1. Introduction
Wireless sensor networks (WSNs) generally consist of numerous distributed sensor nodes and several base station (BS). Sensor nodes detect the events and gather the environment information, and this information is then delivered to the BS over multi-hop. Recently, WSNs are getting attentions as an essential component of the Internet of Things (IoT), which can be applied to various applications such as environmental monitoring, patient monitoring, and industrial fields [
1,
2,
3,
4]. The important thing to note is that these applications must guarantee quality-of-service (QoS) requirement, especially
delay. For example, when sensor nodes detect a fire in the mountain, it must be notified to the BS as soon as possible. If the detection information is delivered to the BS late, it becomes useless [
4]. Thus, a lot of works have been focused on the QoS in WSNs [
5,
6,
7,
8,
9,
10,
11,
12].
As deployment of WSNs increases, security threats to WSNs are also increasing. However, ensuring security in WSNs is not so trivial because sensor nodes have very low computation capability and limited energy, and thus cannot apply general security technology such as public key cryptography. Furthermore, sensor nodes are subject to node compromise attacks where the adversary can physically compromise sensor nodes and extract all information such as key materials from them. Lots of research on security in WSNs have been done in the field of efficient and lightweight key management, data encryption, and authentication [
13,
14,
15,
16,
17,
18,
19,
20,
21,
22].
On the other hand, in a variety of wireless sensor networks applications such as the intruder detection system and the remote patient monitoring system, the sensory data must be delivered to the BS while ensuring both security and QoS. For example, the information of the intruder in the intruder detection system must not only be forwarded to the BS within the predefined time budget, but also be protected by security primitives such as confidentiality, integrity, and authentication. However, ensuring both security and QoS is challenging in WSNs since it takes non-trivial time a resource-constrained sensor node to perform security operations such as encryption and decryption. Thus, security and QoS have been studied independently as mentioned above.
Only very few works have focused on both security and QoS [
23,
24,
25,
26]. Xu et al. [
23] tried to optimize security and QoS at the same time using both connection outage probability and secrecy outage probability, but it does not take energy efficiency into account. Rachedi et al. [
24] focused on maximizing the security level without sacrificing QoS, thus it can be vulnerable to security attacks when congestion happens. Rathee et al. [
25] attempted to find a balance among security, QoS, and energy efficiency by employing a multi-objective function. However, they do not guarantee security strictly. Rachedi et al. [
26] proposed a genetic algorithm based on optimization method for security, QoS and energy efficiency. They also fail to satisfy security requirements because of the priority to QoS and energy efficiency.
In this paper, we propose a secure forwarding scheme whose goal is to minimize energy consumption while satisfying the requirement of both QoS and security in WSNs. It is important to note that among many QoS parameters, we especially focus on delay which is the most critical parameter in a variety of WSNs applications such as the intruder detection system and the remote patient monitoring system. Furthermore, we focus on three security requirements of confidentiality, authenticity, and integrity which are fundamental in most WSNs applications. Confidentiality is guaranteed by encryption and decryption, and authenticity and integrity are achieved by authentication tokens such as message authentication code (MAC). To accomplish our goal, we alternatively use hop-by-hop security and end-to-end security according to the remaining time budget. Hop-by-hop security implies that each node shares a key with its neighbor and the data are decrypted and encrypted in every hop. Thus, hop-by-hop security has computation delay in each hop that aggravates QoS. However, hop-by-hop security gives an opportunity to perform in-network data aggregation [
27,
28,
29] using spatial and temporal correlations among sensed data from nearby sensors, thereby reducing the energy consumption. On the other hand, end-to-end security performs encryption and decryption in the source node and the BS only, not in the intermediate nodes, and thus have no computation delay in each hop. However, end-to-end security does not provide data aggregation since intermediate nodes do not know a key between the source node and the BS. Thus, we use hop-by-hop security to conserve energy through data aggregation as long as the time budget is sufficient. When estimating that the sensor node does not have enough time with hop-by-hop security, it switches into end-to-end security in order to reach the BS within deadline. Our main contributions are as follows.
We propose a secure forwarding scheme with QoS assurance which tries to minimize energy consumption. Given QoS requirements, our scheme performs data aggregation as many times as possible by preferring hop-by-hop security.
We analyze the relation between QoS and security in terms of energy efficiency in detail and prove that hop-by-hop security with data aggregation provides better energy efficiency than end-to-end security without data aggregation.
We evaluate our proposed scheme through a variety of simulations in terms of energy efficiency and packet delivery ratio under a variety of scenarios. The result shows that our proposed scheme guarantees security and security at the same time while minimizing energy consumption.
The remainder of the paper is organized as follows.
Section 2 provides related works on QoS and security. In
Section 3, we propose our secure forwarding scheme with QoS guarantee, and we analyze the energy consumption in hop-by-hop security and end-to-end security in
Section 4. After
Section 5 presents and discusses the performance evaluation about our scheme,
Section 6 concludes the paper.
2. Related Works
In this section, we thoroughly investigate a variety of related works on energy efficiency, QoS, and security in WSNs since our goal is to minimize energy consumption while satisfying both QoS and security simultaneously. We further present several related works on data aggregation which motivate our proposed scheme. After we emphasize the importance of energy efficiency in WSNs, we look into several works on QoS and security separately. Finally, a few schemes aiming to guarantee both QoS and security are followed by works on data aggregation.
Since sensor nodes are generally deployed in the unattended environment, they are equipped with batteries with limited capacity. Obviously, the most important goal in WSNs is to conserve energy in sensor nodes. This is why most existing research on WSNs has been focusing on energy efficiency while considering other factors such as routing, QoS, security, and data aggregation [
30].
There have been a lot of research on QoS in WSNs which are mainly combined with routing. Xu et al. [
5] proposed an energy-efficient clustering routing protocol based on a high-QoS node deployment with an inter-cluster routing mechanism that extends the network lifetime by selecting the cluster head based on the residual energy and the distance of the nodes to the BS. Gao et al. [
6] presented a statistical QoS-driven power control scheme while maximizing energy efficiency. They selected best power control policy under different QoS constraints. Zhang et al. [
7] proposed a QoS-aware and energy-efficient routing algorithm in industrial WSNs by selecting the optimal relay node in terms of real-time and reliability. Hasan et al. [
8] proposed multipath QoS routing algorithms by adaptively switching QoS paths whereby significantly improving packet delivery ratio, energy efficiency, and end-to-end delay. Genta et al. [
9] presented a meta-heuristic optimization based on routing algorithm by considering minimum distance and least energy dissipation in order to provide QoS and energy efficiency. QoS-aware and heterogeneously clustered routing protocol was proposed in [
10] which provides the dedicated paths for satisfying QoS requirements. Wu et al. [
11] proposed a novel delay-aware routing algorithm that achieves energy efficiency by employing a location-based forwarding scheme. Faheem et al. [
12] proposed a cross-layer QoS-aware routing protocol for the underwater acoustic sensor networks. All of these works provided novel approaches on QoS in WSNs, but they only focused on QoS and energy efficiency without taking security into account.
Since security in WSNs is of paramount importance, many researchers have been focusing on tailoring existing security methods into resource-constrained WSNs in terms of key management, encryption/decryption, integrity, and authentication. Liu et al. [
14] proposed a lightweight pseudo-random encryption scheme to ensure confidentiality over insecure wireless links. Hayajneh et al. [
15] proposed a security protocol for WSNs with cooperative communication, thereby improving the network reliability and resilience. Hasseb et al. [
16] developed a secure and energy-efficient routing protocol for avoiding intrusion. They ensure the integrity and reliability of the sensory data by exploiting Shamir secret sharing scheme [
17]. Hussein et al. [
18] provided a scalable group key management scheme and a secure communication method based on elliptic curve cryptography. Yu et al. [
19] presented a novel authentication protocol for vehicular communications in WSNs which can guarantee mutual authentication, session key management, and privacy. Jung et al. [
20] proposed an authenticated key agreement protocol which provides enhanced features such as anonymous authentication, resistance to session key compromise, and energy efficiency. Gope et al. [
21] proposed a lightweight mutual authentication protocol with privacy-preserving which are secure against physical node compromise attacks and energy efficiency. Energy-efficient and secure path optimization protocol was proposed in [
22] where security and energy efficiency are accomplished by binary hop count and security code using Huffman coding. All of above works guaranteed effective security and energy efficiency for WSNs, but they do not consider QoS at all.
Even though a lot of attentions have been paid to QoS and security as mentioned above, there have been very few works which considers both QoS and security simultaneously. This is because security gives adverse effect on QoS in terms of processing time and transmission time. In other words, sensor nodes must perform encryption/decryption for confidentiality or generate security tokens for authentication, and then deliver these security tokens to the destination node. Xu et al. [
23] proposed a secure optimal QoS routing protocol (SOQR) which attempts to optimize both security and QoS at the same time using both connection outage probability and secrecy outage probability. Even though SOQR achieves a balance between QoS and security, but it does not take energy efficiency into account. Rachedi et al. [
24] proposed a new integration scheme of QoS and security based on the PID controller. Given QoS requirements, they try to maximize security by considering resource availability and residual energy. This scheme is very novel in that it gracefully integrates security with QoS using the PID controller, but it can be vulnerable to security attacks when congestion happens since it does not sacrifice QoS instead of security. Rathee et al. [
25] proposed a QoS aware energy balancing secure routing (QEBSR) protocol based on ant colony optimization. QEBSR selects a routing path according to the metric of energy cost, end-to-end delay and the trust factor computed by enhanced heuristics. QEBSR attempts to make tradeoffs among security, QoS, and energy efficiency by employing a multi-objective function, but it does not guarantee security strictly. Rachedi et al. [
26] proposed a genetic algorithm based on optimization method for security, QoS, and energy efficiency. They accomplish to find a balance among them, but also fail to satisfy security requirements due to the priority to the QoS and energy efficiency.
Data aggregation in WSNs is a good technique to save energy by aggregation multiple packets into one packet [
27]. This effectively reduces the amount of transmitted data and helps to improve the lifetime of sensor nodes. Li et al. [
28] proposed a differentiated data aggregation routing protocol in order to conserve energy. Zhang et al. [
29] proposed a novel data aggregation scheme based on rings which provides reliability and energy efficiency. In this paper, we utilize data aggregation to conserve as much energy as possible while delivering data to the BS. Data aggregation can have negative or positive impacts on QoS. If each sensor node waits for a long time to aggregate more packets, it will affect QoS badly. However, if each sensor node waits for a short time, it gives better QoS since data aggregation reduce the amount of data to be transmitted. In this paper, we try to aggregate as many packets as possible in order to reduce energy consumption by considering the QoS requirement.
3. Proposed Secure Forwarding Scheme with QoS Guarantee
3.1. Overview
The goal of our proposed scheme is to deliver the sensed data collected from the sensor nodes to the BS securely within deadline while minimizing energy consumption. To achieve this goal, we take advantage of the fact that the sensed data has spatial and temporal correlation. Instead of forwarding the received sensed data directly, each node waits for another sensed data for some time and aggregates them into one packet by removing the redundant data and header overhead. The aggregated packet is then forwarded to the next sensor node. This process is repeated until the packet arrives at the BS. Since energy consumed by communication is most significant in WSNs, hop-by-hop security must be used to enable data aggregation in secure forwarding. Unfortunately, the waiting time and hop-by-hop security for data aggregation have an adverse effect on the QoS requirement. Thus, we adaptively adjust the waiting time for data aggregation using fully distributed hop count and average transmission time at each node. Adaptive waiting time increases the probability of data aggregation and reduces energy consumption. Energy consumption in hop-by-hop security with data aggregation and end-to-end security without data aggregation is analyzed in detail in
Section 4.
3.2. Assumptions
We first assume that WSNs consists of resource-constrained sensor nodes with limited resources and one BS with infinite resources. Our goal is to minimize energy consumption of sensor nodes while ensuring QoS and security. We assume that each packet has a predetermined QoS requirement (
Tdeadline) according to the applications and every packet can be delivered to the BS successfully if we do not perform data aggregation and do not have collisions during transmission. We assume that symmetric key cryptography, especially AES-128 for encryption/decryption and hash-based MAC (HMAC) for authenticity and integrity, is used for WSNs and parameters related to security, including key materials and cryptographic algorithms, are established in each node by using existing key establishment scheme such as COKES [
31]. It is important to note that security in our scheme is provided with the help of existing security algorithms using symmetric key cryptography. We focus on how to balance between QoS and energy efficiency by alternately using existing secure hop-by-hop security and end-to-end security. Each sensor node is assumed to be synchronized with the BS using existing synchronization protocols such as SETB [
32] and transmit the collected information to the BS through multi-hop communication.
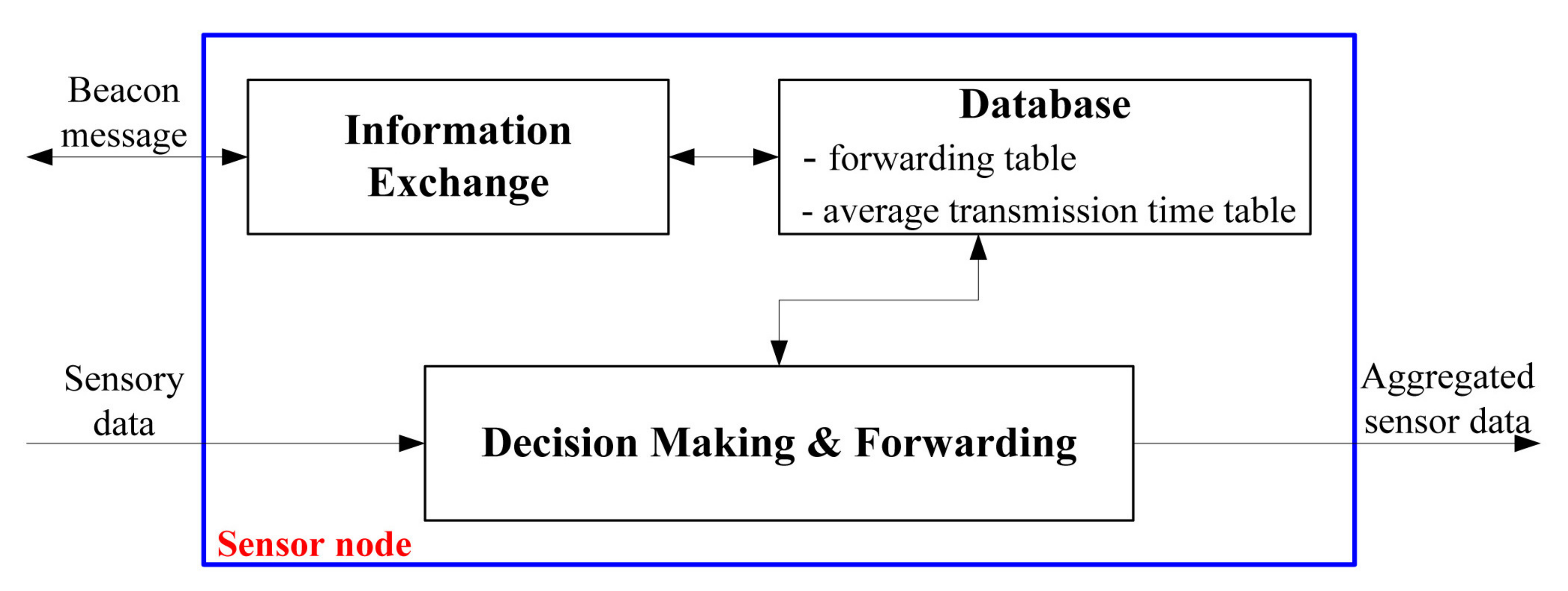
3.3. Database Component (DC)
The database component (DC) stores the information, obtained from the information exchange component (IEC), for forwarding the sensing data as shown in
Figure 1. When requested, the DC provides the information to the IEC or the decision making and forwarding component (DMFC). The DC consists of two tables; the forwarding table (FT) and the average transmission time table (ATTT).
The FT stores the information of one neighboring node to be forwarded, which has the smallest hop count to the BS, including the ID, the hop count to the BS, and the average transmission time as shown in
Figure 2. If a better neighbor, which has the smaller hop count than the current one, is discovered through a beacon message, the FT is updated accordingly. The ATTT is a table that stores the average transmission time that it takes to deliver a message from each neighboring node to itself. Whenever receiving the sensing data from the neighbor node, each node obtains the real transmission time from the timestamp of the received packet and updates the average transmission time of the neighboring node in the ATTT using exponentially weighted moving average. Furthermore, the ATTT of each node is exchanged with the neighbor nodes via a beacon message in order to inform the neighboring nodes of the average transmission time to the sender of the beacon message. The structure of FT and ATT is shown in
Figure 2.
3.4. Information Exchange Component (IEC)
The IEC periodically transmits a beacon message which contains the ID of the sending node, the minimum hop count to the BS, the ID of the neighbor nodes, and the corresponding average transmission time from each neighbor node to the sending node. Upon receiving the beacon message from the neighboring node, the IEC compares the hop count in the beacon message with that of the FT, and updates the FT with the received information if the hop count in the message is smaller than that of the FT. It is important to note that the overhead due to beacon messages can be negligible since sensor nodes in WSNs already use beacon messages for the neighbor discovery. To avoid collision with neighboring nodes, each node sends a beacon message after random waiting.
3.5. Decision Making and Forwarding Component (DMFC)
The DMFC is responsible for making forwarding decision of either hop-by-hop with data aggregation or end-to-end security without data aggregation.
When selecting to perform hop-by-hop security with data aggregation, the total time spent in the intermediate node
i is expressed as
where
tdec(
i) is the time taken to decrypt the data and authenticate the data,
tagg(
i) is the time taken to wait and perform data aggregation,
tenc(
i) is the time to encrypt the data and generate an authentication token, and
ttx(
i) is the time to transmit the data to the next-hop node.
ttx(
i) includes all possible delay such as queueing delay, transmission delay, propagation delay, and delay due to collision and contention.
Without data aggregation at intermediate nodes, the following equation is always satisfied from our assumption.
where
h is a hop count from the source node to the BS.
When performing data aggregation to conserve energy, each intermediate node spends additional time,
tagg(
i), for waiting and processing data aggregation. Thus, we need to guarantee the following equation.
In Equation (3), each node knows
h via a periodic beacon message.
tdec and
tenc is predetermined by the performance of the sensor node. For example, it takes 1.53 ms and 3.52 ms for TelosB, widely used in WSNs, to perform encryption and decryption using AES-128, respectively [
33]. Since the sum of
tdec and
tenc is five times longer than the time taken to send a 28-byte packet using CC2420 RF transceiver (250 kbps), which is 28 bytes/250 kbps = 0.896 ms,
tdec and
tenc must be taken into account.
tagg is the time we can adjust to improve the energy efficiency while satisfying the QoS.
ttx is the most difficult part to predict accurately because of queueing delay and retransmission from collision and contention. To estimate
ttx, each node updates the average transmission time whenever sensing data is received. Upon receiving sensing data, the receiving node obtains the time taken for the actual transmission and updates the average transmission time using exponentially weighted moving average. The updated average transmission time is then delivered to the neighboring node through a beacon message and used for forwarding.
Algorithm 1 shows the operation of our proposed scheme. When the sensing data are received from node A, the receiving node B computes the time taken for the real transmission through timestamps of the packet (step 1, 2), and updates the average transmission time (step 3). Node B then calculates the remaining time (step 4) and adaptively adjusts the time when the received data is forwarded to the next node. If the remaining time is equal to or less than 0, the data are discarded since the deadline is exceeded so that it is no longer useful (step 5). If the remaining time is larger than y and the current security mode is hop-by-hop security, node B first computes RT1 to check whether data aggregation can be enabled (step 6). We use the reserved bit in the Frame Control field of the 802.15.4 MAC header to denote the current security mode where “0” is hop-by-hop security and “1” is end-to-end security. We ignore the switching time because it consists of a few computations. If the current security mode is end-to-end security, the node just records a timestamp and relay it to the next node without modification (step 9). The term of y is a margin for the QoS requirement. Since the estimated average transmission time and the actual transmission time can be different, we add the term of y to enhance delivery ratio. As y increases, tagg decreases, thereby enhancing the probability of meeting the QoS requirement. However, the term of y has an adverse impact on the energy consumption by reducing tagg. Thus, we try to balance between the delivery ratio and the energy consumption by multiplying rand() with y where rand() is a uniformly random value between 0 and 1. If rand() returns 0, the actual margin is 0. If rand() returns 1, the actual margin becomes y. RT1 is the estimated remaining time when intermediate nodes perform data aggregation. If RT1 is larger than y which means that node B has sufficient time for aggregation, node B computes the aggregation time, tagg, as shown in step 7. The term of makes tagg become larger in the node with a larger hop count since the nodes near the event have more probability for aggregation due to spatial correlation. Once node B computes tagg, it waits for tagg in order to perform data aggregation and send the sensing data using hop-by-hop security as explained in step 7.
| Algorithm 1 Operations of node B upon receiving sensing data from node A. |
| 1: | Record a timestamp of data reception, . |
| 2: | // AB means “from node A to node B” |
| 3: |
|
| 4: | Tdeadline = Tdeadline − |
| 5: | if Tdeadline <= 0,
Discard the data. |
| 6: | else if hop-by-hop security
Retrieve the information of the neighbor node C with the smallest hop h in the FT.
|
| 7: | if RT1 > y, // in case of data aggregation (hop-by-hop security)
Wait for tagg to perform data aggregation.
Record a timestamp, in the data packet.
Send node C the data encrypted by a key shared with node C. |
| 8: | else // in case of no data aggregation (end-to-end security)
if RT2 > y, tagg = RT2−rand()×y
Wait for tagg to perform data aggregation.
Record a timestamp, in the data packet.
Mark end-to-end security in the Frame Control field of the MAC header.
Send node C the data encrypted by a key shared with the BS. |
| 9: | else if end-to-end security
Record a timestamp, in the data packet.
Send node C the data without modification. |
If RT1 is smaller than y, node B cannot use hop-by-hop security in the subsequent sensor nodes. Thus, node B decides to use end-to-end security instead of hop-by-hop security. Node B then calculates RT2 which is the estimated remaining time when end-to-end security is adopted. If RT2 is larger than y, node B has a chance for data aggregation, thus node B waits for tagg after it sends the sensing data using end-to-end security as shown in step 8. It is important to note that node B does not perform aggregation if RT2 is equal to or less than y.
4. Analysis on Energy Consumption of Hop-by-Hop Security and End-to-End Security
In this section, we analyze energy consumption of hop-by-hop security with aggregation and end-to-end security without aggregation in detail. We first assume a very simple topology as shown in
Figure 3 where each circle is a sensor node and arrows denote the direction of transmission. Each node is denoted as
Sx which is a sensor node
x hops away from the BS. We focus on the effect of data aggregation in a specific node,
Sh, which is an intermediate node
h hops away from the BS.
Sh receives data from downstream nodes and can aggregate them into one packet, which is then transmitted to the upstream node
Sh−1.
We assume that the size of a packet is the sum of a header, H, and a payload, P. We refer to Eenc, Edec, and Eauth as the energy consumed by encryption, decryption, and authentication. Authentication adds a HMAC of size T to the packet in order to guarantee authenticity and integrity. Eagg is the energy consumed by aggregating one byte, and Ebyte is the energy consumed by transmitting one byte and receiving one byte. We finally assume that Sh has N packets in the buffer.
Under these assumptions, total energy consumption to deliver
N packets from
Sh to the BS with end-to-end security without aggregation is
It is worth noting that intermediate nodes do not perform encryption and decryption since they use end-to-end security.
Data aggregation can reduce energy by taking advantage of redundancy which means that sensor nodes can send identical packet when they detect the same event. We assume that
Sh aggregate
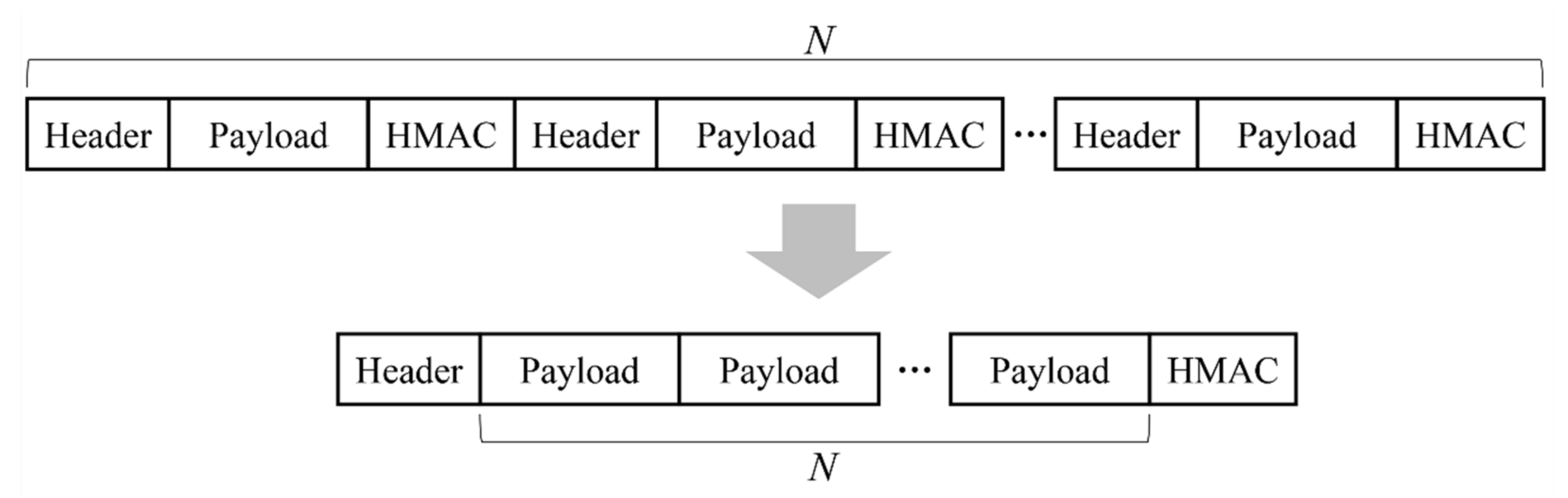
N packets received from downstream nodes into one packet. In the worst case, all
N packets are different and thus all packets must be delivered to the upstream node. Even with this situation, we can make the size of a packet transmitted shorter by aggregation them into one packet. More specifically, the size of
N packets is
N × (
H +
P + T) which becomes
H + N ×
P + T as
Figure 4.
Thus, in the worst case, total energy consumption to transmit
N packets from
Sh to the BS with hop-by-hop security with aggregation is
In this case, energy consumption by communication is reduced by performing data aggregation but energy consumption by encryption and decryption is added due to hop-by-hop security. Obviously, the best case using data aggregation is that all
N packets are identical, i.e., redundant, thus
Sh can aggregate
N packets into only one packet whose size is
H +
P. In this case, total energy consumption becomes
With above equations, we compare end-to-end security without aggregation to hop-by-hop security with aggregation by setting the parameters as shown in
Table 1. We assume that the number of packets to be aggregated is 5. “Data aggregation (best)” and “Data aggregation (worst)” show even smaller energy consumption than no data aggregation by 35.5% and 72.7%, respectively.
From the analysis in this section, we can conclude that hop-by-hop security with data aggregation gives much better energy efficiency than end-to-end security with no data aggregation since energy consumed by communication is much better than energy consumed by encryption, decryption, authentication, and data aggregation.
5. Evaluation
In this section, we compare our proposed scheme to one with no data aggregation at all in terms of energy consumption and packet delivery ratio since we focus on how to balance between energy efficiency and QoS, especially delay, by alternately using hop-by-hop security and end-to-end security. Packet delivery ratio is the ratio of packets received by the BS within deadline over total packets sent by sensor nodes. It is worth noting that it is impossible to compare our scheme with other existing schemes [
23,
24,
25,
26] that consider both QoS and security since they focus on different metrics from ours as introduced in
Section 2. We perform simulations with MATLAB where one BS, located at the center, and 400 sensor nodes are deployed randomly in a field of 200 m × 200 m. The event occurs every second and the event location is uniformly random. When an event occurs, every node within the range of 10 m can detect the event and send the event to the BS according to IEEE 802.15.4. Each node performs data aggregation by discarding data when receiving the same event data or by compressing headers when receiving different event data, and each node is assumed to have infinite energy since nodes near the sink usually spend much more energy, thus fail earlier which makes the entire WSN disabled. We also perform simulations with several margins,
y, in order to identify the influences of
y on energy consumption and delivery ratio. We finally set the deadline to 1 s and 2 s. For more accurate result, we derive an average result based on ten times. The remaining parameters for the simulation based on TelosB platform with TinyOS employed from [
33,
34,
35,
36] are summarized in
Table 1.
Figure 5 shows the energy consumption of both the no data aggregation forwarding method and our proposed method with three different margins when the deadline is 1 s. The proposed method is better than no data aggregation method in terms of energy efficiency by approximately 73.2%, 67.5%, and 63.6% in case of
y = 0, 10, and 20, respectively. This is because the proposed scheme sends a small number of packets by effectively aggregating payloads and HMACs through hop-by-hop security. It is important to note that even though hop-by-hop security consumes more energy to encrypt, decrypt, authenticate, and aggregate data in each hop, this is much smaller than the energy for communicating more data without data aggregation.
Figure 5 also shows that the margin value has an adverse impact on energy consumption. When the margin value increases,
tagg is shortened and the opportunity for data aggregation is reduced, thereby increasing energy consumption slightly.
Figure 6 shows the packet delivery ratio within the deadline of both no data aggregation method and our proposed method with three different margins. Our proposed method with a margin of 20 and the no data aggregation scheme delivered every packet within deadline successfully. In contrast, our proposed method with a margin of 0 and 10 shows lower packet delivery ratio by approximately 3.01% and 2.01%, respectively. It is because additional delay due to data aggregation is introduced when sending data after waiting for
tagg, thereby exceeding the deadline of the data. More specifically, our proposed scheme predicts the transmission time by averaging the actual transmission time as shown in line 3 of algorithm 1. Hence, if congestion in each node occurs, packets cannot be delivered to the BS within the deadline because it takes more time than predicted for the congested sensor node to send data. Even though our proposed method with a margin of 0 and 10 shows lower packet delivery ratio than one with no data aggregation, it is very important to note that our proposed method with a margin of 20 can achieve 100% of delivery ratio with much lower energy consumption by 63.6% than one with no data aggregation. This is because adding a fixed margin value to each hop is good for not violating the deadline and still helps nodes with larger hops to perform sufficient data aggregation.
Figure 7 shows the average energy consumption within the deadline when the deadline is 2 s. In this case, each node waits for longer time, thus it can have more opportunity to aggregate packets. As a result, it shows slightly smaller energy consumption than the case with deadline of 1 s. However, no data aggregation is not affected by the deadline because it does not perform data aggregation. Thus, we can find that our proposed scheme conserves much more energy than one with no data aggregation by approximately 76.2%, 70.1%, and 65.6% in case of
y = 0, 10, and 20. It is worth noting that we can reduce more energy if we have longer deadline. We show the packet delivery ratio with the deadline of 2 s in
Figure 8. You can verify that packet delivery ratio is almost the same as the case with deadline of 2 s because we spend additional time for data aggregation, not for transmitting faster. Compared with
Figure 6, similar percentage of packets exceed the deadline due to congestion in
Figure 8.
Figure 9 shows the average energy consumption when the number of nodes increases. In no aggregation case, the energy consumption increases rapidly since more sensor nodes detect the same event and they send all information individually. On the contrary, energy consumption in our proposed method increases more slowly as the number of nodes increases. This is because more redundant packets are aggregated in the intermediate node when more sensor nodes detect the same event. It is worth noting that our proposed scheme outperforms one with no data aggregation by about 89.1% in the case that
y is 0 and the number of nodes is 2000.
In
Figure 10, we finally show the tradeoffs between the average energy consumption and the deadline violation probability when the margin value changes. As the average energy consumption increases from 5.68 J to 7.87 J, the deadline violation probability decreases from 0.301 to 0. Thus, with our proposed scheme, we can obtain no deadline violation by sacrificing approximately 28.9% of energy consumption. However, it is important to note that our proposed scheme still consume less energy than one with no data aggregation by 63.6%.