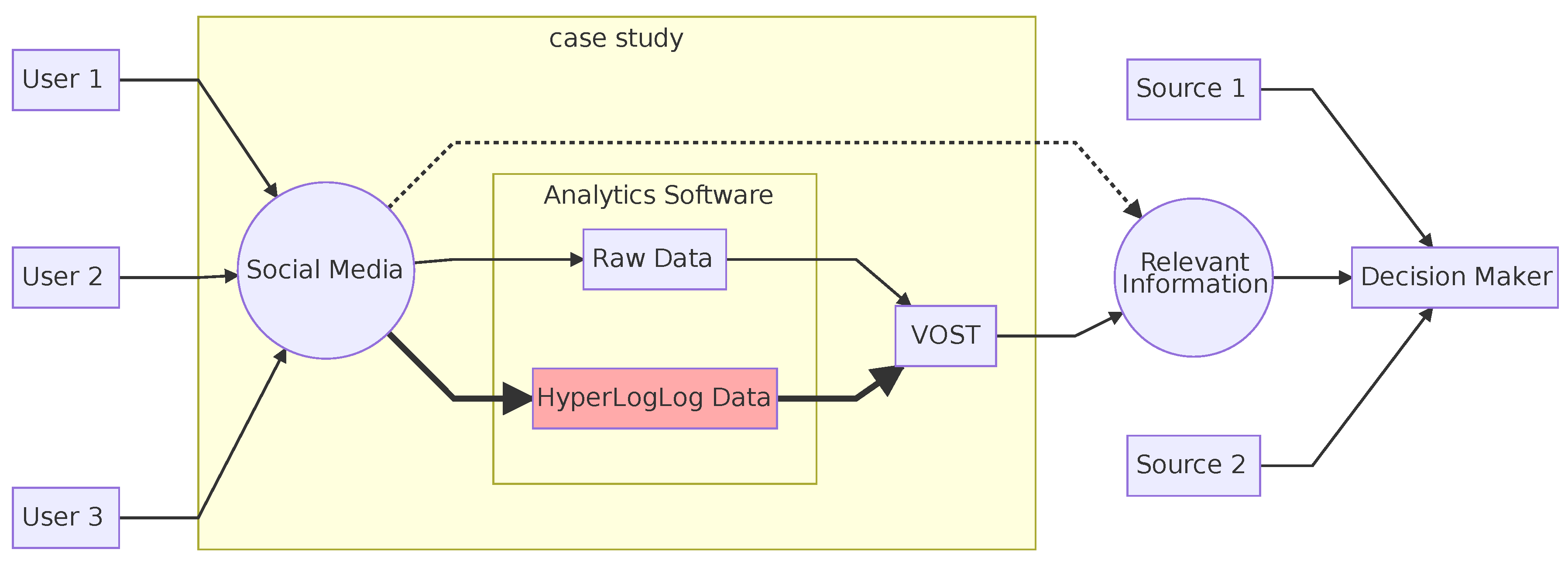
2.2. Virtual Operations Support Teams
- Social media monitoring as well as conducting data processing, filtering and assessment
- Creating and updating spatial analysis of digital maps
- Recognizing and analyzing trends and sentiment in social media
- Identifying rumors and false information
- Verifying and geolocating social media posts
- Crowdsourcing and collaborations with other VOST
- Presentation to the operational staff of the EMAs [31].
2.3. The Privacy Aspect of Data Retention
2.4. Privacy-Aware Storage
3. Methods
3.1. Focus Group Discussion
3.2. Data Acquisition
4. Evaluation
4.1. Findings of the Discussion
4.2. Analysis of the Findings
5. Conclusions and Outlook
Author Contributions
Funding
Conflicts of Interest
References
- Koeze, E.; Popper, N. The Virus Changed the Way We Internet. Available online: https://www.nytimes.com/interactive/2020/04/07/technology/coronavirus-internet-use.html (accessed on 25 November 2020).
- Reuter, C.; Kaufhold, M.-A. Fifteen Years of Social Media in Emergencies: A Retrospective Review and Future Directions for Crisis Informatics. J. Conting. Crisis Manag. 2018, 26, 41–57. [Google Scholar] [CrossRef]
- Kuner, C.; Marelli, M. Social Media. In Handbook on Data Protection in Humanitarian Action; International Committee of the Red Cross: Geneva, Switzerland, 2020; pp. 223–237. [Google Scholar]
- Rouse, M. Data Retention. Available online: https://searchstorage.techtarget.com/definition/data-retention (accessed on 25 November 2020).
- Fiesler, C.; Beard, N.; Keegan, B.C. No robots, spiders, or scrapers: Legal and ethical regulation of data collection methods in social media terms of service. In Proceedings of the International AAAI Conference on Web and Social Media, Atlanta Georgia, GA, USA, 8–11 June 2020; Volume 14, pp. 187–196. [Google Scholar]
- Miller, V. Understanding Digital Culture; SAGE Publications Limited: London, UK, 2020; pp. 145–146. [Google Scholar]
- Dunkel, A.; Löchner, M.; Burghardt, D. Privacy-Aware Visualization of Volunteered Geo-Graphic Information (Vgi) to Analyze Spatial Activity: A Benchmark Implementation. ISPRS Int. J. Geo-Inf. 2020, 9, 607. [Google Scholar] [CrossRef]
- Reuter, C.; Hughes, A.L.; Kaufhold, M.-A. Social Media in Crisis Management: An Evaluation and Analysis of Crisis Informatics Research. Int. J. Hum. Comput. Interact. 2018, 34, 280–294. [Google Scholar] [CrossRef]
- St Denis, L.A.; Hughes, A.L.; Palen, L. Trial by fire: The deployment of trusted digital volunteers in the 2011 shadow lake fire. In Proceedings of the 9th International ISCRAM Conference, Vancouver, BC, Canada, 22–25 April 2012; pp. 1–10. [Google Scholar]
- Castillo, C. Big Crisis Data: Social Media in Disasters and Time-Critical Situations, 1st ed.; Cambridge University; Cambridge University Press: New York, NY, USA, 2016; ISBN 978-1-107-13576-5. [Google Scholar]
- Statista Global Consumer Survey Umfrage in Deutschland zu beliebten Arten von Social Media 2020: Welche Arten von Social Media nutzen Sie regelmäßig? Available online: https://de.statista.com/prognosen/999854/umfrage-in-deutschland-zu-beliebten-arten-von-social-media (accessed on 25 November 2020).
- Bitkom e.V Social-Media-Nutzung Steigt durch Corona stark an. Available online: https://www.bitkom.org/Presse/Presseinformation/Social-Media-Nutzung-steigt-durch-Corona-stark-an (accessed on 25 November 2020).
- Sackmann, S.; Lindner, S.; Gerstmann, S.; Betke, H. Einbindung ungebundener Helfer in die Bewältigung von Schadensereignissen. In Sicherheitskritische Mensch-Computer-Interaktion; Reuter, C., Ed.; Springer: Wiesbaden, Germany, 2018; pp. 529–549. ISBN 978-3-658-19523-6. [Google Scholar]
- Fathi, R.; Rummeny, D.; Fiedrich, F. Organisation von Spontanhelfern am Beispiel des Starkregenereignisses vom 28.07. 2014 in Münster. Notfallvorsorge 2017, 2, 1–8. [Google Scholar]
- Shao, C.; Ciampaglia, G.L.; Varol, O.; Yang, K.-C.; Flammini, A.; Menczer, F. The Spread of Low-Credibility Content by Social Bots. Nat. Commun. 2018, 9, 4787. [Google Scholar] [CrossRef] [PubMed]
- Starbird, K.; Maddock, J.; Orand, M.; Achterman, P.; Mason, R.M. Rumors, False Flags, and Digital Vigilantes: Misinformation on Twitter after the 2013 Boston Marathon Bombing. In iConference 2014 Proceedings; iSchools: Washington, DC, USA, 2014. [Google Scholar]
- Kirchner, J.; Reuter, C. Countering Fake News: A Comparison of Possible Solutions Regarding User Acceptance and Effectiveness. Proc. ACM Hum.-Comput. Interact. 2020, 4, 1–27. [Google Scholar] [CrossRef]
- World Health Organization Novel Coronavirus(2019-nCoV): Situation Report 13. Available online: https://www.who.int/docs/default-source/coronaviruse/situation-reports/20200202-sitrep-13-ncov-v3.pdf (accessed on 25 November 2020).
- Vieweg, S.; Palen, L.; Liu, S.B.; Hughes, A.; Sutton, J. (Eds.) Collective Intelligence in Disaster: Examination of the Phenomenon in the Aftermath of the 2007 Virginia Tech Shooting; University of Colorado: Boulder, CO, USA, 2008. [Google Scholar]
- Imran, M.; Castillo, C.; Lucas, J.; Meier, P.; Vieweg, S. AIDR— Artificial intelligence for disaster response. In Proceedings of the 23rd International Conference on World Wide Web, Seoul, Korea, 11 April 2014; pp. 159–162. [Google Scholar]
- Imran, M.; Castillo, C.; Diaz, F.; Vieweg, S. Processing Social Media Messages in Mass Emergency. ACM Comput. Surv. 2015, 47, 1–38. [Google Scholar] [CrossRef]
- Leysia, P.; Sarah, V.; Jeannette, S.; Sophia, B.; Liu, A.H. Crisis Informatics: Studying Crisis in a Networked World. In Proceedings of the Third International Conference on E-Social Science, Ann Arbor, MI, USA, 4–9 October 2007. [Google Scholar]
- Qadir, J.; Ali, A.; ur Rasool, R.; Zwitter, A.; Sathiaseelan, A.; Crowcroft, J. Crisis Analytics: Big Data-Driven Crisis Response. J. Int. Humanit. Action 2016, 1, 1–21. [Google Scholar] [CrossRef]
- Goodchild, M.F. Citizens as Sensors: The World of Volunteered Geography. GeoJournal 2007, 69, 211–221. [Google Scholar] [CrossRef]
- Goodchild, M.F.; Glennon, J.A. Crowdsourcing Geographic Information for Disaster Response: A Research Frontier. Int. J. Digit. Earth 2010, 3, 231–241. [Google Scholar] [CrossRef]
- Alam, F.; Ofli, F.; Imran, M. Descriptive and Visual Summaries of Disaster Events Using Artificial Intelligence Techniques: Case Studies of Hurricanes Harvey, Irma, and Maria. Behav. Inf. Technol. 2019, 3, 1–31. [Google Scholar] [CrossRef]
- Hughes, A.; Tapia, A. Social Media in Crisis: When Professional Responders Meet Digital Volunteers. J. Homel. Secur. Emerg. Manag. 2015, 12, 203. [Google Scholar] [CrossRef]
- Comes, T.; Vybornova, O.; Van de Walle, B. Bringing structure to the disaster data typhoon: An analysis of decision-makers’ information needs in the response to haiyan. In Proceedings of the AAAI Spring Symposium, Stanford, CA, USA, 23–25 March 2015. [Google Scholar]
- Reuter, C. (Ed.) Sicherheitskritische Mensch-Computer-Interaktion: Interaktive Technologien und soziale Medien im Krisen- und Sicherheitsmanagement; Springer Vieweg: Wiesbaden, Germany, 2018; ISBN 978-3-658-19523-6. [Google Scholar]
- Fathi, R.; Schulte, Y.; Schütte, P.; Tondorf, V.; Fiedrich, F. Lageinformationen Aus Den Sozialen Netzwerken: Virtual Operations Support Teams (Vost) International Im Einsatz. Notfallvorsorge 2018, 49, 1–9. [Google Scholar]
- Fathi, R.; Thom, D.; Koch, S.; Ertl, T.; Fiedrich, F. VOST: A Case Study in Voluntary Digital Participation for Collaborative Emergency Management. Inf. Process. Manag. 2020, 57, 102–174. [Google Scholar] [CrossRef]
- Reuter, C.; Kaufhold, M.-A.; Schmid, S.; Spielhofer, T.; Hahne, A.S. The Impact of Risk Cultures: Citizens’ Perception of Social Media Use in Emergencies Across Europe. Technol. Forecast. Soc. Chang. 2019, 148, 119724. [Google Scholar] [CrossRef]
- Polous, K. Event Cartography: A New Perspective in Mapping. Ph.D. Thesis, Technische Universität München, Munich, Germany, 2016. [Google Scholar]
- Blanchette, J.-F.; Johnson, D.G. Data Retention and the Panoptic Society: The Social Benefits of Forgetfulness. Inf. Soc. 2002, 18, 33–45. [Google Scholar] [CrossRef]
- Leetaru, K. The Era of Precision Mapping of Social Media Is Coming to an End. Available online: https://web.archive.org/web/20191219100123/https://www.forbes.com/sites/kalevleetaru/2019/03/06/the-era-of-precision-mapping-of-social-media-is-coming-to-an-end/ (accessed on 25 November 2020).
- Eberle, E.J. The Right to Information Self-Determination. Utah Law Rev. 2001, 2001, 965. [Google Scholar]
- Kuner, C.; Marelli, M. Data Analytics and Big Data. In Handbook on Data Protection in Humanitarian Action; International Committee of the Red Cross: Geneva, Switzerland, 2020; pp. 92–111. [Google Scholar]
- Samarati, P.; Sweeney, L. Protecting Privacy When Disclosing Information: K-Anonymity and Its Enforcement Through Generalization and Suppression. 1998. Available online: https://epic.org/privacy/reidentification/Samarati_Sweeney_paper.pdf (accessed on 25 November 2020).
- Dwork, C. Differential privacy: A survey of results. In Proceedings of the International Conference on Theory and Applications of Models of Computation, Kitakyushu, Japan, 13–16 April 2008; pp. 1–19. [Google Scholar]
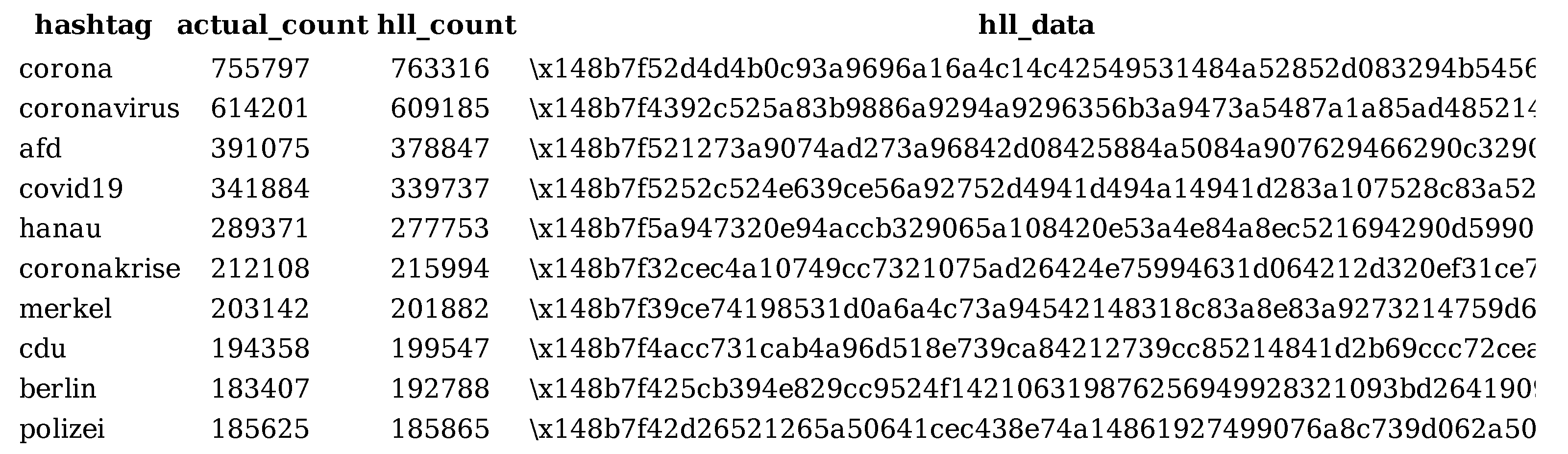
- Singh, A.; Garg, S.; Kaur, R.; Batra, S.; Kumar, N.; Zomaya, A.Y. Probabilistic Data Structures for Big Data Analytics: A Comprehensive Review. Knowl.-Based Syst. 2020, 188, 104987. [Google Scholar] [CrossRef]
- Flajolet, P.; Fusy, É.; Gandouet, O.; Meunier, F. Hyperloglog: The analysis of a near-optimal cardinality estimation algorithm. In Proceedings of the Discrete Mathematics and Theoretical Computer Science, Dijon, France, 7–12 July 2007; pp. 137–156. [Google Scholar]
- Desfontaines, D.; Lochbihler, A.; Basin, D. Cardinality Estimators Do Not Preserve Privacy. Proc. Priv. Enhanc. Technol. 2019, 2019, 26–46. [Google Scholar] [CrossRef]
- Löchner, M.; Dunkel, A.; Burghardt, D. Protecting Privacy Using Hyperloglog to Process Data from Location Based Social Networks. In Proceedings of the Legal Ethical factorS crowdSourced geOgraphic iNformation 2019: 1st International Workshop on Legal and Ethical Issues in Crowdsourced Geographic Information, Zürich, Switzerland, 8–9 October 2019. [Google Scholar]
- Krumpe, F.; Dunkel, A.; Löchner, M. LBSN Structure. Available online: https://pypi.org/project/lbsnstructure/ (accessed on 25 November 2020).
- Prüfer, P.; Rexroth, M. Verfahren zur Evaluation von Survey-Fragen: Ein Überblick; Social Science Open Access Repository: Mannheim, Germany, 1996. [Google Scholar]
- Dunkel, A. Lbsntransform. Available online: https://pypi.org/project/lbsntransform/ (accessed on 25 November 2020).
- Chen, X.; Pival, P.R.; Cirik, A.; Mohajerani, S. Many More Awesome Public Datasets. Available online: https://github.com/awesomedata/awesome-public-datasets (accessed on 25 November 2020).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Löchner, M.; Fathi, R.; Schmid, D.‘.-1.; Dunkel, A.; Burghardt, D.; Fiedrich, F.; Koch, S. Case Study on Privacy-Aware Social Media Data Processing in Disaster Management. ISPRS Int. J. Geo-Inf. 2020, 9, 709. https://doi.org/10.3390/ijgi9120709
Löchner M, Fathi R, Schmid D‘-1, Dunkel A, Burghardt D, Fiedrich F, Koch S. Case Study on Privacy-Aware Social Media Data Processing in Disaster Management. ISPRS International Journal of Geo-Information. 2020; 9(12):709. https://doi.org/10.3390/ijgi9120709
Chicago/Turabian StyleLöchner, Marc, Ramian Fathi, David ‘-1’ Schmid, Alexander Dunkel, Dirk Burghardt, Frank Fiedrich, and Steffen Koch. 2020. "Case Study on Privacy-Aware Social Media Data Processing in Disaster Management" ISPRS International Journal of Geo-Information 9, no. 12: 709. https://doi.org/10.3390/ijgi9120709
APA StyleLöchner, M., Fathi, R., Schmid, D. ‘.-1., Dunkel, A., Burghardt, D., Fiedrich, F., & Koch, S. (2020). Case Study on Privacy-Aware Social Media Data Processing in Disaster Management. ISPRS International Journal of Geo-Information, 9(12), 709. https://doi.org/10.3390/ijgi9120709





