DDTMS: Dirichlet-Distribution-Based Trust Management Scheme in Internet of Things
Abstract
1. Introduction
2. Related Works
2.1. TMS Based on Beta Distribution
2.2. TMS Based on Gaussian Distribution
2.3. TMS Based on Dirichlet Distribution
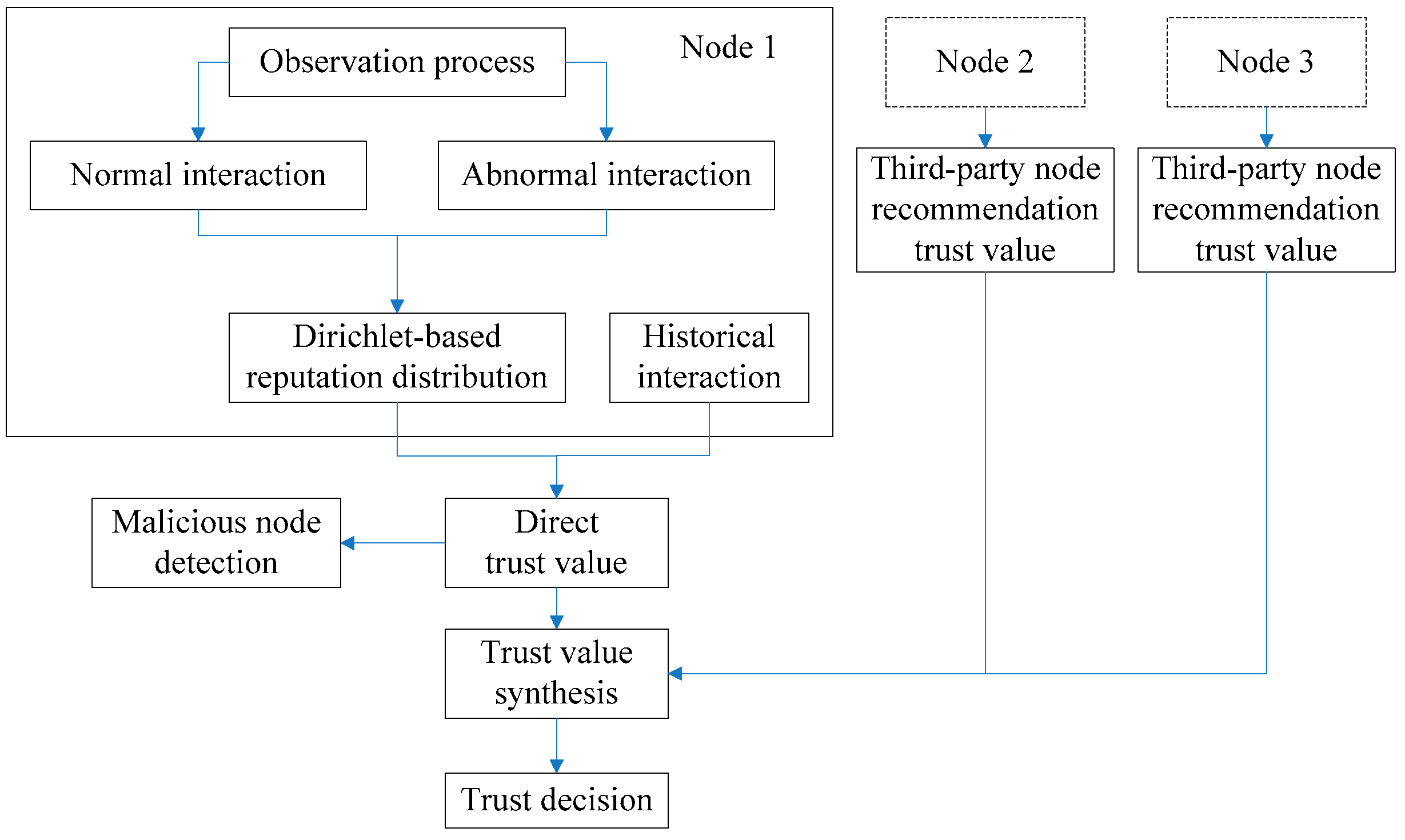
3. Dirichlet-Distribution-Based Trust Management Scheme (DDTMS)
3.1. Design of DDTMS
3.2. Dirichlet-Based Reputation Distribution Model
3.2.1. Dirichlet Distribution
3.2.2. Trust Value Based on Dirichlet Distribution
A. Trust ValueunderDirect Observation
B. Third-Party Recommended Trust Value Calculation
C. Trust Value Synthesis
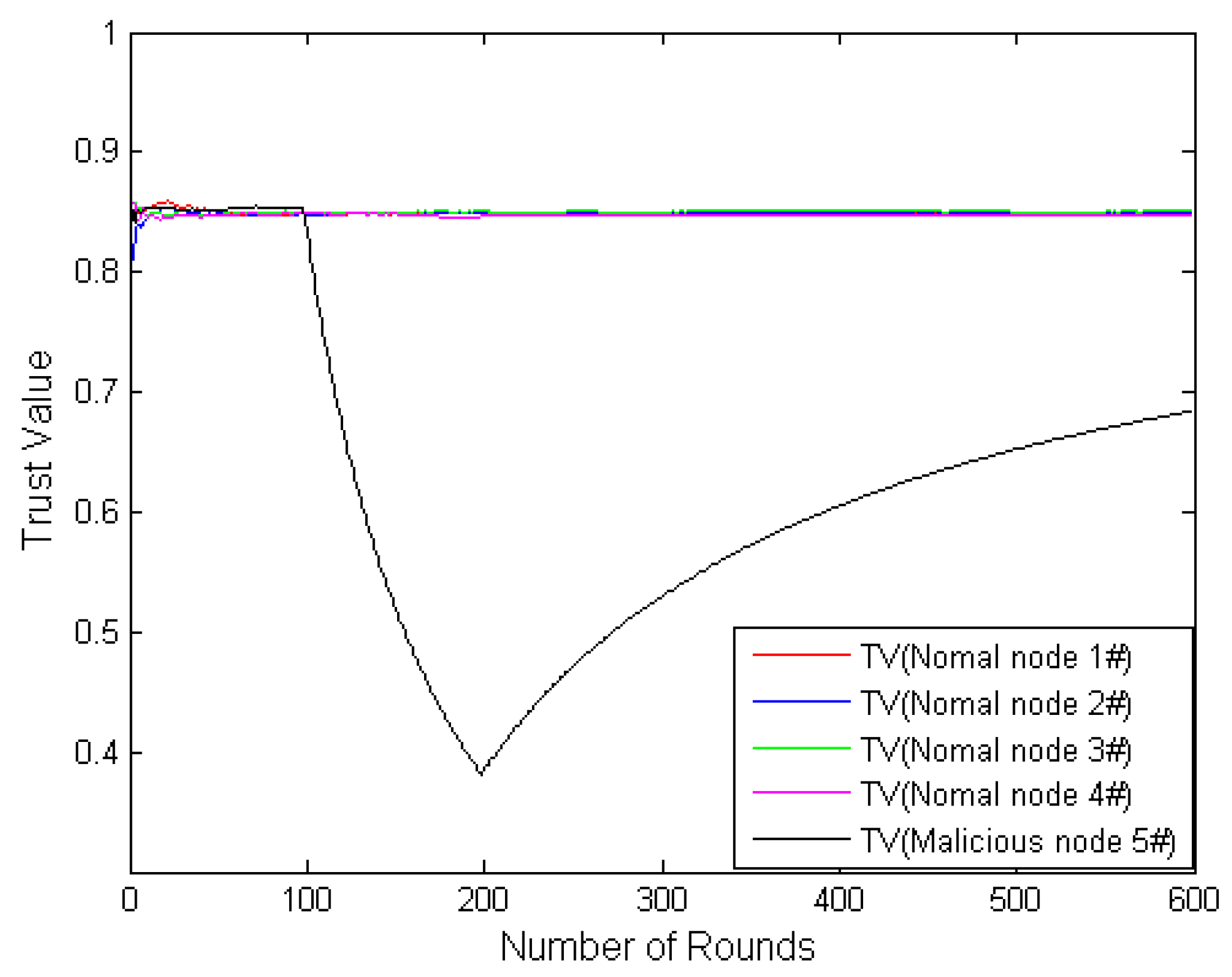
4. Simulations and Analysis
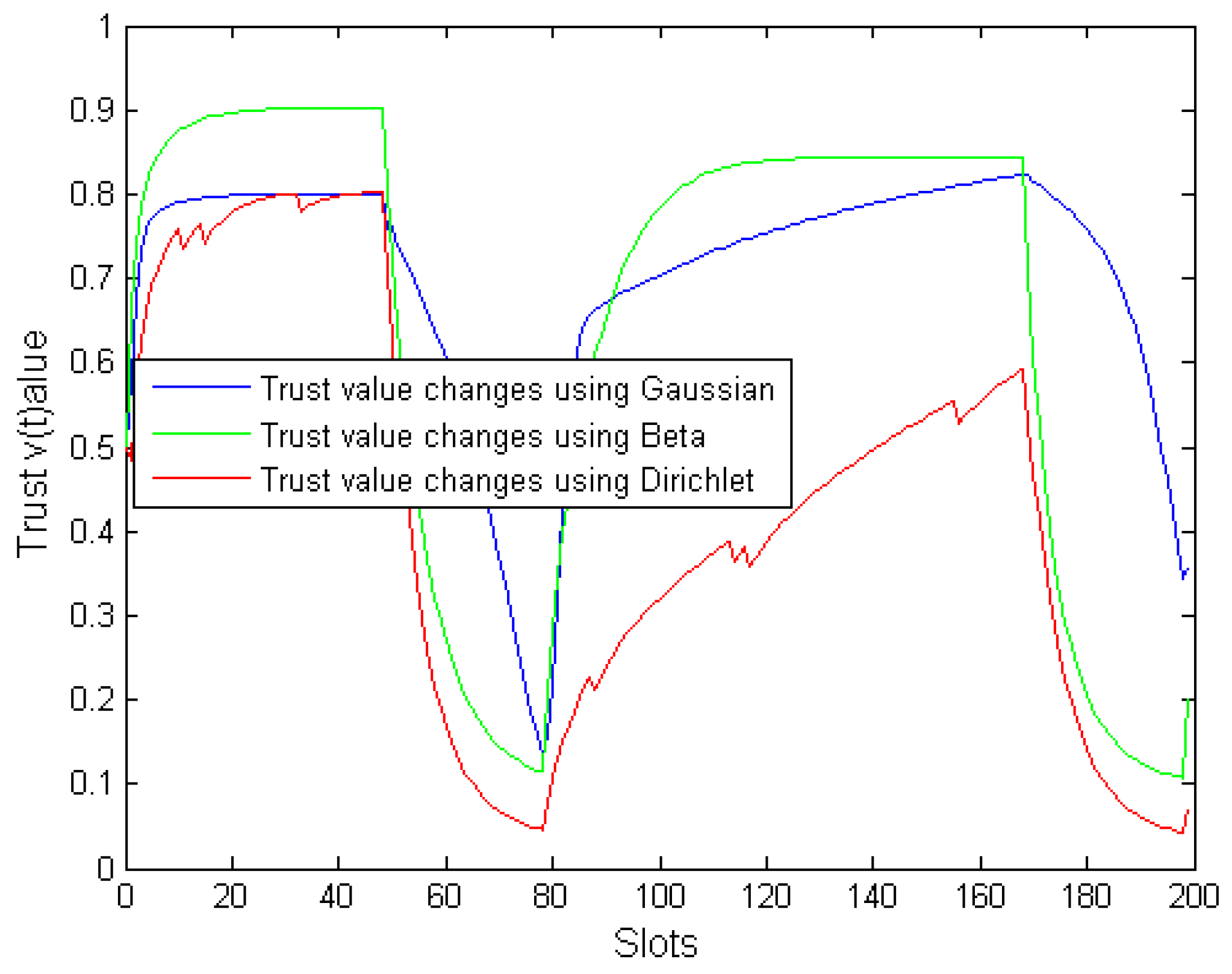
4.1. Comparison Between DDTMS, Beta Distribution, and Gaussian Distribution
- The initial trust value of both nodes without any interaction is 0.5 ∈ (0,1).
- Normal nodes and malicious nodes perform a total of 200 interactions.
- A malicious node performs the attack on the 50th interaction and the 170th interaction, respectively, 30 attacks per attack.
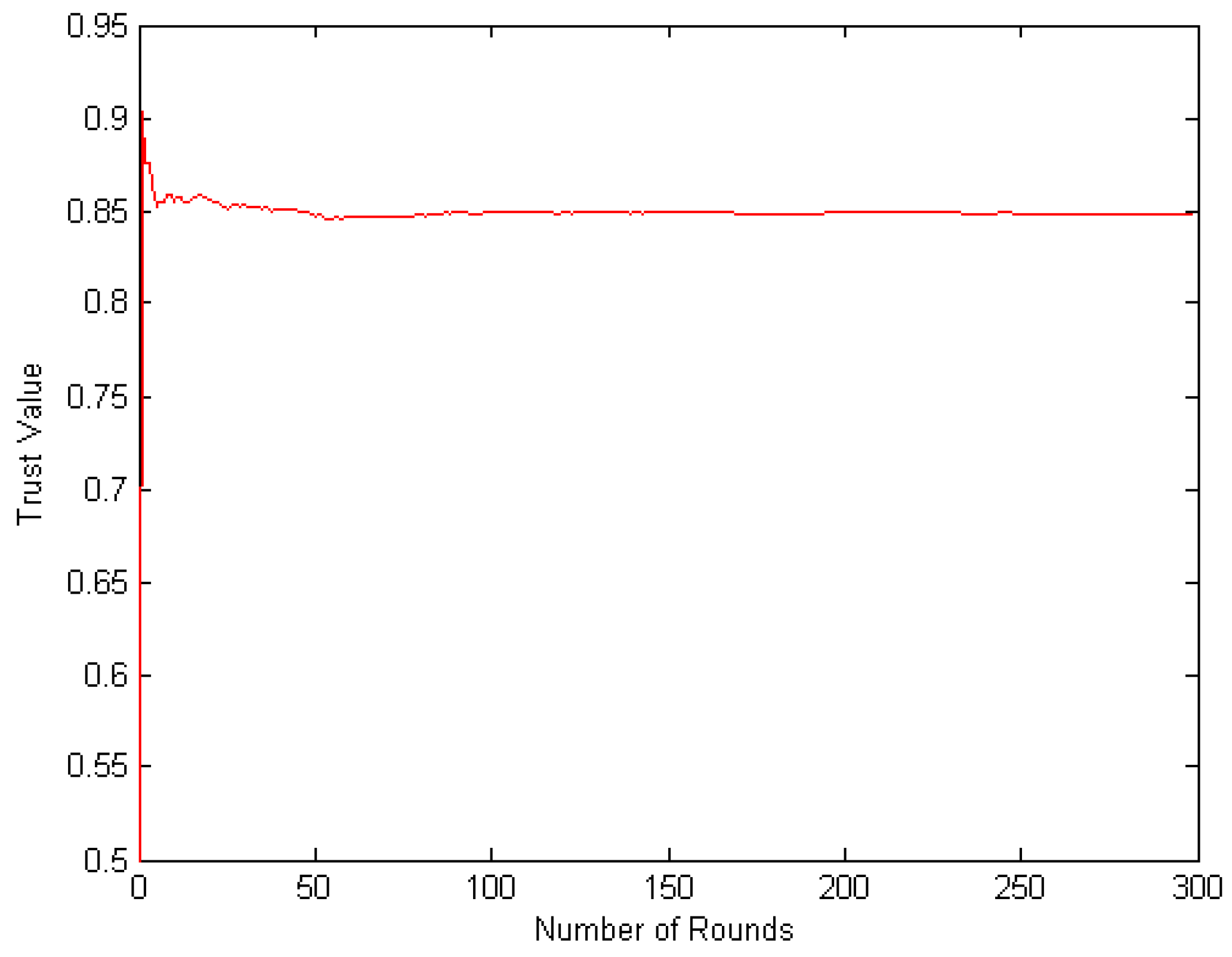
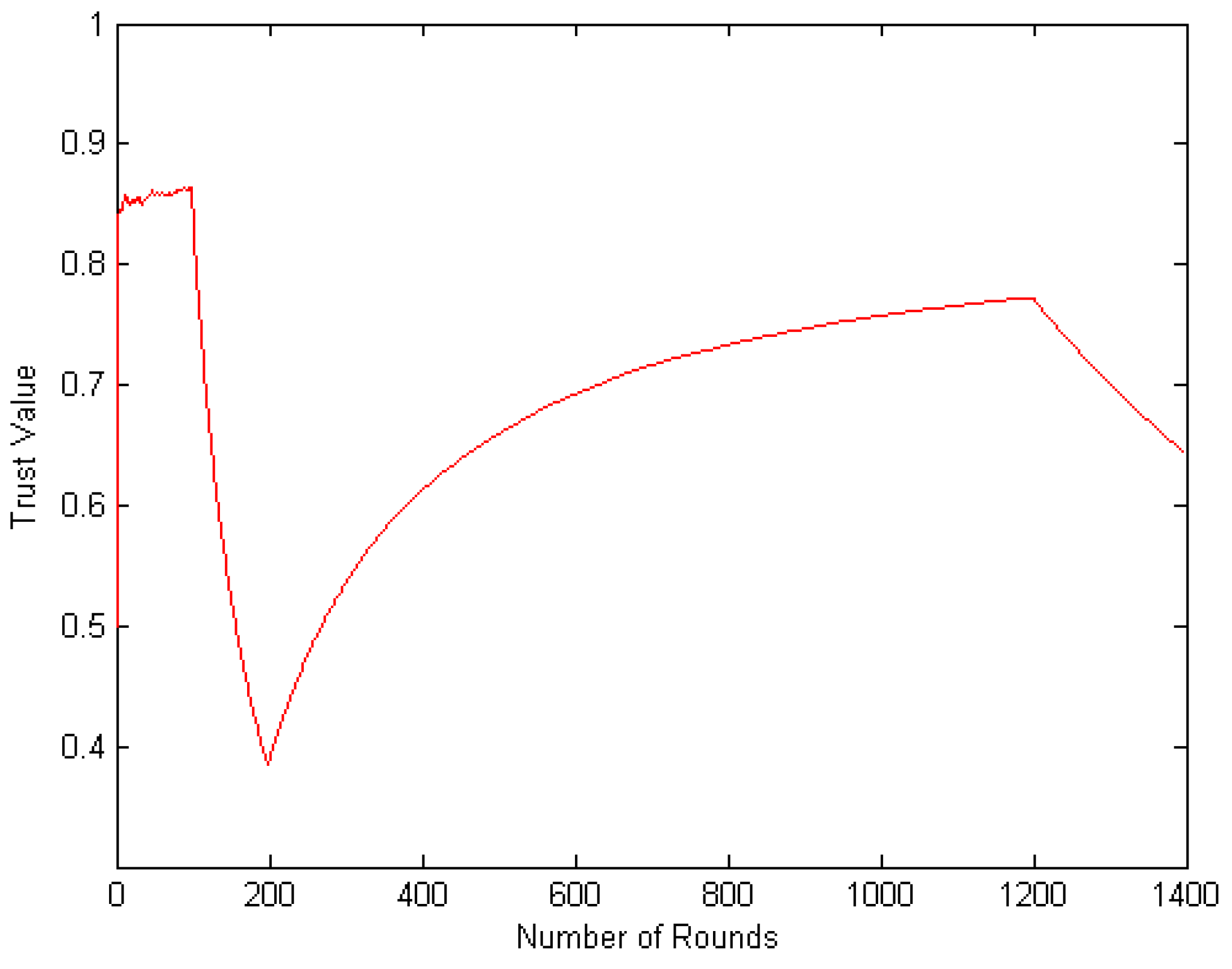
4.2. Node Interaction Based on Dirichlet Distribution
5. Conclusions and Prospect
Author Contributions
Funding
Conflicts of Interest
References
- Mehdi, N.C.; Ahmad, K.-Z.; Majid, H.A. New Hybrid Fault Tolerance Approach for Internet of Things. Electronics 2019, 8, 518. [Google Scholar] [CrossRef]
- Ge, W.; Zhu, Z.; Hao, W.; Wang, Y.; Wang, Z.; Wu, Q.; Chu, Z. AN-Aided Secure Beamforming in Power-Splitting-Enabled SWIPT MIMO Heterogeneous Wireless Sensor Networks. Electronics 2019, 8, 459. [Google Scholar] [CrossRef]
- Fang, W.; Zhang, C.; Shi, Z.; Zhao, Q.; Shan, L. BTRES: Beta-based Trust and Reputation Evaluation System for wireless sensor networks. J. Netw. Comput. Appl. 2016, 59, 84–92. [Google Scholar] [CrossRef]
- Ganeriwal, S.; Srivastava, M.B. Reputation-based framework for high integrity sensor networks. In Proceedings of the2nd ACM Workshop on Security of Ad Hoc and Sensor Networks (SASN ’04), Washington DC, NY, USA, 25–25 October 2004; pp. 66–77. [Google Scholar]
- Wu, X.; Huang, J.; Ling, J.; Shu, L. BLTM: Beta and LQI Based Trust Model for Wireless Sensor Networks. IEEE Access 2019, 7, 43679–43690. [Google Scholar] [CrossRef]
- Ahmed, A.; Bhangwar, A.R. WPTE: Weight-Based Probabilistic Trust Evaluation Scheme for WSN. In Proceedings of the 5th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Prague, Czech, 21–23 August 2017; pp. 108–113. [Google Scholar]
- UmaRani, V.; Sundaram, K.S.; Jayashree, D. Enhanced Beta Trust Model in wireless sensor networks. In Proceedings of the International Conference on Information Communication and Embedded Systems (ICICES), Chonburi, Thailand, 25–26 February 2016; pp. 1–5. [Google Scholar]
- Mahmud, M.; Kaiser, M.S.; Rahman, M.M.; Rahman, M.A.; Shabut, A.; Al-Mamun, S.; Hussain, A. A Brain-Inspired Trust Management Model to Assure Security in a Cloud Based IoT Framework for Neuroscience Applications. Cogn. Comput. 2018, 10, 864–873. [Google Scholar] [CrossRef]
- Yin, G.; Zhang, J.; Yan, T. Study on the penalty function based on redemption mechanism for trust value of WSN. In Proceedings of the 6th International Conference on New Trends in Information Science, Service Science and Data Mining (ISSDM2012), Taipei, Taiwan, 23–25 October 2012; pp. 683–688. [Google Scholar]
- Momani, M.; Challa, S.; Alhmouz, R. BNWSN: Bayesian network trust model for wireless sensor networks. In Proceedings of the Mosharaka International Conference on Communications, Computers and Applications, Amman, Jordan, 8–10 August 2008; pp. 110–115. [Google Scholar]
- Sinha, R.K.; Jagannatham, A.K. Gaussian trust and reputation for fading MIMO wireless sensor networks. In Proceedings of the IEEE International Conference on Electronics, Computing and Communication Technologies (CONECCT), Bangalore, India, 6–7 January 2014; pp. 1–6. [Google Scholar]
- Singh, S.I.; Sinha, S.K. A framework for reputation model based on time and trust aware Heteroscedastic Gaussian process. In Proceedings of the International Symposium on Advanced Computing and Communication (ISACC), SilcharAssam, India, 14–15 September 2015; pp. 16–20. [Google Scholar]
- Fung, C.J.; Zhang, J.; Aib, I.; Boutaba, R. Dirichlet-Based Trust Management for Effective Collaborative Intrusion Detection Networks. IEEE Trans. Netw.Serv. Manag. 2011, 8, 79–91. [Google Scholar] [CrossRef]
- Rani, V.U.; Sundaram, K.S. Dirichlet Distribution Based Trust Model for Malicious Node Detection in Wireless Sensor Network. J. Eng. Appl. Sci. 2019, 14, 4191–4199. [Google Scholar]
- Abderrahim, O.B.; Elhedhili, M.H.; Saidane, L. DTMS-IoT: A Dirichlet-based trust management system mitigating on-off attacks and dishonest recommendations for the Internet of Things. In Proceedings of the IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016; pp. 1–8. [Google Scholar]
- Li, B.; Lu, R.; Wang, W.; Choo, K.-K.R. DDOA: A Dirichlet-Based Detection Scheme for Opportunistic Attacks in Smart Grid Cyber-Physical System. IEEE Trans. Inf. ForensicsSecur. 2016, 11, 2415–2425. [Google Scholar] [CrossRef]
- Huang, Q.; Nan, H. Reputation Computing for Wireless Sensor Networks Based on Dirichlet Distribution. Chin. J. Sens. Actuat. 2009, 22, 526–530. [Google Scholar]
| Parameter | Value |
|---|---|
| Direct and indirect reputation information weights (α,β) | (60%,40%) |
| Tinit | 0.5 |
| μGaussian | 0.5 |
| δGaussian | 0.5 |
| ws | 0.85 |
| wf | 1 |
| wu | 0.05 |
| DDTMS | Beta-Distribution-Based (BD) | Gaussian-Distribution-Based(GD) | |
|---|---|---|---|
| Under normal status |
|
|
|
| Under attack status |
|
|
|
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fang, W.; Zhang, W.; Shan, L.; Ji, X.; Jia, G. DDTMS: Dirichlet-Distribution-Based Trust Management Scheme in Internet of Things. Electronics 2019, 8, 744. https://doi.org/10.3390/electronics8070744
Fang W, Zhang W, Shan L, Ji X, Jia G. DDTMS: Dirichlet-Distribution-Based Trust Management Scheme in Internet of Things. Electronics. 2019; 8(7):744. https://doi.org/10.3390/electronics8070744
Chicago/Turabian StyleFang, Weidong, Wuxiong Zhang, Lianhai Shan, Xiaohong Ji, and Guoqing Jia. 2019. "DDTMS: Dirichlet-Distribution-Based Trust Management Scheme in Internet of Things" Electronics 8, no. 7: 744. https://doi.org/10.3390/electronics8070744
APA StyleFang, W., Zhang, W., Shan, L., Ji, X., & Jia, G. (2019). DDTMS: Dirichlet-Distribution-Based Trust Management Scheme in Internet of Things. Electronics, 8(7), 744. https://doi.org/10.3390/electronics8070744






