An Efficient and Provably Secure Certificateless Blind Signature Scheme for Flying Ad-Hoc Network Based on Multi-Access Edge Computing
Abstract
1. Introduction
- (1)
- A command center initiates command and computes the corresponding digital signature.
- (2)
- The corresponding command and signature are then forwarded to the UAV by the command center.
- (3)
- The UAV, upon receiving the command and signature, attempts to verify the signature.
- If the signature is valid, the UAV deems it to be issued by the command center and proceeds with executing the command.
- Otherwise, the command is considered counterfeit and, thus, the UAV does not execute it.
1.1. Authors’ Motivations and Contributions
- We introduce a novel architecture for flying ad-hoc network (FANET) constituted by UAVs with a multi-access edge computing (MEC) facility that leverages the 5G wireless technology.
- We propose an efficient and provably secure certificateless signature (CL-BS) scheme for the same architecture using the concept of hyperelliptic curve for operating in resource-constrained environments.
- The proposed scheme is shown to be resistant against various attacks through formal as well as informal security analysis using the widely-accepted automated validation for internet security validation and application (AVISPA) tool.
- The proposed scheme is also compared with existing counterparts and it is shown that our approach provides better efficiency in terms of computational and communication costs.
1.2. Structure of the Paper
2. Related Work
2.1. Flying Ad-Hoc Network
2.2. Multi-Access Edge Computing
2.3. Related Certificateless Blind Signature Schemes
3. Preliminaries
3.1. Hyperelliptic Curve Cryptosystems (HECC)
3.2. Threat Model
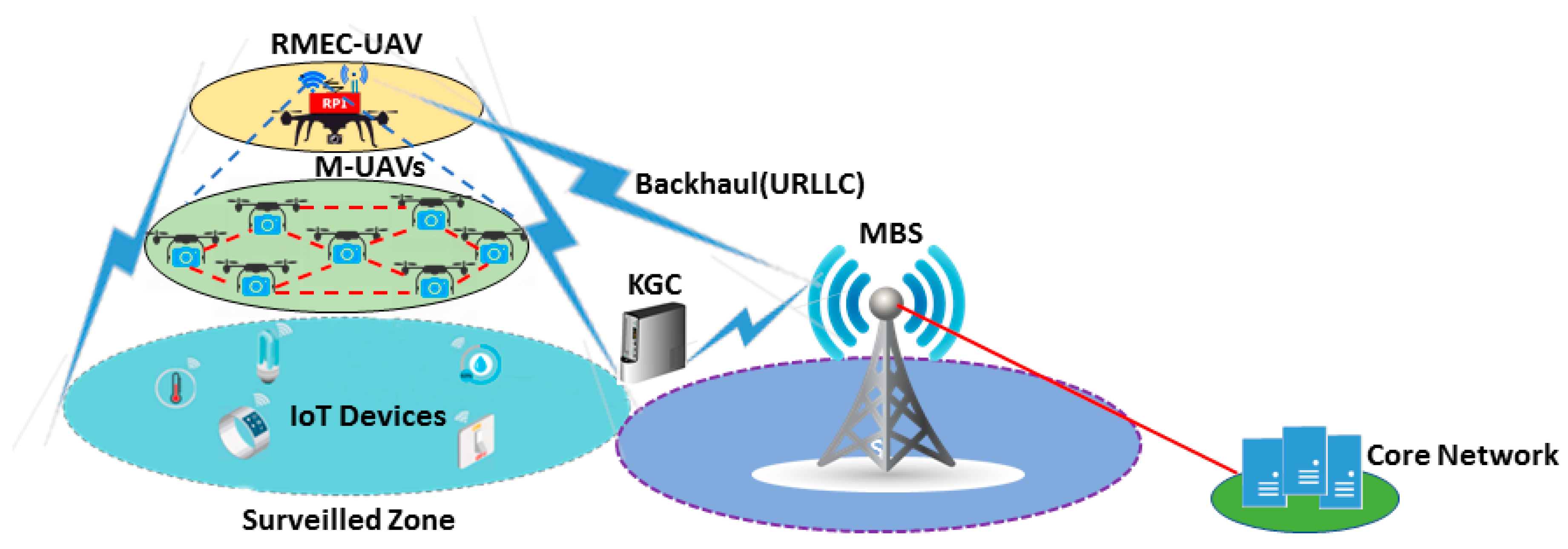
4. Proposed Architecture
- Layer 1 consists of the ground-level IoT devices that are devoted to different tasks as per application scenario. The ground-level IoT devices are connected with the RMEC-UAV and BS via URLLC, a 5G wireless link. Furthermore, the macro base station (MBS) are typically linked with the core network via wires that have huge bandwidth.
- Layer 2 comprises a team of M-UAVs equipped with the essential gadgets, these being cameras, IMU, sensors, and a GPS unit, among others, for monitoring the assigned zone. Moreover, M-UAVs are connected with each other using Bluetooth 5 (2.4 GHz) link and with the RMEC-UAV with 802.11 ac (5 GHz) Wi-Fi link.
- Layer 3 is composed of RMEC-UAV that is used to collect data from M-UAVs and forwards it to the base station. RMEC-UAV can also connect with the ground-level IoT devices and collect data from them.
Construction of the Proposed Scheme
- A hyper elliptic curve (C);
- A divisor (), where D is the divisor in C;
- The hash function (h);
- Select ∂ from {1, 2, …, n − 1} and the size of n = 280.
- It selects 𝛸u from {1, 2, ..., n − 1};
- It computes 𝛼u = 𝛸u. and 𝛽u = 𝛸u + ∂. 𝛼u;
- It computes 𝛿u = 𝛽u. ;
- It sends (𝛽u, 𝛿u) to the users (verifier and signer) with identity 𝓊.
- Blind signature: In this part, the blind signer first selects 𝜔 from {1, 2, …, n − 1}, computes Δ1 = 𝜔/s, Δ2 = 𝛽s/𝜔, and then sends it (Δ1, Δ2) to the requester. Further, the requester proceeds as follows:
- It selects (𝜏, 𝜑) from {1, 2, …, n − 1};
- It computes = 𝒽(𝓂, Δ1, Δ2, 𝜎r) and 𝒵 = + 𝜑;
- It sends 𝒵 to the blind signer. The blind signer generates the partial blind signature * = s − 𝒵.𝛽s and sends it to the requester;
- The requester, then, generates the hash value as 𝓇 = (𝓂, Ns) and full blind signature, using ** = * − 𝜏, and transfers it (**, 𝓇) to the verifier.
5. Implementation of Proposed Scheme in FANET
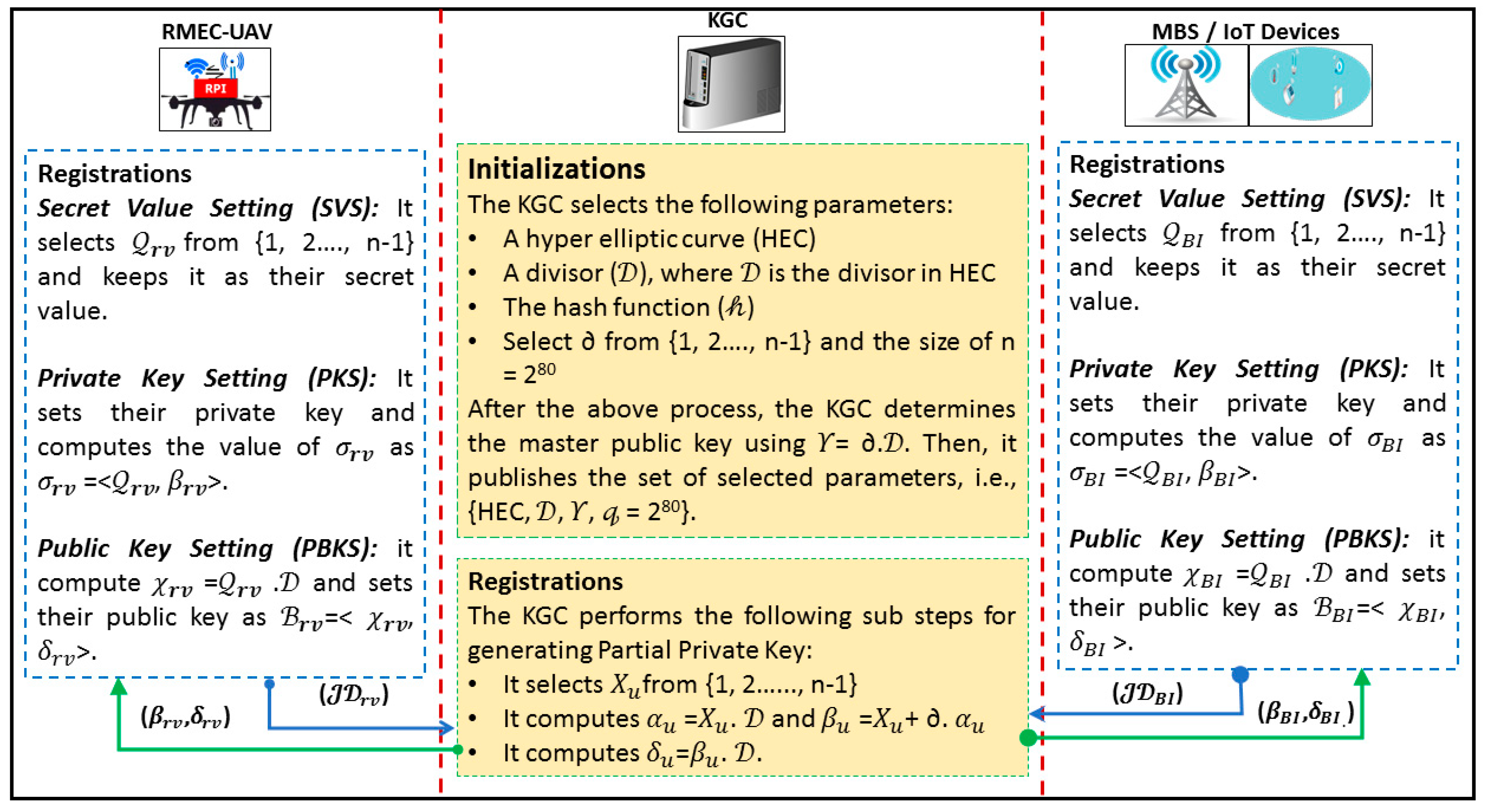
5.1. Initialization and Registration
- Partial Private Key Generation for RMEC-UAV: In order to set the partial private key for RMEC-UAV with identity rv, the KGC performs the following sub steps:
- It selects 𝛸rv from {1, 2, …, n − 1};
- It computes 𝛼rv = 𝛸rv. and 𝛽rv = 𝛸rv + ∂. 𝛼rv;
- It computes 𝛿rv = 𝛽rv. ;
- It sends (𝛽rv, 𝛿rv) to the RMEC-UAV.
- Secret Value Setting for RMEC-UAV: The RMEC-UAV selects rv from {1, 2, …, n − 1} and keeps it as their secret value.
- Private Key Setting for RMEC-UAV: The RMEC-UAV sets the private key as 𝜎rv = <rv, 𝛽rv>.
- Public Key Generation for RMEC-UAV: The RMEC-UAV computes 𝜒rv = 𝜎rv. and sets their public key as rv = <𝜒rv, 𝛿rv>.
- Partial Private Key Setting for BS/IoT: In order to set the partial private key for BS/IoT with identity BI, the KGC performs the following sub steps:
- It selects 𝛸BI from {1, 2, …, n − 1};
- It computes 𝛼BI = 𝛸BI. and 𝛽BI = 𝛸BI + ∂. 𝛼BI;
- It computes 𝛿BI = 𝛽BI. ;
- It sends (𝛽BI, 𝛿BI) to BS/IoT.
- Secret Value Setting for BS/IoT: The BS/IoT selects BI from {1, 2, …, n − 1} and keeps it as their secret value.
- Private Key Setting for BS/IoT: The BS/IoT sets the private key as 𝜎BI = <BI, 𝛽BI>.
- Public Key Setting for BS/IoT: The BS/IoT computes 𝜒BI = 𝜎BI. and sets their public key as B = <𝜒BI, 𝛿BI>.
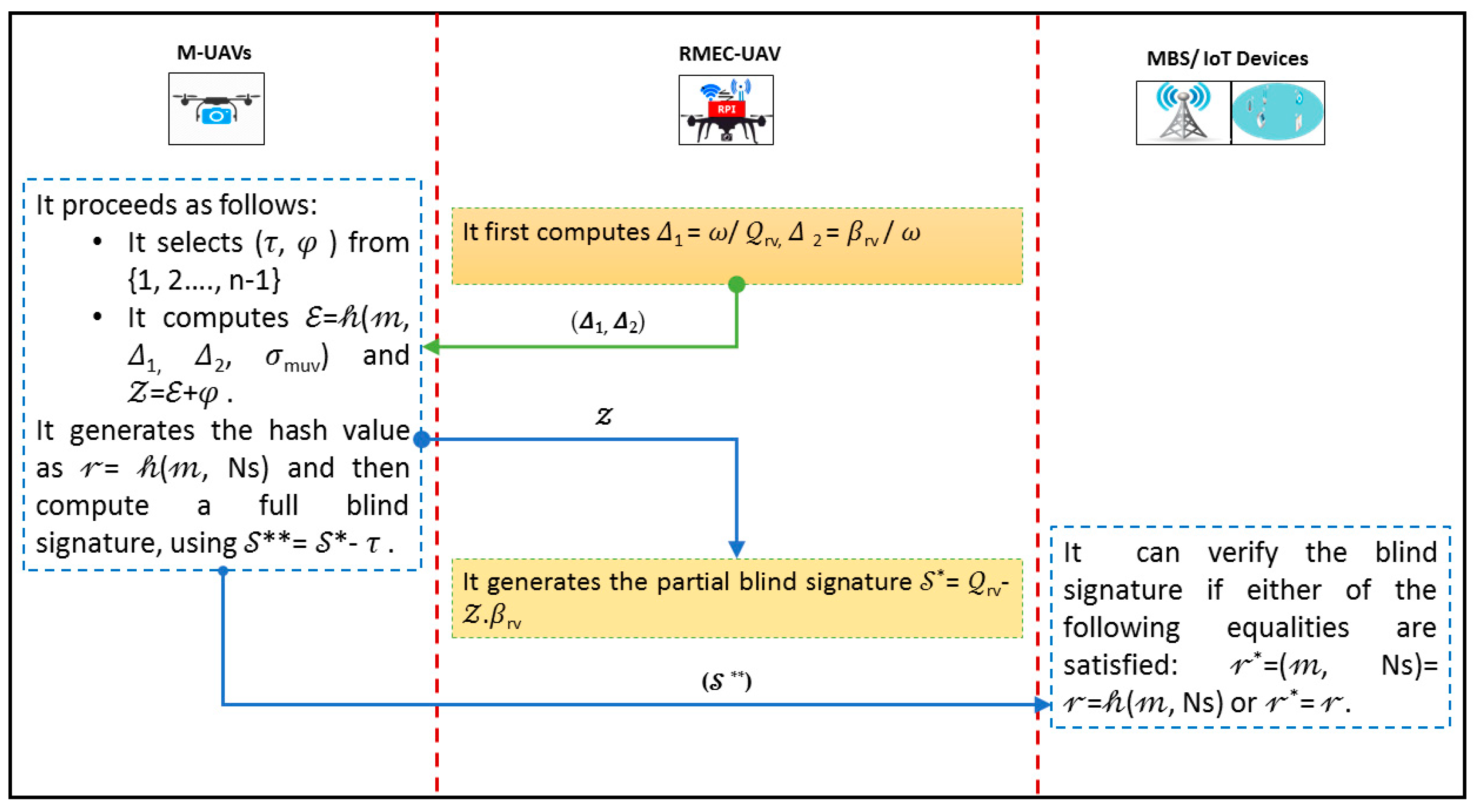
5.2. Signing and Verifying Phase
- It selects (𝜏, 𝜑) from {1, 2,…, n − 1};
- It computes = 𝒽(𝓂, Δ1, Δ2, 𝜎muv) and 𝒵 = + 𝜑;
- It sends 𝒵 to the RMEC-UAV. The RMEC-UAV generates the partial blind signature * = rv − 𝒵.𝛽rv and sends it to the M-UAV;
- The M-UAV, then, generates the hash value as 𝓇 = (𝓂, Ns) and full blind signature, using ** = * − 𝜏, and transfers it (**, 𝓇) to the BS/IoT.
6. Security Analysis
6.1. Informal Security Analysis
6.1.1. Theorem 1←Unforgeability
6.1.2. Theorem 1←Integrity
6.1.3. Theorem 1←Unlinkability
6.1.4. Theorem 1←Replay Attack
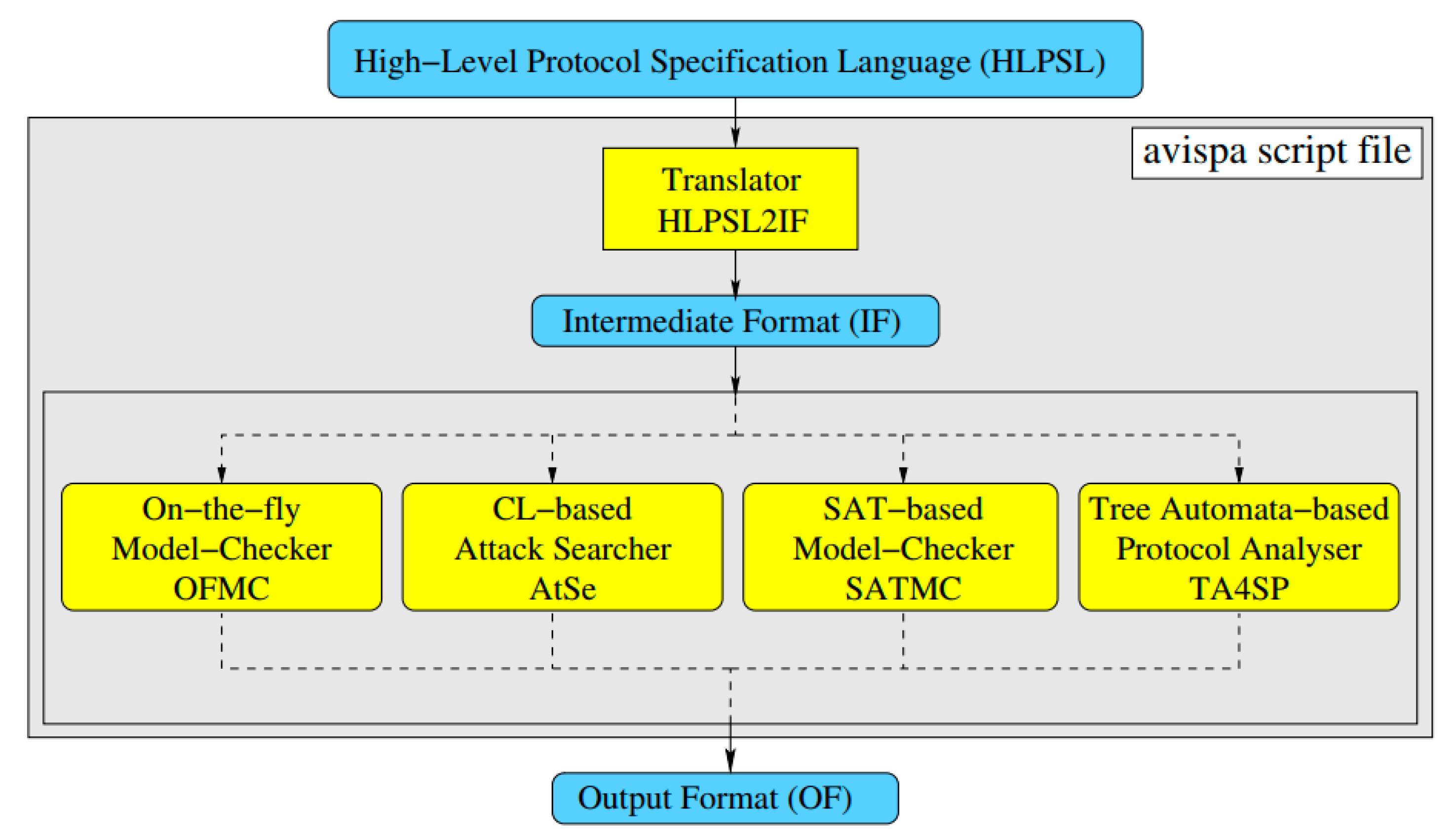
6.2. Formal Security Analysis Using Analysis
7. Performance Comparison
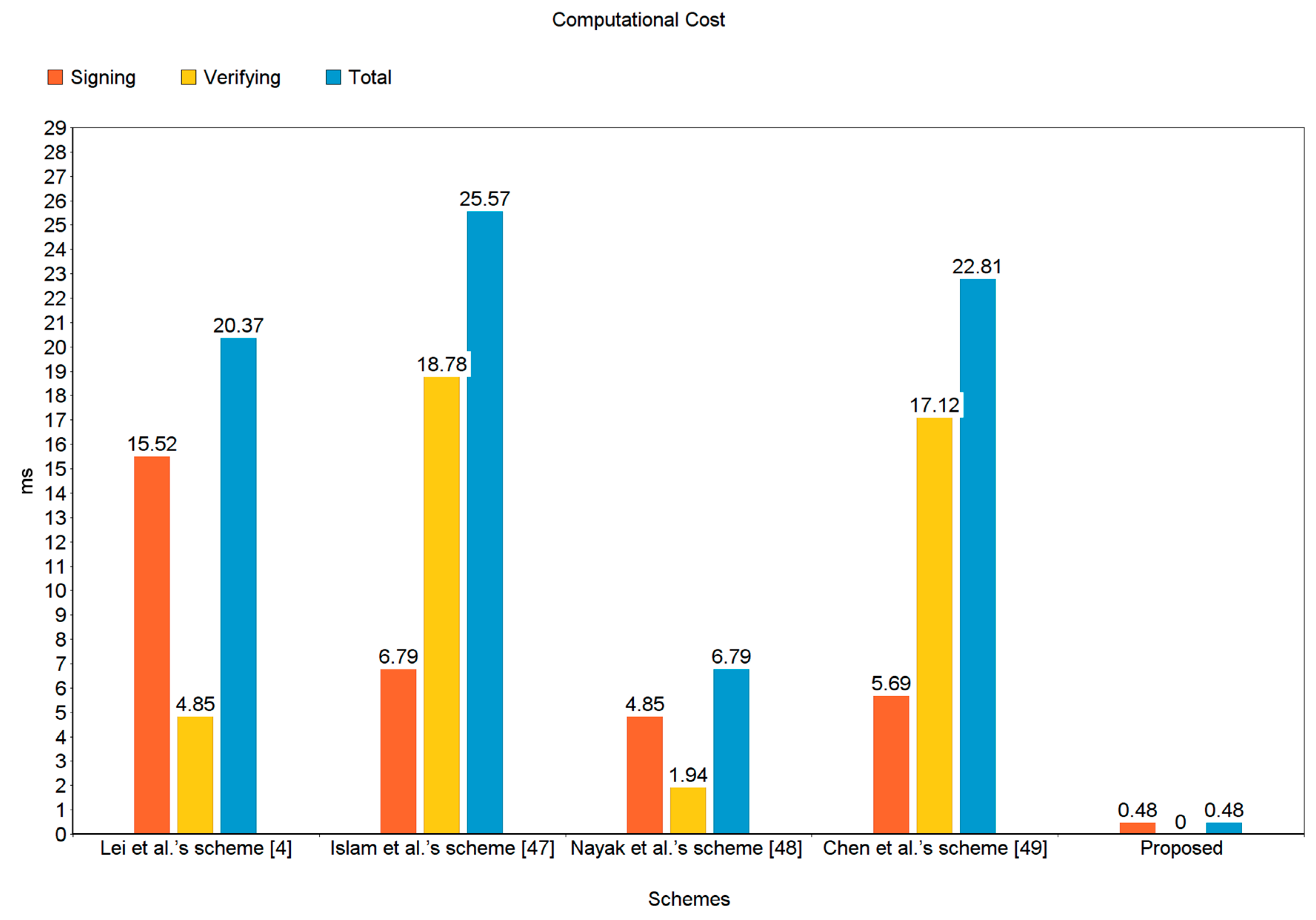
7.1. Computational Cost
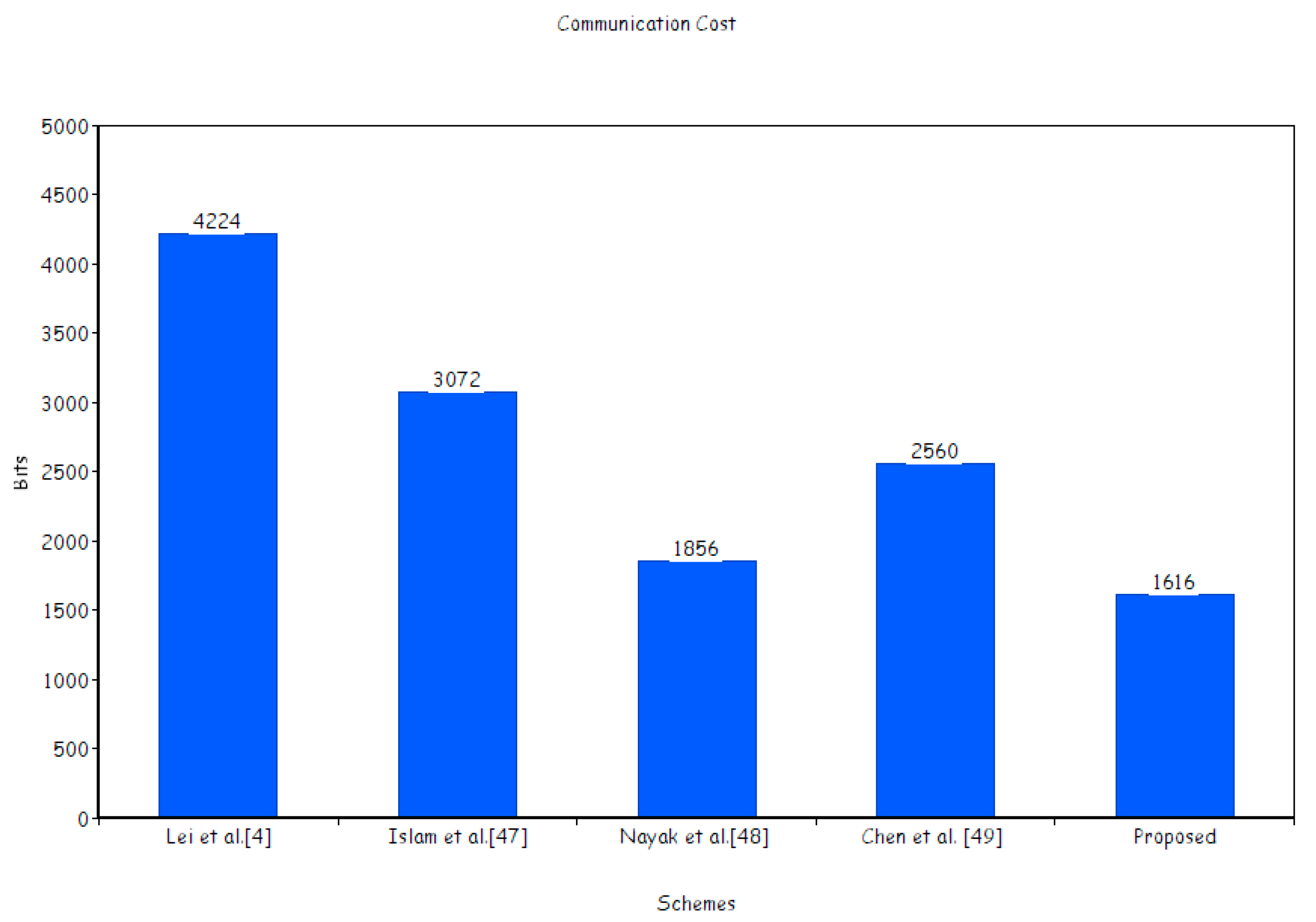
7.2. Communication Cost
7.3. Security Funtionalities
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A. Implementation of Our Proposed CL-BS Scheme in AVISPA
| Algorithm A1 High-level protocol specification language (HLPSL) code for Signer role |
| role role_Blindsigner(Blindsigner:agent,Verifier:agent,Xs:public_key,Xv:public_key,SND,RCV:channel(dy)) played_by Blindsigner def= local State:nat,Ns:text,Sub:hash_func,Z:text,T:text init State: = 0 transition 1. State=0 /\ RCV (start) =|> State’: =1 /\ SND (Blindsigner.Verifier) 2. State=1 /\ RCV (Verifier. {Ns’} _Xv) =|> State’: =2 /\ T':=new() /\ Z':=new() /\ SND(Blindsigner.{Sub(Z'.T')}_inv(Xs)) end role |
| Algorithm A2 High-level protocol specification language (HLPSL) code for Verifier role |
| role role_Verifier(Blindsigner:agent,Verifier:agent,Xs:public_key,Xv:public_key,SND,RCV:channel(dy)) played_by Verifier def= local State:nat,Ns:text,Sub:hash_func,Z:text,T:text init State: = 0 transition 1. State=0 /\ RCV(Blindsigner.Verifier) =|> State':=1 /\ Ns':=new() /\ SND(Verifier.{Ns'}_Xv) 2. State=1 /\ RCV (Blindsigner. {Sub (Z’. T')} _inv (Xs)) =|> State’: =2 end role |
| Algorithm A3 High-level protocol specification language (HLPSL) code for Sessions role |
| role session1(Blindsigner:agent,Verifier:agent,Xs:public_key,Xv:public_key) def= local SND2,RCV2,SND1,RCV1:channel(dy) composition role_Verifier(Blindsigner,Verifier,Xs,Xv,SND2,RCV2) /\ role_Blindsigner(Blindsigner,Verifier,Xs,Xv,SND1,RCV1) end role role session2(Blindsigner:agent,Verifier:agent,Xs:public_key,Xv:public_key) def= local SND1,RCV1:channel(dy) composition role_Blindsigner(Blindsigner,Verifier,Xs,Xv,SND1,RCV1) end role |
| Algorithm A4 High-level protocol specification language (HLPSL) code for Environment role |
| role environment() def= const hash_0:hash_func,xs:public_key,alice:agent,bob:agent,xv:public_key,const_1:agent,const_2:public_key,const_3:public_key,auth_1:protocol_id,sec_2:protocol_id intruder_knowledge = {alice,bob} composition session2(i, const_1, const_2, const_3) /\ session1(alice,bob,xs,xv) end role goal authentication_on auth_1 secrecy_of sec_2 end goal |
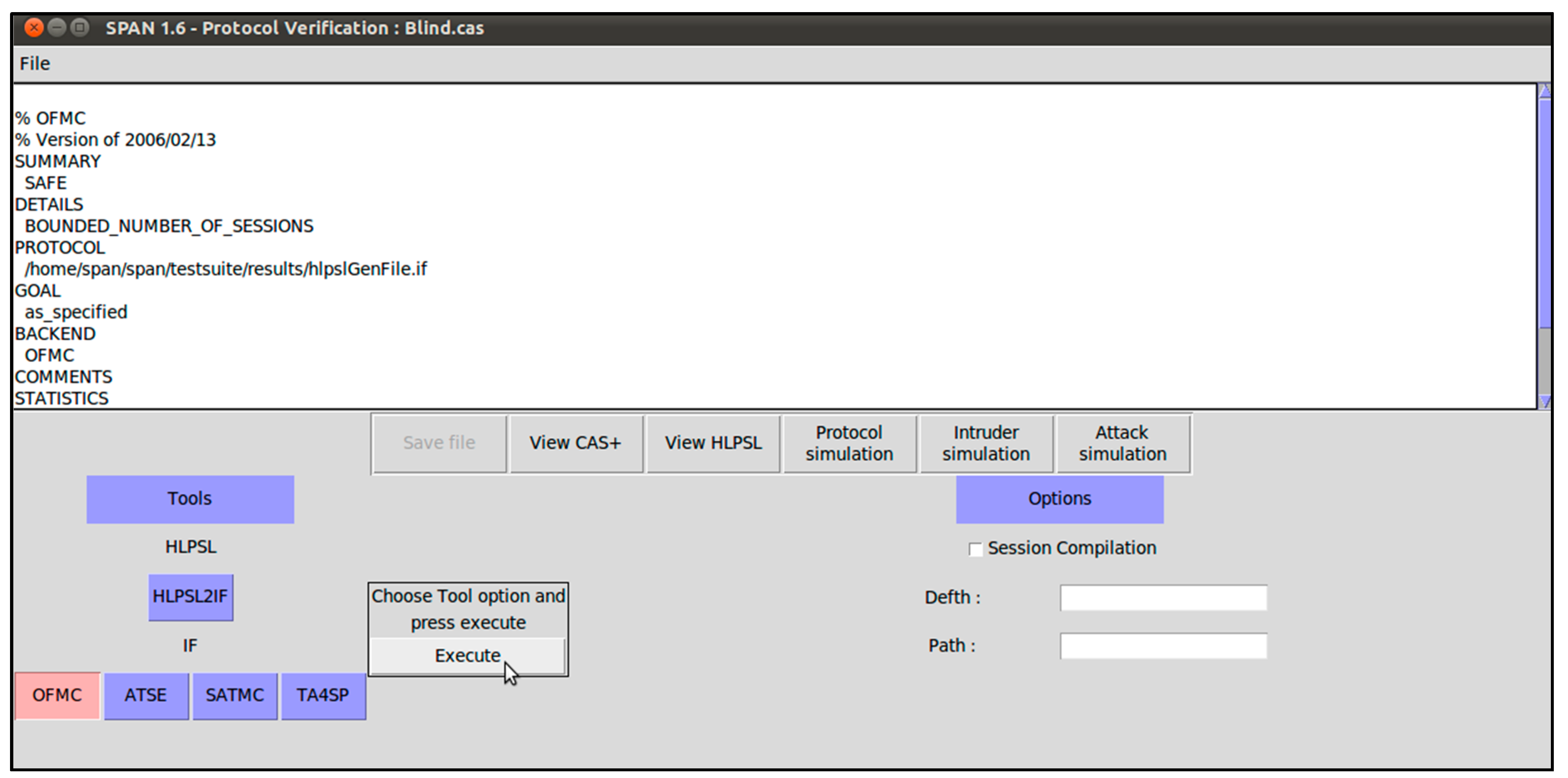
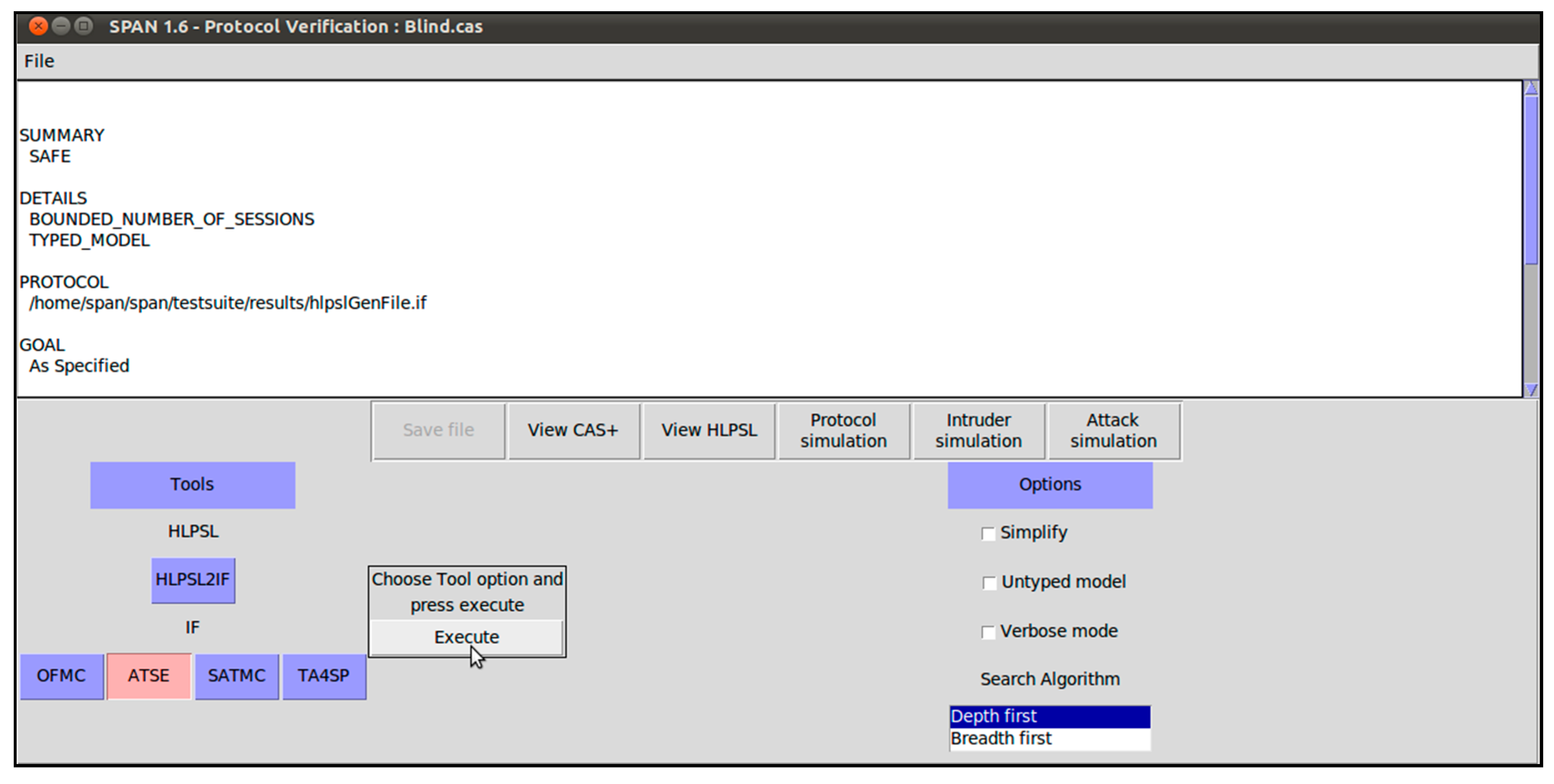
References
- Khan, M.A.; Qureshi, I.M.; Khanzada, F.A. Hybrid Communication Scheme for Efficient and Low-Cost Deployment of Future Flying Ad-Hoc Network (FANET). Drones 2019, 3, 16. [Google Scholar] [CrossRef]
- Bekmezci, I.; Sahingoz, O.K.; Temel, Ş. Flying ad-hoc Network (FANET): A survey. Ad Hoc Netw. 2013, 11, 1254–1270. [Google Scholar] [CrossRef]
- Khan, M.A.; Safi, A.; Qureshi, I.M.; Khan, I.U. Flying ad-hoc Network (FANET): A review of communication architectures, and routing protocols. In Proceedings of the 2017 First International Conference on Latest trends in Electrical Engineering and Computing Technologies (INTELLECT), Karachi, Pakistan, 15–16 November 2017; pp. 1–9. [Google Scholar]
- He, L.; Ma, J.; Mo, R.; Wei, D. Designated Verifier Proxy Blind Signature Scheme for Unmanned Aerial Vehicle Network Based on Multi-access Edge Computing (MEC). Secur. Commun. Netw. 2019, 2019, 8583130. [Google Scholar] [CrossRef]
- Khan, M.A.; Qureshi, I.M.; Khan, I.U.; Nasim, M.A.; Javed, U.; Khan, M.W. On the performance of flying ad-hoc Network (FANET) with directional antennas. In Proceedings of the 2018 5th International Multi-Topic ICT conference (IMTIC), Jamshoro, Pakistan, 25–27 April 2018; pp. 1–8. [Google Scholar]
- Khan, M.A.; Khan, I.U.; Safi, A.; Quershi, I.M. Dynamic Routing in Flying Ad-Hoc Networks Using Topology-Based Routing Protocols. Drones 2018, 2, 27. [Google Scholar] [CrossRef]
- Suárez-Albela, M.; Fraga-Lamas, P.; Fernández-Caramés, T.M. A Practical Evaluation on RSA and ECC-Based Cipher Suites for IoT High-Security Energy-Efficient Fog and Mist Computing Devices. Sensors 2018, 18, 3868. [Google Scholar] [CrossRef]
- Yu, M.; Zhang, J.; Wang, J.; Gao, J.; Xu, T.; Deng, R.; Zhang, Y.; Yu, R. Internet of Things security and privacy-preserving method through nodes differentiation, concrete cluster centers, multi-signature, and blockchain. Int. J. Distrib. Sens. Netw. 2018, 14, 12. [Google Scholar] [CrossRef]
- Braeken, A. PUF Based Authentication Protocol for IoT. Symmetry 2018, 10, 8. [Google Scholar] [CrossRef]
- Zhou, C.; Zhao, Z.; Zhou, W.; Mei, Y. Certificateless Key-Insulated Generalized Signcryption Scheme without Bilinear Pairings. Secur. Commun. Netw. 2017, 2017, 8405879. [Google Scholar] [CrossRef]
- Kumari, S.; Karuppiah, M.; Das, A.K.; Li, X.; Wu, F.; Kumar, N. A secure authentication scheme based on elliptic curve cryptography for IoT and cloud servers. J. Supercomput. 2017, 74, 12. [Google Scholar] [CrossRef]
- Omala, A.; Mbandu, A.; Mutiria, K.; Jin, C.; Li, F. Provably Secure Heterogeneous Access Control Scheme for Wireless Body Area Network. J. Med. Syst. 2018, 42, 6. [Google Scholar] [CrossRef]
- Tamizhselvan, C.; Vijayalakshmi, V. An Energy Efficient Secure Distributed Naming Service for IoT. Int. J. Adv. Stud. Sci. Res. 2019, 3, 8. [Google Scholar]
- Naresh, V.S.; Sivaranjani, R.; Murthy, N.V.E.S. Provable secure lightweight hyper elliptic curve-based communication system for wireless sensor Network. Int. J. Commun. Syst. 2018, 31, 15. [Google Scholar] [CrossRef]
- Rahman, A.; Ullah, I.; Naeem, M.; Anwar, R.; Khattak, H.S.; Ullah, A. Lightweight Multi-Message and Multi-Receiver Heterogeneous Hybrid Signcryption Scheme based on Hyper Elliptic Curve. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 5. [Google Scholar] [CrossRef][Green Version]
- Won, J.; Seo, S.H.; Bertino, E. Certificateless Cryptographic Protocols for Efficient Drone-Based Smart City Applications. IEEE Access 2017, 5, 3721–3749. [Google Scholar] [CrossRef]
- Barka, E.; Kerrache, C.; Hussain, R.; Lagraa, N.; Lakas, A.; Bouk, S. A Trusted Lightweight Communication Strategy for Flying Named Data Networking. Sensors 2018, 18, 2683. [Google Scholar] [CrossRef]
- Bae, M.; Kim, H. Authentication and Delegation for Operating a Multi-Drone System. Sensors 2019, 19, 2066. [Google Scholar] [CrossRef]
- Seo, S.-H.; Won, J.; Bertino, E. pCLSC-TKEM: A pairing-free certicateless signcryption-tag key encapsulation mechanism for a privacy-preserving IoT. Trans. Data Priv. 2016, 9, 101–130. [Google Scholar]
- Liu, W.; Strangio, M.A.; Wang, S. Efficient Certificateless Signcryption Tag-KEMs for Resource constrained Devices. arXiv 2015, 1510, 01446. [Google Scholar]
- Reddy, P.V.; Babu, A.R.; Gayathri, N.B. Efficient and Secure Identity-based Strong Key Insulated Signature Scheme without Pairings. J. King Saud Univ. Comput. Inf. Sci. 2018. [Google Scholar]
- Xiong, H.; Mei, Q.; Zhao, Y. Efficient and provably secure certificateless parallel key-insulated signature without pairing for IIoT environments. IEEE Syst. J. 2019, 1–11. [Google Scholar] [CrossRef]
- Bekkouche, O.; Taleb, T.; Bagaa, M. UAVs Traffic Control based on Multi-Access Edge Computing. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM 2018), Abu Dhabi, UAE, 9–13 December 2018. [Google Scholar]
- Ouahouah, S.; Taleb, T.; Song, J.; Benzaid, C. Efficient offloading mechanism for UAVs-based value-added services. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Motlagh, N.H.; Bagaa, M.; Taleb, T. Uav-based iot platform: A crowd surveillance use case. IEEE Commun. Mag. 2017, 55, 128–134. [Google Scholar] [CrossRef]
- ETSI. Multi-Access Edge Computing (MEC). In Framework and Reference Architecture; DGS MEC; ETSI: Sophia Antipolis, France, 2016; Volume 3. [Google Scholar]
- Garg, S.; Singh, A.; Batra, S.; Kumar, N.; Yang, L.T. UAV empowered edge computing environment for cyber-threat detection in smart vehicles. IEEE Netw. 2018, 32, 42–51. [Google Scholar] [CrossRef]
- Lee, J.; Lee, J. Hierarchical Multi-access Edge Computing (MEC) architecture based on context awareness. Appl. Sci. 2018, 8, 1160. [Google Scholar] [CrossRef]
- Intharawijitr, K.; Iida, K.; Koga, H. Simulation study of low latency network architecture using Multi-access Edge Computing (MEC). IEICE Trans. Inf. Syst. 2017, E100D, 963–972. [Google Scholar] [CrossRef]
- Messous, M.-A.; Sedjelmaci, H.; Houari, N.; Senouci, S.-M. Computation offloading game for an UAV network in Multi-access Edge Computing (MEC). In Proceedings of the 2017 IEEE International Conference on Communications, ICC 2017, Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Ansari, N.; Sun, X. Multi-access Edge Computing (MEC) empowers internet of things. IEICE Trans. Commun. 2018, E101B, 604–619. [Google Scholar] [CrossRef]
- Zhang, K.; Leng, S.; He, Y.; Maharjan, S.; Zhang, Y. Multi-access Edge Computing (MEC) and networking for green and low-latency internet of things. IEEE Commun. Mag. 2018, 56, 39–45. [Google Scholar] [CrossRef]
- Grasso, C.; Schembra, G. A Fleet of MEC UAVs to Extend a 5G Network Slice for Video Monitoring with Low-Latency Constraints. J. Sens. Actuator Netw. 2019, 8, 3. [Google Scholar] [CrossRef]
- Chaum, D. Blind signatures for untraceable payments. Adv. Cryptol. 1983, 199–203. [Google Scholar]
- Mambo, M.; Usuda, K.; Okamoto, E. Proxy signatures for delegating signing operation. In Proceedings of the 3rd ACM Conference on Computer and Communications Security, New Delhi, India, 14–15 March 1996; pp. 48–56. [Google Scholar]
- Tan, Z.; Liu, Z.; Tang, C. Digital proxy blind signature schemes based on DLP and ECDLP. MM Res. Prepr. 2002, 21, 212–217. [Google Scholar]
- Tan, Z. Efficient pairing-free provably secure identity-based proxy blind signature scheme. Secur. Commun. Netw. 2013, 6, 593–601. [Google Scholar] [CrossRef]
- Yang, F.-Y.; Liang, L.-R. A proxy partially blind signature scheme with proxy revocation. J. Ambient Intell. Humaniz. Comput. 2013, 4, 255–263. [Google Scholar] [CrossRef]
- Verma, G.K.; Singh, B.B. Efficient message recovery proxy blind signature scheme from pairings. Trans. Emerg. Telecommun. Technol. 2017, 28, e3167. [Google Scholar] [CrossRef]
- Zhu, H.; Tan, Y.-A.; Zhu, L.; Zhang, Q.; Li, Y. An efficient identity-based proxy blind signature for semi offline services. Wirel. Commun. Mob. Comput. 2018, 2018, 5401890. [Google Scholar] [CrossRef]
- Jakobsson, M.; Sako, K.; Impagliazzo, R. Designated verifier proofs and their applications. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Berlin, Heidelberg, 13 July 2001; pp. 143–154. [Google Scholar]
- Dai, J.Z.; Yang, X.H.; Dong, J.X. Designated-receiver proxy signature scheme for electronic commerce. In Proceedings of the IEEE International Conference on Systems, Man and Cybernetics, Washington, DC, USA, 10 November 2003; pp. 384–389. [Google Scholar]
- Huang, X.; Mu, Y.; Susilo, W.; Zhang, F. Short designated verifier proxy signature from pairings. In Proceedings of the International Conference on Embedded and Ubiquitous Computing, Nagasaki, Japan, 6–9 December 2005; pp. 835–844. [Google Scholar]
- Shim, K.-A. Short designated verifier proxy signatures. Comput. Electr. Eng. 2011, 37, 180–186. [Google Scholar] [CrossRef]
- Islam, S.H.; Biswas, G. A provably secure identity-based strong designated verifier proxy signature scheme from bilinear pairings. J. King Saud Univ. Comput. Inf. Sci. 2014, 26, 55–67. [Google Scholar] [CrossRef]
- Hu, X.; Tan, W.; Xu, H.; Wang, J. Short and provably secure designated verifier proxy signature scheme. IET Inf. Secur. 2016, 10, 69–79. [Google Scholar] [CrossRef]
- Islam, S.; Obaidat, M.S. Design of provably secure and efficient certificateless blind signature scheme using bilinear pairing. Secur. Commun. Netw. 2015, 8, 4319–4332. [Google Scholar] [CrossRef]
- Nayak, S.K.; Mohanty, S.; Majhi, B. CLB-ECC: Certificateless Blind Signature Using ECC. JIPS 2017, 13, 970–986. [Google Scholar]
- Chen, H.; Zhang, L.; Xie, J.; Wang, C. New Efficient Certificateless Blind Signature Scheme. In Proceedings of the 2016 IEEE Trustcom/BigDataSE/ISPA, Tianjin, China, 23–26 August 2016; pp. 349–353. [Google Scholar]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Hyperelliptic Curve. 2019. Available online: https://en.wikipedia.org/wiki/Hyperelliptic_curve (accessed on 25 October 2019).
- Pelzl, J.; Wollinger, T.; Guajardo, J.; Paar, C. Hyperelliptic curve cryptosystems: Closing the performance gap to elliptic curves. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin, Heidelberg, 2003; pp. 351–365. [Google Scholar]
- Cantor, D.G. Computing in Jacobian of a Hyperelliptic Curve. Math. Comput. 1987, 48, 95–101. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Siddiqi, M.A.; Yu, H.; Joung, J. 5G Ultra-Reliable Low-Latency Communication Implementation Challenges and Operational Issues with IoT Devices. Electronics 2019, 8, 981. [Google Scholar] [CrossRef]
- AVISPA. Automated Validation of Internet Security Protocols and Applications. 2019. Available online: http://www.avispa-project.org/ (accessed on 25 October 2019).
- AVISPA. SPAN: A Security Protocol Animator for AVISPA. 2019. Available online: http://www.avispa-project.org/ (accessed on 25 October 2019).
- Oheimb, D.V. The high-level protocol specification language HLPSL developed in the EU project avispa. In Proceedings of the APPSEM 2005 Workshop, Tallinn, Finland, 13–15 September 2005; pp. 1–2. [Google Scholar]
- Basin, D.; Modersheim, S.; Vigano, L. OFMC: A symbolic model checker for security protocols. Int. J. Inf. Secur. 2005, 4, 181–208. [Google Scholar] [CrossRef]
- Turuani, M. The CL-Atse porotocol analyser. In Proceedings of the International Coneference on Rewriting Techniques and Applications (RTA), Seattle, WA, USA, 12–14 August 2006; pp. 227–286. [Google Scholar]
- Yu, S.; Lee, J.; Lee, K.; Park, K.; Park, Y. Secure Authentication Protocol for Wireless Sensor Network in Vehicular Communications. Sensors 2018, 18, 3191. [Google Scholar] [CrossRef]
- Park, K.; Park, Y.; Park, Y.; Reddy, A.G.; Das, A.K. Provably secure and efficient authentication protocol for roaming service in global mobility Network. IEEE Access 2017, 5, 25110–25125. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Choo, K.R.; Kumar, N.; Park, Y.H. Efficient and secure time-key based single sign-on authentication for mobile devices. IEEE Access 2017, 5, 27707–27721. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Kumari, S.; Huang, X.; Wazid, M. Provably secure authenticated key agreement scheme for distributed mobile cloud computing services. Futuer Generat. Comput. Syst. 2017, 68, 74–88. [Google Scholar] [CrossRef]
- Park, K.; Park, Y.; Park, Y.; Das, A.K. 2PAKEP: Provably Secure and Efficient Two-Party Authenticated Key Exchange Protocol for Mobile Environment. IEEE Access 2018, 6, 30225–30241. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Park, Y.H.; Tanwar, S. Design of an Anonymity-Preserving Group Formation Based Authentication Protocol in Global Mobility Network. IEEE Access 2018, 6, 20673–20693. [Google Scholar] [CrossRef]
- AVISPA v1.1 User Manual. 2019. Available online: http://www.avispa-project.org/package/user-manual.pdf (accessed on 25 October 2019).
- Shamus Sofware Ltd. Miracl library. Available online: http://github.com/miracl/ MIRACL (accessed on 25 October 2019).
- Ullah, I.; Amin, N.U.; Naeem, M.; Khattak, S.; Khattak, S.J.; Ali, H. A Novel Provable Secured Signcryption Scheme PSSS: A Hyper-Elliptic Curve-Based Approach. Mathematics 2019, 7, 686. [Google Scholar] [CrossRef]
- Ullah, I.; Alomari, A.; Ul Amin, N.; Khan, M.A.; Khattak, H. An Energy Efficient and Formally Secured Certificate-Based Signcryption for Wireless Body Area Network with the Internet of Things. Electronics 2019, 8, 1171. [Google Scholar] [CrossRef]
| S.NO | Symbol | Definition |
|---|---|---|
| 1 | C | Means hyperelliptic curve with genus 2, which is the generalized form elliptic curve requiring 80 bit key |
| 3 | A divisor, which is a finite formal sum of points on hyperelliptic curve | |
| 4 | ∂ | Master secret key which is generated by KGC for producing partial private key |
| 5 | 𝛶 | The master public key of KGC |
| 6 | N | Randomly generated number and the size of N as n = 280 |
| 7 | 𝒽 | One-way hash function, which means that it has the property of irreversibility |
| 8 | 𝜎r = <r, 𝛽r> | Private key of requester |
| 9 | 𝜎s = <s, 𝛽s> | Private key of signer |
| 10 | Ns | A fresh nonce that is used for anti-replay attack |
| 11 | 𝓊 | Identities for sender and receiver |
| 12 | 𝓂 | Plain-text (message) |
| Schemes | Signing | Verifying | Total |
|---|---|---|---|
| Lei et al.’s scheme [4] | 16 𝑒𝑚 | 5 𝑒𝑚 | 21 𝑒𝑚 |
| Islam et al.’s scheme [47] | 7 𝑒𝑚 | 1 𝒷𝓅 + 4 𝑒𝑚 | 11 𝑒𝑚 + 1 𝒷𝓅 |
| Nayak et al.’s scheme [48] | 5 𝑒𝑚 | 2 𝑒𝑚 | 7 𝑒𝑚 |
| Chen et al.’s scheme [49] | 2 𝑒𝑚 + 3 𝓂𝓍𝓅 | 1 𝑒𝑚 + 1 𝒷𝓅 + 1 𝓂𝓍𝓅 | 3 𝑒𝑚 + 1 𝒷𝓅 + 4 𝓂𝓍𝓅 |
| Proposed | 1 𝒽𝓂 | 0 𝒽𝓂 | 1 𝒽𝓂 |
| Schemes | Signing | Verifying | Total |
|---|---|---|---|
| Lei et al.’s scheme [4] | 15.52 ms | 4.85 ms | 20.37 ms |
| Islam et al.’s scheme [47] | 6.79 ms | 18.78 ms | 25.57 ms |
| Nayak et al.’s scheme [48] | 4.85 ms | 1.94 ms | 6.79 ms |
| Chen et al.’s scheme [49] | 5.69 ms | 17.12 ms | 22.81 ms |
| Proposed | 0.48 ms | 0 ms | 0.48 ms |
| Schemes | Security Functionalities | ||||
|---|---|---|---|---|---|
| Informal | Formal | ||||
| U | I | UL | RA | FA | |
| Lei et al.’s scheme [4] | ✓ | ✕ | ✕ | ✕ | ✕ |
| Islam et al.’s scheme [47] | ✓ | ✕ | ✓ | ✕ | ✕ |
| Nayak et al.’s scheme [48] | ✓ | ✕ | ✕ | ✕ | ✕ |
| Chen et al.’s scheme [49] | ✓ | ✕ | ✕ | ✕ | ✕ |
| Proposed | ✓ | ✓ | ✓ | ✓ | ✓ |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, M.A.; Qureshi, I.M.; Ullah, I.; Khan, S.; Khanzada, F.; Noor, F. An Efficient and Provably Secure Certificateless Blind Signature Scheme for Flying Ad-Hoc Network Based on Multi-Access Edge Computing. Electronics 2020, 9, 30. https://doi.org/10.3390/electronics9010030
Khan MA, Qureshi IM, Ullah I, Khan S, Khanzada F, Noor F. An Efficient and Provably Secure Certificateless Blind Signature Scheme for Flying Ad-Hoc Network Based on Multi-Access Edge Computing. Electronics. 2020; 9(1):30. https://doi.org/10.3390/electronics9010030
Chicago/Turabian StyleKhan, Muhammad Asghar, Ijaz Mansoor Qureshi, Insaf Ullah, Suleman Khan, Fahimullah Khanzada, and Fazal Noor. 2020. "An Efficient and Provably Secure Certificateless Blind Signature Scheme for Flying Ad-Hoc Network Based on Multi-Access Edge Computing" Electronics 9, no. 1: 30. https://doi.org/10.3390/electronics9010030
APA StyleKhan, M. A., Qureshi, I. M., Ullah, I., Khan, S., Khanzada, F., & Noor, F. (2020). An Efficient and Provably Secure Certificateless Blind Signature Scheme for Flying Ad-Hoc Network Based on Multi-Access Edge Computing. Electronics, 9(1), 30. https://doi.org/10.3390/electronics9010030






