Reducing Unnecessary Alerts in Pedestrian Protection Systems Based on P2V Communications
Abstract
1. Introduction
2. State of the Art
3. Algorithms for a Communication-Based Warning System to Protect Pedestrians
3.1. The Warning System
3.2. The Algorithms to Decide When Alerts are Active
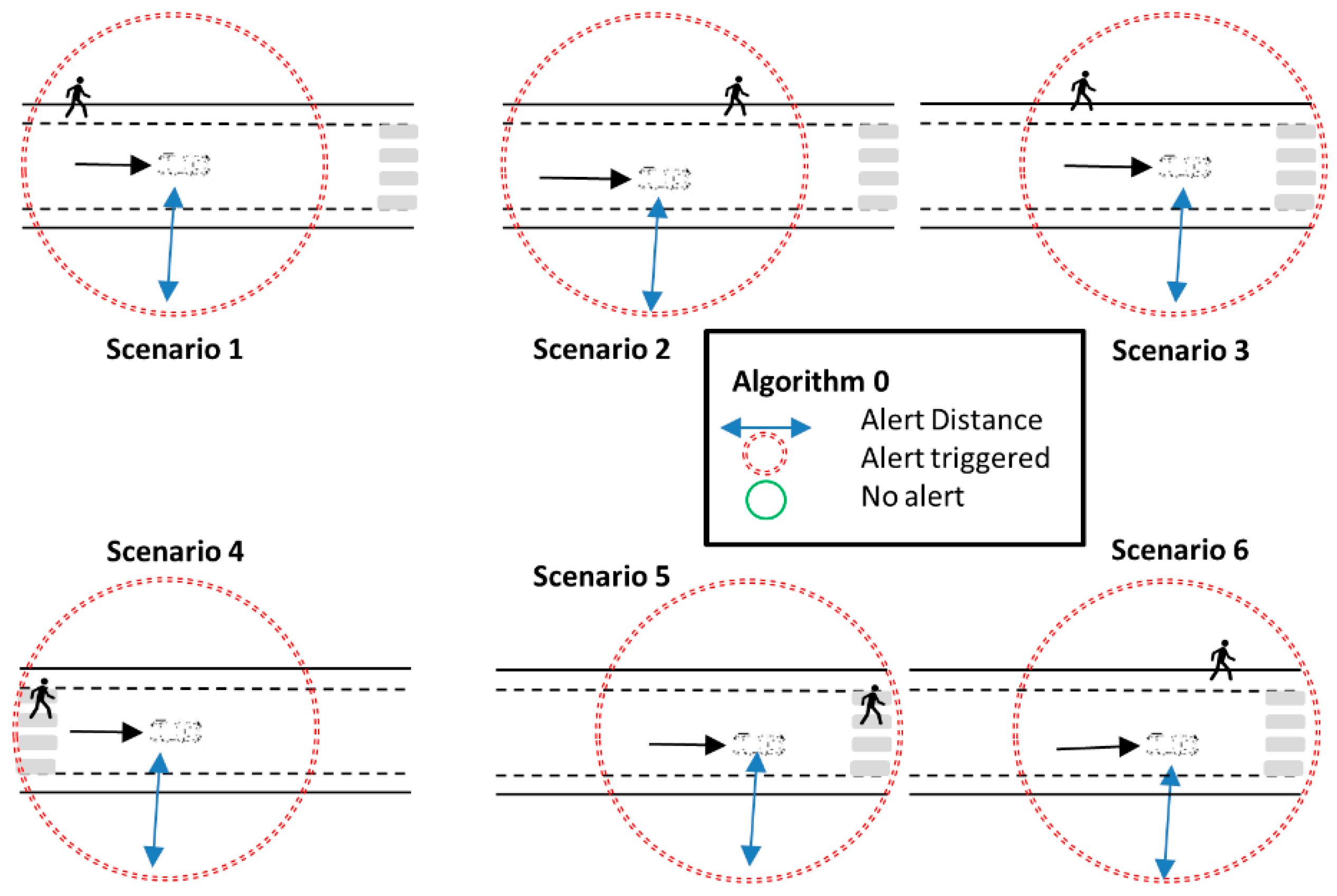
- Algorithm 0: This is the simplest approach. If a vehicle detects a pedestrian at a distance that is below a threshold, an alert is triggered for that pedestrian. The threshold is called alert distance threshold (, and is a configurable parameter in the algorithm: a larger threshold means more time to react but also more and longer alerts. The behavior of Algorithm 0 is presented in Figure 1. In this figure, and the following, several example scenarios are shown, and those in which an alert is active are highlighted with a red circle, while those that do not activate an alert have a green circle. Note that Algorithm 0 is very simple and robust. It does not need to worry about the course of the vehicle, for example, as it only depends on the distance between pedestrians and vehicles. On the other hand, Algorithm 0 can be expected to create many unnecessary alerts that distract the drivers. Therefore, Algorithm 0 is intended as a baseline performance reference for our work.
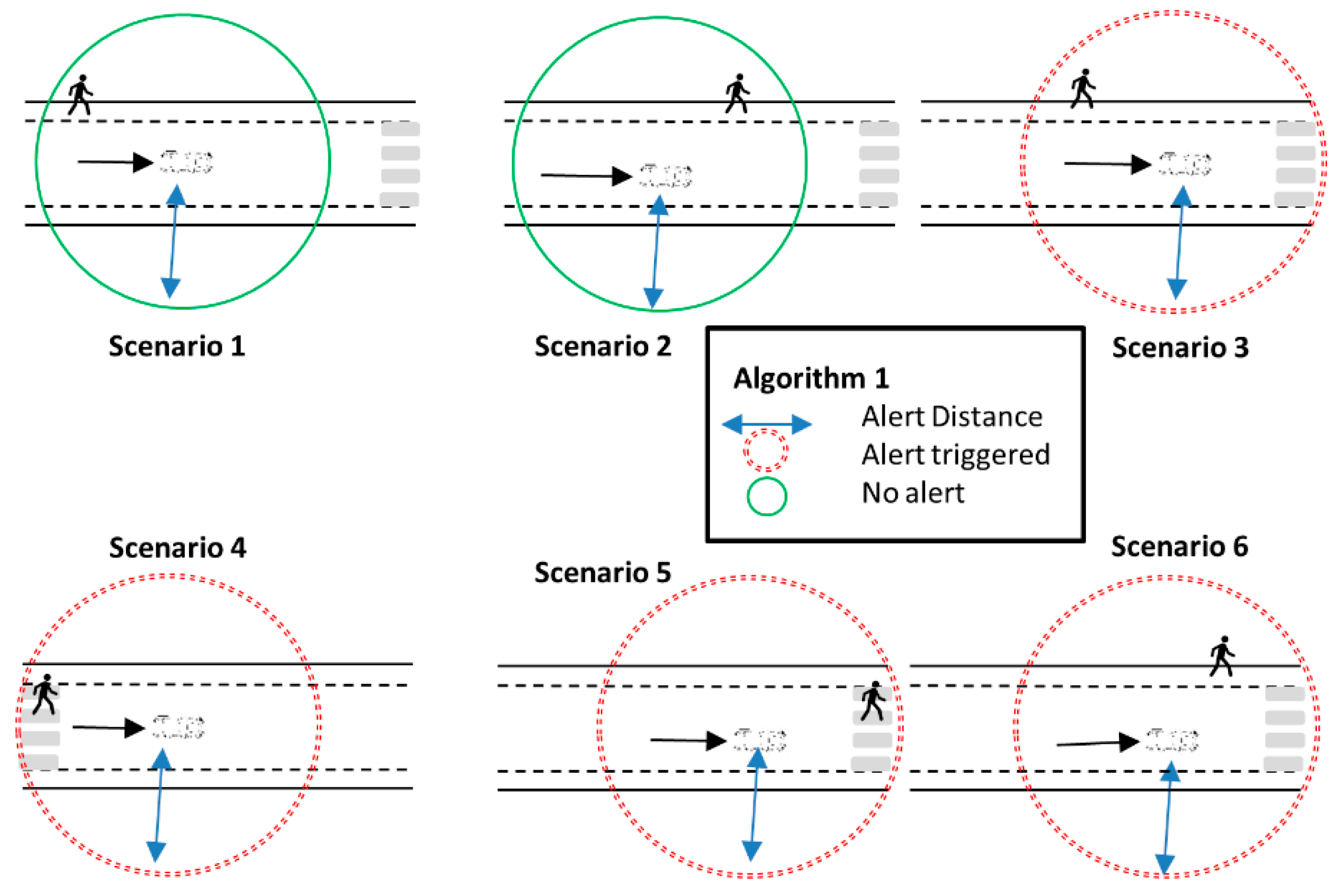
- Algorithm 1 (Figure 2): We add a restriction to Algorithm 0. In this case, an alert is triggered if the conditions of Algorithm 0 are met, but also the vehicle is close to a crossing. Therefore, an alert is active when a vehicle is close to a crossing and the distance between the vehicle and the pedestrian is below . The vehicle is considered close to a crossing using the same threshold as the one used to activate the alerts (). The reason for this is that in both cases the requirement is that a driver must be able to brake before traveling that distance.
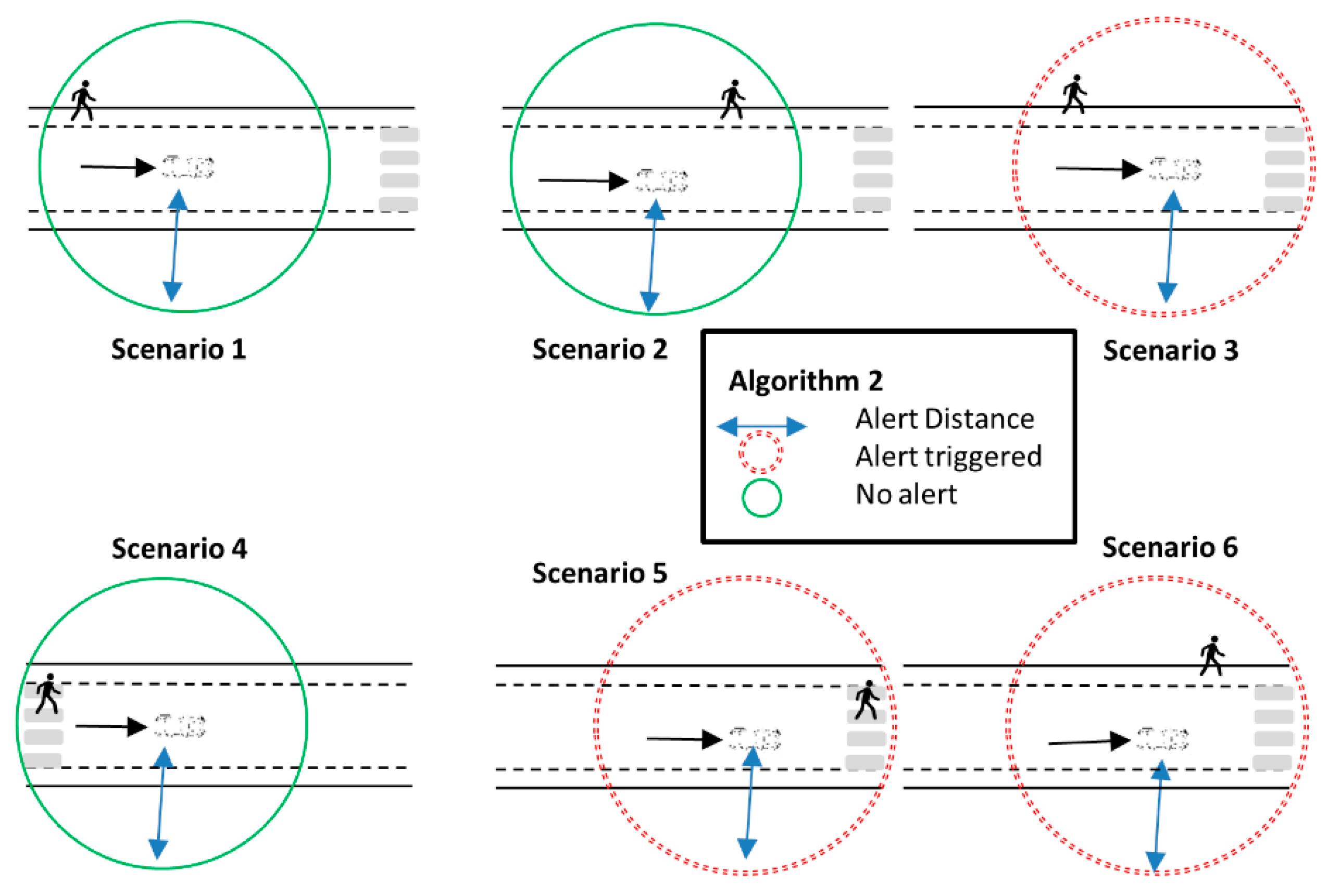
- Algorithm 2 (Figure 3): We add a new restriction to Algorithm 1. To trigger an alert, the vehicle not only has to be close to a crossing, the crossing must be in front of the vehicle. The crossing is considered in front of the vehicle if the crossing is located at an angle of ±90° around the direction of movement of the vehicle.
- Algorithm 3 (Figure 4): We add a new restriction to Algorithm 2. To trigger an alert, the pedestrian that causes the alert must be in front of the vehicle and near the crossing. Therefore, an alert, associated with a pedestrian, is active when the vehicle is close to a crossing, the pedestrian is close to the same crossing, the pedestrian and the crossing are in front of the vehicle, and the distance between the vehicle and the pedestrian is below . The pedestrian is close to the crossing using a threshold that we call pedestrian safety threshold ).
3.3. Configuration of the Algorithms
3.3.1. Alert Distance Threshold
3.3.2. Pedestrian Safety Threshold
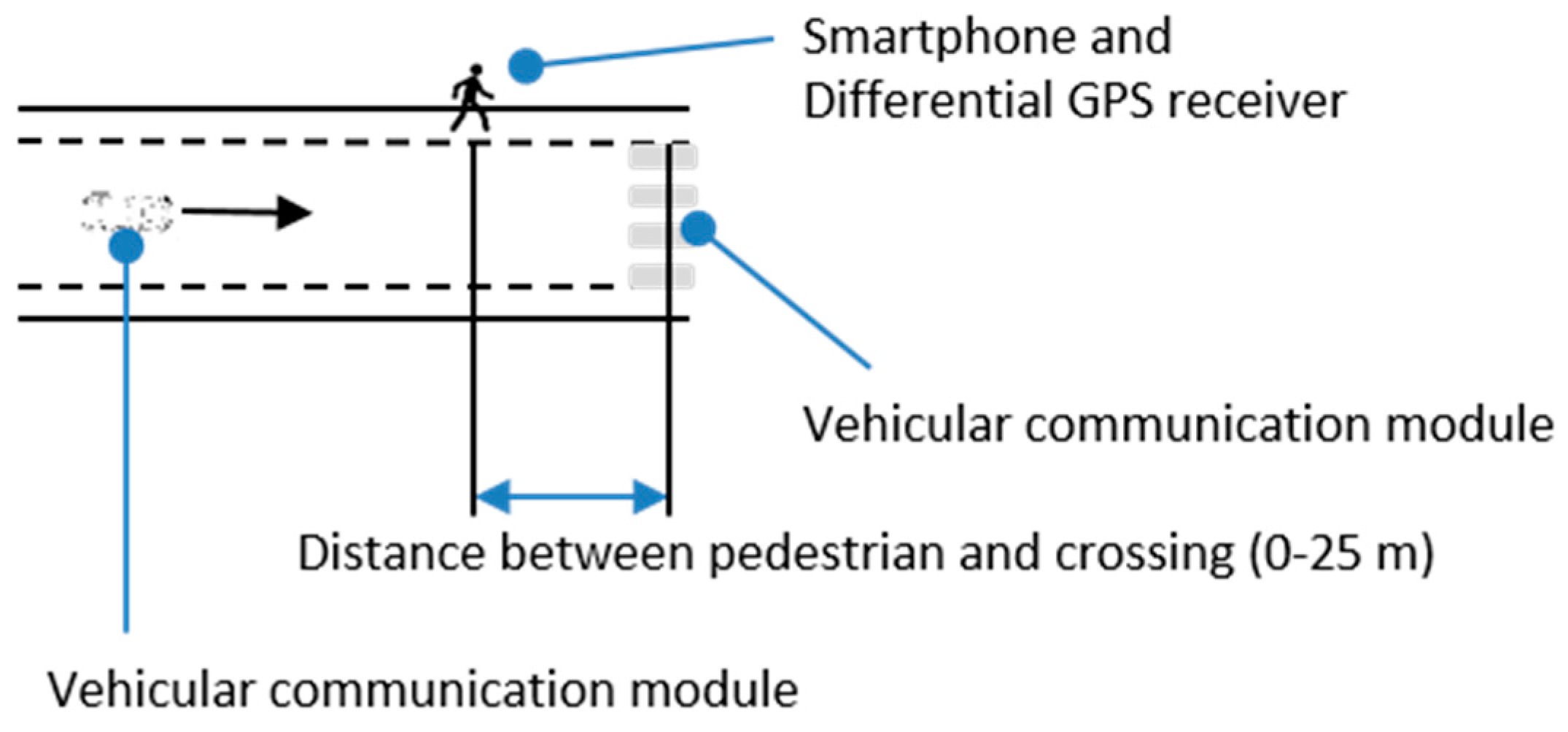
4. Evaluation of the Feasibility of the Defined Alerts
- Vehicular communication modules. These modules were based on an AR9220 chipset that uses the ath9k modified driver to allow the 802.11p bands. The operating system that incorporated the modules was a Debian wheezy with a 3.19.0 kernel version. The kernel was configured to allow OCB (Outside the Context of a BSS) mode in the ath9k driver. This module also acts as a Wi-Fi router, which enables a 2.4 GHz network with neighboring devices (we used this communication functionality in our experiments). Finally, the module included the Global Navigation Satellite System NV08C-CSM chipset (NVC). It is an integrated GLONASS + GPS + GALILEO + SBAS satellite navigation receiver for use in various applications that demand low cost, low power consumption and uncompromised performance. One module was installed in the vehicle while another module was used to identify the position of the pedestrian crossing.
- Motorola Nexus 6 smartphone. This phone was used to position the pedestrian and send this information to the vehicle. In particular, pedestrians used the smartphone to become part of the V2X environment. The smartphone oversaw the execution of two actions. On the one hand, it used its geo-position libraries to calculate its geographical coordinates. On the other hand, the smartphone connected automatically to the Wi-Fi network of the vehicle V2X on-board unit (OBU) when the phone was within its range of coverage. An ad-hoc application installed in the smartphone retrieved the position and sent it (in a custom message) to the vehicle (the OBU). In the vehicle, the pedestrian was added to the list of elements that navigates in the surroundings, and the pedestrian protection algorithms were applied.
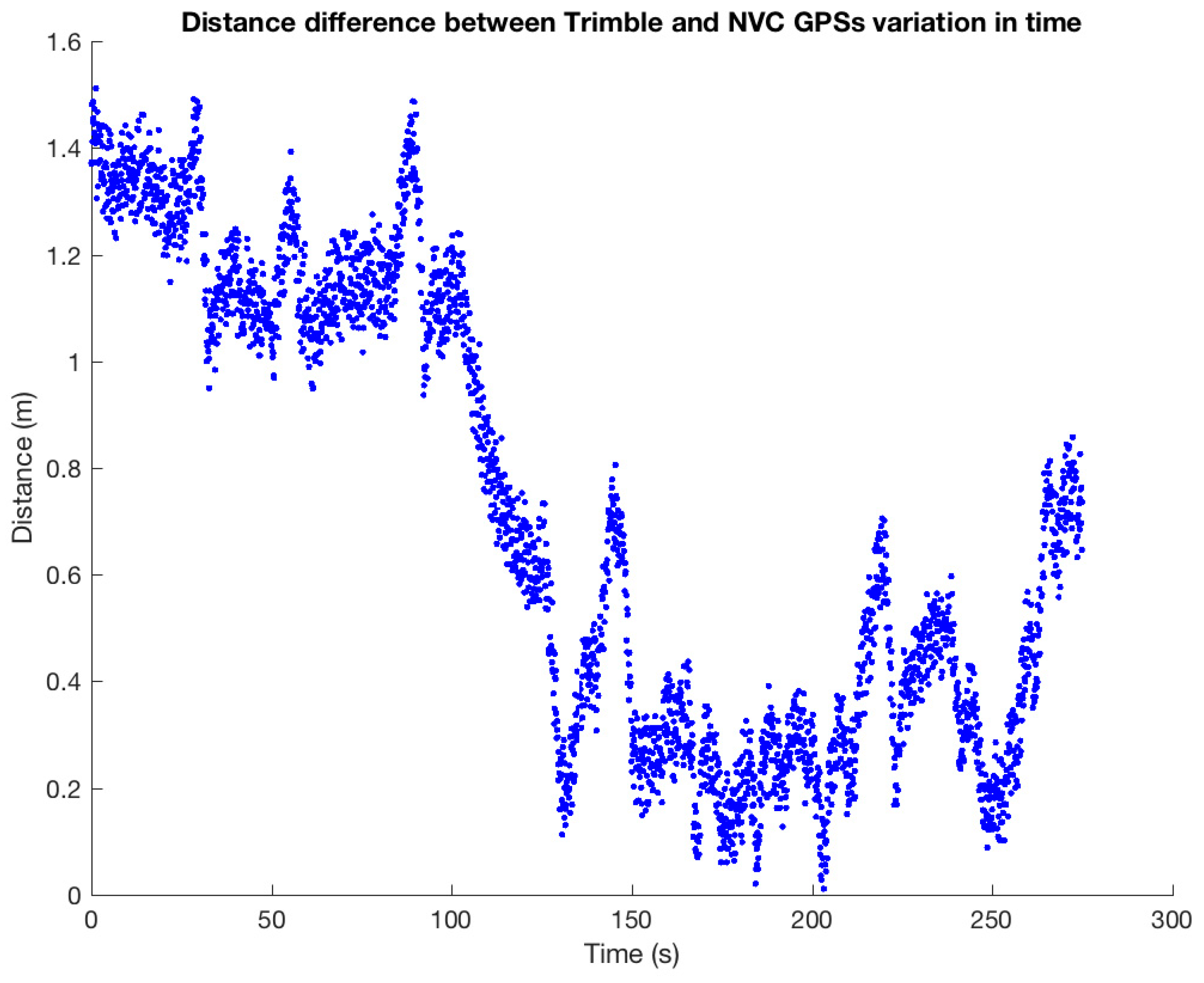
- Trimble® R4 DGPS receiver provided an update rate of 10 Hz and worked with differential correction via GPRS. Differential correction was performed by software NTRIP Client 2.0 and connected to a server of differential correction NTRIP (Networked Transport of RTCM via Internet Protocol) via a smartphone connection and Bluetooth GPS equipment. Given its high accuracy, this equipment was used for the validation of the positions in the preliminary calibration studies and during the tests to assess those cases in which the positioning errors could imply errors in the warnings (false positives or false negatives).
- Estimation of positioning errors (in static and dynamic conditions)
- Tests for the analysis of the warning system
4.1. Positioning Errors Estimation
4.2. Warning System Analysis
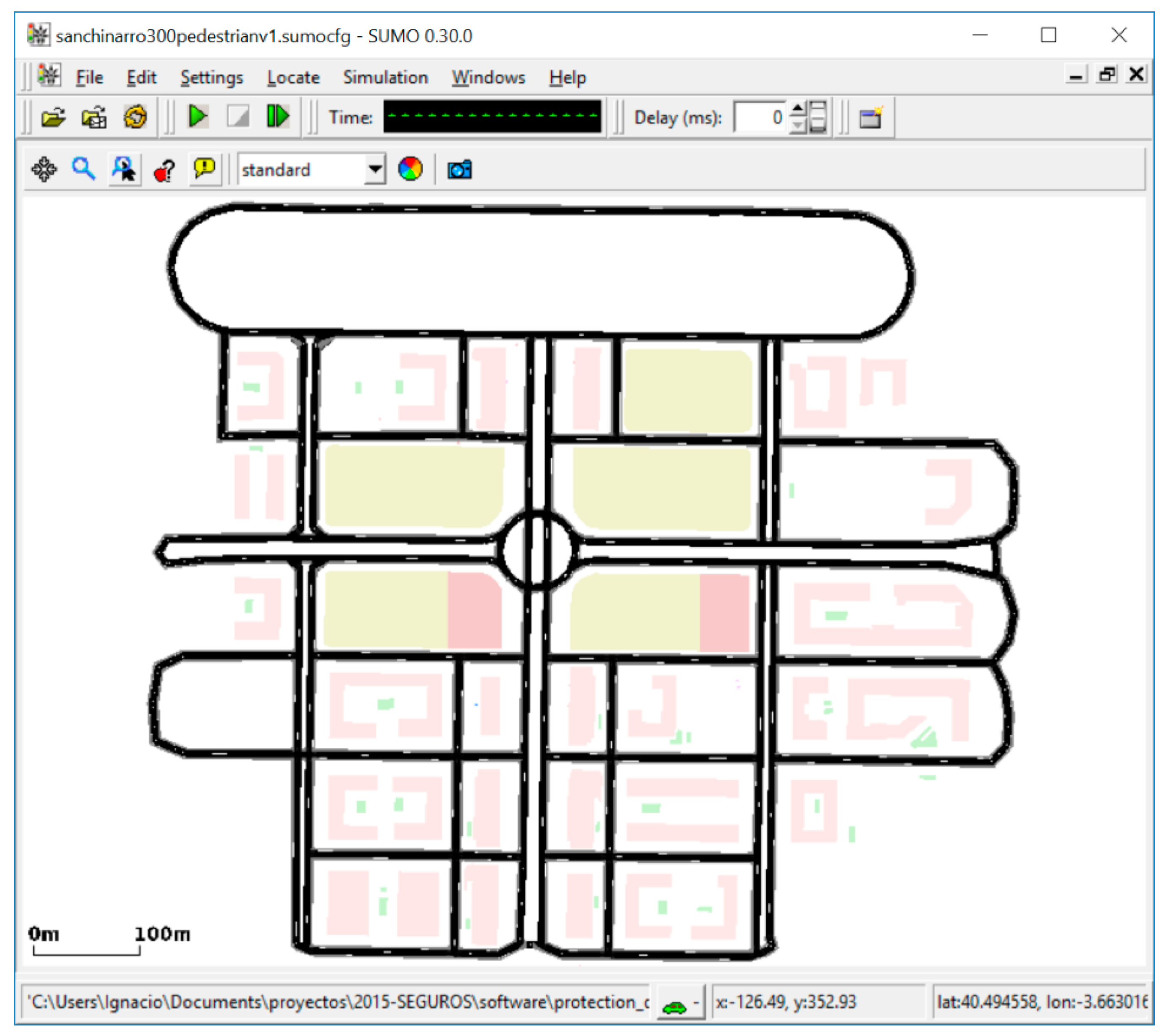
5. Evaluation of the Behavior of the Algorithms Using Simulation
5.1. Simulation Tool
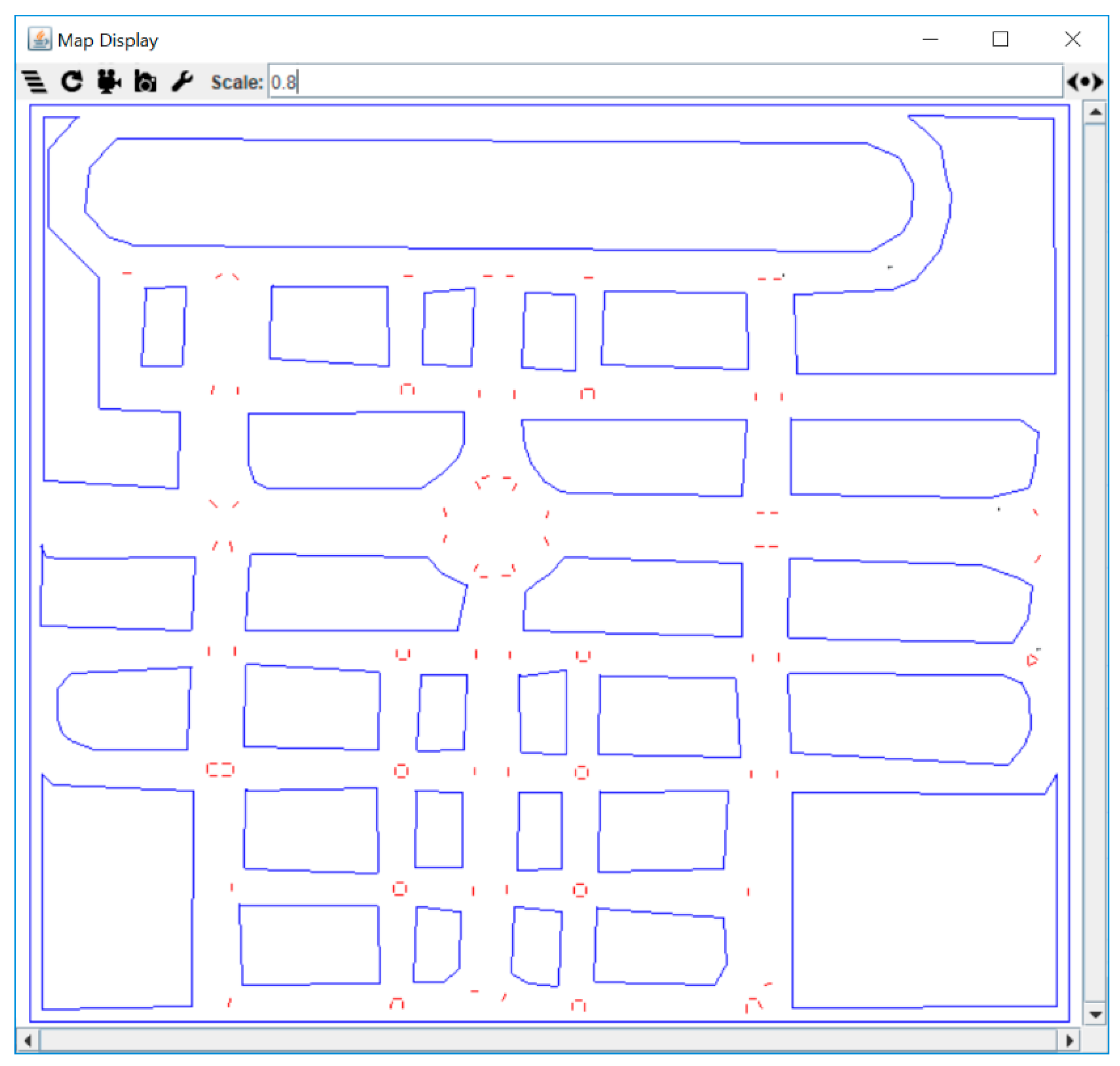
5.2. Urban Area Map
5.3. Traffic Conditions
5.4. Beacon System
5.5. Configuration of the Simulations
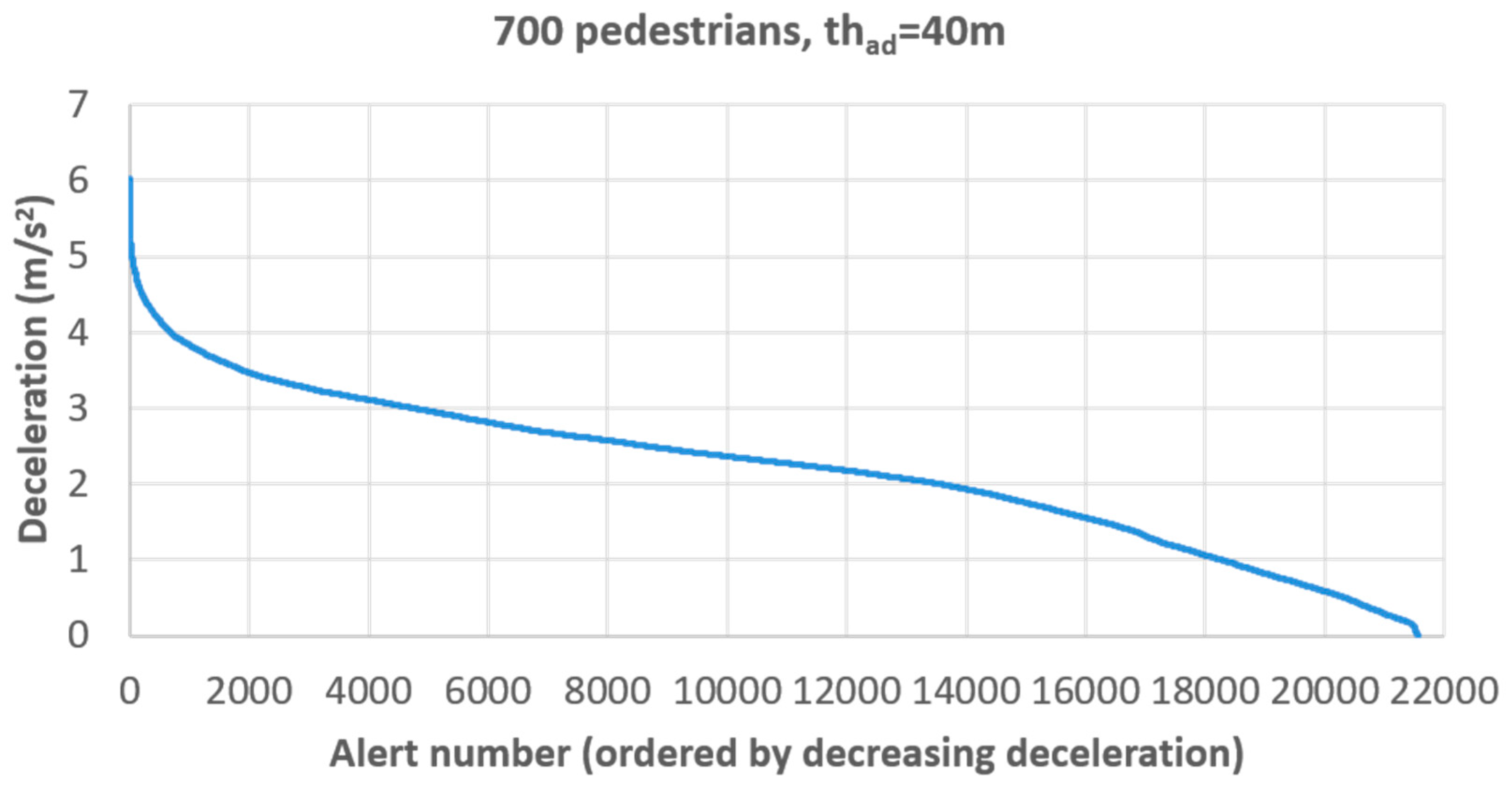
5.6. Simulation Results
5.7. Discussion
6. Conclusions
Supplementary Materials
Author Contributions
Funding
Conflicts of Interest
References
- Traffic Safety Basic Facts on Main Figures; European Commission, Directorate General for Transport: Brussels, Belgium, June 2017.
- Fua, T.; Miranda-Moreno, L.; Saunierb, N. A novel framework to evaluate pedestrian safety at non-signalized locations. Accid. Anal. Prev. 2018, 111, 23–33. [Google Scholar] [CrossRef]
- Soilán, M.; Riveiro, B.; Sánchez-Rodríguez, A.; Arias, P. Safety assessment on pedestrian crossing environments using MLS data. Accid. Anal. Prev. 2018, 111, 328–337. [Google Scholar] [CrossRef]
- Broggi, A.; Cattani, S.; Porta, P.P.; Zani, P. A laser scanner–vision fusion system implemented on the TerraMax autonomous vehicle. In Proceedings of the IEEE/RSJ International Conference on Intelligent Robots and Systems, Beijing, China, 9–15 October 2006; pp. 111–116. [Google Scholar]
- Fuerstenberg, K.C.; Roessler, B. Results of the EC-project INTERSAFE. In Proceedings of the International Conference on Advanced Microsystems for Automotive Applications, Berlin, Germany, 11–12 March 2008. [Google Scholar]
- Widmann, G.; Daniels, M.K.; Hamilton, L.; Humm, L.; Riley, B.; Schiffmann, J.K.; Schnelker, D.E.; Wishon, W.H. Comparison of lidar-based and radar based adaptive cruise control systems. In Proceedings of the SAE World Congress, Detroit, MI, USA, 6–9 March 2000. [Google Scholar]
- Jiménez, F.; Naranjo, J.E. Improving the obstacle detection and identification algorithms of a laser scanner-based collision avoidance system. Transp. Res. Part C Emerg. Technol. 2011, 19, 658–672. [Google Scholar] [CrossRef]
- Shimonura, N.; Fujimoto, K.; Oki, T.; Muro, H. An algorithm for distinguishing the types of objects on the road using laser radar and vision. IEEE Trans. Intell. Transp. Syst. 2002, 3, 189–195. [Google Scholar] [CrossRef]
- Zhao, G.; Xiao, X.; Yuan, J.; Wah, G. Fusion of 3D-LIDAR and camera data for scene parsing. J. Vis. Commun. Image Represent. 2014, 25, 165–183. [Google Scholar] [CrossRef]
- Gaikwad, V.; Lokhande, S. Vision based pedestrian detection for advanced driver assistance. Procedia Comput. Sci. 2015, 46, 321–328. [Google Scholar] [CrossRef]
- Matsumi, R.; Raksincharoensak, P.; Nagai, M. Autonomous Braking Control System for Pedestrian Collision Avoidance by Using Potential Field. In Proceedings of the 7th IFAC Symposium on Advances in Automotive Control, Tokyo, Japan, 4–9 September 2013. [Google Scholar]
- Wang, H.; Wang, B.; Liu, B.; Meng, X.; Yanga, G. Pedestrian recognition and tracking using 3D LiDAR for autonomous vehicle. Robot. Auton. Syst. 2017, 88, 71–78. [Google Scholar] [CrossRef]
- García, F.; García, J.; Ponz, A.; de la Escalera, A.; Armingol, J.M. Context aided pedestrian detection for danger estimation based on laser scanner and computer vision. Expert Syst. Appl. 2014, 41, 6646–6661. [Google Scholar] [CrossRef]
- Aparicio, A.; Cieslik, I.; Stoll, J.; Kunert, M.; Flohr, F.; Arbitmann, M.; Wimmer, T.; Bräutigan, J.; Gavrila, D. Advancing active safety towards the protection of Vulnerable Road Users by evolution of ADAS solutions that meet real-world deployment challenges: The project PROSPECT. In Proceedings of the 7th Transport Research Arena TRA, Vienna, Austria, 16–19 April 2018. [Google Scholar]
- Jiménez, F. (Ed.) Intelligent Road Vehicles: Enabling Technologies and Future Developments; Elsevier: Amsterdam, The Netherlands, 2017. [Google Scholar]
- Moreno, A.; Osaba, E.; Onieva, E.; Perallos, A.; Iovino, G.; Fernández, P. Design and Field Experimentation of a Cooperative ITS Architecture Based on Distributed RSUs. Sensors 2016, 16, 1147. [Google Scholar] [CrossRef] [PubMed]
- Sam, D.; Velanganni, C.; Evangelin, T.E. A vehicle control system using a time synchronized Hybrid VANET to reduce road accidents caused by human error. Veh. Commun. 2016, 6, 17–28. [Google Scholar] [CrossRef]
- Rostami, A.; Cheng, B.; Lu, H.; Gruteser, M.; Kenney, J.B. Reducing Unnecessary Pedestrian-to-Vehicle Transmissions Using a Contextual Policy. In Proceedings of the 2nd ACM International Workshop on Smart, Autonomous, and Connected Vehicular Systems and Services, Snowbird, UT, USA, 16 October 2017; pp. 3–10. [Google Scholar]
- Satish, C. Inter Vehicular Communication for Collision Avoidance Using Wi-Fi Direct. Master’s Thesis, Rochester Institute of Technology, Rochester, NY, USA, 2014. [Google Scholar]
- Anaya, J.J.; Talavera, E.; Giménez, D.; Gómez, N.; Jiménez, F.; Naranjo, J.E. Vulnerable Road Users Detection Using V2X Communications. In Proceedings of the IEEE International Conference on Intelligent Transportation Systems, Las Palmas, Spain, 15–18 September 2015; pp. 107–112. [Google Scholar]
- Wu, X.; Miucic, R.; Yang, S.; Al-Stouhi, S.; Misener, J.; Bai, S.; Chan, W.-H. Cars Talk to Phones: A DSRC Based Vehicle-Pedestrian Safety System. In Proceedings of the IEEE Vehicular Technology Conference, Vancouver, BC, Canada, 14–17 September 2014; pp. 1–7. [Google Scholar]
- Dhondge, K.; Song, S.; Choi, B.; Park, H. WiFiHonk: Smartphone-Based Beacon Stuffed WiFi Car2X-Communication System for Vulnerable Road User Safety. In Proceedings of the IEEE 79th Vehicular Technology Conference, Seoul, Korea, 18–21 May 2014; pp. 1–5. [Google Scholar]
- Dozza, M.; Idegren, M.; Andersson, T.; Fernandez, A. Platform enabling intelligent safety applications for vulnerable road users. IET Intell. Transp. Syst. 2014, 8, 368–376. [Google Scholar] [CrossRef]
- Sugimoto, C.; Nakamura, Y.; Hashimoto, T. Development of Pedestrian-to-Vehicle Communication System Prototype for Pedestrian Safety Using both Wide-Area and Direct Communication. In Proceedings of the International Conference on Advanced Information Networking and Applications, Ginowan, Japan, 25–28 March 2008; pp. 64–69. [Google Scholar]
- David, K.; Flach, A. CAR-2-X and Pedestrian Safety. IEEE Veh. Technol. Mag. 2010, 5, 70–76. [Google Scholar] [CrossRef]
- Sewalkar, P.; Krug, S.; Seitz, J. Towards 802.11p-based vehicle-to-pedestrian communication for crash prevention systems. In Proceedings of the International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), Munich, Germany, 6–8 November 2017; pp. 404–409. [Google Scholar]
- Bagheri, M.; Siekkinen, M.; Nurminen, J.K. Cloud-Based Pedestrian Road-Safety with Situation-Adaptive Energy-Efficient Communication. IEEE Intell. Transp. Syst. Mag. 2016, 8, 45–62. [Google Scholar] [CrossRef]
- Jutila, M.; Scholliers, J.; Valta, M.; Kujanpää, K. ITS-G5 performance improvement and evaluation for vulnerable road user safety services. IET Intell. Transp. Syst. 2017, 11, 126–133. [Google Scholar] [CrossRef]
- Artail, H.; Khalifeh, K.; Yahfoufi, M. Avoiding Car-Pedestrian Collisions Using a VANET to Cellular Communication Framework. In Proceedings of the 13th International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, 26–30 June 2017; pp. 458–465. [Google Scholar]
- European Commission. C-ITS Platform; Final Report; European Commission: Brussels, Belgium, September 2017. [Google Scholar]
- Scholliers, J.; van Sambeek, M.; Moerman, K. Integration of vulnerable road users in cooperative ITS systems. Eur. Transp. Res. Rev. 2017, 9, 1–9. [Google Scholar] [CrossRef]
- Storck, C.R.; Duarte-Figueiredo, F. A 5G V2X Ecosystem Providing Internet of Vehicles. Sensors 2019, 19, 550. [Google Scholar] [CrossRef] [PubMed]
- Kudarauskas, N. Analysis of emergency braking of a vehicle. Transport 2007, 22, 154–159. [Google Scholar] [CrossRef]
- Makishita, H.; Matsunaga, K. Differences of drivers’ reaction times according to age and mental workload. Accid. Anal. Prev. 2008, 40, 567–575. [Google Scholar] [CrossRef] [PubMed]
- SUMO—Simulation of Urban Mobility. Available online: http://sumo-sim.org/ (accessed on 17 January 2019).
- Behrisch, M.; Bieker, L.; Erdmann, J.; Krajzewicz, D. SUMO—simulation of urban mobility: An overview. In Proceedings of the Third International Conference on Advances in System Simulation, Barcelona, Spain, 23–29 October 2011; pp. 63–68. [Google Scholar]
- Krajzewicz, D. Traffic simulation with SUMO—Simulation of Urban Mobility. Fundam. Traffic Simul. 2010, 145, 269–293. [Google Scholar]
- MASON—Multiagent Simulation Tookit. Available online: http://cs.gmu.edu/~eclab/projects/mason/ (accessed on 17 January 2019).
- Luke, S.; Cioffi-Revilla, C.; Panait, L.; Sullivan, K.; Balan, G. MASON: A Multi-Agent Simulation Environment. Simul. Trans. Soc. Model. Simul. Int. 2005, 82, 517–527. [Google Scholar]
- TraCI4J—A High-Level Java Library to Communicate with SUMO through Its TraCI Protocol. Available online: https://github.com/egueli/TraCI4J (accessed on 17 January 2019).
- OpenStreetMap. Available online: http://www.openstreetmap.org/ (accessed on 17 January 2019).
- Java OpenStreetMap Editor. Available online: http://josm.openstreetmap.de/ (accessed on 17 January 2019).
- Levine, R.V.; Norenzayan, A. The Pace of Life in 31 Countries. J. Cross Cult. Psychol. 1999, 30, 178–205. [Google Scholar] [CrossRef]
- Gawron, C. Simulation-Based Traffic Assignment—Computing User Equilibria in Large Street Networks. Ph.D. Thesis, 1999. Available online: http://e-archive.informatik.uni-koeln.de/366/ (accessed on 17 January 2019).
- Behrisch, M.; Krajzewicz, D.; Wagner, P.; Wang, Y. Comparison of methods for increasing the performance of a DUA computation. In Proceedings of the International Symposium on Dynamic Traffic Assignment, Hongkong, China, 6–8 June 2008; pp. 1–9. [Google Scholar]




| Algorithm | Conditions |
|---|---|
| Algorithm 0 | |
| Algorithm 1 | |
| Algorithm 2 | Crossing in front of vehicle |
| Algorithm 3 | Crossing in front of vehicle Pedestrian in front of vehicle |
| Configuration | Distance between Pedestrian and Crossing (m) 1 | Scenario Defined in Section 3 |
|---|---|---|
| 1 | 25 | 1,2 |
| 2 | 15 | 3 |
| 3 | 0 | 4,5 |
| 4 | 5 | 6 |
| Configuration | |||||
|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | ||
| Deviation DGPS-mobile phone (m) | Average value | 1.01 | 2.83 | 1.20 | 1.61 |
| Standard deviation | 0.37 | 1.01 | 0.31 | 0.29 | |
| Total duration of alerts (s) | Algorithm 0 | 33.15 | 30.30 | 30.15 | 27.45 |
| Algorithm 1 | 0 | 17.70 | 26.85 | 24.30 | |
| Algorithm 2 | 0 | 14.55 | 9.45 | 7.65 | |
| Algorithm 3 | 0 | 2.55 | 9.45 | 7.35 | |
| Total (s) | 0 | 2.73 | 0 | 0.75 | |
| Discrepancies in alerts | Total (%) | 0 | 4.19 | 0 | 1.12 |
| Maximum (s) | 0 | 0.22 | 0 | 0.14 | |
| 300 Pedestrians | 500 Pedestrians | 700 Pedestrians | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| thad = 100 m | thad = 70 m | thad = 40 m | thad = 100 m | thad = 70 m | thad = 40 m | thad = 100 m | thad = 70 m | thad = 40 m | ||||||||||
| Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | |
| Algorithm 0 | 16.07 | ±1.05 | 13.24 | ±0.81 | 10.05 | ±0.65 | 26.11 | ±1.62 | 21.46 | ±1.26 | 16.11 | ±0.94 | 35.94 | ±2.63 | 29.54 | ±2.24 | 22.09 | ±1.91 |
| Algorithm 1 | 16.09 | ±1.04 | 14.89 | ±0.88 | 9.56 | ±0.61 | 26.07 | ±1.69 | 23.99 | ±1.48 | 15.33 | ±0.93 | 35.96 | ±2.61 | 33.03 | ±2.74 | 20.97 | ±1.72 |
| Algorithm 2 | 18.30 | ±1.20 | 15.87 | ±0.99 | 10.08 | ±0.62 | 29.77 | ±1.78 | 25.72 | ±1.57 | 16.26 | ±1.04 | 40.97 | ±3.31 | 35.25 | ±2.56 | 22.38 | ±1.67 |
| Algorithm 3 | 7.22 | ±0.35 | 5.53 | ±0.28 | 3.95 | ±0.25 | 11.83 | ±0.89 | 9.08 | ±0.63 | 6.44 | ±0.51 | 16.34 | ±1.29 | 12.53 | ±0.96 | 8.84 | ±0.67 |
| 300 Pedestrians | 500 Pedestrians | 700 Pedestrians | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| thad = 100 m | thad = 70 m | thad = 40 m | thad = 100 m | thad = 70 m | thad = 40 m | thad = 100 m | thad = 70 m | thad = 40 m | ||||||||||
| Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | |
| Algorithm 0 | 77.03 | ±2.90 | 65.67 | ±2.55 | 45.71 | ±1.89 | 88.16 | ±3.99 | 77.81 | ±3.98 | 58.52 | ±3.30 | 96.22 | ±3.48 | 86.96 | ±3.44 | 68.58 | ±3.12 |
| Algorithm 1 | 75.49 | ±2.46 | 61.44 | ±1.87 | 38.26 | ±1.27 | 85.06 | ±3.68 | 71.86 | ±3.38 | 48.62 | ±2.27 | 92.38 | ±2.56 | 79.60 | ±2.31 | 56.34 | ±1.64 |
| Algorithm 2 | 63.89 | ±1.64 | 49.85 | ±1.32 | 28.67 | ±0.92 | 71.47 | ±2.70 | 57.85 | ±2.37 | 36.09 | ±1.50 | 77.13 | ±1.86 | 63.65 | ±1.45 | 41.45 | ±1.17 |
| Algorithm 3 | 28.83 | ±1.05 | 21.22 | ±0.86 | 12.89 | ±0.65 | 38.03 | ±2.12 | 28.93 | ±1.62 | 18.53 | ±1.19 | 44.98 | ±1.45 | 34.84 | ±1.30 | 23.08 | ±1.03 |
| 300 Pedestrians | 500 Pedestrians | 700 Pedestrians | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| thad = 100 m | thad = 70 m | thad = 40 m | thad = 100 m | thad = 70 m | thad = 40 m | thad = 100 m | thad = 70 m | thad = 40 m | ||||||||||
| Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | Avg. | CI | |
| Algorithm 0 | 87.72 | ±0.22 | 65.78 | ±0.11 | 38.69 | ±0.08 | 87.89 | ±0.21 | 65.95 | ±0.11 | 38.77 | ±0.05 | 87.82 | ±0.24 | 65.93 | ±0.13 | 38.77 | ±0.05 |
| Algorithm 1 | 87.38 | ±0.26 | 61.11 | ±0.34 | 36.25 | ±0.28 | 87.56 | ±0.24 | 61.38 | ±0.18 | 36.35 | ±0.10 | 87.44 | ±0.24 | 61.40 | ±0.17 | 36.37 | ±0.02 |
| Algorithm 2 | 80.02 | ±0.64 | 57.05 | ±0.20 | 32.65 | ±0.20 | 80.38 | ±0.48 | 57.36 | ±0.27 | 32.81 | ±0.28 | 80.34 | ±0.40 | 57.44 | ±0.06 | 32.82 | ±0.06 |
| Algorithm 3 | 82.33 | ±0.59 | 62.22 | ±0.33 | 36.56 | ±0.21 | 82.22 | ±0.40 | 62.33 | ±0.24 | 36.62 | ±0.13 | 82.30 | ±0.25 | 62.37 | ±0.23 | 36.63 | ±0.14 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Soto, I.; Jimenez, F.; Calderon, M.; Naranjo, J.E.; Anaya, J.J. Reducing Unnecessary Alerts in Pedestrian Protection Systems Based on P2V Communications. Electronics 2019, 8, 360. https://doi.org/10.3390/electronics8030360
Soto I, Jimenez F, Calderon M, Naranjo JE, Anaya JJ. Reducing Unnecessary Alerts in Pedestrian Protection Systems Based on P2V Communications. Electronics. 2019; 8(3):360. https://doi.org/10.3390/electronics8030360
Chicago/Turabian StyleSoto, Ignacio, Felipe Jimenez, Maria Calderon, Jose E. Naranjo, and Jose J. Anaya. 2019. "Reducing Unnecessary Alerts in Pedestrian Protection Systems Based on P2V Communications" Electronics 8, no. 3: 360. https://doi.org/10.3390/electronics8030360
APA StyleSoto, I., Jimenez, F., Calderon, M., Naranjo, J. E., & Anaya, J. J. (2019). Reducing Unnecessary Alerts in Pedestrian Protection Systems Based on P2V Communications. Electronics, 8(3), 360. https://doi.org/10.3390/electronics8030360









