PRIPRO—Privacy Profiles: User Profiling Management for Smart Environments
Abstract
:1. Introduction
- We propose a taxonomy to establish metrics, parameters, and hierarchy criteria for the evolution of users’ profiles in smart environments.
- We present the deployment and assessment of a solution for the evolution of the user profile in smart environments that are based on data privacy.
2. Background
2.1. Smart Environments
2.2. Ubiquitous Computing
2.3. Smartphones, Privacy And Security
2.4. Indoor Positioning
2.5. Privacy Policy
2.6. Privacy Profiles
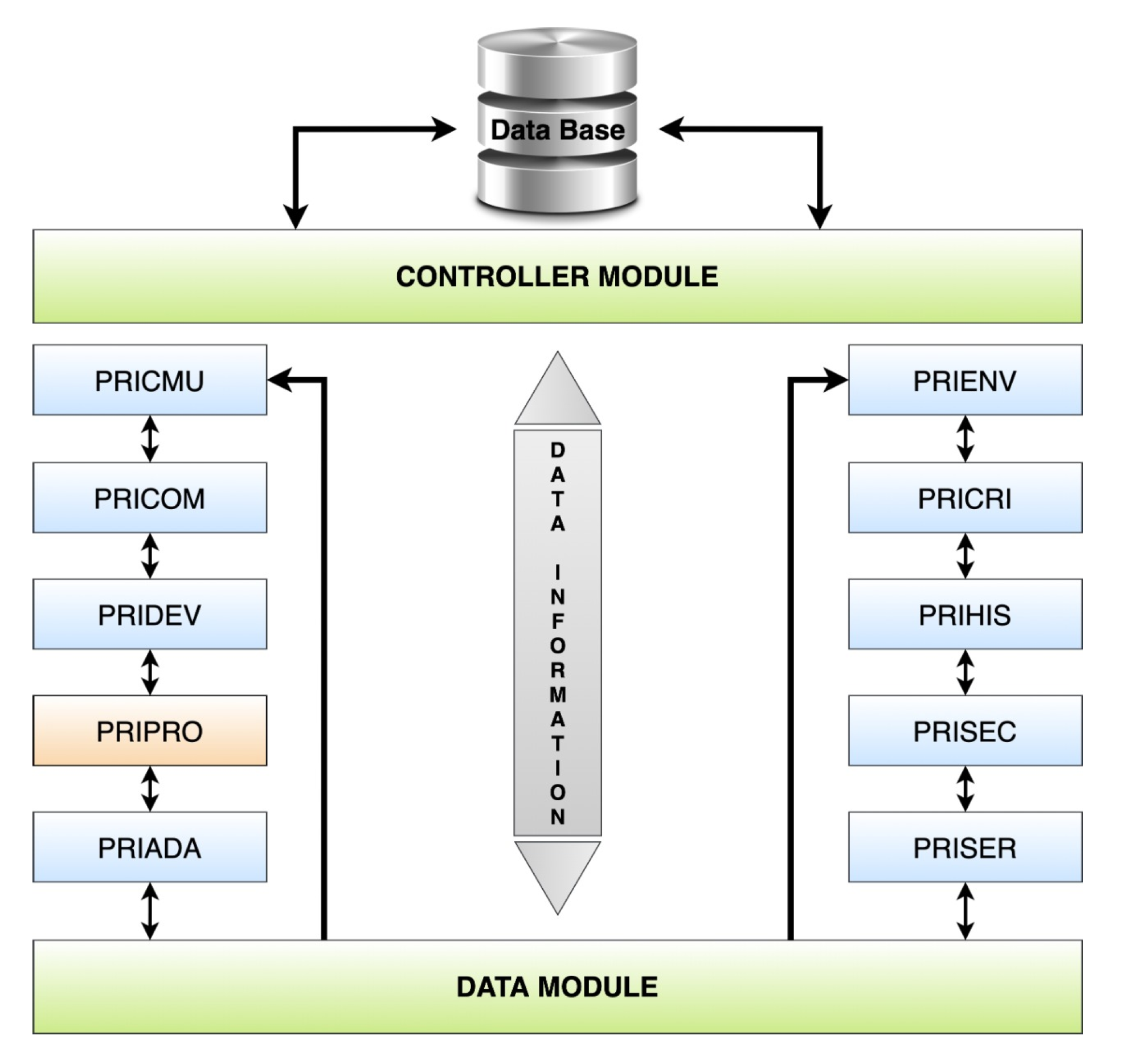
2.7. The UbiPri Middleware
- Data Base: contains all of the information necessary for the control and management of the privacy mechanism in ubiquitous environments.
- Controller module: has the purpose of receiving access requests and carrying out the control of the database directly in the database tables.
- Data module: responsible for processing all variables and parameters from other modules. It also has the function of receiving various data and treating them, generating a single output of information for each processing performed.
- PRICMU: deals with the definitions of characteristics related to the user’s individual preferences, such as temperature, brightness, and authorized shares (information that the user wants to share with other users and with the environment).
- PRICOM: deals with the forms of communication and how these forms are used within the ubiquitous environment.
- PRIDEV: treats data about devices that can be from the environment itself or that can interact with it.
- PRIPRO: performs control transactions that are related to user profile management.
- PRIADA: performs the management and control of adaptation and is responsible for handling information related to the adaptation of software and hardware in the ubiquitous environment.
- PRIENV: makes the registration of attributes that are related to the environment. This information enables the checking and management what makes up the environment,
- PRICRI: has the rules and definitions of criteria for the environment, such as access, use, sharing, location, and other variables, which can be included, changed, modified, or replaced according to the environment’s definitions.
- PRIHIS: stores and handles information related to the user’s history, environment, devices, and other variables that can be added later to obtain contextual information.
- PRISEC: performs security-related controls and management, both for the user and the environment.
- PRISER: does the service management of the environment. It handles information about the availability of services that are used individually in each environment.
3. Related Work
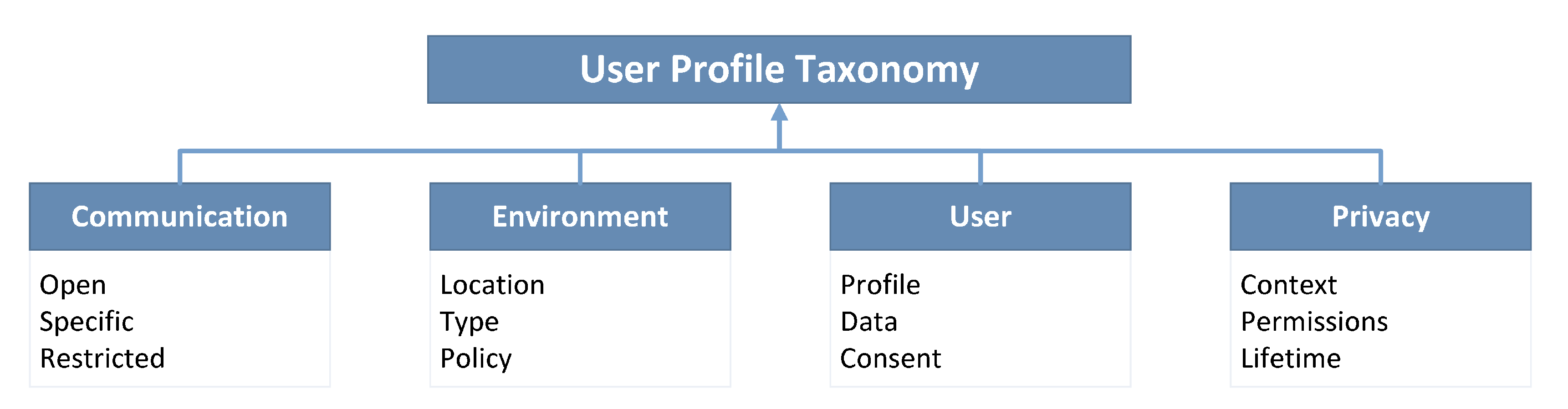
4. A Taxonomy for User’s Profile Management
4.1. Communication
- Open Environments: provide services that can be common to all users. The network technologies used for these environments must allow great mobility and minimal interference, enabling multiple users and devices to be connected at the same time. Some protocols that cover these requirements include Wireless Networks (IEEE 802.11) and Mobile Data Network.
- Specific Environments: the identification of a specific environment requires precision. For this, protocols, such as Bluetooth, NFC (Near Field Communication), and RFID (Radio-Frequency IDentification), can be used.
- Restricted Environment: these environments require user identification and permission locally.
4.2. Environment
4.3. Users
4.4. Privacy
- Context: are the circumstances that accompany a fact or situation. In this case, the user is assigned permissions in an intelligent environment [21].
- Permissions: defines what information or actions the user allows to be accessed or transmitted from his profile.
- Lifetime: duration of the context in which a user is in a ubiquitous environment.
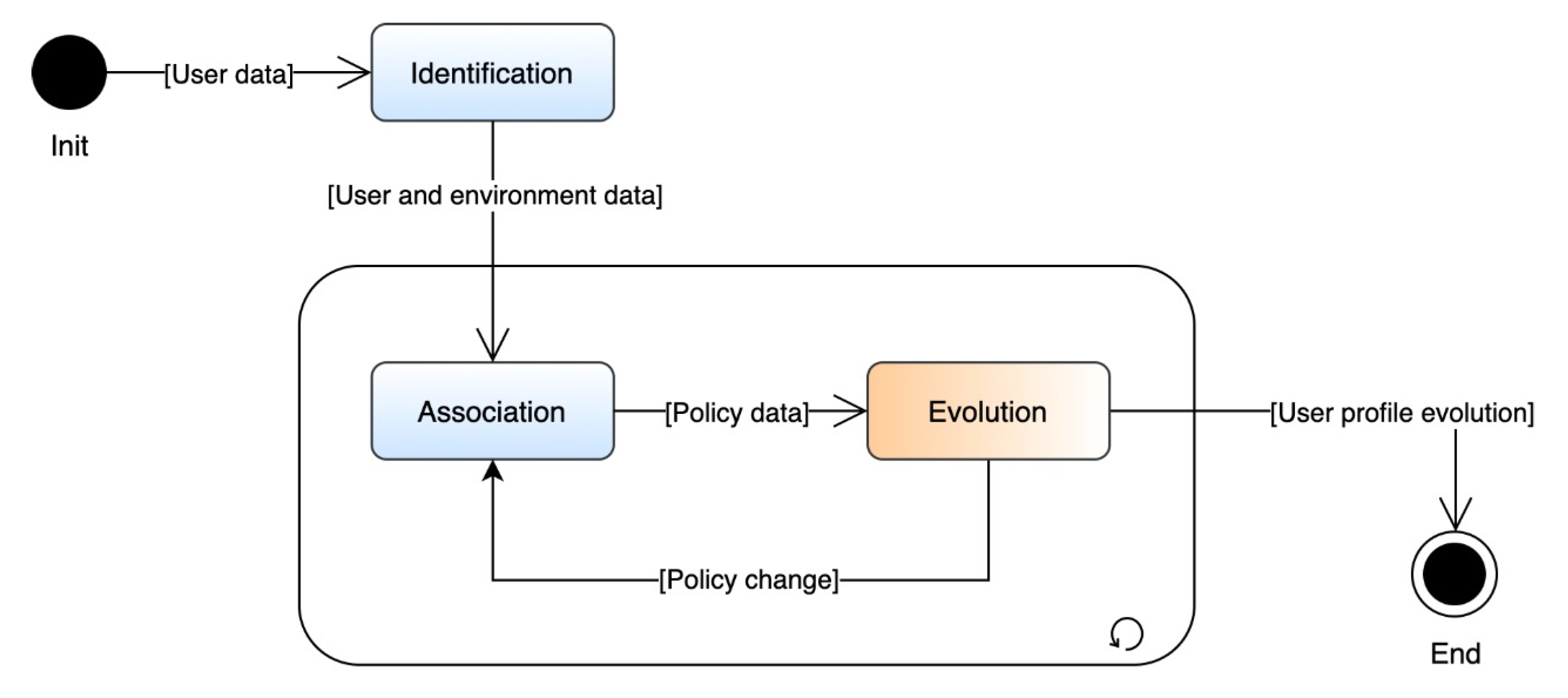
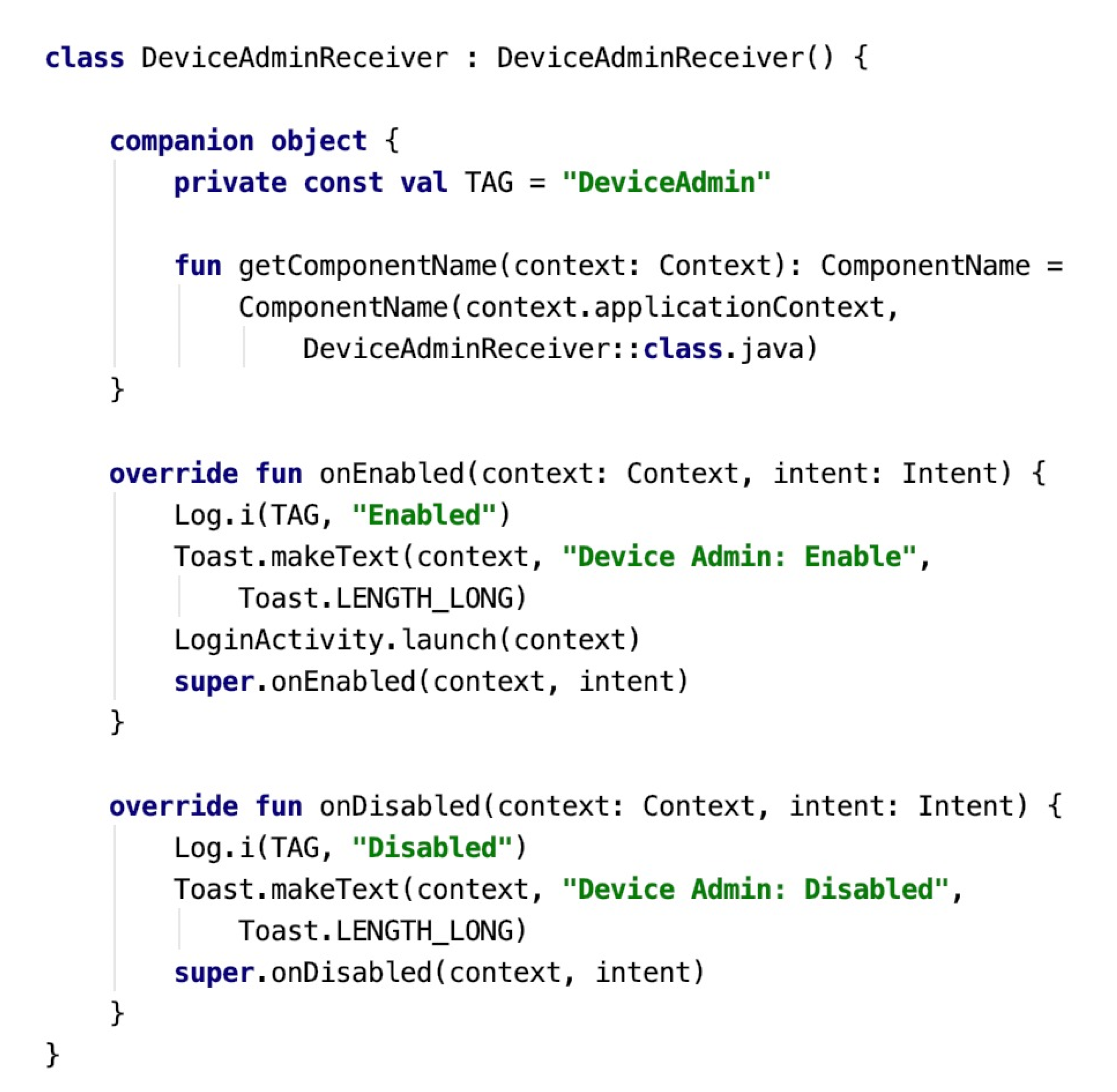
5. Architecure
5.1. Client Application
5.2. Web Server
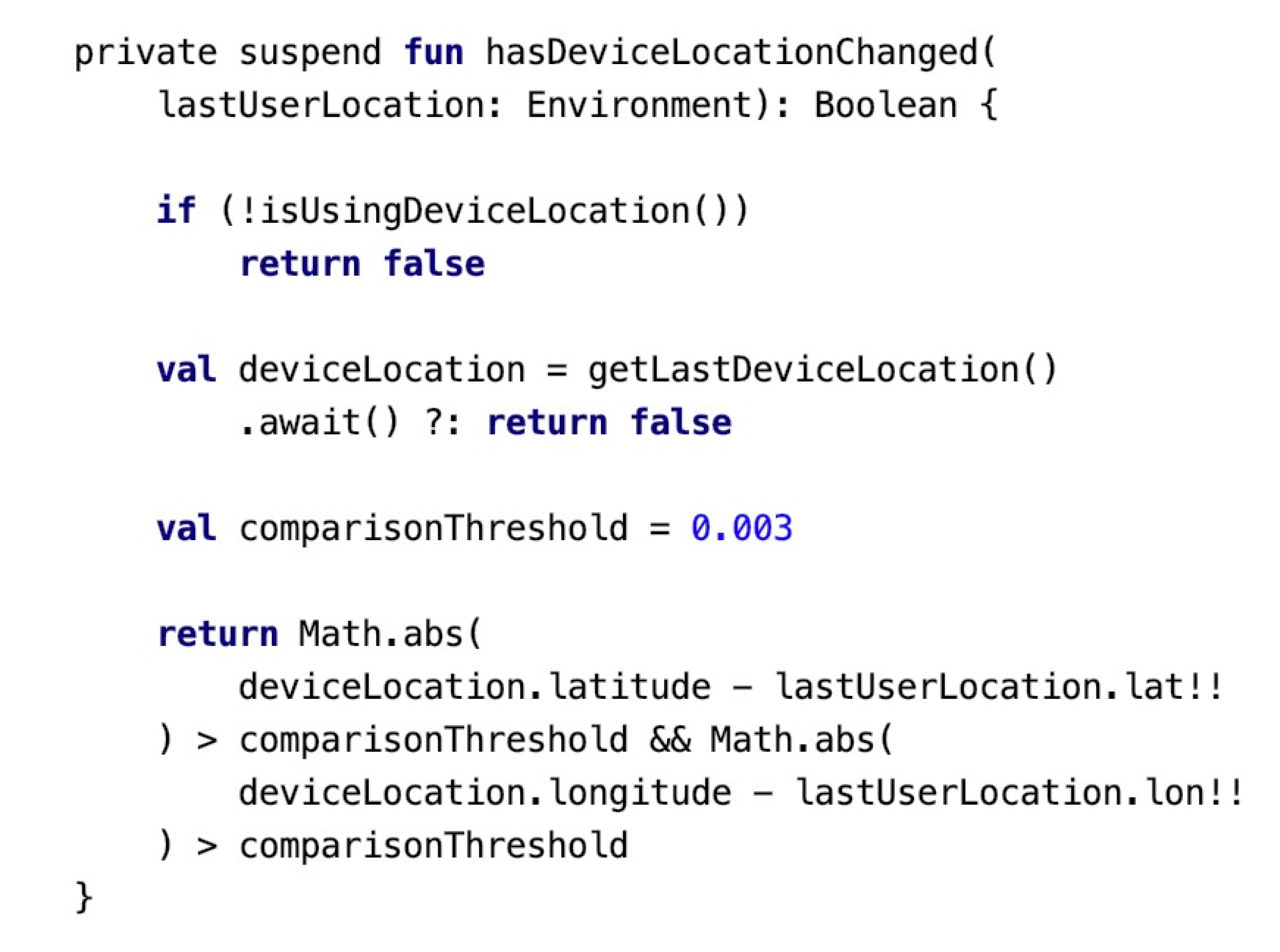
| Algorithm 1 Managging device and profile code |
|
6. Experimental Results
6.1. Materials and Methods
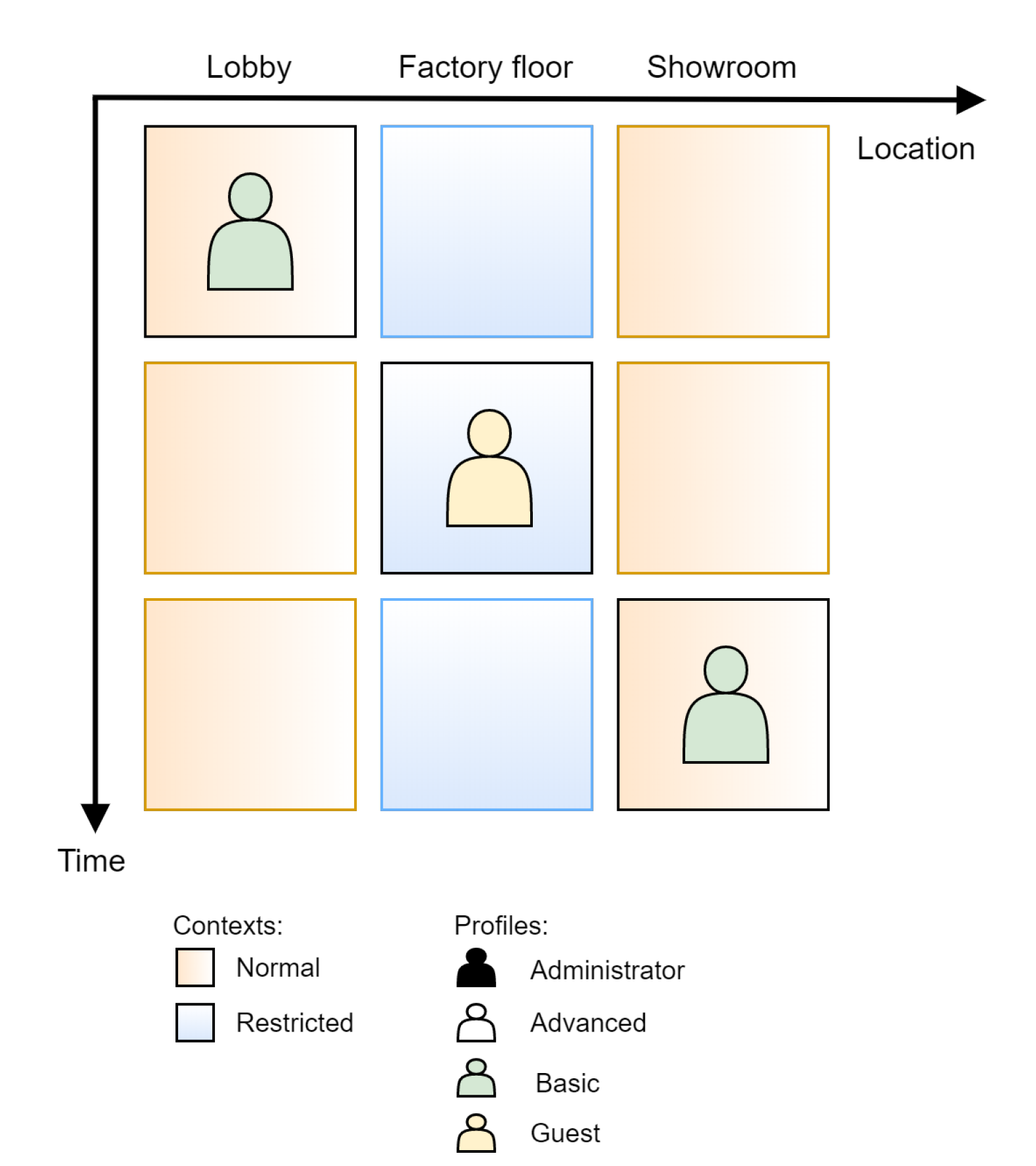
6.2. Scenario #1: Factory Guided Tour
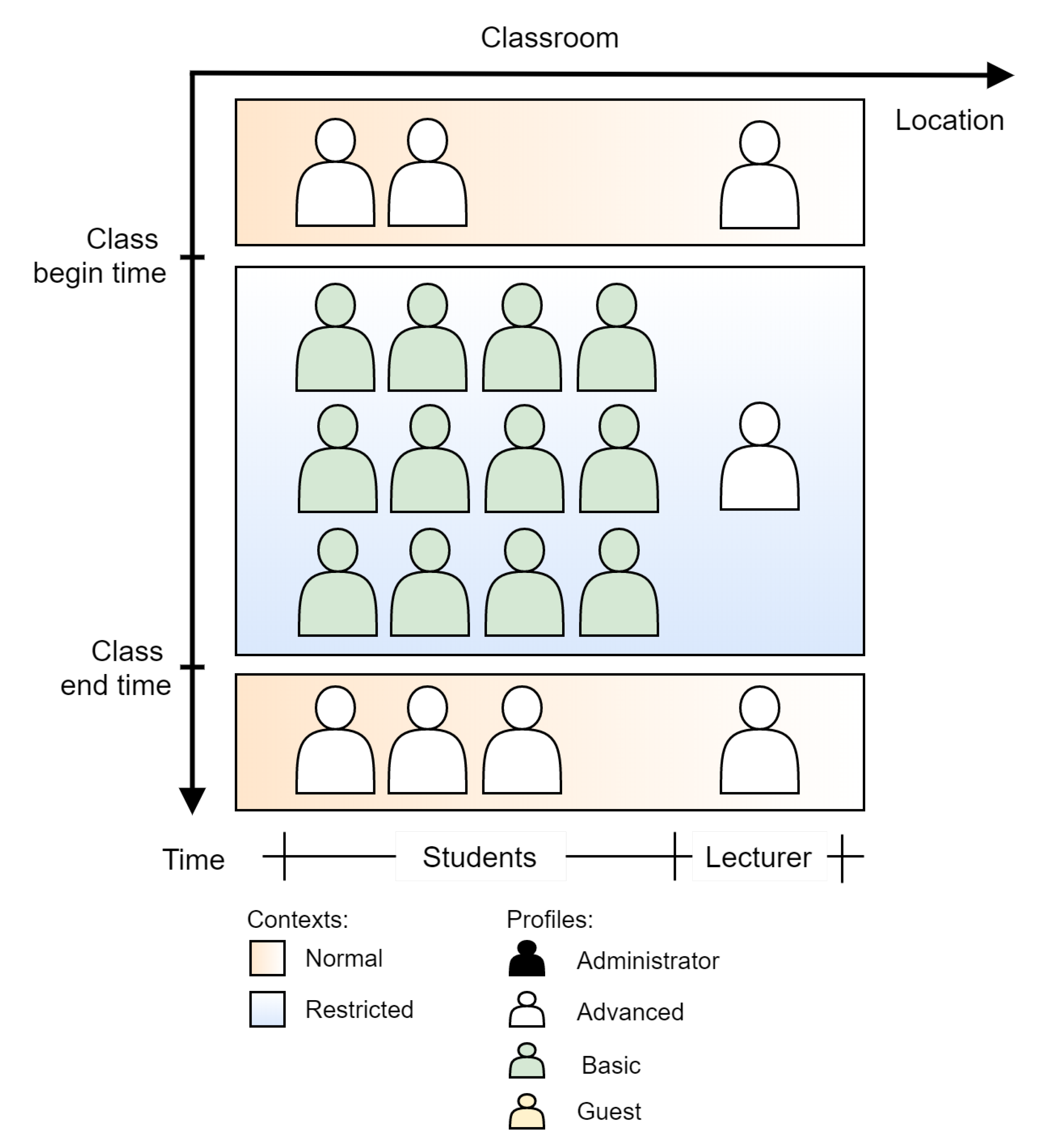
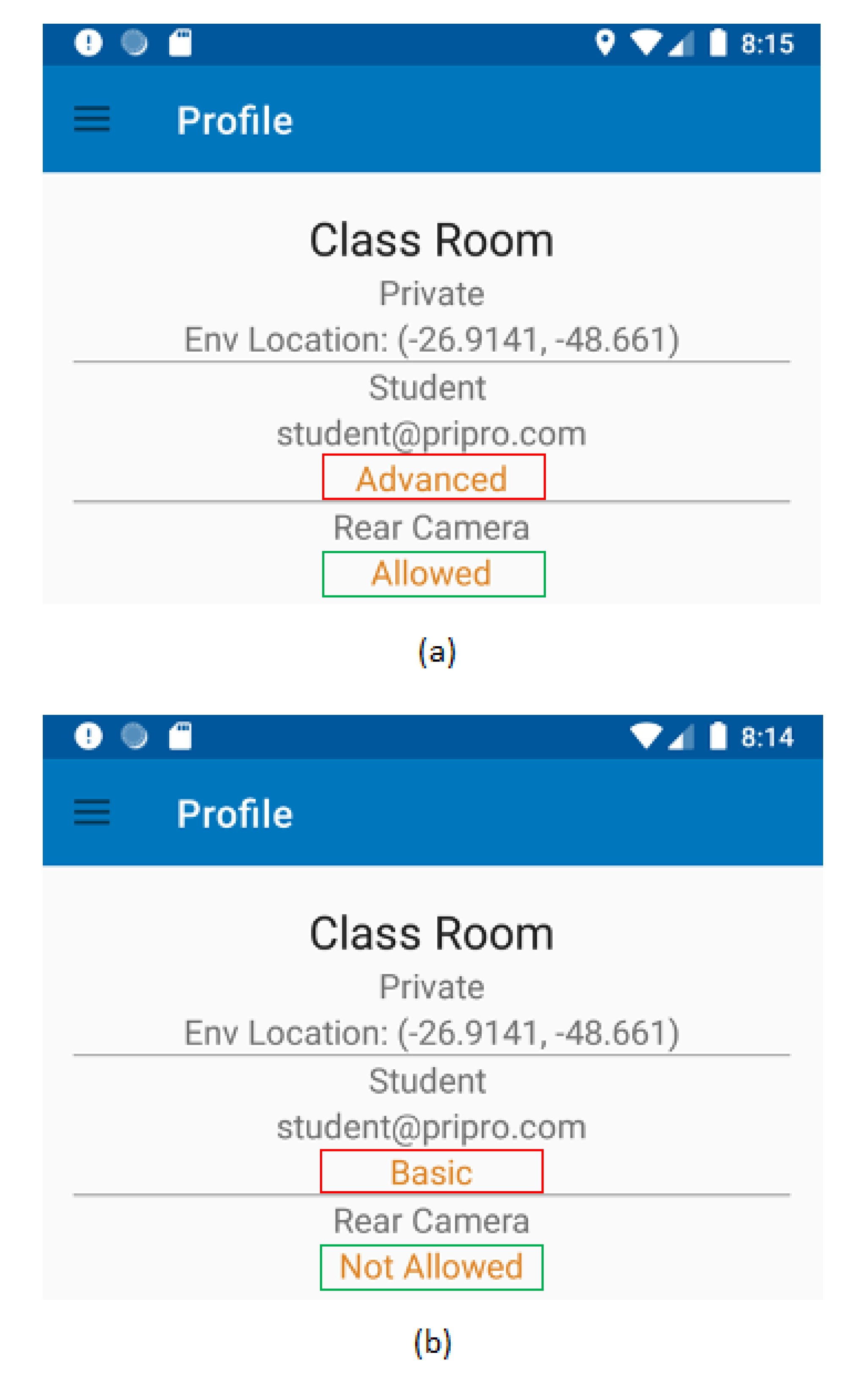
6.3. Scenario #2: University Classroom
6.4. Performance and Costs
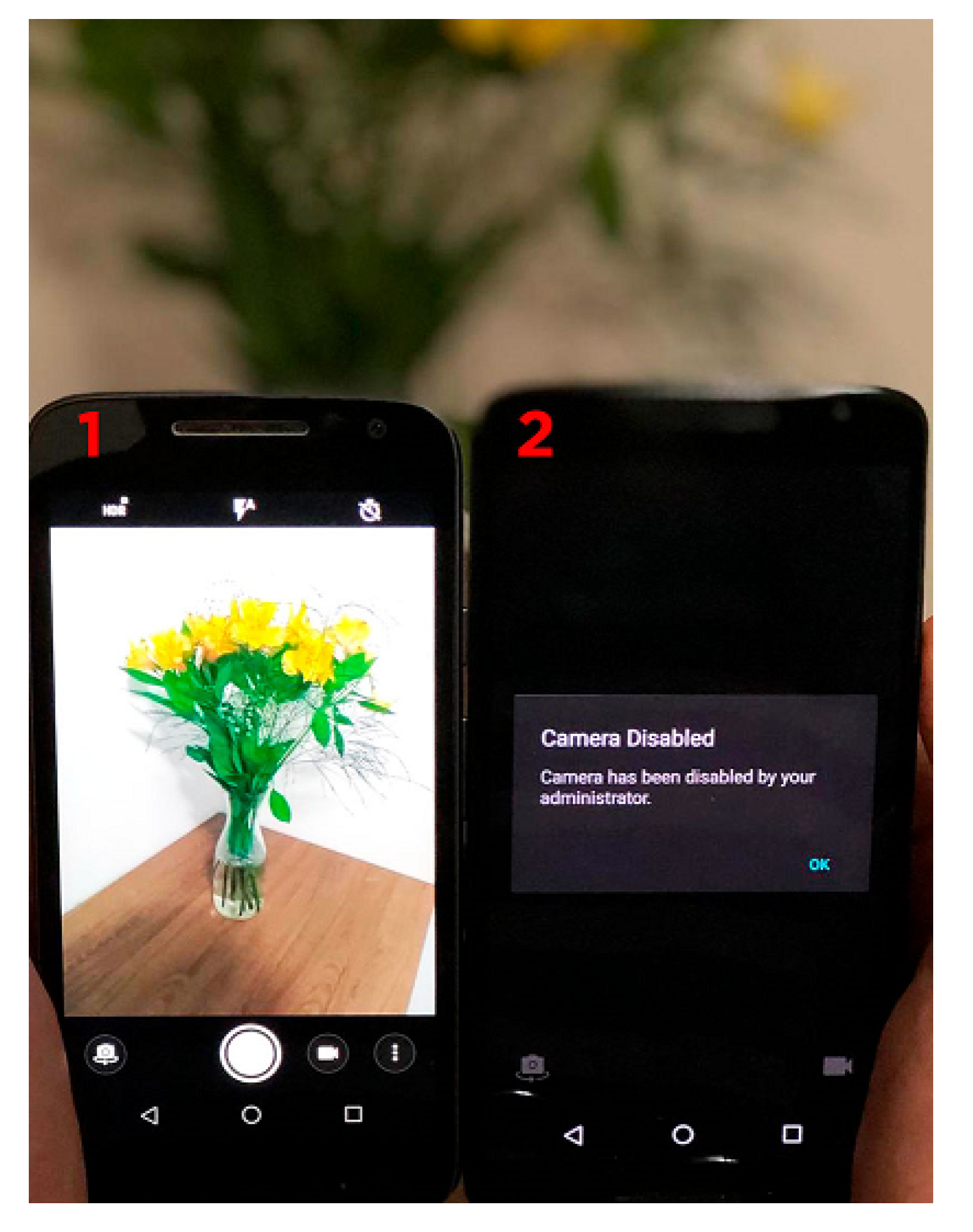
- 1
- Loading and connecting to the web server (from 0 to 5 ms).
- 2
- Processing and applying environmental rules to block the rear camera (from 5 to 13.5 ms).
- 3
- Standby operation (after 13.5 ms).
6.5. Discussion
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| ABAC | Attribute-Based Access Control |
| AC | Access Control |
| API | Application Programming Interface |
| ELM | Extreme Learning Machine |
| ESFCM | Semi-Supervised Fuzzy C-Means |
| GADAR | Group Activity Detection and Recognition |
| GPS | Global Positioning System |
| HTTP | Hyper Text Transfer Protocol |
| IoT | Internet of Things |
| IT | Information Technology |
| JSON | JavaScript Object Notation |
| NFC | Near Field Communication |
| NIST | National Institute of Standards and Technology |
| NGAC | Next Generation Access Control |
| OS | Operating System |
| PerBac | Pervasive-Based Access Control |
| PRICMU | Privacy Controll Management User |
| PRICOM | Privacy Communication |
| PRIDEV | Privacy Devices |
| PRIPRO | Privacy Profile |
| PRIADA | Privacy Adaptation |
| PRIENV | Privacy Environment |
| PRICRI | Privacy Criteria |
| PRIHIS | Privacy History |
| PRISEC | Privacy Security |
| PRISER | Privacy Service |
| JSON | JavaScript Object Notation |
| GNSS | Global Navigation Satellite System |
| GSON | Google JavaScript Object Notation Converter |
| OS | Operating System |
| RFID | Radio-Frequency Identification |
| SMD | Smart Mobile Devices |
| SSN | Spontaneous Social Network |
| UbiPri | Ubiquitous Privacy |
| UWB | Ultra Wide Band |
| WSN | Wireless Sensor Network |
| TLS | Transport Layer Security |
References
- Fernquist, J.; Fangstrom, T.; Kaati, L. Iot data profiles: The routines of your life reveals who you are. In 2017 European Intelligence and Security Informatics Conference (EISIC); IEEE: Athens, Greece, 2017; pp. 61–67. [Google Scholar] [CrossRef]
- Eckhoff, D.; Wagner, I. Privacy in the smart city—Applications, technologies, challenges, and solutions. IEEE Commun. Surv. Tutor. 2018, 20, 489–516. [Google Scholar] [CrossRef] [Green Version]
- Navarro, N.D.A.B.; da Costa, C.A.; Barbosa, J.L.V.; da Rosa Righi, R. Spontaneous Social Network: Toward dynamic virtual communities based on context-aware computing. Expert Syst. Appl. 2018, 95, 72–87. [Google Scholar] [CrossRef]
- Esposito, C. Interoperable, dynamic and privacy-preserving access control for cloud data storage when integrating heterogeneous organizations. J. Netw. Comput. Appl. 2018, 108, 124–136. [Google Scholar] [CrossRef]
- Bezawada, B.; Haefner, K.; Ray, I. Securing Home IoT Environments with Attribute-Based Access Control. In Proceedings of the Third ACM Workshop on Attribute-Based Access Control—ABAC’18; ACM Press: New York, NY, USA, 2018; pp. 43–53. [Google Scholar] [CrossRef]
- El Bouanani, S.; El Kiram, M.A.; Achbarou, O.; Outchakoucht, A. Pervasive-Based Access Control Model for IoT Environments. IEEE Access 2019, 7, 54575–54585. [Google Scholar] [CrossRef]
- Amini, M.; Osanloo, F. Purpose-Based Privacy Preserving Access Control for Secure Service Provision and Composition. IEEE Trans. Serv. Comput. 2019, 12, 604–620. [Google Scholar] [CrossRef]
- Chen, H.; Cha, S.H.; Kim, T.W. A framework for group activity detection and recognition using smartphone sensors and beacons. Build. Environ. 2019, 158, 205–216. [Google Scholar] [CrossRef]
- Leithardt, V.R.Q. UbiPri–Middleware for Privacy Control and Management in Ubiquitous Environments. Ph.D. Thesis, PPGC, Federal Univ. of Rio Grande do Sul (UFRGS), Porto Alegre, Brazil, 2015. (In Portuguese). [Google Scholar]
- Leithardt, V.; Santos, D.; Silva, L.; Viel, F.; Zeferino, C.; Silva, J. A solution for dynamic management of user profiles in IoT environments. IEEE Lat. Am. Trans. 2020, 18, 1193–1199. [Google Scholar] [CrossRef]
- Martins, J.A.; Ochôa, I.S.; Silva, L.A.; Mendes, A.S.; González, G.V.; De Paz Santana, J.; Leithardt, V.R.Q. PRIPRO: A Comparison of Classification Algorithms for Managing Receiving Notifications in Smart Environments. Appl. Sci. 2020, 10, 502. [Google Scholar] [CrossRef] [Green Version]
- Cesconetto, J.; Silva, L.A.; Cáceres, M.N.; Garcia, N.M.; Valderi Leithardt, R.Q. PRIPRO: Solution for user profile control and management based on data privacy. In Proceedings of the 2020 15th Iberian Conference on Information Systems and Technologies (CISTI), Sevilla, Spain, 24–27 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Ahmed, E.; Yaqoob, I.; Gani, A.; Imran, M.; Guizani, M. Internet-of-things-based smart environments: State of the art, taxonomy, and open research challenges. IEEE Wirel. Commun. 2016, 23, 10–16. [Google Scholar] [CrossRef]
- Silva, L.A.; Leithardt, V.R.Q.; Rolim, C.O.; González, G.V.; Geyer, C.F.R.; Silva, J.S. PRISER: Managing notification in multiples devices with data privacy support. Sensors 2019, 19, 3098. [Google Scholar] [CrossRef] [Green Version]
- Victorelli, E.Z.; Dos Reis, J.C.; Hornung, H.; Prado, A.B. Understanding human-data interaction: Literature review and recommendations for design. Int. J. Hum.-Comput. Stud. 2020, 134, 13–32. [Google Scholar] [CrossRef]
- Zeng, W.; Chen, P.; Chen, H.; He, S. PAPG: Private Aggregation Scheme based on Privacy-preserving Gene in Wireless Sensor Networks. KSII Trans. Internet Inf. Syst. 2016, 10, 4442–4466. [Google Scholar] [CrossRef]
- Xie, K.; Ning, X.; Wang, X.; He, S.; Ning, Z.; Liu, X.; Wen, J.; Qin, Z. An efficient privacy-preserving compressive data gathering scheme in WSNs. Inf. Sci. 2017, 390, 82–94. [Google Scholar] [CrossRef]
- Weiser, M. The Computer for the 21st Century. SIGMOBILE Mob. Comput. Commun. Rev. 1999, 3, 3–11. [Google Scholar] [CrossRef]
- Hirsch, M.; Mateos, C.; Zunino, A. Augmenting computing capabilities at the edge by jointly exploiting mobile devices: A survey. Future Gener. Comput. Syst. 2018, 88, 644–662. [Google Scholar] [CrossRef]
- Statista. Number of Smartphone Users Worldwide from 2016 to 2021; Statista: Hambourg, Germany, 2020. [Google Scholar]
- Kumar, S.; Shanker, R.; Verma, S. Context aware dynamic permission model: A retrospect of privacy and security in android system. In Proceedings of the 2018 International Conference on Intelligent Circuits and Systems (ICICS), Phagwara, India, 19–20 April 2018; pp. 324–329. [Google Scholar] [CrossRef]
- Google Developers Device Administration Overview; Google: Mountain View, CA, USA, 2019.
- Horsmanheimo, S.; Lembo, S.; Tuomimaki, L.; Huilla, S.; Honkamaa, P.; Laukkanen, M.; Kemppi, P. Indoor Positioning Platform to Support 5G Location Based Services. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Groβwindhager, B.; Stocker, M.; Rath, M.; Boano, C.A.; Römer, K. SnapLoc: An ultra-fast UWB-based indoor localization system for an unlimited number of tags. In Proceedings of the 2019 18th ACM/IEEE International Conference on Information Processing in Sensor Networks (IPSN), Montreal, QC, Canada, 15–18 April 2019; pp. 61–72. [Google Scholar]
- Tiwari, P.; Malik, P.K. Design of UWB Antenna for the 5G Mobile Communication Applications: A Review. In Proceedings of the 2020 International Conference on Computation, Automation and Knowledge Management (ICCAKM), Dubai, UAE, 9–10 January 2020; pp. 24–30. [Google Scholar]
- Desolda, G.; Ardito, C.; Matera, M. Empowering end users to customize their smart environments: Model, composition paradigms, and domain-specific tools. ACM Trans. Comput.-Hum. Interact. 2017, 24, 1–52. [Google Scholar] [CrossRef] [Green Version]
- Rathore, S.; Park, J.H. Semi-supervised learning based distributed attack detection framework for IoT. Appl. Soft Comput. 2018, 72, 79–89. [Google Scholar] [CrossRef]
- Hasan, R.; Zawoad, S.; Haque, M.M. StuxMob: A situational-aware malware for targeted attack on smart mobile devices. In Proceedings of the MILCOM 2016 IEEE Military Communications Conference, Baltimore, MD, USA, 1–3 November 2016; pp. 509–514. [Google Scholar] [CrossRef]
- Nurgaliyev, K.; Mauro, D.D.; Khan, N.; Augusto, J.C. Improved Multi-user Interaction in a Smart Environment through a Preference-Based Conflict Resolution Virtual Assistant. In Proceedings of the 2017 International Conference on Intelligent Environments (IE), Seoul, Korea, 21–25 August 2017; pp. 100–107. [Google Scholar] [CrossRef]
- Coulouris, G.; Dollimore, J.; Kindberg, T.; Blair, G. Distributed Systems: Concepts and Design, 5th ed.; Bookman Editora: São Paulo, Brazil, 2012; pp. 24–40. [Google Scholar]
- Hu, V.C.; Kuhn, D.R.; Ferraiolo, D.F.; Voas, J. Attribute-Based Access Control. Computer 2015, 48, 85–88. [Google Scholar] [CrossRef]
- Vital, L.P.; Cafe, L.M.A. Ontologias e taxonomias: Diferenças. Perspect. Cienc. Inform. 2011, 16, 115–130. [Google Scholar] [CrossRef] [Green Version]
- Lu, Y.; Xu, L.D. Internet of Things (IoT) cybersecurity research: A review of current research topics. IEEE Internet Things J. 2019, 6, 2103–2115. [Google Scholar] [CrossRef]
- Lozano Domínguez, J.M.; Mateo Sanguino, T.J. Review on V2X, I2X, and P2X Communications and Their Applications: A Comprehensive Analysis over Time. Sensors 2019, 19, 2756. [Google Scholar] [CrossRef] [Green Version]
- Khan, M.A.; Peters, S.; Sahinel, D.; Pozo-Pardo, F.D.; Dang, X.T. Understanding autonomic network management: A look into the past, a solution for the future. Comput. Commun. 2018, 122, 93–117. [Google Scholar] [CrossRef]
- Cho, D.; Kwon, K.H. The impacts of identity verification and disclosure of social cues on flaming in online user comments. Comput. Hum. Behav. 2015, 51, 363–372. [Google Scholar] [CrossRef]
- Ud Din, I.; Guizani, M.; Kim, B.S.; Hassan, S.; Khurram Khan, M. Trust management techniques for the Internet of Things: A survey. IEEE Access 2019, 7, 29763–29787. [Google Scholar] [CrossRef]
- Aleroud, A.; Karabatis, G. Contextual information fusion for intrusion detection: A survey and taxonomy. Knowl. Inf. Syst. 2017, 52, 563–619. [Google Scholar] [CrossRef]
- Asghari, P.; Rahmani, A.M.; Javadi, H.H.S. Internet of Things applications: A systematic review. Comput. Netw. 2019, 148, 241–261. [Google Scholar] [CrossRef]
- Boubiche, D.E.; Imran, M.; Maqsood, A.; Shoaib, M. Mobile crowd sensing—Taxonomy, applications, challenges, and solutions. Comput. Hum. Behav. 2019, 101, 352–370. [Google Scholar] [CrossRef]
- Hendrikx, F.; Bubendorfer, K.; Chard, R. Reputation systems: A survey and taxonomy. J. Parallel Distrib. Comput. 2015, 75, 184–197. [Google Scholar] [CrossRef]
- Lau, B.P.L.; Marakkalage, S.H.; Zhou, Y.; Hassan, N.U.; Yuen, C.; Zhang, M.; Tan, U.X. A survey of data fusion in smart city applications. Inf. Fusion 2019, 52, 357–374. [Google Scholar] [CrossRef]
- Hui, T.K.; Sherratt, R.S.; Sánchez, D.D. Major requirements for building Smart Homes in Smart Cities based on Internet of Things technologies. Future Gener. Comput. Syst. 2017, 76, 358–369. [Google Scholar] [CrossRef] [Green Version]
- Hors-Fraile, S.; Rivera-Romero, O.; Schneider, F.; Fernandez-Luque, L.; Luna-Perejon, F.; Civit-Balcells, A.; de Vries, H. Analyzing recommender systems for health promotion using a multidisciplinary taxonomy: A scoping review. Int. J. Med Inform. 2018, 114, 143–155. [Google Scholar] [CrossRef] [PubMed]
- Zhu, K.; Li, W.; Fu, X.; Zhang, L. Data routing strategies in opportunistic mobile social networks: Taxonomy and open challenges. Comput. Netw. 2015, 93, 183–198. [Google Scholar] [CrossRef]
- Audulv, A.; Ghahari, S.; Kephart, G.; Warner, G.; Packer, T.L. The Taxonomy of Everyday Self-management Strategies (TEDSS): A framework derived from the literature and refined using empirical data. Patient Educ. Couns. 2019, 102, 367–375. [Google Scholar] [CrossRef] [PubMed]
- Gassen, M.; Fhom, H.S. Towards Privacy-preserving Mobile Location Analytics. In EDBT/ICDT Workshops; CEUR-WS Team: Aschen, Germany, 2016. [Google Scholar]
- Desouza, K.C.; Ahmad, A.; Naseer, H.; Sharma, M. Weaponizing information systems for political disruption: The actor, lever, effects, and response taxonomy (ALERT). Comput. Secur. 2019, 88, 101606. [Google Scholar] [CrossRef]
- Anthonysamy, P.; Rashid, A.; Chitchyan, R. Privacy requirements: Present & future. In Proceedings of the 2017 IEEE/ACM 39th International Conference on Software Engineering: Software Engineering in Society Track (ICSE-SEIS), Bueons Aires, Argentina, 20–28 May 2017; pp. 13–22. [Google Scholar] [CrossRef] [Green Version]
- Riahi Sfar, A.; Natalizio, E.; Challal, Y.; Chtourou, Z. A roadmap for security challenges in the Internet of Things. Digit. Commun. Netw. 2018, 4, 118–137. [Google Scholar] [CrossRef]
- Mokhtari, J.E.; El Kalam, A.A.; Benhadou, S.; Medroumi, H. PrivUML: A privacy metamodel. Procedia Comput. Sci. 2019, 151, 53–60. [Google Scholar] [CrossRef]
- Taherkordi, A.; Zahid, F.; Verginadis, Y.; Horn, G. Future cloud systems design: Challenges and research directions. IEEE Access 2018, 6, 74120–74150. [Google Scholar] [CrossRef]
- Solove, D.J. A taxonomy of privacy. Univ. PA Law Rev. 2006, 154, 477. [Google Scholar] [CrossRef]

| Work | Year | Environment Identification | User Identification | Context Identification | Data Privacy | User Profile Evolution |
|---|---|---|---|---|---|---|
| [1] | 2017 | • | • | • | ||
| [3] | 2018 | • | • | |||
| [4] | 2018 | • | • | • | ||
| [5] | 2018 | • | • | • | • | |
| [8] | 2019 | • | • | |||
| [6] | 2019 | • | • | • | • | |
| [7] | 2019 | • | • | |||
| This work | 2020 | • | • | • | • | • |
| Component | Works |
|---|---|
| Communication | [14,33,34,35,36] |
| Environment | [26,37,38,39,40,41,42,43], |
| User | [44,45,46,47,48] |
| Privacy | [2,9,19,21,49,50,51,52,53] |
| Environment | Cameras | Loudspeaker | Wi-Fi | Mobile Data | Calls | Emergency Call |
|---|---|---|---|---|---|---|
| Classroom | • | • | • | |||
| Museum | • | • | ||||
| Airplane takeoff | • | • | • | • | • | |
| Airplane in flight | • | • | • | |||
| City bus | • | |||||
| Travel bus | • | |||||
| Public library | • | • | • | |||
| Theater/Cinema | • | • | • | • | • | |
| Hospital: Lobby | • | |||||
| Hospital: ITU | • | • | • | • | • | • |
| Home: Dinner Room * | • | • | • | |||
| Restaurant * | • | • | • |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cesconetto, J.; Augusto Silva, L.; Bortoluzzi, F.; Navarro-Cáceres, M.; A. Zeferino, C.; R. Q. Leithardt, V. PRIPRO—Privacy Profiles: User Profiling Management for Smart Environments. Electronics 2020, 9, 1519. https://doi.org/10.3390/electronics9091519
Cesconetto J, Augusto Silva L, Bortoluzzi F, Navarro-Cáceres M, A. Zeferino C, R. Q. Leithardt V. PRIPRO—Privacy Profiles: User Profiling Management for Smart Environments. Electronics. 2020; 9(9):1519. https://doi.org/10.3390/electronics9091519
Chicago/Turabian StyleCesconetto, Jonas, Luís Augusto Silva, Fabricio Bortoluzzi, María Navarro-Cáceres, Cesar A. Zeferino, and Valderi R. Q. Leithardt. 2020. "PRIPRO—Privacy Profiles: User Profiling Management for Smart Environments" Electronics 9, no. 9: 1519. https://doi.org/10.3390/electronics9091519
APA StyleCesconetto, J., Augusto Silva, L., Bortoluzzi, F., Navarro-Cáceres, M., A. Zeferino, C., & R. Q. Leithardt, V. (2020). PRIPRO—Privacy Profiles: User Profiling Management for Smart Environments. Electronics, 9(9), 1519. https://doi.org/10.3390/electronics9091519








