Performance Analysis of IEEE 802.11p for Continuous Backoff Freezing in IoV
Abstract
1. Introduction
- We have modeled the MAC service process based on the PGF method to transform traditional Markov chains into z domain under the situation of non-saturation.
- Considering continuous backoff freezing, we have employed the Mason formula to derive the mean and deviation of the MAC access delay.
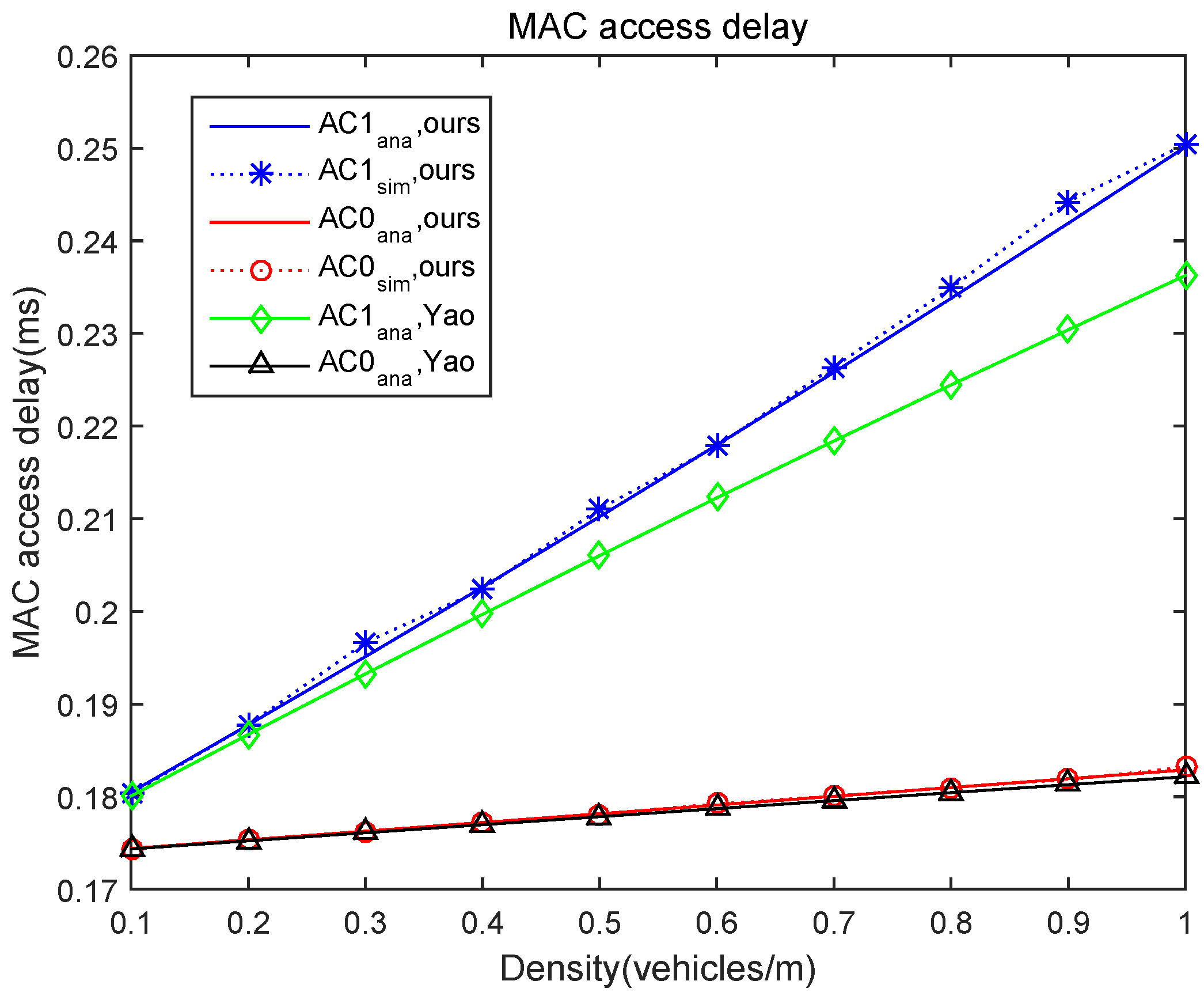
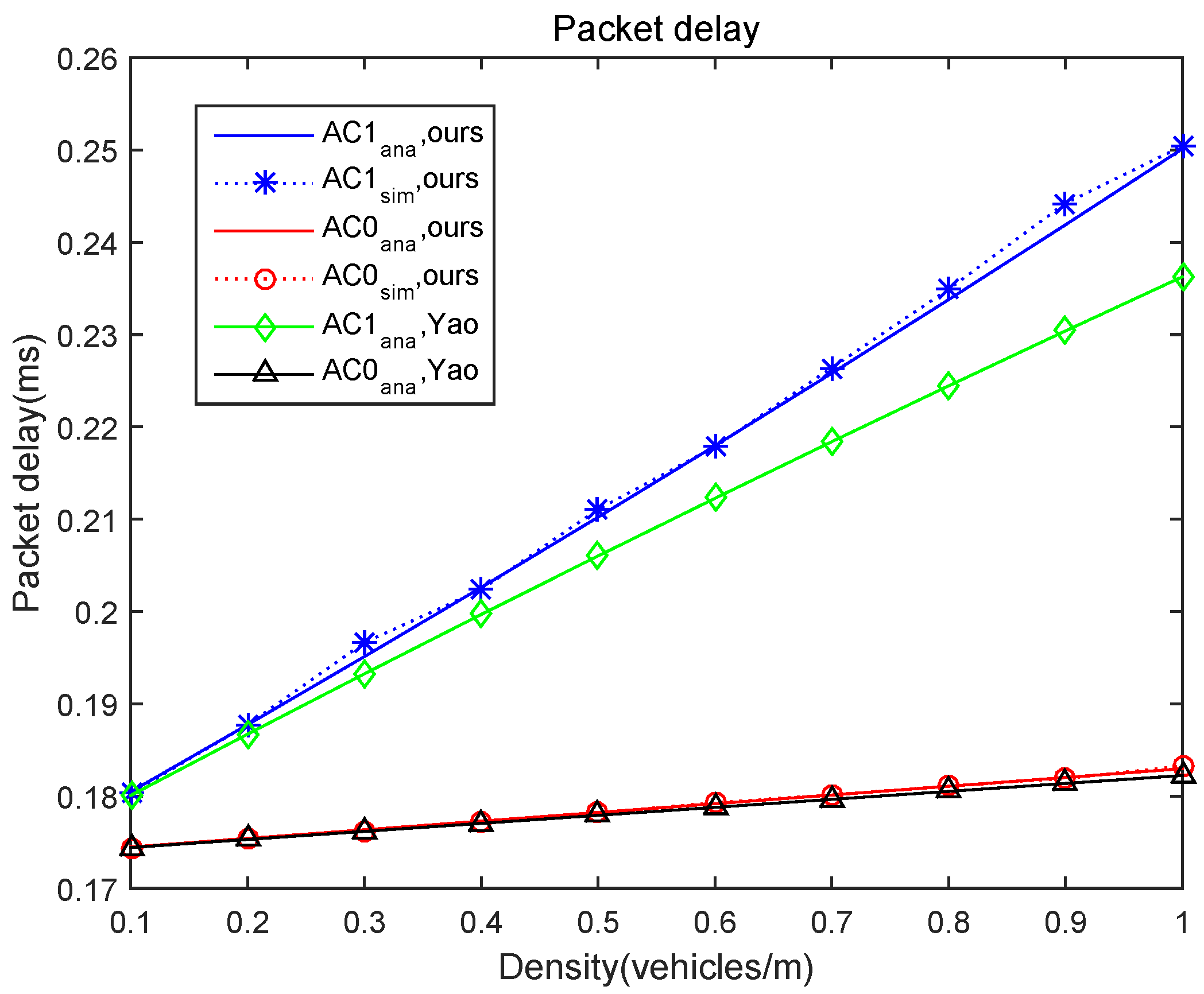
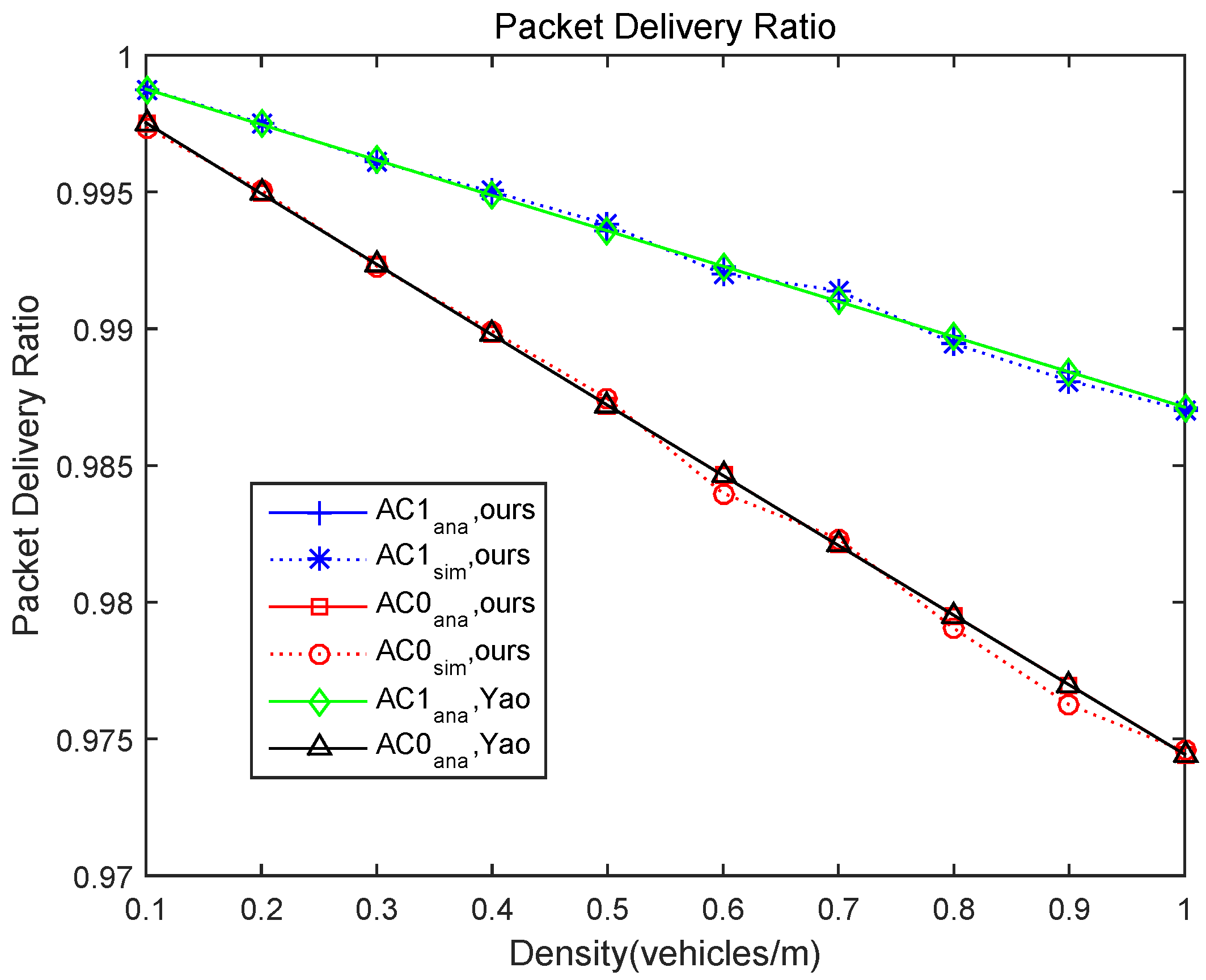
- As compared with the model presented in [28], which did not consider the situation of continuous backoff freezing, the performance of our analytical model in terms of packet delay and packet delivery ratio has been verified.
2. Related Work
3. IEEE 802.11p EDCA Mechanism and Scenario Description
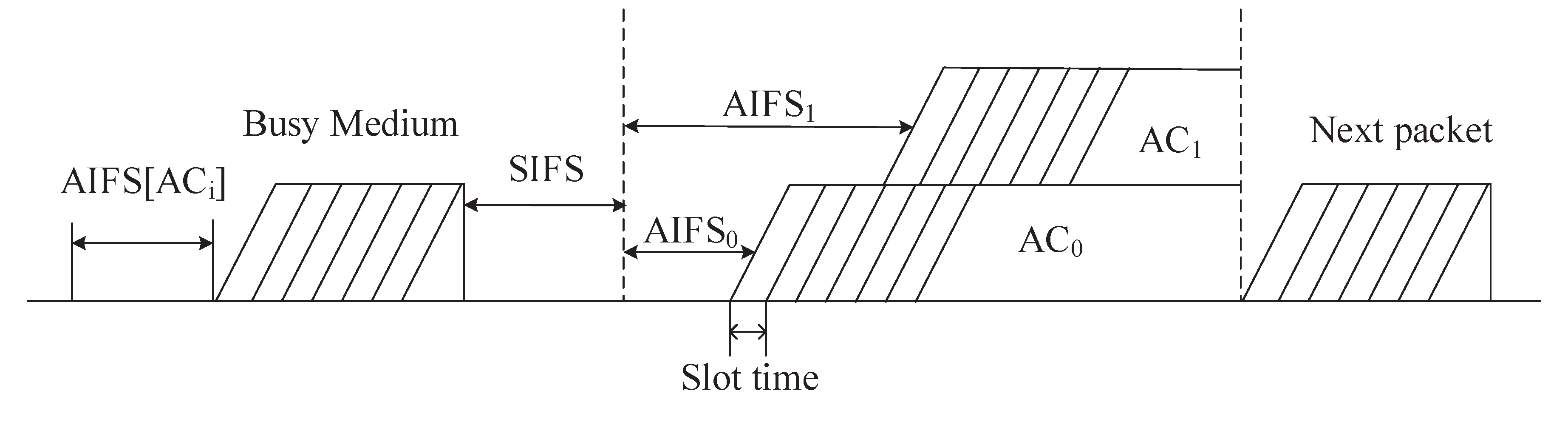
3.1. An Overview of IEEE 802.11p EDCA Mechanism
- : the minimum contention window;
- : the maximum contention window;
- : transmission opportunity;
- : Arbitration Inter Frame Space, which indicates the channel idle time that must be waited for to obtain a transmission opportunity.
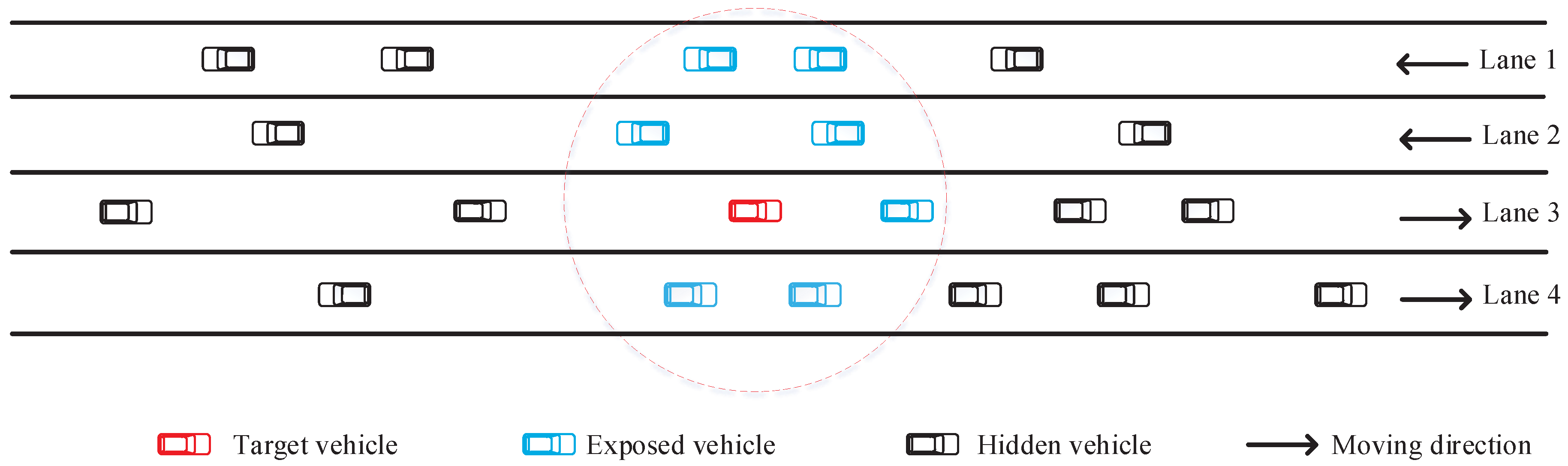
3.2. Scenario Description
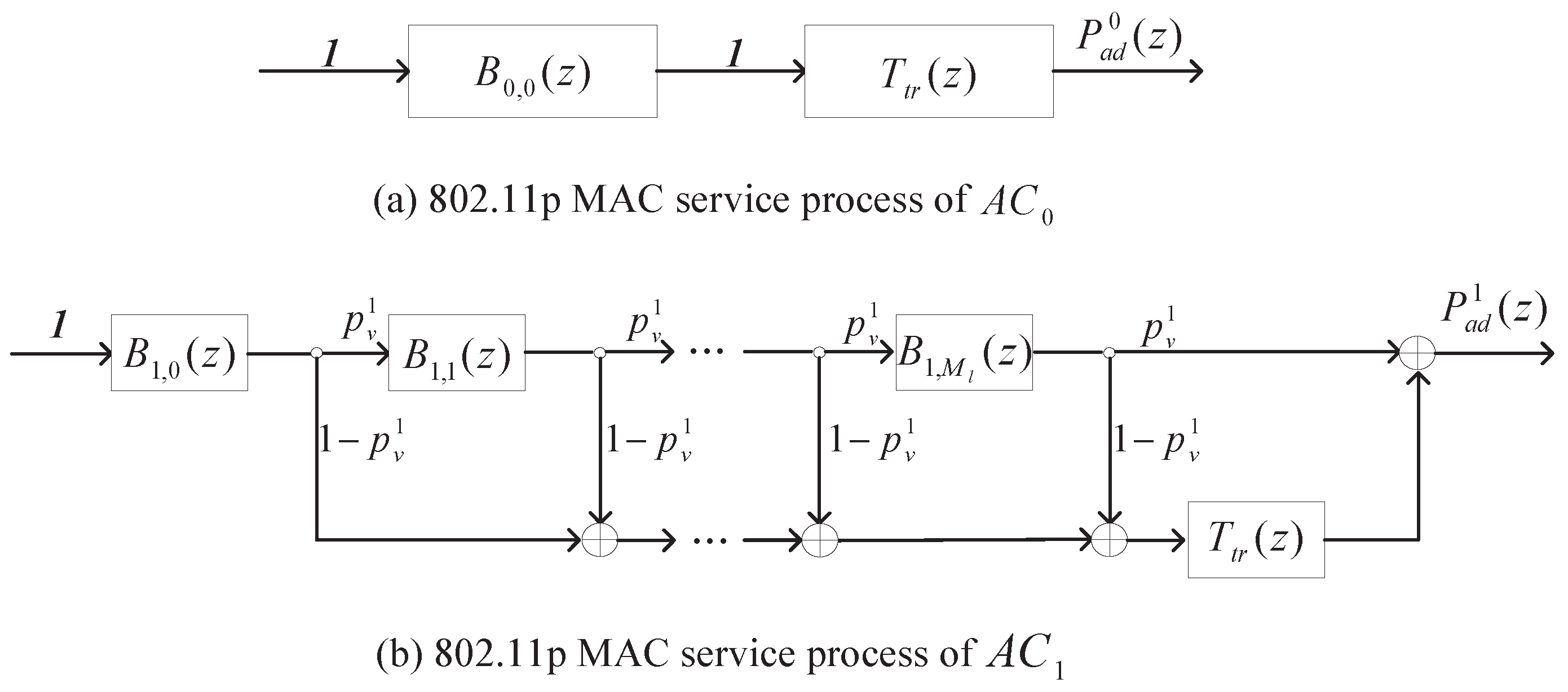
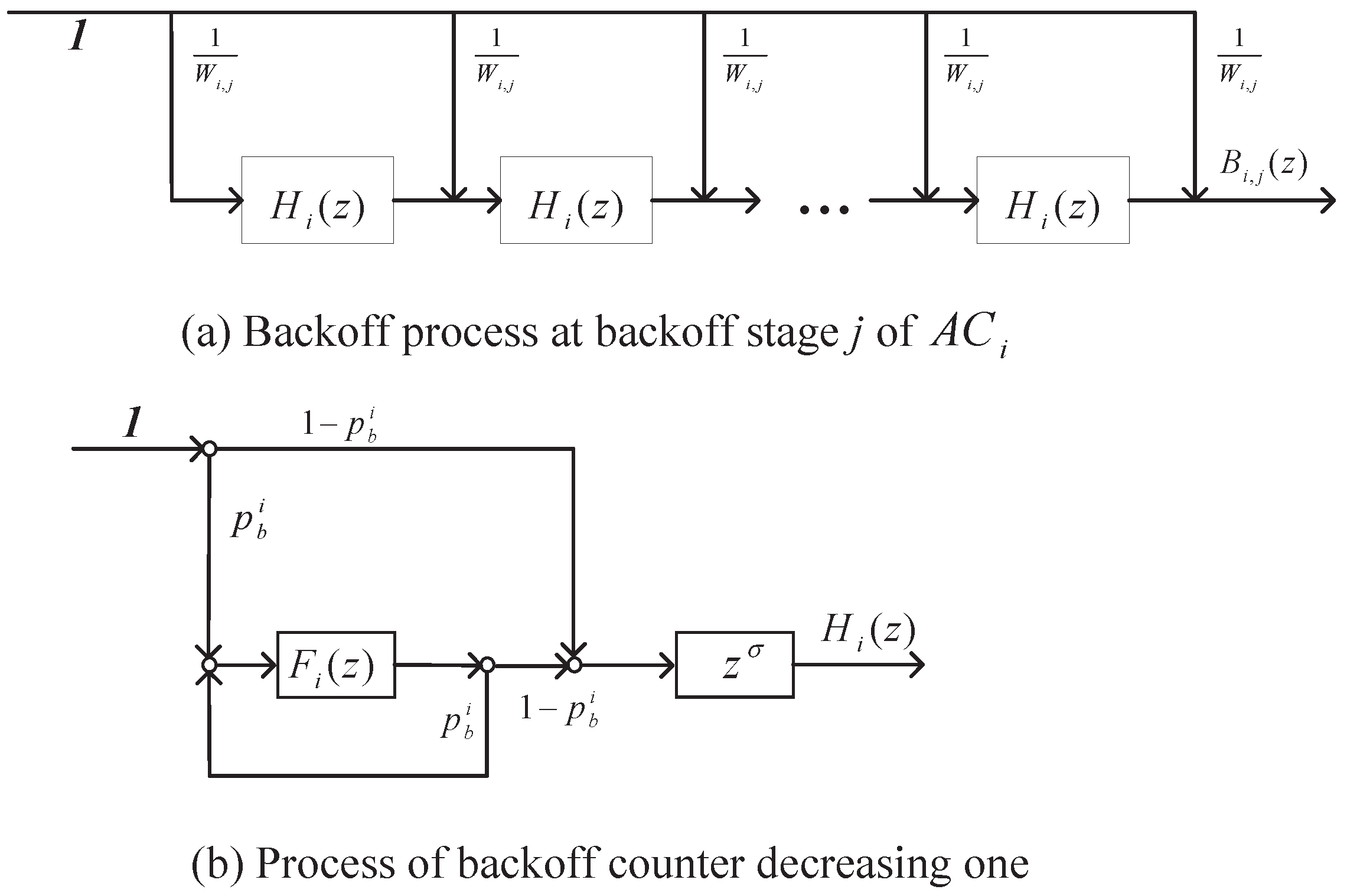
4. Analytical Model for Continuous Backoff Freezing
5. Simulation Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Wu, Q.; Liu, H.; Zhang, C.; Fan, Q.; Li, Z.; Wang, K. Trajectory Protection Schemes Based on a Gravity Mobility Model in IoT. Electronics 2019, 8, 148. [Google Scholar] [CrossRef]
- Bu, Z.; Li, H.; Zhang, C.; Cao, J.; Li, A.; Shi, Y. Graph K-means based on Leader Identification, Dynamic Game and Opinion Dynamics. IEEE Trans. Knowl. Data Eng. 2019. [Google Scholar] [CrossRef]
- Cao, J.; Bu, Z.; Wang, Y.; Yang, H.; Jiang, J.; Li, H. Detecting Prosumer-Community Groups in Smart Grids From the Multiagent Perspective. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 1652–1664. [Google Scholar] [CrossRef]
- Fan, Q.; Ansari, N. Towards Traffic Load Balancing in Drone-Assisted Communications for IoT. IEEE IoT-J. 2019, 6, 3633–3640. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, H.; Li, Z.; Liu, Y.; Zhang, C. Performance Evaluation of the V2I Fair Access with a Finite Retry Limit. EURASIP J. Wirel. Commun. Netw. 2018, 2018, 20. [Google Scholar] [CrossRef]
- Wu, Q.; Nie, S.; Fan, P.; Liu, H.; Fan, Q.; Li, Z. A Swarming Approach to Optimize the One-Hop Delay in Smart Driving Inter-Platoon Communications. Sensors 2018, 18, 3307. [Google Scholar] [CrossRef]
- Xu, W.; Zhou, H.; Cheng, N.; Lyu, F.; Shi, W.; Chen, J.; Shen, X. Internet of vehicles in big data era. IEEE/CAA J. Autom. Sin. 2018, 5, 19–35. [Google Scholar] [CrossRef]
- Cao, J.; Wu, Z.; Wu, J.; Xiong, H. SAIL: Summation-bAsed Incremental Learning for Information-Theoretic Text Clustering. IEEE Trans. Cybern. 2013, 43, 570–584. [Google Scholar] [CrossRef]
- Lyu, F.; Cheng, N.; Zhu, H.; Zhou, H.; Xu, W.; Li, M.; Shen, X. Intelligent Context-Aware Communication Paradigm Design for IoVs Based on Data Analytics. IEEE Netw. 2018, 32, 74–82. [Google Scholar] [CrossRef]
- Fan, Q.; Ansari, N. Workload Allocation in Hierarchical Cloudlet Networks. IEEE Commun. Lett. 2018, 22, 820–823. [Google Scholar] [CrossRef]
- Fan, Q.; Ansari, N. Application Aware Workload Allocation for Edge Computing-Based IoT. IEEE IoT-J. 2018, 5, 2146–2153. [Google Scholar] [CrossRef]
- Seif, H.G.; Hu, X. Autonomous Driving in the iCity-HD Maps as a Key Challenge of the Automotive Industry. Engineering 2016, 2, 159–162. [Google Scholar] [CrossRef]
- Xiong, K.; Chen, C.; Qu, G.; Fan, P.; Letaief, K. Group Cooperation with Optimal Resource Allocation in Wireless Powered Communication Networks. IEEE Trans. Wirel. Commun. 2017, 16, 3840–3853. [Google Scholar] [CrossRef]
- Lu, Y.; Xiong, K.; Fan, P.; Zhong, Z.; Letaief, K. Robust Transmit Beamforming With Artificial Redundant Signals for Secure SWIPT System Under Non-Linear EH Model. IEEE Trans. Wirel. Commun. 2018, 17, 2218–2232. [Google Scholar] [CrossRef]
- Xiong, K.; Zhang, Y.; Fan, P.; Yang, H.; Zhou, X. Mobile Service Amount Based Link Scheduling for High-Mobility Cooperative Vehicular Networks. IEEE Trans. Veh. Technol. 2017, 66, 9521–9533. [Google Scholar] [CrossRef]
- Xiong, K.; Wang, B.; Jiang, C.; Liu, K. A Broad Beamforming Approach for High-Mobility Communications. IEEE Trans. Veh. Technol. 2017, 66, 10546–10550. [Google Scholar] [CrossRef]
- Xiong, K.; Fan, P.; Zhang, Y.; Letaief, K. Towards 5G High Mobility: A Fairness-Adjustable Time-Domain Power Allocation Approach. IEEE Access 2017, 5, 11817–11831. [Google Scholar] [CrossRef]
- Li, T.; Xiong, K.; Fan, P.; Letaief, K. Service-oriented power allocation for high-speed railway wireless communications. IEEE Access 2017, 5, 8343–8356. [Google Scholar] [CrossRef]
- Yao, Y.; Rao, L.; Liu, X.; Zhou, X. Delay analysis and study of IEEE 802.11p based DSRC safety communication in a highway environment. In Proceedings of the 2013 IEEE INFOCOM, Turin, Italy, 14–19 April 2013. [Google Scholar]
- Awad, M.; Seddik, K.; Elezabi, A. Low-Complexity Semi-Blind Channel Estimation Algorithms for Vehicular Communications Using the IEEE 802.11p Standard. IEEE Trans. Intell. Transp. Syst. 2019, 20, 1739–1748. [Google Scholar] [CrossRef]
- Shah, A.; Ilhan, H.; Tureli, U. RECV-MAC: A novel reliable and efficient cooperative MAC protocol for VANETs. IET Commun. 2019, 13, 2541–2549. [Google Scholar] [CrossRef]
- Wu, Q.; Liu, H.; Wang, R.; Fan, P.; Fan, Q.; Li, Z. Delay Sensitive Task Offloading in the 802.11p Based Vehicular Fog Computing Systems. IEEE IoT-J. 2019. [Google Scholar] [CrossRef]
- Nguyen, V.; Khanh, T.; Oo, T.; Tran, N.; Huh, E.; Hong, C. A Cooperative and Reliable RSU-Assisted IEEE 802.11P-Based Multi-Channel MAC Protocol for VANETs. IEEE Access 2019, 7, 107576–107590. [Google Scholar] [CrossRef]
- IEEE Standard for Information Technology– Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 6: Wireless Access in Vehicular Environments; 2010. Available online: https://ieeexplore.ieee.org/document/5514475?section=abstract (accessed on 20 November 2019).
- Wu, Q.; Zheng, J. Performance Modeling and Analysis of IEEE 802.11 DCF Based Fair Channel Access for Vehicle-to-Roadside Communication in a Non-Saturated State. Wirel. Netw. 2015, 21, 1–11. [Google Scholar] [CrossRef]
- Wu, Q.; Zheng, J. Performance Modeling and Analysis of the ADHOC MAC Protocol for Vehicular Networks. Wirel. Netw. 2016, 22, 799–812. [Google Scholar] [CrossRef]
- Zheng, J.; Wu, Q. Performance modeling and analysis of the IEEE 802.11p EDCA mechanism for VANET. IEEE Trans. Veh. Technol. 2015, 65, 2673–2687. [Google Scholar] [CrossRef]
- Yao, Y.; Rao, L.; Liu, X. Performance and Reliability Analysis of IEEE 802.11p Safety Communication in a Highway Environment. IEEE Trans. Veh. Technol. 2013, 62, 4198–4212. [Google Scholar] [CrossRef]
- Xu, K.; Tipper, D.; Qian, Y.; Krishnamurthy, P. Time-Dependent Performance Analysis of IEEE 802.11p Vehicular Networks. IEEE Trans. Veh. Technol. 2016, 65, 5637–5651. [Google Scholar] [CrossRef]
- Shmerling, E. Algorithms for generating random variables with a rational probability-generating function. Int. J. Comput. Math. 2015, 92, 2001–2010. [Google Scholar] [CrossRef]
- Li, B.; Sutton, G.; Hu, B.; Liu, R.; Chen, S. Modeling and QoS analysis of the IEEE 802.11p broadcast scheme in vehicular ad hoc networks. J. Commun. Netw. 2017, 19, 169–179. [Google Scholar] [CrossRef]
- Peng, H.; Li, D.; Abboud, K.; Zhou, H.; Zhao, H.; Zhuang, W.; Shen, X. Performance analysis of IEEE 802.11p DCF for multiplatooning communications with autonomous vehicles. IEEE Trans. Veh. Technol. 2017, 66, 2485–2498. [Google Scholar] [CrossRef]
- Bazzi, A.; Masini, B.; Zanella, A.; Thibault, I. On the Performance of IEEE 802.11p and LTE-V2V for the Cooperative Awareness of Connected Vehicles. IEEE Trans. Veh. Technol. 2017, 66, 10419–10432. [Google Scholar] [CrossRef]
- Yang, Y.; Fei, D.; Dang, S. Inter-vehicle cooperation channel estimation for IEEE 802.11p V2I communications. J. Commun. Netw. 2017, 19, 227–238. [Google Scholar] [CrossRef]
- Qiu, H.J.F.; Ho, I.; Tse, C.K.; Xie, Y. A Methodology for Studying 802.11p VANET Broadcasting Performance With Practical Vehicle Distribution. IEEE Trans. Veh. Technol. 2015, 64, 4756–4769. [Google Scholar] [CrossRef]
- Noor-A-Rahim, M.; Ali, G.M.; Nguyen, H.; Guan, Y.L. Performance Analysis of IEEE 802.11p Safety Message Broadcast With and Without Relaying at Road Intersection. IEEE Access 2018, 6, 23786–23799. [Google Scholar] [CrossRef]
- Wu, Q.; Xia, S.; Fan, P.; Fan, Q.; Li, Z. Velocity-Adaptive V2I Fair-Access Scheme Based on IEEE 802.11 DCF for Platooning Vehicles. Sensors 2018, 18, 4198. [Google Scholar] [CrossRef]
- Wang, P.; Wang, F.; Ji, Y.; Liu, F.; Wang, X. Performance analysis of EDCA with strict priorities broadcast in IEEE802.11p VANETs. In Proceedings of the 2014 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 3–6 February 2014. [Google Scholar] [CrossRef]
- Xu, S. Study on uncertain decision factors of logistics distribution using Mason theory. In Proceedings of the 2011 International Conference on Electric Information and Control Engineering, Wuhan, China, 15–17 April 2011. [Google Scholar] [CrossRef]
- Meighem, P.V. Performance Analysis of Communications Networks and Systems; Cambridge University Press: London, UK, 2006. [Google Scholar]
- Kramer, W.; Langenbach-Belz, M. Approximate formulae for the delay in the queuing system GI/G/1. In Proceedings of the International Teletraffic Congress, Melbourne, Australia, 10–17 November 1976. [Google Scholar]
| Model | Protocol | MAC Type | Queue Length | ACs | Transmission Type | BF/CBF |
|---|---|---|---|---|---|---|
| Li et al. [31] | 802.11p | DCF | finite | − | B | − |
| Peng et al. [32] | 802.11p | DCF | − | − | U | − |
| Wu et al. [37] | 802.11e | DCF | infinite | − | U | BF |
| Qiu et al. [35] | 802.11p | EDCA | − | 4 | B | BF |
| Noor-A-Rahim et al. [36] | 802.11p | EDCA | − | 4 | B | BF |
| Yao et al. [19] | 802.11p | EDCA | − | 2 | B | BF |
| Yao et al. [28] | 802.11p | EDCA | finite | 4 | B | BF |
| Xu et al. [29] | 802.11p | EDCA | infinite | 2 | B | BF |
| Proposed Model | 802.11p | EDCA | infinite | 2 | B | CBF |
| AC | AIFSN | TXOP Limit | ||
|---|---|---|---|---|
| 1 | 3 | 0 | ||
| 0 | 2 | 0 |
| Parameter | Value |
|---|---|
| 2 | |
| 3 | |
| Basic rate | 1 Mbps |
| Data rate | 3 Mbps |
| Length of each lane | 2000 m |
| Maximum number of vehicles | 200 |
| Minimum contention window of | 3 |
| Minimum contention window of | 3 |
| MAC header | 112 bits |
| Number of lanes | 4 |
| PHY header | 48 bits |
| Packet size | 200 bits |
| Packet arrival rate of | 5 pkts/s |
| Packet arrival rate of | 5 pkts/s |
| Propagation delay | 2 s |
| Retransmission limit | 1 |
| Slot time | 13 s |
| SIFS | 32 s |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, Q.; Xia, S.; Fan, Q.; Li, Z. Performance Analysis of IEEE 802.11p for Continuous Backoff Freezing in IoV. Electronics 2019, 8, 1404. https://doi.org/10.3390/electronics8121404
Wu Q, Xia S, Fan Q, Li Z. Performance Analysis of IEEE 802.11p for Continuous Backoff Freezing in IoV. Electronics. 2019; 8(12):1404. https://doi.org/10.3390/electronics8121404
Chicago/Turabian StyleWu, Qiong, Siyang Xia, Qiang Fan, and Zhengquan Li. 2019. "Performance Analysis of IEEE 802.11p for Continuous Backoff Freezing in IoV" Electronics 8, no. 12: 1404. https://doi.org/10.3390/electronics8121404
APA StyleWu, Q., Xia, S., Fan, Q., & Li, Z. (2019). Performance Analysis of IEEE 802.11p for Continuous Backoff Freezing in IoV. Electronics, 8(12), 1404. https://doi.org/10.3390/electronics8121404





