IoT-Inspired Framework of Intruder Detection for Smart Home Security Systems
Abstract
:1. Introduction
1.1. Research Field
1.2. Research Motivation
- Detection of real-time identity-based parameters of intruder personnel has not been addressed specifically by the researchers. it is essential to develop user-centered decision-making strategies.
- Minimal research has been presented for regularized monitoring of home security and related attributes by the monitoring officials, thereby compromising the home security.
- Another factor that has been minimally explored in state-of-the-art research is the incorporation of ANFIS-PSO for interactive intruder detection decision-making.
- Finally, limited work has been done to quantify the identity parameters for effective decision-making by security officials and users.
1.3. State-of-the-Art Research Objectives
- Monitors identity-based attributes by using IoT devices equipped in the smart mat in real time for the identification of intruders.
- Classifies identity-based attributes in 2 classes, Authentic Class and Non-Authentic Class using the Bayesian Belief Model (BBM) which is quantified in probabilistic feature of Probability of Authenticity (PoA).
- Enabling data analysis in time-sensitive manner, using the Temporal Granulation Process for collecting and processing information. It is further quantified into the Authentic Index (AI) for the prediction of identity-related information over the Fog-Cloud computing framework.
- Predicts the probability of authenticity based on temporal aspects of AI value by using the Adaptive neuro-fuzzy inference system (ANFIS) mechanism.
- State-of-the-art validation of the presented framework performance in comparison to decision-modeling techniques.
2. Literature Review
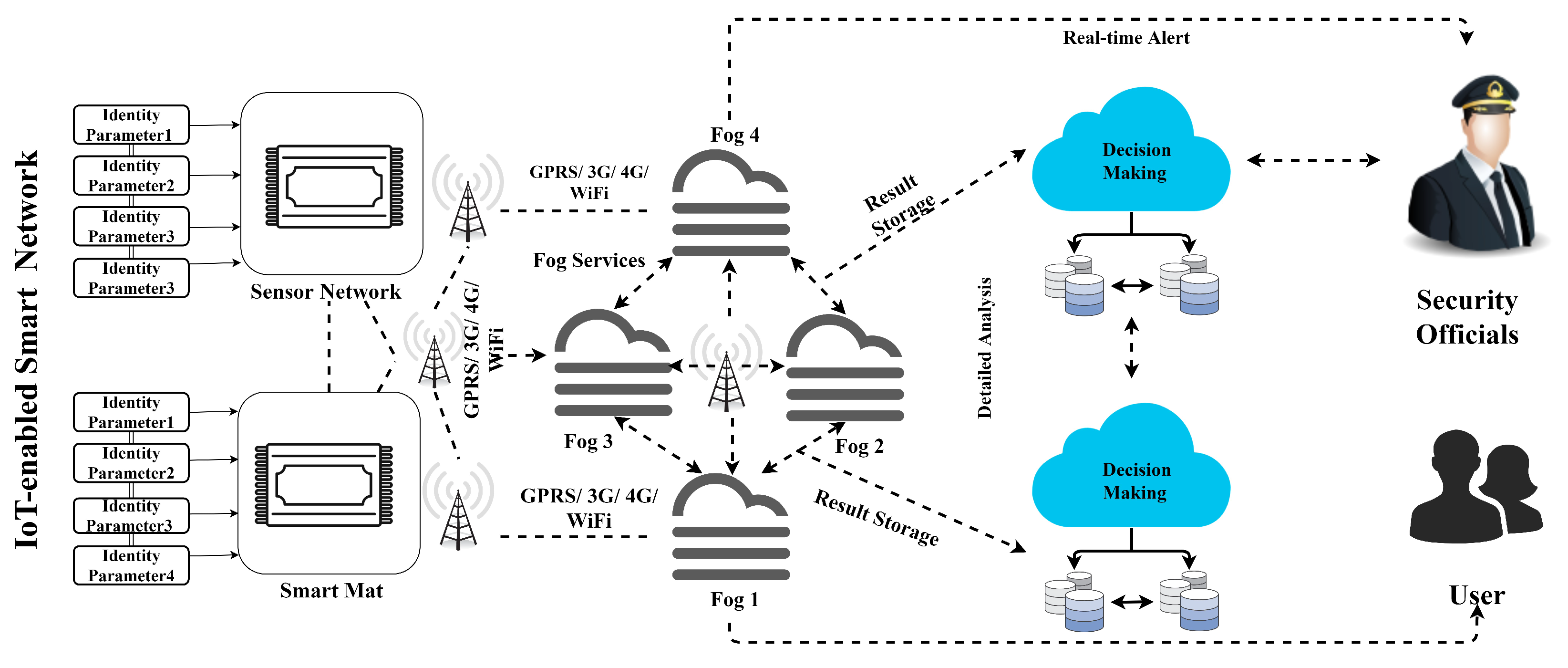
3. Proposed Methodology
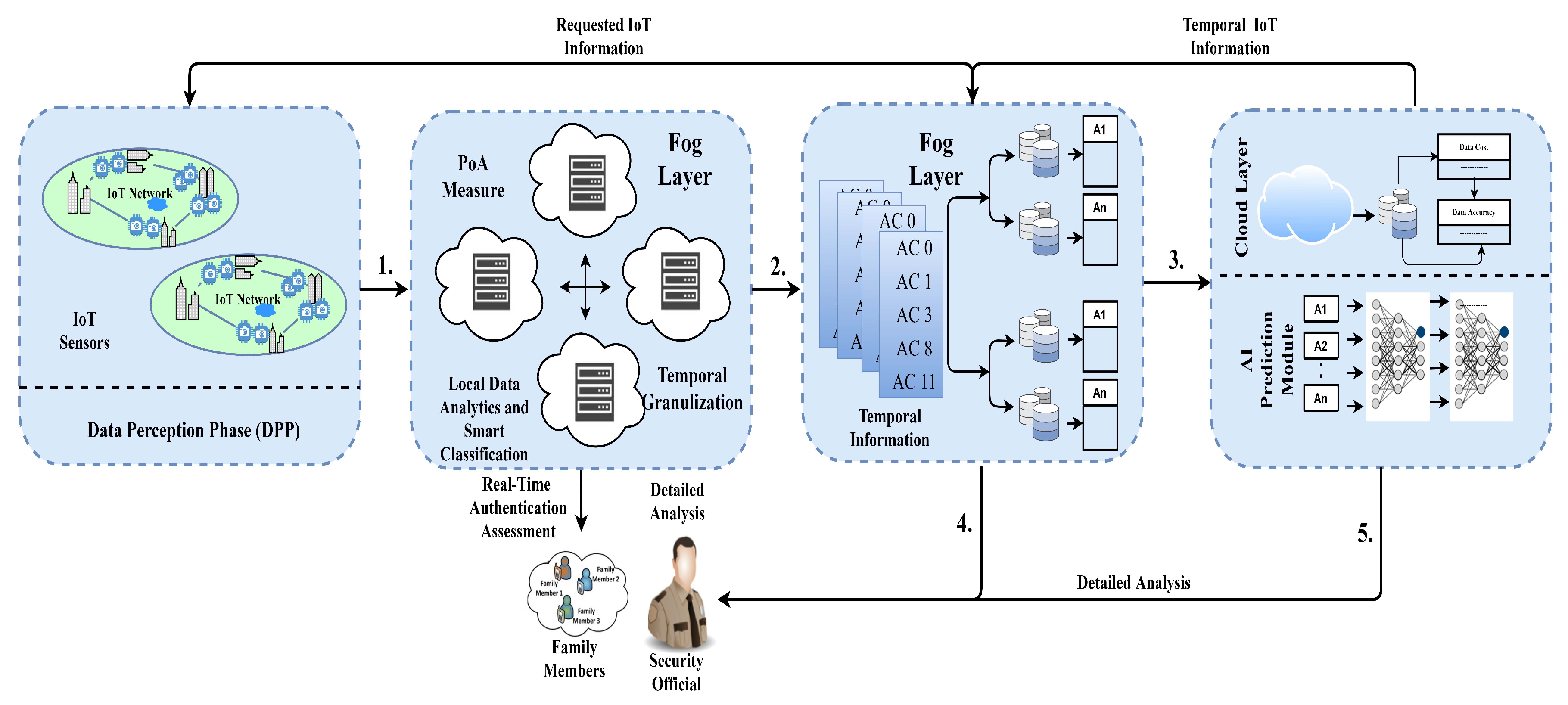
3.1. Data Perception Phase (DPP)
3.2. Data Analysis Phase (Dap)
- Authentic Class:This data set comprises of those parameter measures which indicate non-intruder or authentic personnel. These parametric values are represented safe as well as compliance values with the security measures. Moreover, data perturbation including increased weight and abnormal shoe-based parameters can be detected using Expectation-Maximization [41] technique.
- Non-Authentic Class:This class is intended to acquire parameter values that are vulnerable and indicates the presence of unauthentic personnel. On the basis of data classification, the Non-Authentic Class has a detrimental effect for home security and thus it is indispensable to assess such measures for providing prevention against intrusion.
Classification Based on BBM
| P(Lj)P(Ai/Lj) = P(a1,a2, …, an, Lj) |
| = P(a1/a2, …, an, Lj)P(a2, …, an, Lj) |
|
= P(a1/a2, …, an, Lj)P(a2/a3, …, an, Lj)P(a3, …, an, Lj) = P(a1/a2, …, an, Lj)P(a2/a3, …, anLj), …, P(an−1/an, …, anLj) × P(an/Lj)P(Lj) |
| P(Lj) = P(Lj)P(ai/Lj) |
| P() = P(Lj)P(ai/Lj)/P(a) |
3.3. Data Extraction Phase (Dep)
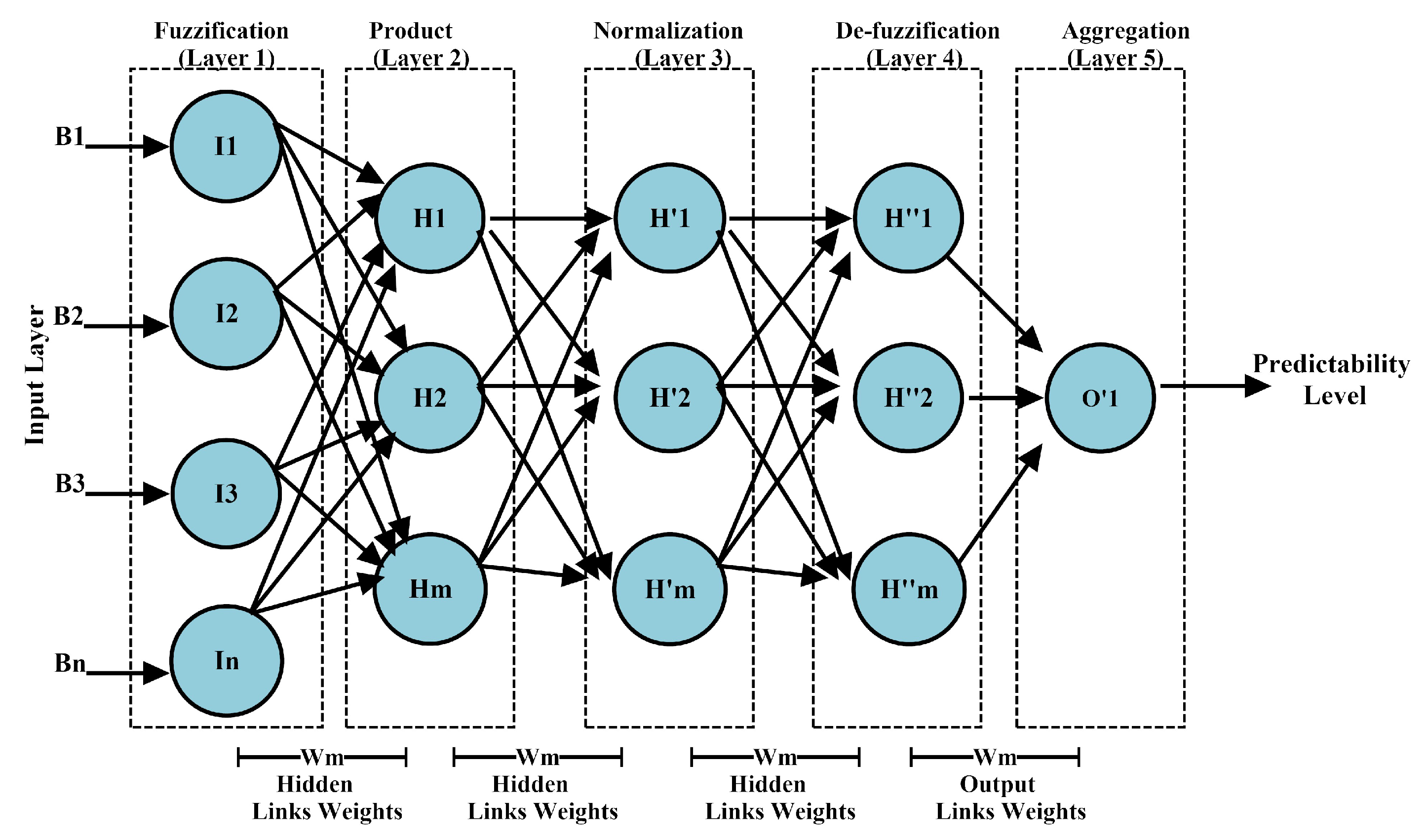
3.4. Intelligent Prediction Phase (IPP)
- (a) Fuzzification (Phase 1): The first phase of the ANFIS system is fuzzy unit, which uses Membership Functions (MFs) to convert inputs into a fuzzy set. Every node in this phase is responsive and shown as follows:where the gaussian membership function is represented as , z is supposed as the input is fed to the node j, and is supposed as the descriptive attribute linked with a node function [46]. In the present context, spatio-time data measures for several identity-based attributes in the initial fuzzification phase are actually provided.
- (b) Product rule (Phase 2): The neurons in the first phase transmit the input data to the next phase by performing the element-based product formation and are mathematically represented as follows:where Xj(z) and Ej(s) represent the nodes in phase 2.
- (c) Normalization (Phase 3): Every neurons of this phase calculates the proportion of the single firing strength rule to the amount of each firing strength rule as shown in Equation (3). The firing strength of is indicated and simplified as follows:
- (d) De-fuzzification (Phase 4): This phase is accountable for evaluating the contribution of the jth rule to the final output. The following standardized consequent variables are identified as the , , and attributes. The de-fuzzification mechanism in this phase is as follows:
- (e) Output generation (Phase 5): The output phase is considered to measure the sum of all outputs from all nodes, and to measure the ultimate value as represented in Equation (5):
4. Experimental Implementation
- Identification of the temporal delay time in the generation of identity-based findings by different computational phases.
- Estimate the categorization efficacy for the presented BBM model of data classification.
- Quantitative identity-based prediction estimation for intruder detection.
- Analyze the prediction model’s reliability across increased number of data segments.
- Determine the system stability to identify the presented model’s effectiveness.
4.1. Simulation Environment
4.2. Temporal Delay Determination
4.3. Classification Efficiency
- The proposed model can be noted to report a mean precision measure of 93.09% for the data sets collected. Compared to this, DT achieved an accuracy of 91.68% and 91.37% was recorded by SVM. Henceforth, the proposed BBM model is more efficient than other classification methods.
- The presented approach can record a higher value of 92.03% as compared with DT (90.10%) and SVM (90.54%) for specificity analysis. It shows that the proposed model is better.
- Another aspect for performance assessment of the proposed model is sensitivity analysis. In the current scenario, it can be seen that the presented model has a high value of 92.19% relative to 91.29% for DT and 91.28% for SVM. Henceforth, based on data classification, the proposed model is more effective and reliable.
4.4. Prediction Efficiency
- The proposed model has recorded a higher value of 93.66% as compared with ANN (89.57%), SVM (90.55%), and KNN (92.19%) for accuracy analysis. Figure 6a shows that the model proposed is much better.
- The presented model has registered higher value of 93.59% as compared with ANN (87.53%), SVM (88.56%), and KNN (89.29%) for sensitivity analysis as shown in Figure 6b.
- The proposed model has attained a higher value of 93.68% as compared with ANN (85.57%), SVM (89.45%), and KNN (91.32%) for F-Measure analysis. Figure 6c shows that the model proposed is much better.
- Results of the proposed model is also estimated in terms of the Coefficient of Determination analysis as shown in Figure 6d. In the current scenario, it can be found that the presented model has a comparatively higher value of 95.63% which is far better as compared to other models.
4.5. Reliability Assessment
4.6. Stability Assessment
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef] [Green Version]
- Bhatia, M.; Sood, S.K. Temporal informative analysis in smart-ICU monitoring: M-HealthCare perspective. J. Med. Syst. 2016, 40, 190. [Google Scholar] [CrossRef]
- Lee, I.; Lee, K. The Internet of Things (IoT): Applications, investments, and challenges for enterprises. Bus. Horiz. 2015, 58, 431–440. [Google Scholar] [CrossRef]
- Bhatia, M.; Sood, S.K.; Kaur, S. Quantum-based predictive fog scheduler for IoT applications. Comput. Ind. 2019, 111, 51–67. [Google Scholar] [CrossRef]
- Sheth, A. Internet of things to smart iot through semantic, cognitive, and perceptual computing. IEEE Intell. Syst. 2016, 31, 108–112. [Google Scholar] [CrossRef]
- Stojkoska, B.L.R.; Trivodaliev, K.V. A review of Internet of Things for smart home: Challenges and solutions. J. Clean. Prod. 2017, 140, 1454–1464. [Google Scholar] [CrossRef]
- Bhatia, M.; Kaur, S.; Sood, S.K. IoT-Inspired Smart Toilet System for Home-Based Urine Infection Prediction. ACM Trans. Comput. Healthc. 2020, 1, 1–25. [Google Scholar] [CrossRef]
- Javed, M.A.; Zeadally, S.; Hamida, E.B. Data analytics for Cooperative Intelligent Transport Systems. Veh. Commun. 2019, 15, 63–72. [Google Scholar] [CrossRef]
- Bhatia, M.; Manocha, A. Cognitive Framework of Food Quality Assessment in IoT-inspired Smart Restaurants. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Westermann, O.; Förch, W.; Thornton, P.; Körner, J.; Cramer, L.; Campbell, B. Scaling up agricultural interventions: Case studies of climate-smart agriculture. Agric. Syst. 2018, 165, 283–293. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Andreev, S.; Petrov, V.; Huang, K.; Lema, M.A.; Dohler, M. Dense Moving Fog for Intelligent IoT: Key Challenges and Opportunities. IEEE Commun. Mag. 2019, 57, 34–41. [Google Scholar] [CrossRef] [Green Version]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar]
- Bhatia, M.; Sood, S.K. Quantum Computing-inspired Network Optimization for IoT Applications. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Chiang, M.; Zhang, T. Fog and IoT: An overview of research opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Jacobsson, A.; Boldt, M.; Carlsson, B. A risk analysis of a smart home automation system. Future Gener. Comput. Syst. 2016, 56, 719–733. [Google Scholar] [CrossRef] [Green Version]
- Yassine, A.; Singh, S.; Hossain, M.S.; Muhammad, G. IoT big data analytics for smart homes with fog and cloud computing. Future Gener. Comput. Syst. 2019, 91, 563–573. [Google Scholar] [CrossRef]
- Boveiri, H.R.; Khayami, R.; Elhoseny, M.; Gunasekaran, M. An efficient Swarm-Intelligence approach for task scheduling in cloud-based internet of things applications. J. Ambient Intell. Hum. Comput. 2019, 10, 3469–3479. [Google Scholar] [CrossRef]
- Kim, T.H.; Hong, Y.S. Prediction of Body Weight of a Person Lying on a Smart Mat in Nonrestraint and Unconsciousness Conditions. Sensors 2020, 20, 3485. [Google Scholar] [CrossRef]
- Matthies, D.J.; Elvitigala, D.S.; Muthukumarana, S.; Huber, J.; Nanayakkara, S. CapMat: A smart foot mat for user authentication. In Proceedings of the 10th Augmented Human International Conference 2019, Reims, France, 11–12 March 2019; pp. 1–2. [Google Scholar]
- Huang, D.Y.; Apthorpe, N.; Li, F.; Acar, G.; Feamster, N. Iot inspector: Crowdsourcing labeled network traffic from smart home devices at scale. Proc. ACM Interact. Mob. Wearable Ubiquit. Technol. 2020, 4, 1–21. [Google Scholar] [CrossRef]
- Minoli, D. Positioning of blockchain mechanisms in IOT-powered smart home systems: A gateway-based approach. Internet Things 2020, 10, 100147. [Google Scholar] [CrossRef]
- Mallikarjuna, B. Feedback-Based Resource Utilization for Smart Home Automation in Fog Assistance IoT-Based Cloud. Int. J. Fog Comput. (IJFC) 2020, 3, 41–63. [Google Scholar] [CrossRef]
- Desai, R.; Gandhi, A.; Agrawal, S.; Kathiria, P.; Oza, P. IoT-Based Home Automation with Smart Fan and AC Using NodeMCU. In Proceedings of ICRIC 2019; Springer: Heidelberg, Germany, 2020; pp. 197–207. [Google Scholar]
- Popa, D.; Pop, F.; Serbanescu, C.; Castiglione, A. Deep learning model for home automation and energy reduction in a smart home environment platform. Neural Comput. Appl. 2019, 31, 1317–1337. [Google Scholar] [CrossRef]
- Ranjan, J.; Yao, Y.; Whitehouse, K. An RF doormat for tracking people’s room locations. In Proceedings of the 2013 ACM International Joint Conference on Pervasive and Ubiquitous Computing, Zurich, Switzerland, 12–16 September 2013; pp. 797–800. [Google Scholar]
- Cheng, J.; Sundholm, M.; Zhou, B.; Hirsch, M.; Lukowicz, P. Smart-surface: Large scale textile pressure sensors arrays for activity recognition. Pervas. Mob. Comput. 2016, 30, 97–112. [Google Scholar] [CrossRef]
- Sokullu, R.; Akkaş, M.A.; Demir, E. IoT Supported Smart Home for the Elderly. Internet Things 2020, 11, 100239. [Google Scholar] [CrossRef]
- Suciu, G.; Suciu, V.; Martian, A.; Craciunescu, R.; Vulpe, A.; Marcu, I.; Halunga, S.; Fratu, O. Big data, internet of things and cloud convergence–an architecture for secure e-health applications. J. Med. Syst. 2015, 39, 141. [Google Scholar] [CrossRef]
- Sun, E.; Zhang, X.; Li, Z. The internet of things (IOT) and cloud computing (CC) based tailings dam monitoring and pre-alarm system in mines. Saf. Sci. 2012, 50, 811–815. [Google Scholar] [CrossRef]
- Sowjanya, G.; Nagaraju, S. Design and implementation of door access control and security system based on IOT. In Proceedings of the 2016 International Conference on Inventive Computation Technologies (ICICT), Coimbatore, India, 26–27 August 2016; Volume 2, pp. 1–4. [Google Scholar]
- Sha, K.; Wei, W.; Yang, T.A.; Wang, Z.; Shi, W. On security challenges and open issues in Internet of Things. Future Gener. Comput. Syst. 2018, 83, 326–337. [Google Scholar] [CrossRef]
- Dabbagh, M.; Rayes, A. Internet of things security and privacy. In Internet of Things from Hype to Reality; Springer: Heidelberg, Germany, 2019; pp. 211–238. [Google Scholar]
- Ammar, M.; Russello, G.; Crispo, B. Internet of Things: A survey on the security of IoT frameworks. J. Inf. Secur. Appl. 2018, 38, 8–27. [Google Scholar] [CrossRef] [Green Version]
- Mendez Mena, D.; Papapanagiotou, I.; Yang, B. Internet of things: Survey on security. Inf. Secur. J. A Glob. Persp. 2018, 27, 162–182. [Google Scholar] [CrossRef]
- Stergiou, C.; Psannis, K.E.; Kim, B.G.; Gupta, B. Secure integration of IoT and cloud computing. Future Gener. Comput. Syst. 2018, 78, 964–975. [Google Scholar] [CrossRef]
- Sun, W.; Cai, Z.; Li, Y.; Liu, F.; Fang, S.; Wang, G. Security and privacy in the medical internet of things: A review. Secur. Commun. Netw. 2018, 2018, 5978636. [Google Scholar] [CrossRef]
- Dastjerdi, A.V.; Buyya, R. Fog computing: Helping the Internet of Things realize its potential. Computer 2016, 49, 112–116. [Google Scholar] [CrossRef]
- Tang, B.; Chen, Z.; Hefferman, G.; Pei, S.; Wei, T.; He, H.; Yang, Q. Incorporating intelligence in fog computing for big data analysis in smart cities. IEEE Trans. Ind. Inform. 2017, 13, 2140–2150. [Google Scholar] [CrossRef]
- Atlam, H.F.; Walters, R.J.; Wills, G.B. Fog computing and the internet of things: A review. Big Data Cogn. Comput. 2018, 2, 10. [Google Scholar] [CrossRef] [Green Version]
- Moon, T.K. The expectation-maximization algorithm. IEEE Signal Process. Mag. 1996, 13, 47–60. [Google Scholar] [CrossRef]
- Liao, Y.; Xu, B.; Liu, X.; Wang, J.; Hu, S.; Huang, W.; Luo, K.; Gao, L. Using a Bayesian belief network model for early warning of death and severe risk of HFMD in Hunan province, China. Stochastic Environ. Res. Risk Assess. 2018, 32, 1531–1544. [Google Scholar] [CrossRef] [Green Version]
- Nauck, D.; Klawonn, F.; Kruse, R. Foundations of Neuro-Fuzzy Systems; John Wiley & Sons, Inc.: New York, NY, USA, 1997. [Google Scholar]
- Jang, J.S. ANFIS: Adaptive-network-based fuzzy inference system. IEEE Trans. Syst. Man Cybernet. 1993, 23, 665–685. [Google Scholar] [CrossRef]
- Nedjah, N.; de Macedo Mourelle, L. Fuzzy Systems Engineering: Theory and Practice; Springer Science & Business Media: Heidelberg/Germany, Germany, 2005; Volume 181. [Google Scholar]
- Reddy, C.S.; Raju, K. An improved fuzzy approach for COCOMO’s effort estimation using gaussian membership function. J. Softw. 2009, 4, 452–459. [Google Scholar] [CrossRef]
- Gupta, H.; Vahid Dastjerdi, A.; Ghosh, S.K.; Buyya, R. iFogSim: A toolkit for modeling and simulation of resource management techniques in the Internet of Things, Edge and Fog computing environments. Softw. Pract. Exp. 2017, 47, 1275–1296. [Google Scholar] [CrossRef] [Green Version]






| Related Work | Fog | IoT | Temporal Analysis | Classification | Cognitive Decision | User-Centered | Time-Sensitive | Precision | Numerical | Stability | Reliability | Security Protocols |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Ranjan et al. (2013) [26] | NA | A | NA | A | NA | NA | NA | NA | NA | NA | NA | NA |
| Sowajanya et al. (2016) [31] | NA | A | NA | NA | NA | NA | NA | NA | NA | NA | NA | A |
| Sun et al. (2012) [30] | NA | A | NA | A | NA | NA | NA | NA | NA | NA | NA | A |
| Cheng et al. (2016) [27] | NA | A | NA | NA | NA | NA | A | A | NA | A | A | A |
| Sokullu et al. (2020) [28] | NA | A | A | A | NA | NA | A | A | NA | NA | A | A |
| Suciu et al. (2015) [29] | NA | A | NA | A | NA | NA | NA | A | NA | A | NA | A |
| Matthies et al. (2019) [20] | NA | A | NA | NA | NA | NA | NA | A | NA | NA | A | A |
| Chiang et al. (2016) [15] | A | A | A | A | NA | NA | NA | NA | NA | NA | NA | NA |
| Proposed Technique | A | A | A | A | A | A | A | A | A | A | A | A |
| AI Analysis Procedure |
|---|
| 1: Input IoT measures for n identity-based attributes and relevant PoA measures. , , , are the associated weights. |
| 2: Set AIt = Null(0). |
| 3: Assess PoA measure of identity-based attribute 1 with pre-defined threshold measure. |
| 4: If PoA1 > 1, Then Sum × PoA1 to AI. |
| 5: Assess PoA measure of identity-based attribute 2 with pre-defined threshold measure. |
| 6: If PoA2 > 2, Then Sum × PoA2 to AI |
| *Repeat for all attribute* |
| 7: Evaluate PoA measure of nth identity-based attribute with prefixed threshold measure. |
| 8: If PoAn > n, Then Sum × PoAn to AI |
| 9: Cumulative AI = × PoA1+ × PoA2+ × PoA3+....... × PoAn |
| Model | BBM Classifier | DT Classifier | SVM Classifier | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Dataset | Prec | Spec | Sens | Prec | Spec | Sens | Prec | Spec | Sens |
| 5000 | 94.45% | 92.04% | 93.82% | 92.82% | 89.02% | 90.67% | 92.42% | 89.14% | 90.11% |
| 10,000 | 92.78% | 91.94% | 92.32% | 91.52% | 91.22% | 91.72% | 91.02% | 91.69% | 91.04% |
| 15,000 | 93.57% | 91.98% | 92.52% | 91.42% | 90.33% | 92.34% | 90.06% | 90.43% | 92.08% |
| 20,000 | 93.73% | 90.84% | 91.32% | 92.52% | 89.14% | 90.49% | 92.32% | 90.63% | 90.59% |
| 25,000 | 91.56% | 92.44% | 92.54% | 91.22% | 90.22% | 92.09% | 91.64% | 91.26% | 92.39% |
| 30,000 | 92.32% | 90.32% | 91.32% | 92.21% | 91.14% | 91.07% | 92.76% | 91.02% | 91.83% |
| 35,000 | 93.82% | 89.93% | 91.31% | 91.26% | 89.82% | 90.24% | 91.14% | 90.79% | 89.16% |
| 40,000 | 92.32% | 90.54% | 92.62% | 92.12% | 89.45% | 91.15% | 92.06% | 89.89% | 91.34% |
| 45,000 | 91.85% | 89.35% | 92.42% | 90.44% | 90.10% | 92.04% | 89.18% | 90.42% | 92.14% |
| 50,000 | 92.42% | 91.01% | 91.72% | 91.32% | 90.59% | 91.10% | 91.18% | 90.14% | 91.60% |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahanger, T.A.; Tariq, U.; Ibrahim, A.; Ullah, I.; Bouteraa, Y. IoT-Inspired Framework of Intruder Detection for Smart Home Security Systems. Electronics 2020, 9, 1361. https://doi.org/10.3390/electronics9091361
Ahanger TA, Tariq U, Ibrahim A, Ullah I, Bouteraa Y. IoT-Inspired Framework of Intruder Detection for Smart Home Security Systems. Electronics. 2020; 9(9):1361. https://doi.org/10.3390/electronics9091361
Chicago/Turabian StyleAhanger, Tariq Ahamed, Usman Tariq, Atef Ibrahim, Imdad Ullah, and Yassine Bouteraa. 2020. "IoT-Inspired Framework of Intruder Detection for Smart Home Security Systems" Electronics 9, no. 9: 1361. https://doi.org/10.3390/electronics9091361







