Mitigating ARP Cache Poisoning Attack in Software-Defined Networking (SDN): A Survey
Abstract
:1. Introduction
2. Related Work
3. Background
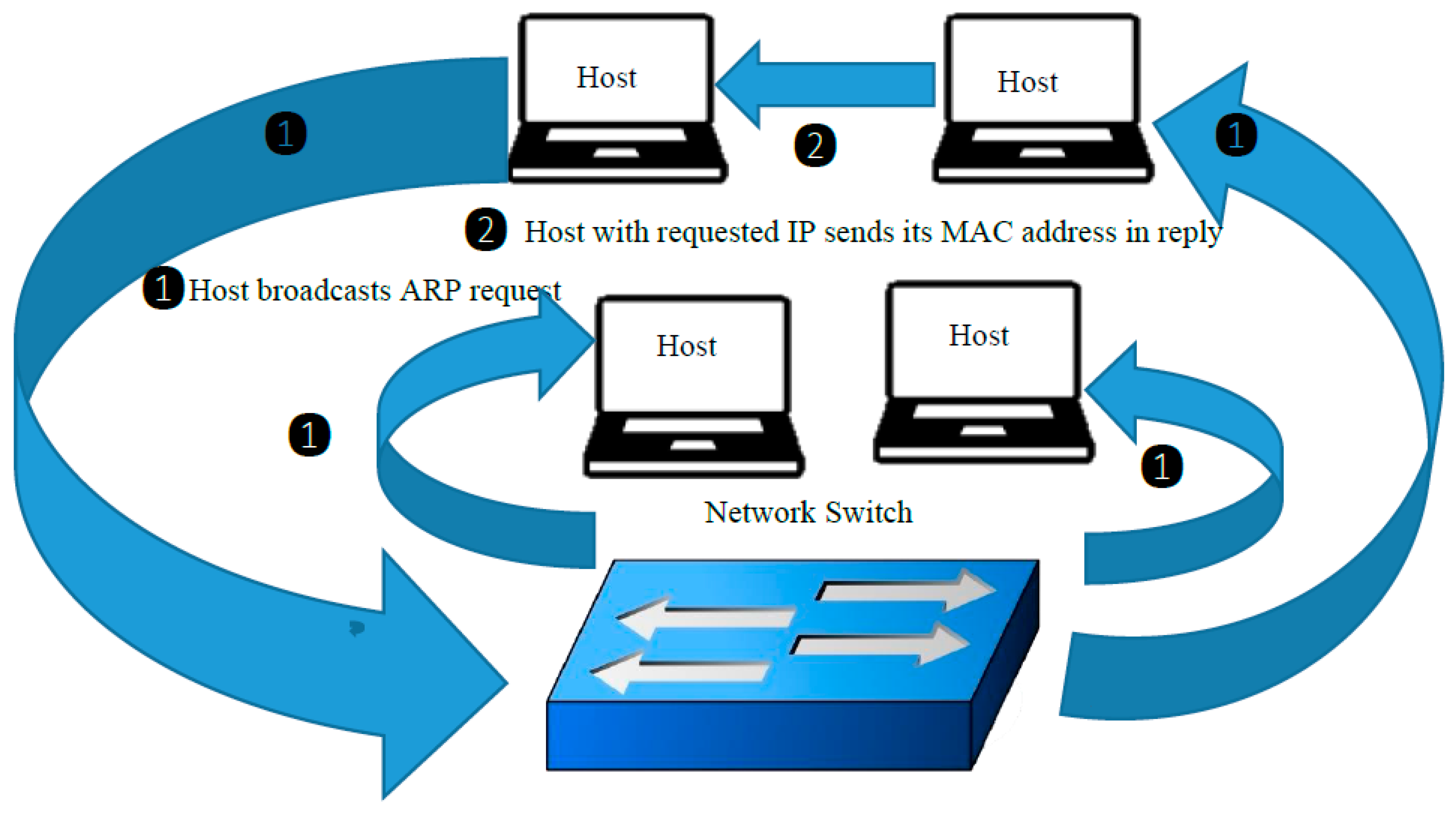
3.1. ARP Handling in Traditional Networks
ARP Cache Poisoning Attack in Traditional Networks
3.2. ARP Handling in SDN
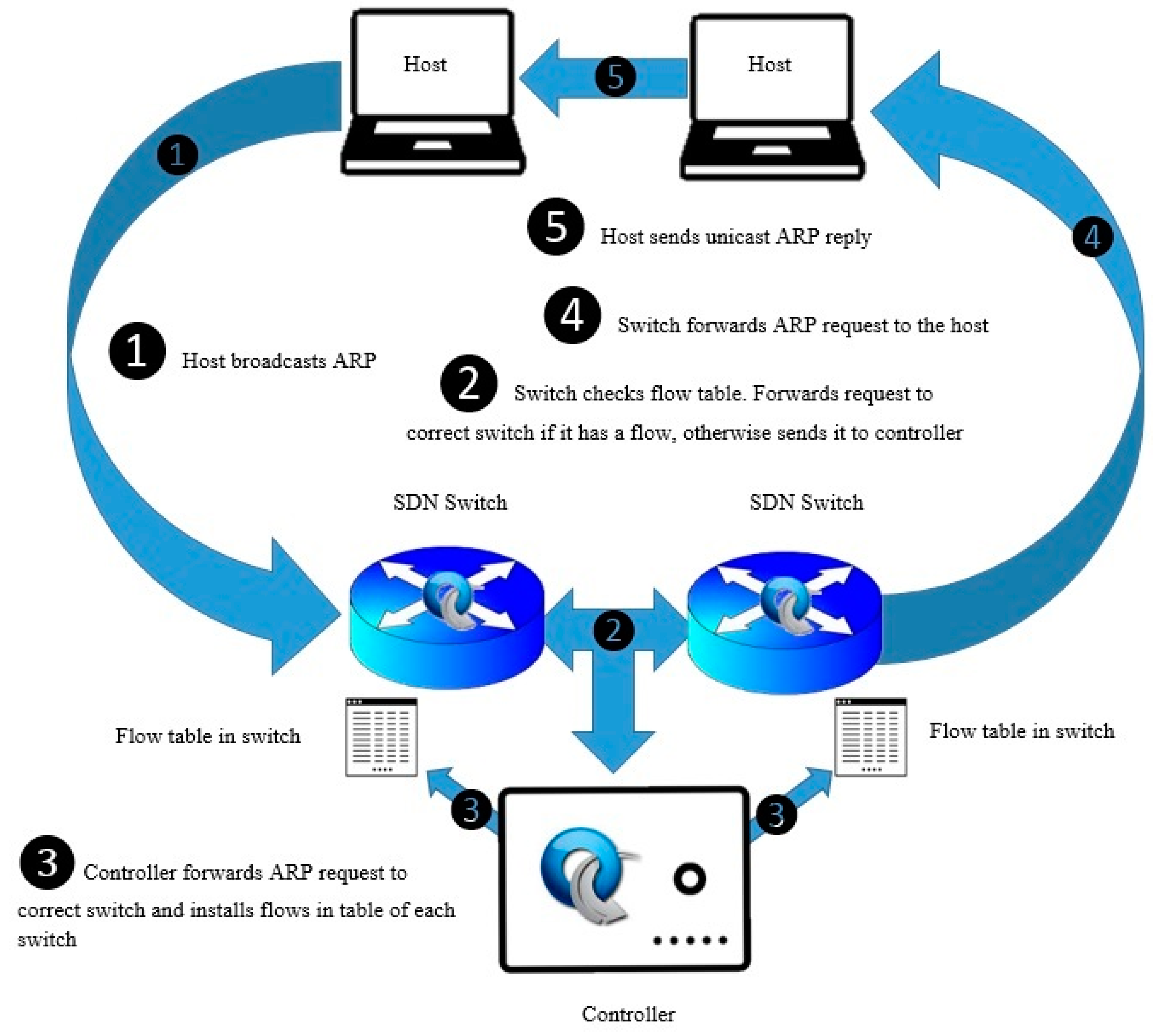
3.2.1. Regular ARP
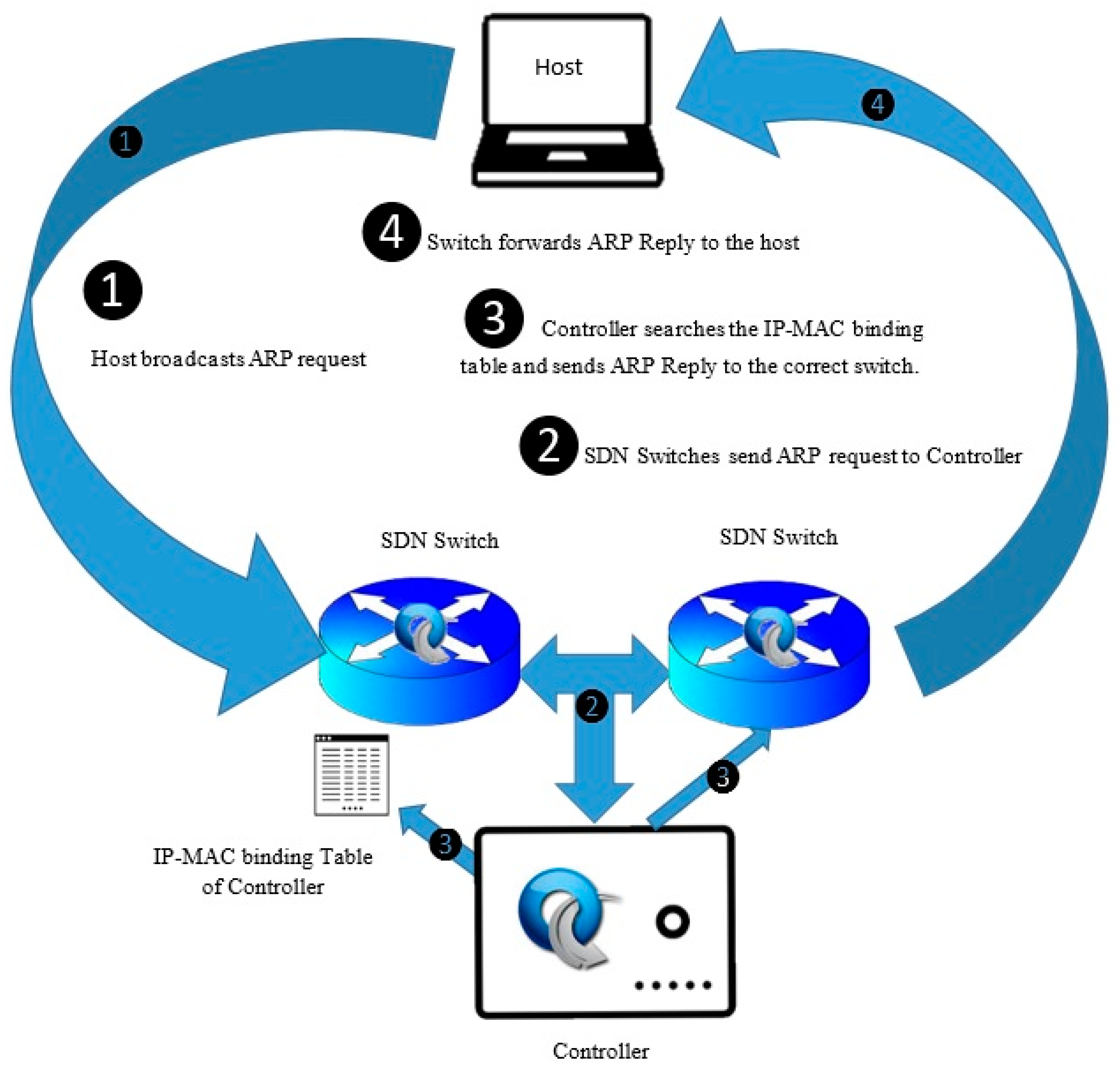
3.2.2. Proxy ARP
3.2.3. ARP Cache Poisoning in SDN
ARP Cache Poisoning in Proxy ARP
ARP Cache Poisoning in Regular ARP
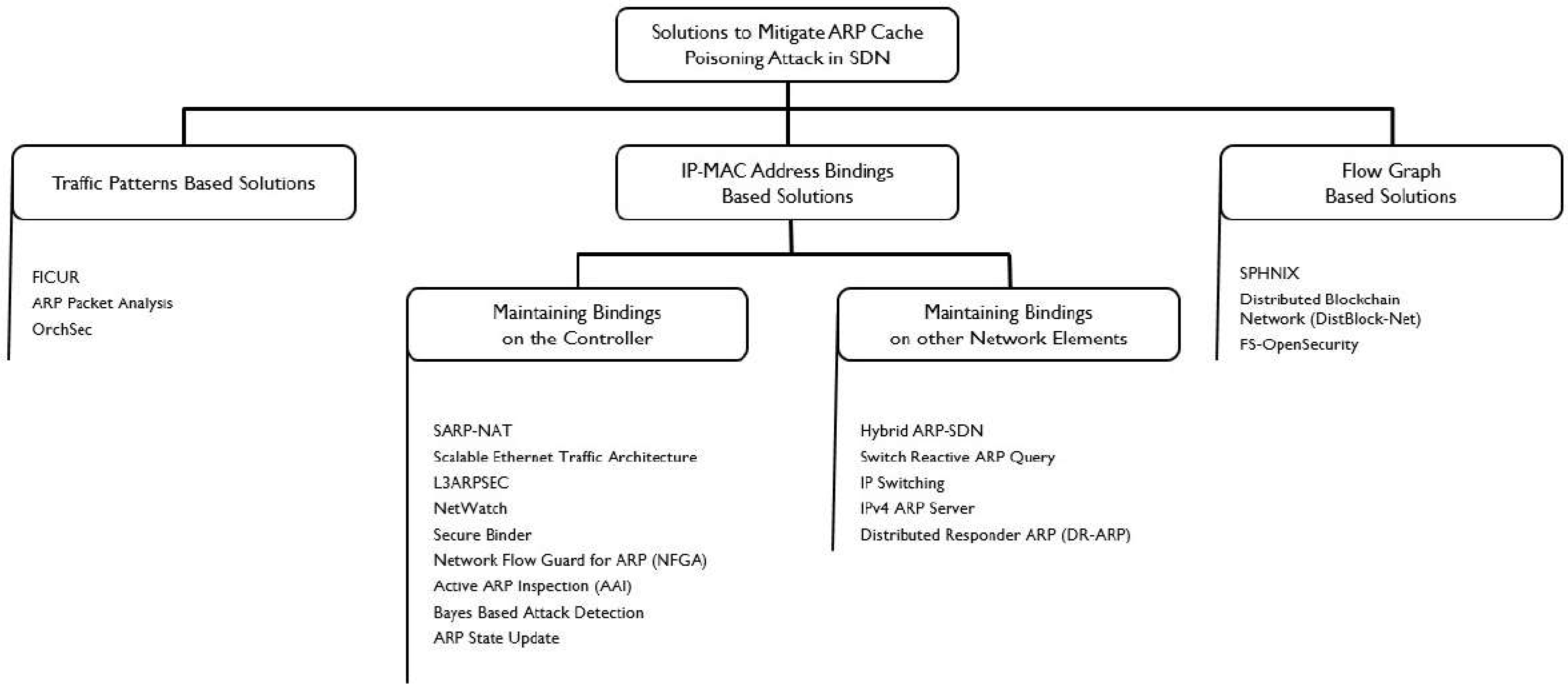
4. Solutions to Mitigate ARP Cache Poisoning Attack in SDN
4.1. Solutions Based on Analysis of Traffic Patterns
4.1.1. Traffic Pattern based Solution to ARP Related Threats (FICUR)
4.1.2. ARP-Packet Analysis
4.1.3. OrchSec
4.1.4. Issues with Solutions Based on Traffic Patterns
4.2. Solutions Based on Flow Graphs
4.2.1. SPHINX
4.2.2. Distributed BlockChain Network Architecture (DistBlockNet)
4.2.3. FS-OpenSecurity
4.2.4. Issues with Solutions Based on Flow Graphs
4.3. Solutions Based on IP-MAC Address Binding
4.3.1. IP-MAC address Bindings on the Controller
SARP_NAT
Scalable Ethernet Traffic Architecture Using SDN (SEASDN)
L3-ARPSEC
NetWatch
Secure Binder
Network Flow Guard for ARP (NFGA)
Active ARP Inspection (AAI)
Bayes-Based Attack Detection
ARP State Update
Issues with IP-MAC address bindings on the Controller Based Solutions
IP-MAC Address Bindings on the Other Network Elements
ARP in Hybrid SDN
Switch Reactive ARP Query
IP Switching
IPv4 ARP Server
Distributed Responder ARP (DR-ARP)
Issues with Maintaining IP-MAC Address Bindings on the Other Network Elements Based Solutions
5. Comparison of Different Solutions and Future Work
5.1. Attack Detection Time
5.2. Attack Mitigation Time
5.3. ARP Response Time
5.4. CPU Utilization of the Controller
5.5. Modification of SDN Architecture
5.6. Number of Hosts
5.7. Hybrid SDN
5.8. Multi-Controller Architecture
5.9. Wireless SDN
5.10. Comparison with Other Solutions
5.11. SDN Based IoT Networks
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Nunes, B.; Mendonca, M.; Nguyen, X.; Obraczka, K.; Turletti, T. A Survey of Software-defined Networking: Past, Present, and Future of Programmable Networks. IEEE Commun. Surv. Tutor. 2014, 16, 1617–1634. [Google Scholar] [CrossRef]
- Kreutz, D.; Ramos, F.; Verissimo, P.; Rothenberg, C.; Azodolmolky, S.; Uhlig, S. Software-Defined Networking: A Comprehensive Survey. Proc. IEEE 2015, 103, 14–76. [Google Scholar] [CrossRef]
- Shah, Z. Mitigating TCP Incast Issue in Cloud Data Centres using Software-Defined Networking (SDN): A Survey. KSII Trans. Internet Inf. Syst. 2018, 12, 5179–5202. [Google Scholar] [Green Version]
- Dhawan, M.; Poddar, R.; Mahajan, K.; Mann, V. SPHINX: Detecting Security Attacks in Software-Defined Networks. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 8–11 February 2015; pp. 8–11. [Google Scholar]
- Ma, H.; Ding, H.; Yang, Y.; Mi, Z.; Yang, J.Y.; Xiong, Z. Bayes-based ARP Attack Detection Algorithm for Cloud Centers. Tsinghua Sci. Technol. 2016, 21, 17–28. [Google Scholar] [CrossRef]
- Sung, Y.; Sharma, P.; Lopez, E.; Park, J. FS-OpenSecurity: A Taxonomic Modeling of Security Threats in SDN for Future Sustainable Computing. Sustainability 2016, 8, 919. [Google Scholar] [CrossRef]
- Conti, M.; Dragoni, N.; Lesyk, V. A Survey of Man in the Middle Attacks. IEEE Commun. Surv. Tutor. 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Hijazi, S.; Obaidat, M.S. A New Detection and Prevention System for ARP Attacks Using Static Entry. IEEE Syst. J. 2018, 13, 2732–2738. [Google Scholar] [CrossRef]
- Rietz, R.; Cwalinski, R.; König, H.; Brinner, A. An SDN-Based Approach to Ward Off LAN Attacks. J. Comput. Netw. Commun. 2018, 2018, 4127487. [Google Scholar] [CrossRef]
- Sasan, Z.; Salehi, M. SDN-based Defending Against ARP Poisoning Attack. J. Adv. Comput. Res. 2017, 8, 95–102. [Google Scholar]
- Bruschi, D.; Ornaghi, A.; Rosti, E. S-ARP: A Secure Address Resolution Protocol. In Proceedings of the 19th Annual Computer Security Applications Conference, Las Vegas, NV, USA, 8–12 December 2003; pp. 66–74. [Google Scholar]
- Nehra, A.; Tripathi, M.; Gaur, M.S. FICUR: Employing SDN Programmability to Secure ARP. In Proceedings of the IEEE 7th Annual Computing and Communication Workshop and Conference, Las Vegas, NV, USA, 9–11 January 2017; pp. 1–8. [Google Scholar]
- Xia, J.; Cai, Z.; Hu, G.; Xu, M. An Active Defense Solution for ARP Spoofing in OpenFlow Network. Chin. J. Electron. 2019, 28, 172–178. [Google Scholar] [CrossRef]
- Hijazi, S.; Obaidat, M. Address resolution protocol spoofing attacks and security approaches: A survey. Secur. Priv. 2019, 2, e49. [Google Scholar] [CrossRef]
- Prajapati, S.; Noorani, Z. A Survey on ARP Poisoning and Techniques for Detection and Prevention. Int. J. Adv. Res. Innov. Ideas Educ. 2017, 3, 594–601. [Google Scholar]
- Hingne, A.; Jain, S. A Survey on Various Detection and Prevention Mechanism for MITM and ARP Attacks. Int. J. Innov. Res. Comput. Commun. Eng. 2016, 4, 19918–19924. [Google Scholar]
- Meghana, J.; Subashri, T.; Vimal, R. A Survey on ARP Cache Poisoning and Techniques for Detection and Mitigation. In Proceedings of the IEEE International Conference on Signal Processing, Communication and Networking (ICSCN), Chennai, India, 16–18 March 2017; pp. 1–6. [Google Scholar]
- Kapil, J.; Manoj, J.; Jay, B. A Survey on Man in the Middle Attack. Int. J. Sci. Technol. Eng. 2016, 2, 277–280. [Google Scholar]
- Jaideep, S.; Vinit, G. A Survey of Different Strategies to Pacify ARP Poisoning Attacks in Wireless Networks. Int. J. Comput. Appl. 2015, 116, 25–28. [Google Scholar] [Green Version]
- Bhushan, B.; Sahoo, G.; Rai, A. Man-in-the-Middle Attack in Wireless and Computer Networking—A Review. In Proceedings of the IEEE International Conference on Advances in Computing, Communication & Automation, Dehradun, India, 15–16 September 2017; pp. 1–6. [Google Scholar]
- Alharbi, T.; Durando, D.; Pakzad, F.; Portmann, M. Securing ARP in Software Defined Networks. In Proceedings of the IEEE Conference on Local Computer Networks (LCN), Dubai, UAE, 7–10 November 2016; pp. 523–526. [Google Scholar]
- Bailey, J.; Stuart, S. Faucet: Deploying SDN in the enterprise. ACM Commun. 2017, 60, 45–49. [Google Scholar] [CrossRef]
- AbdelSalam, A.; El-Sisi, A.; Reddy, V. Mitigating ARP Spoofing Attacks in Software-Defined Networks. In Proceedings of the International Conference on Computer Theory and Applications (ICCTA), Alexandria, Egypt, 25–27 October 2016. [Google Scholar]
- Zaalouk, A.; Khondoker, R.; Marx, R.; Bayarou, K. OrchSec: An Orchestrator-Based Architecture for Enhancing Network-Security Using Network Monitoring and SDN Control Functions. In Proceedings of the Network Operations and Management Symposium (NOMS), Krakow, Poland, 5–9 May 2014; pp. 1–9. [Google Scholar]
- Sharma, P.; Singh, S.; Jeong, Y.; Park, J. Distblocknet: A distributed blockchains-based secure SDN architecture for IoT networks. IEEE Commun. Mag. 2017, 55, 78–85. [Google Scholar] [CrossRef]
- Karame, G. On the Security and Scalability of Bitcoin’s Blockchain. In Proceedings of the ACM Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 1861–1862. [Google Scholar]
- Gramoli, V. On the Danger of Private Blockchains. In Proceedings of the Workshop on Distributed Cryptocurrencies and Consensus Ledgers, Chicago, IL, USA, 25 July 2016. [Google Scholar]
- Saad, M.; Spaulding, J.; Njilla, L.; Kamhoua, C.; Shetty, S.; Nyang, D.; Mohaisen, A. Exploring the attack surface of blockchain: A systematic overview. arXiv 2019, arXiv:1904.03487. [Google Scholar]
- Gupta, A.; Sukheja, D.; Tiwari, A. Impact of Sybil Attack and Security Threat in Mobile Adhoc Network. Int. J. Comput. Appl. 2015, 124, 5–12. [Google Scholar] [CrossRef]
- Jehan, N.; Haneef, A. Scalable Ethernet Architecture Using SDN by Suppressing Broadcast Traffic. In Proceedings of the IEEE International Conference on Advances in Computing and Communications (ICACC), Kochi, India, 2–4 September 2015; pp. 24–27. [Google Scholar]
- Oliveira, R.; Shinoda, A.; Schweitzer, C.; Iope, R.; Prete, L. L3-ARPSec–A Secure Openflow Network Controller Module to Control and Protect the Address Resolution Protocol. In Proceedings of the XXXIII Simpósio Brasileiro Telecomunicações, Juiz de Fora, Brazil, 25 February 2015; pp. 158–162. [Google Scholar] [CrossRef]
- Balagopal, D.; Rani, X. NetWatch: Empowering Software-Defined Network Switches for Packet Filtering. In Proceedings of the IEEE International Conference on Applied and Theoretical Computing and Communication Technology (iCATccT), Davangere, India, 29–31 October 2015; pp. 837–840. [Google Scholar]
- Jero, S.; Koch, W.; Skowyra, R.; Okhravi, H.; Nita-Rotaru, C.; Bigelow, D. Identifier Binding Attacks and Defenses in Software-Defined Networks. In Proceedings of the USENIX Security Symposium, Vancouver, BC, Canada, 16–18 August 2017; pp. 415–432. [Google Scholar]
- Cox, J.; Clark, R.; Owen, H. Leveraging SDN for ARP Security. In Proceedings of the IEEE SoutheastCon, Norfolk, VA, USA, 30 March–3 April 2016; pp. 1–8. [Google Scholar]
- Kumar, S.; Tapaswi, S. A centralized detection and prevention technique against ARP poisoning. In Proceedings of the IEEE International Conference on Cyber Security, Cyber Warfare and Digital Forensic (CyberSec), Kuala Lumpur, Malaysia, 26–28 June 2012; pp. 259–264. [Google Scholar]
- Kim, Y.; Ahn, S.; Thang, N.; Choi, D.; Park, M. ARP Poisoning Attack Detection Based on ARP Update State in Software-Defined Networks. In Proceedings of the IEEE International Conference on Information Networking, Kuala Lumpur, Malaysia, 9–11 January 2019; pp. 366–371. [Google Scholar]
- Mallik, A.; Ahsan, A.; Shahadat, M.; Tsou, J. Man-in-the-middle-attack: Understanding in simple words. Int. J. Data Netw. Sci. 2019, 3, 77–92. [Google Scholar] [CrossRef]
- Fahad, U.; Rashid, A.; Faisal, U.; Muwar, I. Mitigating Address Spoofing Attacks in Hybrid SDN. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 562–570. [Google Scholar]
- Solomon, N. Mitigating Layer 2 Attacks: Re-Thinking the Division of Labor. Master’s Thesis, School of Computer Science, The Interdisciplinary Center, Herzliya, Israel, 2015. [Google Scholar]
- Al-Shaboti, M.; Welch, I.; Chen, A.; Mahmood, M. Towards Secure Smart Home IoT: Manufacturer and User Network Access Control Framework. In Proceedings of the IEEE International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 892–899. [Google Scholar]
- Matties, M. Distributed Responder ARP: Using SDN to Re-Engineer ARP from Within the Network. In Proceedings of the IEEE International Conference on Computing, Networking and Communications (ICNC), Santa Clara, CA, USA, 26–29 January 2017; pp. 678–683. [Google Scholar]
- Sinha, Y.; Haribabu, K. A survey: Hybrid SDN. J. Netw. Comput. Appl. 2017, 100, 35–55. [Google Scholar]
- Amin, R.; Reisslein, M.; Shah, N. Hybrid SDN networks: A survey of existing approaches. IEEE Commun. Surv. Tutor. 2018, 20, 3259–3306. [Google Scholar] [CrossRef]
- Vissicchio, S.; Vanbever, L.; Bonaventure, O. Opportunities and research challenges of hybrid software defined networks. ACM Comput. Commun. Rev. 2014, 44, 70–75. [Google Scholar] [CrossRef]
- Blial, O.; Ben, M.; Benaini, R. An overview on SDN architectures with multiple Controllers. J. Comput. Netw. Commun. 2016, 2016, 9396525. [Google Scholar] [CrossRef]
- Phemius, K.; Bouet, M.; Leguay, J. Disco: Distributed Multi-Domain SDN Controllers. In Proceedings of the IEEE Network Operations and Management Symposium (NOMS), Krakow, Poland, 5–9 May 2014; pp. 1–4. [Google Scholar]
- Qi, C.; Wu, J.; Hu, H.; Cheng, G.; Liu, W.; Ai, J.; Yang, C. An Intensive Security Architecture with Multi-Controller for SDN. In Proceedings of the IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), San Francisco, CA, USA, 10–14 April 2016; pp. 401–402. [Google Scholar]
- Shu, Z.; Wan, J.; Li, D.; Lin, J.; Vasilakos, A.; Imran, M. Security in software-defined networking: Threats and countermeasures. Mob. Netw. Appl. 2016, 21, 764–776. [Google Scholar] [CrossRef]
- Zander, J.; Mähönen, P. Riding the data tsunami in the cloud: Myths and challenges in future wireless access. IEEE Commun. Mag. 2013, 51, 145–151. [Google Scholar] [CrossRef]
- Hätönen, S.; Savolainen, P.; Rao, A.; Flinck, H.; Tarkoma, S. SWIFT: Bringing SDN-Based Flow Management to Commodity Wi-Fi Access Points. In Proceedings of the IEEE Networking Conference and Workshops, Zurich, Switzerland, 14–16 May 2018; pp. 1–9. [Google Scholar]
- Software Defined Networks. Available online: https://www.alliedtelesis.com/solutions/software-defined-networks (accessed on 28 September 2019).
- Wi-Fi & SDN…Why? Available online: https://blogs.arubanetworks.com/industries/wi-fi-sdn-why/ (accessed on 28 September 2019).
- Cisco Wireless LAN Controller. Available online: https://www.cisco.com/c/en/us/products/wireless/wireless-lan Controller/index.html (accessed on 28 September 2019).
- Zarca, A.; Garcia-Carrillo, D.; Bernabe, B.; Ortiz, J.; Marin-Perez, R.; Skarmeta, A. Enabling Virtual AAA Management in SDN-Based IoT Networks. Sensors 2019, 19, 295. [Google Scholar] [CrossRef] [PubMed]
- Bedhief, I.; Kassar, M.; Aguili, T.; Foschini, L.; Bellavista, P. Self-Adaptive Management of SDN Distributed Controllers for Highly Dynamic IoT Networks. In Proceedings of the IEEE International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 2098–2104. [Google Scholar]
- Salman, O.; Elhajj, I.; Chehab, A.; Kayssi, A. IoT survey: An SDN and fog computing perspective. Comput. Netw. 2018, 143, 221–246. [Google Scholar] [CrossRef]
- Ahmed, S.; Hassan, R.; Othman, E.; Ahmad, I.; Kenish, Y. Impacts evaluation of DoS attacks over IPv6 neihbor discovery protocol. J. Comput. Sci. 2019, 15, 702–727. [Google Scholar] [CrossRef]
- Barbhuiya, A.; Bansal, G.; Kumar, N.; Biswas, S.; Nandi, S. Detection of neighbor discovery protocol based attacks in IPv6 network. Netw. Sci. 2013, 2, 91–113. [Google Scholar] [CrossRef]
| Solution | Advantage | Issue | Proxy ARP Attack Prevention | Regular ARP Attack Prevention | Spoofed ARP Requests Handling | Spoofed ARP Replies Handling |
|---|---|---|---|---|---|---|
| FICUR [12] | Quickly detects the attack | Controller CPU utilization is not considered | Yes (only for spoofed ARP Requests) | Yes (only for spoofed ARP Requests) | Yes | No |
| ARP-Packet Analysis [23] | Low CPU utilization at the Controller | Tested on a small network | Yes | Yes | Yes | Yes |
| OrchSec [24] | Can be deployed in a Multi-Controller Architecture | Attack detection time is not calculated | Yes | Yes | Not explained | Not explained |
| Solution | Advantage | Issue | Proxy ARP Attack Prevention | Regular ARP Attack Prevention | Spoofed ARP Requests Handling | Spoofed ARP Replies Handling |
|---|---|---|---|---|---|---|
| SPHINX [4] | Can be deployed over four different Controllers | Attack detection time is dependent on processing time of Packet_In messages | Yes | Yes | Yes | Not explained |
| DistBlockNet [25] | Scalable Architecture | Attack detection time is not calculated | Yes | Yes | Yes | Not explained |
| FS-OpenSecurity [6] | Quickly detects the attack | No simulation or experimental results are provided | Yes | Yes | Not explained | Not explained |
| Solution | Advantage | Issue | Proxy ARP Attack Prevention | Regular ARP Attack Prevention | Spoofed ARP Requests Handling | Spoofed ARP Replies Handling |
|---|---|---|---|---|---|---|
| SARP-NAT [21] | Less time taken to handle ARP request compared to regular ARP | Too much load on the Controller for large number of hosts | Yes | Yes | Yes | Yes |
| SEASDN [30] | Less CPU utilization of the Controller | Time taken to detect ARP spoofing attack is not computed | Yes | No | Yes | Yes |
| L3-ARPSEC [31] | Can effectively detect and block the attacker | Overhead of maintaining Timers | Yes | No | Yes | Yes |
| NetWatch [32] | Quickly detects the attack than standard POX Controller | Cannot detect the attack if number of spoofed ARP packets is small | Yes | No | Yes | Yes |
| Secure Binder [33] | Protect against identifier bindings based attacks | Overhead to implement IEEE 802.1x protocol. | Yes | No | Yes | Yes |
| NFGA [34] | Detect spoofed ARP replies | CPU utilization of the Controller is not determined | Yes (Spoofed ARP replies only) | No | No | Yes |
| AAI [13] | Low ARP response time even with 1000 hosts | Attack detection time is not computed | Yes (Spoofed ARP replies only) | No | No | Yes |
| Bayes Based Attack Detection [5] | Increases the accuracy to detect the attacker | Cannot detect the attacker if attack frequency is low | Yes | No | Yes | Yes |
| ARP State Update [36] | Detects the attack carried out by spoofed ARP replies | Attack detection time is not calculated | Yes (Spoofed ARP replies only) | No | No | Yes |
| Solution | Advantage | Issue | Proxy ARP Attack Prevention | Regular ARP Attack Prevention | Spoofed ARP Requests Handling | Spoofed ARP Replies Handling |
|---|---|---|---|---|---|---|
| ARP in Hybrid SDN [38] | Detects attack in a hybrid network | Server can be a single point of failure | Yes | No | Yes | Yes |
| Switch Reactive ARP Query [39] | Less load on the Controller | Overhead to send ARP packets to validate hosts. | Yes | No | Yes | Yes |
| IP Switching [9] | Using IP address for switching | Delay to replace virtual MAC address with real MAC address | Yes (only from spoofed ARP requests) | No | Yes | No |
| IPv4 ARP Server [40] | Easily handle 50 parallel ARP requests | Solution cannot be used in traditional networks | Yes | No | Yes | Yes |
| DR-ARP [41] | Less ARP completion time even with large number of hosts | Attack detection time is not computed | Yes (only from spoofed ARP requests) | No | Yes | No |
| Taxonomy of Solutions | Solution | Attack Detection Time | ARP Response Time | Controller Utilization | SDN Architecture Modified | Number of Hosts | Hybrid SDN | Multi-Controller Architecture |
|---|---|---|---|---|---|---|---|---|
| Traffic Patterns Based Solutions [12,23,24] | FICUR | Yes | No | No | No | 03 | No | No |
| ARP Packet Analysis | Yes | No | Yes | No | 03 | No | No | |
| OrchSec | No | No | No | Yes | N/A | No | Yes | |
| Flow Graph Based Solutions [4,6,25] | SPHINX | Yes | No | Yes | No | 1000 | No | No |
| DistBlock-Net | No | No | Yes | Yes | 6000 | No | Yes | |
| FS-Open Security | No | No | No | No | N/A | No | No | |
| IP-MAC Address Bindings on the Controller Based Solutions [5,13,21,30,31,32,33,34,36] | SARP- NAT | No | Yes | Yes | No | 03 | No | No |
| SEASDN | No | No | Yes | No | 50 | No | No | |
| L3-ARPSEC | No | No | No | No | 03 | No | No | |
| NetWatch | No | Yes | No | No | 04 | No | No | |
| Secure Binder | Yes | No | Yes | Yes | 04 | No | No | |
| NFGA | No | No | No | No | 06 | No | No | |
| AAI | No | Yes | Yes | No | 1000 | No | No | |
| Bayes Based Attack Detection | No | No | No | No | 1000 | No | No | |
| ARP State Update | No | No | No | No | 04 | No | No | |
| IP-MAC Address Bindings on Other Network Elements Based Solutions [9,38,39,40,41] | Hybrid ARP-SDN | Yes | No | Yes | Yes | 09 | Yes | No |
| Switch Reactive ARP Query | No | No | Yes | Yes | 02 | No | No | |
| IP Switching | No | No | No | Yes | 02 | No | No | |
| IPv4 ARP Server | No | Yes | No | Yes | 50 | No | No | |
| DR-ARP | No | Yes | No | Yes | 48 | No | No |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shah, Z.; Cosgrove, S. Mitigating ARP Cache Poisoning Attack in Software-Defined Networking (SDN): A Survey. Electronics 2019, 8, 1095. https://doi.org/10.3390/electronics8101095
Shah Z, Cosgrove S. Mitigating ARP Cache Poisoning Attack in Software-Defined Networking (SDN): A Survey. Electronics. 2019; 8(10):1095. https://doi.org/10.3390/electronics8101095
Chicago/Turabian StyleShah, Zawar, and Steve Cosgrove. 2019. "Mitigating ARP Cache Poisoning Attack in Software-Defined Networking (SDN): A Survey" Electronics 8, no. 10: 1095. https://doi.org/10.3390/electronics8101095
APA StyleShah, Z., & Cosgrove, S. (2019). Mitigating ARP Cache Poisoning Attack in Software-Defined Networking (SDN): A Survey. Electronics, 8(10), 1095. https://doi.org/10.3390/electronics8101095




