Moving to the Edge-Cloud-of-Things: Recent Advances and Future Research Directions
Abstract
1. Introduction
- Present Cloud, Edge and IoT concepts in a comprehensive way for readers from different areas.
- Highlight the advancement of the Edge-Cloud-of-Things paradigm and its support to the current innovation in various domains (i.e., healthcare).
- Provide a summary of the most common technologies related to Edge Computing.
- Conduct a case study to demonstrate the examination of the impact of location based IoT services in Edge environment.
- Discuss the most recent issues and future trends that need to be addressed for the development of sustainable IoT applications and services under the Edge-Cloud-of-Things paradigm.
2. Review of Edge Paradigms
2.1. Fog Computing
2.2. Cloudlet
2.3. Ad-Hoc Clouds
2.4. Mobile Edge Computing
3. Moving Cloud to Edge Computing
3.1. Summary of Key Observations
4. Roles of Edge Paradigms
4.1. Edge as an Extender of Cloud Services
4.2. Edge as a Middle Layer
4.3. Coordinated Fog-to-Cloud Resources
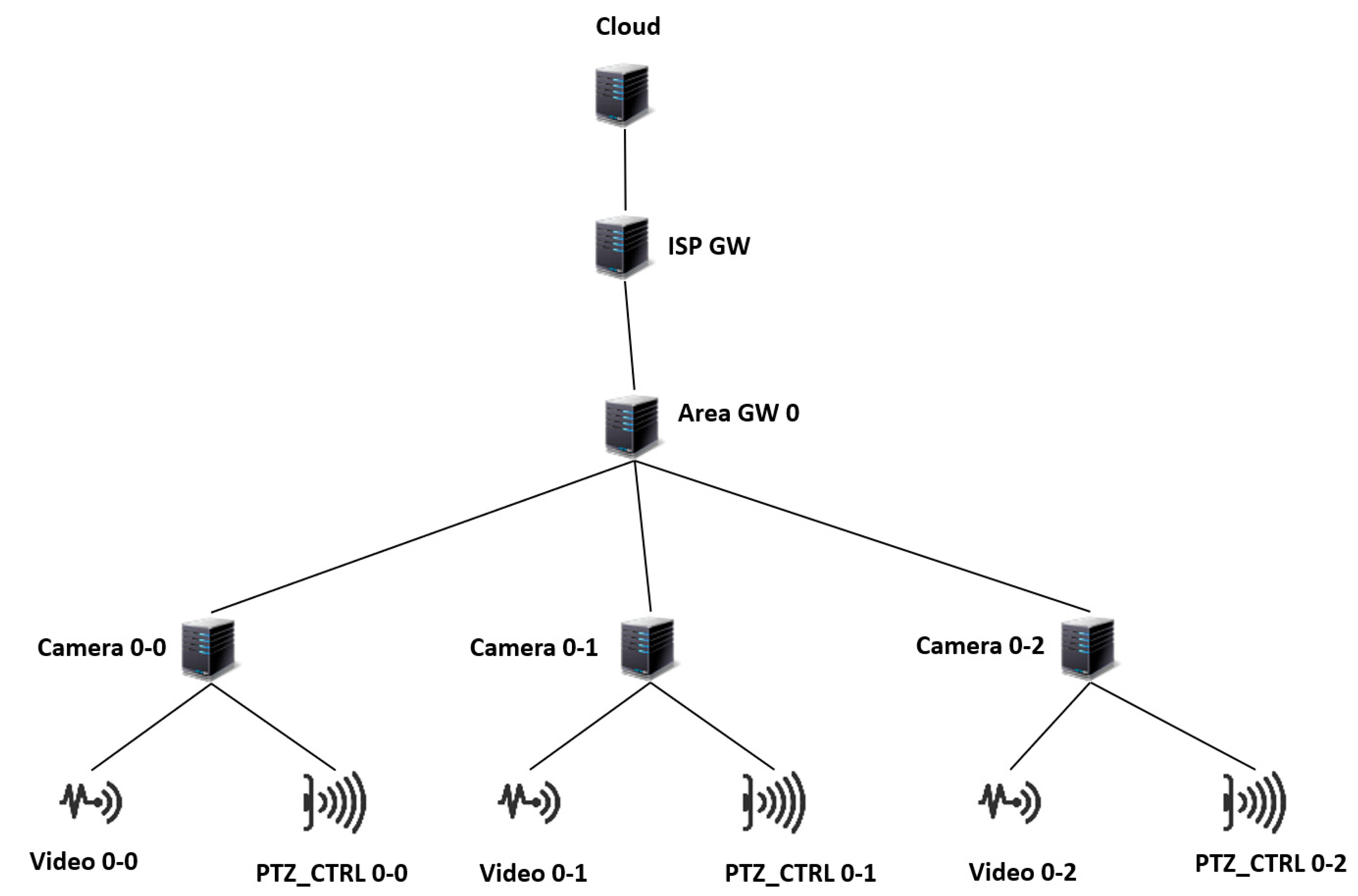
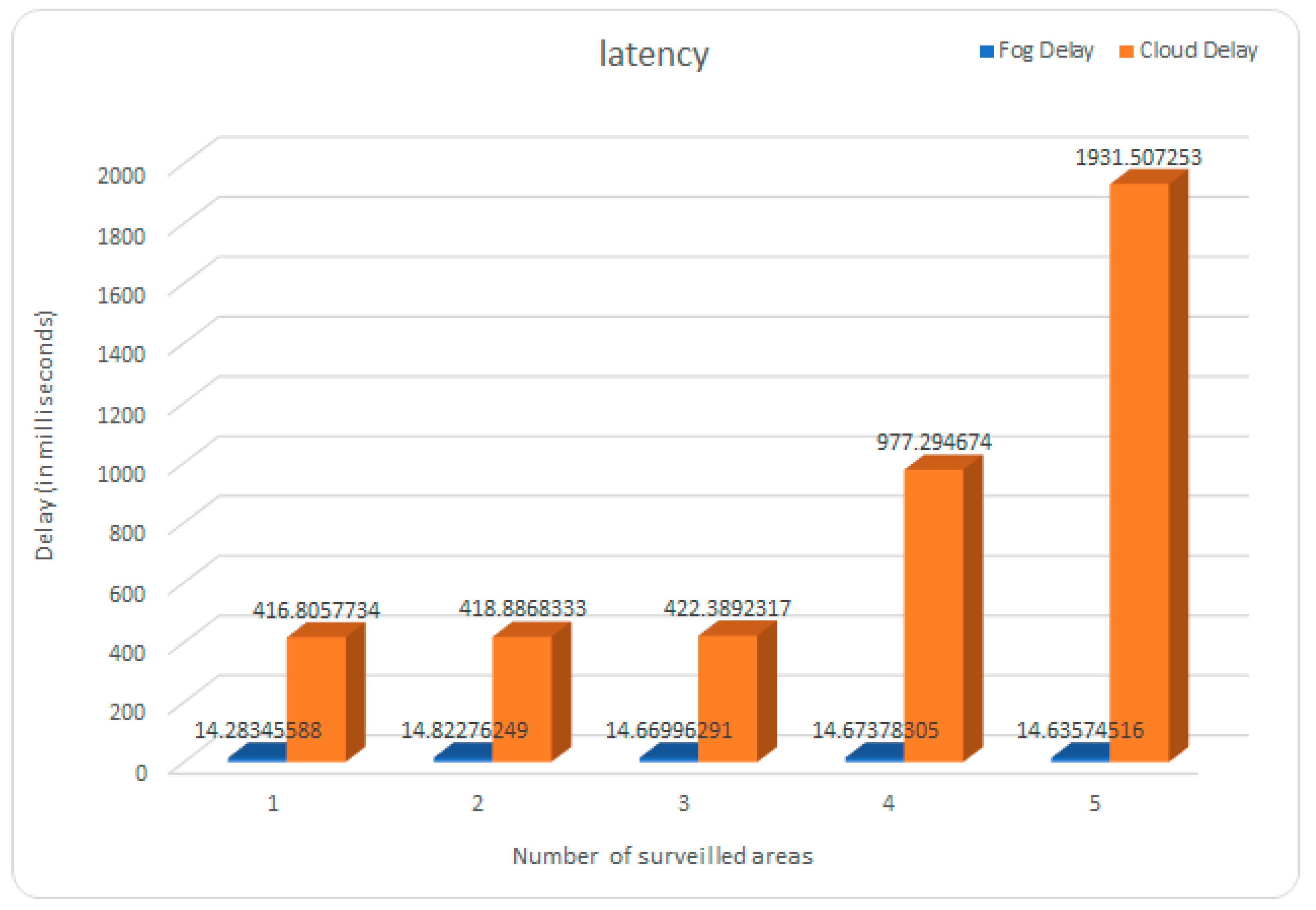
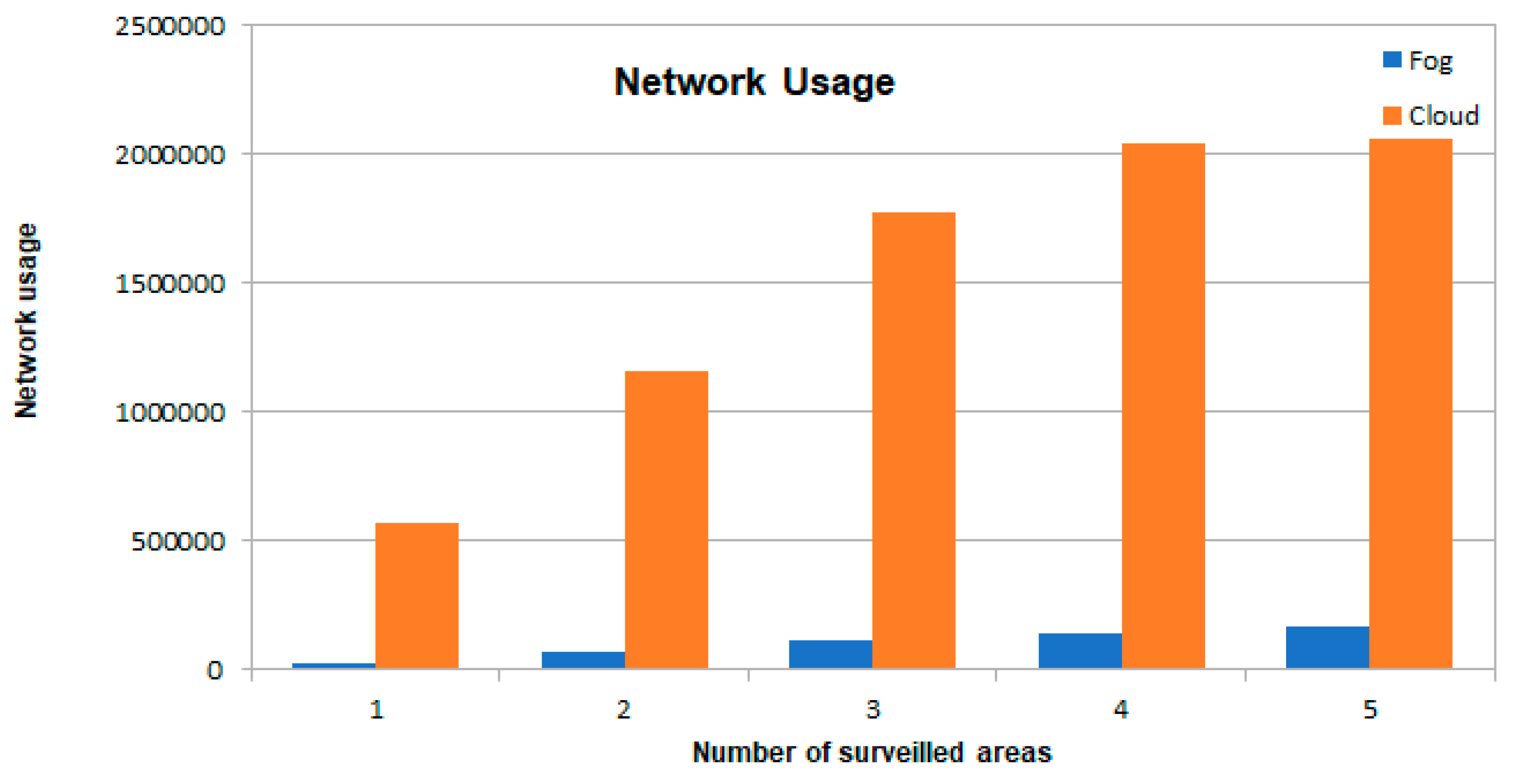
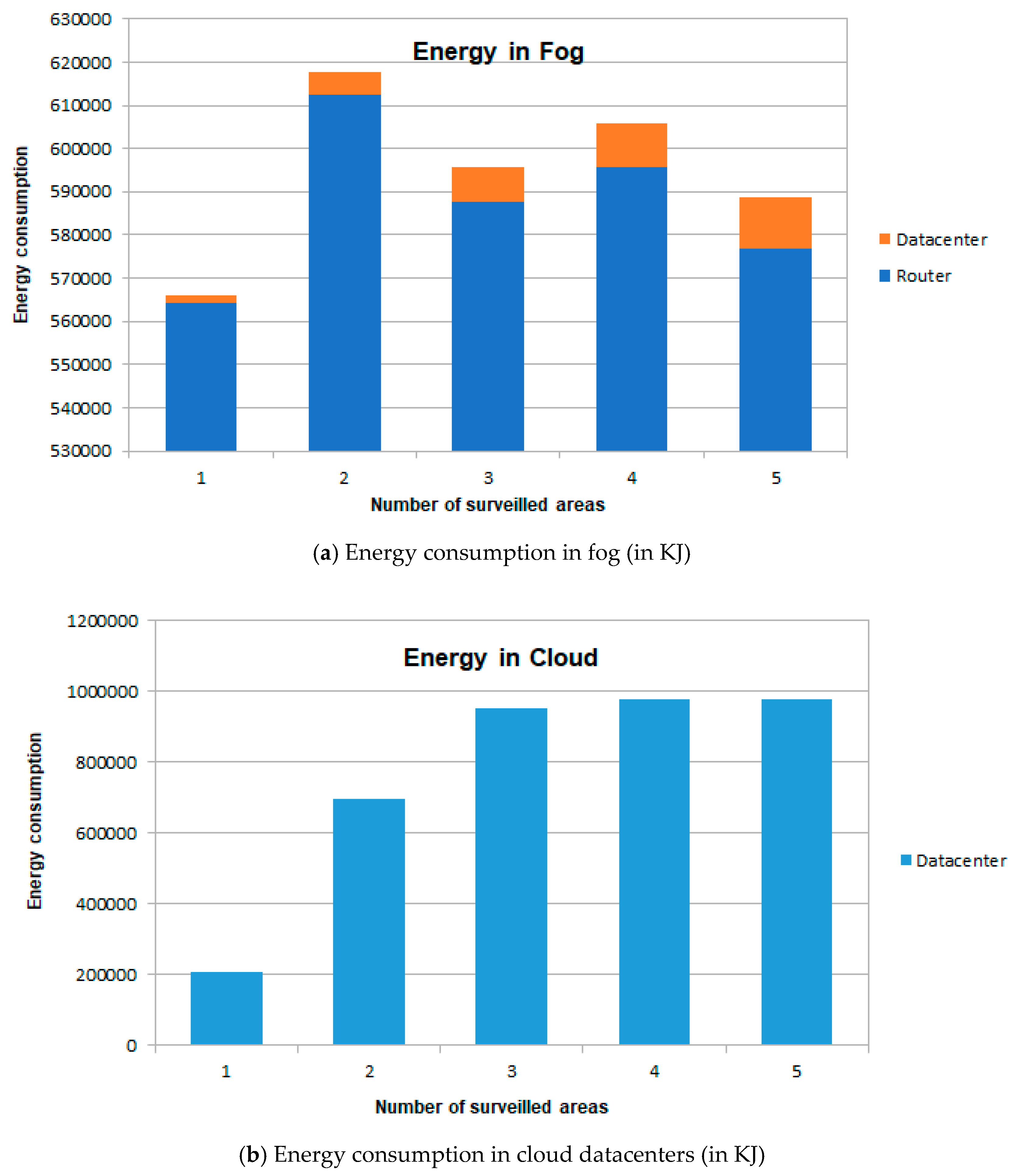
5. Case Study
5.1. Description of the Case Study
5.2. Discussion of Results
6. Challenges and Research Directions
6.1. Interoperable Middleware Platforms for Edge Computing
6.2. Edge Analytics for Big Data
6.3. Social Networks into Edge Computing
6.4. Security in Edge Computing
7. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Misra, G.; Kumar, V.; Agarwal, A.; Agarwal, K. Internet of things (iot)—A technological analysis and survey on vision, concepts, challenges, innovation directions, technologies, and applications (an upcoming or future generation computer communication system technology). Am. J. Electr. Electron. Eng. 2016, 4, 23–32. [Google Scholar]
- Lee, I.; Lee, K. The Internet of Things (IoT): Applications, investments, and challenges for enterprises. Bus. Horiz. 2015, 58, 431–440. [Google Scholar] [CrossRef]
- Petrolo, R.; Loscri, V.; Mitton, N. Towards a smart city based on cloud of things, a survey on the smart city vision and paradigms. Trans. Emerg. Telecommun. Technol. 2017, 28, e2931. [Google Scholar] [CrossRef]
- Santos, J.; Leroux, P.; Wauters, T.; Volckaert, B.; De Turck, F. Anomaly detection for Smart City applications over 5G low power wide area networks. In Proceedings of the NOMS 2018-2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018; pp. 1–9. [Google Scholar]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- de Assuncao, M.D.; da Silva Veith, A.; Buyya, R. Distributed data stream processing and edge computing: A survey on resource elasticity and future directions. J. Netw. Comput. Appl. 2018, 103, 1–17. [Google Scholar] [CrossRef]
- Khodashenas, P.S.; Ruiz, C.; Siddiqui, M.S.; Betzler, A.; Riera, J.F. The role of Edge Computing in future 5G mobile networks: Concept and challenges. Cloud Fog Comput. 5G Mob. Netw. 2017, 70, 349. [Google Scholar]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A survey on mobile edge computing: The communication perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef]
- Abbas, N.; Zhang, Y.; Taherkordi, A.; Skeie, T. Mobile edge computing: A survey. IEEE Internet Things J. 2018, 5, 450–465. [Google Scholar] [CrossRef]
- Roman, R.; Lopez, J.; Mambo, M. Mobile edge computing, fog et al.: A survey and analysis of security threats and challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef]
- Yi, S.; Qin, Z.; Li, Q. Security and privacy issues of fog computing: A survey. In Proceedings of the International Conference on Wireless Algorithms, Systems, and Applications, Qufu, China, 10–12 August 2015; pp. 685–695. [Google Scholar]
- Yi, S.; Qin, Z.; Li, Q. A survey of fog computing: Concepts, applications and issues. In Proceedings of the 2015 Workshop on Mobile Big Data, Hangzhou, China, 22–25 June 2015; pp. 37–42. [Google Scholar]
- Mukherjee, M.; Shu, L.; Wang, D. Survey of Fog Computing: Fundamental, Network Applications, and Research Challenges. IEEE Commun. Surv. Tutor. 2018, 20, 1826–1857. [Google Scholar] [CrossRef]
- Mouradian, C.; Naboulsi, D.; Yangui, S.; Glitho, R.H.; Morrow, M.J.; Polakos, P.A. A Comprehensive Survey on Fog Computing: State-of-the-art and Research Challenges. IEEE Commun. Surv. Tutor. 2017, 20, 416–464. [Google Scholar] [CrossRef]
- Taleb, T.; Samdanis, K.; Mada, B.; Flinck, H.; Dutta, S.; Sabella, D. On multi-access edge computing: A survey of the emerging 5G network edge cloud architecture and orchestration. IEEE Commun. Surv. Tutor. 2017, 19, 1657–1681. [Google Scholar] [CrossRef]
- Kitanov, S.; Monteiro, E.; Janevski, T. 5G and the Fog—Survey of related technologies and research directions. In Proceedings of the 2016 18th Mediterranean Electrotechnical Conference (MELECON), Lemesos, Cyprus, 18–20 April 2016; pp. 1–6. [Google Scholar]
- Mahmud, R.; Kotagiri, R.; Buyya, R. Fog computing: A taxonomy, survey and future directions. In Internet of Everything; Springer: Singapore, 2018; pp. 103–130. [Google Scholar]
- Simmhan, Y. Big Data and Fog Computing. arXiv, 2017; preprint. arXiv:1712.09552. [Google Scholar]
- Mach, P.; Becvar, Z. Mobile edge computing: A survey on architecture and computation offloading. IEEE Commun. Surv. Tutor. 2017, 19, 1628–1656. [Google Scholar] [CrossRef]
- Bilal, K.; Khalid, O.; Erbad, A.; Khan, S.U. Potentials, trends, and prospects in edge technologies: Fog, cloudlet, mobile edge, and micro data centers. Comput. Netw. 2018, 130, 94–120. [Google Scholar] [CrossRef]
- Ahmed, E.; Rehmani, M.H. Mobile edge computing: Opportunities, solutions, and challenges. Future Gener. Comput. Syst. 2017, 70, 59–63. [Google Scholar] [CrossRef]
- The NIST Definition of Fog Computing. Available online: https://csrc.nist.gov (accessed on 28 January 2018).
- Zhou, B.; Buyya, R. Augmentation Techniques for Mobile Cloud Computing: A Taxonomy, Survey, and Future Directions. ACM Comput. Surv. (CSUR) 2018, 51, 13. [Google Scholar] [CrossRef]
- Dolui, K.; Datta, S.K. Comparison of edge computing implementations: Fog computing, cloudlet and mobile edge computing. In Proceedings of the 5th Workshop on All Things Cellular: Operations, Applications and Challenges (GIoTS), Geneva, Switzerland, 6–9 June 2017. [Google Scholar]
- Wang, K.; Shen, M.; Cho, J.; Banerjee, A.; Van der Merwe, J.; Webb, K. Mobiscud: A fast moving personal cloud in the mobile network. In Proceedings of the 5th Workshop on All Things Cellular: Operations, Applications and Challenges, London, UK, 17 August 2015; pp. 19–24. [Google Scholar]
- Panigrahi, C.R.; Sarkar, J.L.; Pati, B. Transmission in mobile cloudlet systems with intermittent connectivity in emergency areas. Digit. Commun. Netw. 2018, 4, 69–75. [Google Scholar] [CrossRef]
- Mori, T.; Nakashima, M.; Ito, T. SpACCE: A sophisticated ad hoc cloud computing environment built by server migration to facilitate distributed collaboration. Int. J. Space-Based Situat. Comput. 2012, 2, 230–239. [Google Scholar] [CrossRef]
- Pippal, S.K.; Kushwaha, D.S. A simple, adaptable and efficient heterogeneous multi-tenant database architecture for ad hoc cloud. J. Cloud Comput. Adv. Syst. Appl. 2013, 2, 5. [Google Scholar] [CrossRef]
- Bandyopadhyay, A.; Mukherjee, N. An Approach to Predict Desktop Uptime for Job Allocation in Ad-Hoc Cloud. In Proceedings of the 47th International Conference on Parallel Processing Companion, Eugene, OR, USA, 13–16 August 2018; p. 21. [Google Scholar]
- Li, B.; Pei, Y.; Wu, H.; Liu, Z.; Liu, H. Computation offloading management for vehicular ad hoc cloud. In Proceedings of the International Conference on Algorithms and Architectures for Parallel Processing, Dalian, China, 24–27 August 2014; Springer: Cham, Germany, 2014; pp. 728–739. [Google Scholar]
- Hasan, R.; Hossain, M.; Khan, R. Aura: An incentive-driven ad-hoc IoT cloud framework for proximal mobile computation offloading. Future Gener. Comput. Syst. 2018, 86, 821–835. [Google Scholar] [CrossRef]
- Shila, D.M.; Shen, W.; Cheng, Y.; Tian, X.; Shen, X.S. AMCloud: Toward a secure autonomic mobile ad hoc cloud computing system. IEEE Wirel. Commun. 2017, 24, 74–81. [Google Scholar] [CrossRef]
- Jebadurai, I.J.; Rajsingh, E.B.; Paulraj, G.J.L. A Novel Node Collusion Method for Isolating Sinkhole Nodes in Mobile Ad Hoc Cloud. In Advances in Big Data and Cloud Computing; Springer: Singapore, 2018; pp. 319–329. [Google Scholar]
- Varghese, B.; Buyya, R. Next generation cloud computing: New trends and research directions. Future Gener. Comput. Syst. 2018, 79, 849–861. [Google Scholar] [CrossRef]
- Hu, G.; Tay, W.P.; Wen, Y. Cloud robotics: Architecture, challenges and applications. IEEE Netw. 2012, 26, 21–27. [Google Scholar] [CrossRef]
- Mora, H.; Gil, D.; Terol, R.M.; Azorín, J.; Szymanski, J. An IoT-Based Computational Framework for Healthcare Monitoring in Mobile Environments. Sensors 2017, 17, 2302. [Google Scholar] [CrossRef] [PubMed]
- Ba, H.; Heinzelman, W.; Janssen, C.A.; Shi, J. Mobile computing-A green computing resource. In Proceedings of the 2013 IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 7–10 April 2013; pp. 4451–4456. [Google Scholar]
- NativeBoinc for Android. Available online: http://www.nativeboinc.org/site/uncat/start (accessed on 28 January 2018).
- Marinelli, E.E. Hyrax: Cloud Computing on Mobile Devices Using MapReduce; No. CMU-CS-09-164; Carnegie-Mellon Univ Pittsburgh PA School of Computer Science: Pittsburgh, PA, USA, 2009. [Google Scholar]
- Benedetto, J.I.; Valenzuela, G.; Sanabria, P.; Neyem, A.; Navón, J.; Poellabauer, C. MobiCOP: A Scalable and Reliable Mobile Code Offloading Solution. Wirel. Commun. Mob. Comput. 2018, 2018, 8715294. [Google Scholar] [CrossRef]
- MF2C. Available online: http://www.mf2c-project.eu/ (accessed on 1 October 2018).
- Butterfield, E.H. Fog Computing with Go: A Comparative Study. Bachelor’s Thesis, Claremont McKenna College, Claremont, CA, USA, April 2016. [Google Scholar]
- Stantchev, V.; Barnawi, A.; Ghulam, S.; Schubert, J.; Tamm, G. Smart items, fog and cloud computing as enablers of servitization in healthcare. Sens. Transducers 2015, 185, 121. [Google Scholar]
- Accelerating Innovation and Collaboration for the Next Stage. Available online: http://www.ntt.co.jp/news2013/1311ehzt/pdf/xgxf131108d_all.pdf (accessed on 1 October 2018).
- Announcing the “Edge Computing” Concept and the “Edge Accelerated Web Platform” Prototype to Improve Response Time of Cloud Applications. Available online: http://www.ntt.co.jp/news2014/1401e/140123a.html (accessed on 1 October 2018).
- Cirani, S.; Ferrari, G.; Iotti, N.; Picone, M. The IoT hub: A fog node for seamless management of heterogeneous connected smart objects. In Proceedings of the 2015 12th Annual IEEE International Conference on Sensing, Communication, and Networking-Workshops (SECON Workshops), Seattle, WA, USA, 22–25 June 2015; pp. 1–6. [Google Scholar]
- Ha, K.; Chen, Z.; Hu, W.; Richter, W.; Pillai, P.; Satyanarayanan, M. Towards wearable cognitive assistance. In Proceedings of the 12th Annual International Conference on Mobile Systems, Applications, and Services, Bretton Woods, NH, USA, 16–19 June 2014; pp. 68–81. [Google Scholar]
- Orsini, G.; Bade, D.; Lamersdorf, W. Computing at the mobile edge: Designing elastic android applications for computation offloading. In Proceedings of the 2015 8th IFIP Wireless and Mobile Networking Conference (WMNC), Munich, Germany, 5–7 October 2015; pp. 112–119. [Google Scholar]
- Cisco Kinetic. Available online: https://www.cisco.com/c/en/us/solutions/internet-of-things/iot-kinetic.html#~stickynav=1 (accessed on 1 October 2018).
- Vortex. Available online: http://www.prismtech.com/vortex (accessed on 1 October 2018).
- Nokia Multi-Access Edge Computing. Available online: https://networks.nokia.com/solutions/multi-access-edge-computing#tab-highlights (accessed on 1 October 2018).
- Cisco IOx. Available online: https://www.cisco.com/c/en/us/products/cloud-systems-management/iox/index.html (accessed on 1 October 2018).
- Garcıa, M.; Fuentes, P.; Odriozola, M.; Vallejo, E.; Beivide, R. FOGSim Interconnection Network Simulator; University of Cantabria: Cantabria, Spain, 2014. [Google Scholar]
- Banerjee, S.; Liu, P.; Patro, A.; Willis, D. ParaDrop: An Edge Computing Platform in Home Gateways. In Fog for 5G and IoT; Wiley: Hoboken, NJ, USA, 2017; p. 13. [Google Scholar]
- Hong, K.; Lillethun, D.; Ramachandran, U.; Ottenwälder, B.; Koldehofe, B. Mobile fog: A programming model for large-scale applications on the internet of things. In Proceedings of the 2nd ACM SIGCOMM Workshop on Mobile Cloud Computing, Hong Kong, China, 12–16 August 2013; pp. 15–20. [Google Scholar]
- Shi, Y.; Abhilash, S.; Hwang, K. Cloudlet mesh for securing mobile clouds from intrusions and network attacks. In Proceedings of the 2015 3rd IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), San Francisco, CA, USA, 30 March–3 April 2015; pp. 109–118. [Google Scholar]
- Li, H.; Shou, G.; Hu, Y.; Guo, Z. Mobile edge computing: Progress and challenges. In Proceedings of the 2016 4th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Oxford, UK, 29 March–1 April 2016; pp. 83–84. [Google Scholar]
- Pan, J.; Ma, L.; Ravindran, R.; TalebiFard, P. HomeCloud: An edge cloud framework and testbed for new application delivery. In Proceedings of the 2016 23rd International Conference on Telecommunications (ICT), Thessaloniki, Greece, 16–18 May 2016; pp. 1–6. [Google Scholar]
- Xu, Y.; Mahendran, V.; Radhakrishnan, S. Towards SDN-based fog computing: MQTT broker virtualization for effective and reliable delivery. In Proceedings of the 2016 8th International Conference on Communication Systems and Networks (COMSNETS), Bangalore, India, 5–10 January 2016; pp. 1–6. [Google Scholar]
- El Amraoui, A.; Sethom, K. Cloudlet softwarization for pervasive healthcare. In Proceedings of the 2016 30th International Conference on Advanced Information Networking and Applications Workshops (WAINA), Crans-Montana, Switzerland, 23–25 March 2016; pp. 628–632. [Google Scholar]
- Monfared, S.; Bannazadeh, H.; Leon-Garcia, A. Software defined wireless access for a two-tier cloud system. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 566–571. [Google Scholar]
- Wu, D.; Arkhipov, D.I.; Asmare, E.; Qin, Z.; McCann, J.A. UbiFlow: Mobility management in urban-scale software defined IoT. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015; pp. 208–216. [Google Scholar]
- Truong, N.B.; Lee, G.M.; Ghamri-Doudane, Y. Software defined networking-based vehicular adhoc network with fog computing. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 1202–1207. [Google Scholar]
- Openfog. Available online: https://www.openfogconsortium.org/ (accessed on 1 October 2018).
- Masip-Bruin, X.; Marín-Tordera, E.; Tashakor, G.; Jukan, A.; Ren, G.J. Foggy clouds and cloudy fogs: A real need for coordinated management of fog-to-cloud computing systems. IEEE Wirel. Commun. 2016, 23, 120–128. [Google Scholar] [CrossRef]
- Masri, W.; Al Ridhawi, I.; Mostafa, N.; Pourghomi, P. Minimizing delay in IoT systems through collaborative fog-to-fog (F2F) communication. In Proceedings of the 2017 Ninth International Conference on Ubiquitous and Future Networks (ICUFN), Milan, Italy, 4–7 July 2017; pp. 1005–1010. [Google Scholar]
- Zeng, D.; Gu, L.; Guo, S.; Cheng, Z.; Yu, S. Joint optimization of task scheduling and image placement in fog computing supported software-defined embedded system. IEEE Trans. Comput. 2016, 65, 3702–3712. [Google Scholar] [CrossRef]
- Zhu, J.; Chan, D.S.; Prabhu, M.S.; Natarajan, P.; Hu, H.; Bonomi, F. Improving web sites performance using edge servers in fog computing architecture. In Proceedings of the 2013 IEEE 7th International Symposium on Service Oriented System Engineering (SOSE), San Francisco Bay, CA, USA, 25–28 March 2013; pp. 320–323. [Google Scholar]
- Aazam, M.; Huh, E.N. Fog computing micro datacenter based dynamic resource estimation and pricing model for IoT. In Proceedings of the 2015 IEEE 29th International Conference on Advanced Information Networking and Applications (AINA), Gwangju, Korea, 25–27 March 2015; pp. 687–694. [Google Scholar]
- Zhang, H.; Zhang, Y.; Gu, Y.; Niyato, D.; Han, Z. A Hierarchical Game Framework for Resource Management in Fog Computing. IEEE Commun. Mag. 2017, 55, 52–57. [Google Scholar] [CrossRef]
- Aazam, M.; St-Hilaire, M.; Lung, C.H.; Lambadaris, I. MeFoRE: QoE based resource estimation at Fog to enhance QoS in IoT. In Proceedings of the 2016 23rd International Conference on Telecommunications (ICT), Thessaloniki, Greece, 16–18 May 2016; pp. 1–5. [Google Scholar]
- Abedin, S.F.; Alam, M.G.R.; Tran, N.H.; Hong, C.S. A Fog based system model for cooperative IoT node pairing using matching theory. In Proceedings of the 2015 17th Asia-Pacific Network Operations and Management Symposium (APNOMS), Busan, Korea, 19–21 August 2015; pp. 309–314. [Google Scholar]
- Giang, N.K.; Blackstock, M.; Lea, R.; Leung, V.C. Developing IoT applications in the fog: A distributed dataflow approach. In Proceedings of the 2015 5th International Conference on the Internet of Things (IOT), Seoul, Korea, 26–28 October 2015; pp. 155–162. [Google Scholar]
- Mei, B.; Cheng, W.; Cheng, X. Fog computing based ultraviolet radiation measurement via smartphones. In Proceedings of the 2015 Third IEEE Workshop on Hot Topics in Web Systems and Technologies (HotWeb), Washington, DC, USA, 12–13 November 2015; pp. 79–84. [Google Scholar]
- Aazam, M.; Huh, E.N. Fog computing and smart gateway based communication for cloud of things. In Proceedings of the 2014 International Conference on Future Internet of Things and Cloud (FiCloud), Barcelona, Spain, 27–29 August 2014; pp. 464–470. [Google Scholar]
- Bittencourt, L.F.; Lopes, M.M.; Petri, I.; Rana, O.F. Towards virtual machine migration in fog computing. In Proceedings of the 2015 10th International Conference on P2P, Parallel, Grid, Cloud and Internet Computing (3PGCIC), Krakow, Poland, 4–6 November 2015; pp. 1–8. [Google Scholar]
- Souza, V.B.C.D.; Ramírez, W.; Masip-Bruin, X.; Marín-Tordera, E.; Ren, G.; Tashakor, G. Handling service allocation in combined fog-cloud scenarios. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 23–27 May 2016; pp. 1–5. [Google Scholar]
- Deng, R.; Lu, R.; Lai, C.; Luan, T.H. Towards power consumption-delay tradeoff by workload allocation in cloud-fog computing. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 3909–3914. [Google Scholar]
- Taneja, M.; Davy, A. Resource aware placement of IoT application modules in Fog-Cloud Computing Paradigm. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 1222–1228. [Google Scholar]
- Bartolí, A.; Hernández, F.; Val, L.; Gorchs, J.; Masip-Bruin, X.; Marín-Tordera, E.; Garcia, J.; Juan, A.; Jukan, A. Benefits of a Coordinated Fog-to-Cloud Resources Management Strategy on a Smart City Scenario. In Proceedings of the European Conference on Parallel Processing, Santiago de Compostela, Spain, 28–29 August 2017; Springer: Cham, Germany, 2017; pp. 283–291. [Google Scholar]
- Worldsensing. Available online: https://www.worldsensing.com/ (accessed on 1 October 2018).
- Gupta, H.; Vahid Dastjerdi, A.; Ghosh, S.K.; Buyya, R. iFogSim: A toolkit for modeling and simulation of resource management techniques in the Internet of Things, Edge and Fog computing environments. Softw. Pract. Exp. 2017, 47, 1275–1296. [Google Scholar] [CrossRef]
- PTZ Camera. Available online: https://en.wikipedia.org/wiki/Pan%E2%80%93tilt%E2%80%93zoom_camera (accessed on 1 October 2018).
- Ferrari, P.; Flammini, A.; Rinaldi, S.; Sisinni, E.; Maffei, D.; Malara, M. Impact of Quality of Service on Cloud Based Industrial IoT Applications with OPC UA. Electronics 2018, 7, 109. [Google Scholar] [CrossRef]
- Chen, Z.; Chen, S.; Feng, X. A design of distributed storage and processing system for Internet of Vehicles. In Proceedings of the 2016 8th International Conference on Wireless Communications and Signal Processing (WCSP), Yangzhou, China, 13–15 October 2016; pp. 1–5. [Google Scholar]
- Biswas, A.R.; Giaffreda, R. IoT and cloud convergence: Opportunities and challenges. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Korea, 6–8 March 2014; pp. 375–376. [Google Scholar]
- Alonso, L.; Barbarán, J.; Chen, J.; Díaz, M.; Llopis, L.; Rubio, B. Middleware and communication technologies for structural health monitoring of critical infrastructures: A survey. Comput. Stand. Interfaces 2018, 56, 83–100. [Google Scholar] [CrossRef]
- Lilis, G.; Kayal, M. A secure and distributed message oriented middleware for smart building applications. Autom. Constr. 2018, 86, 163–175. [Google Scholar] [CrossRef]
- Fortino, G.; Guerrieri, A.; Russo, W.; Savaglio, C. Integration of agent-based and cloud computing for the smart objects-oriented IoT. In Proceedings of the 2014 IEEE 18th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Hsinchu, Taiwan, 21–23 May 2014; pp. 493–498. [Google Scholar]
- Yuan, D.; Jin, J.; Grundy, J.; Yang, Y. A framework for convergence of cloud services and Internet of things. In Proceedings of the 2015 IEEE 19th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Calabria, Italy, 6–8 May 2015; pp. 349–354. [Google Scholar]
- Hou, L.; Zhao, S.; Li, X.; Chatzimisios, P.; Zheng, K. Design and implementation of application programming interface for Internet of things cloud. Int. J. Netw. Manag. 2017, 27, e1936. [Google Scholar] [CrossRef]
- Vulpe, A.; Arseni, Ş.C.; Marcu, I.; Voicu, C.; Fratu, O. Building a Unified Middleware Architecture for Security in IoT. In Proceedings of the World Conference on Information Systems and Technologies, Madeira, Portugal, 11–13 April 2017; Springer: Cham, Germany, 2017; pp. 105–114. [Google Scholar]
- Ngu, A.H.; Gutierrez, M.; Metsis, V.; Nepal, S.; Sheng, Q.Z. IoT middleware: A survey on issues and enabling technologies. IEEE Internet Things J. 2017, 4, 1–20. [Google Scholar] [CrossRef]
- Hossain, M.S.; Muhammad, G. Cloud-assisted industrial internet of things (iiot)–enabled framework for health monitoring. Comput. Netw. 2016, 101, 192–202. [Google Scholar] [CrossRef]
- Manogaran, G.; Thota, C.; Lopez, D.; Sundarasekar, R. Big data security intelligence for healthcare industry 4.0. In Cybersecurity for Industry 4.0; Springer: Berlin, Germany, 2017; pp. 103–126. [Google Scholar]
- Xu, G.; Gao, S.; Daneshmand, M.; Wang, C.; Liu, Y. A survey for mobility big data analytics for geolocation prediction. IEEE Wirel. Commun. 2017, 24, 111–119. [Google Scholar] [CrossRef]
- Verma, S.; Kawamoto, Y.; Fadlullah, Z.M.; Nishiyama, H.; Kato, N. A survey on network methodologies for real-time analytics of massive IoT data and open research issues. IEEE Commun. Surv. Tutor. 2017, 19, 1457–1477. [Google Scholar] [CrossRef]
- Hosseini, M.P.; Tran, T.X.; Pompili, D.; Elisevich, K.; Soltanian-Zadeh, H. Deep learning with edge computing for localization of epileptogenicity using multimodal rs-fMRI and EEG big data. In Proceedings of the 2017 IEEE International Conference on Autonomic Computing (ICAC), Columbus, OH, USA, 17–21 July 2017; pp. 83–92. [Google Scholar]
- Sookhak, M.; Yu, F.R.; Zomaya, A.Y. Auditing Big Data Storage in Cloud Computing Using Divide and Conquer Tables. IEEE Trans. Parallel Distrib. Syst. 2018, 29, 999–1012. [Google Scholar] [CrossRef]
- Wan, J.; Tang, S.; Hua, Q.; Li, D.; Liu, C.; Lloret, J. Context-aware cloud robotics for material handling in cognitive industrial internet of things. IEEE Internet Things J. 2018, 5, 2272–2281. [Google Scholar] [CrossRef]
- Jayasena, K.P.N.; Li, L.; Xie, Q. Multi-modal multimedia big data analyzing architecture and resource allocation on cloud platform. Neurocomputing 2017, 253, 135–143. [Google Scholar] [CrossRef]
- Chard, R.; Chard, K.; Wolski, R.; Madduri, R.; Ng, B.; Bubendorfer, K.; Foster, I. Cost-Aware Cloud Profiling, Prediction, and Provisioning as a Service. IEEE Cloud Comput. 2017, 4, 48–59. [Google Scholar] [CrossRef]
- Ma, L.; Tao, L.; Gai, K.; Zhong, Y. A novel social network access control model using logical authorization language in cloud computing. Concur. Comput. Pract. Exp. 2017, 29, e3893. [Google Scholar] [CrossRef]
- Bianchini, D.; De Antonellis, V.; Melchiori, M. Services Discovery and Recommendation for Multi-Datasource Access: Exploiting Semantic and Social Technologies; A Comprehensive Guide through the Italian Database Research over the Last 25 Years; Springer: Cham, Germany, 2018; pp. 375–390. [Google Scholar]
- Li, H.; Zhu, H.; Du, S.; Liang, X.; Shen, X.S. Privacy leakage of location sharing in mobile social networks: Attacks and defense. IEEE Trans. Dependable Secure Comput. 2018, 15, 646–660. [Google Scholar] [CrossRef]
- Pham, V.V.H.; Yu, S.; Sood, K.; Cui, L. Privacy issues in social networks and analysis: A comprehensive survey. IET Netw. 2017, 7, 74–84. [Google Scholar] [CrossRef]
- Zhang, J.; Xue, N.; Huang, X. A secure system for pervasive social network-based healthcare. IEEE Access 2016, 4, 9239–9250. [Google Scholar] [CrossRef]
- Tosh, D.K.; Shetty, S.; Liang, X.; Kamhoua, C.A.; Kwiat, K.A.; Njilla, L. Security implications of blockchain cloud with analysis of block withholding attack. In Proceedings of the 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, Madrid, Spain, 14–17 May 2017; pp. 458–467. [Google Scholar]
- Farahani, B.; Firouzi, F.; Chang, V.; Badaroglu, M.; Constant, N.; Mankodiya, K. Towards fog-driven IoT eHealth: Promises and challenges of IoT in medicine and healthcare. Future Gener. Comput. Syst. 2018, 78, 659–676. [Google Scholar] [CrossRef]
- Wang, C.; Zhu, Y.; Shi, W.; Chang, V.; Vijayakumar, P.; Liu, B.; Mao, Y.; Wang, J.; Fan, Y. A Dependable Time Series Analytic Framework for Cyber-Physical Systems of IoT-based Smart Grid. ACM Trans. Cyber-Phys. Syst. 2018, 3, 7. [Google Scholar] [CrossRef]
- Sun, G.; Chang, V.; Ramachandran, M.; Sun, Z.; Li, G.; Yu, H.; Liao, D. Efficient location privacy algorithm for Internet of Things (IoT) services and applications. J. Netw. Comput. Appl. 2017, 89, 3–13. [Google Scholar] [CrossRef]
- Taylor, R.; Baron, D.; Schmidt, D. The world in 2025-predictions for the next ten years. In Proceedings of the 2015 10th International Packaging, Assembly and Circuits Technology Conference (IMPACT), Taipei, Taiwan, 21–23 October 2015; pp. 192–195. [Google Scholar]
- Antunes, J.B.; Denés, I.L.; Castro, T.O.; Macedo, D.F.; dos Santos, A.L. ManIoT: A 2-tier management platform for heterogeneous IoT devices and applications. Int. J. Netw. Manag. 2018, 28, e2034. [Google Scholar] [CrossRef]
- Mora-Gimeno, F.; Mora-Mora, H.; Marcos-Jorquera, D.; Volckaert, B. A Secure Multi-Tier Mobile Edge Computing Model for Data Processing Offloading Based on Degree of Trust. Sensors 2018, 18, 3211. [Google Scholar] [CrossRef] [PubMed]
| Reference | Topics | Background Described | Challenges and Opportunities Discussed |
|---|---|---|---|
| [5] | Edge technologies | Overview of concepts, applications and benefits of edge computing in different areas. | Programmability, naming, data abstraction, service management, privacy, security and optimization metrics. |
| [6] | Edge technologies | Description of existing solutions for distributed data stream processing and the techniques to manage resource elasticity features of clouds. | Development and deployment of stream processing applications under heterogeneous distributed architectures. |
| [7] | Communication networks | Overview of benefits of edge computing technologies in future 5G mobile networks. | Wireless backhauling, security, management and orchestration of services. |
| [8] | Mobile edge computing | Review on computation/communication components of the typical existing solutions in mobile edge computing (MEC). | Mobility management, deployment, privacy, security, and standardization of MEC systems in terms of 5G. |
| [9] | Mobile edge computing | Overview of concepts and applications of mobile edge computing. | Computational offloading, infrastructures, security and privacy mechanisms, resource optimization, and pricing in MEC. |
| [10] | Security | Overview of the edge approaches (like fog computing, mobile cloud computing and mobile edge computing) and the integration of security mechanisms in edge paradigms. | Security challenges in edge paradigms like trust management, Identity and authentication, Intrusion detection systems, protocol and network security. |
| [11] | Security | Overview of security and privacy issues of fog computing. | Security challenges of fogging like access control, intrusion detection systems, secure and private data computation. |
| [12] | Fogging | Overview of concepts and applications of fog computing. | Network issues, quality of service (QoS), accounting, billing, monitoring, computation offloading, programming model, resource management, security and privacy in fog computing. |
| [13] | Communication networks | Overview of concepts and network applications of fog computing. | SDN communication, incentives, standardization, heterogeneity, resource management, radio access networks, and offloading in fog computing. |
| [14] | Fogging | Overview of concepts and applications of fog computing and classification of fog systems according to five criteria: heterogeneity, QoS management, scalability, mobility and federation. | Classification of current architectural and algorithmic challenges in fogging according to five criteria: heterogeneity, QoS management, scalability, mobility and federation. |
| [15] | Edge technologies | Overview of multi-access edge architectures and orchestration deployment options. | Orchestration, programmability, QoE, resiliency, continuity, mobility, monetization, and security of MEC services. |
| [16] | Communication networks | Overview of 5G and fog computing technologies. | Ubiquity of devices, connectivity, network management, privacy and security challenges in fog computing. |
| [17] | Fogging | Overview of fog computing as an intermediate layer between IoT devices and cloud datacentres. | Context-aware resource, service provisioning, multi-tenant Support, power management, distributed application deployment, pricing, programming languages, simulation tools, sustainable and reliable services in fogging. |
| [18] | Big data | Overview of fog computing in terms of Big Data. | Programming models, data management, security, privacy, and trust for fog applications. |
| [19] | Mobile edge computing | Overview of concept mobile edge computing and computation offloading to MEC. | Computation offloading challenges in MEC: offloading decision, allocation of computing resources, mobility management and distribution, management of MEC resources, and traffic paradigm imposed by coexistence of offloaded data and conventional data. |
| [20] | Edge technologies | Overview of edge computing motivation and edge technologies (i.e., cloudlet). | Resource management and allocation, scalability of resource provisioning strategies, data abstraction, fault tolerance and quality of service, security and privacy in the edge computing. |
| Reference | Description |
|---|---|
| [41] | mF2C is a European project that aims to design, implement and validate novel management for a coordinated fog and cloud computing systems |
| [42] | Google’s Go language used to implement fog architecture for IoT applications |
| [43] | Cloud and fog environments are used to develop application for smart healthcare environments that is being developed as part of OpSIT-Project-Germany |
| [44,45] | Nippon Telegraph and Telephone Corporation (NTT) developed an edge accelerated web platform to reduce the response time for cloud applications |
| [46] | Implementation of fog node to manage heterogeneous smart objects in complex IoT scenarios |
| [47] | Implementation of a wearable cognitive assistance based on Google Glass and cloudlet |
| [48] | Development of the CloudAware framework based on mobile edge features to design elastic mobile applications |
| [49] | Cisco Kinetic platform provides fog processing module to process IoT Data |
| [50] | Vortex platform allows to connect each vortex edge device to an IoT device to construct global shared fog domain |
| [51] | The Nokia Multi-access Edge Computing (MEC) platform for processing mobile network applications |
| [52] | Cisco IOx platform offers edge features to develop IoT applications |
| [53] | FogSim simulator allows the manipulation of edge features |
| [54] | ParaDrop is an edge computing platform for wireless gateways and applications |
| [55] | Mobile Fog is a programming model for large scale IoT applications |
| [56] | Implementation of a cloudlet mesh architecture for securing mobile clouds from network attacks |
| [57] | WiCloud is a mobile edge computing platform with OpenStack for enhancing location-awareness and managing inter-mobile-edge communication |
| [58] | HomeCloud framework integrated NFV (Network Function Virtualization) and SDN (Software Defined Networking) for orchestration and application delivery in the Edge-cloud |
| [59] | Implementation of the MQTT broker functionalities at Fog computing node based on SDN for orchestration of IoT devices |
| [60] | Implementation of cloudlet based on SDN for patient monitoring |
| [61] | A converged wireless access architecture based on edge servers for heterogeneous cloud access networks |
| [62] | UbiFlow framework for management and configuration of heterogeneous IoT networks |
| [63] | FSDN is a Vehicular Adhoc Network (VANET) based on fog features for supporting connectivity, mobility, scalability and flexibility of VANETs |
| [64] | OpenFog is a consortium that provides fogging features |
| [65] | F2C (Fog-to-Cloud) computing is a hierarchical layered architecture relying on a coordinated and distributed management of both fog and cloud platforms |
| [66] | F2F (Fog-to-Fog) architecture allows fogs to communicate with each other |
| References | Date of Publication | Description | Collaborator with Cloud Architectures | Extender of Centralized Cloud Platforms | Middle Layer | Main Research Domains Discussed | Advantages of Edge Solutions | Drawbacks of Edge Solutions |
|---|---|---|---|---|---|---|---|---|
| [67] | 2016 | Fog computing architecture supporting software-defined embedded system equipped with the resources of clients to compute and store data. | No | Yes | No |
|
|
|
| [68] | 2013 | Edge servers in fog computing architecture are used to improve web-site performance. | No | Yes | No |
|
|
|
| [43] | 2015 | Fogging is proposed as an intermediate role at the edge to develop a smart healthcare application that is being developed as part of OpSIT-Project -Germany. | No | No | Yes |
|
|
|
| [69] | 2015 | Fog computing is proposed to manage the IoT resources and allow cloud platforms to act according to the current situations of clients (i.e., pricing). | No | No | Yes |
|
|
|
| [44,45] | 2013 | Nippon Telegraph and Telephone Corporation (NTT) developed an edge accelerated web platform to reduce the response time for cloud applications. | No | No | Yes |
|
|
|
| [70] | 2017 | Multi Fog nodes based on a Hierarchical Game Approach proposed to interact with multiple cloud provider to reduce delay and cost for the clients. | No | No | Yes |
|
|
|
| [71] | 2016 | Fog computing proposed to improve the QoS by using the context of multi-media IoT devices. | No | Yes | No |
|
|
|
| [72] | 2015 | Fogging based system model proposed to solve the pairing problem with the same domain of IoT nodes. | No | Yes | No |
|
|
|
| [73] | 2015 | Fog computing based on distributed Dataflow programming mode suggested to develop IoT applications according to the perspective of the fogging. | Yes | No | No |
|
|
|
| [74] | 2015 | Fog Computing Based UV (ultraviolet radiation) measurement for mobile phones. | No | Yes | No |
|
|
|
| [75] | 2014 | Fog Computing based smart gateway proposed to enhance the communication between cloud and IoT devices. | No | No | Yes |
|
|
|
| [76] | 2015 | multiple cloudlets used in Fog computing to enhance the migration of virtual machines to cloud platforms. | No | No | Yes |
|
|
|
| [77] | 2016 | A second fog layer is proposed to enhance the communication of cloud and fog infrastructures. | Yes | Yes | Yes |
|
|
|
| [65] | 2016 | A new strategy proposed to coordinate the different cloud and fog resources. | Yes | Yes | Yes |
|
|
|
| [78] | 2015 | A new solution proposed to enhance the cooperation between the fog and the cloud. | Yes | Yes | Yes |
|
|
|
| [79] | 2017 | Deployment of application modules in fog-cloud infrastructure to manage the IoT resources in the network infrastructure. | Yes | Yes | Yes |
|
|
|
| [46] | 2015 | A fog node for managing heterogeneous smart objects in complex IoT scenarios. | No | Yes | No |
|
|
|
| [42] | 2016 | Google’s Go language used to implement fog architecture for IoT applications. | No | Yes | No |
|
|
|
| [47] | 2014 | Development of a wearable cognitive assistance based on Google Glass and cloudlet. | No | Yes | No |
|
|
|
| [48] | 2015 | Development of the CloudAware framework based on mobile edge features to design elastic mobile applications. | No | Yes | No |
|
|
|
| [55] | 2013 | Mobile Fog is a programming model for large scale IoT applications. | No | Yes | No |
|
|
|
| [56] | 2015 | Implementation of a cloudlet mesh architecture for securing mobile clouds from network attacks. | No | No | Yes |
|
|
|
| [57] | 2016 | WiCloud is a mobile edge computing platform with OpenStack for enhancing location-awareness and managing inter-mobile-edge communication. | No | Yes | No |
|
|
|
| [58] | 2016 | HomeCloud framework integrated NFV (Network Function Virtualization) and SDN (Software Defined Networking) for orchestration and application delivery in the Edge cloud. | No | No | Yes |
|
|
|
| [59] | 2016 | Implementation of the MQTT broker functionalities at Fog computing node based on SDN for orchestration of IoT devices. | No | Yes | No |
|
|
|
| [60] | 2016 | Implementation of cloudlet based on SDN for patient monitoring. | No | No | Yes |
|
|
|
| [60] | 2015 | A converged wireless access architecture based on edge servers for heterogeneous cloud access networks. | No | No | Yes |
|
|
|
| [61] | 2015 | UbiFlow framework for management and configuration of heterogeneous IoT networks. | No | Yes | No |
|
|
|
| [63] | 2015 | FSDN is a Vehicular Ad-hoc Network (VANET) based on fog features for supporting connectivity, mobility, scalability and flexibility of VANETs. | no | yes | no |
|
|
|
| [66] | 2017 | Fog-to-Fog architecture allows fogs to communicate with each other, and it reduces the overall end-to-end delay for F2C. | Yes | Yes | Yes |
|
|
|
| Source | Destination | Latency (ms) |
|---|---|---|
| PTZ_CTRL (pan–tilt–zoom _control) | camera | 1 |
| VIDEO | Camera | 6 |
| GW (WiFi gateway) | ISP GW | 2 |
| ISP GW (Internet Service Provider) | cloud | 200 |
| Camera | GW | 2 |
| Type | Downlink Bandwidth (Mbps) | Uplink Bandwidth (Mbps) | RAM (MB) | Processing Capability (Mips) | Rate per Mips |
|---|---|---|---|---|---|
| Cloud | 10,000 | 100 | 40,000 | 20,000 | 0.001 |
| ISP GW | 10,000 | 10,000 | 4000 | 2000 | 0 |
| GW | 10,000 | 10,000 | 4000 | 2000 | 0 |
| camera | 270 | 10,000 | 1000 | 1400 | 0 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bangui, H.; Rakrak, S.; Raghay, S.; Buhnova, B. Moving to the Edge-Cloud-of-Things: Recent Advances and Future Research Directions. Electronics 2018, 7, 309. https://doi.org/10.3390/electronics7110309
Bangui H, Rakrak S, Raghay S, Buhnova B. Moving to the Edge-Cloud-of-Things: Recent Advances and Future Research Directions. Electronics. 2018; 7(11):309. https://doi.org/10.3390/electronics7110309
Chicago/Turabian StyleBangui, Hind, Said Rakrak, Said Raghay, and Barbora Buhnova. 2018. "Moving to the Edge-Cloud-of-Things: Recent Advances and Future Research Directions" Electronics 7, no. 11: 309. https://doi.org/10.3390/electronics7110309
APA StyleBangui, H., Rakrak, S., Raghay, S., & Buhnova, B. (2018). Moving to the Edge-Cloud-of-Things: Recent Advances and Future Research Directions. Electronics, 7(11), 309. https://doi.org/10.3390/electronics7110309





