1. Introduction
Peer-to-peer (P2P) streaming has emerged as a promising paradigm for delivering multimedia content to large-scale audiences, eliminating the need for centralized content distribution networks (CDNs). This decentralized model leverages the collective bandwidth of peers to distribute video content more efficiently, thereby reducing server loads and enhancing scalability [
1]. With the increasing demand for multimedia services in entertainment, education, and surveillance, there is a growing need for more efficient and reliable P2P streaming solutions [
2]. Recent years have witnessed exponential growth in network traffic, primarily driven by streaming video applications, highlighting the need for optimized Internet infrastructure to ensure smooth multimedia transmission. Reports indicate that video streaming accounts for the majority of Internet traffic and this dominance is expected to continue [
3]. The rise of modern networking technologies, the expansion of over-the-top (OTT) content providers, and the increasing preference for online streaming over traditional broadcasting have made video transmission the most dominant type of Internet traffic. Video streaming applications account for approximately 66% of global Internet traffic, and live video made up more than 17% of all video traffic in 2023 [
4].
However, ensuring reliability, security, and quality of service (QoS) in decentralized P2P environments remains a significant challenge. In recent research, software-defined networking (SDN) and blockchain have been increasingly explored as complementary technologies to address these issues. SDN introduces centralized programmability by decoupling the control and data planes, enabling more adaptive and manageable network configurations [
5,
6]. This architectural flexibility enables efficient traffic management in dynamic streaming environments [
7], while also enhancing scalability and fault tolerance [
8]. Meanwhile, blockchain provides decentralized, tamper-proof data storage and secure peer-to-peer interactions, eliminating the need for intermediaries. Its distributed consensus mechanisms and cryptographic integrity have been applied in various domains to enhance trust and transparency [
9].
Although SDN–blockchain integration has been explored in domains such as IoT, 5G, and traditional CDNs [
5], its joint application in P2P streaming networks remains underdeveloped and often addresses challenges in isolation. Existing research can be broadly categorized into two streams. The first stream leverages SDN to enhance P2P networks by improving traffic management [
10], enabling reliable transmission for real-time video [
11], or constructing efficient overlays [
12]. However, these SDN-centric approaches typically lack a native mechanism for establishing decentralized trust and securing transactions between peers, leaving them vulnerable to malicious activities such as content pollution or peer collusion. The second stream of research employs blockchain to introduce trust and incentive models in P2P systems [
13,
14] or to optimize blockchain’s own P2P network for faster broadcast [
15]. Conversely, these blockchain-focused solutions operate on a relatively static network layer and lack the dynamic, real-time control capabilities needed to guarantee QoS for latency-sensitive video streaming, such as proactive congestion mitigation or SVC-aware routing.
This dichotomy highlights a clear research gap: the absence of a unified architecture that synergistically combines the real-time, QoS-aware control of SDN with the decentralized, tamper-proof security of blockchain, specifically tailored for the high-performance demands of P2P streaming. Prior works have not fully leveraged the potential of having a control plane for dynamic network optimization and a trust plane for secure interactions working in concert. While our previously published study in Electronics [
16] presented a comparative analysis of SDN–blockchain integration focusing on performance metrics, it stopped at a high-level comparison without proposing a detailed, implementable framework.
To address this gap, this study makes a distinct contribution by proposing a novel hybrid DSDN–blockchain framework. The key innovation lies in its hierarchical state machine design, which features two decoupled yet synergistic layers: a control plane layer managed by distributed SDN (DSDN) for real-time network orchestration, and a trust plane layer managed by blockchain for decentralized security and automation via smart contracts. This design explicitly tackles the intertwined challenges of performance, scalability, and security in a single, coherent model.
The primary objective of this research is to design, implement, and validate this framework through NS-3 simulations. Our specific goals are as follows:
To mitigate transmission delay through SDN real-time traffic optimization and blockchain-automated verification.
To manage overhead ratio by leveraging SDN centralized resource orchestration and distributing blockchain consensus load.
To ensure transmission security by combining SDN programmable security policies with a blockchain immutable ledger.
To quantitatively validate the framework’s efficacy against standalone blockchain and DSDN models by measuring throughput, latency, and energy consumption under varying network scales and security threats.
The remainder of this paper is organized as follows.
Section 2 provides a comprehensive literature review and a systematic analysis of the gaps in existing research.
Section 3 details the proposed hybrid framework and its operational workflow.
Section 4 presents the experimental results and comparative analysis. Finally,
Section 5 concludes the paper and outlines future work.
2. Literature Review
This section reviews the state-of-the-art approaches applied in P2P streaming networks, including SDN-based and blockchain-based solutions. It also highlights key research gaps and unresolved challenges in the existing methodologies.
The authors in [
17] present a unique hybrid redundancy system that guarantees the consistency of video data in P2P cloud storage while facilitating the fast streaming of video files. Their work makes three primary contributions. First, by using replication and erasure coding simultaneously, both streaming speed and storage capacity utilization can be improved. Second, by dynamically varying the redundancy level of each video data based on its appeal, the number of simultaneous playback requests handled may be minimized while also minimizing the drop in file availability. Third, by using storage capacity effectively and implementing the researchers’ suggested two-phase replacement approach, performance may be further enhanced. Moreover, the authors aim to improve their model and conduct trials with an improved bandwidth allocation, taking into account variables such as network type, location, and device capabilities, to increase the usability of their technique in more diverse network settings. The author in [
18] presented a “fuzzy logic-based prediction” technique to forecast, in terms of characteristics such as buffer size and bandwidth, the system of control that would be suitable for the desired peers. Depending on which threshold layer the model predicts, the model uses alternative control strategies in the event of a flash crowd. These include preserving system resources, giving top-performing peers precedence, rejecting the requests of the lowest-performing peers, and somewhat lowering service quality. They also describe peers’ credit scores, which indicate their respective achievements. However, the suggested solution has a high level of overall complexity.
The integration of SDN and blockchain is being actively explored to create robust security architectures beyond streaming. For instance, the author in [
19] proposes an optimized, energy-efficient blockchain-based SDN framework for the IoT, which uses a trust-based classifier to handle and reduce malicious traffic, demonstrating improved throughput and energy efficiency [
19]. Building on this, the author in [
20] presents an AI-empowered, blockchain-and-SDN-integrated security architecture for the IoT, which uses a cluster-based routing protocol and distributed authentication to outperform traditional protocols in energy consumption and network throughput [
20].
The author in [
21] designed a “software-defined mobility architecture for NDN”, extending the SDN paradigm to facilitate NDN architecture mobility handling. Additionally, the software-defined mobile design for NDN, specifically addressing “intra-domain and inter-domain changeover management situations,” is explained. This includes a demonstration of the “Mininet and Opnet” scenarios with enhanced security. To reduce packet loss, the authors of [
11] suggested the use of SDN switches with a retransmission mechanism that includes a buffering agent. Furthermore, the framework enhances practicality and dependability by utilizing SDN controllers to provide a reliable UDP structure for efficient data transport. Furthermore, the existing context has wide application to UDP streams, even if it does not expressly handle multimedia-specific optimizations or video frame prioritization. It is believed that incorporating these additional methods will significantly enhance the effectiveness of their work; therefore, the researchers wish to investigate them further in their subsequent studies. Beyond trust and security, the underlying P2P topology significantly impacts performance. The author in [
12] presents a decentralized multi-venue real-time video broadcasting system that employs a novel P2P chain topology over IPv6 with intelligent self-healing mechanisms. This approach achieves substantial improvements in latency, video quality stability, and fault tolerance, demonstrating the performance gains possible with optimized overlays tailored for real-time streaming [
12]. At the intersection of P2P networks and lightweight security, the author in [
22] proposes a Physical Unclonable Function (PUF)-based mutual authentication and key exchange protocol for P2P IoT applications. This protocol allows two resource-constrained devices to authenticate each other directly without storing challenge–response pairs, providing a lightweight security solution resistant to replay and man-in-the-middle attacks.
FRING, a geography-based P2P overlay network for quick and reliable broadcast in blockchain systems, is presented in [
23]. Three key characteristics of FRING are its rapid convergence, reduced message redundancy, and adequate resilience. FRING develops the network architecture by taking geographical closeness into account, which reduces convergence time. A new broadcast technique, based on the FRING topology, is proposed that reduces message redundancy while maintaining sufficient resilience. Reducing the possibility of topological inference via traffic pattern analysis is a significant task. FRING utilizes Intel SGX to ensure that nodes operate in an integrity-preserving manner and incorporates pattern obfuscation to thwart traffic pattern analysis. Additionally, by modeling the per-hop network latency fluctuations depending on the abstract length between every two nodes, large-scale tests are conducted in AWS data centers within a single region. It is widely recognized that simulating realistic networks is a challenging task. In [
24], the author examines the “socio-technical interaction and mechanism for sustainable peer-to-peer (P2P)” energy trading from three perspectives: the social perspective, which focuses on the collaboration of multi-level marketplace players; the technical perspective, which emphasizes the exchange of advanced flexibility; and the financial perspective, which examines cooperative decentralized/regulated marketplaces.
There are three inquiries in this study: How does the operational structure in the P2P trading of energy achieve interoperable markets with the formation of P2P energy communities and the injection of multi-scale adaptability services? How does the use of ICT enable the co-creation of decentralized, diverse, user-centered digital frameworks to support large-scale P2P trading interaction? What services related to energy motivate international relationships for the exchange of multiple scales of P2P flexibility? The interplay among these factors may result in several problems, including the settlement issue. Furthermore, recent advances have refined the concept of blockchain-based incentivization. The author in [
25] proposes a framework for blockchain-based P2P content delivery with monetary incentivization and fairness. Their FairStream protocol ensures that deliverers are paid proportionally to their in-time delivery, guaranteeing fairness for all parties even under collusion, which addresses critical trust issues in ad hoc P2P settings.
In [
26], the author proposes a blockchain network design that ensures flexibility, fast reconfigurability, compactness, and efficient clustering, while reducing topology management overhead. To achieve this, they apply the SDN paradigm, where a secure overlay of synchronized servers takes control of the P2P topology, rather than the peers themselves. This overlay is built using random r-out digraphs and analyzed through binomial distribution and preferential attachment models to maintain a stable structure. The design sets controlled limits on inbound and outbound links to ensure connectivity while reducing peer load. Key network properties such as connectedness, diameter, and clustering are also examined. Finally, the system is designed to dynamically adjust the network’s structure based on usage needs, allowing the P2P layer to scale and adapt in practical scenarios.
2.1. Comparison with Recent SDN–Blockchain Integrations
While recent studies have made significant strides in integrating SDN and blockchain, key gaps remain for P2P streaming applications. For instance, in [
26], the SDN paradigm is successfully applied in the management of blockchain P2P topologies for efficiency, but it does not address the specific QoS demands of real-time video streaming such as dynamic bandwidth allocation for SVC layers. Similarly, in [
15], BlockP2P-EP enhances blockchain broadcast using trust and clustering but lacks the dynamic network control provided by SDN to proactively mitigate latency and congestion. Our work bridges this gap by proposing a unified control–trust layer that leverages both DSDN for real-time, QoS-aware traffic engineering and blockchain for decentralized security and incentives, creating a holistic solution tailored for the high-throughput, low-latency requirements of P2P video streaming.
Table 1 summarizes the literature survey.
The analysis in
Table 1 clearly demonstrates that while individual studies make progress in specific areas, none provide a holistic solution.
2.2. Existing Integrations and Gaps in Current Research
This section outlines some of the specific issues addressed in previous work. The majority of the problems faced by existing works are related to security issues, load balancing issues, and other concerns. Some of the specific difficulties encountered in previous works are described below.
The authors in [
27] analyze the behavioral characteristics of P2P using formal verification approaches. To determine whether every potential activity within P2P streaming systems complies with the established criteria, temporal logic is used. The researchers use model checking to verify that the temporal characteristics of the suggested system meet the requirements and to assess the coherence, fullness, and confidence of the model. However, in this research, a transmission delay failure occurred.
In [
28], a novel approach to reducing content pollution in peer-to-peer networks that transmit live video is proposed and comparison-based diagnostics are employed. This comprehensive approach effectively prevents the spread of contaminated information. Peers use the method to identify and steer clear of pollutants independently. Fireflies is a scalable overlay network on which the solution is built. The primary concerns include the fact that the research focuses on analyzing dynamic and self-adaptive monitoring, which can increase or decrease in runtime based on system load.
An “incentive-aware pricing game for interest-based socially aware forwarding” in DTNs is presented in [
29]. To improve content distribution in DTNs, the researchers construct a price game between nodes based on the Rubinstein Bargain model. Based on three factors—the social strength of the communication nodes, message value, and remaining battery life—the authors determine the price and degree of collaboration. Moreover, the suggested technique enables nodes to exchange information peer-to-peer, thereby improving the dissemination of large messages in such networks. However, when the number of nodes increases, the overhead ratio rises slightly.
To reduce the burden on the SDN control plane, the author in [
30] sought to enhance the general performance of TC by choosing a pertinent FS using the SL approach. To achieve this, the authors recommend the following actions. First, the Boruta FS mechanism should be used. Second, the authors suggest three streaming-based TC techniques for SDN: “k-nearest neighbor with adaptive sliding window detector (KNN-ADWIN), adaptable random forest (ARF), and Hoffding adaptive trees (HAT)”. These methods can reduce the overhead of the SDN controller by dynamically managing concept drift and resolving issues related to memory and time usage. Third, the performance of the suggested FS and streaming TC is assessed using both artificial and actual traffic traces. The primary concern of this research is that the approach needs to be validated across heterogeneous network topologies to confirm its efficiency and scalability.
A trust-enhanced blockchain P2P architecture that considers communication rate and transmission dependability was established in [
15]. Transmission dependability indicates whether the transmission rate varies significantly over erratic network connections, while the transmission rate itself indicates how quickly blocks and transactions are distributed throughout a blockchain network. “BlockP2P-EP”, a unique “trust-enhanced blockchain topology”, is presented in this study to retain transmission reliability while accelerating transmission pace. BlockP2P-EP first manages the “geographical proximity sensing clustering”, which groups proximity peer nodes into clusters using the K-Means method. Subsequently, the node attribute classification-based hierarchical topological structure guarantees robust connections and a compact diameter. The authors suggest creating a network architecture that is strengthened by trust. BlockP2P-EP implements the parallel spanning tree broadcast technique on top of a trust-enhanced blockchain architecture, providing rapid data broadcast across nodes within and between clusters. To lessen the network burden, a proper node inactivation detection technique is implemented. To confirm the legitimacy of the BlockP2P-EP protocol, the researchers meticulously create and execute a blockchain network simulator. However, despite enhancing the efficiency of the existing blockchain network, BlockP2P-EP prioritizes both transmission speed and reliability, but does not correctly validate the data in transmission. This represents a lack of transmission security.
2.3. Integrated SDN–Blockchain Solution for P2P Streaming
The integration of SDN into P2P streaming networks significantly enhances scalability, enables system load optimization, and reduces communication delays. By leveraging SDN programmability and centralized control, these networks can dynamically adapt to various topologies while maintaining performance. At the same time, security issues in P2P streaming can be effectively mitigated through SDN’s centralized policy enforcement and flow control. On the other hand, blockchain contributes secure data distribution, end-to-end encryption, immutable audit trails, and decentralized trust mechanisms. These features reinforce transmission security and improve the integrity of communication in P2P systems.
The collaboration between SDN and blockchain yields highly efficient, secure, and resilient peer-to-peer (P2P) streaming. Together, they provide a robust architecture that addresses both latency and security challenges, ensuring a scalable and reliable user experience.
3. Proposed Work
We propose a novel hybrid framework that integrates distributed software-defined networking (DSDN) with blockchain technology to address key challenges in peer-to-peer (P2P) streaming systems. The framework is conceptualized as a hierarchical state machine with two synergistic control layers: a control plane layer (managed by DSDN) and a trust plane layer (managed by blockchain). This bifurcation allows for the decoupling of network efficiency from transactional security, enabling independent optimization and robust integration. The overall architecture, operates on the following hierarchical principle:
Control plane layer (DSDN): This layer is responsible for real-time network intelligence and orchestration. The distributed SDN controller maintains a global view of the network topology, monitors link states, and executes dynamic traffic engineering. Its functions include the following:
Path computation: Calculating optimal low-latency paths for media streams.
Traffic scheduling: Rerouting flows dynamically to avoid congestion.
QoS-aware routing: Prioritizing traffic based on application requirements.
Security policy enforcement: Implementation of proactive security via intrusion detection system (IDS) access control list (ACL) modules integrated directly into the controller.
Trust plane layer (blockchain): This layer provides a decentralized trust anchor for the P2P network. It manages secure identities, records all transactions immutably, and automates enforcement through smart contracts. Its functions include the following:
Peer authentication and authorization: Verifying the identity of participating nodes.
Immutable logging: Recording all data block requests, transfers, and peer reputations.
Smart contract execution: Automating processes like trustworthy peer discovery and incentive distribution.
Data-in-transit security: Leveraging cryptographic modules for securing communication channels.
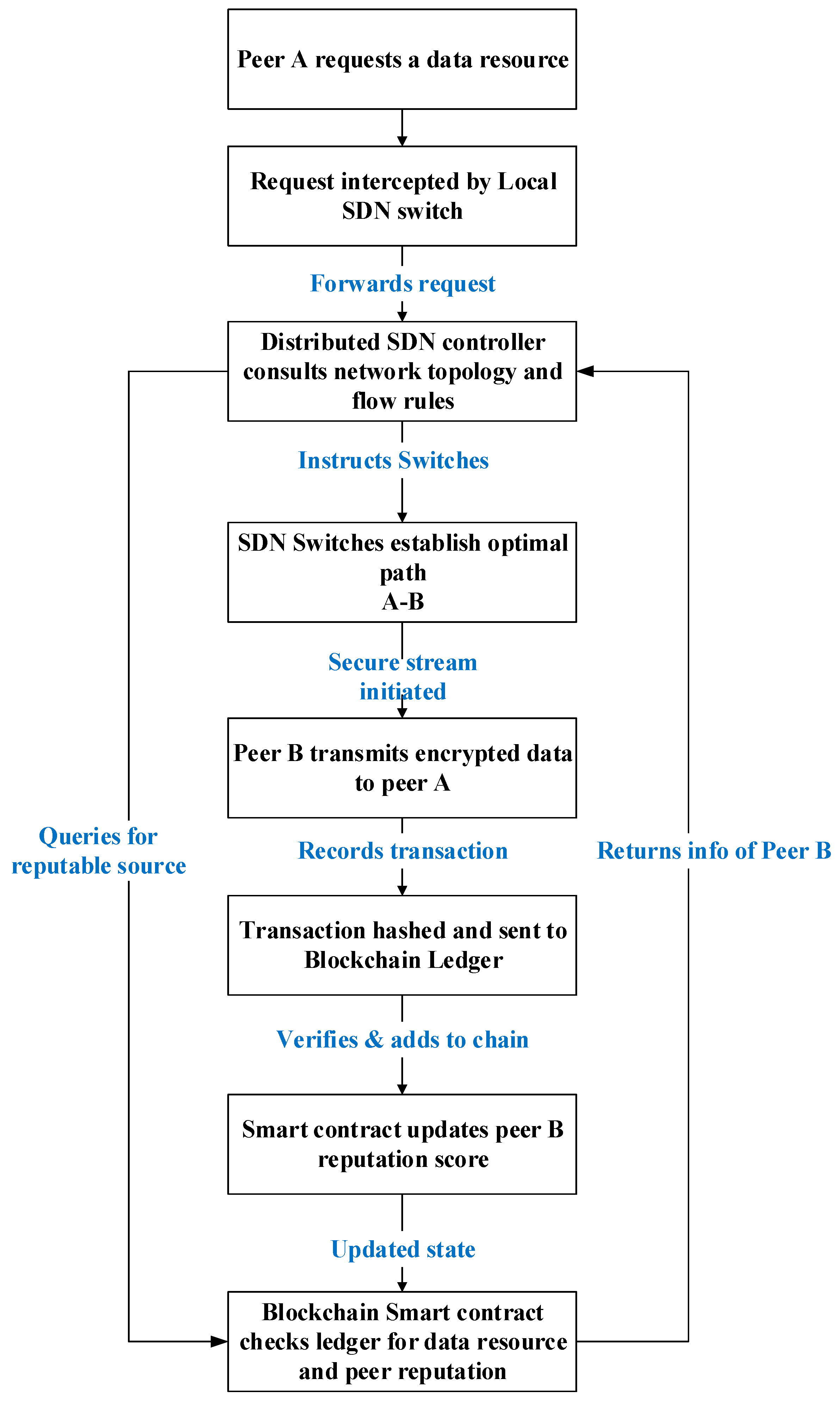
The operational flow of the proposed system is illustrated in
Figure 1, which presents a sequence diagram describing the interaction between the DSDN control plane and the blockchain ledger. The process begins when a peer (Peer A) requests a specific data block. This request is intercepted by the local SDN switch and forwarded to the distributed controller, which maintains a global view of the network. Before routing the request, the controller consults a blockchain-based smart contract to identify a trustworthy peer (Peer B) that holds the required resource. The smart contract uses historical transaction records to evaluate the reputation of Peer B. Once validated, the controller computes the optimal communication path and initiates data transfer over the DSDN-managed route. Upon successful transmission, the transaction is logged on the blockchain ledger, updating Peer B’s reputation score to encourage future cooperation and trust.
To implement this vision, the framework is decomposed into three major modules, as detailed below. Additionally, this study integrates established techniques, such as GPSC clustering and SHNT topology formation, into a unified simulation framework, enabling, for the first time, a practical evaluation of their combined effectiveness in decentralized P2P streaming—something not explored in our prior analytical study [
16].
3.1. Hierarchical Model
To provide a rigorous theoretical foundation for our framework, we model the proposed system as a hierarchical state machine composed of three distinct planes: the control plane, the data plane, and the trust plane. This abstraction decouples the system’s concerns, allowing for independent analysis and verification of each layer’s logic and interactions.
Control plane (CP): This plane, managed by the distributed SDN (DSDN) controllers, is responsible for global network intelligence and real-time orchestration. It maintains the global view of the network topology and link states. Its states can be defined as , where is the network graph, is the set of real-time link states, and is the set of active flows.
Data plane (DP): This plane consists of the underlying network infrastructure that forwards traffic based on rules installed by the control plane. Its state is the collective state of all forwarding devices and data streams.
Trust plane (TP): This plane, managed by the blockchain, provides a decentralized trust anchor. Its state is the immutable, cryptographically secured ledger, represented as , a chain of blocks containing transactions, peer reputations and smart contract code. The synergy between the control and trust planes is the core innovation of our framework. We define a state transition function that governs the system’s behavior in response to an event. The transition is not solely dependent on the control planes state: it is also conditioned on the state of the trust plane.
This function can be decomposed into the following coordinated workflow, which is also illustrated in the sequence diagram of
Figure 1:
This formal model ensures that every data flow is predicated on a verified trust relationship, and every successful transaction reinforces the trust model, creating a feedback loop that enhances both security and efficiency.
3.2. SDN-Enhanced Peer-to-Peer Network
Integrating software-defined networking (SDN) into peer-to-peer networks enables the efficient management of network resources and dynamic adaptation to changing conditions, thereby enhancing scalability and reliability and reducing delay. The primary aspects of the flow are outlined below.
3.2.1. Network Construction
The suggested architecture offers high bandwidth, low latency, and management accessibility by establishing direct, dedicated communication lines between nodes using a point-to-point topology.
3.2.2. Traffic Scheduling
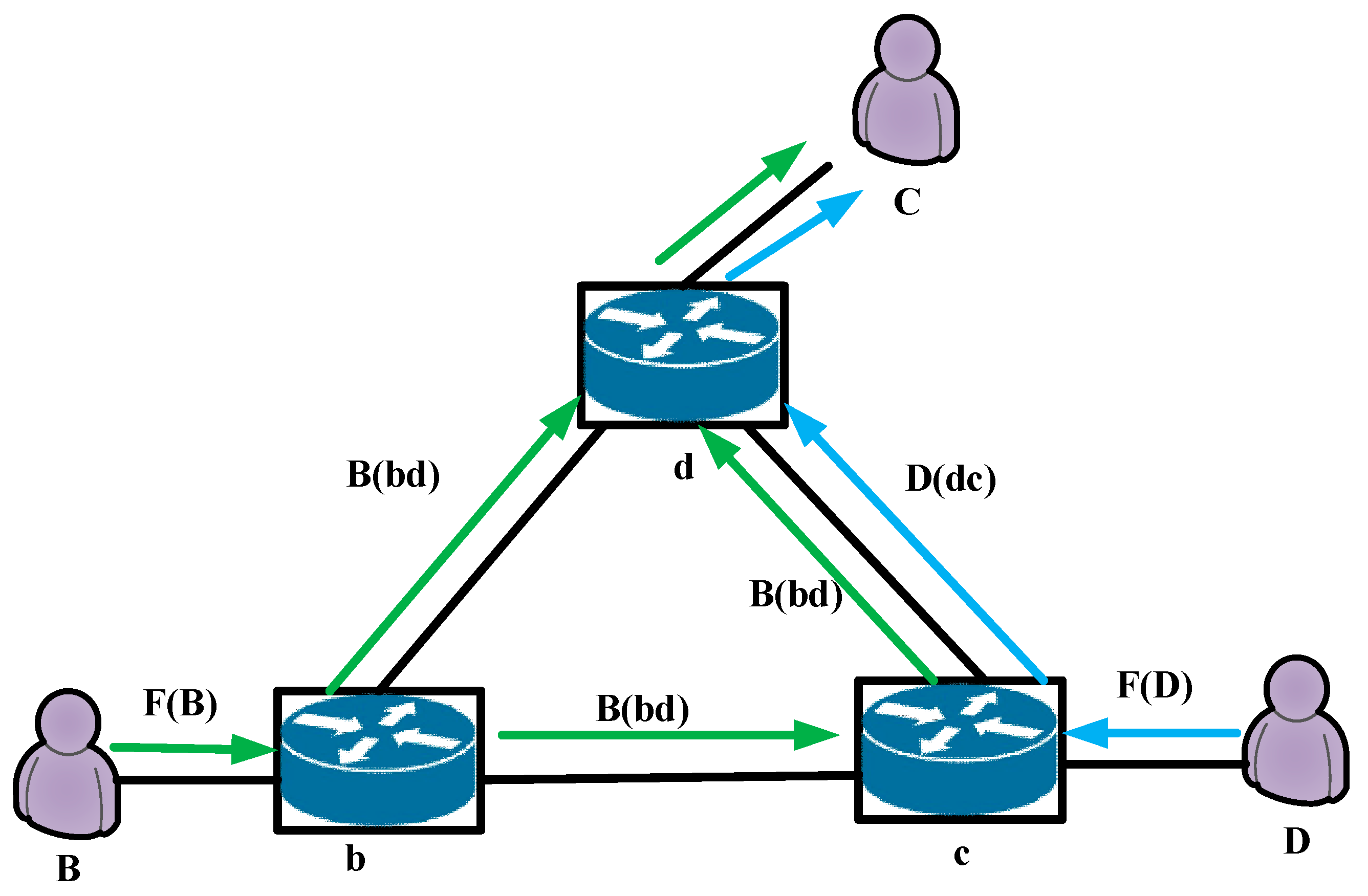
The traffic scheduling strategy, summarized in
Figure 2, leverages the SDN controller’s global view of the network topology and real-time link load. Let
and
represent the traffic demands of nodes
and
, respectively both transmitting to destination node
. If the traffic load
exceeds the capacity of the shortest path
, causing congestion, a portion of this traffic can be rerouted via paths
and
. This multi-commodity flow issue is managed by the SDN controller, which dynamically allocates traffic to different connections by selecting independent output ports for each flow, subject to the capacity constraints of each network link. In
Figure 2 the arrows indicate data flow paths: the blue arrow represents the primary congested path, while the green arrow shows the alternative traffic route allocated by the SDN controller to alleviate congestion.
and denote the flows that node transmitted on connections and , respectively. The traffic transmitted by node on link is denoted as . The network performance may be negatively impacted by flows directed at the same node, congesting the same connection. The SDN controller can selectively choose the independent output ports for each flow and allocate traffic to various connections, as it has a global topology view and is aware of the real-time load on each link. In network flow theory, this is recognized as a multi-commodity flow problem. In current technologies, ports and interfaces can be utilized in a one-to-many correlation to accomplish dynamic link consolidation between connected switches, which can offer better controllability and flexibility by configuring forwarding gadgets in a bond mode (“enabling the LACP protocol”). While it is essential to ensure that a stream is delivered in the same manner for delay-sensitive applications, dividing a stream into multiple paths has no significant impact on other applications.
3.2.3. Interconnected Bandwidth Allocation
The interconnected bandwidth allocation model is illustrated in
Figure 3. This scenario is fundamental to P2P networks and critically differentiates streaming from simple file sharing. In a classic P2P file sharing system, the primary goal is eventual, complete download. Bandwidth allocation can be more opportunistic, and temporary unfairness has a lesser impact on the end-user experience. However, in P2P streaming, the goal is the continuous, real-time, and timely delivery of data blocks to sustain video stuttering, buffering, and poor quality of experience (QoE). The scenario in
Figure 3 depicts this core challenge: nodes
and
are simultaneously transmitting data to node
. Consequently, the peer-to-peer (P2P) connections
and
must compete for the available bandwidth on
access link.
This allocation is governed by an internal incentive mechanism, analogous to those found in systems such as BitTorrent. Node evaluates the historical contributions of nodes and based on the volume of data each has previously uploaded to it. If the quantity of data received from node over connection is insufficient for a sustained period, node will assign it a lower priority. This may result in node reducing its upload rate to node or severing the connection entirely in favor of establishing links with more cooperative nodes. The SDN switches then use the specified output ports to execute this traffic scheduling, thereby implementing the intended bandwidth allocation plan. To realize these advanced quality of service (QoS) functions, the OpenFlow switch can be integrated with the Linux kernel’s traffic control module, supporting sophisticated policies such as hierarchical flow classification and bandwidth rate limiting. This SDN-driven enforcement of a streaming-aware incentive mechanism is crucial for maintaining low-latency, high-throughput data delivery and ensuring a fair and stable streaming environment for all participating peers.
The SDN controller defines each flow and populates the flow tables on the SDN switches. These switches then use the specified output ports and queues to execute traffic scheduling, thereby implementing the intended bandwidth allocation plan. To realize advanced quality of service (QoS) functions, the Open switch can be integrated with the Linux kernel’s traffic control module (Hierarchical Token Bucket), supporting sophisticated policies such as hierarchical flow classification and bandwidth rate limiting.
3.2.4. QoS-Aware Routing Mechanism
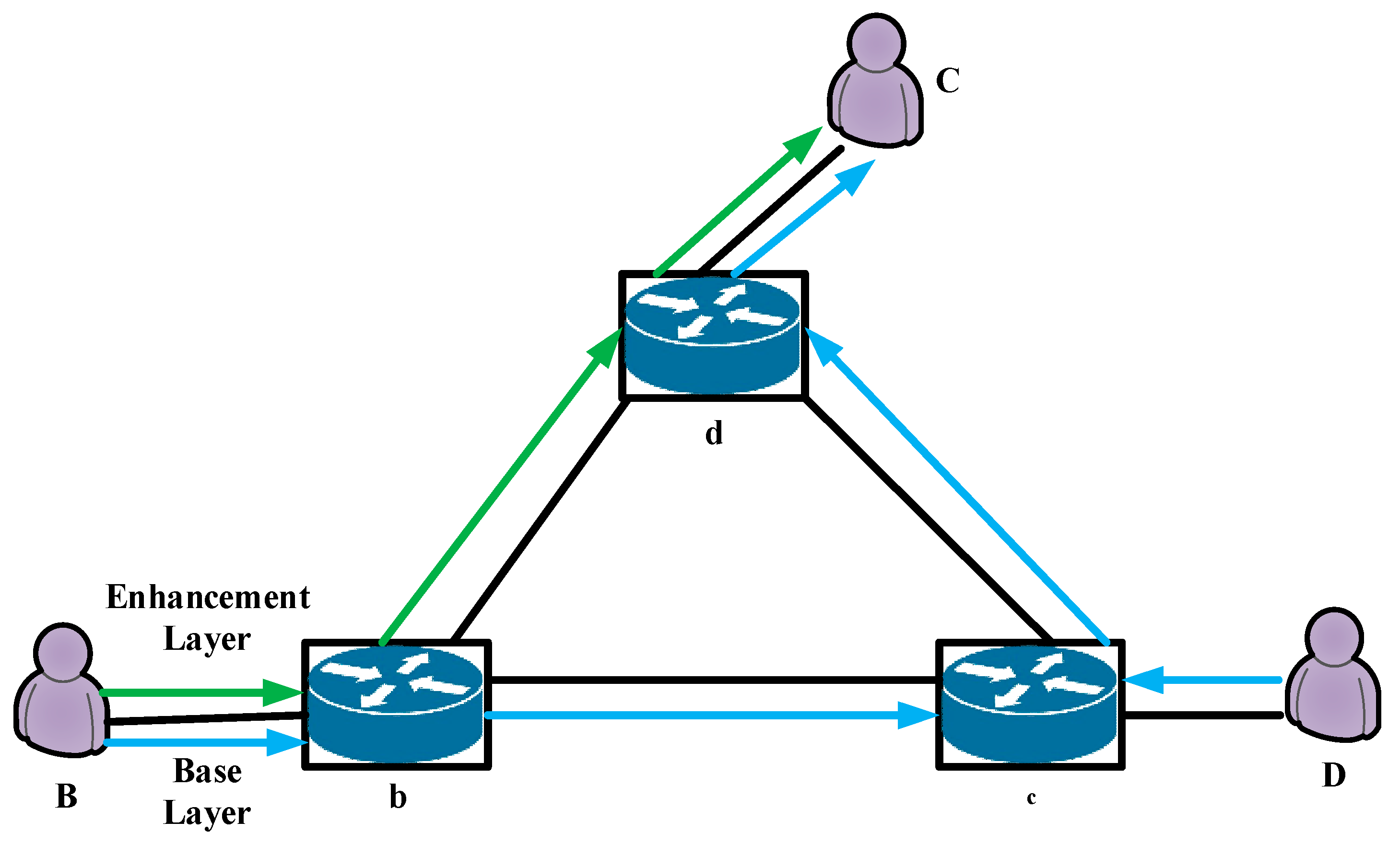
The proposed QoS routing technique is illustrated in
Figure 4. It depicts a scenario where scalable video coding (SVC) data is transmitted from a source node
to destination node
In a traditional peer-to-peer (P2P) system, all data would typically follow a single, identical path.
In contrast, the SDN-enabled QoS routing method allows for dynamic and differentiated path selection. The SDN controller continuously monitors the network and can select a path with higher available bandwidth, such as , for transmitting the crucial base layer of the SVC stream. Simultaneously, a shortest-path-first algorithm can be used to route enhancement layers along a faster, lower-latency path, like .
A fundamental metric for this routing is the bottleneck bandwidth, as it dictates the path’s maximum data transfer rate. In P2P streaming, the efficiency of transferring media blocks—measured by their timely and complete arrival—is the primary factor governing the user’s quality of experience (QoE). While traditional metrics such as delay and jitter are necessary, their impact is indirect, as they influence the transmission efficiency of this block, which ultimately governs video playback fluency.
3.3. Integration of Blockchain into Peer-to-Peer Network
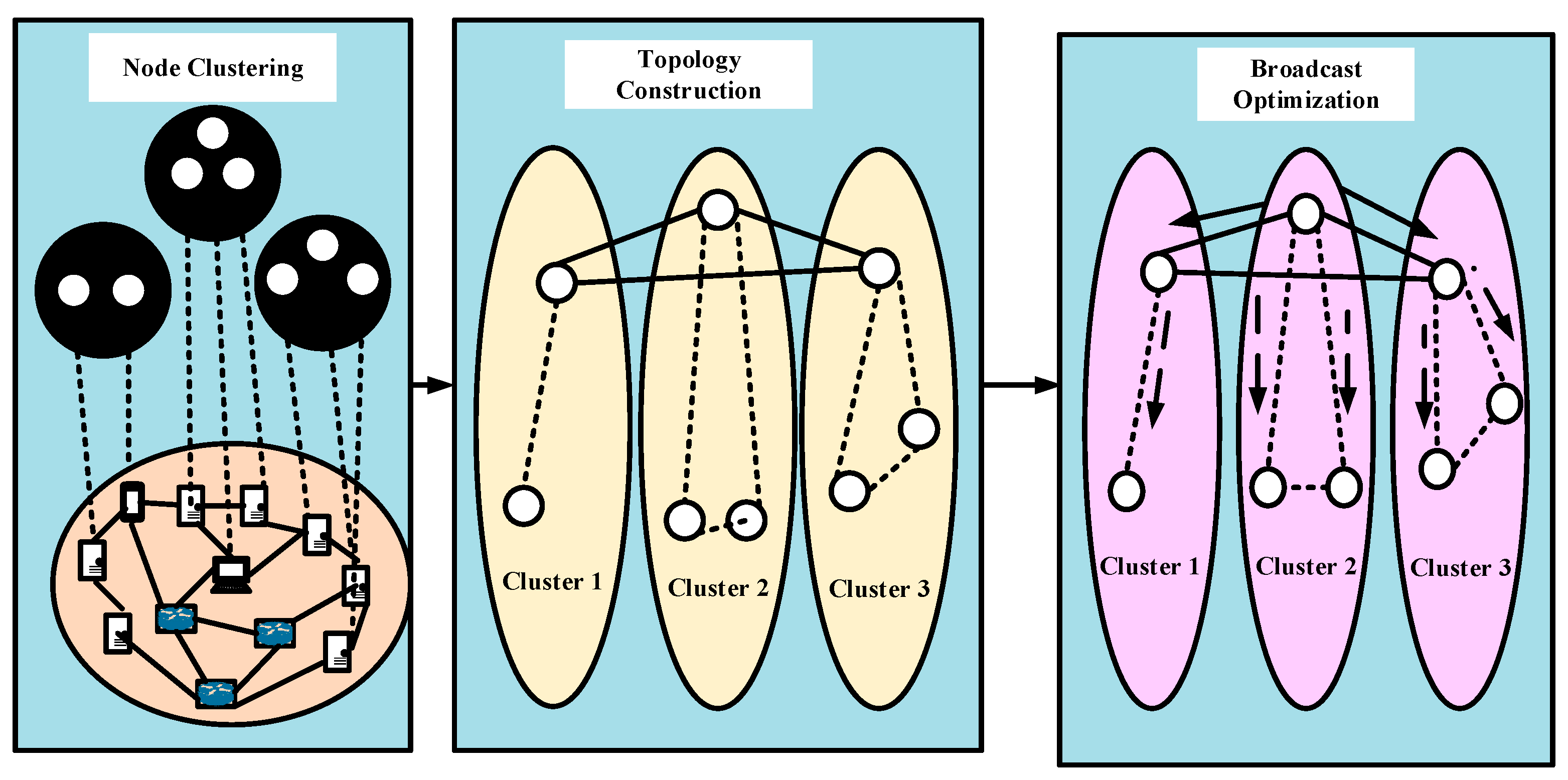
The BlockP2P protocol enhances blockchain operations over a P2P network through three core components: node clustering, topology creation, and broadcast optimization. The overall architecture of the BlockP2P protocol, which enhances blockchain operations over a P2P network, is summarized in
Figure 5.
The architecture operates through a structured, three-stage workflow:
Input and clustering: The process begins with the entire set of network nodes as input. The Geographical Proximity Sensing Clustering (GPSC) algorithm. Using network latency as a proxy for distance, GPSC partitions the nodes into several distinct, geographically proximal clusters. This step is crucial for reducing intra-cluster communication latency.
Topology construction: Within each cluster formed by GPSC, the Structured Hierarchical Network Topology (SHNT) mechanism, described in
Section 3.3.2, organizes nodes into a hierarchical structure. This involves the following:
Electing a core node that maintains the full blockchain and manages cluster operations.
Connecting regular nodes to their closet core node.
Forming a robust, Haray-like network among the core nodes within a cluster to ensure resilience and efficiency.
Electing a routing node from the pool of core nodes in each cluster. This routing node is responsible for all inter-cluster communication.
Optimized broadcast: The parallel spanning tree broadcast (PSTB) mechanism, outlined in
Section 3.3.3, leverages the established topology for efficient data dissemination. The process is two-fold:
Inter-cluster broadcast: When a routing node in one cluster receives a new block or transaction, it immediately forwards it in parallel to all other routing nodes across the network. This ensures rapid, network-wide propagation at the inter-cluster level.
Intra-cluster broadcast: Upon receiving data, a routing node initiates a broadcast within its own cluster. Instead of using a gossip protocol that generates significant overhead, the data is disseminated along a pre-computed spanning tree rooted at the routing node. This method is highly efficient and minimizes redundant messages within the cluster.
3.3.1. Node Clustering via Geographical Proximity Sensing Clustering (GPSC)
To manage network complexity and reduce latency, the BlockP2P protocol employs the GPSC algorithm to partition nodes into geographically proximal clusters. Using network latency as a proxy for Euclidean distance, GPSC applies a K-Means variant to group nodes to optimize cluster efficiency with inter-cluster overhead. The GPSC algorithm proceeds in three phases:
Phase 1: Cluster Center Selection. A computationally efficient method is used to select initial cluster centers, avoiding the overhead of measuring all node pairs. From a candidate subset of nodes, the algorithm iteratively selects the most dispersed nodes as centers.
Phase 2: Aggregation Node Election. Within each nascent cluster, an aggregation node is elected. This node acts as a local coordinator, responsible for intra-cluster management and serving as a gateway for inter-cluster communication. Its location is determined using a network coordinate system (NCS) to approximate the geometric center of the cluster, minimizing average latency to all cluster members. The node whose NCS coordinates are closest to this calculated center is designated the .
Phase 3: Cluster Formation. All remaining nodes are assigned to a cluster by minimizing a weighted objective function (Equation (3)) that considers both the distance to a cluster center and the distance from that center to its aggregation node . This ensures that clusters are not only tight-knit but also centered around a well-positioned coordinator. The formal steps for phases 1 and 2 are presented in Algorithm 1.
| Algorithm 1: GPSC cluster center and aggregation node selection |
Input: Set of all nodes , number of clusters Phase 1: Center selection Let be a random subset of nodes from . Find the two nodes in with the maximum pairwise latency. For to do Find the node in with the maximum distance to any node in . Add this node to and remove it from . End for Phase 2: aggregation node selection For each cluster in do Using NCS, calculate the geometric center coordinates , for the cluster led bu Select the node , whose NCS coordinates are closest to . End for Return
|
This structured approach reduces the overall algorithmic complexity to , enabling rapid re-clustering in response to network churn.
The assistance nodes, known as aggregation nodes
, each of which is situated in the geometric center of a cluster, is selected to guarantee that all of the cluster centers are dispersed equally. Calculating
only based on the network delay between two nodes is challenging. As a result, GPSC uses the network coordinate system (NCS) approach to determine
. Using Equation (5), GPSC first assigns a network coordinate to each cluster center node.
where
stands for the error function that measures the discrepancy between actual and coordinate-based distances;
and
stand for the network distances among two nodes in the real system and the network coordinate scheme, respectively; and
and H illustrate the cluster centers and the cluster center network coordinates, respectively. This equation serves as the optimization objective for the network coordinate system. It quantifies how accurately the virtual coordinate space
represents the actual network topology. By minimizing this function, GPSC ensures that distances in the coordinate system closely approximate real network latencies, which is crucial for correctly identifying the geometric center of each cluster. Once the geometric center coordinates,
, are obtained, GPSC selects the cluster aggregation node using Equation (6).
where
illustrates the matching function of the cluster aggregation node,
denotes the minimum network distance between two nodes in NCS, and
means the geometric center coordinates.
Relying on the above prerequisites, GPSC finally clusters all of the nodes, permitting an objective function
in Equation (7).
where
is the distance between a node (
) and a center (
, and
is the distance between the center and an aggregation node
.
and
stand for the general node and the center node, respectively. Moreover, there are two weight factors:
and
. The resilience of the system is enhanced by GPSC’s ability to reduce algorithm complexity from
in BCBPT to
. This allows for quick node re-clustering in response to potential network changes.
3.3.2. Topology Construction
The execution of the GPSC algorithm may result in clusters containing hundreds of nodes. Hence, a key challenge is enabling each node to identify a small, optimal subset of peers within its cluster to establish efficient neighbor lists. To address this, we adopt the Structured Hierarchical Network Topology (SHNT) approach, which is designed to achieve both low network diameter and high connectivity. The SHNT mechanism comprises two key procedures: network initialization and network maintenance.
After the clustering phase, the SHNT technique constructs a scalable and efficient topology by assigning specific roles to nodes within each cluster.
Leaf nodes: These are SPV (Simplified Payment Verification) nodes responsible for initiating transactions.
Core nodes: These are full nodes tasked with maintaining the blockchain, managing the associated leaf nodes, and forwarding blocks or transactions within their respective clusters.
Routing nodes: A selected subset of core nodes (one per cluster), determined using a secure hash function of their node IDs, are designated to handle inter-cluster data forwarding.
The establishment of the SHNT involves three main phases:
Connecting each leaf node to its closest core node based on proximity or latency.
Forming a resilient Harary-like network among the core nodes to ensure optimal intra-cluster communication.
Selecting routing nodes that facilitate secure and efficient communication across clusters.
Additionally, an autonomous maintenance procedure ensures that cluster sizes remain stable around O(log N) by dynamically adjusting cluster boundaries. This is achieved by splitting oversized clusters or merging undersized ones according to predefined scalability thresholds.
3.3.3. Parallel Spanning Tree Broadcast (PSTB)
The PSTB mechanism optimizes data dissemination by parallelizing broadcasts within and between clusters.
Inter-cluster broadcast: Routing nodes maintain a route table of all other routing nodes. Upon receiving data, a routing node immediately forwards it to all other routing nodes in parallel, enabling rapid network-wide propagation. For fault tolerance, a backup core node is assigned to each routing node.
Intra-cluster broadcast: To avoid the overhead of gossip protocols, data is broadcast within a cluster along a spanning tree rooted at the routing node. A center-based approach is used to construct and regularly update the spanning tree table, ensuring efficiency despite network churn.
3.4. Integrating SDN and Blockchain into a Peer-to-Peer Network
The integration of blockchain and software-defined networking (SDN) addresses the core challenges of reliability, security, and scalability in P2P streaming by leveraging their complementary strengths. This synergy creates a robust framework that enhances network management, secures transactions, and optimizes resource utilization. The integrated benefits are categorized below.
3.4.1. Mitigation of Transmission Delay
The hybrid framework directly targets latency reduction through coordinated action:
SDN’s role: The centralized SDN control plane enables real-time network monitoring and dynamic adaptation. It can instantly reroute traffic and reallocate bandwidth in response to congestion, minimizing delay and preventing packet loss.
Blockchain’s role: Blockchain provides a tamper-proof ledger for recording transactions. Smart contracts automate processes such as delivery verification and settlement, ensuring timely and reliable packet delivery without the need for protracted inter-peer negotiations, thereby reducing transactional latency.
3.4.2. Management of Overhead Ratio
The architecture ensures scalable efficiency as the network grows:
SDN’s role: SDN’s centralized orchestration optimizes resource allocation and path selection. Through intelligent traffic scheduling and dynamic reconfiguration, it eliminates redundant overhead and mitigates congestion, preserving streaming quality at scale.
Blockchain’s role: Blockchain distributes the computational load of consensus and transaction validation across all participating nodes. This decentralized approach prevents any single node from becoming a bottleneck, ensuring that the verification workload remains manageable as the network expands.
3.4.3. Validation Across Diverse Network Topologies
The combination provides a robust foundation for rigorous evaluation:
SDN’s role: SDN’s flexibility allows for the dynamic reconfiguration of the network environment. This enables efficient simulation and practical experimentation across various topological structures, which is crucial for assessing the scalability and robustness of the proposed model.
Blockchain’s role: Blockchain ensures the trustworthiness of validation data. An immutable ledger records all performance metrics and evaluation results, making findings verifiable and tamper-proof. Smart contracts can further automate testing protocols, standardize methods, and reduce manual overhead.
3.4.4. Assurance of Transmission Security
Security is enhanced through a layered, synergistic approach:
SDN’s role: The centralized control plane allows for the implementation of dynamic security policies. This includes enforcing encryption rules, deploying network-wide Intrusion Detection Systems (IDSs), and managing Access Control Lists (ACLs) to prevent unauthorized access and mitigate breaches.
Blockchain’s role: Blockchain provides a foundational layer of security through cryptographic techniques and decentralized consensus. Every transaction is cryptographically signed and recorded on an immutable ledger, creating a tamper-proof audit trail that ensures transparency and security. The consensus mechanism ensures network-wide agreement on data validity, eliminating single points of failure and making the system highly resilient to attacks.
3.4.5. Synthesis of the Integrated Architecture
The overall architecture (
Figure 6) leverages SDN for dynamic, centralized network control—facilitating efficient traffic scheduling, bandwidth allocation, and QoS-aware routing. Concurrently, blockchain introduces a decentralized trust layer, ensuring transaction integrity and security through immutable logging and smart contracts.
An integrated incentive mechanism is key to this synergy. Blockchain can reliably track peer contributions (e.g., bandwidth shared, data forwarded). The SDN controller can then use this information to dynamically prioritize traffic and allocate resources to well-behaved peers, as governed by smart contract rules. This rewards cooperation and discourages malicious activity. Furthermore, blockchain’s decentralized nature enhances SDN’s QoS capabilities by enabling trustless routing decisions. The network can prioritize paths based on verified performance data and available bandwidth without relying solely on a central authority’s perspective.
This study complements our previous work [
16] by re-evaluating the proposed framework under multiple configurations—blockchain-only, SDN-only, and the combined SDN–blockchain integration—within the same simulation environment and variable set. Unlike the prior comparative analysis, which focused on benchmarking performance across existing models, this study examines the implementation behavior and interaction dynamics of each configuration to provide deeper insights into scalability, security, and reliability.
In conclusion, the integration of SDN and blockchain into peer-to-peer (P2P) networks offers a comprehensive solution. It synergizes SDN’s operational efficiency with blockchain’s transactional security and trust to create a scalable, reliable, and high-performance streaming environment.
5. Discussion
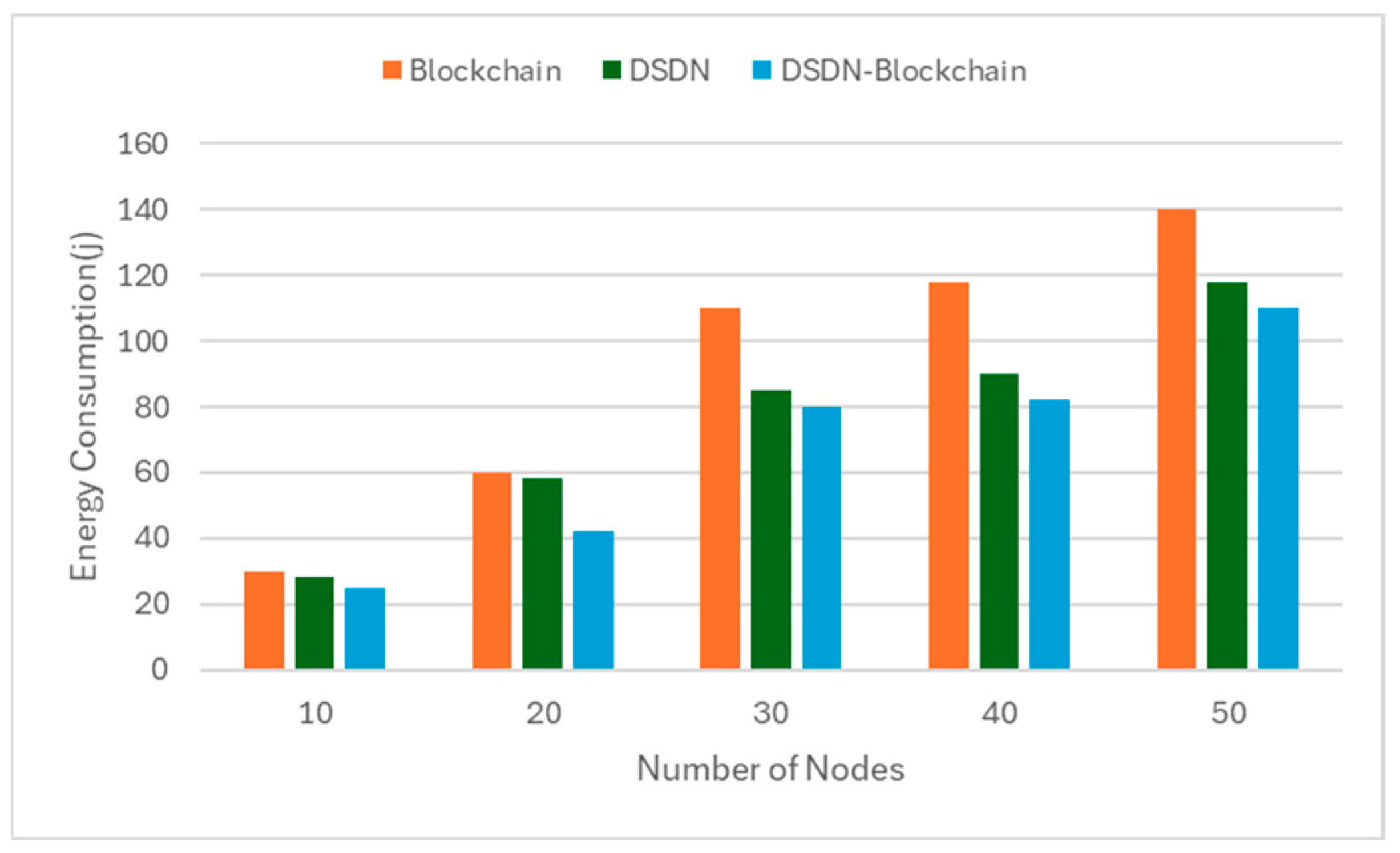
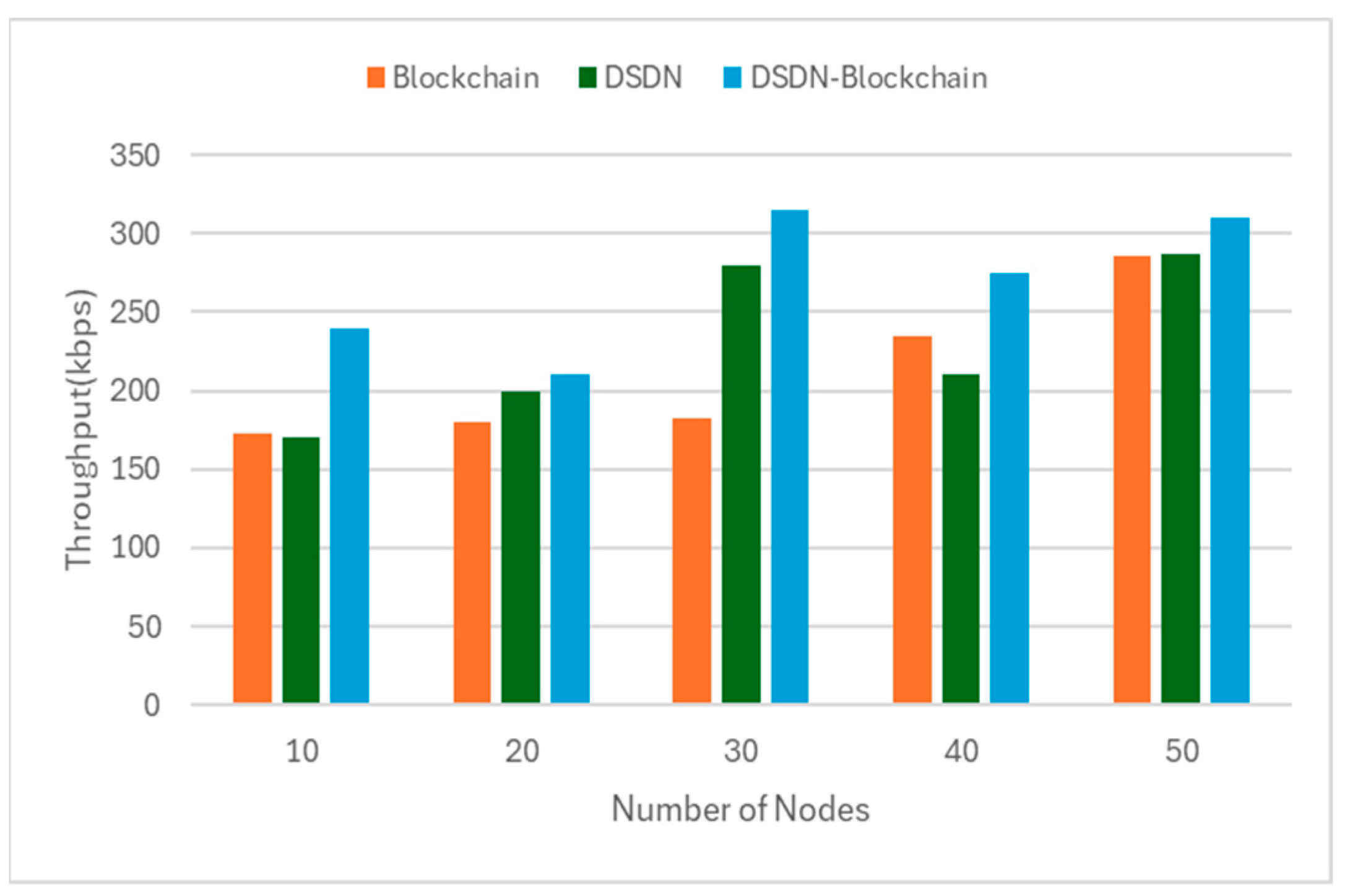
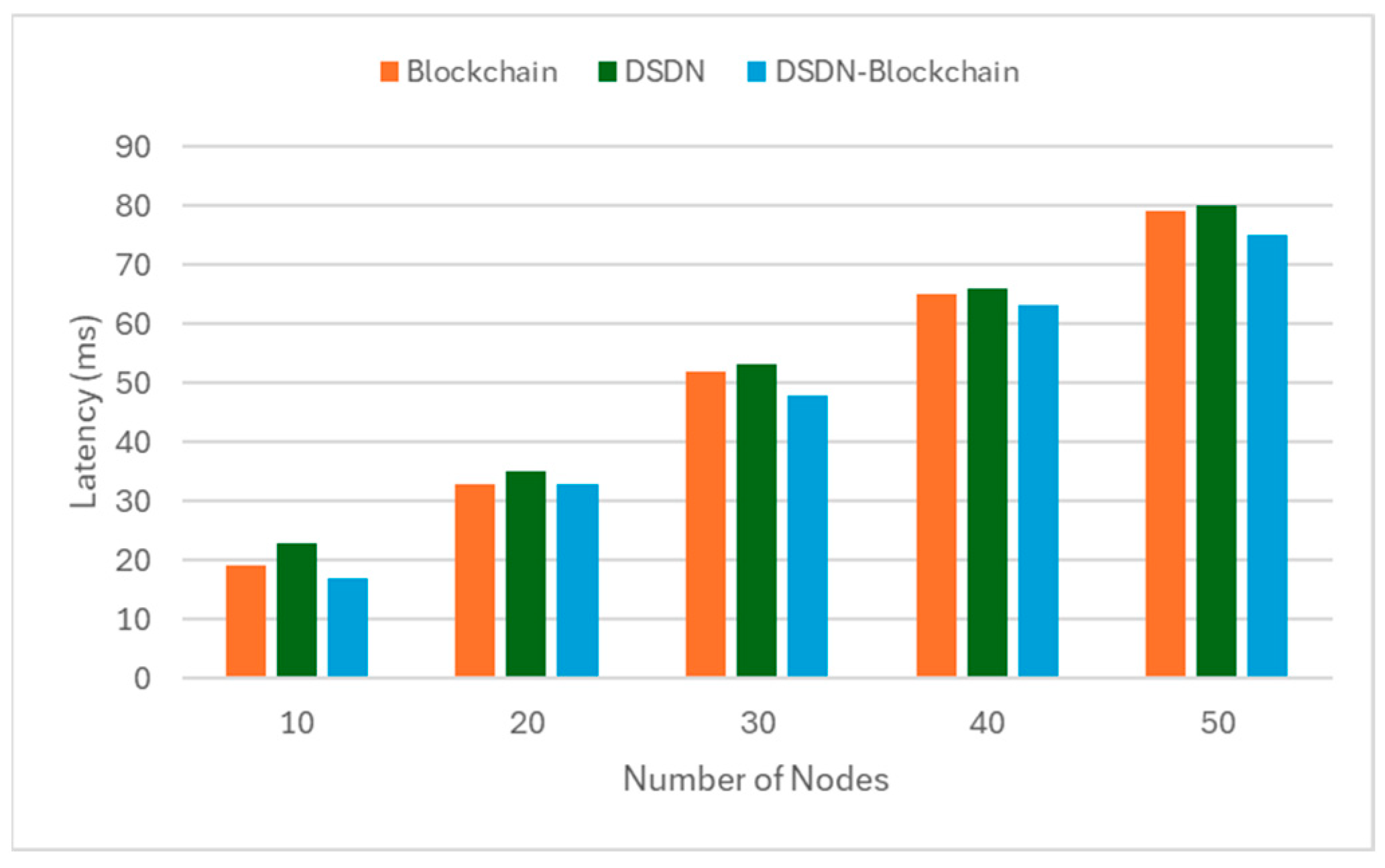
The experimental evaluation demonstrates that the hybrid DSDN–blockchain framework outperforms standalone approaches across all primary metrics: energy consumption, throughput, and latency. By integrating SDN’s adaptive control with blockchain’s secure transactions, the proposed system enhances quality of service, resource utilization, and scalability in P2P streaming. Specifically, the hybrid model demonstrated superior energy efficiency, consuming 110 joules at 50 nodes compared to 140 joules (blockchain-only) and 118 joules (DSDN-only), reflecting reductions of approximately 21% and 7%, respectively. For throughput, the hybrid system achieved 310 kilobits per second at 50 nodes, outperforming the blockchain-only model (285 kilobits per second) and the DSDN-only model (287 kilobits per second) by approximately 9% and 8%, respectively, in terms of latency; the hybrid model maintained the lowest end-to-end delay at 75 milliseconds, 5% lower than blockchain-only (79 milliseconds) and 6% lower than DSDN-only (80 milliseconds).
Critically, the security validation confirms the framework’s resilience. The hybrid model successfully neutralized 95% of malicious activity, combining the proactive mitigation of SDN with the inherent trust verification of blockchain. This layered security approach is essential for modern P2P applications facing diverse threats.
These results indicate that the hybrid approach successfully reduces control plane and verification delays, ensures secure transactions, and guarantees smoother content delivery, leading to a higher quality of service in larger networks. While practical deployment may involve integration challenges, the clear performance and security advantages make the hybrid DSDN–blockchain framework a promising solution for next-generation P2P streaming systems.