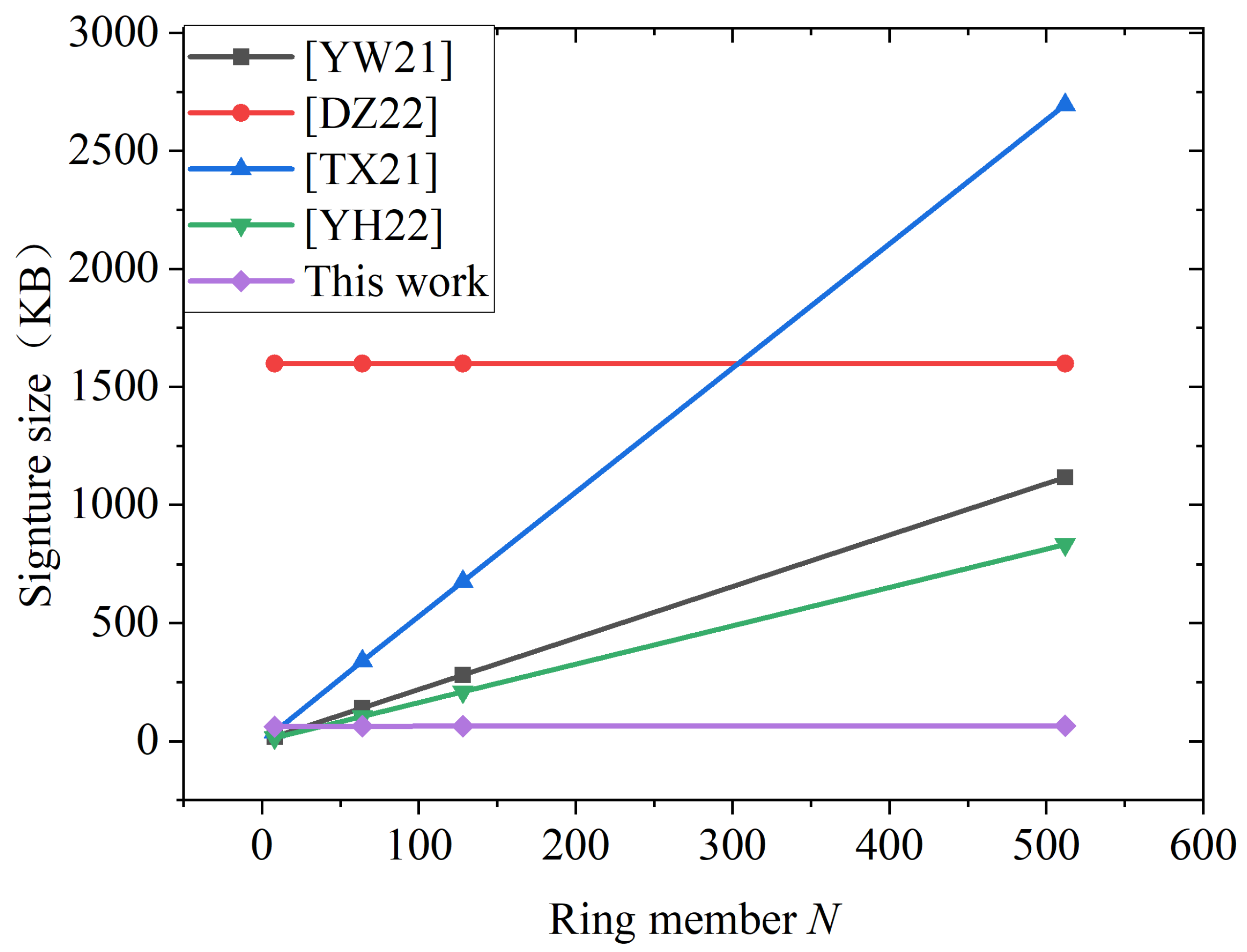
5.1. Basic Security Properties Analysis
Theorem 1. The NTRU-CRS scheme is correct.
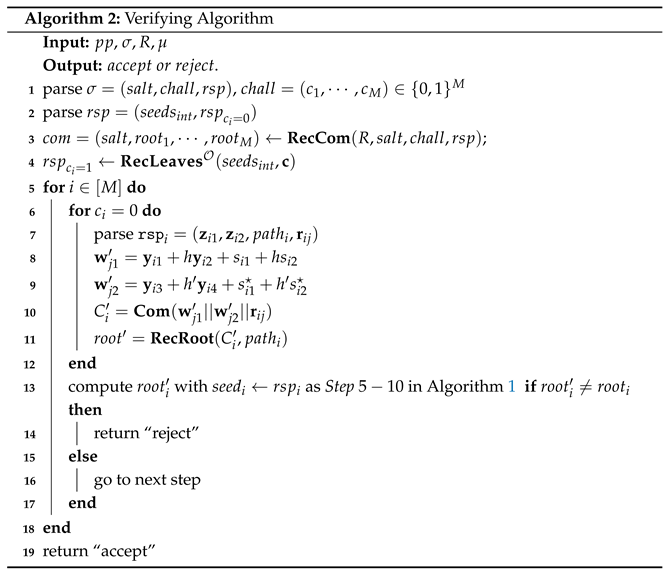
Proof. According to the signature algorithm, if the signature is valid, then
From the above, it is clear that generated by and ; thus, holds. Our scheme is correct. □
Theorem 2. Under the assumption that NTRU-SIS is hard, is collision-resistant, our scheme is anonymous in the ROM.
Proof. Anonymity is proved by a game between and . The distribution of the two signatures is statistically indistinguishable for . Then, our scheme is anonymous.
Setup phase. The challenger completes the following setup based on the inputs and n along with the number of ring members N.
Determining the ring .
Generating the related public parameters using the algorithm, where is a collision-resistant hash function.
Calling to generate the master public key MPK and secret key MSK.
The challenger makes the and MPK open, while the MSK is kept secret.
Query phase. The adversary can make adaptive inquiries about the following random oracles:
Corruption query: The adversary enters the user identity , then the challenger computes and randomly chooses two small-size secrets to compute . In addition, uses to compute , then returns to and stores into .
challenge oracle query: The adversary first asks for the challenge of , then the challenger first searches the list and returns it to if it exists. Otherwise, randomly selects a challenge value from the challenge space, returns it to , and stores it in .
Signing query: The adversary inquires about identity (a message under ring such that ). If exists, then the challenger checks to return ; otherwise, computes the corresponding private key and calls the challenge oracle query to generate the signature with the signing algorithm, returns , and stores it in .
Challenge phase. The adversary submits a message , a ring , and two identities , to the challenger . Then, randomly selects to generate the corresponding signature using the signature algorithm.
Guess phase. The adversary outputs their guess of .
Analysis. For
, the signature is divided into three parts, where
is a random number and
is a string of 0,1 bits. Both are indistinguishable from the adversary
as to whether the signer is b or 1 − b. Here,
is also a random number in
, and the remaining
and
are statistically indistinguishable under the effect of rejection sampling [
33]. Finally, from
in [
32],
relies only on the distribution, and the adversary cannot obtain any information about the user’s index. For
, the signature is
at this point, and it follows from
in [
32] that the adversary
distinguishes between the
generated by
and
with probability only
. In summary, our scheme is anonymous. □
Theorem 3. Under the assumption that NTRU-SIS is hard, and are CRHFs, our scheme is unforgeable in the ROM (Type 1).
Proof. We utilize an interactive game between and for the proof of unforgeability. We emphasize that unforgeability is under an adaptive chosen-message-and-identity attack (EUF-IDRS-CMIA). The adversary is an external attacker who can perform a public key replacement attack. After obtaining an instance related to a polynomial , the challenger aims to output two non-zero small polynomials that satisfy , . Suppose that the adversary can output a forgery with a non-negligible probability ; then, the challenger can break the NTRU-SIS problem with a non-negligible probability . The game is described as follows:
Setup phase. The challenger first receives an instance h and runs to generate , embeds h into as , and sends and to the adversary .
Query phase. The adversary can make adaptive inquiries about the following random oracles.
query: The adversary inquires about identity and the challenger checks the 3-tuples list . If exists, they return to . Otherwise, randomly chooses two small-size polynomials and computes and , returns to , and finally stores in the list , where .
Register query: When adversary inquires about identity , the challenger first checks the 3-tuples list . If it exists, they return ; otherwise, randomly chooses two small-size secret values and computes . Finally, they store and return to the adversary . This query can only be made at most N times.
Partial-Private-Key query: The adversary inquires about identity and the challenger checks for the partial private key . If it does not exist, they respond by calling oracle . This query can only be made at most times.
Public-Key-Replacement query: The adversary provides and a new public key , then searches for the public key corresponding to the and replaces it by . The challenger records this replacement by adding them to . This query can only be made at most times.
query: The adversary inquires about the challenge of , then searches for the four-tuples list . If exists, it is returned to . Otherwise, randomly selects a challenge from the challenge space, returns it to , and stores it in . The query can be queried at most times.
Signing query: The adversary inquires about identity , a message under ring such that . If the signature exists, then the challenger checks and returns it. Otherwise, checks and to generate the signature with the signing algorithm, returns , and stores it in . If the corresponding private key is not found in the two lists, then the corresponding oracle is called. Note that .
Forgery Phase. Through a series of queries, the adversary generates a valid forgery about . This forgery must be verified and must satisfy the following three conditions:
is a valid signature.
The adversary did not query anyone for part of the private key in and there is no public key replacement in .
The forgery does not appear in the signing query.
Analysis. Assume that the probability that the adversary succeeds in forging a signature is and that the probability of the challenger solving by taking advantage of adversary ’s ability is .
From the forking lemma [
34], it follows that two valid signatures
and
are output by
with probability
, where
but
. Because
is a random number, we have
The case for
and
is similar. In addition,
can be extracted only when all
are 0 with probability
. Because
, the challenger
solves the
problem with a probability of
If is non-negligible, then is non-negligible. However, is hard, which contradicts this. Thus, our scheme is unforgeable for adversary . □
Theorem 4. Under the assumption that NTRU-SIS is hard, and are CRHFs, our scheme is unforgeable in the ROM (Type 2).
Proof. Here, adversary is an internal attacker that has the MSK and can compute a part of any user’s private key. In general, the adversary here simulates a malicious KGC. Similar to the above, the challenger finds a set of polynomials that satisfies to break NTRU-SIS with probability by utilizing an adversary that can output a forgery with probability . The game is as follows:
Setup phase. Suppose that the challenger receives an NTRU-SIS instance related to , runs Setup and to generate and , then sends and to the adversary.
Query phase. The adversary can make adaptive inquiries about the following random oracles.
query: The adversary inquires about identity , then the challenger checks the 3-tuples list . If it exists, they return to ; otherwise, uses to generate , stores , and returns .
Register query: The adversary inquires about identity and the challenger checks the 3-tuples list . If it exists, they return ; otherwise, randomly chooses two small-size secret values and computes , then stores and returns to the adversary .
Partial-Private-Key query: The adversary can use the master private key to compute anyone’s partial private key.
Public-Key-Replacement query: This is the same query as adversary .
query: The adversary asks for a challenge about , then searches list and returns if it exists. Otherwise, randomly selects a challenge from the challenge space and stores it in list while returning it to . The query can be queried at most times.
Signing query: The same query as adversary .
Forgery Phase. Eventually, the adversary outputs a forgery about , which must satisfy the following:
is a valid signature.
The adversary cannot ask for anyone’s secret value in .
The adversary cannot replace users’ public keys in .
The forgery does not appear in the signing query.
Analysis. For the adversary , consistent with the analysis for adversary , the forging is still based on the forking lemma. We have
Meanwhile, the probability of the challenger
solving the NTRU-SIS problem is
If is non-negligible, then is non-negligible. However, is hard, which contradicts this. Thus, our scheme is unforgeable for adversary . □