Abstract
Two party authentication schemes can be good candidates for deployment in Internet of Things (IoT)-based systems, especially in systems involving fast moving vehicles. Internet of Vehicles (IoV) requires fast and secure device-to-device communication without interference of any third party during communication, and this task can be carried out after registration of vehicles with a trusted certificate issuing party. Recently, several authentication protocols were proposed to enable key agreement in two party settings. In this study, we analyze two recent protocols and show that both protocols are insecure against key compromise impersonation attack (KCIA) as well as both lack of user anonymity. Therefore, this paper proposes an improved protocol that does not only resist KCIA and related attacks, but also offers comparable computation and communication. The security of proposed protocol is tested under formal model as well as using well known Burrows–Abadi–Needham (BAN) logic along with a discussion on security features. While resisting the KCIA and related attacks, proposed protocol also provides comparable trade-of between security features and efficiency and completes a round of key agreement in just ms, which makes it a promising candidate to be deployed in IoT environments.
1. Introduction
A Two-Party Authentication Key Agreement Protocol (2PAKA) shares a secret key after authentication for secure communication between two parties. The certificate based 2PAKA can be deployed in Internet of Things (IoT)-based vehicular environments to offer autonomous device to device communication because in such dynamic and fast moving devices network, the interference of some gateway or trusted authority may lead to delay, and such delays may lead to infeasibility of the whole network [1]. In 2PAKA systems, the vehicle, after registering with the trusted certificate generation authority, gets a private and public key pair based credentials of both trusted authority and the requesting vehicle. However, the security and privacy of such schemes remain on stake due to open architecture beneath the communication. Such architecture is shown in Figure 1, involving the smart devices networks and the certificate authority which can also termed as server. Every device in a smart network gets its key pair from certificate authority and then can communicate autonomously without involvement of the authority. In this article the term device and vehicle are used interchangeably as well as server and certificate authority means same.
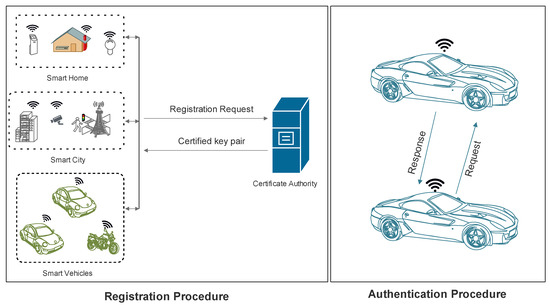
Figure 1.
Device to Device Authentication Scenario.
Diffie & Hellman key exchange protocol [2] was the first approach in this direction. After then, several key exchange protocols [3,4,5,6] based on traditional public key infrastructure (PKI) were proposed to avoid man-in-middle (MIM) attack. The use of modular exponentiation in PKI led towards PKI’s inapplicability in resource constrained environments like smart phones, smadrcards etc. Therefore, research efforts then have focused on lightweight Elliptic Curve Cryptography (ECC) and some 2PAKA protocols based on ECC [7,8,9] were proposed. The ECC-based 2PAKA protocols require less computation and storage with same level of security, due to the use of 160 bits key in ECC instead of 1024 bits key in Rivest, Shamir, and Adleman (RSA) algorithm. The ECC-based 2PAKA protocols require a trusted third party, called certificate authority(CA), to manage and generate certificates. It also validates and generates public keys of users.
In 1989, Gunther et al. [10] proposed a key exchange protocol based on user’s identity. The protocol in [10] requires the intervention of certificate authority for establishing a secure channel between two users. In 2000 Saeedina [11] proposed the improvement over Gunther et al.’s identity-based key exchange protocol. The modified scheme overcomes the number of passes to half, and so minimize the communication between the parties. In 2002, Hsieh et al. [12] proposed a slight modification of Saeednia’s identity-based key exchange protocol to reduce computation cost. However, Tseng et al. [9] demonstrated that the scheme proposed by Hiesh et al. cannot withstand key compromise impersonation attack (KCIA). Holbl and Welzer [13] proposed two new two-party identity-based authenticated key agreement protocols.The first is based on the protocol of Hsieh et al. to make it immune against KCIA, while the second is an efficient enhancement of Tseng’s protocol. Zhang et al. [14] proved that the protocols proposed in [13] cannot resist impersonation attack as well as KCIA. Smart [15] proposed another identity based key agreement protocol using weil pairing. Chen and Kudla [16] and Shim [17] independently purposed authenticated key agreement (AKA) protocols. Sun and Hsieh [18] proved that both the protocols [16,17] are vulnerable to KCIA and man-in-middle (MIM) attacks. Ryu et al. [19] also proposed another protocol and demonstrated that their protocol minimizes the cost of computation and communication and is more efficient than Chen and Kudla’s protocol with same security properties. Boyd and Choo [20] showed that the Ryu et al.’s protocol could not achieve the KCIA resilience properties. McCullagh and Barreto [21] claimed that their protocol can be used in either escrow or escrow-less mode. They also described conditions under which users of different key generation centers can agree on a shared secret key. In 2005 Zu-hua et al. [22] proposed bilinear pairing based self-certified protocol using computational Diffie-Hellman assumption. Ni et al. [23] also presented two secure variants of their proposal.
In 2008 Cao et al. [24] put forwarded a new identity-based authentication key agreement protocol and claimed it to achieve forward secrecy. Tsaur [25] also proposed an ECC-based self-certified public key cryptosystem based AKA and their protocol achieved session and public keys in a single step. In 2009 Hölbl and Welzer [26] proposed two new identity-based 2PAKA protocols but their scheme were proved to be vulnerable to key compromise impersonation attacks. Their protocol do not offer provable security. Some other IBC-based 2PAKA protocols using ECC were also proposed [9,11,12,13,16,17,18,19,20,21,27,28,29,30], these protocols suffer from private key escrow problem because the private key is known as Private Key Generation (PKG) party. If the PKG is malicious with man-in-middle (MIM) attack then the whole protocol is suffered [31].
Motivations and Contribution
In 2015, Islam & Biswas (Islam-Biswas) [31] proposed a self certified ECC based key agreement protocol and claimed that their protocol provides security against all kinds of attacks. Mandal et al. [32] found that their protocol lacks anonymity and is defenseless against replay and clogging attacks [33]. However, in this paper we show that both the protocols of Islam-Biswas and Mandal et al. are insecure against key compromise impersonation attack (KCIA). Moreover, both protocols lack user anonymity. This paper then introduces a new scheme to overcome the insecurities of Islam-Biswas and Mandal et al.’s protocols. The proposed protocol achieves following merits:
- Proposed protocol resists KCIA and related attacks under the hardness assumption of Elliptic Curve Discrete Logarithm Problem ().
- Proposed protocol achieves low computation and communication cost as compared with related secure schemes.
2. Fundamentals
This section describes some fundamental concepts relating to Hash Functions, Elliptic Curve Cryptography along with some hard problems. The adversarial model is also defined in this section. Moreover, notation guide is provided in Table 1.

Table 1.
Notation Guide.
2.1. Hash Function
The arbitrary size input to a hash function with collision resistant property yields a fixed length value with following additional pre-requisit properties:
- A slight fluctuation in (the input), there is a massive change in output .
- Computing , given is easy; whereas, computing , given is a hard problem
- Finding a pair such that is a hard problem and this property is termed as collision resistance property (CRP).
Definition 1.
[CRP for Secure Hash] Given , an attacker can compute an input pair such that with probability . is considered to select the pair at random. The computed advantage is based on polynomial-time t bound arbitrary choices. As per CRP for .
2.2. Elliptic Curve Cryptography
Consider p (a very large prime, (), an Elliptic Curve : is a set with finite points . The pair is pragmatically selected to satisfy the relationship (. The point W multiplication with some chosen scalar a can be computed as a times addition repeatedly. All system parameters are chosen from finite field ; whereas, forms an abelian group with point O considered to be at infinity and described as additive identity.
Definition 2.
[ Discrete logarithm problem for EC (ECDLP)] Consider are two points over such that , knowing the duo , the probability of computing a can be solicited as: , the experiment is allowed to be conducted by a polynomial-time t bound attacker . As per , .
Definition 3.
[ Diffie Hellman problem for EC (ECDHP)]Consider are three points over such that , and knowing the trio , the probability of computing can be solicited as: , the experiment is allowed to be conducted by a polynomial-time t bound attacker . As per , .
2.3. Attacker Model
The authenticated key agreement is achieved over an insecure networks, assuming a strong attacker having many capabilities [34,35]. Some common assumptions related with attackers’ capabilities are made as follows:
- The adversary is having access to public keys of both parties.
- knows public identities of all users of the system.
- can control the insecure communication channel, precisely can eavesdrop, inject, delete or replay any message, while can not have any access to secure channel.
3. Review of Islam-Biswas Protocol
In this section, we review Islam-Biswas 2PAKA protocol [31] consisting of three phases: system setup, registration and authenticated key agreement phase, the detail of each phase is as follows:
3.1. System Setup Phase
In system setup phase, the server () initializes the system parameter Ω. Initially chooses a security parameter along with an elliptic curve , then selects a base point G over . Further selects as his private key and computes and chooses three one-way hash functions . Finally publishes all public parameters and keeps secret.
3.2. Registration Phase
This phase is executed when a user wants to register with server. selects his identity and a random number , then computes and sends to via some secure channel, which selects upon receiving a message from . then computes , and . sends to via some secure channel and publishes . Upon receiving, computes his private key , the public key of is .
3.3. Authenticated Key Agreement Phase
This phase takes place when two users say and want to exchange information and initiates the process. The following steps as shown in Figure 2 are performed among and .
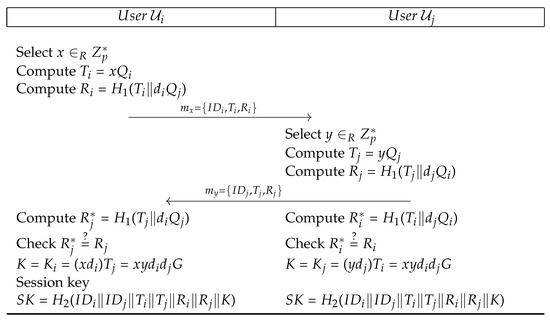
Figure 2.
Islam-Biswas Key Agreement Protocol.
- IKA 1:
- selects and computes & , then sends to .
- IKA 2:
- selects and computes & , then sends to .
- IKA 3:
- Now the authenticated key is computed as follows:
- computes and verifies , if not true, aborts the session, otherwise the key is computed as: .
- Similarly computes and verifies , if not true, aborts the session, otherwise the key is computed as: .
4. Review of Mandal et al.’s Protocol
In this section, we review Mandal et al.’s 2PAKA protocol [32] consisting of three phases: system setup, registration and authenticated key agreement phase. The system setup phase is as it is taken from Islam-Biswas protocol, except Mandal et al. just selected one hash function instead of three in Islam-Biswas protocol. The detail of other two phases is as follows:
4.1. Registration Phase
This phase is executed when a user wants to register with server. selects his identity and a random number , then computes and sends to via some secure channel, which selects upon receiving a message from . then computes , , and . sends to via some secure. Upon receiving, computes his private key , and public key . checks the validity/correctness of public private key pair as . On successful verification, keeps secret and publishes .
4.2. Authenticated Key Agreement Phase
This phase takes place when two users say and want to exchange information and initiates the process. The following steps as shown in Figure 3 are performed among and .

Figure 3.
Mandal Key Agreement Protocol.
- MKA 1:
- selects , generate and computes , , , and . then compute encryption as: and sends to .
- MKA 2:
- On receiving a message, checks the time-stamp freshness and aborts the session if , does not hold. Otherwise, computes and decrypts using key to obtain . further computes , and aborts the session if , does not hold. Otherwise, computes and selects and current time-stamp and further computes , , , , . then computes session key and and sends back to .
- MKA 3:
- On receiving a message, checks the time-stamp freshness and aborts the session if , does not hold. Otherwise, computes , and decrypts using to obtain . Further computes , and aborts the session if , does not hold. Otherwise, considers is authenticated and computes session key .
5. Weakness of Existing Protocols
In this section, firstly we perform cryptanalysis of Islam-Biswas protocol to show its weaknesses and then we perfom the cryptanalysis of Mandal et al.’s protocol. The following subsections show that both the protocols of Islam-Biswas and Mandal et al. are vulnerable to key compromise impersonation attack, and lack of user anonymity.
5.1. Key Compromise Impersonation Attack on Islam-Biswas Protocol
By key compromise impersonation attack, if an active adversary is able to get access to a user’s (e.g., ) long term private key, then he can masquerade himself as an other user (e.g., ) to the victim. In this subsection, we show that Islam-Biswas protocol is vulnerable to key compromise impersonation attack. An active adversary can mount this attack to share a session key with a peer. Let be an attacker who wants to impersonate as a legal user to another legal user . For successful impersonation, the steps performed between and are described as follows:
- Step KCI 1:
- computes:
Then sends to .
- Step KCI 2:
- Upon receiving the message selects , and computes
Further sends to .
- Step KCI 3:
- intercepts the message and computes
and verifies
Then computes:
Similarly computes:
and verifies
If Equation (10) does not hold, aborts the session, otherwise believes the party on other side is and computes:
Proposition 1.
In Islam-Biswas protocol, upon execution of key compromise impersonation attack, user accepts adversary as another user and shares the session key with on behalf of .
Proof.
initiates the key compromise impersonation attack by computing and , then sends to , which believes the other party is legal if Equation (10) holds. computes in Equation (9), which is equal to computed by in Equation (2). Hence is believed to be by . The session key computed by both and is also same, as computed session key in Equation (8) which is exactly the same as computed by in Equation (12). Hence, has successfully launched KCIA on Islam-Biswas’s protocol. □
5.2. Key Compromise Impersonation Attack on Mandal et al.’s Protocol
This subsection shows that the protocol of Mandal et al. is also vulnerable to Key Compromise Impersonation Attack (KCIA). Let be an attacker who wants to impersonate as a legal user to another legal user . For successful impersonation, the steps performed between and are simulated as follows:
- KCM 1:
- randomly selects , generates and computes:
sends to .
- KCM 2:
- On receiving a message, checks the time-stamp freshness and aborts the session if , does not hold. then computes:
then checks:
Upon success, selects and and computes:
sends back to .
- KCM 3:
- intercepts the messages and computes:
then computes session key as:
Proposition 2.
In Mandal et al.’s protocol, upon execution of key compromise impersonation attack, user accepts adversary as another user and shares the session key with on behalf of .
Proof.
initiates the key compromise impersonation attack by computing and then sends tuple to , which believes the other party is legal if Equation (22) holds. The security of the protocol relies on the computation of , if is computed same on both sides, then decryption of on will be same as computed by . Therefore, computed in Equation (15) by and in Equation (21) by will also be same. Hence Equation (22) will hold true. computes in Equation (18), which is equal to computed by in Equation (14). Therefore, Equation (22) holds. Hence, is believed to be by . The session key computed by both and is also same, as computed session key in Equation (35) which is exactly the same as computed by in Equation (29). Hence, has successfully launched KCIA on Mandal et al.’s protocol. ☐
5.3. Lacking User Anonymity
Both the protocols of Islam-Biswas and Mandal et al., lack user anonymity and privacy. The former did not claim to provide anonymity, whereas, latter claimed to provide it. However, after a careful analysis, it is revealed that their protocol lacks anonymity. Our analysis is simulated as follows:
After computing and , the sends tuple to . after verification of freshness computes:
The computation of Equation (36) requires the public key of the user . However, the received message does not contain any information to identify the requesting user. Therefore, the protocol will not work. The authors in this paper consider it a typographical mistake and the complete request message may be , because in other case, the protocol is incorrect and cannot complete the authentication process. As per the valid assumption made by authors, the protocol of Mandal et al. does not provide user anonymity.
6. Proposed Protocol
This section briefly explains the proposed protocol designed specifically to resist key compromise impersonation attack (KCIA). The proposed protocol is based on ECC and self certified keys and resist all known attacks. The proposed protocol involves two entities: (1) The server is responsible for registration of the devices and assigns certificates to each of the device, the server is assumed to be trusted, (2) the communicating devices after getting certificate from server can establish secure connection with each other without intervention of server or any other party. Following subsections explains the proposed methodology:
6.1. Setup Phase
In system setup phase, the server () initializes the system parameter Ω. Initially chooses a security parameter along with an elliptic curve , then selects a base point G over . Further selects as his private key and computes and chooses a one way hash functions . Finally publishes all public parameters and keeps secret.
6.2. Registration Phase
This phase is very similar to the corresponding phase of Islam et al.’s protocol and is initiated by a device , when wants to register with . selects his identity and a random number , then computes and sends to via some secure channel, which selects upon receiving a message from . then computes , and . sends to via some secure channel and publishes . Upon receiving, computes his private key , the public key of is . The registration phase is also illustrated in Figure 4. The private key of can be verified as follows:
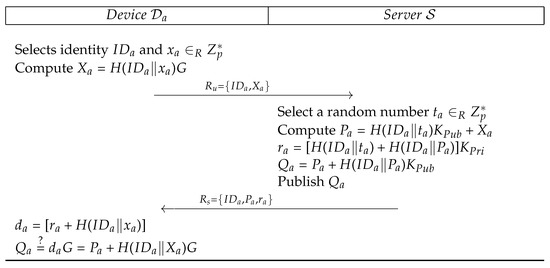
Figure 4.
Proposed registration.
6.3. Authenticated Key Agreement Phase
In proposed scheme, a device say initiates the process to exchange authenticated key with peer say . Following steps as shown in Figure 5 are performed among and :
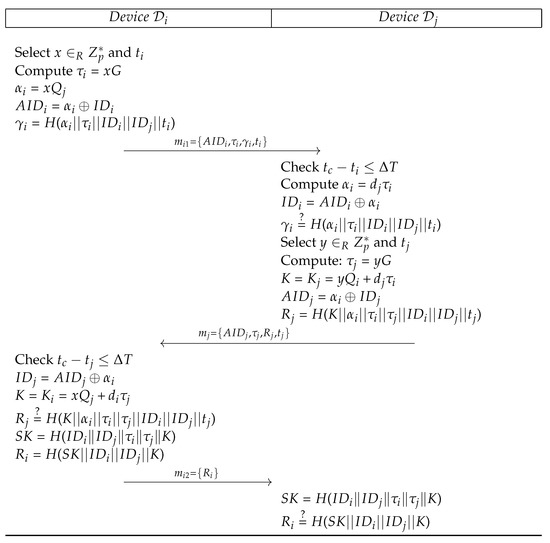
Figure 5.
Proposed key agreement.
- PKA 1:
- selects , generates and computes , , and . Then sends to .
- PKA 2:
- On receiving request message, aborts the session if . Otherwise, computes , and aborts the session if . Otherwise, selects , generates and computes , , , . The sends to .
- PKA 3:
- After receiving the reply, aborts the session if . Otherwise, computes , and checks , continues to compute and , if the equality holds. The sends to .
- PKA 4:
- on receiving computes and verifies . terminates the session on failure and keeps as session key upon success.
7. Security Analysis
In this section the security of proposed protocol under the attack model of automated tool Scyther is performed, backed by the security requirements discussion. This section also provides a security features comparison of the proposed and existing protocols [13,31,32,36,37] in Table 2. Referring to Table 2, only the proposed schemes provide all security features, whereas all other protocols lacks device anonymity. The protocols [13,36,37] are insecure key replication (KRA/KOA) attack, the protocols [13,31,32] are insecure against Key compromise impersonation attack (KCIA). Protocol proposed by Islam-Biswas [31] is also insecure against replay attack. Following subsections provides detailed security analysis and security features provided by the proposed protocol:

Table 2.
Security Comparison table.
7.1. Formal Security
To analyze formally, the security and privacy of the proposed protocol, following oracles are defined:
- : Execution of this oracle unconditionally yields out of .
- : Given the pair , execution of this oracle unconditionally provides a.
Theorem 1.
The proposed device to device security protocol is secure for - an attacker, to expose of device , the parameter , the session key shared between and under the hardness of and hash function is considered as a random oracle.
Proof.
is considered as an attacker with abilities to compute of device , secretly computed parameter and between and . simulates the oracles oracles and for the execution of the algorithmic experiment (Algorithm 1) against the two party device-to-device authenticated key agreement () protocol. The success probability of can be solicited as , where the advantage of is . The maximum allowed queries can make are and , for each of the oracles and . Referring the simulation of , can compute , K and if has the abilities to (i) break one-way property of hash and (ii) Compute the hard . As per Definition 1, inverting hash is hard problem; likewise, by Definition 2 solving ECDLP is also computationally infeasible for large parameter sizes ( bits). Hence, proposed is unbreakable against disclosure of secretly computed parameter K, session key and device identity . ☐
| Algorithm 1 |
|
Theorem 2.
The proposed device to device security protocol is secure for - an attacker, with access to private key of a registered device , to share a session key with on behalf of another registered device .
Proof.
having access to private key of registered device is considered as competent enough to compute, secretly computed parameter and between (on behalf of ) and . simulates the oracles and for the execution of the algorithmic-experiment (Algorithm 2) against the 2 party device-to-device authenticated key agreement () protocol. The success probability of can be solicited as , where the advantage of is . The maximum allowed queries can make are and , for each of the oracles and . Referring the simulation of , can compute K and if has the abilities to (i) break one-way property of hash and (ii) Compute the hard . As per Definition 1, inverting hash is hard problem; likewise, by Definition 2 solving ECDLP is also computationally infeasible for large parameter sizes ( bits). Therefor, proposed is unbreakable against disclosure of secretly computed parameter K and session key , given private key of victim and can resist KCIA. ☐
| Algorithm 2 |
| Compute , , and |
| 2: Send to |
| 4: Eavesdrop Challenge , where , and |
| Compute |
| 6: Call oracle on and get |
| Compute |
| 8: Call on and get |
| if () then |
| 10: Compute |
| Compute |
| 12: else Send to |
| return Fail |
| 14: end if |
7.2. BAN Logic Based Security Analysis
In this section the formal security analysis of the proposed scheme has been done by using Burrows-Abadi-Needham (BAN) logic. We analyze the likelihood of mutual authentication among participants, along with the resistance from session key disclosure by using the BAN logic.
Various rules and principals were presented by Burrows, Abadi and Needham in 1989. If any one of these rules is being violated then the protocol/scheme is considered incorrect. Here are some rules and their descriptions:
Rule 1: Message Meaning
This rule depicts that P believe, and Q one time said that if P believes than secret key K shared with Q and P see that X is encrypted by using key K.
Rule 2: Nonce Verification
this rule says that P is believing that Q also believes X, if P is still believing that X is fresh and Q said that X.
Rule 3: Jurisdiction
We can say that P is believing on Q and also X is valid, if and only if when P is believing that Q has the jurisdiction over X.
Rule 4: Acceptance Conjunction
If a P believes on X and X believes on Y, as a result we can say that P principal believes on both too.
Rule 5: Freshness Conjunction
In this rule we can said that P believing that both X and Y are fresh if and only if when P believe X is still fresh.
Rule 6: Session Key
In the session key rule if a P principal believes on the freshness of session key then also P and then Q also on X believes which is the most important part of the session key. And then P principal also believes that user shares a session key ”K” with Q.
We employ the following notations in verifying the the security properties.
- believes
- sees
- once said , some time ago.
- has got jurisdiction over
- #(): The message is to be taken as fresh.
- (): The formulae is hashed in combination with formulae .
- or being the part of message .
- or is encrypted with symmetric or asymmetric key K of .
- and can securely contact using the shared key K.
The following are the assumptions for the BAN logic analysis.
- :
- :
- :
- :
- :
The following goals serve as the target for proving this analysis.
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
The protocol’s generic form is illustrated as under.
- M1:
- M2: :
- M3:
The idealized form of the protocol is designed as follows.
- :
- :
- :
Considering the first and third message of the idealized form:
- :
- :
By Applying seeing rule, we get,
- :
- :
According to S1, S2, A3 and message meaning rule,
- :
- :
According to A1, S3, S4 freshness conjucatenation, and nonce verification rules, we get
- :
- :
According to A6, S5, S6 and Jurisdiction rule
- :
- :
According to A3, S6, S7, and session key rule, we get
- : (Goal 2)
According to A6, S8, and Jurisdiction rule
- : (Goal 1)
Considering the second idealized form as:
- :
By applying seeing rule, we get
- :
According to S10, A4 and message meaning rule,
- :
According to A2, S11, freshness conjucatenation, and nonce verification rules we get,
- :
According to A5, S12, and Jurisdiction rule
- :
According to A4, S13, and session key rule, we get
- : (Goal 4)
According to A5, S14, and Jurisdiction rule
- : (Goal 3)
The above BAN logic analysis formally proves that the proposed protocol achieves mutual authentication and the session key SK is mutually established between and .
7.3. Security Features Analysis
Following subsections provide a discussion on attack resilience of the proposed protocol:
7.3.1. Key Compromise Impersonation Attack
By KCIA, if an adversary gets long private key of a device say can impersonate himself as anyother device say of the system to the victim . In proposed protocol if gets the long term private key , cannot impersonate himself as anyother device say to the victim . To launch KCIA can be the initiator or the responder, and for responding role can intercept the message sent by the to . cannot compute as it requires private key of . The inability of computing is also extended to compute the identity of initiator. Moreover, cannot compute because with known and the public key , finding is elliptic curve discrete logarithm (ECDLP)—a hard problem. Hence will also fail to compute and as both also requires the knowledge of K. Similarly, in initiator case, can compute , and (With supposition that all identities are known to adversary). Similarly, after receiving the return message from , the adversary can also compute , but computing is again intractable ECDLP. Therefore, the proposed protocol provides resistance against KCIA.
7.3.2. Device Anonymity
The proposed scheme provides device anonymity and un-traceability [38,39]. In the proposed scheme, sends his pseudo calculated identity , any adversary just by listening the channel can get this pseudo identity and to compute original identity , the adversary needs to know , which is not sent on communication channel. The adversary can get but computing from needs the private key of the receiver , same private key is required to get the original identity from pseudo calculated identity . Moreover, the temporary is dynamically computed for each session. The proposed scheme provides identity hiding as well as resistance to traceability attack.
7.3.3. Man-in-Middle Attack
For two devices ( and ), the proposed protocol exchanges and and generates and session key using two private keys and , and two session specific parameters x and y generated each participant. Since the devices can authenticate and very easily, a valid session key is generated.Therefore, to get authenticated from other side, the attacker requires the private key of the 2nd participant as well as session specific temporary parameter generated on other side. Even if can generate session specific parameter but computing private key out of public key is the hard ECDLP problem and computing from and is ECC Diffie-Hellman problem (ECDHP), which is also a hard problem. Thus, the proposed protocol provides protection against MIM attack.
7.3.4. Known-Key Attacks
Known-key-attack (KKA) is a cryptographic attack in which an adversary can access the ciphertext. Known-key-attacks can be attempted successfully by an adversary when the palintext is related with the ciphertext and the adversary could trace the plaintext by just performing backtracking. A protocol holds KKA property if a disclosure of whole or part of previously generated keys occur and such disclosure may not help to generate other past or future session keys. In the proposed protocol, each key is formed using private keys of both interconnected devices as well as their random numbers generated solely for formation of each session key and if an attacker by some means gets one or more generated session keys, it may have no advantage in computing any other safe past or future keys and to expose any past or future keys , needs to compute K, and which are based on private keys and session specific parameters and are unknown to . Hence, proposed protocol resists KKS attack.
7.3.5. Unknown Key Share Attack (UKS)
By UKS, An entity, say believes that a correct session key with other device is accomplished and on other hand another device say wrongly believes that the key is established with instead of . In the proposed protocol, the session key computed on both sides is same and it requires the privates keys as well as identities of both the participants. Therefore, the proposed protocol is secure from UKS.
7.3.6. Backward/Forward secrecy
A protocol satisfies forward secrecy [40,41], if the private key of one or more participant but not all or some of the previously generated sessions keys are compromised, it may not effect future sessions keys. Similarly, in a protocol if compromise of current session key or some of the private keys cannot help to expose any previous session key, the protocol is said to be forward secure. The protocol is said to posses perfect forward secrecy if the compromise of all private keys have no effect on previously generated session keys. In the proposed protocol, even if the private keys of both participants are known to an adversary, he cannot compute any previously generated session key due to the inclusion of the session specific random parameters. Hence our device to device AKA provides .
7.3.7. Known Session Specific Information Attack (KSSIA)
Resistance to KSSIA implies that, the exposure of all session parameters () to , may not expose the session key. In the proposed device authentication protocol, both devices and compute . can reveal if and only if he knows or . Knowing only the pair may not help to derive or . Therefore, the proposed protocol resists KSSIA.
7.3.8. Key Off-Set/Replicating Attack
The key replicating attack is a distinction of MIM attack, where one or more active adversaries intercept and modify the exchanged information between devices and in such a way that the modification results into agreement of an incorrect session key. In our proposed protocol the and exchange and . can modify some values by offset and produces and . Nevertheless, remains unable to compute that is agreed by and , as requires the knowledge of the private keys and/or . Hence, the proposed device to device key is resistance to key off-set/replicating attack .
7.3.9. No Key Control
The session key computed between and contains equal share of both participants, i.e., both participants add their session parameters as well as their private keys. Therefore, none of the participant has any control on session key formation and proposal provides No Key Control (NKC) property.
7.3.10. Replay Attack
Our proposed protocol is free from replay attack (RA). Any adversary can replay any old message say exchanged between to legal devices. However, the timestamp is also a part of message in plain text as well as hidden in . The receiver can easily detect the freshness and discard the message in case it is replayed. Same is the case, if against any request, the adversary replays an old reply message say , the initiator will easily detect the replay and will discard the message.
8. Performance Analysis
This section shows the comparative performance measure of the proposed protocol with existing protocols [13,31,32,36,37] in terms of computation and communication efficiency. Following notations and their running time computed by Kilinic and Yanik [42] on a Dual CPU with 2.20 GHz speed and with 2048 MB of RAM, were used for computation cost analysis:
- ms: Cost of modular exponentiation
- ms: Cost of Point multiplication over ECC
- ms: Cost of Point multiplication over ECC
- ms: Cost of hash function
- ms: Cost of bilinear pairing operation
- ms: Cost of symmetric encryption
Table 3 shows a comprehensive performance comparisons; referring the table, the proposed scheme completed the key exchange process by performing operations and with running time ≈ 13.42 ms. Mandal et al.’s protocol accomplished the same with operations and a running time of ms. The protocol proposed by Islam-Biswas completed it in ms by performing operations. Wang et al.’s protocol performed operations and completed the authentication process in ms. Holbl-Walzer protocols [13] accomplished authentication in and respectively with running time ≈ 46.48 ms and ≈ 34.866 ms respectively. The proposed protocol funished the authentication with slight higher computation time as compared with Mandal et al. and Islam-Biswas protocols, whereas it was efficient as compared with other related protocols. For communication cost, we considered an ECC point of size 160 bits, the output of hash function (SHA-1) is 160 bits and for simplicity identity was also taken as 160 bit, with timestamps of 32 bits length. The communication cost of the proposed protocol was just 168 bytes in comparison with Mandal et al.’s 252 bytes, Islam-Biswas’s 120, Ni et al.’s 132 bytes, Wang et al.’s 66 bytes and Holbl-Walzer’s 258 bytes. The communication cost of the proposed protocol was less than Mandal et al. and Holbl-Wazler’s protocols and more than Islam-Biswas, Ni et al. and Wang et al.’s protocols. Therefore, the proposed protocol achieved a good trad-off between computation and communication efficiencies.

Table 3.
Communication and Computation cost.
9. Conclusions
In this paper, we have simulated key compromise impersonation attack (KCIA) on two recent ECC and self certified public key based authentication protocols. It has been shown that both the protocols of Islam-Biswas and Mandal et al. are not only insecure against KCIA, but also lacking anonymity. We then proposed an improved protocol to resist KCIA and related known attacks and to provide anonymity and related important security features. Proposed scheme is tailored to work in IoT-based fast moving vehicular networks and does not require involvement of a third party for sharing a key between two smart vehicles. The security of proposed scheme is analyzed through formal and informal methods. Although, proposed protocol accomplishes the authentication with slight high computation and communication costs as compared with related protocols but it provides resistance against all known attacks and encompasses all required security features. Hence, the proposed protocol is best suited for key exchange in device to device using certificates.
Author Contributions
B.A.A. wrote the initial draft as well as revision and BAN logic analysis of the proposed scheme. S.A.C. conceptualized the idea and performed cryptanalysis and designed the new scheme. A.B., and A.A.-B. performed security and efficiency analysis. T.S. performed formal analysis, proof read and supervised the whole process. All authors have read and agreed to the published version of the manuscript.
Funding
This Project was funded by the Deanship of Scientific Research (DSR), at King Abdulaziz University, Jeddah, under grant no. (RG-7-611-40). The authors, therefore, acknowledge with thanks DSR for technical and financial support. This research was supported by Energy Cloud R&D Program through the National Research Foundation of Korea(NRF) funded by the Ministry of Science, ICT (2019M3F2A1073386).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Chen, C.M.; Xiang, B.; Liu, Y.; Wang, K.H. A secure authentication protocol for internet of vehicles. IEEE Access 2019, 7, 12047–12057. [Google Scholar] [CrossRef]
- Diffie, W.; Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Chen, T.H.; Lee, W.B.; Chen, H.B. A round-and computation-efficient three-party authenticated key exchange protocol. J. Syst. Softw. 2008, 81, 1581–1590. [Google Scholar] [CrossRef]
- Lu, R.; Cao, Z. Simple three-party key exchange protocol. Comput. Secur. 2007, 26, 94–97. [Google Scholar] [CrossRef]
- Phan, R.C.W.; Yau, W.C.; Goi, B.M. Cryptanalysis of simple three-party key exchange protocol (S-3PAKE). Inf. Sci. 2008, 178, 2849–2856. [Google Scholar] [CrossRef]
- Chen, C.M.; Wang, K.H.; Yeh, K.H.; Xiang, B.; Wu, T.Y. Attacks and solutions on a three-party password-based authenticated key exchange protocol for wireless communications. J. Ambient Intell. Humaniz. Comput. 2019, 10, 3133–3142. [Google Scholar] [CrossRef]
- Pu, Q.; Zhao, X.; Ding, J. Cryptanalysis of a three-party authenticated key exchange protocol using elliptic curve cryptography. In Proceedings of the International Conference on Research Challenges in Computer Science, ICRCCS’09, Shanghai, China, 28–29 December 2009; pp. 7–10. [Google Scholar]
- Tan, Z. An Enhanced Three-Party Authentication Key Exchange Protocol Using Elliptic Curve Cryptography for Mobile Commerce Environments. J. Commun. 2010, 5, 436–443. [Google Scholar] [CrossRef]
- Tseng, Y.M. An efficient two-party identity-based key exchange protocol. Informatica 2007, 18, 125–136. [Google Scholar]
- Günther, C.G. An identity-based key-exchange protocol. In Proceedings of the Workshop on the Theory and Application of of Cryptographic Techniques, Houthalen, Belgium, 10–13 April 1989; pp. 29–37. [Google Scholar]
- Saeednia, S. Improvement of Günther’s identity-based key exchange protocol. Electron. Lett. 2000, 36, 1535–1536. [Google Scholar] [CrossRef]
- Hsieh, B.; Sun, H.; Hwang, T.; Lin, C. An improvement of Saeednia’s identity-based key exchange protocol. Inf. SecuR. Conf. 2002, 2002, 41–43. [Google Scholar]
- Hölbl, M.; Welzer, T. Two improved two-party identity-based authenticated key agreement protocols. Comput. Stand. Interfaces 2009, 31, 1056–1060. [Google Scholar] [CrossRef]
- Zhang, S.; Cheng, Q.; Wang, X. Impersonation attack on two identity-based authenticated key exchange protocols. In Proceedings of the 2010 WASE International Conference on Information Engineering, Beidaihe, China, 14–15 August 2010. [Google Scholar]
- Smart, N. Identity-based authenticated key agreement protocol based on Weil pairing. Electron. Lett. 2002, 38, 630–632. [Google Scholar] [CrossRef]
- Chen, L.; Kudla, C. Identity based authenticated key agreement protocols from pairings. In Proceedings of the 16th IEEE Computer Security Foundations Workshop, Pacific Grove, CA, USA, 30 June–2 July 2003; pp. 219–233. [Google Scholar]
- Shim, K. Efficient ID-based authenticated key agreement protocol based on Weil pairing. Electron. Lett. 2003, 39, 653–654. [Google Scholar] [CrossRef]
- Sun, H.M.; Hsieh, B.T. Security Analysis of Shim’s Authenticated Key Agreement Protocols from Pairings. IACR Cryptol. EPrint Arch. 2003, 2003, 113. [Google Scholar]
- Ryu, E.K.; Yoon, E.J.; Yoo, K.Y. An efficient ID-based authenticated key agreement protocol from pairings. In International Conference on Research in Networking; Springer: Berlin/Heidelberg, Germany, 2004; pp. 1458–1463. [Google Scholar]
- Boyd, C.; Choo, K.K.R. Security of two-party identity-based key agreement. In Proceedings of the International Conference on Cryptology in Malaysia, Kuala Lumpur, Malaysia, 28–30 September 2005; pp. 229–243. [Google Scholar]
- McCullagh, N.; Barreto, P.S. A new two-party identity-based authenticated key agreement. In Proceedings of the Cryptographers’ Track at the RSA Conference, San Francisco, CA, USA, 14–18 February 2005; pp. 262–274. [Google Scholar]
- Shao, Z.-H. Efficient authenticated key agreement protocol using self-certified public keys from pairings. Wuhan Univ. J. Nat. Sci. 2005, 10, 267–270. [Google Scholar]
- Ni, L.; Chen, G.; Li, J.; Hao, Y. Strongly secure identity-based authenticated key agreement protocols. Comput. Electr. Eng. 2011, 37, 205–217. [Google Scholar] [CrossRef]
- Cao, X.; Kou, W.; Yu, Y.; Sun, R. Identity-based authentication key agreement protocols without bilinear pairings. IEICE Trans. Fundam. 2008, 12, 3833–3836. [Google Scholar] [CrossRef]
- Tsaur, W.J. Several security schemes constructed using ECC-based self-certified public key cryptosystems. Appl. Math. Comput. 2005, 168, 447–464. [Google Scholar] [CrossRef]
- Hölbl, M.; Welzer, T.; Brumen, B. An improved two-party identity-based authenticated key agreement protocol using pairings. J. Comput. Syst. Sci. 2012, 78, 142–150. [Google Scholar] [CrossRef]
- Chen, L.; Cheng, Z.; Smart, N.P. Identity-based key agreement protocols from pairings. Int. J. Inf. Secur. 2007, 6, 213–241. [Google Scholar] [CrossRef]
- Choo, K.K.R.; Boyd, C.; Hitchcock, Y.; Maitland, G. On session identifiers in provably secure protocols. In Proceedings of the International Conference on Security in Communication Networks, Amalfi, Italy, 8–10 September 2004; pp. 351–366. [Google Scholar]
- Li, S.; Yuan, Q.; Li, J. Towards Security Two-part Authenticated Key Agreement Protocols. IACR Cryptol. EPrint Arch. 2005, 2005, 300. [Google Scholar]
- Wang, S.; Cao, Z.; Choo, K.K.R.; Wang, L. An improved identity-based key agreement protocol and its security proof. Inf. Sci. 2009, 179, 307–318. [Google Scholar] [CrossRef]
- Islam, S.H.; Biswas, G. Design of two-party authenticated key agreement protocol based on ECC and self-certified public keys. Wirel. Pers. Commun. 2015, 82, 2727–2750. [Google Scholar] [CrossRef]
- Mandal, S.; Mohanty, S.; Majhi, B. Cryptanalysis and Enhancement of an Anonymous Self-Certified Key Exchange Protocol. Wirel. Pers. Commun. 2018, 99, 863–891. [Google Scholar] [CrossRef]
- Khatwani, C.; Roy, S. Security Analysis of ECC Based Authentication Protocols. In Proceedings of the 2015 International Conference on Computational Intelligence and Communication Networks (CICN), Jabalpur, India, 12–14 December 2015; pp. 1167–1172. [Google Scholar]
- Chaudhry, S.A.; Shon, T.; Al-Turjman, F.; Alsharif, M.H. Correcting design flaws: An improved and cloud assisted key agreement scheme in cyber physical systems. Comput. Commun. 2020, 153, 527537. [Google Scholar] [CrossRef]
- Mansoor, K.; Ghani, A.; Chaudhry, S.A.; Shamshirband, S.; Ghayyur, S.A.K.; Mosavi, A. Securing IoT-Based RFID Systems: A Robust Authentication Protocol Using Symmetric Cryptography. Sensors 2019, 19, 4752. [Google Scholar] [CrossRef]
- Wang, S.; Cao, Z.; Cao, F. Efficient Identity-based Authenticated Key Agreement Protocol with PKG Forward Secrecy. Int. J. Netw. Secur. 2008, 7, 181–186. [Google Scholar]
- Ni, L.; Chen, G.; Li, J.; Hao, Y. Strongly secure identity-based authenticated key agreement protocols in the escrow mode. Sci. China Inf. Sci. 2013, 56, 1–14. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Khan, M.K.; Wang, L.; Shen, J. Efficient Privacy-Aware Authentication Scheme for Mobile Cloud Computing Services. IEEE Syst. J. 2018, 12, 1621–1631. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, Y.; Tang, S.; Luo, H. Privacy Protection for E-Health Systems by Means of Dynamic Authentication and Three-Factor Key Agreement. IEEE Trans. Ind. Electron. 2018, 65, 2795–2805. [Google Scholar] [CrossRef]
- Hussain, S.; Chaudhry, S.A. Comments on “Biometrics-Based Privacy-Preserving User Authentication Scheme for Cloud-Based Industrial Internet of Things Deployment”. IEEE Internet Things J. 2019, 6, 10936–10940. [Google Scholar] [CrossRef]
- Ghani, A.; Mansoor, K.; Mehmood, S.; Chaudhry, S.A.; Rahman, A.U.; Najmus Saqib, M. Security and key management in IoT-based wireless sensor networks: An authentication protocol using symmetric key. Int. J. Commun. Syst. 2019, 32, e4139. [Google Scholar] [CrossRef]
- Kilinc, H.H.; Yanik, T. A survey of SIP authentication and key agreement schemes. IEEE Commun. Surv. Tutor. 2014, 16, 1005–1023. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).