Revisit of Password-Authenticated Key Exchange Protocol for Healthcare Support Wireless Communication
Abstract
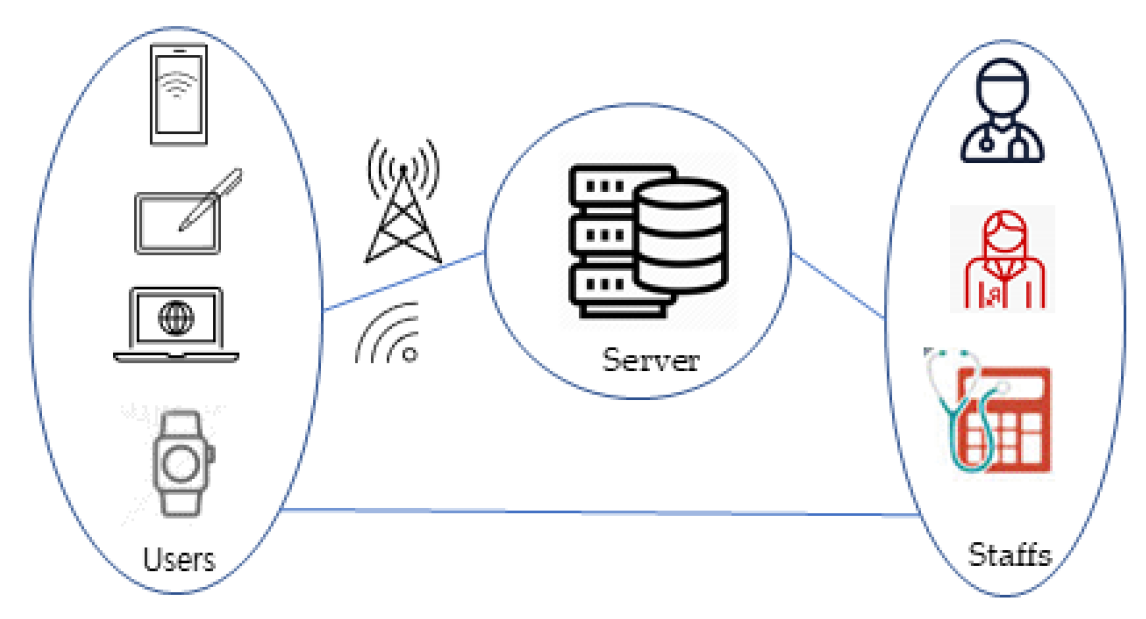
1. Introduction
2. Materials and Methods
- A can eavesdrop, insert, intercept, alter, and delete messages exchanged among the protocol, user UA, user UB, and the server S.
- A may be a legitimate protocol participant (an insider), an external party (an outsider), or some combination of the two.
- User anonymity: Even if an adversary eavesdrops on the messages transmitted in the communication parties, the user’s identity should be protected.
- Mutual authentication: Two partnering users and the server can authenticate one another.
- Session key security: No one except for those who are partnered can establish the session key.
- Known-key security: When a particular session key is lost, it does not reveal the other session keys.
- Forward secrecy: Even if a user’s password is compromised, it does not reveal past session keys or the new password.
- Robustness: The protocol should withstand various types of attacks, such as offline password guessing, replay, insider, and impersonation.
3. Results
3.1. Revisit of 3WPAKE Protocol
3.2. Security Analysis of 3WPAKE Protocol
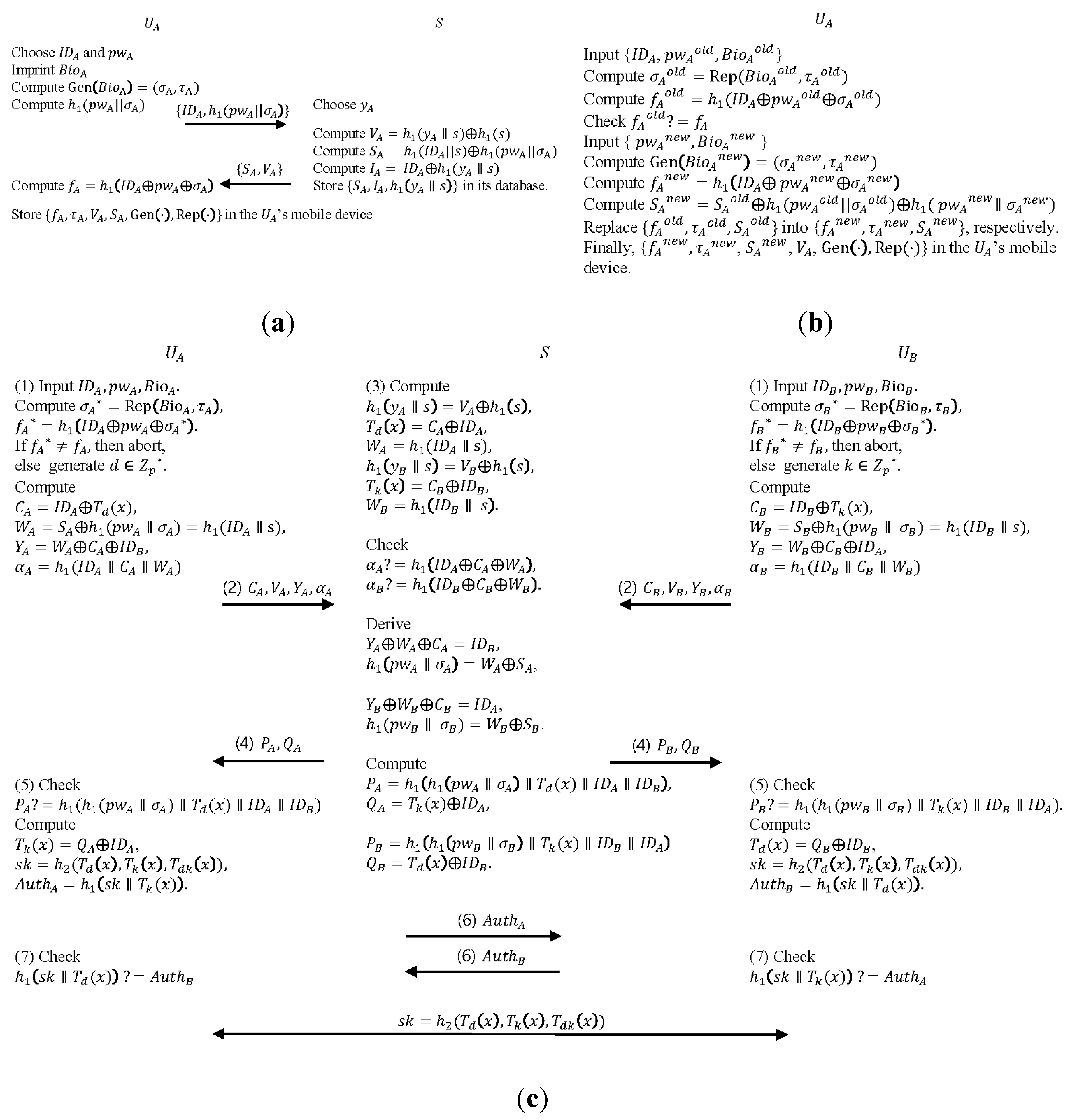
3.3. The SBAKE Protocol
3.4. Security Analysis and Proof of SBAKE Protocol
3.4.1. Simulation using AVISPA
3.4.2. Formal Security Proof
| Algorithm 1: Algorithm |
| Eavesdrop login request message {CA,YA,αA,VA} |
| Call the Reveal oracle. Let (IDA′,CA′,WA′) ← Reveal (αA) |
| Call the Reveal oracle. Let (IDA″, s′) ← Reveal (WA’) |
| if (CA′ = CA) and (IDA′ = IDA″) then |
| Accept IDA′ as the correct IDA of user UA and s’ as the correct private key of S |
| Compute Td(x) = CA ⊕ IDA |
| Eavesdrop login response message {PA,QA} |
| Call the Reveal oracle. |
| Let (h1(pwA′σA′),Td(x)’,IDA‴,IDB‴) ← Reveal (PA) |
| Call the Reveal oracle. |
| Let (pwA″,σA″) ← Reveal (h1(pwA′σA′)) |
| if (Td(x)’ = Td(x)) and (IDA‴ = IDA) then |
| Accept pwA″ and σA″ of the correct password and biometric key of user UA |
| Compute SA=h1(pwAσA) ⊕ h1(IDAs) |
| Compute Tk(x) = QA ⊕ IDA |
| Evesdrop authentication message {AuthA} |
| Call the Reveal oracle. |
| Let (sk’,Tk(x)’) ← Reveal (AuthA) |
| if (Tk(x)’ = Tk(x)) then |
| Accept SA as the correct shared secret key between UA and S, sk’ as the session key sk shared between UA and UB |
| return 1 |
| else |
| reutrn 0 |
| end if |
| else |
| return 0 |
| end if |
| else |
| return 0 |
| end if |
3.4.3. Informal Security Proof
4. Discussion
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Bellovin, S.M.; Merritt, M. Encrypted key exchange: Password-based protocols secure against dictionary attacks. In Proceedings of the IEEE Symposium on Research in Security and Privacy, Oakland, CA, USA, 4–6 May 1992; pp. 72–84. [Google Scholar] [CrossRef]
- Khan, M.K.; Zhang, J. Improving the security of ‘a flexible biometrics remote user authentication scheme’. Comput. Standards Interfaces 2007, 29, 82–85. [Google Scholar] [CrossRef]
- Tseng, Y.M.; Yu, C.H.; Wu, T.Y. Towards scalable key management for secure multicast communication. Inf. Technol. Control 2012, 41, 173–182. [Google Scholar] [CrossRef]
- Sun, H.; Wen, Q.; Zhang, H.; Jin, Z. A strongly secure pairing-free certificateless authenticated key agreement protocol for low-power devices. Inf. Technol. Control 2013, 42, 113–123. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Li, G.; Ma, Z. An improved password-based remote user authentication protocol without smart cards. Inf. Technol. Control 2013, 42, 150–158. [Google Scholar] [CrossRef]
- Roy, S.; Chatterjee, S.; Das, A.K.; Chattopadhyay, S.; Kumari, S.; Jo, M. Chaotic map-based anonymous user authentication scheme with user biometrics and fuzzy extractor for crowdsourcing Internet of Things. IEEE Internet Things J. 2018, 5, 2884–2895. [Google Scholar] [CrossRef]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. LAMHU: A new lightweight robust scheme for mutual users authentication in healthcare applications. Secur. Commun Netw. 2019. [Google Scholar] [CrossRef]
- Lee, T.F.; Liu, J.L.; Sung, M.J.; Yang, S.B.; Chen, C.M. Communication-efficient three-party protocols for authentication and key agreement. Comput. Math. Appl. 2009, 58, 641–648. [Google Scholar] [CrossRef][Green Version]
- Lu, Y.; Li, L.; Peng, H.; Yang, Y. A three-party password-based authenticated key exchange protocol for wireless communications. Inf. Technol. Control 2015, 44, 404–409. [Google Scholar] [CrossRef]
- Jeon, W.; Kim, J.; Nam, J.; Lee, Y.; Won, D. An enhanced secure authentication scheme with anonymity for wireless environments. IEICE Trans. Commun. 2012, 95, 2505–2508. [Google Scholar] [CrossRef]
- Farash, M.S.; Attari, M.A. An enhanced and secure three-party password-based authenticated key exchange protocol without using server’s public-keys and symmetric cryptosystems. Inf. Technol. Control 2014, 43, 143–150. [Google Scholar] [CrossRef]
- Liu, T.; Pu, Q.; Zhao, Y.; Wu, S. ECC-based password-authenticated key exchange in the three-party setting. Arab. J. Sci. Eng. 2013, 38, 2069–2077. [Google Scholar] [CrossRef]
- Chien, H.Y.; Wu, T.C. Provably secure password-based three-party key exchange with optimal message steps. Comput. J. 2009, 52, 646–655. [Google Scholar] [CrossRef]
- Guo, C.; Chang, C.C. Chaotic maps-based password-authenticated key agreement using smart cards. Commun. Nonlinear Sci. Numer. Simul. 2013, 18, 1433–1440. [Google Scholar] [CrossRef]
- Yau, W.; Phan, R. Cryptanalysis of a chaotic map-based password-authenticated key agreement protocol using smart cards. Nonlinear Dyn. 2015, 79, 809–821. [Google Scholar] [CrossRef]
- Stallings, W. Cryptography and Network Security: Principles and Practices, 4th ed.; Prentice Hall: Upper Saddle River, NJ, USA, 2006. [Google Scholar]
- Huang, H.F. A simple three-party password-based key exchange protocol. Int. J. Commun. Syst. 2009, 22, 857–862. [Google Scholar] [CrossRef]
- Yoon, E.J.; Yoo, K.Y. Cryptanalysis of a simple three-party password-based key exchange protocol. Int. J. Commun. Syst. 2011, 24, 532–542. [Google Scholar] [CrossRef]
- Tallapally, S. Security enhancement on simple three party PAKE protocol. Inf. Technol. Control 2012, 41, 15–22. [Google Scholar] [CrossRef]
- Chen, C.M.; Wang, K.H.; Yeh, K.H.; Xiang, B.; Wu, T.Y. Attacks and solutions on a three-party password-based authenticated key exchange protocol for wireless communications. J. Ambient Intell. Hum. Comput. 2019, 10, 3133–3142. [Google Scholar] [CrossRef]
- Zhang, L.P.; Zhu, S.H.; Tang, S. Privacy protection for telecare medicine information system using a chaotic map-based three-factor authenticated key agreement scheme. IEEE J. Biomed. Health Inform. 2015, 2168–2194. [Google Scholar] [CrossRef]
- Lee, T.F. Efficient and secure temporal credential-based authenticated key agreement using extended chaotic maps for wireless sensor networks. Sensors 2015, 15, 14960–14980. [Google Scholar] [CrossRef]
- Renuka, K.; Kumar, S.; Kumari, S.; Chen, C.M. Cryptanalysis and improvement of a privacy-preserving three-factor authentication protocol for wireless sensor networks. Sensors 2019, 19, 4625. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Lee, J.H.; Sherratt, R. Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans. Consum. Electron. 2014, 60, 30–37. [Google Scholar] [CrossRef]
- Ravanbakhsh, N.; Nazari, M. An efficient improvement remote user mutual authentication and session key agreement scheme for E-health care system. Multimed. Tools Appl. 2016, 1–34. [Google Scholar] [CrossRef]
- Lee, C.C.; Hsu, C.W. A secure biometric-based remote user authentication with key agreement scheme using extended chaotic maps. Nonlinear Dyn. 2013, 71, 201–211. [Google Scholar] [CrossRef]
- Mishra, D.; Das, A.K.; Mukhopadhyay, S. A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Syst. Appl. 2014, 41, 8129–8143. [Google Scholar] [CrossRef]
- Chatterjee, S.; Roy, S.; Das, A.K.; Chattopadhyay, S.; Kumar, N. Secure biometric-based authentication scheme using Chebyshev chaotic map for multi-server environment. IEEE Trans. Dependable Secur. Comput. 2016. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumari, S.; Li, X.; Wu, F. Design of an efficient and provably secure anonymity preserving three-factor user authentication and key agreement scheme for TMIS. Secur. Commun. Netw. 2016, 9, 1983–2001. [Google Scholar] [CrossRef]
- Wei, F.; Ma, J.; Jiang, Q.; Shen, J.; Ma, C. Cryptanalysis and improvement of an enhanced two-factor user authentication scheme in wireless sensor networks. Inf. Technol. Control 2016, 45, 62–70. [Google Scholar] [CrossRef][Green Version]
- Dodis, Y.; Kanukurthi, B.; Katz, J.; Rezin, L.; Smith, A. Robust fuzzy extractors and Authenticated key agreement from close secrets. IEEE Trans. Dependable Secur. Comput. 2012, 58, 6207–6222. [Google Scholar] [CrossRef]
- Kuo, W.; Lin, C.; Chuang, C.; Kao, M. Simultaneous and anonymous mobile network authentication scheme based on chaotic maps. Inf. Technol. Control 2016, 45, 208–213. [Google Scholar] [CrossRef]
- Wang, W.; Cheng, Q.A. Multi-party secret handshake scheme based on chaotic maps. Inf. Technol. Control 2017, 46, 138–149. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. Adv. Cryptol. (Eurocrypt) 2004, LNCS 3027, 523–540. [Google Scholar]
- Zhang, L. Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos Solitons Fractals 2008, 37, 669–674. [Google Scholar] [CrossRef]
- Xu, D.; He, D.; Choo, K.K.R.; Chen, J. Provably secure three-party password authenticated key exchange protocol based on ring learning with error. In Cryptographers’ Track at the RSA Conference; Springer: Cham, Switzerland, 2017; p. 360. [Google Scholar]
- Chen, C.; Fang, W.; Liu, S.; Wu, T.; Pan, J.; Wang, K. Improvement on a chaotic map-based mutual anonymous authentication protocol. J. Inf. Sci. Eng. 2016, 34, 371–390. [Google Scholar]
- Bellare, M.; Rogaway, P. Entity authentication and key distribution. In Advances in Cryptology—CRYPTO’93; Lecture Notes in Computer Science; Stinson, D.R., Ed.; Springer: Berlin/Heidelberg, Germany, 1993; Volume 773, pp. 232–249. [Google Scholar]
- Gollman, D. Insider Fraud. Security Protocols-6th International Workshop; Springer Science & Business Media: Cambridge, UK, 1998; Volume 1550, pp. 220–226. [Google Scholar]
- Moon, J.; Lee, Y.; Kim, J.; Won, D. Improving an anonymous and provably secure authentication protocol for a mobile user. Secur. Commun. Netw. 2017. [Google Scholar] [CrossRef]
- Das, A.K. A secure and effective user authentication and privacy preserving protocol with smart cards for wireless communications. Netw. Sci. 2013, 2, 12–27. [Google Scholar] [CrossRef]
- Das, A.K.; Paul, L.N.; Tripathy, R. Cryptanalysis and improvement of an access control in user hierarchy based on elliptic curve cryptosystem. Inf. Sci. 2012, 209, 80–92. [Google Scholar] [CrossRef]
- Jung, J.; Moon, J.; Lee, D.; Won, D. Efficient and security enhanced anonymous authentication with key agreement scheme in wireless sensor networks. Sensors 2017, 17, 644. [Google Scholar] [CrossRef]
- Xie, Q.; Hu, B.; Wu, T. Improvement of a chaotic maps-based three-party password-authenticated key exchange protocol without using servers public key and smart card. Nonlinear Dyn. 2015. [Google Scholar] [CrossRef]
- Wu, S.; Pu, Q.; Wang, S.; He, D. Cryptanalysis of a communication-efficient three-party password authenticated key exchange protocol. Inf. Sci. 2012, 215, 83–96. [Google Scholar] [CrossRef]
- Chang, T.Y.; Hwang, M.S.; Yang, W.P. A Communication-Efficient Three-Party Password Authenticated Key Exchange Protocol. Inf. Sci. 2011, 181, 217–226. [Google Scholar] [CrossRef]
| Notation | Description | |
|---|---|---|
| 3WPAKE | SBAKE | |
| UA, UB | UA, UB | Communication parties user A and user B |
| S | S | Server |
| IDA, IDB | IDA, IDB | IDs of user A and user B |
| pwA, pwB | pwA, pwB | Passwords of user A and user B |
| p, q | p | Large prime numbers |
| Zp | Zp | Ring of integer modulo p |
| Zp* | Zp* | The multiplicative group of non-zero integers modulo p |
| g | - | A generator of G (⊆ Zp*) |
| h(∙) | h1(∙) | One-way hash function h1:{0,1}*→{0,1}l |
| - | h2(∙) | One-way hash function h2:[−1, 1]→{0,1}l |
| - | yA, yB | Random numbers selected by server S |
| rA, | d | Random numbers selected by user A |
| rB, | k | Random numbers selected by user B |
| x, y, z | - | Random exponents selected by user A, user B, and server S, respectively |
| - | s | Secret master key selected by server S |
| HA, VA, WA, RA | fA, CA,WA, YA,αA | Authentication parameters of user A |
| HB, VB, WB, RB | fB, CB, WB, YB,αB | Authentication parameters of user B |
| Ns, TA, TB | PA, PB, QA, QB | Authentication parameters of server S |
| KSA, KSB | SA, SB | Server S’s keys used to authenticate user A and user B |
| KAS, KBS | - | User’s keys used to authenticate the server S |
| AuthA, AuthB | AuthA, AuthB | Computed user’s parameters used to authenticate user A and user B |
| QA, QB | VA, VB, IA, IB, | Computed server’s parameters for user A and user B |
| sk | sk | Session key shared with user A and user B |
| ⊕, | ⊕, | Exclusive-or and concatenation operation |
| - | BioA, BioB | Biometric data of user A and user B |
| - | Gen, Rep | Fuzzy generator and reproduction procedure, respectively |
| - | σA, σB | Biometric secret key of user A and user B |
| - | τA, τB | Biometric public reproduction parameter of user A and user B |
| - | th | Error tolerance threshold used by fuzzy extractor |
| - | Tn(.) | Chebyshev polynomial of degree n |
| (a) | (b) |
| role usera(Ua, AS, Ub: agent, | role userb(Ua, AS, Ub: agent, |
| SKas: symmetric_key, | SKbs: symmetric_key, |
| H, F: hash_func, | H, F: hash_func, |
| SND, RCV: channel(dy)) | SND, RCV: channel (dy)) |
| played_by Ua def= | played_by Ub def= |
| local State: nat, | local State: nat, |
| IDa, IDb, PWa, BIOa, Oa, Ga, RPWa: text, | IDa, IDb, PWb, BIOb, Ob, Gb, RPWb: text, |
| Ya, Va, Wa, Sa, La, S: text, | Yb, Vb, Wb, Sb, Lb, S: text, |
| Aa, Ca, Pa, Pb, Qa, Qb, D, K, X, Y1, Y2, SKab: text | Ab, Cb, Pa, Pb, Qa, Qb, D, K, X, Y1, Y2, |
| SKba: text | |
| init State:= 0 | |
| init State:= 0 | |
| transition | |
| transition | |
| 1. State = 0 /\ RCV(start) =|> | |
| State’:= 1 /\ RPWa’:= H(PWa.Oa) | 1. State = 0 /\ RCV(start) =|> |
| /\ secret({PWa,Oa}, sc1, Ua) | State’:= 1 /\ RPWb’:= H(PWb.Ob) |
| /\ secret(IDa, sc2, {Ua, Ub, AS}) | /\ secret({PWb,Ob}, sc3, Ub) |
| /\ SND({IDa.RPWa’}_SKas) | /\ secret(IDb, sc4, {Ua, Ub, AS}) |
| /\ SND({IDb.RPWb’}_SKbs) | |
| 2. State = 2 | |
| /\ RCV({xor(H(IDa.S),H(PWa.Oa)).xor(H(Y1’.S),H( | 2. State = 3 |
| S)).X}_SKas) =|> | /\ RCV({xor(H(IDb.S),H(PWb.Ob)).xor(H(Y |
| State’:= 4 /\ D’:= new() | 2’.S),H(S)).X}_SKbs) =|> |
| /\ Ca’:= xor(IDa,F(D’.X)) | State’:= 5 /\ K’:= new() |
| /\ Wa’:= | /\ Cb’:= xor(IDb,F(K’.X)) |
| xor(xor(H(IDa.S),H(PWa.Oa)),H(PWa.Oa)) | /\ Wb’:= |
| /\ Ya’:= xor(Wa’,Ca’,IDb) | xor(xor(H(IDb.S),H(PWb.Ob)),H(PWb.Ob)) |
| /\ Aa’:= H(IDa.Ca’.Wa’) | /\ Yb’:= xor(Wb’,Cb’,IDa) |
| /\ SND(Ca’.xor(H(Y1’.S),H(S)).Ya’.Aa’) | /\ Ab’:= H(IDb.Cb’.Wb’) |
| /\ SND(Cb’.xor(H(Y2’.S),H(S)).Yb’.Ab’) | |
| 3. State = 6 | |
| /\ RCV(H(H(PWa.Oa).F(D’.X).IDa.IDb).xor(F(K’.X) | 3. State = 6 |
| ,IDa)) =|> | /\ RCV(H(H(PWb.Ob).F(K’.X).IDb.IDa).xor |
| State’:= 7 /\ SKab’:= | (F(D’.X),IDb)) =|> |
| H(F(D’.X).xor(xor(F(K’.X),IDa),IDa).F(D’.xor(xor(F( | State’:= 8 /\ SKba’:= |
| K’.X),IDa),IDa))) | H(F(K’.X).xor(xor(F(D’.X),IDb),IDb).F(K’.xo |
| r(xor(F(D’.X),IDb),IDb))) | |
| end role | |
| end role | |
| (c) | (d) |
| role applicationserver(Ua, AS, Ub: agent, | role session(Ua, Ub, AS: agent, |
| SKas, SKbs: symmetric_key, | SKas, SKbs: symmetric_key, |
| H, F: hash_func, | H, F: hash_func) |
| SND, RCV: channel (dy)) | |
| def= | |
| played_by AS def= | local Z1, Z2, Z3, S1, S2, S3: channel (dy) |
| local State: nat, | composition |
| IDa, IDb, PWa, PWb, BIOa, BIOb, Oa, Ga, Ob, Gb, | |
| RPWa, RPWb: text, | usera(Ua, AS, Ub, SKas, H, F, Z1, S1) |
| Ya, Yb, Va, Vb, Sa, Sb, La, Lb, S, Y1, Y2: text, | /\ userb(Ua, AS, Ub, SKbs, H, F, Z2, S2) |
| Aa, Ab, Ca, Cb, Fa, Fb, Pa, Pb, Qa, Qb, D, K, X: text | /\ applicationserver(Ua, AS, Ub, SKas, |
| SKbs, H, F, Z3, S3) | |
| init State:= 1 | |
| end role | |
| transition | |
| role environment() def= | |
| 1. State = 1 /\ RCV(IDa.H(PWa.Oa)) =|> | |
| State’:= 2 /\ Y1’:= new() | const ua, as, ub: agent, |
| /\ Va’:= xor(H(Y1’.S),H(S)) | skas, skbs, skab, skba: symmetric_key, |
| /\ Sa’:= xor(H(IDa.S),H(PWa.Oa)) | h, f: hash_func, |
| /\ La’:= xor(IDa,H(Y1’.S)) | ca, va, ya, aa: text, |
| /\ secret(S, sc5, AS) | cb, vb, yb, ab: text, |
| /\ secret(H(Y1’.S), sc6, AS) | pa, qa, pb, qb: text, |
| /\ SND({Sa’.Va’.X}_SKas) | sc1, sc2, sc3, sc4, sc5, sc6, sc7, sc8: |
| protocol_id | |
| 2. State = 3 /\ RCV(IDb.H(PWb.Ob)) =|> | |
| State’:= 4 /\ Y2’:= new() | intruder_knowledge = {ua, as, ub, h, f, ca, |
| /\ Vb’:= xor(H(Y2’.S),H(S)) | va, ya, aa, cb, vb, yb, ab, pa, qa, pb, qb} |
| /\ Sb’:= xor(H(IDb.S),H(PWb.Ob)) | |
| /\ Lb’:= xor(IDb,H(Y2’.S)) | composition |
| /\ secret(H(Y2’.S), sc7, AS) | |
| /\ SND({Sb’.Vb’.X}_SKbs) | session(ua, as, ub, skas, skbs, h, f) |
| 3. State = 5 | end role |
| /\ RCV(xor(IDa,F(D’.X)).xor(H(Y1’.S),H(S)).xor(H(I | |
| Da.S),xor(IDa,F(D’.X)), | goal |
| IDb).H(IDa.xor(IDa,F(D’.X)).H(IDa.S))) | |
| /\ RCV(xor(IDb,F(K’.X)).xor(H(Y2’.S),H(S)).xor(H(I | secrecy_of sc1 |
| Db.S),xor(IDb,F(K’.X)),IDa). | secrecy_of sc2 |
| H(IDb.xor(IDb,F(K’.X)).H(IDb.S))) =|> | secrecy_of sc3 |
| State’:= 6 /\ Pa’:= | secrecy_of sc4 |
| H(xor(H(IDa.S),xor(H(IDa.S),H(PWa.Oa))).F(D’.X). | secrecy_of sc5 |
| IDa.IDb) | secrecy_of sc6 |
| /\ Qa’:= xor(F(K’.X),IDa) | secrecy_of sc7 |
| /\ Pb’:= | |
| H(xor(H(IDb.S),xor(H(IDb.S),H(PWb.Ob))).F(K’.X). | end goal |
| IDb.IDa) | |
| /\ Qb’:= xor(F(D’.X),IDb) | environment() |
| /\ SND(Pb’.Qb’) | |
| /\ SND(Pa’.Qa’) | |
| end role |
| SUMMARY |
| SAFE |
| DETAILS |
| BOUNDED_NUMBER_OF_SESSIONS |
| TYPED_MODEL |
| PROTOCOL |
| /home/span/span/testsute/results/test.if |
| GOAL |
| As Specified |
| BACKEND |
| CL-AtSe |
| STATISTICS |
| Analysed: 0 states |
| Reachable: 0 states |
| Translation: 0.02 seconds |
| Computation: 0.00seconds |
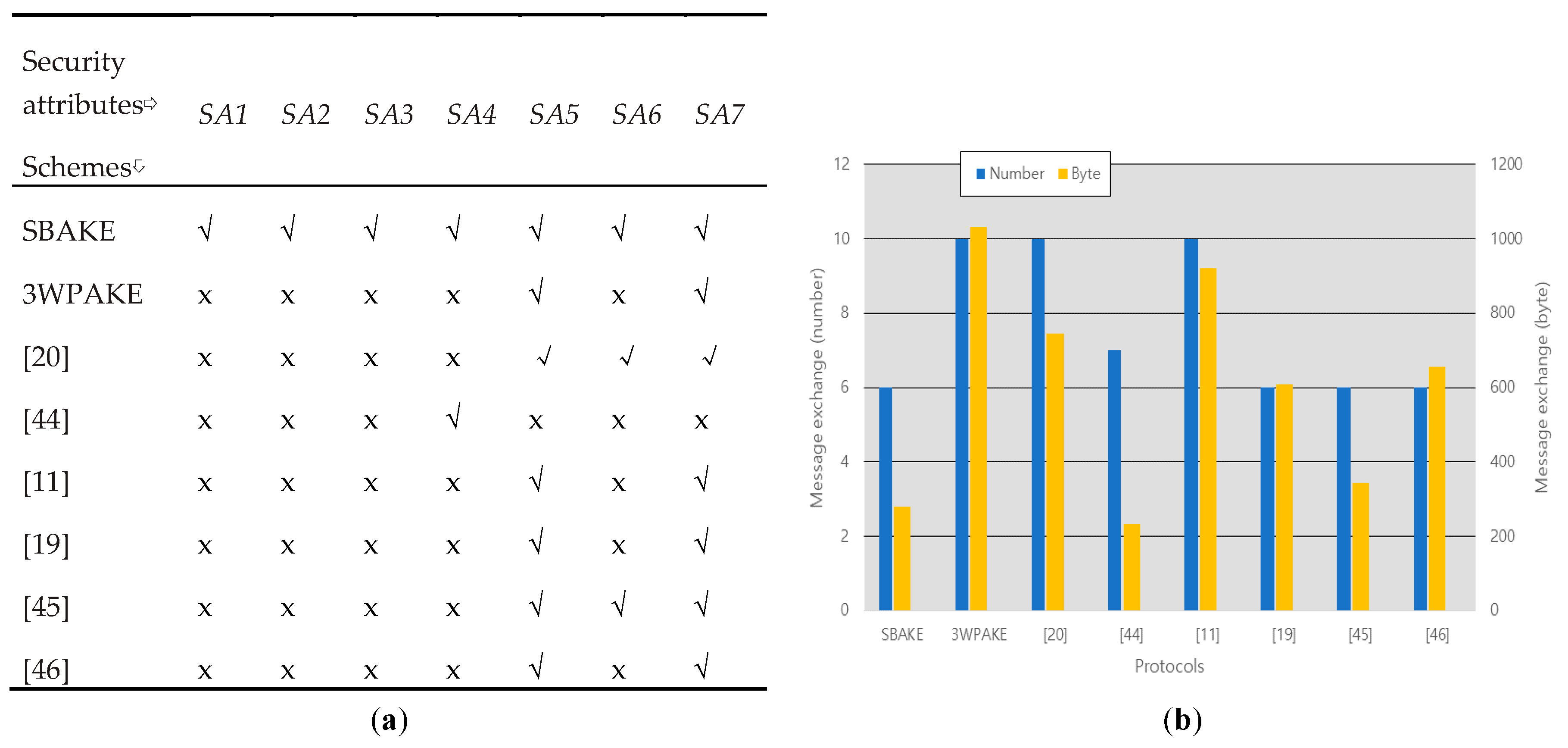
| Protocol | Computation Cost | Total Cost | Message Exchange (Number/Byte) | |||||
|---|---|---|---|---|---|---|---|---|
| UA | UB | S | UA-S | UB-S | UA-UB | Total | ||
| SBAKE | 7TH + 2TCCM + 1TFE | 7TH + 2TCCM + 1TFE | 7TH | 21TH + 4TCCM + 2TFE | 2/120 | 2/120 | 2/40 | 6/280 |
| 3WPAKE [9] | 5TH + 3TEXP | 5TH + 3TEXP | 10TH + 3TEXP | 20TH + 9TEXP | 4/488 | 4/488 | 2/56 | 10/1032 |
| Chen et al. [20] | 5TH + 3TEXP | 5TH + 3TEXP | 6TH + 4TEXP | 16TH + 10TEXP | 4/372 | 4/372 | 0/0 | 10/744 |
| Xie et al. [44] | 3TH + 3TCCM | 3TH + 3TCCM | 6TH + 4TCCM | 12TH + 10TCCM | 4/124 | 3/108 | 0/0 | 7/232 |
| Farash and Attari [11] | 6TH + 3TEXP | 6TH + 3TEXP | 6TH + 3TEXP | 18TH + 9TEXP | 4/440 | 4/440 | 2/40 | 10/920 |
| Tallapally [19] | 5TH + 2TEXP | 5TH + 2TEXP | 5TH + 2TEXP | 15TH + 6TEXP | 2/284 | 2/284 | 2/40 | 6/608 |
| Wu et al. [45] | 4TH + 3TECC | 4TH + 3TECC | 4TH + 4TECC | 12TH + 10TECC | 3/136 | 1/100 | 2/108 | 6/344 |
| Chang et al. [46] | 5TH + 3TEXP | 5TH + 3TEXP | 4TH + 4TEXP | 14TH + 10TEXP | 3/312 | 1/20 | 2/324 | 6/656 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, M.; Moon, J.; Won, D.; Park, N. Revisit of Password-Authenticated Key Exchange Protocol for Healthcare Support Wireless Communication. Electronics 2020, 9, 733. https://doi.org/10.3390/electronics9050733
Kim M, Moon J, Won D, Park N. Revisit of Password-Authenticated Key Exchange Protocol for Healthcare Support Wireless Communication. Electronics. 2020; 9(5):733. https://doi.org/10.3390/electronics9050733
Chicago/Turabian StyleKim, Mijin, Jongho Moon, Dongho Won, and Namje Park. 2020. "Revisit of Password-Authenticated Key Exchange Protocol for Healthcare Support Wireless Communication" Electronics 9, no. 5: 733. https://doi.org/10.3390/electronics9050733
APA StyleKim, M., Moon, J., Won, D., & Park, N. (2020). Revisit of Password-Authenticated Key Exchange Protocol for Healthcare Support Wireless Communication. Electronics, 9(5), 733. https://doi.org/10.3390/electronics9050733






