Abstract
User authentication for the Internet of Things (IoT) is a vital measure as it consists of numerous unattended connected devices and sensors. For security, only the user authenticated by the gateway node can access the real-time data gathered by sensor nodes. In this article, an efficient privacy-preserving authentication and key agreement scheme for IoT is developed which enables the user, the gateway node and sensor nodes to authenticate with each other. Only the trusted gateway node can determine the real identity of user; however, no other entities can get information about user’ identity by just intercepting all exchanged messages during authentication phase. The gateway cannot prove the received messages from the sender to a third party, and thus preserving the privacy of the sender. The correctness of the proposed scheme is proved to be feasible by using BAN logic, and its security is proved under the random oracle model. The execution time of the proposed scheme is evaluated and compared with existing similar schemes, and the results demonstrate that our proposed scheme is more efficient and applicable for IoT applications.
1. Introduction
The Internet of Things (IoT) [1] is an enormous ubiquitous-network which is connecting the objects through various sensor devices and networks. It plays an important role in people’s lives and has been widely used in many fields to gather data such as transportation [2], education, smart healthcare [3,4,5], logistics, etc. In general, the network of IoT is formed by end-users, sensors and base stations (e.g., gateway), in which sensors can collect data of specific areas around them and then end users can access data on demand through the network.
However, the IoT is vulnerable to lots of malicious attacks due to its inherent the computational constraints of the sensors and the openness of wireless channel in IoT environment [1]. It is becoming a principal security concern that how to ensure that only valid end-users can access the critical data. To address this problem effectively, several authentication mechanisms [6,7,8,9] have been proposed to guarantee the authenticity of entities as well as the confidentiality of transferred data during communication in IoT. In an IoT environment, there exist three types entities, i.e., users, gateways and sensors. The gateways are specific modes which are served as trusted servers during authentication. Then sensors locate in various application environment to collect data. The user can access data in sensors while he or she has been authenticated by gateway. The basic goal of authentication is to enable gateway nodes, end-users and sensor nodes to authenticate each other. In order to meet functionality and security requirements, however, designing authentication and key agreement schemes to guarantee secure communication for the Internet of Things is challenging.
User authentication is vital in the IoT environment since it is used to distinguish legitimate users from illegal users. Only legitimate users can be granted with permission to access the data collected by sensor devices. Over the past few years, many user authentication schemes about the IoT environments have been designed. For example, Wong et al. [10] in 2006 put forward a user authentication protocol using symmetric encryption which utilizes hash and XOR operations to lower the computational complexity. Later, Das [11] presented an improved password-based user authentication to enhance the security of Wong et al.’s scheme. [10]. Other scholars [12,13,14] revealed that Wong et al.’s scheme is short of providing user anonymity and mutual authentication. Due to the merits of identity-based cryptography, some researchers presented novel identity-based authentication schemes [15,16], however, the computational cost in these schemes are expensive because of the adoption of pairing operation. Taking account of many existing construction of classic authentication schemes are based on public key technique, some researchers adopted symmetric cryptography-based means to improve the performance of authentication. Jung et al. [17] proposed a user anonymous authentication scheme based on symmetric encryption, which uses dynamic to achieve anonymity. Considering mutual authentication is important in some IoT applications, Xue et al. [18] constructed a user authentication scheme based on temporal-credential where the gateway node issues temporary certificates to the user and sensor nodes to achieve mutual authentication. Jiang et al. [19] pointed out that Xue et al.’s scheme fails to resist privileged-insider attack and then proposed an improved signature-based authentication scheme. Das [20] introduced an enhanced three-factor user authentication scheme based on Jiang et al.’s [19] work using user biometric information.
Since privacy plays a central role in designing authentication and key agreement schemes, and great efforts have been made in privacy-preserving authentication. Fox example, in 2015, Wang et al. [21] presented a new authentication scheme for wireless body area networks(WBANs) using bilinear pairing to achieve anonymity; however, it is vulnerable to the impersonation attack. Li et al. [22] proposed an anonymous authentication scheme using the hash message authentication code (HMAC). However, it is infeasible for the limited IoT environment since the bilinear pairing would bring enormous costs. Porambage et al. [23] presented an ECC-based authentication protocol without bilinear pairing to achieve high efficiency. Some signature-based authentication schemes [24,25] have been investigated besides interactive protocol-based authentication schemes.
The previous work has proposed different methods to ensure security and to meet the functionality requirements. However, most of the existing schemes have weaknesses, such as high computation overhead, being susceptible to some attacks or not providing user privacy-preserving. Furthermore, all these existing schemes fail to deal with deniability and traceability at the same time, which looks contradicts with each other. Deniability is essential for users in IoT environment to preserve her or his privacy, however, traceability is vital to prevent malicious entities to damage the IoT applications. Hence, based on the previous work, we propose an ECC-based privacy-preserving authentication and key agreement scheme for IoT, which aims to provide conditional privacy protection and desirable performance.
This paper presents a privacy-preserving authentication and key agreement scheme with deniability for IoT, which enables user to access IoT sensor securely. More specifically, the scheme meets appropriate security requirements and supports desirable features. The characteristics of our proposal are as follows:
- User anonymity. No entity except the trusted gateway nodes can obtain any information about the identity of the users during the authentication phase.
- Deniability. The gateway node can generate another message that is indistinguishable from the received message from the user, such that when the user request a service via the gateway node, any third party cannot tell whether the message is sent by the user or generated by the gateway node. Therefore, the user can deny that he or she has requested the service.
- Unlinkability. Any external entity except the trusted gateway node cannot determine whether two messages from distinguished authentication sessions are sent by the same entity.
- Traceability. If any dispute or misbehavior occurs during the authentication phase, the trusted gateway node can reveal the identity of the user with the exchanged messages.
- High-efficiency. Due to the adoption of low-cost hash functions and ECC(elliptic curve cryptography) operations, the proposed scheme is more efficient than the existing exponential or bilinear pairing-based authentication schemes.
The remainder of this article is structured as follows. Section 2 provides related preliminaries. The concrete construction of the proposed scheme is described in Section 3. Section 4 presents a rigorous security analysis about the proposed scheme. Section 5 conducts the performance evaluation. Conclusions of the paper are presented in Section 6.
2. Preliminaries
In this section, some basic knowledge including communication model, the random oracle model and elliptic curve discrete logarithm problem are introduced.
2.1. Communication Model
The communication model of our proposed scheme is shown in Figure 1. It includes three kinds of entities: the gateway node , the user U and the sensor node S. A secure communication channel can be established between U and S. Once the user U intends to request a certain service or access the data via GWN, the authentication session is initiated. U first sends an authentication request the message to which requests for authentication; after checking the validity of messages from U, sends the message to S. When receives the message from , S replies the confirmation message about session key establishment with message to . Then verifies , generates and sends the message including the message to U. At last, after U authenticating and S, U securely establishes a session key with S successfully.
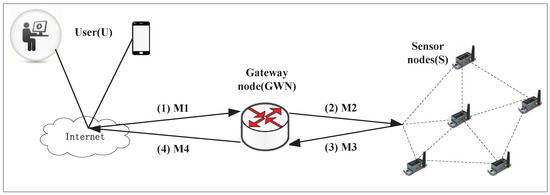
Figure 1.
Communication model of the proposed scheme.
2.2. Security Definition
The secrecy of the session key is the central security goal for authentication and key agreement scheme. To formally prove the security, a game-based method is introduced in our paper based on Abdalla et al.’s [26] method. The security model of our proposed scheme is introduced as follows.
Participants. There are three types of participants: users, gateway nodes and sensor nodes. Let be the instance n of the participants such that , where represent users, gateway nodes and sensor nodes respectively. Let represent the j-th instance of S, denote the i-th instance of U, and represent the k-th instance of G. Any participant instance is assumed as an oracle.
Partnering. Let denote the session identification which is unique for each conversation. If the instances and are called partners, then the following conditions would be satisfied: (1) A same between and is shared; (2) and have accepted the conversation; (3) and are each other’s partners.
Adversary. It is assumed that there exists a probabilistic polynomial-time(PPT) adversary that can fully control all the communications by accessing to a series of oracle queries during the execution of the protocol. All the adversary’s queries are listed as below:
- : This query issued by the adversary simulates the eavesdropping attacks on honest executions among the user instance , trusted gateway instance and sensor instance . It outputs a transcript of the exchanged messages during the honest execution of the protocol.
- : This query models the active attacks such as impersonation attack and replay attack. Once has received the messages, returns a corresponding result to .
- : This query is issued by the adversary , it is used to simulate the attack that corrupts an entity from . can get the private key of a participant with this query.Please note that this query does not corrupt the partner’s same internal data and ephemeral values of the instance .
- : The query is designed to simulate known session key attack. If there is a valid session from the instance , returns the shared session key to . Otherwise, returns null.
- : This query is used to model the capability of the adversary to distinguish between a random number and a real session key by flipping an unbiased coin b. If the session key of the instance has been defined, the session key of will be responded to if or a random value will be returned if ; otherwise, ⊥ will be responded.
- : As soon as the adversary makes query adaptively on the message x, it returns the existing if the list exist a tuple , where initially is an empty set; otherwise, it picks a random value , stores the tuple in the list and returns to .
- : Upon receiving the query about y from the adversary , examines whether the tuple is in , where initially is an empty set. If so, it responds to the existing to ; otherwise, it generates a random value , stores the tuple in the list and returns to .
The adversary could issue any query to the instances after being provided with the above queries. The output of query is relevant to the bit b. At last, outputs a guessing bit about b. is successful if . Let represent the event that succeeds in the game, the advantage of the adversary is defined as follows:
If the advantage is negligible, then we conclude that the proposed scheme is secure.
2.3. Elliptic Curve Discrete Logarithm Problem
Let G be a cyclic additive elliptic curve group with the prime order q and P is a generator of G. Suppose that the multiplication and inversion operation in G can be computed efficiently, the two intractable problems in G are defined as follows:
- Elliptic curve discrete logarithm (ECDL) problem: Given for unknown , to find a.
- Elliptic curve computational Diffie-Hellman (ECCDH) problem: Given P, , for unknown a, , to compute .
3. The Proposed Scheme
In this section, we describe the proposed scheme in detail. It consists of four phases: system set up, user registration, sensor node registration and authentication phase. Table 1 summarizes all the notations used in this paper.

Table 1.
NOTATIONS.
3.1. System Setup Phase
System setup is performed by as follows,
- chooses a non-singular elliptic curve over a prime finite , where p is a large prime. Let G be an elliptic curve group. Then, chooses a generator P of order q over . selects its private key and computes the public key in accordance with .
- selects three collision-resistant one-way hash functions .
- Finally, the system parameters is published while the private key is kept secretly by .
3.2. Registration Phase
A user U registers at the gateway node in line with the requirement, while a regular sensor node S registers at offline. A detailed process of registration process about U and S is highlighted as below.
3.2.1. User Registration Phase
The registration process is between the and U is as follows:
- U selects an identity , a private key and then gets the public key according to . Then, U calculates the registration message , and sends it to via a non-public channel.
- After receiving the registration message from U, calculates and returns it to U via a non-public channel.
- U computes and deletes .
3.2.2. Sensor Node Registration Phase
S proceeds offline registration with the help of as below:
- S generates its identity , private key and computes the corresponding public key and . Then, S sends to GWN via a non-public channel.
- After receiving the message from S, computes and sent it to S. publish and stores into its database.
- Upon receiving from , S stores it into its memory.
3.3. Authentication and Key Agreement Phase
When the user U wants to access the sensor node S, he or she initiates this phase by issuing a request via . This phase enables , U and S to effectively authenticate each other and then establish a session key between U and S. If a session key is negotiated successfully by U and S, then they can exchange private messages with each other via a public channel. A detailed description of the steps of this phase are as follows:
- U selects a random number , generates the current timestamp and computes , , , , , and . Then, U sends the request message via a public channel to GWN.
- When receives the authentication request message from U at the time , it checks whether the condition holds. If yes, then computes: , . then verifies U by computing the following: , , , and . verifies if the equation holds or not. If the verification does not hold, rejects the user’s authentication request; else, goes to 3.
- generates its current timestamp , selects a random number and calculates: , , , . Then, the gateway node sends the message {, , , , , } to S via a public channel.
- Upon receiving the authentication message from at time , S first checks the validity of the timestamp on the condition . If is invalid, S terminates the session. If it is valid, S then computes: , , and . Next, S verifies . If , the sensor node S accepts and goes to 5; otherwise, it rejects .
- S generates its current timestamp and selects a random number , and computes , , , and . S sends the message to via a public channel. Then, S computes the session key .
- Upon receiving the replied message from S at time , checks the validity of on the condition . If is valid, computes and . Then, checks whether . If yes, generates its current timestamp , computes and sends the message to U.
- After receiving the replied message from at time , U checks the validity of with the condition . If it is valid, U computes and checks whether . If yes, U computes , . Then, U checks whether . If yes, U calculates the secret session key .
The process of authentication and key agreement is visually illustrated in Figure 2.

Figure 2.
Authentication and key establishing phase of the proposed scheme.
4. Analysis of Correctness and Security
In this section, the correctness of the proposed scheme is validated using BAN-logic and the security of our scheme is proved under the random oracle model. In addition, some other security features are also discussed in the end.
4.1. Correctness
With the formal validation tool Burrows-Abadi-Needham Logic (BAN-logic) [27], we provide the proof of correctness of the proposed scheme in this section. Let U be the user, S represent the sensor node and denote the gateway node. We demonstrate that a session key can be created successfully after the process of mutual authentication among S and U. Now, the basic notations of BAN-logic are given below:
- : P believes X.
- : P sees X. i.e., P has received messages containing X.
- : P said X. i.e., P has sent messages containing X.
- : P controls X.
- or : X is a fresh message. X is usually a temporary value.
- : The hashed value of X.
- : K is a shared secret key between P and Q.
- : X is combined with secret Y.
- : X or Y is one part of .
Some logic postulates of BAN-logic are described as follows:
- Message-meaning rule: orIf P believes that K is a shared secret key between P and Q and has received messages containing X, P believes that Q has sent messages containing the message X.
- Nonce-verification rule: orIf P believes that X is a fresh message and Q has sent messages containing the message X, P believes that Q believes the message X.
- Jurisdiction rule: orIf P believes that Q controls the message X and Q believes the message X, P believes the message X.
- Freshness rule: orIf P believes that X is a fresh message, P believes is fresh messages.
- Belief rule: orIf P believes the messages , P believes the message X.
Our proposed scheme can realize the establishment of a secret session key between U and S, and the following goals can be achieved after the protocol execution.
- Goal 1:
- Goal 2:
The exchange of messages during the authentication phase is depicted as follows:
- Message 1: :
- Message 2: :
- Message 3: :
- Message 4: :
To proceed the derivation, the initial state assumptions are set as A1–A9:
- A1:
- A2:
- A3:
- A4:
- A5:
- A6:
- A7:
- A8: .
- A9: .
U and S intend to share a session key to achieve confidential communication. As stated above, the mutual authentication between U and S shows that 1 and 2 can be achieved in the end. The result is proved as follows:
- From Message 1, we have:S has received the message encrypted by .
- According to the message-meaning rule, if the Formula (1) and the state assumption A4 hold at the same time, we can infer that:S believes that has sent the messages .
- According to the freshness rule, if the state assumption A1 holds, we then obtain:S believes the message are fresh.
- According to the belief rule, if the Formula (4) holds, we can get:S believes that believes is a shared secret key between and S.
- According to the jurisdiction rule, if the Formula (5) and the state assumption A6 hold at the same time, we can obtain:S believes that is a shared secret key between and S.
- From Message 2, we can have:S has received the message encrypted by .
- According to the freshness rule, if the state assumption A2 holds, we can deduce:S believes the messages are fresh.
- According to the belief rule, if the Formula (10) holds, we can obtain:S believes that believes is a shared secret key between U and S.
- According to the jurisdiction rule, if the Formula (11) and the state assumption A7 hold at the same time, we can have:S believes that is a shared secret key between U and S.
- From Message 3, we can get:U has received the message encrypted by .
- According to the message-meaning rule, if the Formula (14) and the state assumption A5 hold at the same time, we can deduce:U believes that has sent the message .
- According to the freshness rule, if the state assumption A3 holds, we can have:U believes the message are fresh.
- According to the belief rule, if the Formula (17) holds, we can infer:U believes that believes is a shared secret key between U and .
- According to the jurisdiction rule, if the Formula (18) and the state assumption A8 hold at the same time, we can deduce:U believes that is a shared secret key between U and .
- From Message 4, we can get:which means that U has received the message encrypted by .
- According to the freshness rule, if the state assumption A3 holds, we can have:which means that U believes the message are fresh.
- According to the belief rule, if the Formula (23) holds, we can infer:U believes that believes is a shared secret key between U and S.
- According to the jurisdiction rule, if the Formula (24) and the state assumption A9 hold at the same time, we can deduce:U believes that is a shared secret key between U and S.
- According to the belief rule, if the Formula (25) holds, we can have:U believes that is a shared secret key between U and S.
At this point, it can be seen that and have been achieved, which means that the proposed scheme is correct and feasible.
4.2. Security
We first demonstrate that our proposed scheme possesses semantic security under the random oracle model.
Theorem 1.
Let denote an adversary within a polynomial time t against the proposed protocol under the random oracle model, then we have:
where is the advantage of breaks the ECCDH problem; , , , represent the number of , , and queries respectively; , denote the range space of and function respectively.
Proof.
Let represent the event that wins in the game , i.e., guesses bit b, where .
Game: In , a real attack against our proposed scheme from is simulated. Firstly, the value of b is selected randomly. According to the above definitions, we obtain:
Game: To increase the probability that wins game, the query is used to model the eavesdropping attacks. Since its goal is to get some information about , has to compute or according to the definition of the proposed scheme; however, , where , are unknown. Without corrupting the gateway node to get , the probability of success would not be increased just by eavesdropping the transmitted messages, which implies that
Game: The game is transferred from is used to simulate active attacks by adding , and oracles in which tries to forge messages. By arbitrarily issuing queries to , , attempts to capture collisions. The probability of collisions is at most according to the birthday paradox. The probability of collisions in the transcripts is at most . Therefore, we get:
Game: models the attack that the the gateway node has been corrupted. By issuing oracles, can get the long-term key of . According to the definition, the common secret value or are the core of the session key . Considering the following fact,
Thus, can use the long-term key to compute partial value from transcripts. The probability of success of between and would not be greater than the advantage of solving ECCDH problem instance. Let be the advantage that the adversary solves ECCDH problem instance within t in this game. Hence, we get
To win the game , has no choice but guess the bit b, which leads to the following result
From (27), we have . Hence,
□
4.3. Deniable Authentication
In our proposed scheme, the polynomial time deniability means that the gateway node as a receiver can simulate the messages sent by the user which are indistinguishable for any third party. The concrete simulation process of is as follows:
- selects a random number , computes and .
- chooses a user pseudo-identity and a public key, computes , and .
sends to the third party. After receiving the message, the third party cannot get any information related to the user by . In addition, can be calculated by the user or the gateway. Hence, the third party is unable to determine the true source of the message. Therefore, our proposed scheme achieves deniable authentication.
4.4. Anonymity
Since the transmitted authentication messages are carried via a public channel, an outside adversary can easily eavesdrop the communication. However, our proposed scheme can preserve the anonymity of the user. Suppose that an adversary intercepts during the authentication phase and attempts to reveal some information about the user’s identity. obtains , , which . Due to the utilization of random number and one-way hash function, cannot calculate and get . Since the use of the timestamps and random numbers, those intercepted messages by are unique and dynamic for each authentication between U, S and . Therefore, the proposed scheme ensures user anonymity.
4.5. Mutual Authentication
With the received request message U sent, can compute to get the values and and checks the validity of U via the equivalence . After receiving the message {, , , , , } from , the sensor node S could obtain the values and and then computes to verify the validity of via the equivalence . Once receiving the message from S, computes and to check the validity of S via the equivalence . Then, sends message {, , , , } to U and U computes , and and checks the validity of and S by the equivalence and . If the above verification processes are successfully completed, our protocol provides mutual authentication.
4.6. Unlinkability
In our proposed scheme, the real identities or related information of all participants are not sent in plaintext over the insecure network because each transmitted message contains timestamps, random values and one-way hash function values. An outside adversary cannot determine whether two or more authentication messages come from the same participant. Therefore, the transmitted messages cannot be linked by the adversary.
4.7. Traceability
In our proposed scheme, given a disputed message , only the trusted gateway node() can reveal the identity of the user. With above message, computes and to get the user’s identity . In addition, the tracing process does not need real user to participate because the message sent by the user contains sufficient information to derive the user identity. Therefore, our proposed scheme achieves traceability.
4.8. Resistance to Impersonation Attack
Assume an adversary intercepts message to impersonate a user, where , , , . By following the authentication process, the adversary produces a timestamp and a value randomly to get , and . However, is unable to successfully compute because he or she does not has the user’s real identity and private key . Hence, our scheme can resist such attacks according to the above analysis.
4.9. Resistance to Replay Attack
Suppose an adversary intercepts all transmitted messages between participants and then attempts to replay some or all of them. In our scheme, however, timestamps and random numbers are integrated into the generation of the messages for U, , S, thus the freshness of messages is well preserved. Therefore, the proposed protocol can resist replay attacks.
4.10. Forward Security
Assume an adversary could get the private keys of all participants, i.e., , , . Even if the adversary had obtained the current session key , he or she cannot derive the previous session key. However, due to , where and are chosen randomly by U and S respectively. can never obtain the previous session key since the difficulty of the ECCDH problem. So, our proposed scheme achieves forward security.
5. Performance Comparison
In this section, we evaluate the performance of our scheme regarding the computational cost in the authentication phase. Moreover, we present the comparison between the proposed scheme and some existing similar schemes [15,16,21,23,24,25]. For convenience, we use the symbols in Table 2 to denote the computational cost regarding hash operation, ECC-based operation and bilinear paring operation and the approximate running time required of various operations is presented in Table 2.

Table 2.
Approximate running time of operations.
Please note that we only consider the operations listed in Table 2 since the running time of addition operation and XoR operation is ignorable. To fairly compare the computational time cost of these similar protocols. The experiments use OpenSSL and JPBC cryptographic libraries, and then are programmed with Visual C language.
Table 3 and Figure 3 presents the comparisons among the other protocols [15,16,21,23,24,25] and ours. Table 4 presents the comparison of security properties between ours and the above protocols. According to the experimental results, it is observed that our scheme costs 3.791 ms, which is better than [15,16,24,25]. We sort the time consumption on the operations as below: . The hash function spends the least time, while the bilinear pairing operation takes the more time. To fully demonstrate the proposed scheme’s advantage, we define , where denotes computational cost of the other schemes and represents computational cost of ours, as the improved ratio of ours compared with others [15,16,24,25]. Hence, the improved ratios of the proposed scheme compared with [15,16,24,25] are , , and respectively.

Table 3.
Comparison of computational cost.
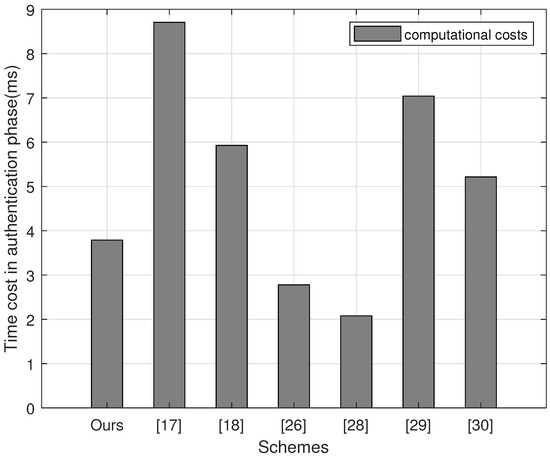
Figure 3.
Computational costs of different authentication schemes.

Table 4.
The comparison of security features.
Compared to Porambage’s scheme [23] and Wang’s scheme [21], our scheme requires more communication overheads from Table 3 and Figure 3. However, from Table 4 our scheme possesses more desirable security compared with the existing schemes. However, Porambage’s scheme cannot protect against the replay attack and provide the user’s anonymity. In addition, the user’s anonymity can be violated. Wang’s scheme [21] is prone to client impersonation attacks. Specifically, an adversary is able to masquerade as a legitimate client to be authenticated by application provider. Therefore, our proposed scheme provides a better secure communication and higher efficiency than the compared existing schemes in IoT.
6. Conclusions
With the evolution of the Internet of Things, its security is currently drawing wide attention. The privacy protection in communication is a major concern for people. In this article, we proposed an anonymous authentication and key agreement protocol with deniability property using elliptic curve. In our proposed scheme, other participants except the trusted gateway node can obtain nothing regarding the real identity of a user. We have demonstrated that our proposed scheme posses more appropriate security features than similar schemes, which are shown in the BAN logic-based proof and random oracle model-based proof. In addition, we have provided informal analysis to further confirm that our scheme can resist various attacks. By experimental evaluation, we demonstrate that the proposed scheme is efficient according to the comparison on computational costs against other similar protocols. In view of the advantages in security and performance, our proposed scheme is more suitable for IoT systems.
From the analysis, the computational overhead of our proposed scheme become relatively low. Therefore, we aim to achieve a better trade-off among security and efficiency in designing authentication protocols for IoT applications in our future work, so as to meet the requirements of low-cost computation and communication of resource-constrained sensors.
Author Contributions
Y.Z. and T.L. conceived and designed the experiments and wrote the paper; F.T. and F.W. designed the experiments; M.T. performed the experiments.
Acknowledgments
This work was supported in part by the Venture and Innovation Support Program for Chongqing Overseas Returnees under Grant CX2018122, and in part by the National Natural Science Foundation of China under Grant 61702067.
Conflicts of Interest
The authors declare that there is no conflict of interest regarding the publication of this paper.
References
- Sundmaeker, H.; Guillemin, P.; Friess, P. Vision and challenges for realising the Internet of Things. Clust. Eur. Res. Proj. Internet Things Eur. Commis. 2010, 3, 34–36. [Google Scholar] [CrossRef]
- Lo, N.W.; Tsai, J.L. An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks without pairings. IEEE Trans. Intell. Transp. Syst. 2016, 17, 1319–1328. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chen, J. Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimed. Syst. 2015, 21, 49–60. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Liao, J.; Liang, W.; Khan, M.K. A new authentication protocol for healthcare applications using wireless medical sensor networks with user anonymity. Secur. Commun. Netw. 2016, 9, 2643–2655. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S. An improved and anonymous two-factor authentication protocol for health-care applications with wireless medical sensor networks. Multimed. Syst. 2017, 23, 195–205. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chilamkurti, N. A secure temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. Int. Symp. Wirel. Pervasive Comput. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- Castiglione, A.; Santis, A.D.; Castiglione, A.; Palmieri, F. An Efficient and Transparent One-Time Authentication Protocol with Non-interactive Key Scheduling and Update. In Proceedings of the 2014 IEEE 28th International Conference on Advanced Information Networking and Applications, Gwangju, Korea, 25–27 March 2014; pp. 351–358. [Google Scholar] [CrossRef]
- Gupta, A.; Tripathi, M. A lightweight Mutually Authenticated Key-Agreement scheme for Wireless Body Area Networks in Internet of Things Environment. Radio Freq. Identif. IoT Secur. 2018, 804–806. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Sangaiah, A.K.; Choo, K.-K.R. A three-factor anonymous authentication scheme for wireless sensor networks in internet of things environments. J. Netw. Comput. Appl. 2018, 103, 194–204. [Google Scholar] [CrossRef]
- Wong, K.H.M.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC’06), Taichung, Taiwan, 5–7 June 2006; Volume 1, p. 8. [Google Scholar] [CrossRef]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 17, 1086–1090. [Google Scholar] [CrossRef]
- Khan, M.K.; Alghathbar, K. Cryptanalysis and Security Improvements of ‘Two-Factor User Authentication in Wireless Sensor Networks’. Sensors 2010, 10, 2450–2459. [Google Scholar] [CrossRef]
- Chen, T.-H.; Shih, W.-K. A Robust Mutual Authentication Protocol for Wireless Sensor Networks. ETRI J. 2010, 32, 704–712. [Google Scholar] [CrossRef]
- He, D.; Gao, Y.; Chan, S. An Enhanced Two-factor User Authentication Scheme in Wireless Sensor Networks. Ad Hoc Wirel. Netw. 2010, 10, 361–371. [Google Scholar]
- Holbl, M.; Welzer, T.; Brumen, B. Two proposed identity-based three-party authenticated key agreement protocols from pairings. Comput. Secur. 2010, 29, 244–252. [Google Scholar] [CrossRef]
- Holbl, M.; Welzer, T.; Brumen, B. An improved two-party identity-based authenticated key agreement protocol using pairings. J. Comput. Syst. Sci. 2012, 78, 233–271. [Google Scholar] [CrossRef]
- Jung, J.; Kim, J.; Choi, Y. An Anonymous User Authentication and Key Agreement Scheme Based on a Symmetric Cryptosystem in Wireless Sensor Networks. Sensors 2016, 16, 1299. [Google Scholar] [CrossRef] [PubMed]
- Xue, K.; Ma, C.; Hong, P. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Lu, X. An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-Peer Netw. Appl. 2015, 8, 1070–1081. [Google Scholar] [CrossRef]
- Das, A.K. A secure and robust temporal credential-based three-factor user authentication scheme for wireless sensor networks. Peer-to-Peer Netw. Appl. 2016, 9, 223–244. [Google Scholar] [CrossRef]
- Wang, C.; Zhang, Y. New Authentication Scheme for Wireless Body Area Networks Using the Bilinear Pairing. J. Med. Syst. 2015, 39, 136. [Google Scholar] [CrossRef] [PubMed]
- Tong, L.; Yuhui, Z.; Ti, Z. Efficient Anonymous Authenticated Key Agreement Scheme for Wireless Body Area Networks. Secur. Commun. Netw. 2017, 2017. [Google Scholar] [CrossRef]
- Porambage, P.; Braeken, A.; Schmitt, C. Group Key Establishment for Enabling Secure Multicast Communication in Wireless Sensor Networks Deployed for IoT Applications. IEEE Access 2015, 3, 1503–1511. [Google Scholar] [CrossRef]
- Xiong, H.; Qin, Z. Revocable and Scalable Certificateless Remote Authentication Protocol with Anonymity for Wireless Body Area Networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1442–1455. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, Z.; Chen, X.; Kwak, K.S. Certificateless Remote Anonymous Authentication Schemes for WirelessBody Area Networks. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 332–342. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.-A.; Pointcheval, D. Password-Based Authenticated Key Exchange in the Three-Party Setting; Springer: Berlin/Heidelberg, Germany, 2015; pp. 65–84. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. R. Soc. 1989, 426, 233–271. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).