1. Introduction
The prompt emergence of surveillance systems within metropolitan areas and services has been required to fulfill the necessities of the people for a better quality of life. Appropriately, there has been a remarkable evolution of digital devices, for example, smartphones, sensors, smart applications, actuators, and intelligent machines, which led to clear business goals for the Internet of Things (IoT) industry. Now it is conceivable to interconnect all nodes and build connections between them over the internet. The smart city is getting more intelligent than in the past due to the modern development of computer-aided technologies. Smart cities incorporate diverse kinds of electronic applications; for example, cameras in an observing framework, and sensors in a transportation framework. A smart city framework upgraded by the IoT innovation turns into a revolutionary idea; it likewise gets new concerns about the security of the information. Closed-circuit television cameras (CCTV) have emerged as the essential component of a smart city [
1].
A CCTV system within a smart city may involve hundreds or thousands of IP based IoT cameras that operate
and generate a vast amount of digital content daily. The number of public and private CCTV is increasing day by day. Additionally, with improving image processing technology, it is possible to obtain diverse information [
2]. Recently, CCTV has been helping in many sectors of life. Therefore, it is necessary to ensure CCTV image integrity. The present control method and the dynamic multimedia innovation advancement made it conceivable in any event, for a fledgling to effectively erase an item from a video sequence. It is also possible to include an article from another video source or to add an article created by illustrations in programming software. The improvement of image analysis innovation via artificial intelligence CCTV, is likewise effectively underway. With the ascent of artificial intelligence (AI) and profound learning methods, the presence of advanced counterfeiting has multiplied in recent years. Now, deepfakes have the capability of modifying reality and disintegrating trust by giving false reality [
3]. A built-in video compression algorithm is usually used in surveillance cameras. To forge a video, the intruder has to decompress the video, change its data, and re-compress again. It can be analyzed by the noise characteristics of frame compression [
4].
Blockchain is overwhelming the world, to a great extent, because of the achievement of digital currency. A blockchain, also called a distributed ledger, is a write-only data structure kept up by a lot of nodes that do not wholly confide in one another. Many studies combine blockchain and image and video processing algorithms. Applications include combating deepfake videos [
5], medical image processing [
6], image encryption [
7], and digital content rights management [
8]. A decentralized solution based on blockchain for digital video obtained by dashboard cameras is presented by [
9]. The presented technique enables proving that video has not been tampered based on time stamping, allowing it to be presented as proof in the court. Blockchain innovation’s core segment is an innovative protocol that empowers information to be traded among different entities inside a system. As such, it does not require any intermediaries, since system members are connected with encrypted identities and legitimately with one another utilizing distributed communication. Each transaction is then added to a changeless ledger chain and distributed to every node. With the ascent of information breaches, extortion, and fraud, a number of projects are utilizing blockchain innovation for document and identity approval [
10]. Validation through blockchain is achieved through end-to-end encryption, time-stamping, and checking for legitimacy.
Table 1 shows the existing state of knowledge articles and proposed gap, which we intend to fill for smart cities.
In this paper, we suggest a system model that can manage, use, and authenticate CCTV. This model allows a CCTV’s data center to verify a CCTV film and surveillance camera. We structured and executed a procedure that can more reliably check video forgery and detect forgery by applying high-security blockchain technology to CCTV. Specifically, by dispersing and sharing a number of CCTV pictures among blockchain participating nodes, it is conceivable to limit the issue of a single point of failure, which is a blockchain advantage. It can also be recognized as evidence under criminal law. A single point of failure is one issue that can make the whole framework stop working. It can be brought about by a variety of factors, including machine malfunctions, purposeful or accidental human behavior, and power outages.
The remainder of this paper is organized as follows:
Section 2 provides the existing research.
Section 3 describes materials and methods, which include the introduction of blockchain technology and details about the proposed scheme.
Section 4 describes the obtained simulation results and analyses.
Section 5 presents a discussion about our proposed system. Finally,
Section 6 concludes this paper.
2. Related Work
Smart Cities are seen as ecosystems that are commonly characterized as networks of associating devices and their surroundings, and are ordinarily depicted as perplexing systems shaped in light of resource interdependencies. Gretzel et al. [
21] included four progressively essential components that exist in this ecosystem’s definition of a smart city. These are interaction or engagement, balance, loosely coupled actors with shared objectives, and finally, self-organization. Numerous IoT gadgets need memory and computational complexities to cope with modern computing devices. Lack of computational power makes them defenseless against a broad scope of cyber attacks. Javaid et al. [
22] displayed an IoT device and server correspondence framework using at Ethereum. They addressed the issue of security issues related to distributed denial of service (DDOS) attacks in the IoT system. They utilized a modified smart contract that empowers a superior resistance mechanism against DDoS and rogue device assaults. Kim et al. [
23] presented an idea of using blockchain technology to solve the security issues of a sensor-based platform. IoT devices are the main components of smart homes, smart factories, and intelligent appliances, which are of great importance. They also concluded that the global market of sensors is expected to grow up to 220 trillion KRW by 2021. So it very important to solve the issue of a substantial sensor market. They proposed a blockchain-based authentication protocol to address security issues. By using that protocol, the IoT environment can become efficient and stable. Heng et al. [
24] used the smart contract of Hyperledger Fabric for the task management of sensors. They used this feature of blockchains in the IoT environment to ensure the verification at runtime of sensors and actuators. The use of smart contracts makes it easy to automate the business logic and helps in time-saving with the surety of zero error.
Substantial work has been done in the field of video forensics. This advancement allows the video evidence to be used in court cases. Recent techniques used for video forgery detection are mainly based on an autoencoder with recurrent convolutional neural networks, an auto-encoder with a goturn algorithm, watermarking techniques, and digital signatures. Reference [
25] proposed an autoencoders and recurrent neural networks based architecture to detect the video forgery. They trained a long short-term memory (LSTM) model to exploit dependencies. Reference [
26] introduces a model to identify the trustworthiness of digital videos using an auto-encoder with a goturn algorithm. Zheng et al. [
27] used the watermarking system of authenticating the sensor data. In their work, they combine spatial and temporal watermarking to obtain compression survival authentication. Sowmya et al. [
28] discussed the spatio-temporal triad feature relationship to authenticate a video. They generated a unique content-based signature to detect inter and intraframe forged videos. In expansion, regardless of whether an image examination innovation is created, there are numerous instances of breakdown because of the restriction of the sensor. It can likewise happen when controlling images for harmful purposes. [
29] explored the correlations between the noise residues at the neighboring blocks level. They also used the Bayesian classifier to get an optimal threshold value. However, this technique can miscalculate the forgery in case of a calculation error in noise residues. In [
30], multiple feature hashing is introduced to deal with the accuracy issues of near-duplicate video retrieval (NDVR). They introduced content-based video hashing methods to ensure the authenticity of video features. However, their approach is sensitive towards the manipulation of content and more focused on video retrieval and identification instead of content-preserving manipulations.
In expansion, an assortment of reasons undermines the respectability of video information caught on CCTV [
31]. On the other hand, CCTV-based administrations are being reinforced and diversified. Therefore, to offer assistance accurately, the trustworthiness of an image was observed by Kwon and his associates [
32]. The Privacy Act takes into account the establishment of CCTVs for public places, which requires reaching out to the proprietors of CCTVs to get video information. However, this procedure takes a lot of time. Regardless of whether a video is procured, it is hard to use in open organizations because the video is not ensured to be an original video that it has not been manipulated. Panwar et al. [
33] proposed a structure to give sensor information confirmation through cryptographic algorithms implementing a log sealing system and creating permanent pieces of evidence utilized for log verification. The structure guarantees that sensor information and log-fixed data could be put away in untrusted storage with the proposed verification system ensuring its integrity. However, this structure depends on the reliability in the instrument; for example, Intel SGX to store the fixed data in an incorporated way. False news has become a global issue that raises extreme difficulties for human culture and the majority rules system. This issue has emerged because of the development of various accompanying technological marvels. Qayyum et al. [
34] have presented the cutting edge—to the point of producing disquietude—of realistic-looking fake data and concentrated explicitly on the marvels of fake news. To address the fake news issue, they have proposed a blockchain-based structure for the identification and alleviation of fake news. They have portrayed a significant level of plan for our answer. They recommend a significant level diagram of a blockchain-based system for counterfeit news avoidance and feature the different structural issues and considerations regarding such a blockchain-based structure for handling fake news.
A video record assumes a critical job in giving proof to crime scenes or street mishaps. In any case, the principle issue with the video record is that it is regularly vulnerable against different video altering attacks. Ghimire et al. [
35] proposed an integrity verification strategy dependent on a blockchain. In their approach, video content with foreordained fragments is key-hashed in a constant way and put away in a sequentially fastened manner along these lines, building up a database. However, they did not discuss the spectrum of the proposed approach, and implementation details were also missing. Kerr et al. [
36] exhibited a practical execution of blockchain technology implemented to the assignment of analyzing CCTV video proof. Their prototype method worked great in production circumstances and demonstrated promising review and dependability properties. However, the visible watermark can not be recommended as a secure solution to protect the video from forgery. The addition of new nodes and the participants’ verification method was also not discussed. In our proposed approach, we have addressed the existing limitations.
3. Materials and Methods
We have used the blockchain platform for the authenticity and verification of data for smart cities. In this section, we explain the flow of the proposed platform and its components in detail.
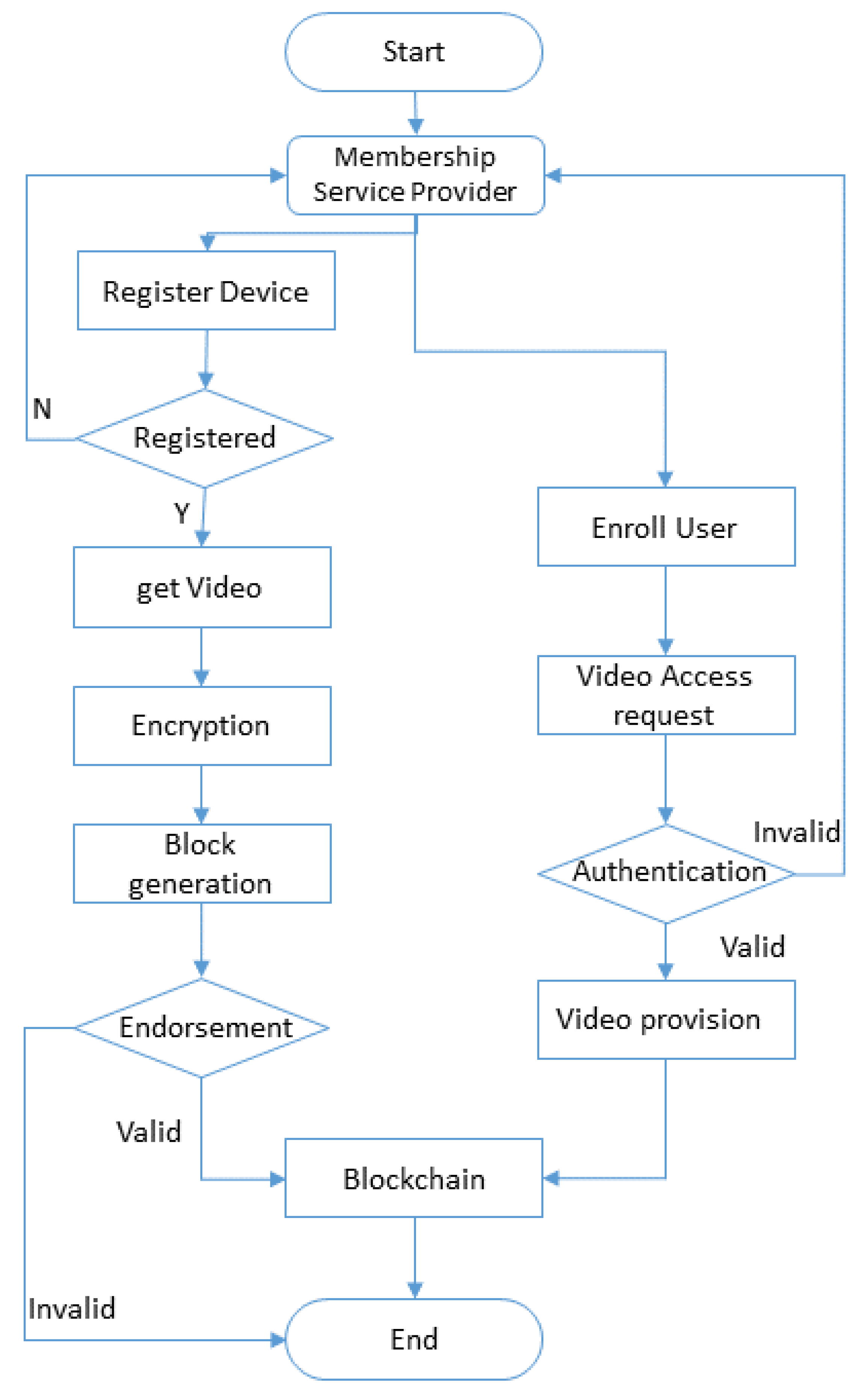
Figure 1 illustrates the flow of our proposed model. It starts with the enrollment of users and registration of the devices. The membership service provider (MSP) assigns a unique key to every peer of the system. Only valid devices and users can access the system. We are using a Hyperledger Fabric that is a private blockchain, and it is different from public blockchain, in terms of user access. In a public blockchain, any user can enroll in the system, but in private, only valid users who have the private key assigned by the system admin can access the system. The proposed system gets the video and metadata of the imaging sensor and encrypts that data. After encryption, it makes a block, and every block is endorsed by endorsing peers. In Hyperledger Fabric, there is no consensus algorithm or no mining of the blocks. But to meet the validation purpose, there are validation peers who are nominated by the system admin. The valid use can generate requests through REST API to access the digital data from the blockchain.
3.1. Blockchain Technology
A blockchain emulates a central computing service through a distributed protocol, run by nodes connected over the Internet. The blockchain technically is replacing current centralized ledger systems with the decentralized ledgers. A blockchain uses encryption techniques, and it does not have the involvement of a third part, which makes it reliable [
37]. A blockchain is composed of a chain of data block. Blocks can be composed and read by specific members, and entries are changeless, transparent, and accessible. Transactions are recorded in sequential order on a consistently developing database. A system of computers is associated through the web, wherein clients at any computer can get or send a data to another computer. Information is duplicated and put away over the framework over a shared system. It encourages shared exchange of significant worth without a central intermediary [
38]. Hyperledger Fabric is an open source distributed ledger platform for private blockchains [
39]. It offers a great scalability and it has been used in many fields of life.
Blockchain technology is relied upon to offer tremendous potential for bringing radical changes in a broad scope of enterprises, business models, and working procedures; for example, installment, bookkeeping, and inspecting. From the perspective of its specialized, multifaceted nature and the need for acknowledging these sweeping changes in the private, public, and commercial areas, this innovation, in the same way as other disruptive advancements previously, will get on gradually with a reasonable increment of pace over time [
40]. The current focal point of blockchain innovation is essentially on utilizing it to approve, execute, and store transactions, which is the reason its improvement has been fundamentally driven by the money-related industries. Still, it is currently spreading across the further markets.
3.1.1. Important Features Of Blockchain Technology
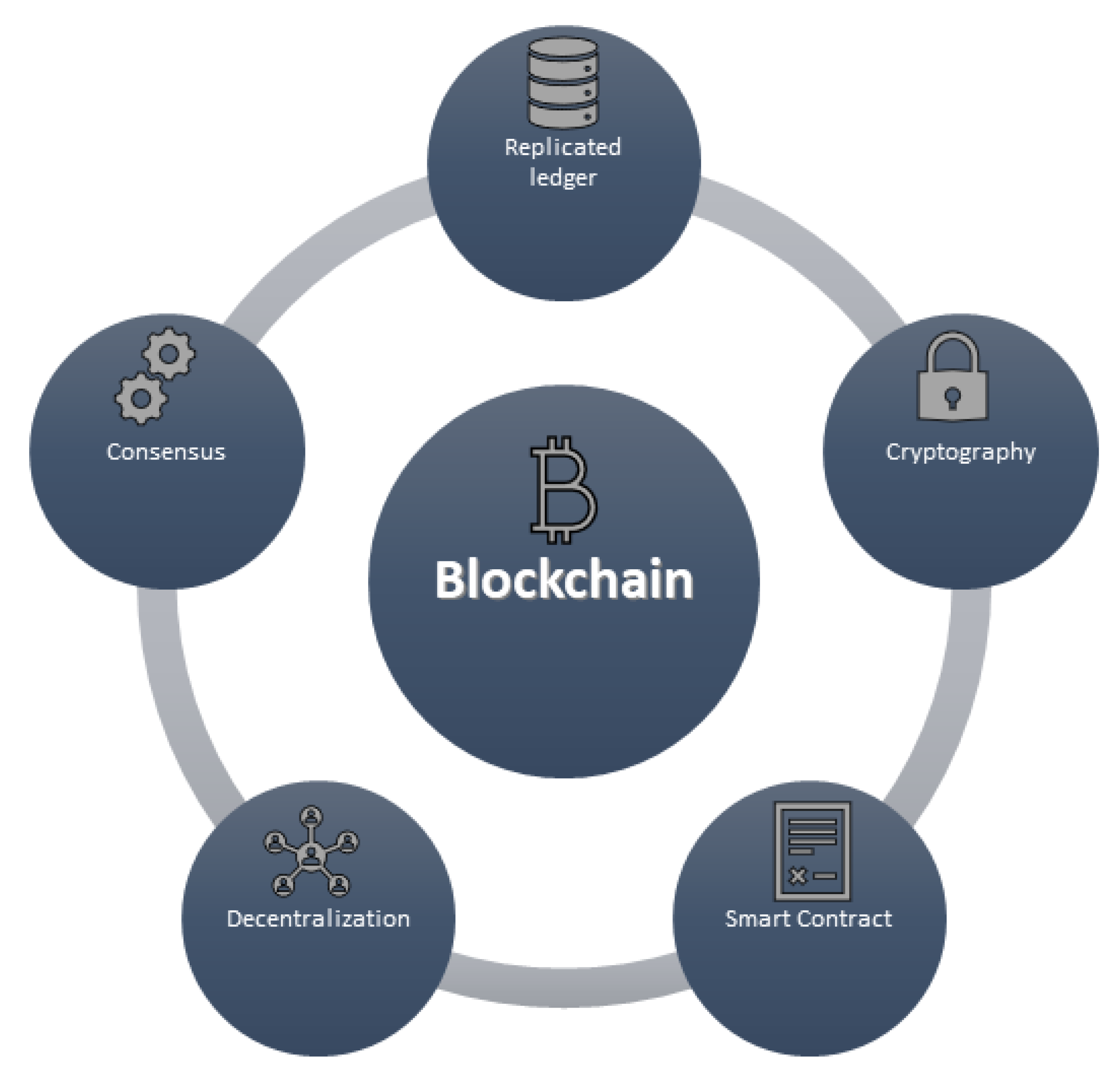
Figure 2 shows the important basic features of a blockchain.
Replicated ledger: In the blockchain, data is not stored on a central point. Blocks are distributed and replicated among the nodes. Each node contains a copy of the complete ledger. It eliminates the risks of data loss.
Cryptography: Data, which is stored on the blockchain, is encrypted by its strong encryption algorithms. Hence, the integrity of all transactions and data is supported with digital signatures.
Consensus: Every block contains a different number of transactions. Transactions need to be validated before adding to the existing blocks. In Hyperledger Fabric, there are validating nodes that validate every block before adding them into the chain.
Smart contract: Blockchain provides an electronic version of the contract between two parties. The smart contract is computer code intended to digitally facilitate, verify, or enforce the negotiation.
Decentralization: All transactions are shared without centralized control. Decentralization provides the trust and safety of the data.
3.1.2. Block
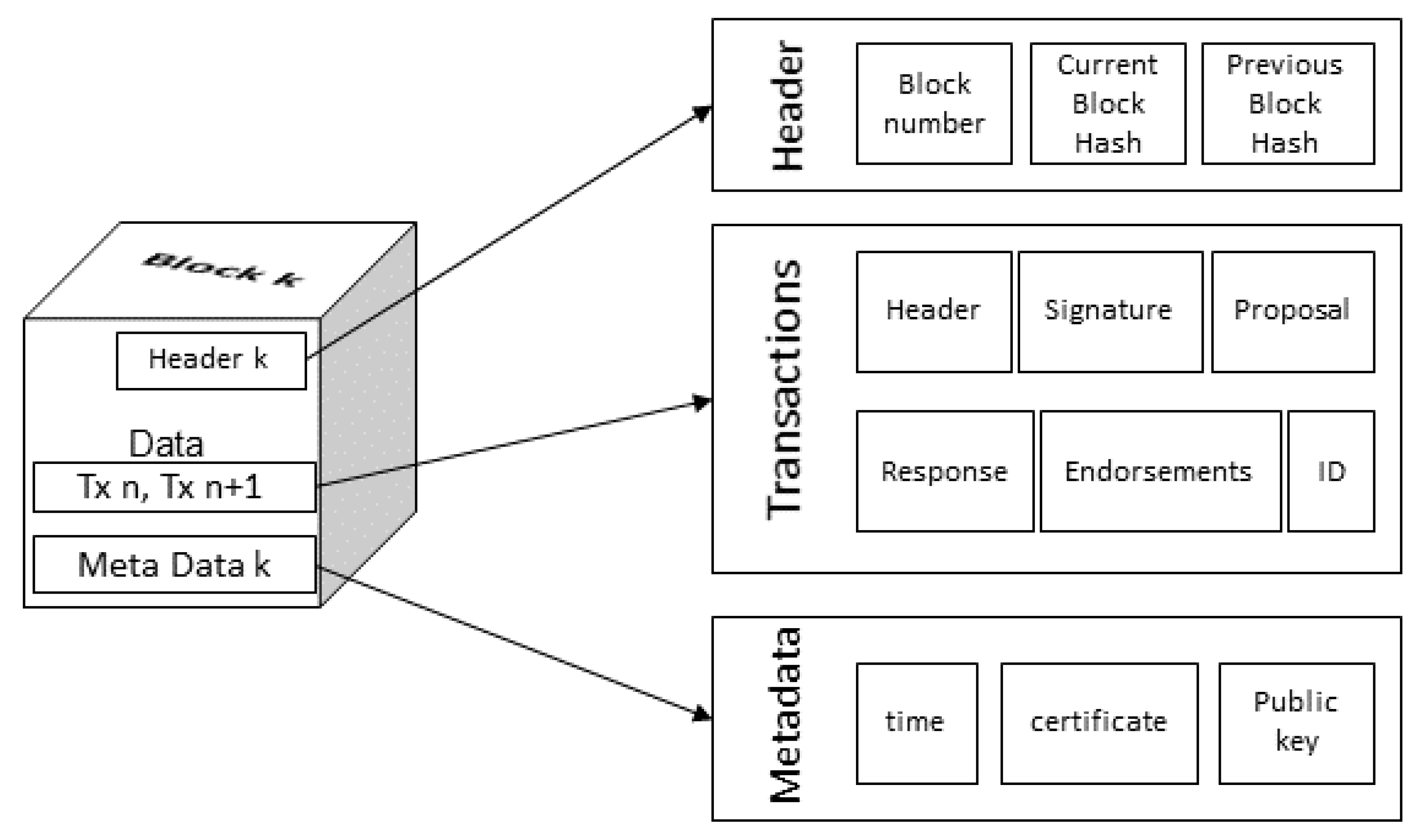
The genesis block is the very first block in a blockchain. It is the opening point for the ledger, though it does not hold any user transactions [
41]. Instead, it includes an initial state of the network within the configuration transaction. Block comprises three sections: the header, transaction, and metadata. Metadata are written when a block is created.
Figure 3 depicts a white box diagram of the
block of a blockchain.
The header of the block captures some essential information about the transaction. It contains the current block number, the hash of the current block, and the hash of the previous block. The data within the blockchain include different transactions [
42]. Each transaction consists of a unique ID, header, cryptographic signature, proposal, response, and endorsement. Input parameters provided by an application to the smart contract are encoded in the proposal, which forms the suggested ledger update. The response obtains the before and after cases of the world state, as a read write set (RW-set). It is the product of a smart contract, and if the transaction is successfully verified, it will be implemented on the ledger to renew the world state. The endorsement is a list of signed transaction acknowledgments from every required organization, adequate to meet the endorsement policy. Block metadata includes a certificate, a public key, the writing time of the block, and the signature of the block writer.
3.1.3. Transactions
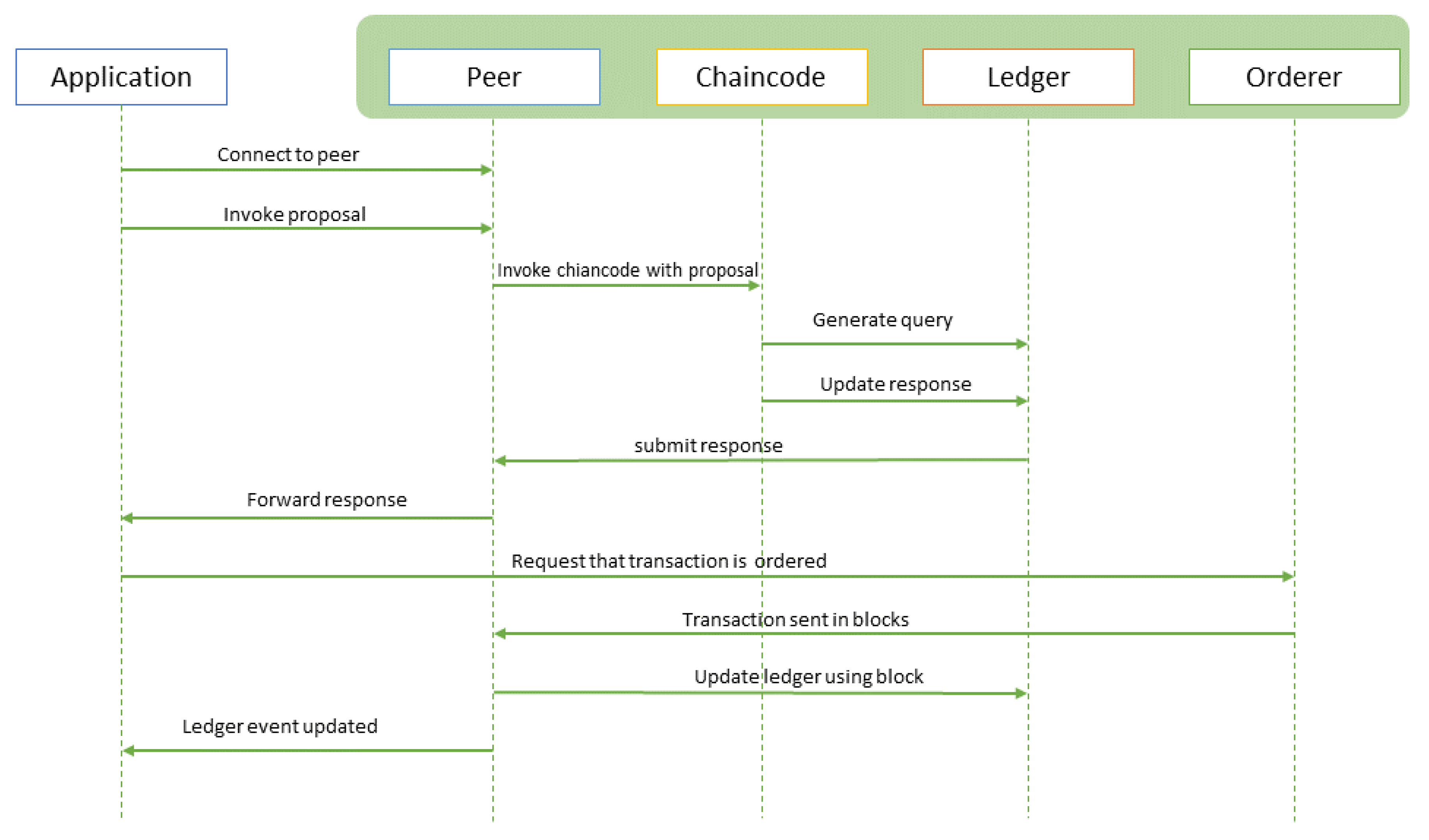
Figure 4 shows the process of transaction processing by application in Hyperledger Fabric v1.4. Before initiating a transaction, the authentication of the application by the membership service provider (MSP) is completed [
43]. The authenticated client app starts the transaction process by connecting to the peer. After connecting, it invokes the transaction proposal to said peer. The peer then invokes the chaincode with that proposal, and the chaincode generates the requested query for the ledger. The chaincode can also propose a ledger update. The ledger sends back the response to the peer, which further forwards this response to the application. After receiving the request, the response application generates a claim that a transaction should be ordered to the orderer. The orderer collects transactions from the network, generates blocks, and sends them to all peers. The peer receives the block and updates the ledger after verification.
3.1.4. Smart Contract
A smart contract is a computer program that can perform transactions and access blockchain blocks and records. It appends functionality to the blockchain. A smart contract is stored in a distributed database [
44]. A smart contract allows the organization to enforce the desired limitation or validation upon transactions. Different rules and business logic are also coded in smart contracts. It can be viewed as a real-life example of an agreement between two parties. Both parties define some set of rules for the transaction of goods or services. But in a smart contract, these rules are enforced automatically with the help of computer code. Computer code for smart contracts contains parts for opening the deal, performing actions, and exiting.
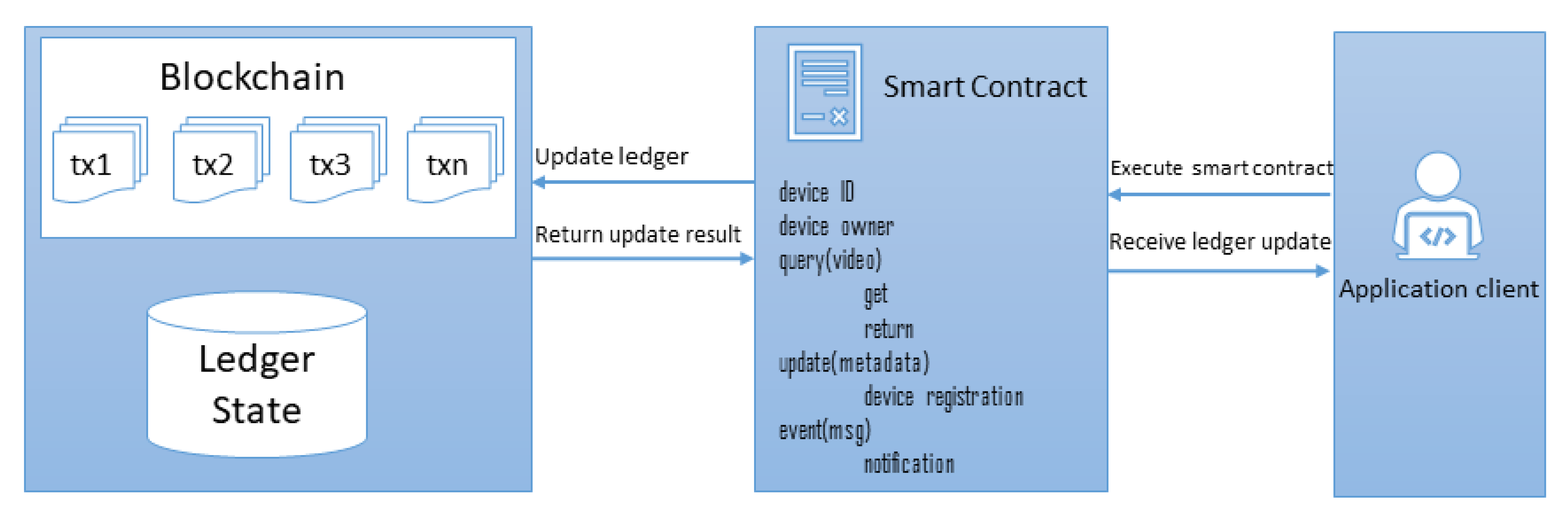
Figure 5 shows the system diagram of the smart contract and its communication with peer nodes. The input parameters determine the new world state. The response contains all the values of the world state as an RW-set.
The pseudo-code used for the operation of smart contracts is detailed in Algorithm 1. In this algorithm, a user requests a particular action. The access function is used to check whether the user can have access to
. It specifies whether that the user is authenticated to use the data generated by
.
| Algorithm 1 Smart contract algorithm for granting access for a particular user request. |
function access() Input :query() Output :granted, denied if message exists & query is valid then check is granted/denied if is registered in the granted list then check role of if = access then return granted else return denied end if else return denied end if else return denied end if end function
|
3.2. Blockchain-Based Secure Data Sharing
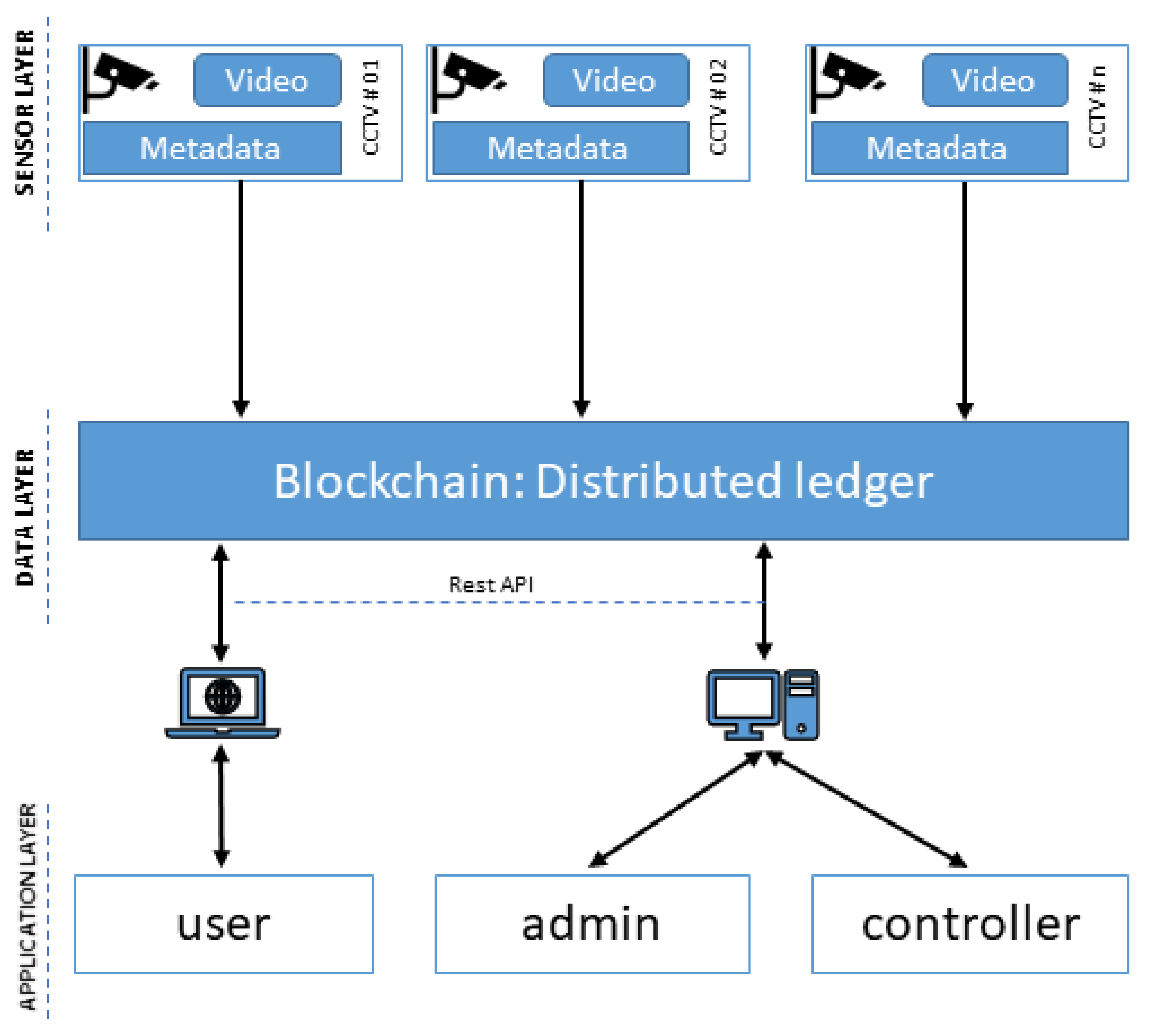
The Blockchain-User Interaction Model represented in
Figure 6 introduces three significant layers—the application, data, and sensor layers; the application layer consists of the user applications run by the clients and network administrators. Users can push and retrieve data using web browsers or client applications. The exchange of data occurs on the middle layer, which consists of the blockchain. This distributed ledger acts as a point of authentication and verification for the data and metadata of surveillance cameras. Different rules and smart contracts also run on this layer. These rules need to be developed in harmony with users, regulatory authorities, and infrastructure providers. Smart contract-based obligations, e.g., transactions of data and physical assets, can, therefore, be settled due to mutual trust in the blockchain. The sensor layer contains the image sensors or surveillance devices, which, in our case, are CCTV cameras.
Blockchain is the backbone of the proposed system. It functions without the need for intermediaries due its peer-to-peer and smart contract capabilities [
45]. Further, trust among stakeholders is not a requirement because distributed ledger platform technology offers encryption features and complete traceability of every block.
3.3. Proposed CCTV Image Forgery and Alteration Verification Technique
The proposed system develops a blockchain interface among CCTV nodes and participants. Some frames of the image are selected and distributed through the blockchain network for image forgery and modulation verification. If all of the continuously created CCTV video frames are stored in the blockchain, the transaction of the blockchain becomes too large, which reduces the data size and increases the possibility of practical use by using only a few frames of every video. Some frames are verified to determine if the image is forged.
Operation Flow
In a smart city, there could be n number of surveillance devices that interact with the IP video server. The control room manages the addition of new devices [
46]. User applications act as a point of interaction with those devices and the blockchain. Image sensors send the sensor data and metadata to the blockchain through its communication interface. The number of frames per second to be extracted is determined according to the policy. If the importance is high, the number of frames per second is increased. Otherwise, only one frame per second is extracted to reduce the transaction size of the blockchain. It constructs block headers for extracted frames; adds CCTV IP and video generation time; performs digital signature with hashing, encryption, and a private key; and distributes generated blocks to the blockchain network. Participating nodes validate the validity of the received blocks and prove their work; and if successful, chain them and store them in a database.
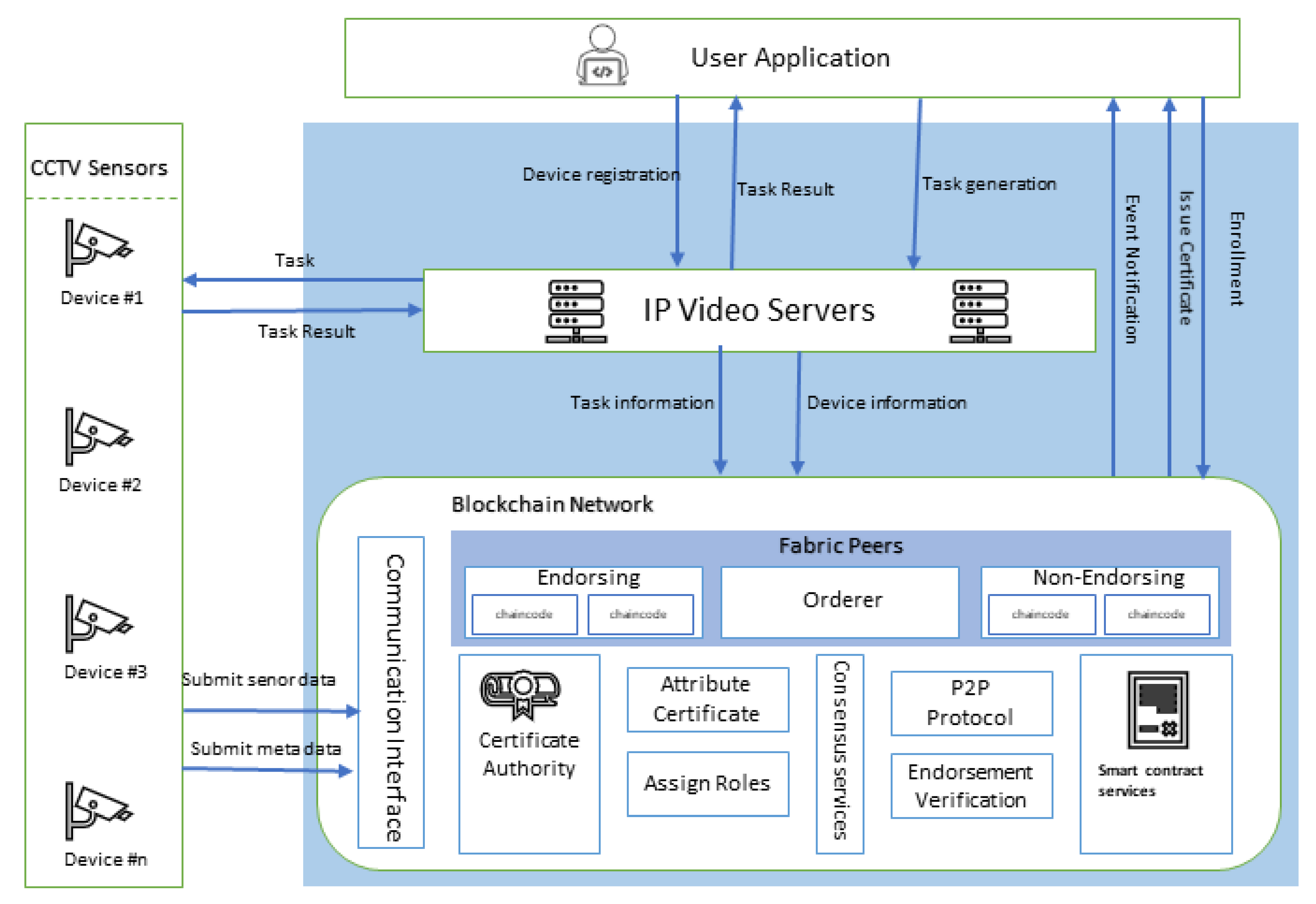
Figure 7 shows the process of verification of image falsification and authentic surveillance node. The node that wants to verify the forgery and alteration of a CCTV image extracts the desired time zone block, and hashes, decodes, and signs to remove the frame. It verifies the forgery by comparing the frame of the image with the extracted frame. If it is the same, the image is not forged or altered. The user registers a new surveillance node on the blockchain through the IP video server. Before adding any modern device, it sends enrollment requests to the blockchain. The membership service provider (MSP) is responsible for issuing a private key to every user. It also sends an event notified after issuing the enrollment certificate. An enrolled user can generate a task through an IP video server. Every CCTV device is connected to the blockchain with the unique hashed key value. Every node sends the periodic metadata to store on the blockchain along with the video and image data. In a blockchain network, there are validating nodes that are specified by the network admin while configuring the system. Each block needs to be endorsed by an authenticating peer before being added into the chain.
4. Results
In this section, we present a developmental evaluation of the proposed scheme using Hyperledger Fabric Composer Playground, and the results. The simulation environment used for implementation is summarized in
Table 2. We have used Ubuntu 18.04.4 LTS operating system on Intel(R) Core(TM) i5-8500 with 16 GB RAM. Version 1.4 of the open-source framework Hyperledger Fabric is used to take full advantage of the latest updates. Composer Playground of Hyper Ledger is used as a development and testing tool, which gives an environment that quickly designs and examines a custom blockchain interface. The Command-line interface CLI composer tool of web-playground is used for the coding of business network definitions.
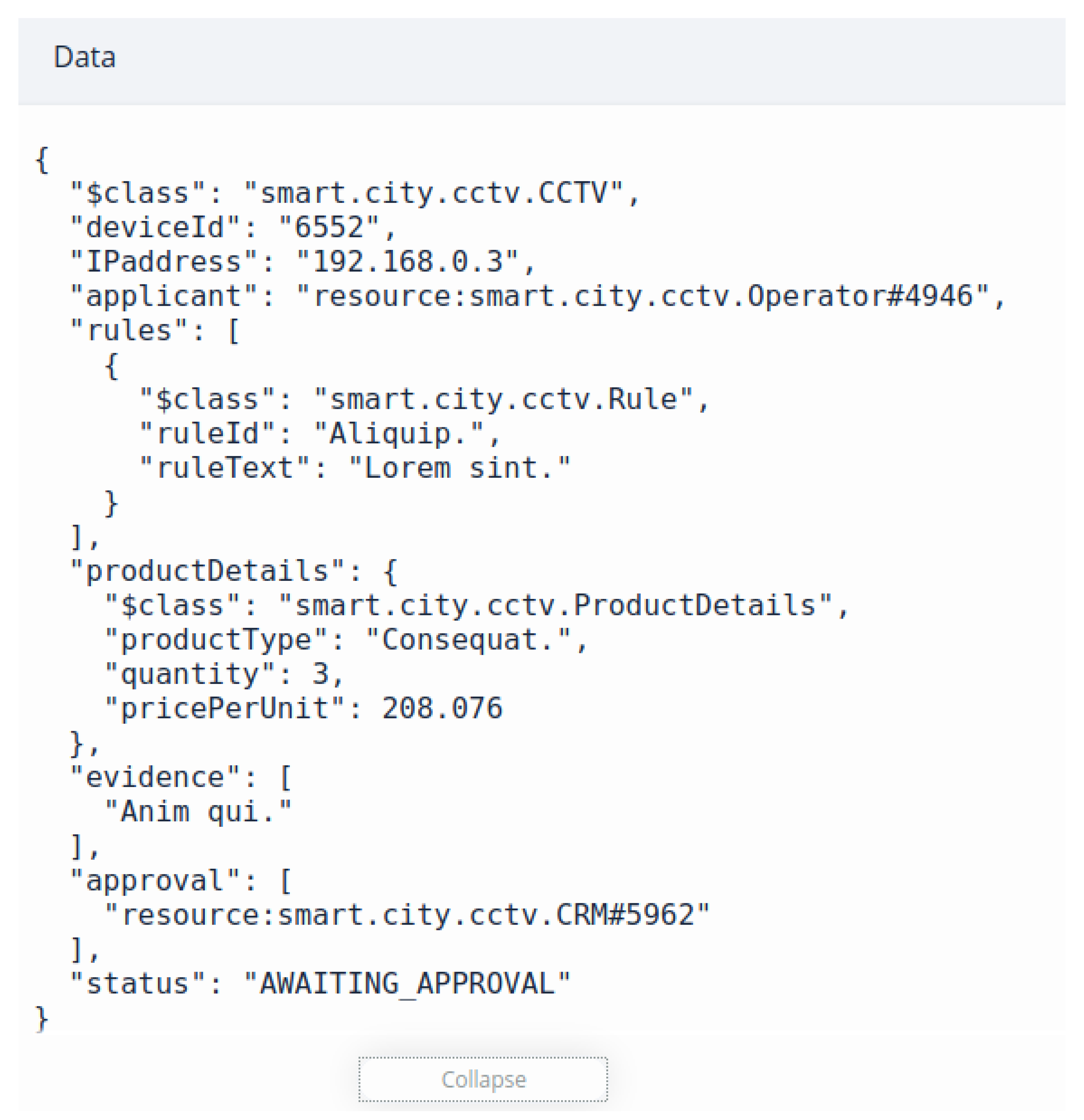
Our main focus is on CCTV cameras in smart cities, so we have used CCTV as an asset for our proposed system. The operator can add new assets in the system after the approval of control room manager. He can define the rules and product details while submitting the request for adding of new device. He also has to define the IP address of a camera.
Figure 8 shows randomly generated data for a newly added asset.
4.1. Participants
Participants are the members of the proposed system. They have their specific jobs and access controls according to the jobs [
47]. Every participant of the blockchain network can initiate a transaction based on assets. They run the business network of the private blockchain.
Table 3 shows the participants and their job descriptions. Instead of using full name, we have used the abbreviations of participants while writing the code and smart contracts. The proposed system consist of six participant types: the control room manager (CRM), control room supervisors (CRS), operators, police officers (POs), police control room operators (PCROs), and local authority staff (LAS).
Figure 9 shows the interface to add new participants. The CRM ensures that all CCTV operators and team leaders are operating all equipment and cameras. The CRS operates all equipment and cameras in line with the CCTV control room policies. Operators perform two types of surveillance, proactive and reactive surveillance; they also do the CCTV video review and administration. POs use police radios to contact CCTV control room operators for incident support using CCTV cameras. PCROs contact the CCTV control room operators for reporting suspicious and actual incidents onsite. LAS use police radios to contact CCTV control room operators.
4.2. Transaction
Every certified participant of the proposed network can start a new transaction based on the rules defined in smart contracts. After successfully executing the transaction, smart contracts generate a response to the participant.
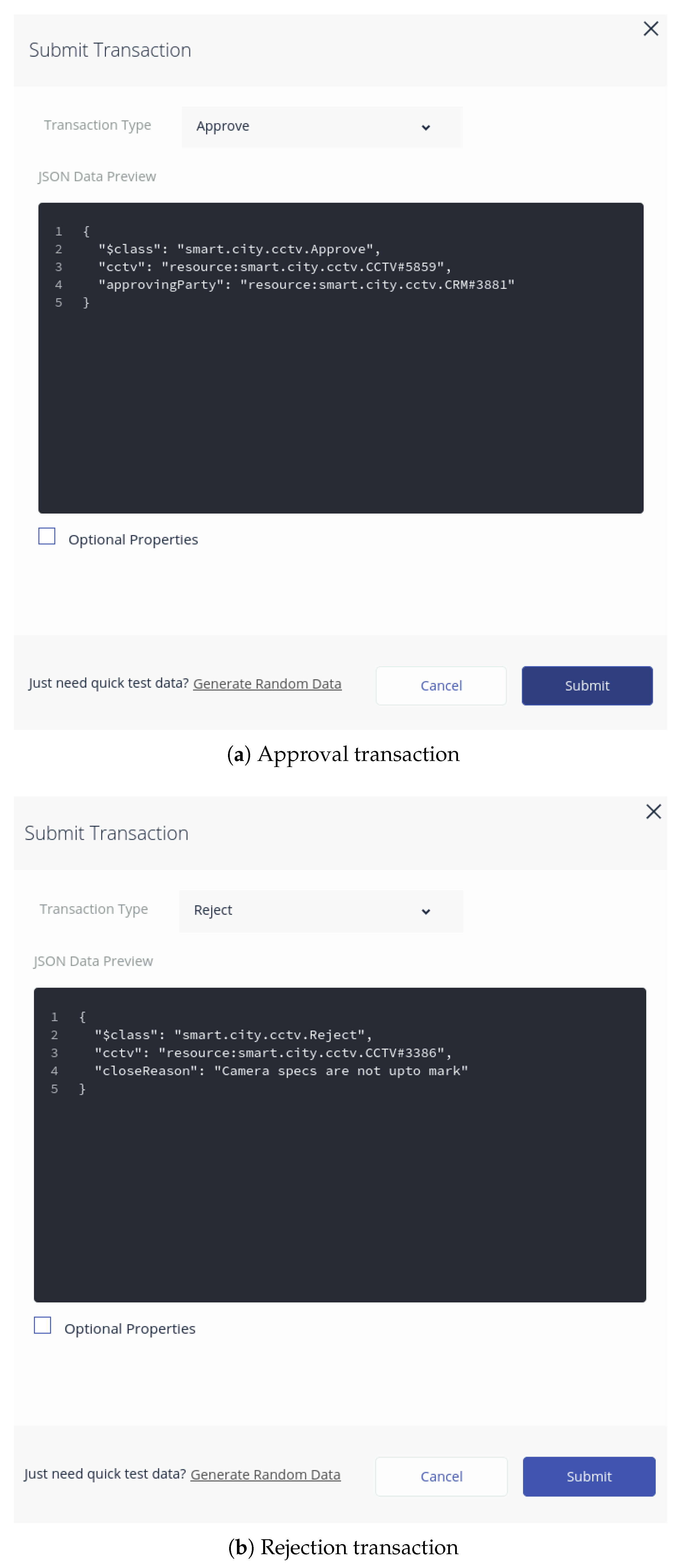
Figure 10 shows two types of transactions.
Figure 10a shows a transaction to approve the addition of a new device by the CRM, and
Figure 10b shows a rejection by the CRM.
On successful completion of the transaction, a notification (
Figure 11a) and a unique event ID (
Figure 11b) are generated.
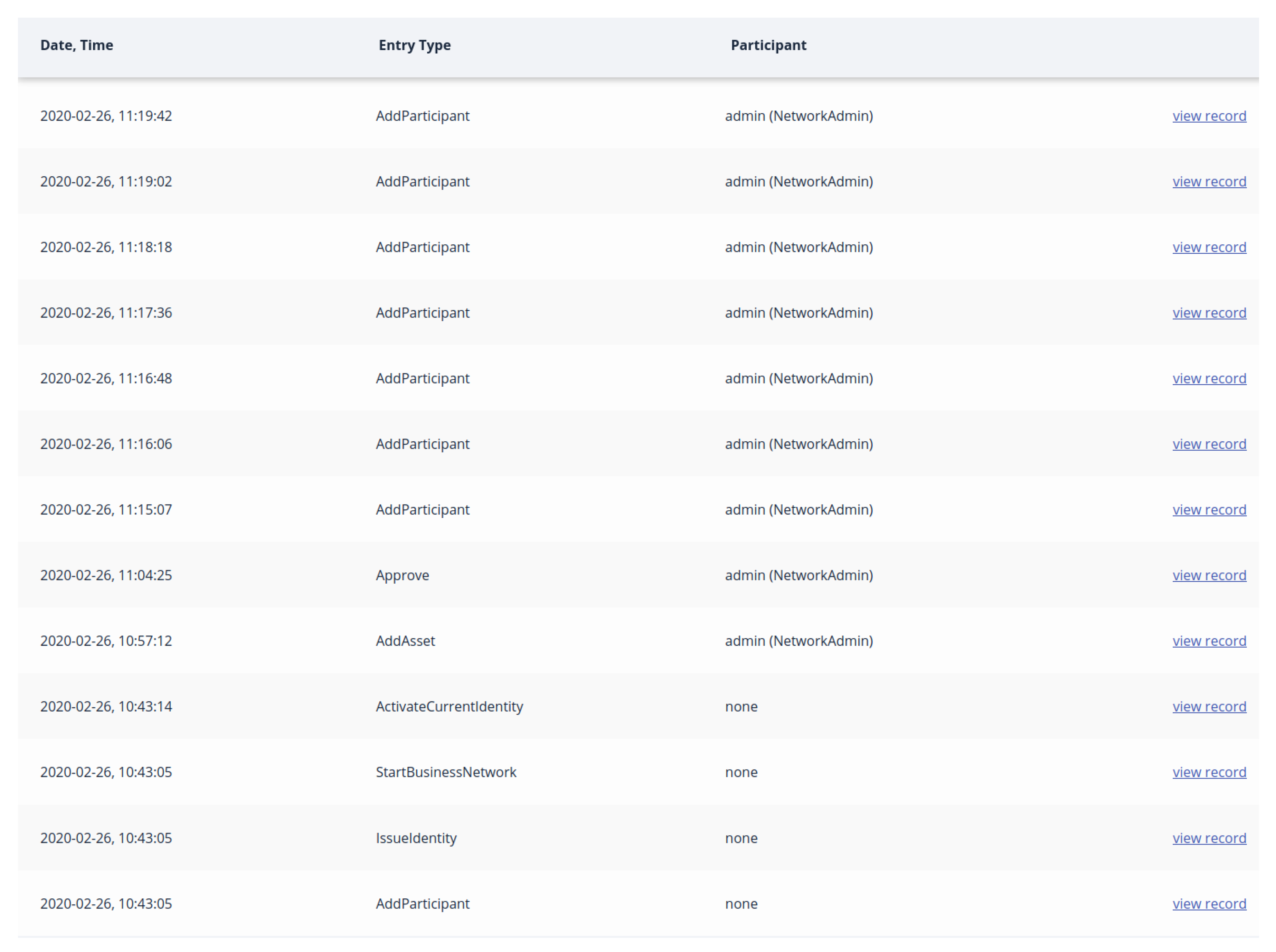
We can see all the transactions with immutable dates, times, entry types and participants in
Figure 12.
We can also see each transaction’s details with immutable date and unique event ID (
Figure 13).
4.3. Smart Contract Implementation
There are four segments within a smart contract of hyperledger; i.e., model, query definition, script, and access control rules. Hyperledger Fabric supports the adoption of state databases based on the format of the data amongst LevelDB and CouchDB. These two databases back core chaincode transactions. LevelDB is the default state database that is implemented to conserve smart contract data as a key-value pair. It is embedded in the peer node of the system. The alternative to LevelDB is CouchDB, which is used to format data of chaincode as binary code. It also concedes fitting the reporting demands. Transaction processor roles are inscribed in JavaScript and confined in a separate file as a part of a smart contract definition.
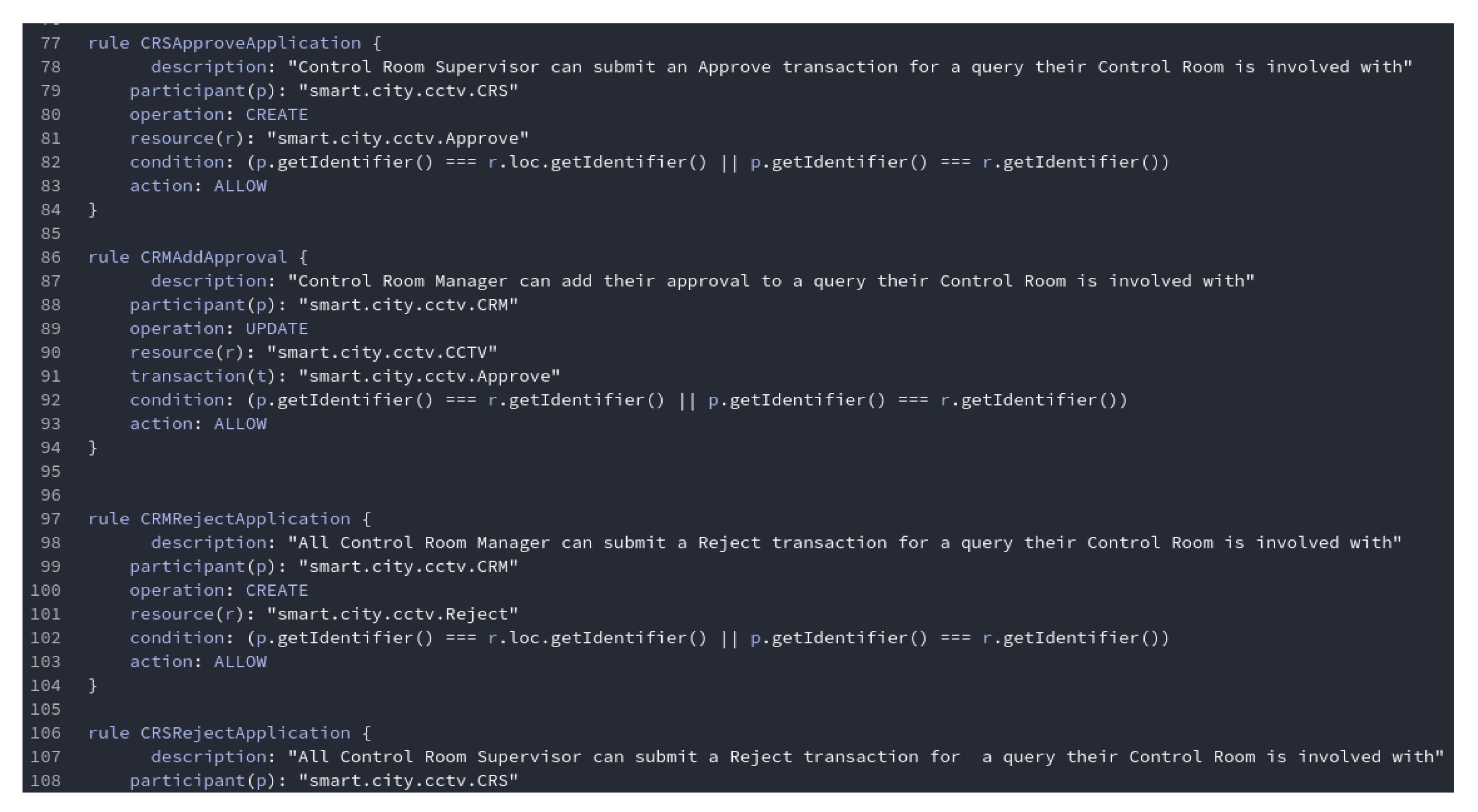
Figure 14 shows a snippet of smart contract rules.
4.4. Cost-Benefit Analysis
The cost-benefit analysis includes the steps involved in the decision-making about the feasibility of a system. The market for smart city surveillance equipment is increasing day by day. According to [
48], this could reach up to 19.5 billion Euros by the year 2023. As per the data gathered from [
49], the largest market for surveillance equipment is Asia, and more specifically, China. Out of the top 10 most-surveilled cities in the world, eight are in China.
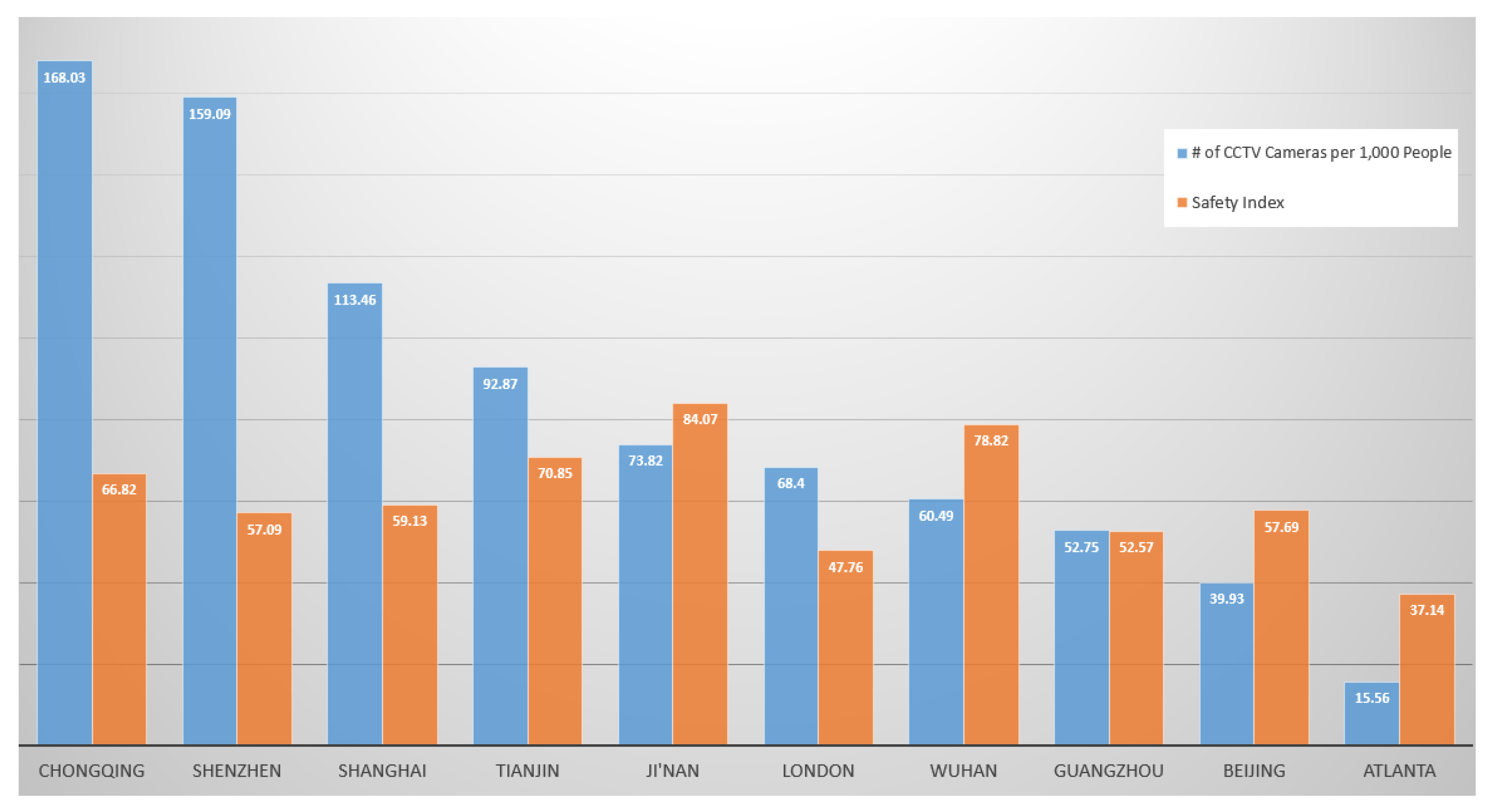
Figure 15 shows the top 10 cities around the world according to the number of cameras, and it also indicates the safety indexes of those cities. EL Piza and his associates [
50] conducted a study in 2019. Their study was based on 40 years of evaluation research. They found out that CCTV is the most effective technology to reduce crimes in residential areas and car parks. That is why this technology is worth spending money on—the safety of people in cities.
There are mainly three types of costs in such a system: purchasing, personnel, and running. Purchasing cost is a one time cost, and usually, it is the most significant portion of the entire system cost. It includes the purchase of initial hardware and setup cost. Personnel costs consist of the salaries of the staff, such as the POs and CRM. It is a continuous cost to run the system effectively. Running costs include the maintenance costs, which can vary according to the life of the hardware. Our proposed approach is using an open-source blockchain technology, which will help in security issues related to CCTV camera recordings. It will also reduce the centralized storage and maintenance costs, as blockchain provides a distributed environment with the guaranty of immutability, security, and privacy.
5. Discussion
A smart city is an urban environment where people enjoy a safe and secure life. Safety is one of the significant factors to keep in mind for the decision-makers of a smart city. Blockchain technology is widely used in many areas of smart cities, including smart grids, smart hospitals, smart vehicles, and supply chains. We first discussed blockchain and CCTV cameras and examined the overview of surveillance environment and blockchain-based video. We looked at research trends on surveillance. One of the major flaws we found in the current research is the verification of data. Data from surveillance cameras can be used as evidence in the court, but to ensure that the evidence is not forged is a problem. The market for surveillance cameras is increasing as countries are trying to provide safe environments to their people. Chongqing, a populous city in China, is the most surveilled city in the world, where there are around 168 cameras per 1000 citizens. China is planning to increase the number up to one camera per two persons [
51]. This will inevitably produce a large amount of metadata along with digital videos. The increasing number of imaging sensors for surveillance also opens a window for potential security attacks. The current systems are vulnerable to physical attacks. The user data is at risk of misuse. Hence, there was a gap in the research regarding a secure and trusted network. The authentication of surveillance devices also needs a trusted mechanism to be enlisted in the system. In this paper, A robust security platform based on blockchain technology is designed and applied. The high-security blockchain technology is applied to CCTV security data of a smart city. The blockchain is a trusted platform; hence, it can be used to deal with the legal aspects regarding the authenticity of the evidence. Reference [
20] gives a solution to data integrity management of the supply chain using blockchain. In their work, they explained the use of Hyperledger Fabric in detail to ensure data safety in the smart hospital. Hyperledger Fabric is an open-source platform by Linux foundation which provides hashed signatures to every participant and every node. Transactions within the blockchain are encrypted and timestamped. A block within this system is immutable, and nobody can change the timestamped data. Blocks are even verified before adding to the security chain. Hack-proof algorithms of blockchains provide trust to the consumers and decision-makers. We offer a system using a private blockchain; hence, it adds one more layer of security. In a private blockchain, every participant needs a private key through the MSP. Only legitimate operators can use the data.
Another point that can be helpful in legal issues is the metadata saved using the smart contract, which includes the IP address of data-generating devices and participants who are dealing with the device. The blockchain also provides data integrity, which ensures that the stored data does not get tampered with. The proposed solution is a cost-effective way to authenticate data for surveillance cameras. Another critical aspect of the proposed method is its decentralization, which will be helpful in fault tolerance. The data is distributed in different nodes; hence, in case of any failure in any node, the data can be retrieved easily. This research will help in the reshaping of better and secure smart cities. The proposed scheme allows the interested parties to go through the implementation details of a secured system.