1. Introduction
With the advancement of urban modernization, urban rail transit has been considerably developed. Due to the development of the city and the growth of the population, urban rail transit is under tremendous pressure [
1]. Therefore, researchers have obtained the communication-based train controls system based on modern communication, control technology, computer and traditional signal technology to improve operational efficiency and capabilities [
2].
The CBTC system has many characteristics compared to traditional railway signal systems, such as high-resolution train location determination, independent of track circuits, and continuous, high capacity, bidirectional train-to-wayside data communications [
3]. It is an automated train control system utilizing a variety of advanced technologies and equipment to ensure that trains operate at minimum safe distances for maximum transport capacity [
4]. The CBTC system, with currently over 100 installations worldwide, is one of the most popular signaling systems among mass-transit rail operators today [
5].
As a contemporary industrial control system, the CBTC system applies a large number of networked and information components, facing the risk of cyber attacks [
6]. The system faces security issues such as high-risk vulnerabilities in devices, industrial network viruses, advanced persistent threats, and wireless technology vulnerabilities. In recent years, information security incidents in urban rail transit have emerged one after another. In March 2012, the Shanghai Shentong Metro Station information release system and the operation and dispatch system wireless network were attacked. In November 2012, the Shenzhen subway signal system was disturbed, resulting in frequent emergency braking of multiple trains during operation. Finally, in 2016, hackers attacked the computer fare system of the Muni subway in San Francisco, USA, and used it to blackmail. These incidents have had a huge impact on urban traffic, disrupted traffic order, and brought huge economic losses. As mentioned above, urban rail transit is a significant urban infrastructure that is closely related to people’s lives. When security problems occur in urban rail transit, emergency braking may occur on the train, which may disrupt train operation, increase urban traffic pressure and cause huge economic losses. Furthermore, train derailment or train collision events may come to happen, which will lead to unmeasurable life and property damage. Therefore, it is significant to capture the interactions between attack and defense and analyze the security of the CBTC systems. In this way, more researchers and industry experts can realize the significance of security for the CBTC system and how to improve the security of the system.
There are some previous works on modeling and evaluating the security of CBTC systems. Based on the continuity of urban rail transit operation services, Wang et al. [
7] proposed a resilience-based security assessment approach that divides security risks into three phases: pre-attack, under attack, and after attack. In [
8], a comprehensive analysis method of security and safety based on an extended fault tree was proposed. This paper synthesized the safety and security features of the urban rail transit train control system, comprehensively considered the security threats and vulnerabilities and the hazard sources of the train control system, and analyzed the relationship between security risks and safety risks. Dong et al. [
9] used attack tree to evaluate the vulnerability of a CBTC system based on its network topology, redundant structure, and operation principles. Assessments covered the current security states, port auditing, password policies, and communication protocols of systems. Ferrari et al. [
10] proposed a stochastic activity networks (SAN) model to conduct an availability assessment of CBTC systems. Lee et al. [
11] defined the security requirements considering characteristics of the radio train control system using LTE-R and analyzing the risk of attack.
The CBTC system is one kind of cyber-physical system (CPS) consisting of two major components: a physical process and a cyber system [
12]. To analyze the impact of offensive and defensive behavior on CBTC systems, we also refer to the research results of cyber-physical systems. In [
13], a nonfunctional requirement (NFR) method was utilized to assess the safety and security of CPS. The intuitiveness of the NFR approach allowed us to determine the reasons for the poor security and to identify the techniques that will help to improve security. Mitchell et al. [
14] simulated the dynamic Interaction between attack and defense behavior of cyber-physical systems based on a stochastic Petri nets model. Furthermore, the paper analyzed the impact of the intrusion detection interval and attack strength on the modernized electrical grid’s mean time to failure (MTTF). In addition, in [
15,
16], authors used game theory to describe the state changes process of CPS under the strategies of attackers and defenders. Several quantitative indicators such as steady-state probability and MTTF were applied to evaluate system reliability. Depoy et al. [
17] described a top–down functional assessment methodology for risk assessment of the system under four types of attacks: physical-only, cyber-enabled physical, cyber-only, and physical-enabled cyber attacks. A Boolean logic driven Markov processes (BDMPs) formalism proposed modeling attack steps and evaluate security risk in [
18,
19]. In [
20,
21], a hidden Markov model (HMM) was utilized to describe the stochastic dynamics of CPSs in the attack scenario. In addition, the authors in [
22,
23,
24] analyzed a smart grid security situation based on Q-learning, which can display the attack–defense confrontation process well.
Refering to the multistage attack process for CPS, we divided the attack process of CBTC systems into two phases: the penetration phase and disruption phase [
25]. In the penetration phase, the attacker invades the system through a wired or wireless approach, and the system will not be substantially damaged. After the successful invasion, the attacker launches substantial physical damage to the system, and the attack enters the disruption phase. In this paper, we can better grasp the vulnerability of the system through the phased research of the attack process.
In this paper, we utilized a generalized stochastic Petri net (GSPN) to describe attack and defense behavior and changes in the system state. We chose several typical attacks against the CBTC system and the corresponding defenses to enrich our model. Different from papers about CPS security analysis, we used concrete attack and defense strategies instead of general strategies such as attack and no attack. The proposed model not only conforms to the characteristics of CPS but also combines the characteristics of CBTC with state changes and strategy choices. To more accurately simulate the attack and defense confrontation in the CBTC system, we introduce the game theory in the paper. By solving the Nash equilibrium, we got the probability that the attacker and the system would choose the attack and defense strategy, which is the most likely behavior choice for decision-makers on both sides under the rational premise. By doing this, we can get a complete GSPN model. We conducted attack and defense drills on the semiphysical simulation platform of the laboratory to help model parameterization. Our GSPN model can be combined with a continuous-time Markov process. We can get the steady-state probability of the system in each state by solving the Markov chain. Finally, we propose several security indicators to evaluate the security of CBTC systems under attack–defense confrontation based on model solution results.
The rest of the paper is organized as follows: In
Section 2, security issues and attack–defense methods in CBTC systems are mentioned. In
Section 3, we propose the security analysis model of CBTC systems under attack–defense confrontation. In
Section 4, we present the process of the model solution. In
Section 5, we utilize several indicators to analyze the system security. Finally, in
Section 6, we conclude the paper and outline future areas.
2. Security Issues and Attack–Defense Strategies in CBTC Systems
2.1. A Typical CBTC System
This section presents the structure and composition of CBTC systems. The CBTC system is mainly composed of on-board equipment and wayside equipment. The basic composition of the CBTC system is shown in
Figure 1. On-board equipment includes automatic train protection (ATP) equipment and automatic train operation (ATO) equipment for train operation monitoring, speed measurement positioning, and human–computer interaction. Wayside equipment includes a zone controller (ZC), automatic train supervision (ATS), computer interlocking (CI), and a database storage unit (DSU). The ATS is divided into the central ATS and the station ATS.
The data communication system (DCS) of the CBTC system consists of two parts: the backbone network and the radio access network. The backbone network provides transparent data transmission channels for ground equipment. Most of the existing wireless access networks of the CBTC system use IEEE 802.11-based wireless local area networks (WLAN) equipment to realize real-time transmission of two-way and large-capacity information of the vehicle. To meet the high availability requirements of the CBTC system, the DCS adopts a ring network redundancy architecture. When a network cannot work normally due to equipment failure, the system can still send and receive data through another network. At the same time, the ground backbone network is divided into several different subnets according to different subsystems. Generally, it is divided into five networks, two redundant signaling networks, two redundant ATS networks, and one maintenance network. The ATS network connects the central ATS and the station ATS and communicates with the signal network through the ATS gateway. The maintenance network consists of distributed maintenance machines and maintenance centers for fault diagnosis and routine maintenance.
2.2. Security Issues in CBTC Systems
A large number of network and information components are used in the CBTC system, such as communication technology, general computer technology, control technology, commercial Windows, a VxWorks operating system, and standard TCP/IP communication protocols. The use of these advanced technologies has greatly improved the automation and information level of the CBTC system but also introduced new security risks to the system. The main information security risks of the CBTC system are as follows:
Communication protocol risks. At present, DCSs use WLAN technology to complete wireless communication. WLAN works in the open industrial scientific medical (ISM) band, and there are vulnerabilities in key technologies such as authentication, encryption, and transmission [
26]. The weaknesses of WLANs themselves provide the possibility of denial of service (DoS) attacks and jamming attacks [
27].
Operating system risks. Some servers and hosts in the CBTC system use commercial systems such as Windows and VxWorks. These commercial systems have many vulnerabilities. Through vulnerabilities exploitation, the attacker can gain system privileges, crash systems, and remote code execution [
28].
Network equipment risks. The CBTC system uses a large number of network equipment as nodes for information exchange, such as switches, or gateways. If these key information exchange nodes are attacked, network communication will be affected.
Attackers utilizing these security risks may cause equipment failure, communication disruption, and service stops. Thanks to the redundant design and fail-safe principle of the CBTC system, the safety of urban rail transit can be guaranteed. However, under attack, the sensitive fail-safe mechanism will reduce train efficiency and disrupt traffic. When the equipment fails or communication is disrupted, the safety mechanism will start the train emergency braking, which may introduce huge economic losses. Therefore, security analysis for CBTC systems is a significant event.
2.3. Attack–Defense Strategy of CBTC Systems
To realistically simulate the interaction process between the attacker and the defender, we selected several attack methods for the CBTC system and developed corresponding defensive measures.
According to the vulnerability of WLAN, attackers can crack the password of WLAN to invade wireless networks. Due to the wireless network and the wired network in the signal network being connected, the attacker successfully invaded the CBTC intranet, laying the foundation for their next physical damage. The weakness of WLAN technology lies in its encryption method: Wi-Fi protected access (WPA). WPA handshake packets that are transmitted in cleartext include many parameters such as the MAC address of the client, BSSID (basic service set identifier) of AP, MIC (message integrity code), and so on. The MIC of the client which is equal to the MIC of AP is obtained by the WLAN password and these parameters through a specific algorithm. Therefore, we can use the password dictionary to calculate the MIC in combination with the parameters in the packet and compare it with the MIC of the AP (access point). If the two are the same, the password is the password of the wireless network, which indicates we have invaded the signaling networks. The prerequisite for successful password cracking is that the system uses a weak password. A complex password requires an extensive dictionary and a lot of time to crack. Therefore, the defense strategy against this attack is to dynamically change strong passwords.
The VxWorks operating system is widely used in signaling equipment, and wind debug (WDB) vulnerability is a system-specific vulnerability which can be utilized by an attacker to read or modify arbitrary memory locations, perform function calls, or manage tasks. Devices using the VxWorks operating system will reboot if we exploit the vulnerability to initiate the reboot program. In this paper, We made this sort of attack against vehicle on-board controller (VOBC) to interrupt the communication between AP and VOBC. To deal with this attack, we can install a specific patch.
ARP spoofing is an attack technology for an ethernet address resolution protocol (ARP). This type of attack allows an attacker to obtain packets on the LAN or even tamper with the packet and can prevent a particular computer or all computers on the network from connecting properly. In this paper, we adopted an ARP spoofing attack to interrupt the communication between ZC and CI. First, send an ARP reply packet, which contains the real IP and the fake MAC address of ZC, to the CC (communication controller) of the CI. After receiving the reply packet, the CC stores the wrong MAC address in the ARP cache table, which interrupts the communication between ZC and CI. ARP spoofing can be effectively addressed through IP-MAC binding.
A SYN flood attack is a denial of service (DoS) attack based on TCP protocol flaws. When TCP initiates a connection, it needs to go through three handshakes. If a client sends a large number of SYN requests to the server and it does not return an ACK packet in the meantime, then, there will be a large number of SYN queues on the server-side, which will cause a large number of server resources to be occupied, so that other normal users cannot access the server normally. In this paper, we used the SYN flood to exhaust the server resources of the CC in the ZC to achieve the purpose of interrupting ZC communication. We used a firewall to defend the attack. A cookie is assigned to each IP address of the request connection. If a duplicate SYN packet of the same IP is received within a short period of time, the packet from the IP address will be discarded.
The above is the attack and defense method for the CBTC system in this paper. Therefore, the strategy sets of attacker and defender in the penetration phase and disruption phase are determined:
,
,
,
.
3. Security Model of CBTC System under Attacks–Defense Confrontation
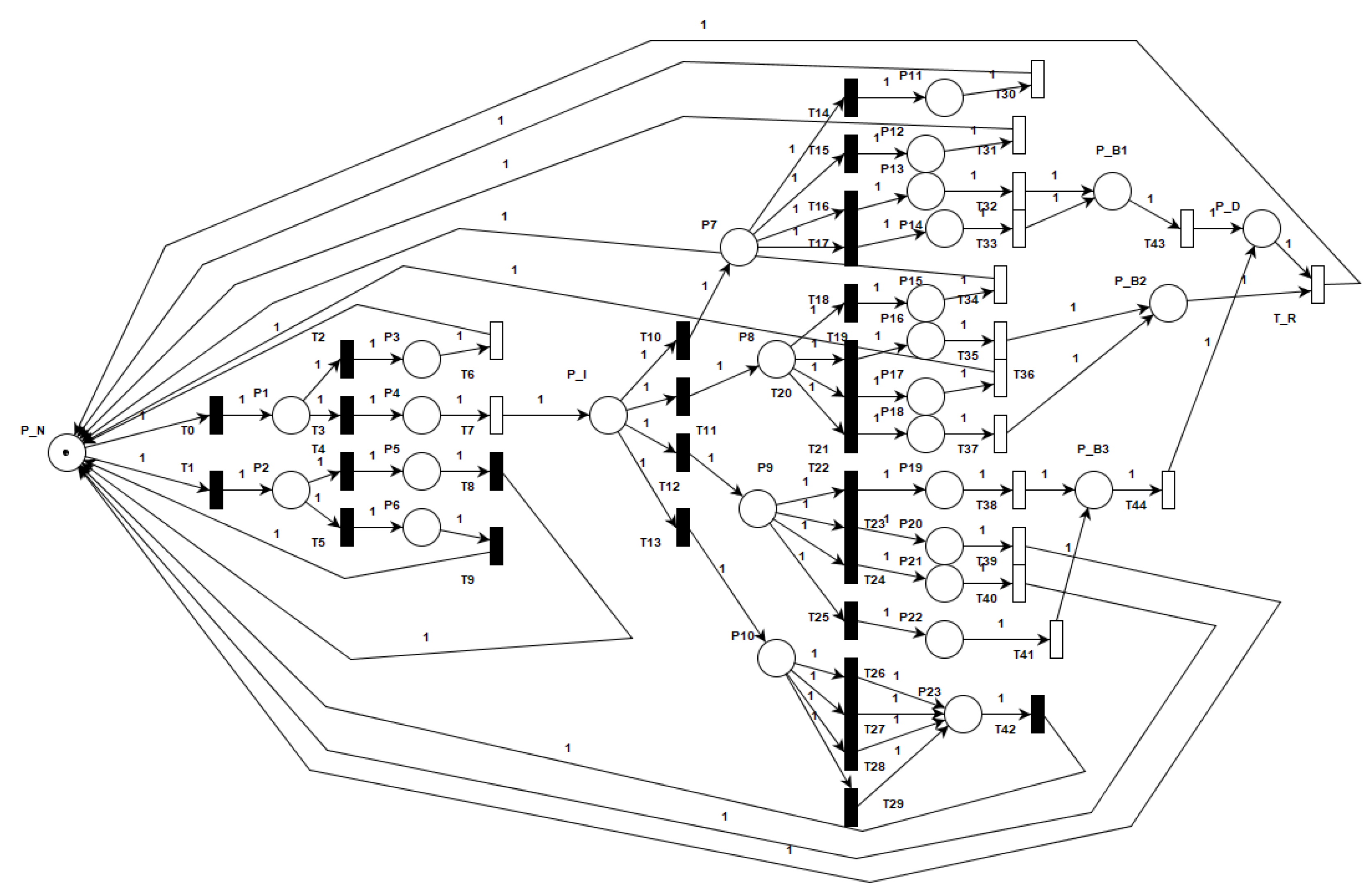
In this section, we propose an analytical model of system security under attacks and counter defense schemes. The overall framework of the model is shown in
Figure 2. We used the steady-state probability of the system obtained by the GSPN model to analyze and evaluate several indicators of system security, and the game model and simulation platform to assign values to parameters of the GSPN model.
3.1. Generalized Stochastic Petri Net Model
Petri nets are suitable for describing asynchronous, concurrent system models [
29]. SPN is used to depict specific business processes in [
30,
31]. The proposed model analyzes system availability by describing changes in system state under attack–defense confrontation. Our model is represented as a 6-tuple:
, where
P is a finite set of places which represent the condition, resource or state;
T is a finite set of transitions which indicate the occurrence of an event or action. T is divided into two subsets: T = , = ⌀, timed transitions consider the time factor of the process of transitions and immediate transitions takes zero time to fire and represent transient processes;
is a set of arcs, where and such that , . Arcs have directionality, connecting libraries and transitions;
is a set of transition firing rates associated with the transitions;
is a routing policy representing the probability of choosing a particular transition;
is the initial marking.
We divided the model into two phases: penetration and disruption, according to the attack process of the attacker. The penetration phase is the process of an attacker invading from the extranet to the intranet. Only by accessing to internal control network of the CBTC systems such as ATS networks and ATC networks can attackers damage the systems. It is well known that industrial control systems such as CBTC systems are relatively close compared to the Internet. In fact, with the continuous integration of industrialization and informatization, industrial control systems are increasingly using standardized communication protocols and hardware and software, and remote control and operation through the Internet, breaking the closure and specialization of the original system [
32]. Therefore, it is possible for an attacker to invade an industrial control network. Even if the industrial control network is entirely physically isolated from the external network, we still have a way to get it down. The US Stuxnet virus is an example.
In this paper, the wireless transmission network between train and ground became our approach to invade the CBTC system. We utilized vulnerabilities of WLAN to access CBTC control networks, namely, signaling networks. Further, there are the following intrusion methods: virus transmitted by USB flash disk, phishing, and wired network connection. To simplify the model for research, this paper adopts the method of wireless intrusion. In contrast, we also have several ways to combat this attack. In terms of hardware, NFC (near field communication) is used in some cellphones to magnetically link data in a range of just an inch or so, and could be integrated into the train power systems, as could similarly secure optical “synapses” at train car junctions. Additionally, a newly developed ELF (extremely low frequency) antenna might be able to evade most hacking attempts while allowing a train-length wireless communication data link. In terms of software, the method that is used in this paper is to improve the password strength of the wireless network.
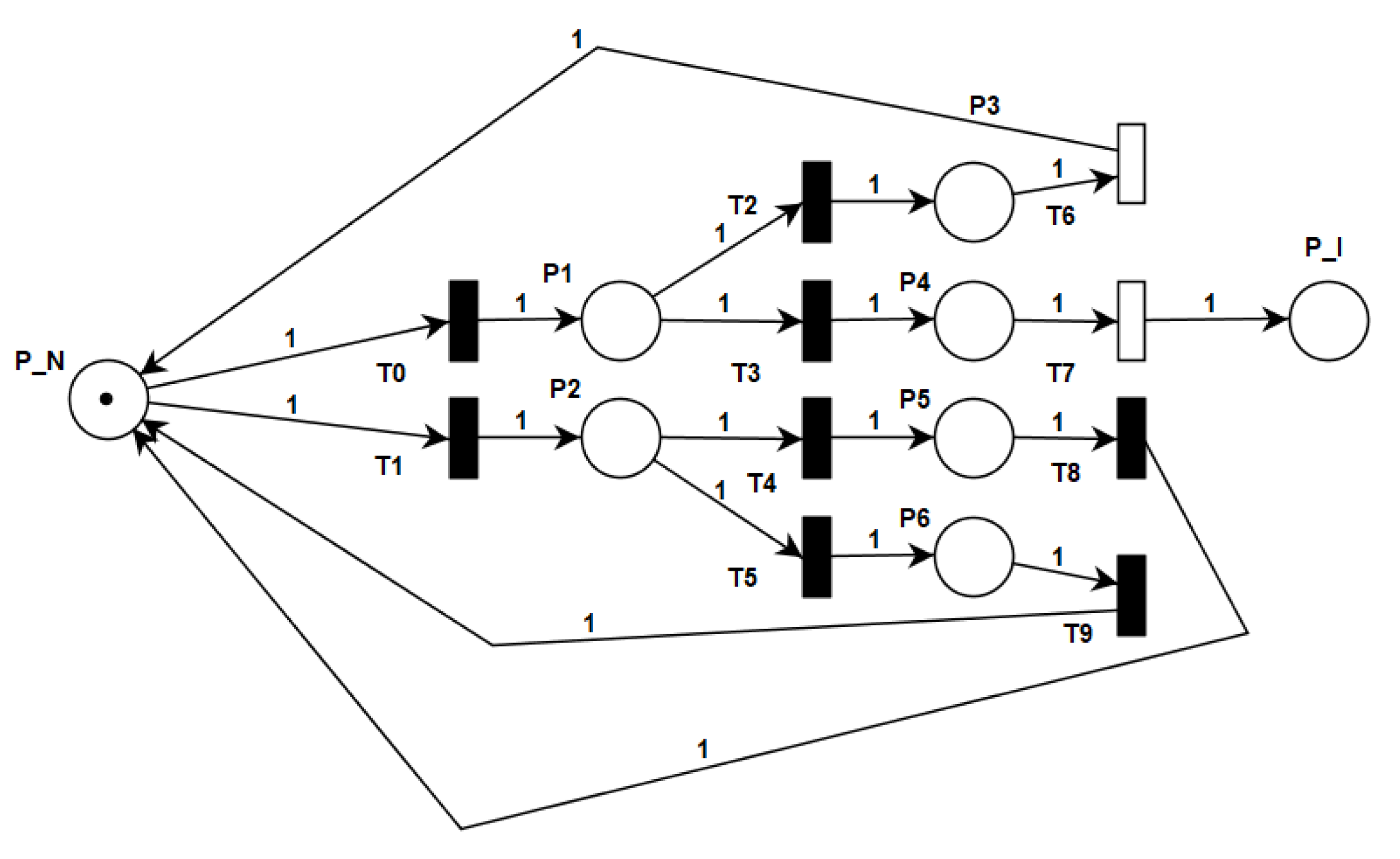
The penetration phase model is shown in
Figure 3, and the parameters description is shown in
Table 3. At first, the system is in a normal state P_N which represents that the CBTC system is running normally. Then, the attacker will decide their strategy and choose their behavior. Correspondingly, the defender will decide their strategy and choose their behavior. This is a confrontation process between attacker and defender. If the attacker launches a wireless intrusion attack and the defender has no resistance, the system will enter the intrusion state P_I, which indicates that the attacker has successfully entered the intranet of the CBTC system. Conversely, if the defender takes defensive measures, the attacker will fail. In this case, the system will not be affected by the attack, and the attacker needs to bear the loss of the attack failed. Obviously, when the attacker chooses behavior (
), regardless of the strategy adopted by the defender, the system remains in a normal state.
The disruption phase is based on the system having been invaded. There is no point in considering the disruption phase if the system state cannot transition to the intrusion state. In the penetration phase, the attacker has not yet performed the damaging attack against the system, and therefore the attacker needs to perform specific damaging attacks on the system. Thanks to the contribution of the penetration phase, the attacker can initiate damage on the intranet of the CBTC system. Various vulnerabilities of the system are exposed to the attacker, especially one who has an understanding of the internal architecture of the system in the disruption phase.
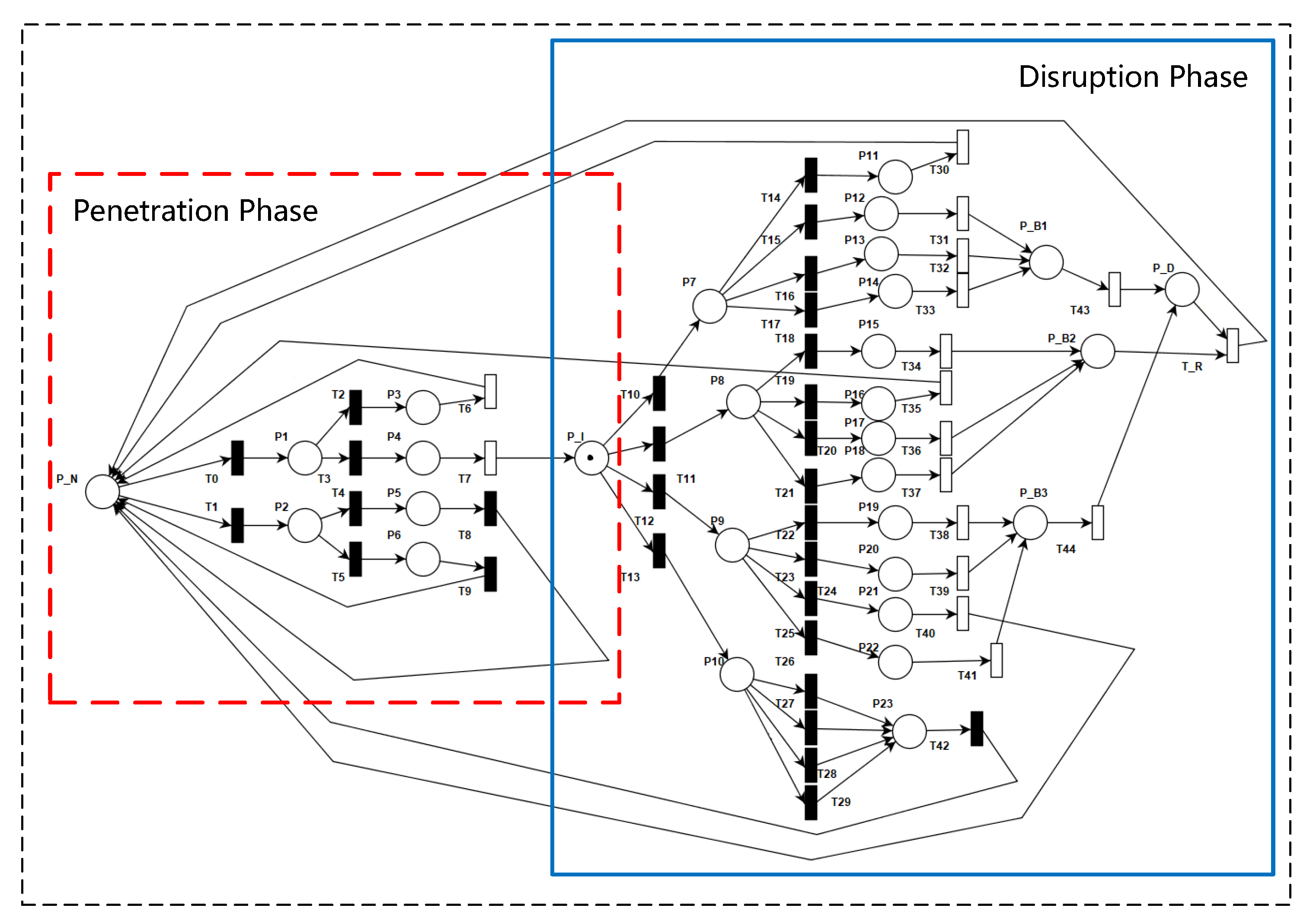
Our disruption phase model is shown in the right part of
Figure 4, and the parameters description is shown in
Table 4. Just like the penetration phase, the attacker chooses the attack behavior and the defender takes countermeasures, and then the state of the system changes. The disruption phase starts from the place P_I, which indicates the attacker has entered the internal network of the system. In this case, the attacker and the defender choose behaviors for the attack–defense game with a certain probability. The next attack–defense confrontation process is as follows:
If the attacker adopts behavior () and the defender does not take the right defensive behavior, emergency braking will occur on the train because of the communication between VOBC and AP is interrupted. The train can be restarted and operate in BLOC (block-based train control) mode after stopping.
If the attacker adopts behavior () and the defender does not take the right defensive behavior, the attacker interrupts the communication between ZC and CI, which causes the system to enter the emergency braking state. Furthermore, the train cannot operate in BLOC mode because the CI cannot handle the route automatically.
If the attacker adopts behavior () and the defender does not take the right defensive behavior, the CBTC system will enter the emergency braking state again because of ZC is crashed by the attacker. In this case, the train can be restarted and operate in BLOC (block-based train control) mode after stopping.
If the defensive measure of the defender works, the system state will return to normal state. In this paper, one defensive measure only works for one type of attack. The corresponding offensive and defensive behavior is as follows: (, ), (, ), (, ).
After a system failure, it will eventually return to normal after a period, which is described by timed transit T_R.
Since the GSPN model is isomorphic with the continuous time Markov chain (CTMC), we found a way to solve the model. By transforming the model into CTMC, we can analyze the steady-state probability of the model. In Petri nets, the states which associate with the immediate transition should be eliminated. The time the token stays in these states approaches zero; therefore, these states have no steady-state probability. According to the correlation theorem of Markov chain stationary distribution and the Chapman–Kolmogorov equation, we get:
where W is the steady-state probability vector of Markov chain marker
which represents the steady state of CBTC systems.
Q is a transfer rate matrix with element
. If
,
is equal to the rate from
to
and when
,
is equal to the inverse of the sum of the rate of arcs from
. In addition, the rate from
to
is obtained by multiplying the transition firing rate
by the probability of choosing an immediate transition
. After quantifying the parameters such as
and
, we can obtain the steady-state probability.
3.2. Attack–Defense Game Model
In this paper, we propose the game model to assist the GSPN model in completing the parameterization process. Through the attack–defense game model, we can predict the behavior of attackers and defenders and obtain the strategies of both players. In this paper, we believe that the attacker is not a reckless person who blindly pursues the proceeds but a wise man who fully considers the gains and losses, and the defender is rational similarly. For the attack–defense confrontation model, both rational players in the process of an attack–defense game aim to maximize their income, which is their criterion for choosing attack–defense behavior. Since the profit of the attacker and the defender is based on the loss of the opponent, there is no win–win between the two players, that is, there is no pure-strategy Nash equilibrium. To predict how rational players would choose their behaviors and play the game, we need to solve the mixed strategy Nash equilibrium.
represents the payoff function of the attacker under the attacker behavior
and the defender behavior
.
represents the payoff function of defender under the attacker behavior
and the defender behavior
. We can obtain the specific payoff of the attacker and defender through the following equations:
where
and
represent the cost and return of attack behavior, and
and
represent the cost and return of defense behavior.
Let
and
denote the attacker and the system defender optimal mixed strategies.
and
are income expectation of the attacker and defender when the attacker adopts stategy
, and the defender adopts strategy
. We can obtain the
and
through the following equations:
Therefore, the Nash equilibrium of the attack–defense game should satisfy the following two conditions:
- (1)
≥ , ≥
- (2)
≥ , ≥
5. Analysis and Evaluation
In this section, we analyze and evaluate the security of the CBTC system based on the solution results of the GSPN model. Several indicators are proposed to complete the assessment of system security.
One indicator is the availability of the system. Availability denotes the probability or proportion of time a system is in a functioning condition. The equation for the calculation is as follows:
where
s represents the state of the system, and
A is the state sets where the system is operating properly. In this paper, the system can perform business normally in the normal state and intrusion state. Therefore, we obtained the availability with value 72.1% under attack–defense confrontation, which indicates that although there are defensive measures, the security of the CBTC system is still greatly threatened. Therefore, improving the security of CBTC systems is an urgent task for system operators.
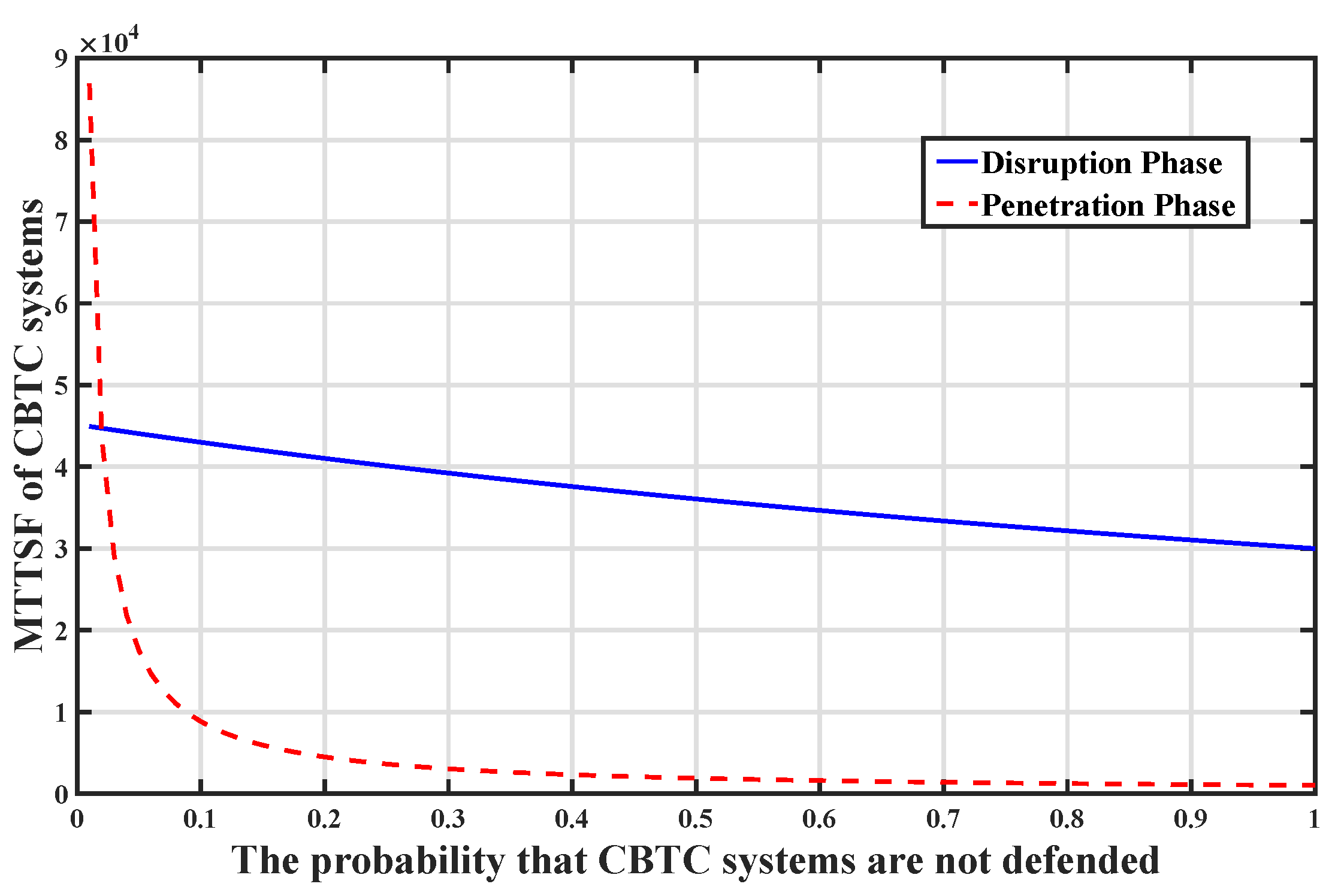
To explore the impact of defense on system security, we adjusted the probability that the system does not use defensive measures in the GSPN model. As shown in
Figure 7, the solid line is the change of system availability with the probability of the nondefense behavior in the disruption phase. We kept increasing the weight of
while keeping the original ratio of
,
, and
unchanged. We can see that as the probability of nondefense increases, the availability of the system continues to decrease. When the system is completely undefended in the disruption phase, the availability reaches 63%. The dotted line represents the same situation in penetration. In this case, strategies of the attacker and defender in the disruption phase are still the optimal strategies
and
obtained above. Comparing the two results, we can find that the defensive measures are more effective in the penetration phase, which means that it is more significant to adopt the defensive measures in the penetration phase.
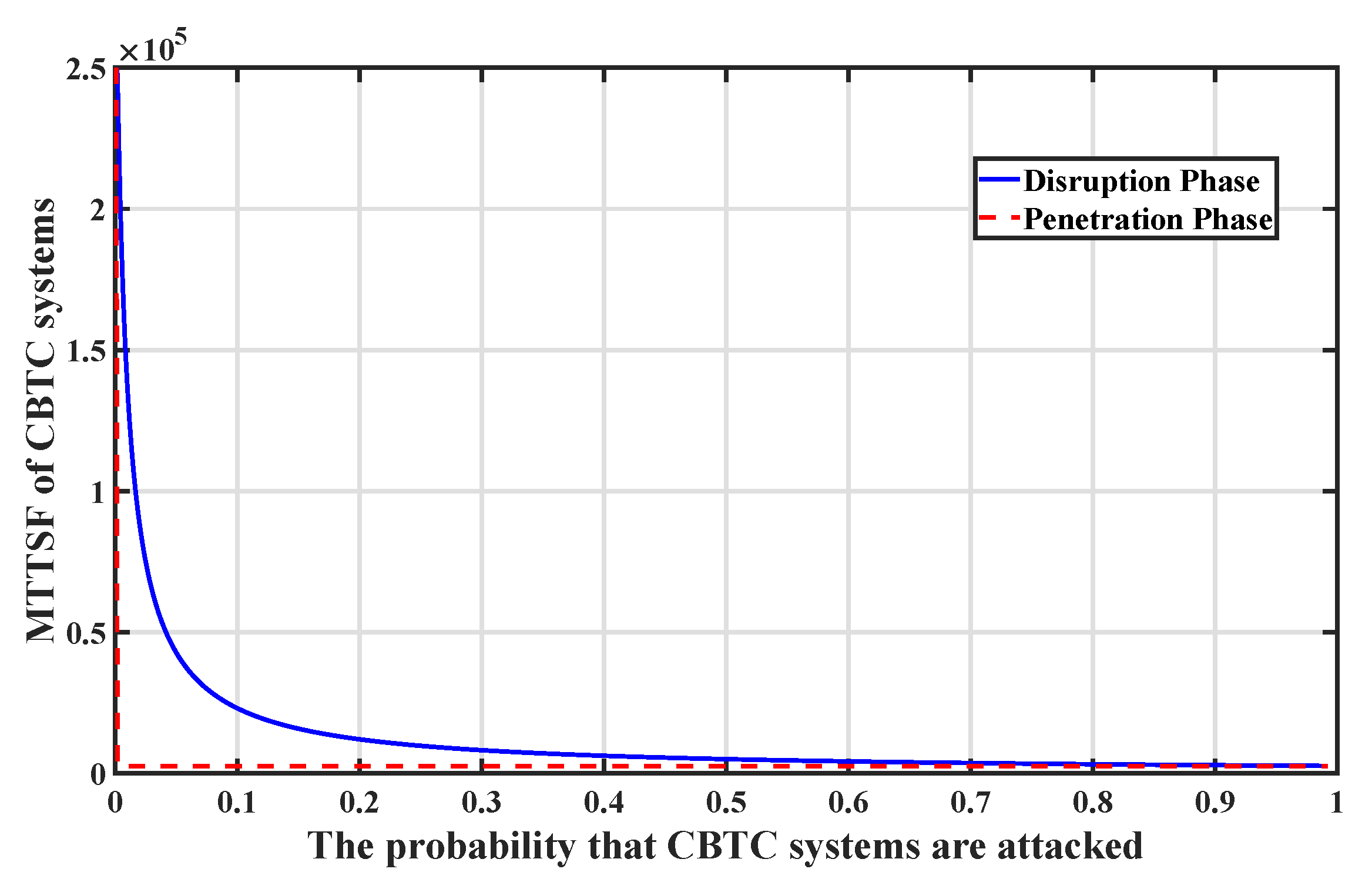
In the same way, we kept the other parameters unchanged and only adjusted the probability of the attacker launching the attack. In the disruption phase, the probabilities of
,
and
are adjusted according to the original ratio. Results are shown in
Figure 8. The lowest point of the two lines is 71%, which indicates that, with specific defensive measures, even if an attacker frequently launches attacks, the availability of the system can remain above 70%. This result fully demonstrates the importance of defensive measures for system security.
Another security indicator is the mean time to security failure (MTTSF), which draws on the experience of the MTTF in the reliability field. MTTSF is defined as the measure for quantifying the security of systems [
33]. MTTSF is the duration time for which the model stays in an intermediate state before it finally enters the absorbing state. Different from the steady-state probability of the system, to calculate MTTSF, we assume that the failure state is the absorption state, that is, it does not recover after the train failure. The MTTSF can be obtained by the following equation:
where
is the visit rate of state a and
is the mean sojourn time in the state a. The average visit rate is defined as the average number of times that a state is visited before the model reaches absorbing states. Further, the visit rate can be calculated by this equation:
where
is the probability of the transition from state b to state a, and
is the probability that the model starts in the state a. The probability of transition can be calculated by the probability of choosing immediate transition
. In addition, we assume the
= 1 in the normal state, and
= 0 in other state.
According to the solution result of the Petri nets and Equations (9) and (
10), the MTTSF under attack–defense confrontation is 2546.2 s. Honestly, this is not a desired result, and the security of CBTC systems needs to be improved.
Like the analysis of system availability above, we get the
Figure 9 and
Figure 10. Simulation results show that, compared to the penetration phase, the security of CBTC systems is not sensitive to defensive measures in a disruption phase. Therefore, defense protection work during the invasion phase is more significant. Further, the existence of defensive measures determines the lower limit of MTTSF, that is, the MTTSF of the system can remain 2546 s in the worst situation.
Therefore, the system operator should spend a lot of effort to resist the attacker’s invasion from the extranet to the intranet. We recommend using a more efficient and secure LTE-M instead of WLANs. The defense of the destruction phase is equally important because internal attackers and certain special jamming attacks can directly skip the penetration phase to damage the system.
Based on the above analysis and evaluation results, we found that under the attack of the attacker, the availability of the system is only 71%, and the MTTSF is only 2546 s. For an urban rail transit system that is related to people’s livelihood, such security is too low. We speculate that the cause of this result is insufficient defense input. In this article, defenders used only one defensive measure at a time. Next, the defender uses the combined measures to complete the attack–defense confrontation process, compared with the security under the previous single measure. Since the offensive and defensive methods are single during the penetration phase, we made a combination of the defense methods of the disruption phase. Therefore, the new attack–defense strategy sets are as follows:
,
,
,
.
The new attack–defense confrontation model is shown in
Figure 11. In this model, the definition of the places and the transitions has not changed. The only change is the path between the places and the transitions. For comparison, we used the probability of the previous model:
,
,
,
.
According to Equations (
1) and (
2), we obtained the steady-state probability of the new model in
Table 9.
Then, we can calculate the security indicators of the CBTC system:
Availability: 83.5%, MTTSF: 14523.6 s.
This result reveals that the combined defense measures can indeed improve the security of the system. Therefore, for security reasons, urban rail transit operators should invest heavily in system defense. For example, disabling unused equipment ports, installing vulnerability patches, and deploying firewalls at the network perimeter are significant to improve system security.