1. Introduction
With the prosperity of wireless networks and smart devices, more and more Internet-of-Things (IoT) applications have penetrated into various domains of industries, business, and daily lives of people. The fifth generation mobile network (5G) has taken the support of IoT applications as one of its major features [
1]. However, IoT devices are vulnerable to the security threats from both network and physical layers due to the simplicity of the signal processing algorithm and encryption protocol running on them [
2,
3,
4]. It is therefore, important to investigate the effective measures to counteract the increasing security threats.
Massive multiple-input multiple-output (massive MIMO) is seen as the key physical layer technique of 5G, and will bring unprecedented spectrum and energy efficiencies [
1]. Recent works [
5,
6,
7,
8,
9,
10] have shown that the enormous degrees of freedom that massive MIMO brings can significantly increase the number of wireless connections, which makes massive MIMO a promising enabler for accommodating massive IoT devices. However, due to the openness of the wireless communication channel, massive MIMO technology also has security risks such as user signal eavesdropping and information leakage. Existing systems usually use encryption algorithms in high-level protocols to ensure user information security. With the continuous development of computing capacity, the communication security solely relying on the high-level encryption is facing more and more challenges [
11,
12].
Physical layer security technology incorporates advanced signal processing methods such as beamforming and artificial noise at the physical layer and can reduce the possibility of legitimate users’ information acquired by malicious users [
13,
14,
15]. The strong spatial beamforming capability of massive MIMO leads to good resistance to passive eavesdropping. However, massive MIMO systems rely on deterministic pilot symbol sequences in the uplink training for channel information acquisition. Once the deterministic sequence is acquired by a malicious user, it can actively transmit this sequence at the same time as the legitimate user. This procedure will mislead the channel estimation process of the base station, and redirect the downlink signal beam to the malicious user’s position. This type of attack is often referred to as active eavesdropping [
16].
Zhou et al. pointed out the security risks caused by active eavesdropping to wireless communication systems with time division duplex (TDD) transmission [
11]. Some studies were conducted to deal with these problems [
12,
16,
17,
18,
19,
20,
21,
22,
23,
24], including the random sequence based detection algorithms [
16,
20,
25], channel statistics based detection algorithms [
21,
22], signal power based detection algorithm [
18,
23] and signal subspace-based detection algorithm [
24]. Among them, the signal subspace-based detection method is an effective way to detect active eavesdropping. The general idea is to determine whether the number of detected system signal sources is equal to the number of legitimate users. If yes, no active eavesdropping is undertaking in the system. However, if the number of detected signal sources is greater than the number of legitimate users, there is high possibility that the system is under the attack of active eavesdropping.
The existing eavesdropping detection algorithms leveraging signal subspace are based on information theory criteria for eavesdropping detection, such as minimum description length (MDL) [
26,
27] and Akaike information criterion (AIC) [
28]. The algorithm introduced by Wax and Kailath [
29] is used for adaptive detection of eavesdropping users in a parameter changing environment. However, the penalty terms in detection criteria affect the accuracy of the detection. For example, the MDL algorithm has underestimation problems, while the AIC algorithm has over estimation problems, caused by their penalty terms [
24].
More recently some methods were proposed to employ random sequences for the active eavesdropping purpose [
16,
25]. The rationale behind these methods is that the random sequences are not deterministic and cannot be acquired through historical observation, nor predicted through time series techniques by malicious users. Hence, if the statistic property of the random sequence is properly characterized, the active eavesdropping can be perceived by detecting the anomaly in the statistics of received random sequence. These methods are particularly suitable for the IoT applications because their simplicity can meet the strict complexity and energy constraint of IoT devices [
2,
3]. However, they were all designed for the classical single user antenna assumption. With the development of massive MIMO technology, the transition from single user antenna to multiple user antennas is an inevitable trend. Therefore, we need to study the active eavesdropping detection mechanism for multi-antenna scenarios.
With the general assumption that mobile users employ multiple antennas, this paper proposes to combine the signal subspace based and random sequence base active eavesdropping detection ideas. Random sequences are transmitted to create the random user features that cannot be forged by eavesdropper. Consequently the limit distribution of the eigenvalues derived from large-dimensional random matrix theory (RMT) [
30,
31] is used to calculate the boundaries of the sample distribution so that the region of the “normal” samples falling into can be properly characterized. Then the decision statistics is designed accordingly.
The rest of the paper is organized as follows. The active eavesdropping problem is described in
Section 2.
Section 3 proposes an active eavesdropping detection algorithm based on RMT. Simulation results are presented in
Section 4. Finally, conclusions are drawn in
Section 5.
2. Active Eavesdropping in Massive MIMO Systems
This paper considers a scenario where base station
Alice has a large amount of (
M) antennas and each legitimate user
Bob equips multiple (
K) antennas. The active eavesdropping is shown in
Figure 1. The legitimate user attempts to setup the wireless link with the base station. To this end Bob sends a series of orthogonal training sequences through its antennas to Alice so that Alice is able to estimate the channel coefficients based on these known sequences. The eavesdropper
Eve tries to affect the channel estimation process of Alice via sending the same training sequences as Bob. Without loss of generality we assume that Eve has the same number of antennas as Alice. When the number of antennas of the eavesdropping user is greater than or equal to the number of antennas of the legitimate user, the information of the legitimate user can be effectively demodulated. However, the more the number of the eavesdropper’s antennas, the easier it is to be detected. Therefore, from the perspective of eavesdropper detection, we consider the most difficult situation, that is, the eavesdropper’s antennas is equal to the legitimate user’s antennas.
Following the random sequence based active eavesdropping detection method, a series of random sequences are transmitted after the training sequences. The random sequences received by Alice with and without the contamination from Eve are expressed as:
where
and
represent the random sequence transmitted from Bob and Eve, respectively, by the
ith transmit antenna;
and
represent the random sequence received by the
jth receive antenna with and without impact from Eve, respectively;
and
are the channel fading coefficient betweens the
ith transmit antenna of Bob or Eve and the
jth receive antenna at base station, respectively. Real values
and
represent the associated path-loss attenuation factors.
and
are the uplink transmission power of Bob and Eve, respectively.
Rewrite the above Equations (
1) and (
2) in matrix form:
where
and
are the random sequences transmitted from Bob and Eve, with the sequence length of
T;
and
are the sequences received by Alice when there exists and does not exist contamination from Eve, respectively;
and
represent small-scale fading.
and
are the received signal power of legitimate user and eavesdropper, respectively.
and
represent the Gaussian noise in the two cases. Their elements are independent and identically distributed (i.i.d.) complex Gaussian random variables with zero mean and variance of
. We assume that the base station can accurately estimate the noise level through long-term observation [
32,
33]. Since
and
are randomly generated in an independent manner, they will expand the
K-dimensional subspaces, respectively.
Denote
,
,
and
. The active eavesdropping detection problem can be characterized by the following hypothesis test:
Wherein, it is assumed that the channel is quasi-static, i.e., channel fading coefficients being constant for a period of at least
T consecutive samples.
3. Active Eavesdropping Detection Based on Large-Dimensional Random Matrix Theory
3.1. Rational Behind the Proposal
According to the idea of signal subspace, if there exist several independent components in the received signal, the spectral distribution of the eigenvalues is near the position characterized by its power, when the number of antennas at the base station and user is large. The empirical spectral distribution of each component converges to its limit distribution. The expression of the eigenvalue distribution can be derived from the large-dimensional RMT. This provides an idea of using the limit distribution as a theoretical guideline to check whether the empirical eigenvalue distribution in practice is reasonable.
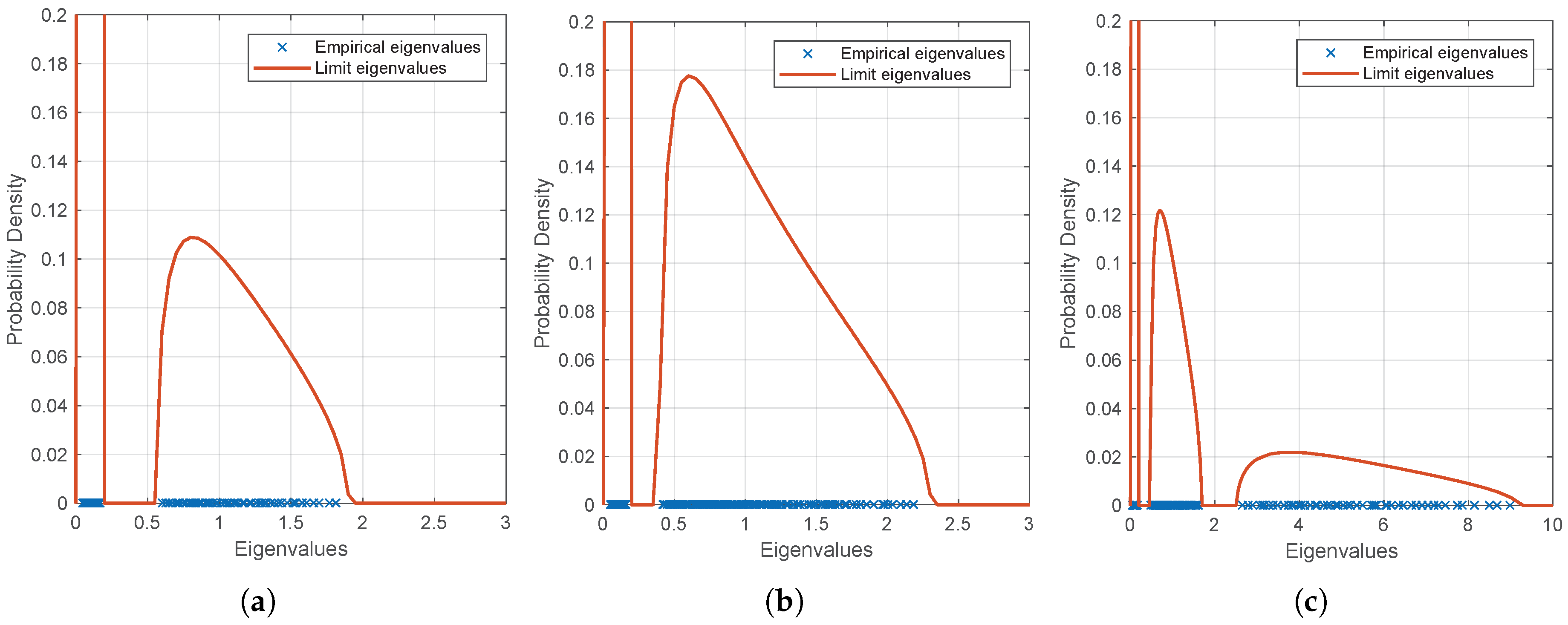
Examples of the empirical eigenvalue distribution of
are presented in
Figure 2. We can observe that the eigenvalues fall into a larger support when there is one eavesdropper compared with the case when there is not, even though the signal powers of user and eavesdropper are the same. Moreover, the eigenvalues fall into multiple disjoint supports when the powers of user and eavesdropper are significantly different. This provides an intuitive evidence that the distribution of the eigenvalues can be leveraged to determine the existence of active eavesdropping.
The large-dimensional RMT suggests that, with the increase of the number of base stations and user antennas, the empirical spectral distribution of the received signal of the base station will gradually converge to its limit spectral distribution. That is, the distribution of empirical spectrum can be accurately estimated when the matrix dimension is large, i.e., M, K, . Note that in reality, the quantities of M, K and T just need to be “sufficiently” large, say on the level of several tens to hundreds, to validate RMT. This assumption can be approaches in the massive MIMO scenarios. Therefore, the theoretical distribution of the limit spectrum can be used to judge whether the observed empirical spectral distribution is “normal”. This constitutes the basis of using the large-dimensional RMT to detect active eavesdropping in massive MIMO systems.
In the following sections, we first characterize the eigenvalue distribution properties of received massive MIMO data sequence before proposing the detection mechanism.
3.2. Eigenvalue Distribution of ()
Recall the random sequences received by base station . We provide an analysis of the eigenvalue distribution of the sample covariance matrix from the large-dimensional RMT in the sequel.
Let
be the population spectral distribution function. The empirical spectral distribution (e.s.d.) of
, noted by
, converges to the deterministic, limit spectral distribution (l.s.d.)
F of
. We have following expression [
30]:
where
m is the Stieltjes transform of
F with
,
. When
M,
K and
T grow at the same rate, i.e.,
M,
K,
with constant
. The Stieltjes transform has one-to-one correspondence to the distribution of the eigenvalues of the matrix. Mathematically it is easier to use and can build the relationship to the linear spectral statistics and other related properties.
The sample covariance matrix has an overall covariance matrix of uncertainty, but its empirical spectral distribution has an almost certain limit. Accordingly, the problem is transformed into a limit distribution that solves the empirical spectral distribution.
For the sake of conciseness, we first derive the signal expression when there is one legitimate user. Following the system model considered in previous section, the received signal is:
where
is the noise components.
. Rewrite the above expression:
Add
Y to zero vector 0 to get a larger matrix
:
where
K refers to the sum of the number of legitimate user’s antennas. We can find that
is a sample covariance matrix, for which the population covariance matrix is:
It is nondeterministic and the random matrix has independent (unnecessarily identically distributed) entries with zero mean and variance of one. When , H is a term with independent finite fourth-order moments. P is a diagonal matrix whose entries are the source powers with multiplicities the number of transmit antennas of each user.
Let
denote the distribution function of the eigenvalues of
. It is shown that
is the Stieltjes transform of a distribution function
which is the limit of
:
where
z is the inverse of the Stieltjes transform, and is calculated as:
As introduced in (
7),
is the population spectral distribution function, and it converges in distribution to a distribution
. For finite
T and
M,
m satisfies:
where
m is the Stieltjes transform of
and
. The “error term”
as
. Hence (
14) becomes (
13). In
Section 3.3 we will derive an estimate of
, and show that by setting
in (
14) and solving
m, we will obtain a finer asymptotics of the eigenvalues of
.
The almost sure convergence of the e.s.d. of
ensures the almost sure convergence of the e.s.d. of the matrix in (
11). The distribution range of eigenvalues of
can be obtained by
z in (
14). Then, we consider a special case, when
, we can get the boundary range of the noise eigenvalues. Thus, the distribution of the eigenvalues of
can be obtained by integrating the ranges of
and noise terms. In the following sections the detailed derivation of the eigenvalues’ distribution range will be presented.
3.3. Eigenvalues’ Boundary of ()
We have an empirical spectral distribution of that weakly and almost surely converges to the limit distribution G. Therefore, we can first obtain the limit distribution of .
With some trivial manipulation we can generalized expression (
7) to the case of
L users. Denote the Stieltjes transform of
G as
. Its inverse transform is
[
17]:
where
are the number of antennas of the first, the second, ⋯, and the
Lth legitimate user,
.
In Equation (
15), we give the inverse of the Stieltjes transform when there are multiple legitimate users. Assuming that there is only one legitimate user in the system, (
15) is turned to:
The discretized minimal and maximal values of the eigenvalues according to the limit distribution are:
where
and
are the two real-valued solutions of the equation:
and satisfies
.
Now we briefly reveal the derivation of Equation (
19). The boundary of the eigenvalues is at the extreme point of the integral curve
[
17], from which we have:
Therefore, let
, we can get:
Rearranging the above equation, we can get the Equation (
19).
From these expressions we can reach an important observation: if we want to increase the estimator’s detection sensitivity, that is, to be able to separate two signal sources with similar received power, we need to increase the number of base station antennas (yielding a larger ).
However, the left and right boundaries of the eigenvalues obtained in (
17) and (
18) have some deviations. As shown in
Figure 3, eigenvalues fall in the areas outside the boundary [
] (i.e., outside the areas bounded by blue circles).
As shown in
Figure 2, when the matrix dimension is large and the powers of the two signal sources satisfy some requirements, the supports of the eigenvalues associated to the two sources are separable. According to the separability of eigenvalues’ supports derived in [
31] in which some corrections were proposed to improve the boundaries where there is no eigenvalue. We have the following Lemma.
Lemma 1. Denote the interval between two supports of eigenvalues as, where there is no eigenvalue.whereis the eigenvalue of theiMth eigenvalue cluster, andis the eigenvalue of the iM+1th eigenvalue cluster, and the eigenvalues are arranged in a descending order, i.e.,.is calculated as:and According to the above Lemma, we propose to modify (
17) and (
18) with a similar correction term
:
The correction term
is an infinitesimal, and
. In this case,
in fact represents the
in Equation (
14). It can be calculated as:
where
With these new expressions in (
25) and (
26), we obtain new support of eigenvalues:
Observing
Figure 3, we find that the corrected eigenvalue boundaries are more accurate compared to the expression given in (
17) and (
18).
3.4. Eigenvalues’ Boundary of ()
The left and right boundaries
and
obtained from (
25) and (
26) are only based on the empirical spectral distribution of
. They characterize the range of the received signal eigenvalues in the absence of noise. With the effect of additive noise, the range of eigenvalues has a significant shift to the right, and the boundaries
and
no longer conform to the eigenvalue distribution, as shown in
Figure 4. With this observation, we continue to improve the expression of the eigenvalues’ boundaries by incorporating the noise effect to (
25) and (
26).
In the massive MIMO scenarios considered in this work, the length of the support of
is approximately equal to the length of the support of
. The main difference between them is that the latter has a significant offset from the former due to the influence of noise. Unfortunately it is difficult to analytically characterize the influence of the noise. We propose the following modifications to the eigenvalues’ boundary expressions:
where the noise effect is counted in the term:
in which
is obtained by:
We plot the new boundaries in
Figure 4. It is clear that the boundaries proposed in (
30) and (
31) fit better the real distribution of the eigenvalues compared to the expressions in (
25) and (
26).
Upon this basis, we propose a test criterion for detecting active eavesdropping:
This value in fact characterizes the maximal range that the eigenvalues distribute when there is only legitimate user. If the actual spread of the eigenvalues is greater than this range, it suggests that there exists some anomaly in the received signal, indicating the active eavesdropping phenomenon.
3.5. Noise Elimination Based on Marčenko–Pastur Law
In this section, we propose to use the limit distribution of the noise covariance matrix to approximate its empirical distribution. More precisely we use the Marčenko–Pastur distribution from large-dimensional RMT (commonly referred to as M-P law) to help eliminating the noise components.
The noise component
N in the received signal of the base station satisfies complex Gaussian distribution, i.e.,
. Then, according to M-P law, the left and right boundaries of its limit spectral distribution can be written as:
With this knowledge, we can eliminate the eigenvalues of the received signal that fall into the range .
The use of the M-P law to eliminate noise components will bring the following advantages. As long as the noise power and legitimate user’s power are relative different, the empirical spectral distribution of noise and legitimate user’s signal are clearly separated. This method does not affect the eigenvalues brought by the active eavesdropping signal components, and thereby does not affect the consequent active eavesdropping detection. In contrast, other traditional noise elimination method that removes a certain number of smallest eigenvalues may cause potential risk of miss detection of active eavesdropping [
29]. This is because the eigenvalues associated with the active eavesdropper may be removed in this process, which will jeopardize the following eavesdropping detection process.
3.6. Proposed Active Eavesdropping Detection Algorithm
Based on the previous analysis and discussion, we propose the following algorithm to detect active eavesdropping.
Step 1: Preliminary. The base station calculates a theoretical decision threshold of the test statistic based on the system parameters e.g., base station’s antenna number M, user’s antenna number K, signal sample number T, as well as the historical observation of noise level and user signal power .
Step 2: Eigenvalue computation. The base station samples the received random sequence and obtains a sample matrix Y. Then it calculates the sample covariance matrix and performs the eigenvalue decomposition of . This yields M eigenvalues .
Step 3: Noise elimination. The base station uses the M-P law to compute the noise range . All the eigenvalues falling into this range are eliminated.
Step 4: Test statistic calculation. The difference between the maximal and minimal values of the remaining eigenvalues is calculated, i.e., where is the smallest remaining eigenvalue.
Step 5: Hypothesis test. The test statistic obtained in Step 4 is compared to the theoretical range of the eigenvalue spread . If , the null hypothesis is accepted. This means there is no active eavesdropping components in the received signal. In the contrary, if , the alternative hypothesis is accepted. It suggests that it is highly probable that the system is under active eavesdropping.
By periodically performing the previous steps, the system can detect the existence of active eavesdropping. We can get the Algorithm 1 shows the process of active eavesdropping detection.
| Algorithm 1 Active Eavesdropping Detection Algorithm |
| Input: Base station received signal Y as shown in (3) and (4). |
| Output: Active eavesdropping detection result. |
- 1:
Calculate test statistic as shown in ( 30) and ( 31). - 2:
Solve the eigenvalue of . - 3:
Eliminate the eigenvalues caused by noise in as shown in ( 32). - 4:
Calculate the actual value of the test statistic. - 5:
Perform a hypothesis test based on the test statistic.
|
4. Performance Evaluation
In this section, we evaluate the performance of the proposed algorithm with various parameters M, and T based on the analytical expressions derived in Sections III and via Monte Carlo simulations. The detection probability indicates the probability that the eavesdropping user is detected, and the false alarm probability indicates that the probability of the eavesdropper is erroneously detected when there is no eavesdropper. All relevant system parameters are provided in the captions of figures. Rayleigh flat-fading channel is adopted in the simulations.
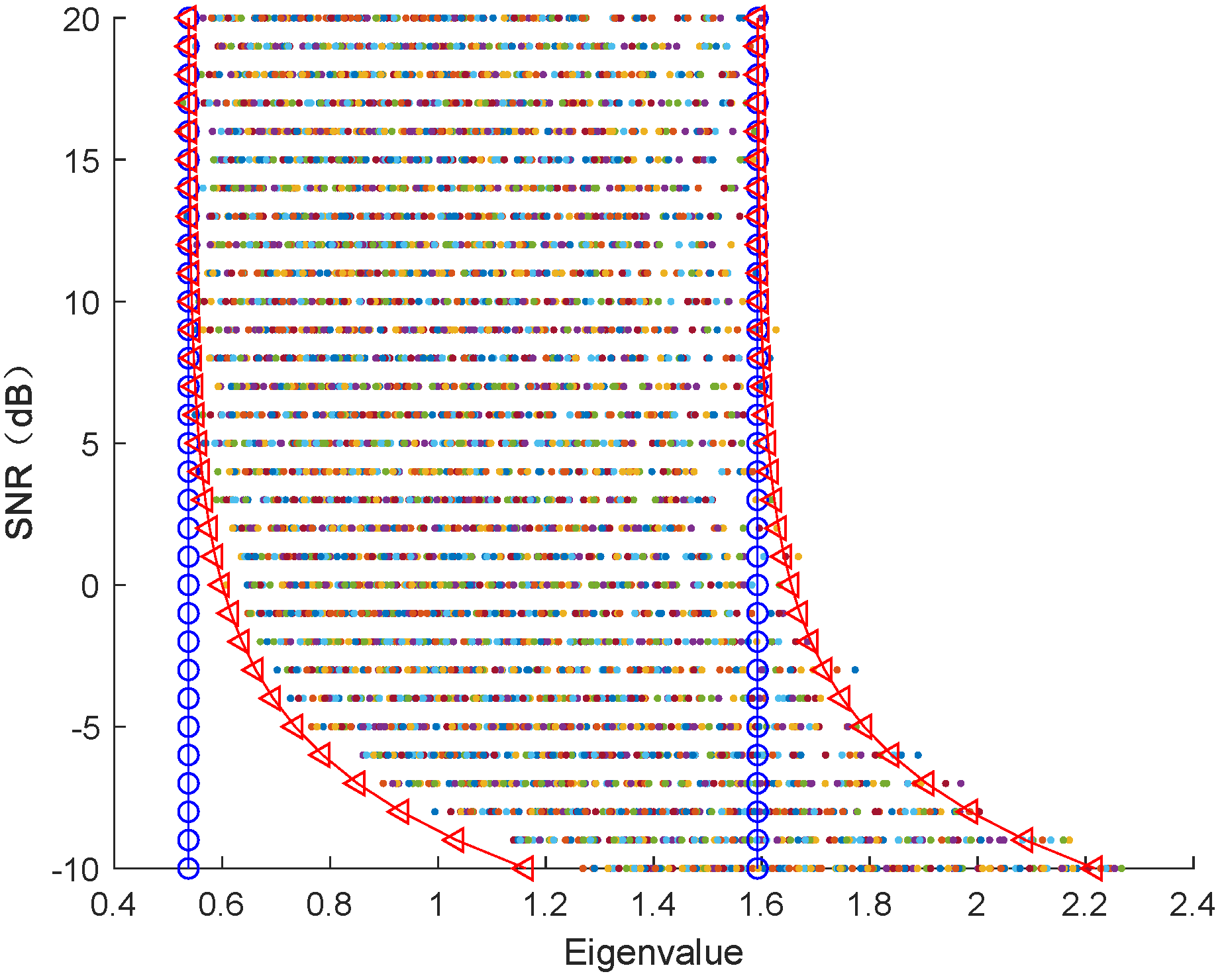
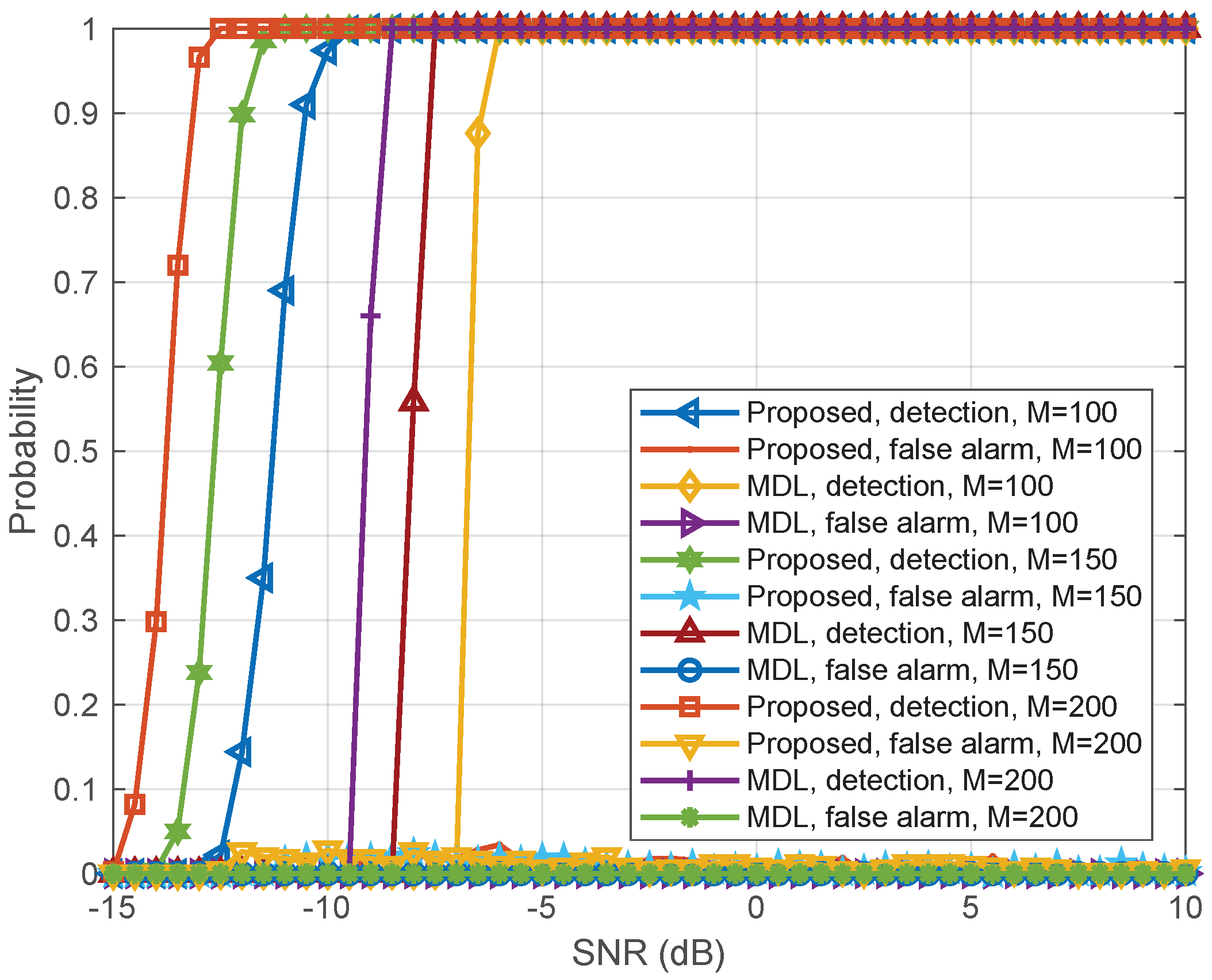
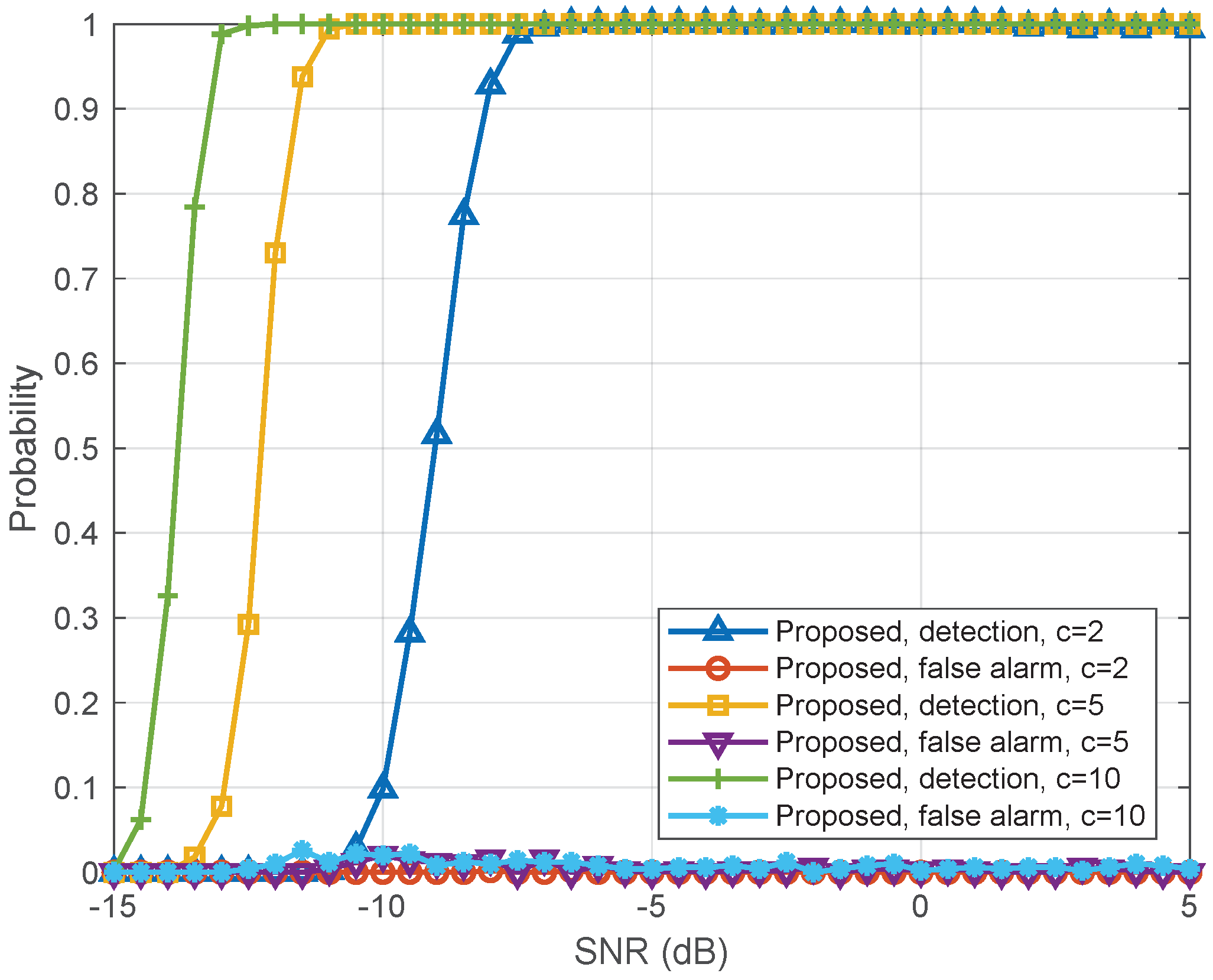
In
Figure 5, we show the detection probability with respect to signal-to-noise ratio (SNR) levels for different base station antennas
M. The detection probability increases to one and the alarm probability tends to zero when SNR increases. When noise power is equal to the power of legitimate user signal, the overlap of the empirical spectral distribution of the signal and noise components is more serious. As SNR increases, the empirical spectral distribution of user signal and noise components is gradually separated, and the detection performance is significantly improved. Moreover, the proposed algorithm obviously outperforms the classical MDL-based detection method [
24].
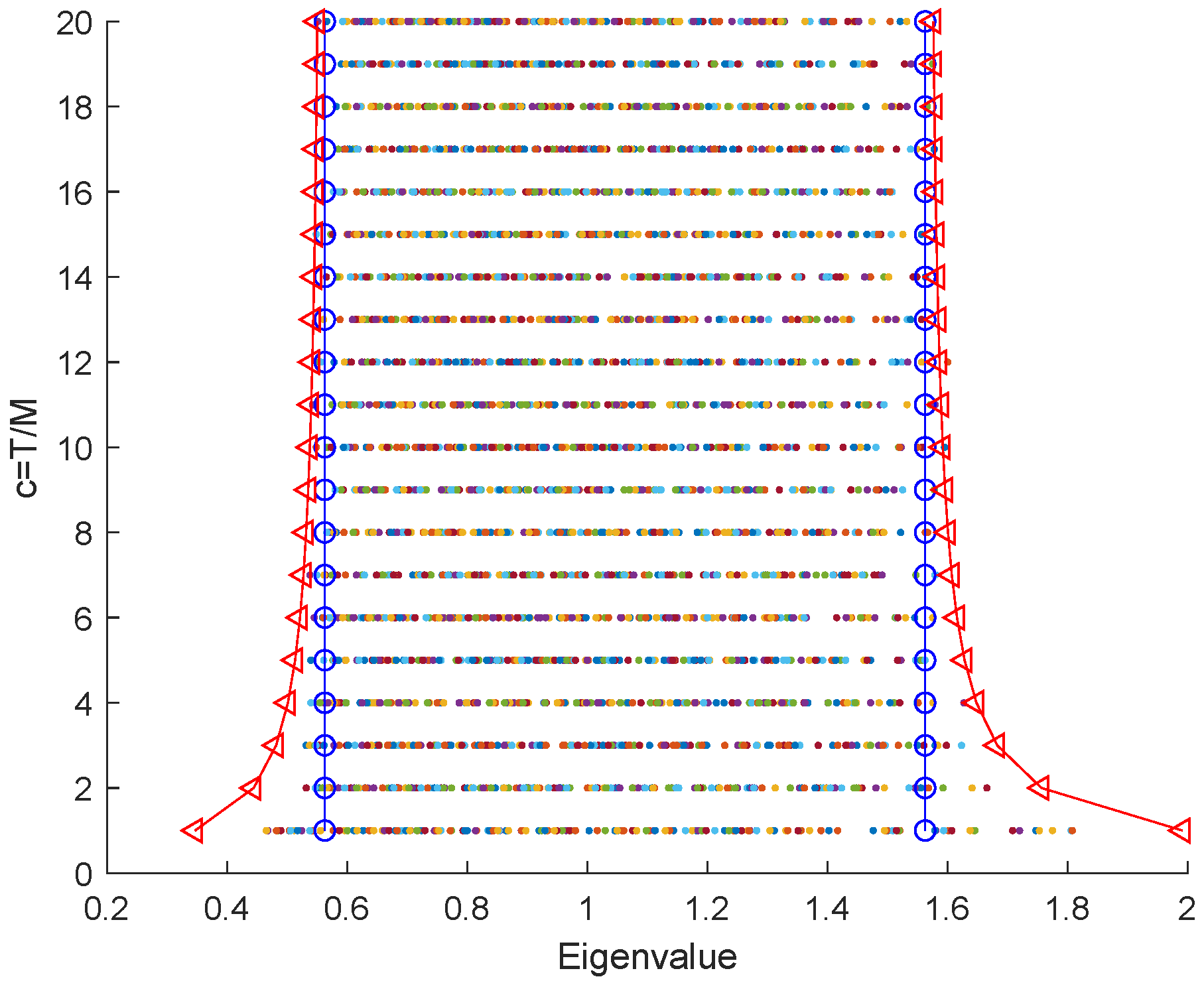
Figure 6 shows the detection probability with respect to SNR with different numbers of data samples. The experimental results show that the detection algorithm is improved when employing more data samples. Moreover, traditional detection methods [
24] require a particularly large number of samples to approximate the sample covariance matrix. However, the proposed scheme only needs to observe the spectrum of the large-scale sample covariance matrix. Even when the number of samples is not very large, we can still obtain a relatively good approximate of the spectrum of sample covariance matrix. From the figure, it is clearly that when the value of
c is relatively low (e.g.,
), the new left and right boundaries can still characterize the actual eigenvalue distribution. In particular, when the number of samples and the number of signal sources are in the same order of magnitude, the proposed scheme can effectively detect the active eavesdropping.
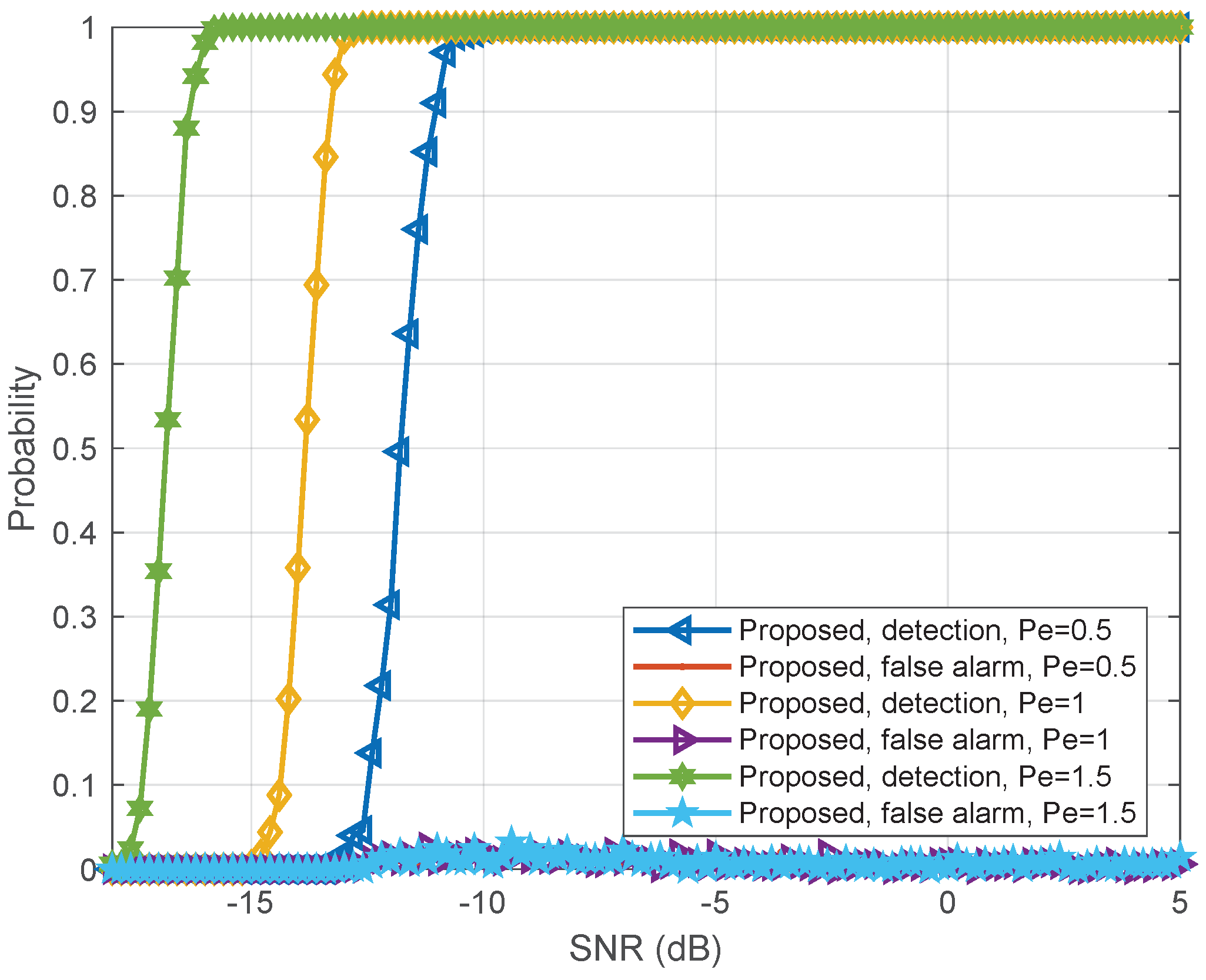
Figure 7 illustrates the detection probability with respect to the relative power ratio of the active eavesdropper versus legitimate user (
). As expected, with the increase of
, detection probability is significantly improved. We should note here that the portion of base station signal redirected to eavesdropper linearly related to eavesdropper’s transmit power. Therefore, there is no interest for eavesdropper to unlimitedly reduce its transmit power to purposely avoid from being detected. So, the fact that the proposed scheme can work in very low SNR regime (e.g.,
dB) and low
ratio suggests that the eavesdropper must have highly superiority over legitimate user (such as having much higher sensitivity or being much closer to the base station) to make the eavesdropping possible.
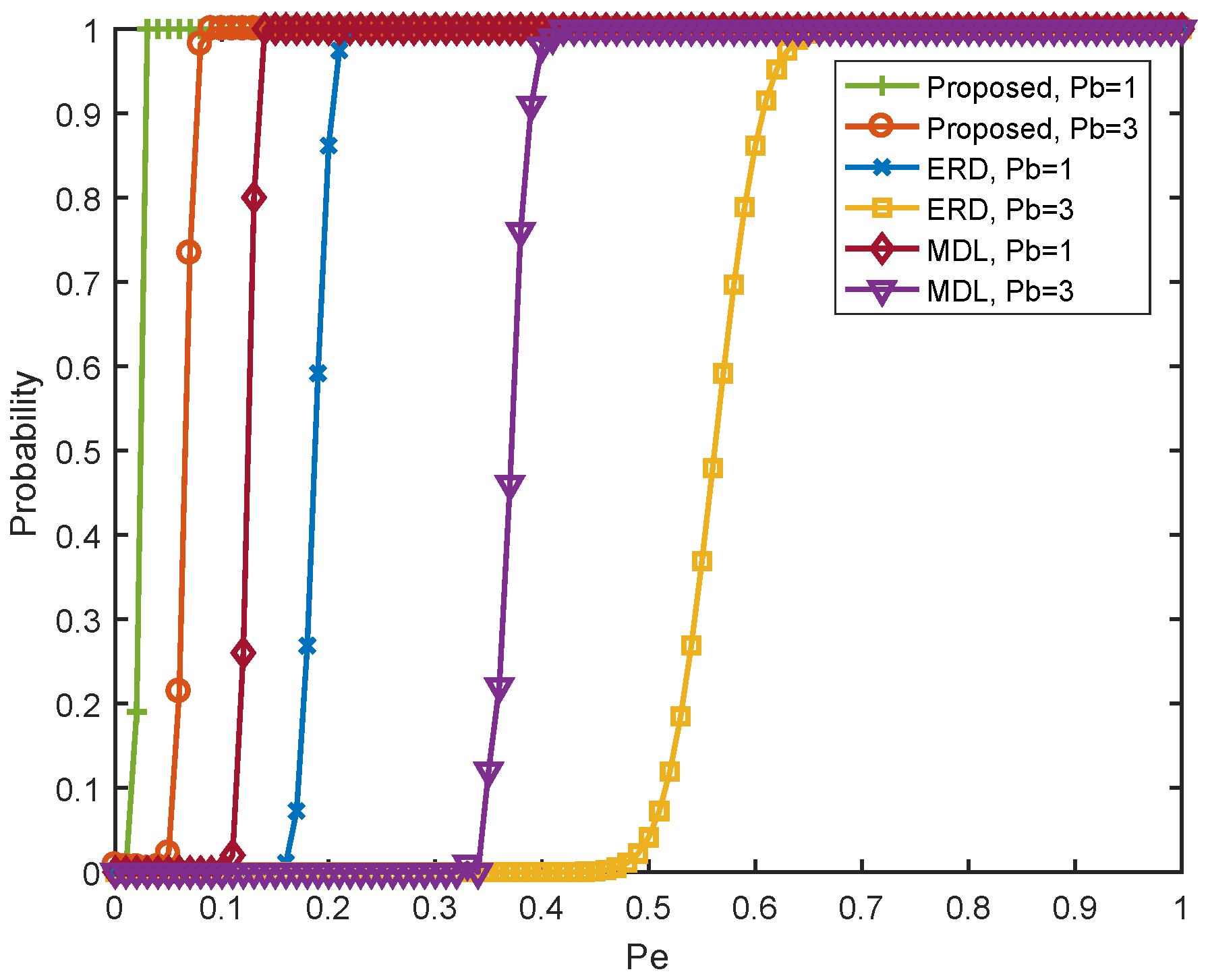
In
Figure 8, we conduct the simulation to illustrate the performance of the proposed algorithm as a function of eavesdropper’s power
. We set the legitimate user’s power
and
, respectively, and the probability of false alarm as
. From
Figure 8, we can conclude that higher eavesdropper power leads to higher probability of correct attack detection. More importantly, even with weak eavesdropper signal, for example
, the performance of our proposed scheme is still high accuracy. This suggests that the proposed scheme can detect the eavesdropping even when the power of eavesdropper is much lower that the legitimate user. We also compare the energy ratio (ER) based algorithm [
23] and MDL based algorithm [
24]. Obviously, the proposed algorithm significantly outperforms ER and MDL based ones.
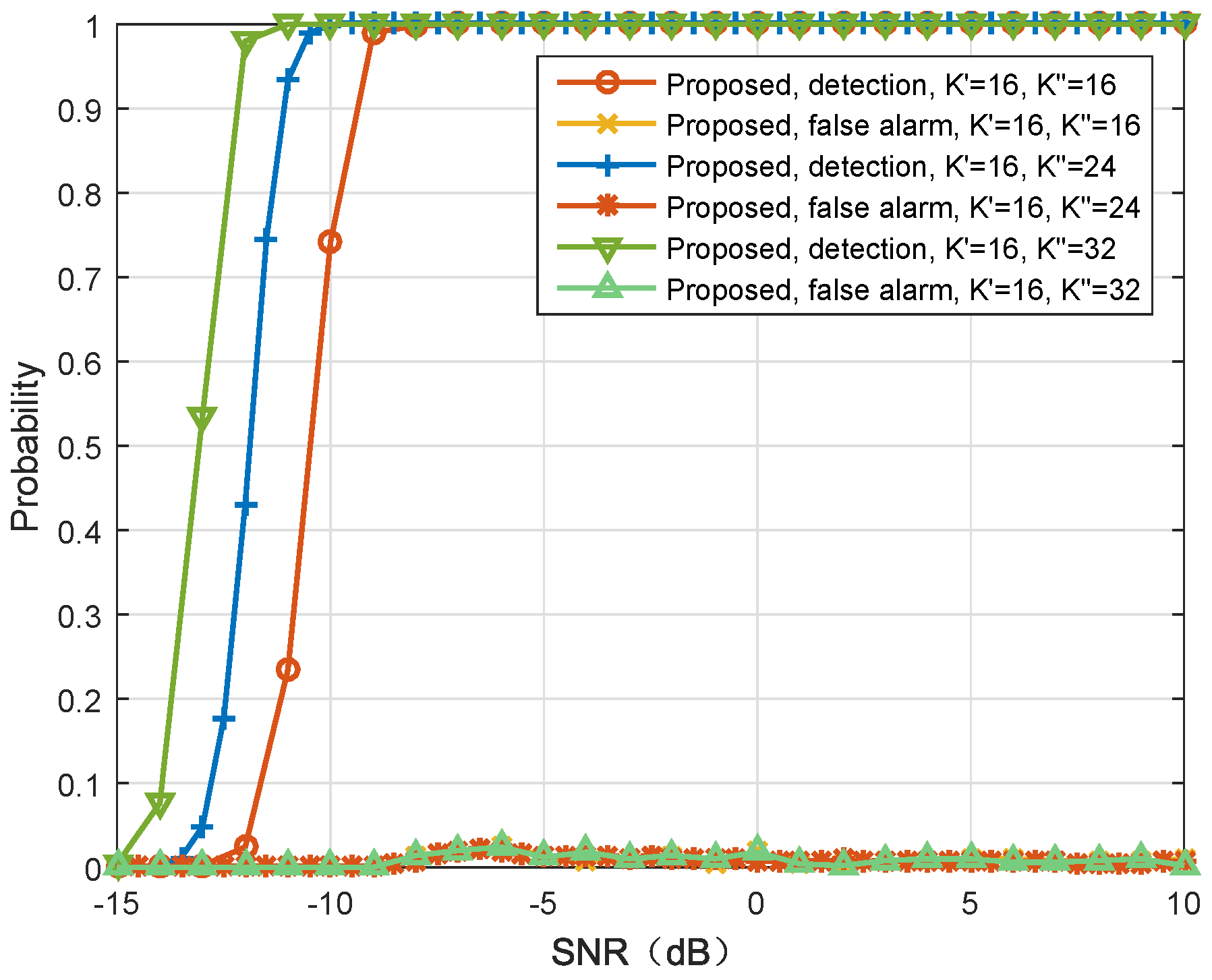
In
Figure 9, the impact of legitimate user’s and eavesdropper’s antenna numbers on the detection performance is evaluated. From the figure, as the number of eavesdropper’s antennas increases, the performance of the proposed algorithm is improved. Recall that only when the number of eavesdropper’s antennas is greater than or equal to the number of legitimate user’s antennas, the eavesdropper can effectively eavesdrop information. Therefore, the results suggest that the proposed scheme can effectively detect active eavesdropping with the reasonable antenna number settings.