RBFAC: A Redactable Blockchain Framework with Fine-Grained Access Control Based on Flexible Policy Chameleon Hash
Abstract
1. Introduction
- Our contributions:
- (1)
- We introduce the concept of flexible policy chameleon hash. Only the users whose attributes satisfy the policy of modification rule can manage the editability rights and generate valid proofs, while other users whose attributes satisfy the policy of data editability can just edit the data.
- (2)
- We propose a new redactable blockchain framework with fine-grained access control based on flexible policy chameleon hash, which provides essential functionalities, including editing accountability, leaked key tracing and revocation mechanisms, and policy privacy protection.
- (3)
- We present the security analysis and formal proofs of the RBFAC. We also provide the instantiation. Experimental evaluations demonstrate that the RBFAC framework maintains acceptable performance overhead while delivering advanced features compared to related work.
- Organization: The rest of the paper is organized as follows. Section 2 reviews related work. Section 3 introduces the necessary preliminaries. Section 4 defines FPCH and its security model. Section 5 describes the RBFAC system model in detail, with its instantiation presented in Section 6. Section 7 discusses the security analysis and proofs of RBFAC, while Section 8 evaluates its performance. Finally, Section 9 provides the conclusion.
2. Related Work
3. Preliminaries
3.1. Complexity Assumptions
3.2. Traceable and Revocable Ciphertext Policy Attribute-Based Encryption Based on Privacy Protection
- Setup(, ) : Given a security parameter and a user tree , output the public parameters and the master secret key .
- KeyGen(, u, ) : Given the master secret key , user identity u, and attribute set , output the attribute key .
- Encrypt(m, , R) : Given message m, policy , and revocation list R, output the ciphertext for message m.
- Decrypt: Given the attribute key and ciphertext , decrypt and recover the message m.
- KeySanityCheck: Given the user’s attribute key , check if the user requires tracking and output a bit .
- Trace: If the attribute key fails the , output the new revocation list .
- Update: Given the ciphertext , revocation list , and update parameter X, output the updated ciphertext .
3.3. Chameleon Hash
- Setup() : Given a security parameter , output the public parameters .
- KeyGen() : Output the trapdoor pair .
- Hash(T, m) : Given the parameter T and message m, output the hash pair .
- Verify(T, m, h, r) : Given the parameter T, message m, and hash pair , output a bit .
- Adapt(t, m, , h, r) →: Given the trapdoor t, message m and , and hash pair , output new hash pair .
3.4. Dynamic Threshold Signature
- Setup() : Given a security parameter , output the public parameters .
- KeyGen() : Output the public key and key shares .
- Sign(, m) →: Given the key shares and message m, output the signature , where .
- Verify(, m, ) : Given the public key , message m, and signature , output a bit .
- Reshare() →: Given the key shares for , output new key shares .
4. Flexible Policy Chameleon Hash
4.1. Definition
- Setup() → (, ): Given a security parameter , output the public parameters and the system master secret key .
- KeyGen(, ) →: Given the master secret key and the attribute set , output attribute key .
- Hash(, m, k) → (h, r, W): Given the access policy , message , and proof value , output hash pair and a proof W. The access policy includes both message editability and policy modification rules.
- Verify(m, h, r, W) → d: Given the message m, hash pair , and proof W, output a bit .
- AdaptM(, m, , h, r) → : Given the attribute key , messages m and , and hash pair , output new hash pair .
- AdaptP(, , h) → (, ): Given the attribute key , access policy , and chameleon hash h, output a new access policy and a proof .
- Correctness: The FPCH is if for a security parameter and the attribute set , for ←Setup(), , and KeyGen(), we have
4.2. Security Model
4.3. Instantiation
- (1)
- (2)
- (3)
- Setup(): Input a security parameter ; output the public parameters and the master secret key , where , and .
- KeyGen(, ): Input the master secret key and attribute set ; output the attribute key , where .
- Hash(): Input the access policy , which includes , message m, and proof value k; output the hash pair and a proof W, where the trapdoor , the trapdoor ciphertext , the proof value , the permission proof , the advanced ciphertext , and the hash pair .
- VerifyM(): If , , and the output is 1; otherwise, the output is 0.
- AdaptM(): Input the attribute key , messages m and , and hash pair ; output new hash pair , where , and .
- AdaptP(): Input the attribute key , access policy , and chameleon hash h; output a new access policy and a proof , where , the new access policy includes and , the new trapdoor ciphertext , and the permission proof .
5. System Model
5.1. Participants
- (1)
- Attribute Authority (AA)AA oversees the publication of public parameters, retains the master secret key, generates attribute keys for users, and traces or revokes malicious users. Notably, AA does not participate in editing-related events.
- (2)
- Data OwnersData owners control data readability, editability, and policy modification, as well as upload data to blockchain nodes.
- (3)
- UsersAccording to the data owner’s policies, users are classified into three types of identities: readers, editors, and advanced editors. Readers are allowed to read the data, editors have both read and editing permissions, and advanced editors, in addition to having editor permissions, can modify the data’s readability and editability policies. Note that editors and advanced editors need to request a token from the token committee in order to make edits to prevent uncontrolled modifications.
- (4)
- NodesNodes store data from data owners and respond to user access requests. If a user satisfies the specified access policy, the following actions will occur:
- (i)
- Nodes allow the reader to read the data;
- (ii)
- If the editor holds a data token, nodes allow the editor to edit the data;
- (iii)
- If the advanced editor holds a policy token, nodes allow the advanced editor to edit both the data and the access policies.
When user revocation occurs, nodes update ciphertexts using the update parameter sent by AA through a secure channel. - (5)
- Token Committee (TC)The token committee reviews editing requests from users, records editing activities, and grants tokens with different levels, granularities, and times based on the reputation of the user, enabling diversified and controlled editing.
5.2. Definition
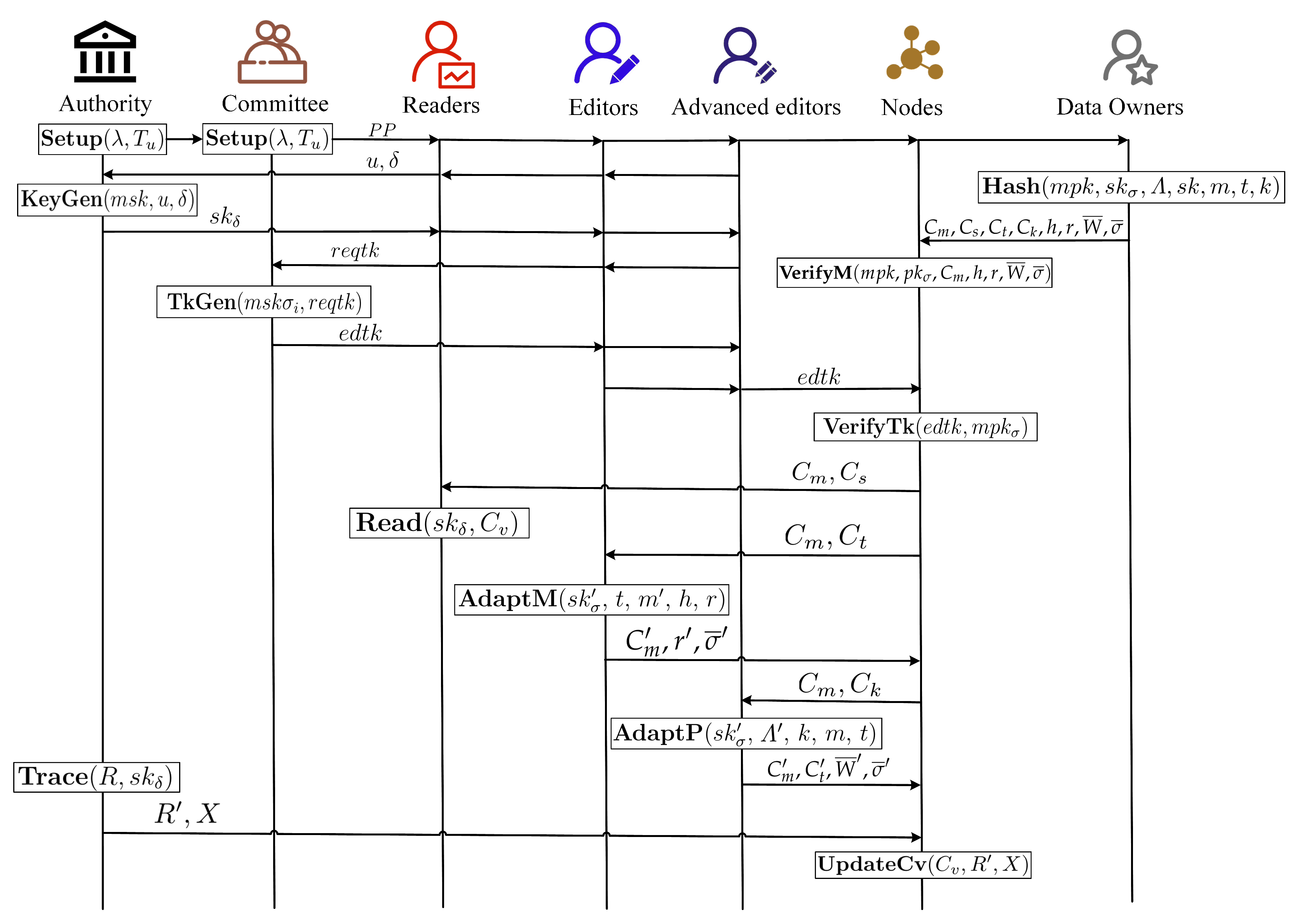
- Setup: The attribute authority (AA) and the initial token committee (TC) input a security parameter and a user tree , outputting the master key pair and the signing key pair . AA retains the master secret key , and TC shares as key shares .
- KeyGen: AA inputs the master secret key , user identity u, and attribute set , generating an attribute key , which it then sends to the user.
- Hash: The data owner inputs the master public key , signing key , access policy , symmetric key , message m, trapdoor t, and proof value k, outputting message ciphertext , readability ciphertext , editability ciphertext , advanced ciphertext , chameleon hash , proof , and signature .
- VerifyM: The node inputs the master public key , message ciphertext , chameleon hash , proof , and signature , outputting a bit .
- TkGen: TC inputs the master signing key share and a user token request , outputting the editing token .
- VerifyTk: The node inputs the editing token and master signing public key , outputting a bit .
- Read() : The user inputs the attribute key and ciphertext . If , it outputs the plaintext .
- AdaptM(, t, , h, r) : The user inputs the signing key , trapdoor t, message , and hash pair , outputting the new message ciphertext , hash pair , and signature .
- AdaptP(, , k, m, t) : The user inputs the signing key , new access policy , proof value k, message m, and trapdoor t, outputting new ciphertexts , , proof , and signature .
- Trace: AA inputs the revocation list R and attribute key , outputting new revocation list .
- UpdateCv: The node inputs ciphertext , revocation list , and the update parameter X, outputting the updated ciphertext .
5.3. Diversified Editing Management Mechanism
- (1)
- Diversified Editing
- (i)
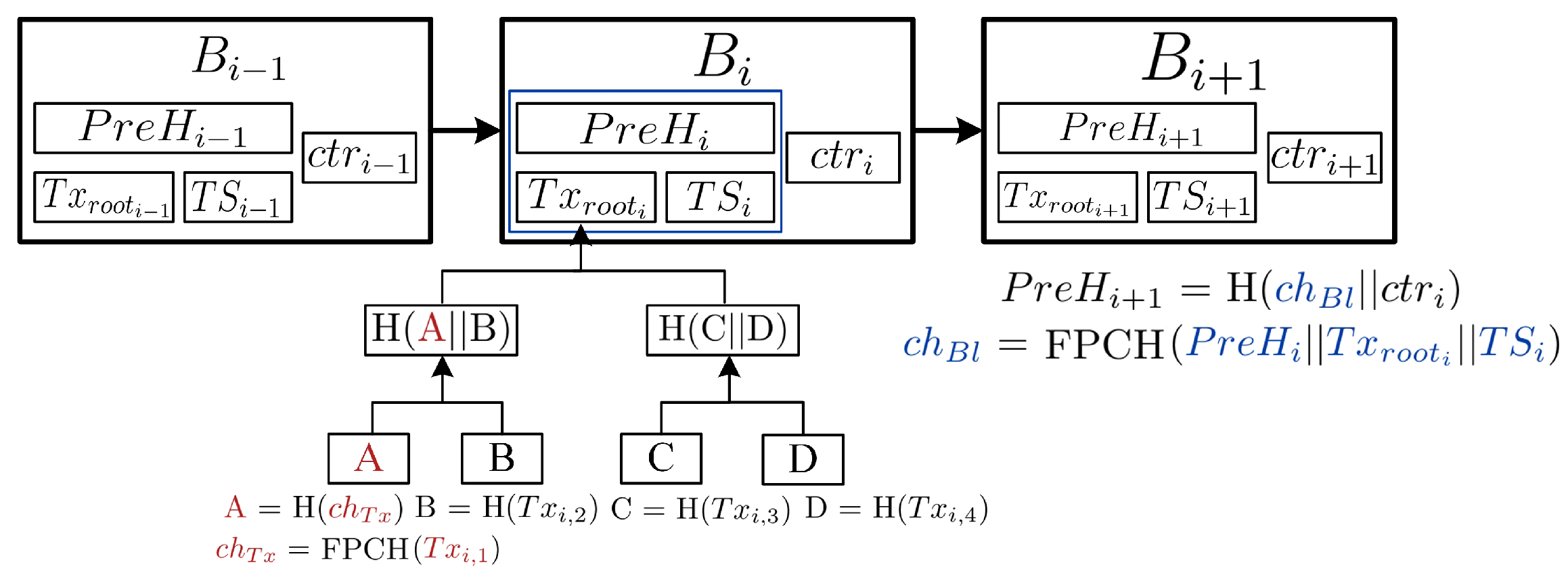
- Generation of Mutable Transactions: A data owner generates the chameleon hash for transaction by executing and defines an access policy to control data readability, editability, and policy modification. typically contains the encrypted data stored by the data owner along with transaction fields, and it is used for FPCH computation. Note that elements such as nonces, ciphertexts, and signatures are stored in the non-hashed portion of the transaction.
- (ii)
- Tx-Level Editing: A user executes to output . The node then verifies the editing validity by running .
- (iii)
- Generation of Mutable Blocks: The node first computes the Merkle root () by applying a multi-hash algorithm to the transactions in block , then forms , and finally calculates the chameleon hash using . Following the standard block-level editing protocol [3], we define the mutable parts of a block as the previous block hash , Merkle root , and timestamp , which are used for FPCH computation. The nonce () serves as the immutable component. This results in a policy-based, mutable block . The conventional hash function H is used to compute , serving as the for the next block and linking the blocks together.
- (iv)
- Bl-Level Editing: For Bl-level editing, a user executes , which produces . The node verifies its validity using . The validity of the new block is checked using by the node. Finally, to ensure the continuity of the blockchain, the condition must be satisfied.
- (2)
- Token Mechanism
- (i)
- Data Token (for editing data only):
- Tx-Level 1-Time/n-Times Data Token (/): A user holding can edit data with specific parameters only once. A user holding can perform up to n tx-level editings before the token expires.
- Bl-Level 1-Time/n-Times Data Token (/): A user holding can modify an entire block using specified parameters. A user holding can modify n blocks using relevant block parameters.
- (ii)
- Policy Token (for editing data and its access policy):
- Tx-Level 1-Time/n-Times Policy Token (/): Same as above.
- Bl-Level 1-Time/n-Times Policy Token (/): Same as above.
5.4. Security Model
- (1)
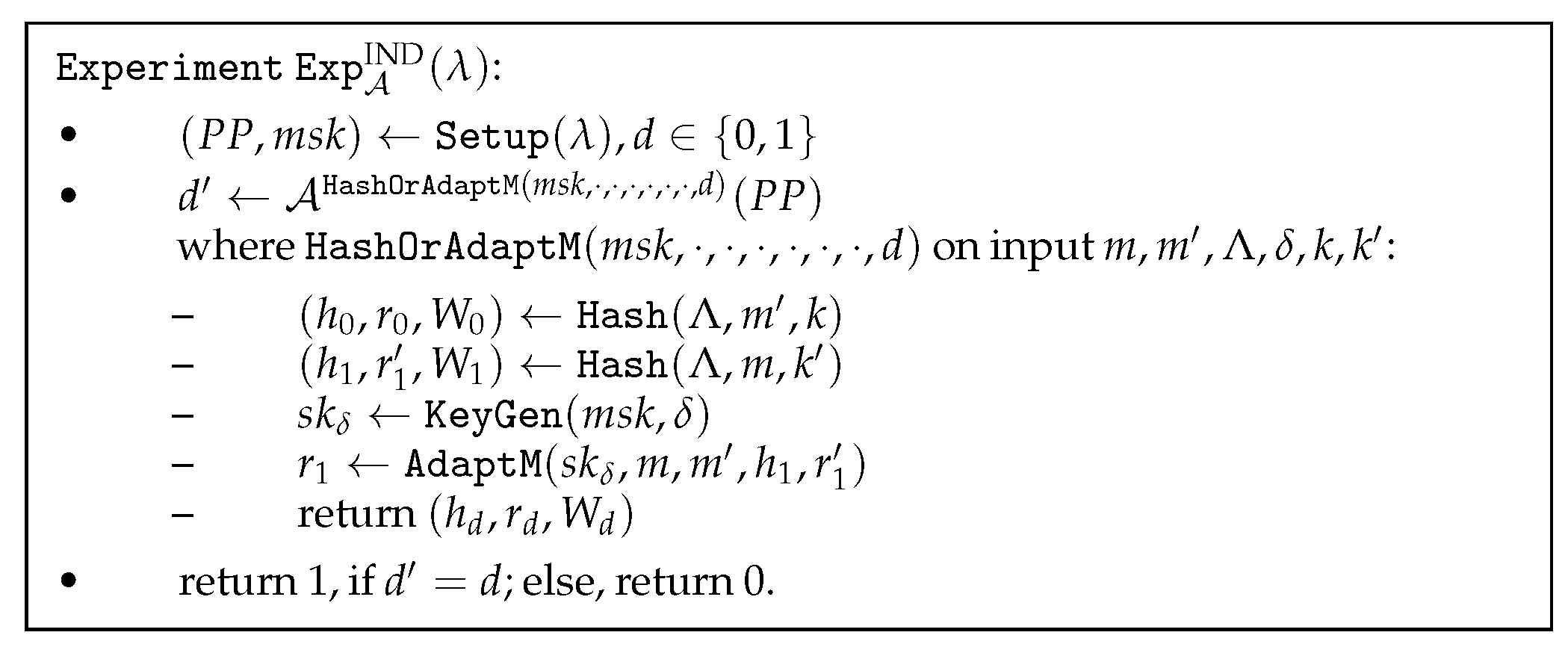
- IND-CPA Security ModelThe security model of RBFAC is defined as indistinguishability under a chosen-plaintext attack (IND-CPA). We present an experiment, including an adversary and a challenger :
- (i)
- Init: executes the Setup algorithm to generate the master key pair .
- (ii)
- Phase 1: makes a series of oracle queries by selecting user u and attribute set , requesting the corresponding attribute key from . executes the KeyGen algorithm to compute and transmits it to .
- (iii)
- Challenge: selects a pair of messages and for . randomly selects , executes the Hash algorithm to compute the ciphertext for message , and returns to .
- (iv)
- Phase 2: Phase 2 is identical to Phase 1.
- (v)
- Guess: outputs a guess for d.
The advantage of is defined as
- (2)
- EUF-CMA Security ModelAn adversary cannot fabricate a legitimate signature for a chameleon hash that corresponds to a specific identity. The experiment is defined in Figure 5. In this setting, we grant access to the Sign oracle, enabling it to verify whether a given chameleon hash is associated with a certain identity. The set Q is utilized to store all chameleon hashes queried by to the Sign oracle.We represent an original transaction as and its edited counterpart as , which are both linked to the chameleon hash h. Additionally, a transaction–identity association is denoted as . The advantage of is defined as
6. Instantiation
6.1. Setup
- (1)
- AA SetupThe attribute authority (AA) takes a security parameter and the user tree as input, executes TR-AP-CPABE.Setup, and initializes the master key pair . Then, the AA generates attribute keys for users and revokes malicious users.
- (2)
- TC SetupThe members of the initial token committee (TC) collaboratively generate secret shares of the master signing key . The TC then publishes the corresponding public key () and individual public shares (). Each secret share corresponds to a point on a polynomial F such that . This process can be implemented using a Distributed Key Generation (DKG) protocol [43]. The TC is responsible for verifying users’ editing requests and issuing editing tokens with appropriate permissions based on the verified requests.
6.2. KeyGen
6.3. Hash
- (1)
- Message EncryptionThe data owner uses the symmetric encryption [40] to encrypt the message. Select a message m and symmetric key ; then, compute .
- (2)
- Symmetric Key EncryptionThe data owner takes symmetric key , readability policy , and revocation list R as input, and the owner executes TR-AP-CPABE.Encrypt to generate the ciphertext of the symmetric key . Please note that in the original encryption TR-AP-CPABE.Encrypt, the message m is bound to the policy , and policy privacy protection prevents nodes from distinguishing between message editing and policy modification.
- (3)
- HashGenThe data owner randomly selects the trapdoor and randomness ; then, the owner computesand similar to Step (2), select the editability policy , and encrypt the information to obtain the editability ciphertext TR-AP-CPABE.Encrypt. Only authorized editors can decrypt to obtain the trapdoor t. Furthermore, permissions are downward compatible, allowing authorized editors to decrypt the message ciphertext as well.
- (4)
- ProofGenThe data owner randomly selects the proof value and randomness ; then, the owner computesand the following proof is constructed: . Similar to Step (2), select the advanced editing policy , and encrypt the information to generate the advanced ciphertext TR-AP-CPABE.Encrypt. Only authorized advanced editors can decrypt to obtain the proof value k. Furthermore, they can also decrypt the message ciphertext and edit the message.
- (5)
- SignatureGenThe data owner randomly selects the signing key and randomness ; then, the owner computesand the following signature is constructed: , where represents a message related to the trapdoor, facilitating the linking of different versions of the same transaction.
6.4. VerifyM
6.5. TkGen
6.6. VerifyTk
- (1)
- .
- (2)
- .
- (3)
- .
- (4)
- .
6.7. Read
6.8. AdaptM
- (1)
- Execute TR-AP-CPABE.Decrypt.
- (2)
- Execute and compute the updated randomness .
- (3)
- Generate a new signature .
6.9. AdaptP
- (1)
- Execute TR-AP-CPABE.Decrypt.
- (2)
- Execute TR-AP-CPABE.Encrypt based on the new readability policy .
- (3)
- Execute TR-AP-CPABE.Encrypt based on the new editability policy .
- (4)
- Select randomness and compute , ; construct the new proof .
- (5)
- Generate a new signature
6.10. Trace
6.11. UpdateCv
7. Security Proof
- : This represents the initial game for indistinguishability.
- : This game modifies as follows: The simulator selects an index guess g from the range for the HashOrAdaptM query. If the adversary does not issue an attack query at the g-th attempt, returns a random bit and halts the game. Thus, we obtain the following:
- : This game modifies as follows: During the g-th query, substitutes the trapdoor t with ⊥ in . We demonstrate that, assuming the ABE scheme is semantically secure, the advantage difference between and remains negligible.Consider targeting the semantic security of the ABE. Given the master public key , along with access to KeyGen and Encrypt oracles, attempts to differentiate the ciphertexts of and encrypted under a designated access policy . The game simulation for proceeds as follows:
- -
- assigns and faithfully executes the rest of the Setup procedure.
- -
- Using the provided oracles, honestly answers any KeyGen and Encrypt queries from . During the g-th query, provides the pair of messages to the ABE and receives the challenge ciphertext . Then, returns to , where , and . can also use the trapdoor t to successfully simulate adaptM queries.
If encrypts t, the simulation follows ; otherwise, it follows . Thus, if there is a significant difference in the advantage of between and , can exploit this to break the semantic security of the ABE. Thus, we obtain the following: - : This game modifies as follows: During the g-th hash query, the simulator hashes the ciphertext to obtain the chameleon hash pair instead of using AdaptM to compute . We prove that if the CH scheme is indistinguishable, the advantage difference between and is negligible.Consider targeting the indistinguishability of the CH scheme. Given the chameleon parameter and HashOrAdaptM oracle, honestly executes the Setup process. Specifically, sets the chameleon parameter for the g-th query as . If submits during the g-th query, first obtains the chameleon hash for from its HashOrAdaptM oracle. Then, simulates the ciphertext (with the encrypted trapdoor replaced by ⊥). Finally, returns to . outputs the same result as . If correctly predicts the random bit, then is able to break the indistinguishability of the CH.Thus, we obtain the following:Based on the results, we obtain the following:
- : This represents the initial game for collision resistance.
- : This game modifies as follows: selects an index guess g from the range for the Hash’ oracle, returning the chameleon hash . If does not issue an attack query at the g-th attempt, returns a random bit and halts the game.Thus, we obtain the following:
- : This game modifies as follows: During the g-th query, substitutes the trapdoor t with ⊥ in . We follow the same procedure as in the previous game to prove that the advantage difference between and is negligible. Consider targeting the semantic security of the ABE scheme. We obtain the following:
- : This game modifies as follows: During the g-th query, when outputs a valid collision that has not been previously generated by the AdaptM’ oracle, outputs a random bit. We prove that if the CH scheme achieves collision resistance, the advantage difference between and is negligible.Consider targeting the collision resistance of the CH scheme. aims to look for a collision for the given hash, and uses the same simulation method as in the previous games. If successfully finds a collision, is able to break the collision resistance of the CH. Thus, we obtain the following:Based on the results, we obtain the following:
- The forging attempt occurs in the g-th query.
- The pair links to the trapdoor t.
- The pair .
- , .
8. Implementation and Discussion
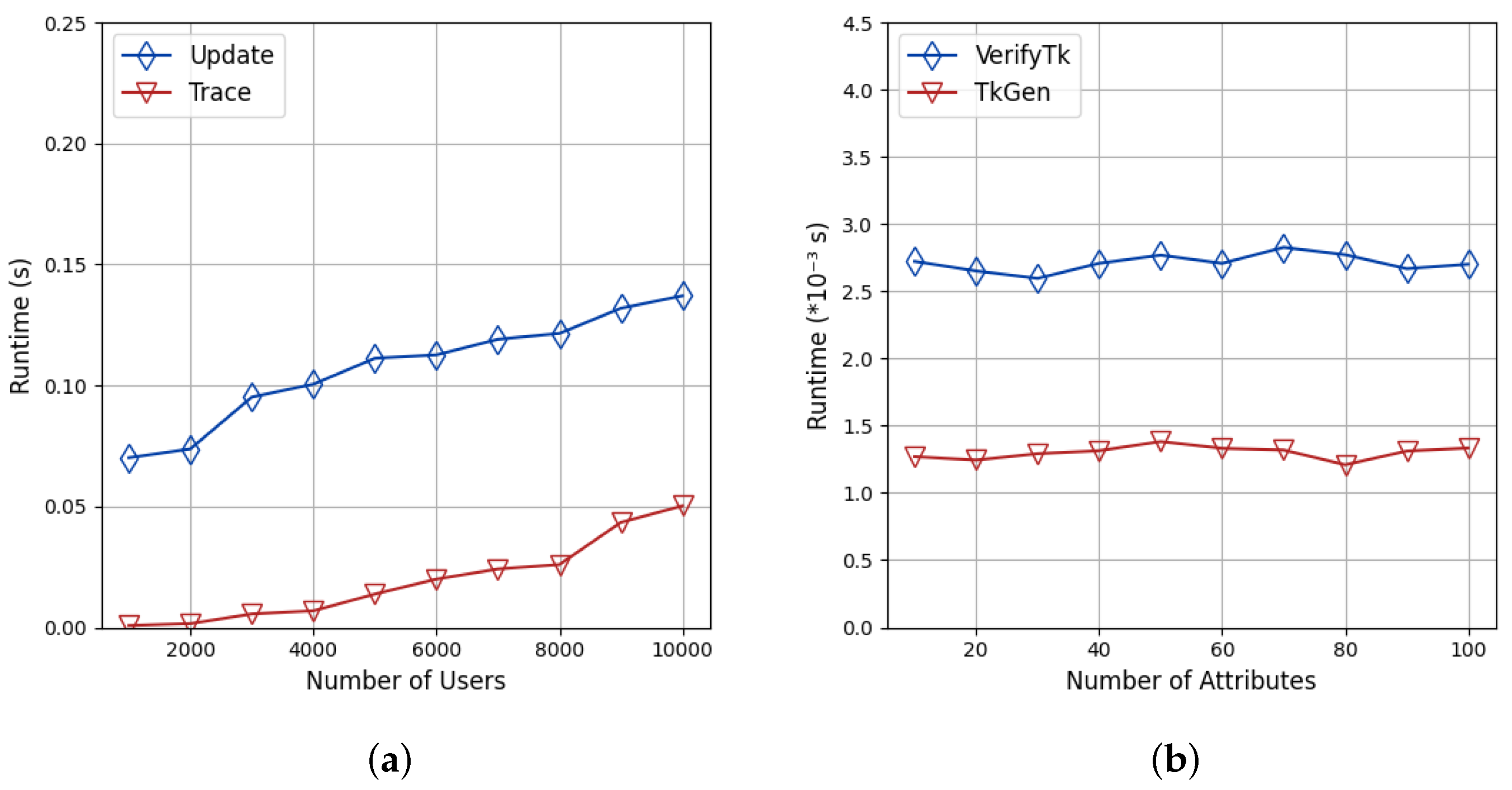
8.1. Performance Analysis
8.2. Blockchain Integration Overhead
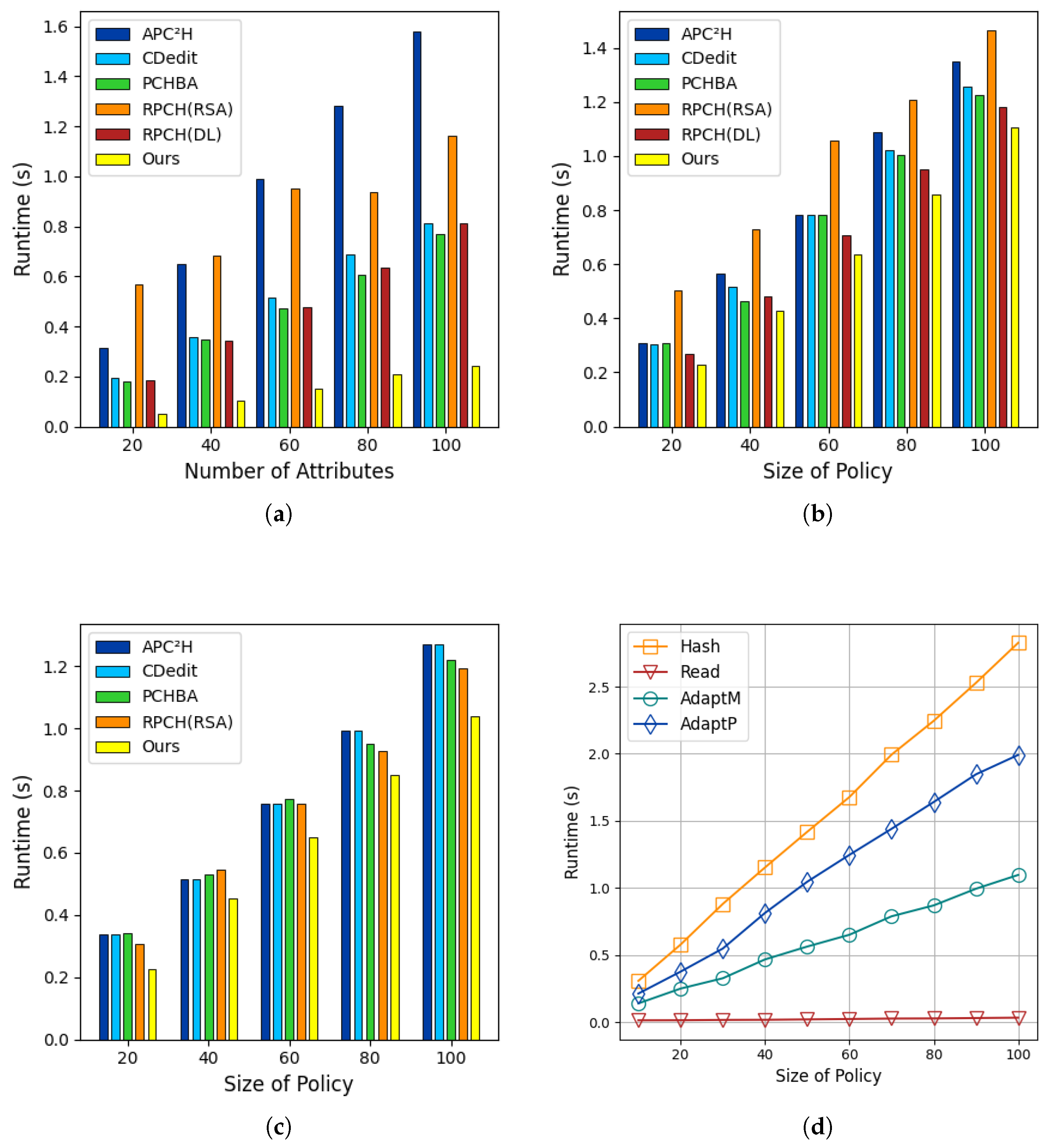
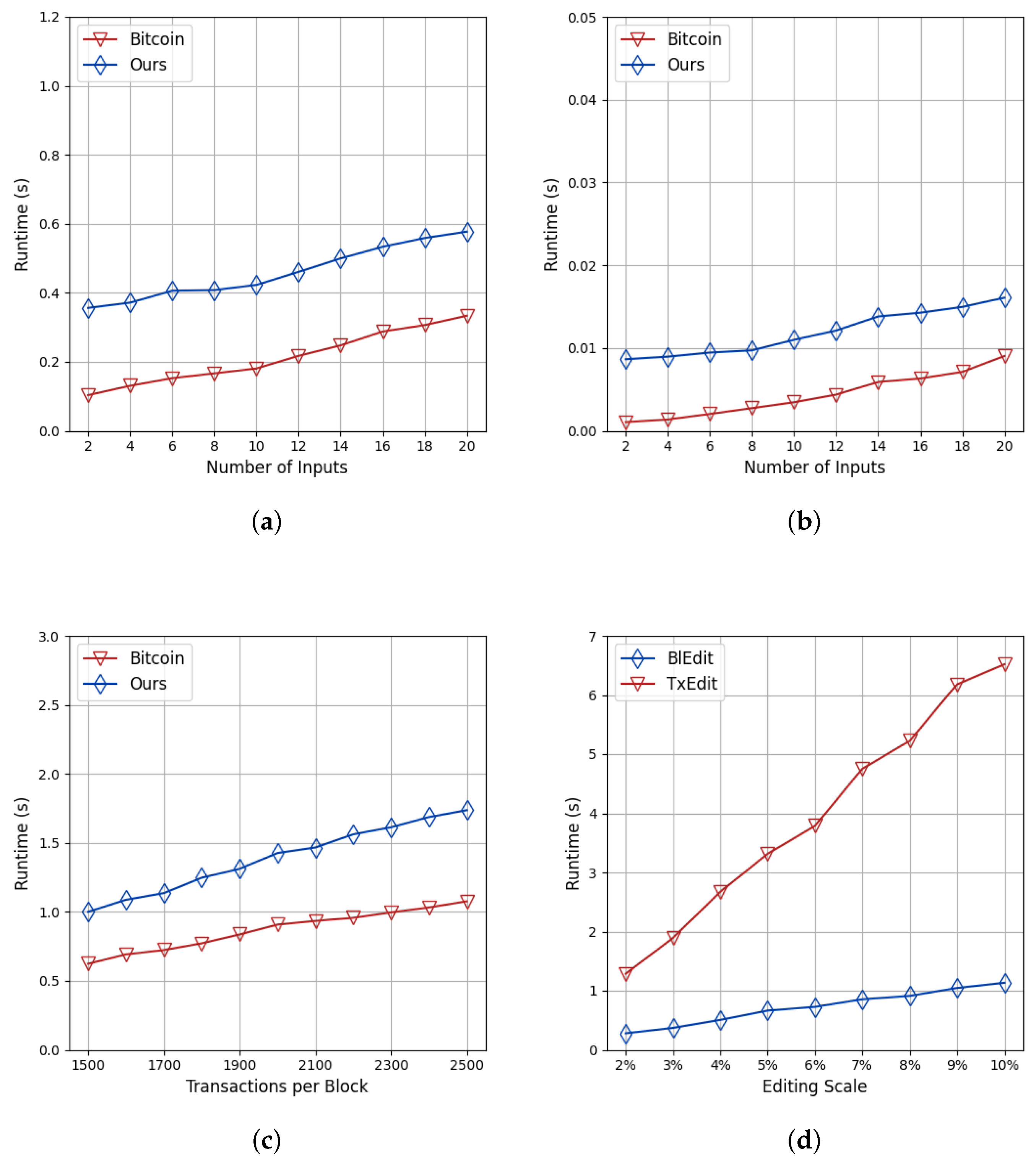
- Transaction Generation: Figure 9a shows a 0.3 s average delay compared to native Bitcoin when generating transactions with 2–20 inputs, two outputs, and a policy size of 10.
- Transaction Verification: Figure 9b reveals an additional 0.007 s overhead per transaction for validating chameleon hashes, signatures, and proofs.
- Block Generation: With 1500–2500 transactions per block and 5% mutable transactions, Figure 9c shows a 0.65 s average increase in block creation time. Since the collision-resistant hash was still used for transaction aggregation and block linking, mutable transactions or blocks introduce negligible overhead in Merkle tree generation and blockchain verification.
8.3. Overhead Comparison of Different Editing Granularities
8.4. Other Discussion
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 4, 15–16. [Google Scholar]
- General Data Protection Regulation. Available online: https://eugdpr.org (accessed on 20 October 2024).
- Ateniese, G.; Magri, B.; Venturi, D.; Andrade, E. Redactable Blockchain–or–Rewriting History in Bitcoin and Friends. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy (EuroS&P), Paris, France, 26–28 April 2017; pp. 111–126. [Google Scholar] [CrossRef]
- Krawczyk, H.; Rabin, T. Chameleon Hashing and Signatures. Cryptology ePrint Archive, Paper 1998/010. 1998. Available online: https://eprint.iacr.org/1998/010 (accessed on 20 October 2024).
- Derler, D.; Samelin, K.; Slamanig, D.; Striecks, C. Fine-grained and controlled rewriting in blockchains: Chameleon-hashing gone attribute based. In Proceedings of the 26th Annual Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 24–27 February 2019; pp. 1–51. [Google Scholar]
- Miao, M.; Wang, M.; Zhao, S.; Zhang, F.; Wei, J. Maintainable verifiable data streaming based on redactable blockchain. Comput. Stand. Interfaces 2025, 93, 103972. [Google Scholar] [CrossRef]
- Zhuang, C.; Dai, Q.; Zhang, Y. A secure and lightweight data management scheme based on redactable blockchain for Digital Copyright. Comput. Stand. Interfaces 2025, 91, 103875. [Google Scholar] [CrossRef]
- Tian, G.; Wei, J.; Miao, M.; Guo, F.; Susilo, W.; Chen, X. Blockchain-Based Compact Verifiable Data Streaming with Self-Auditing. IEEE Trans. Dependable Secur. Comput. 2024, 21, 3917–3930. [Google Scholar] [CrossRef]
- Wei, J.; Tian, G.; Chen, X.; Susilo, W. Lightweight 0-RTT Session Resumption Protocol for Constrained Devices. IEEE Trans. Inf. Forensics Secur. 2025, 20, 221–233. [Google Scholar] [CrossRef]
- Wei, J.; Tian, G.; Wang, D.; Guo, F.; Susilo, W.; Chen, X. Pixel+ and Pixel++: Compact and Efficient Forward-Secure Multi-Signatures for PoS Blockchain Consensus. In Proceedings of the 33rd USENIX Security Symposium (USENIX Security 24), Philadelphia, PA, USA, 14–16 August 2024; pp. 6237–6254. [Google Scholar]
- Tian, G.; Hu, Y.; Wei, J.; Liu, Z.; Huang, X.; Chen, X.; Susilo, W. Blockchain-Based Secure Deduplication and Shared Auditing in Decentralized Storage. IEEE Trans. Dependable Secur. Comput. 2022, 19, 3941–3954. [Google Scholar] [CrossRef]
- Shen, J.; Chen, X.; Wei, J.; Guo, F.; Susilo, W. Blockchain-Based Accountable Auditing with Multi-Ownership Transfer. IEEE Trans. Cloud Comput. 2023, 11, 2711–2724. [Google Scholar] [CrossRef]
- Tian, G.; Wei, J.; Kutyłowski, M.; Susilo, W.; Huang, X.; Chen, X. VRBC: A Verifiable Redactable Blockchain with Efficient Query and Integrity Auditing. IEEE Trans. Comput. 2023, 72, 1928–1942. [Google Scholar] [CrossRef]
- Benhamouda, F.; Halevi, S.; Krawczyk, H.; Ma, Y.; Rabin, T. SPRINT: High-Throughput Robust Distributed Schnorr Signatures. Cryptology ePrint Archive, Paper 2023/427. 2023. Available online: https://eprint.iacr.org/2023/427 (accessed on 20 October 2024).
- Han, D.; Pan, N.; Li, K.C. A Traceable and Revocable Ciphertext-Policy Attribute-based Encryption Scheme Based on Privacy Protection. IEEE Trans. Dependable Secur. Comput. 2022, 19, 316–327. [Google Scholar] [CrossRef]
- Xu, S.; Ning, J.; Ma, J.; Huang, X.; Deng, R.H. K-Time Modifiable and Epoch-Based Redactable Blockchain. IEEE Trans. Inf. Forensics Secur. 2021, 16, 4507–4520. [Google Scholar] [CrossRef]
- Chen, X.; Gao, Y. CDEdit: Redactable Blockchain with Cross-audit and Diversity Editing. In Proceedings of the 2022 IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Wuhan, China, 9–11 December 2022; pp. 945–952. [Google Scholar] [CrossRef]
- Shen, J.; Chen, X.; Liu, Z.; Susilo, W. Verifiable and Redactable Blockchains with Fully Editing Operations. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3787–3802. [Google Scholar] [CrossRef]
- Jia, M.; Chen, J.; He, K.; Du, R.; Zheng, L.; Lai, M.; Wang, D.; Liu, F. Redactable Blockchain From Decentralized Chameleon Hash Functions. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2771–2783. [Google Scholar] [CrossRef]
- Huang, K.; Zhang, X.; Mu, Y.; Wang, X.; Yang, G.; Du, X.; Rezaeibagha, F.; Xia, Q.; Guizani, M. Building Redactable Consortium Blockchain for Industrial Internet-of-Things. IEEE Trans. Ind. Inform. 2019, 15, 3670–3679. [Google Scholar] [CrossRef]
- Duan, J.; Wang, W.; Wang, L.; Gu, L. Controlled Redactable Blockchain Based on T-Times Chameleon Hash and Signature. IEEE Trans. Inf. Forensics Secur. 2024, 19, 7560–7572. [Google Scholar] [CrossRef]
- Xu, S.; Huang, X.; Yuan, J.; Li, Y.; Deng, R.H. Accountable and Fine-Grained Controllable Rewriting in Blockchains. IEEE Trans. Inf. Forensics Secur. 2023, 18, 101–116. [Google Scholar] [CrossRef]
- Tian, Y.; Li, N.; Li, Y.; Szalachowski, P.; Zhou, J. Policy-based chameleon hash for blockchain rewriting with black-box accountability. In Proceedings of the 36th Annual Computer Security Applications Conference, Austin, TX, USA, 7–11 December 2020; pp. 813–828. [Google Scholar]
- Xu, S.; Ning, J.; Ma, J.; Xu, G.; Yuan, J.; Deng, R.H. Revocable Policy-Based Chameleon Hash. In Proceedings of the Computer Security—ESORICS 2021, Darmstadt, Germany, 4–8 October 2021; Volume 12972, pp. 327–347. [Google Scholar]
- Tian, Y.; Miyaji, A.; Matsubara, K.; Cui, H.; Li, N. Revocable Policy-Based Chameleon Hash for Blockchain Rewriting. Comput. J. 2022, 66, 2365–2378. [Google Scholar] [CrossRef]
- Ma, J.; Xu, S.; Ning, J.; Huang, X.; Deng, R.H. Redactable Blockchain in Decentralized Setting. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1227–1242. [Google Scholar] [CrossRef]
- Zhang, C.; Zhao, M.; Liang, J.; Fan, Q.; Zhu, L.; Guo, S. NANO: Cryptographic Enforcement of Readability and Editability Governance in Blockchain Databases. IEEE Trans. Dependable Secur. Comput. 2024, 21, 3439–3452. [Google Scholar] [CrossRef]
- Tian, Y.; Liu, B.; Li, Y.; Szalachowski, P.; Zhou, J. Accountable Fine-Grained Blockchain Rewriting in the Permissionless Setting. IEEE Trans. Inf. Forensics Secur. 2024, 19, 1756–1766. [Google Scholar] [CrossRef]
- Deuber, D.; Magri, B.; Thyagarajan, S.A.K. Redactable Blockchain in the Permissionless Setting. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2019; pp. 124–138. [Google Scholar] [CrossRef]
- Li, X.; Xu, J.; Yin, L.; Lu, Y.; Tang, Q.; Zhang, Z. Escaping From Consensus: Instantly Redactable Blockchain Protocols in Permissionless Setting. IEEE Trans. Dependable Secur. Comput. 2023, 20, 3699–3715. [Google Scholar] [CrossRef]
- Wang, W.; Wang, L.; Duan, J.; Tong, X.; Peng, H. Redactable Blockchain Based on Decentralized Trapdoor Verifiable Delay Functions. IEEE Trans. Inf. Forensics Secur. 2024, 19, 7492–7507. [Google Scholar] [CrossRef]
- Guo, H.; Gan, W.; Zhao, M.; Zhang, C.; Wu, T.; Zhu, L.; Xue, J. PriChain: Efficient Privacy-Preserving Fine-Grained Redactable Blockchains in Decentralized Settings. Chin. J. Electron. 2025, 34, 82–97. [Google Scholar] [CrossRef]
- Guo, H.; Chen, L.; Ren, X.; Zhao, M.; Li, C.; Xue, J.; Zhu, L.; Zhang, C. Privacy-Preserving and Revocable Redactable Blockchains with Expressive Policies in IoT. IEEE Internet Things J. 2024, 11, 35390–35404. [Google Scholar] [CrossRef]
- Wang, S.; Guo, K.; Zhang, Y. Traceable ciphertext-policy attribute-based encryption scheme with attribute level user revocation for cloud storage. PLoS ONE 2018, 13, e0203225. [Google Scholar] [CrossRef]
- Ning, J.; Dong, X.; Cao, Z.; Wei, L.; Lin, X. White-Box Traceable Ciphertext-Policy Attribute-Based Encryption Supporting Flexible Attributes. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1274–1288. [Google Scholar] [CrossRef]
- Noack, A.; Spitz, S. Dynamic Threshold Cryptosystem Without Group Manager. Cryptology ePrint Archive, Paper 2008/380. 2008. Available online: https://eprint.iacr.org/2008/380 (accessed on 20 October 2024).
- Gilad, Y.; Hemo, R.; Micali, S.; Vlachos, G.; Zeldovich, N. Algorand: Scaling byzantine agreements for cryptocurrencies. In Proceedings of the 26th Symposium on Operating Systems Principles, Shanghai, China, 28 October 2017; pp. 51–68. [Google Scholar]
- Luu, L.; Narayanan, V.; Zheng, C.; Baweja, K.; Gilbert, S.; Saxena, P. A Secure Sharding Protocol For Open Blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, New York, NY, USA, 24–28 October 2016; CCS’16. pp. 17–30. [Google Scholar] [CrossRef]
- Hao, F. Schnorr Non-Interactive Zero-Knowledge Proof. Technical Report. 2017. Available online: https://datatracker.ietf.org/doc/html/rfc8235 (accessed on 20 October 2024).
- Goldwasser, S.; Micali, S. Probabilistic encryption. J. Comput. Syst. Sci. 1984, 28, 270–299. [Google Scholar] [CrossRef]
- Schnorr, C.P. Efficient signature generation by smart cards. J. Cryptol. 1991, 4, 161–174. [Google Scholar] [CrossRef]
- Derler, D.; Slamanig, D. Key-homomorphic signatures: Definitions and applications to multiparty signatures and non-interactive zero-knowledge. Des. Codes Cryptogr. 2019, 87, 1373–1413. [Google Scholar] [CrossRef]
- Gennaro, R.; Jarecki, S.; Krawczyk, H.; Rabin, T. Secure distributed key generation for discrete-log based cryptosystems. J. Cryptol. 2007, 20, 51–83. [Google Scholar] [CrossRef]
- Redactable Blockchain with Fine-Grained Access Control. Available online: https://github.com/Gofor-Light/RBFAC (accessed on 20 October 2024).



| [27] | [17] | [21] | [16] | [23] | [24] | [25] | [26] | [28] | |
|---|---|---|---|---|---|---|---|---|---|
| Readability Management | ✓ | × | × | × | × | × | × | × | × |
| Editability Management | ✓ | ✓ | × | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Access Policy Editing | × | × | × | × | × | × | × | × | × |
| Policy Protection | ✓ | × | × | × | × | × | × | × | × |
| Diversified Editing | × | ✓ | × | × | × | × | × | × | × |
| Decentralized Editing | × | × | ✓ | × | × | × | × | ✓ | ✓ |
| Controllability | × | ✓ | ✓ | ✓ | × | × | × | × | × |
| Accountability | × | ✓ | ✓ | ✓ | ✓ | × | × | ✓ | ✓ |
| Traceability | × | ✓ | × | × | ✓ | × | × | × | ✓ |
| User Revocation | ✓ | × | × | × | × | ✓ | ✓ | × | × |
| Notations | Descriptions |
|---|---|
| security parameter | |
| user tree | |
| master key pair | |
| master signing secret key and shares | |
| master signing public key and shares | |
| u | user identity |
| user’s attribute set | |
| access policies | |
| readability policy, editability policy, advanced editing policy | |
| data owner’s symmetric key | |
| user’s attribute key | |
| m | message |
| message ciphertext | |
| R | revocation list |
| readability ciphertext, editability ciphertext, advanced ciphertext | |
| trapdoor pair | |
| chameleon hash pair | |
| proof value pair | |
| proof randomness pair | |
| W | response |
| permission proof | |
| user’s signing key pair | |
| signature randomness pair | |
| message signature pair | |
| editing signature | |
| editing request | |
| TC’s signature | |
| editing token | |
| arbitrary ciphertext | |
| plaintext set | |
| X | ciphertext update parameter |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, S.; Wei, L.; Wu, S.; Zhang, L. RBFAC: A Redactable Blockchain Framework with Fine-Grained Access Control Based on Flexible Policy Chameleon Hash. Electronics 2025, 14, 1680. https://doi.org/10.3390/electronics14081680
Wu S, Wei L, Wu S, Zhang L. RBFAC: A Redactable Blockchain Framework with Fine-Grained Access Control Based on Flexible Policy Chameleon Hash. Electronics. 2025; 14(8):1680. https://doi.org/10.3390/electronics14081680
Chicago/Turabian StyleWu, Shiyang, Lifei Wei, Shihai Wu, and Lei Zhang. 2025. "RBFAC: A Redactable Blockchain Framework with Fine-Grained Access Control Based on Flexible Policy Chameleon Hash" Electronics 14, no. 8: 1680. https://doi.org/10.3390/electronics14081680
APA StyleWu, S., Wei, L., Wu, S., & Zhang, L. (2025). RBFAC: A Redactable Blockchain Framework with Fine-Grained Access Control Based on Flexible Policy Chameleon Hash. Electronics, 14(8), 1680. https://doi.org/10.3390/electronics14081680






