Review of Fuzzy Methods Application in IIoT Security—Challenges and Perspectives
Abstract
1. Introduction
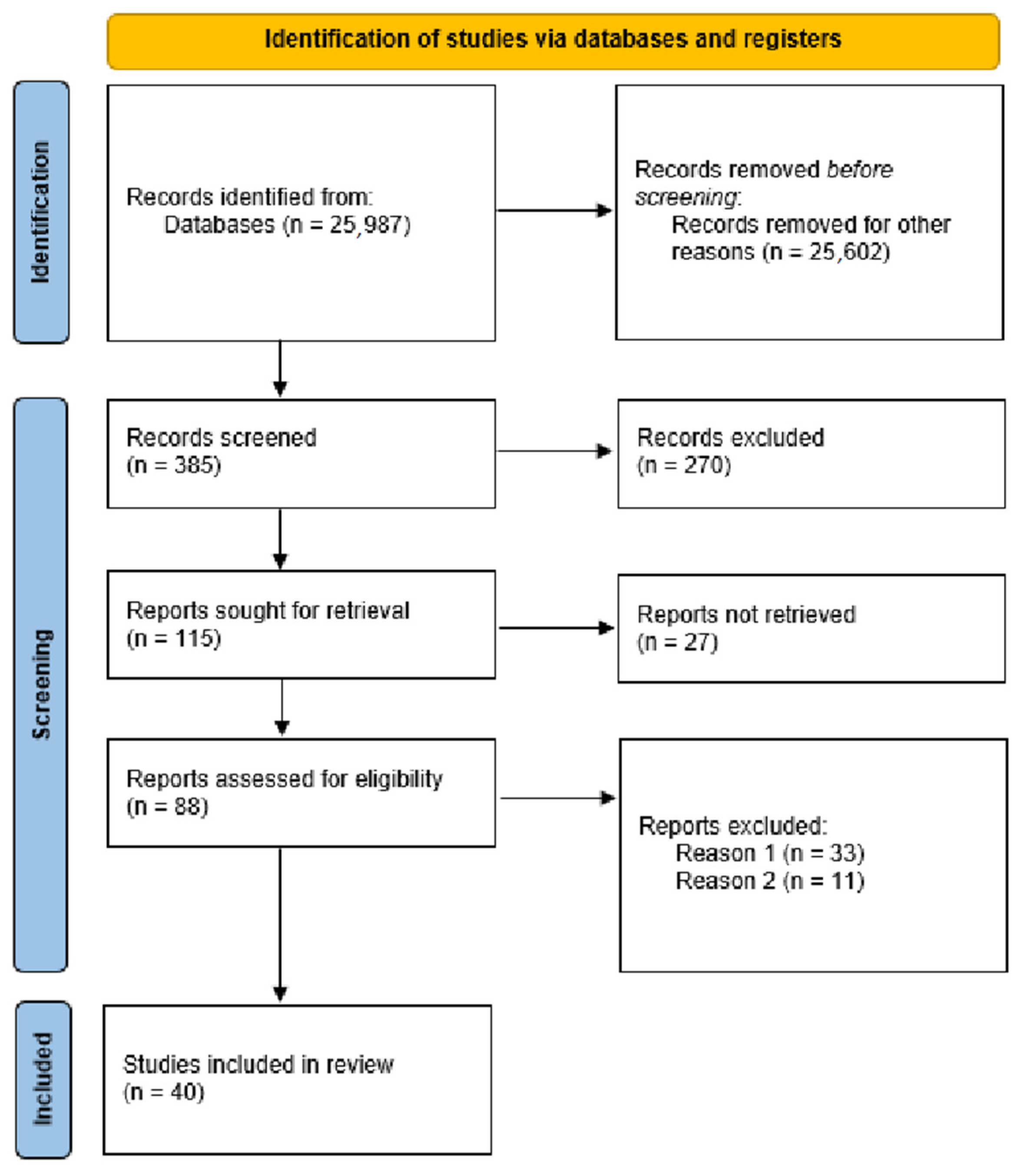
1.1. Methodology
1.2. Research Gap, Questions and Contributions
- How can uncertainty and ambiguity in IIoT system data be effectively modelled?
- In what way can fuzzy set theory be utilised to represent degrees of membership to specific states and behavioural patterns to ensure the security of IIoT systems?
- What are the potential benefits and challenges associated with applying fuzzy set theory to IIoT system profiling, especially in the context of incomplete and ambiguous data?
| Year/ Reference | Thematic Scope | Review Methodology | Type of Analysis (Descriptive vs. Critical) | Case Studies Included | Conclusions and Research Gaps |
|---|---|---|---|---|---|
| 2020/[5] | Security with fuzzy set methods | narrative | descriptive | Yes, detailed case studies | Complex review of fuzzy methods with identified gaps in research regarding system interpretability, scalability, and the need to create unified evaluation benchmarks. |
| 2023/[6] | IDS for IoT/IIoT | narrative | critical and analytical | No, focused on a literature synthesis | Lack of a unified design methodology, scalability limitations, and lack of public datasets. |
| 2023/[7] | IIoT security | systematic | critical and analytical | Yes, a general, non-detailed case studies | Research gaps in the scalability of fuzzy systems, lack of standard evaluation data sets, and integration with other security techniques in the IIoT context. |
| 2023/[8] | Situation awareness with fuzzy set methods | Systematic-PRISMA | descriptive | No, focused on a literature synthesis | Review highlights the need for advanced fuzzy logic and neuro-fuzzy models that can be effectively deployed on resource-constrained IIoT devices to handle real-time threat detection and anomaly analysis, thus bridging the gap between theoretical frameworks and practical, low-power applications. |
| 2024/[9] | Fuzzy systems in Medical IoT | Systematic-PRISMA | critical and analytical | Yes, a general, non-detailed case study | Comprehensive review that focuses on the need for more efficient and scalable models for real-time threat detection and the lack of standardised datasets for evaluating these systems. |
| Ourwork | IIoT security with fuzzy set methods | Systematic-PRISMA | critical and analytical | Yes, detailed case studies | First review of fuzzy theory applications in IIoT security, while identifying research gaps such as rule subjectivity, computational complexity, and the urgent need to develop dynamic system profiling methods. |
2. Research Problem Statement—IIoT Security
Threat Taxonomy in IIoT
3. Fundamentals of Fuzzy Set Theory
3.1. Fuzzy Set
- If , then element x does not belong to the fuzzy set A at all.
- If , then element x fully belongs to the fuzzy set A.
- If , then element x belongs to the fuzzy set A to some degree.
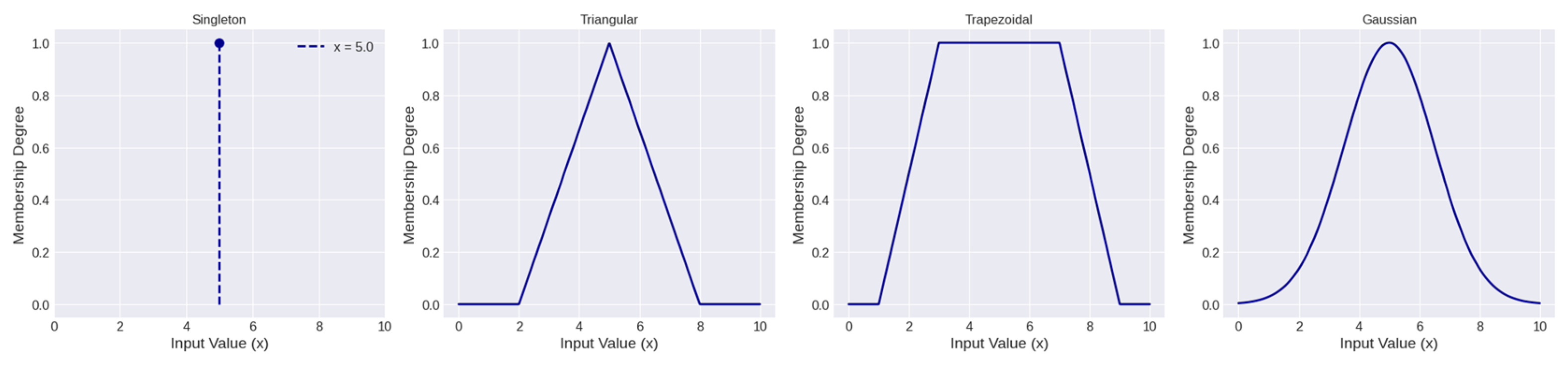
3.2. Membership Function
3.3. Fuzzy Logic
3.4. Fuzzy Inference System
3.5. Fuzzy Clustering
- N–Total number of data points in the dataset.
- C–Number of clusters.
- –Degree of membership of the i-th data point () to the j-th cluster (a value within the interval [0,1]).
- m–Fuzzification parameter, which is any real number greater than 1.
- –The i-th data point in the dataset.
- –The centre (centroid) of the j-th cluster.
- –The squared Euclidean distance between point and cluster centre .
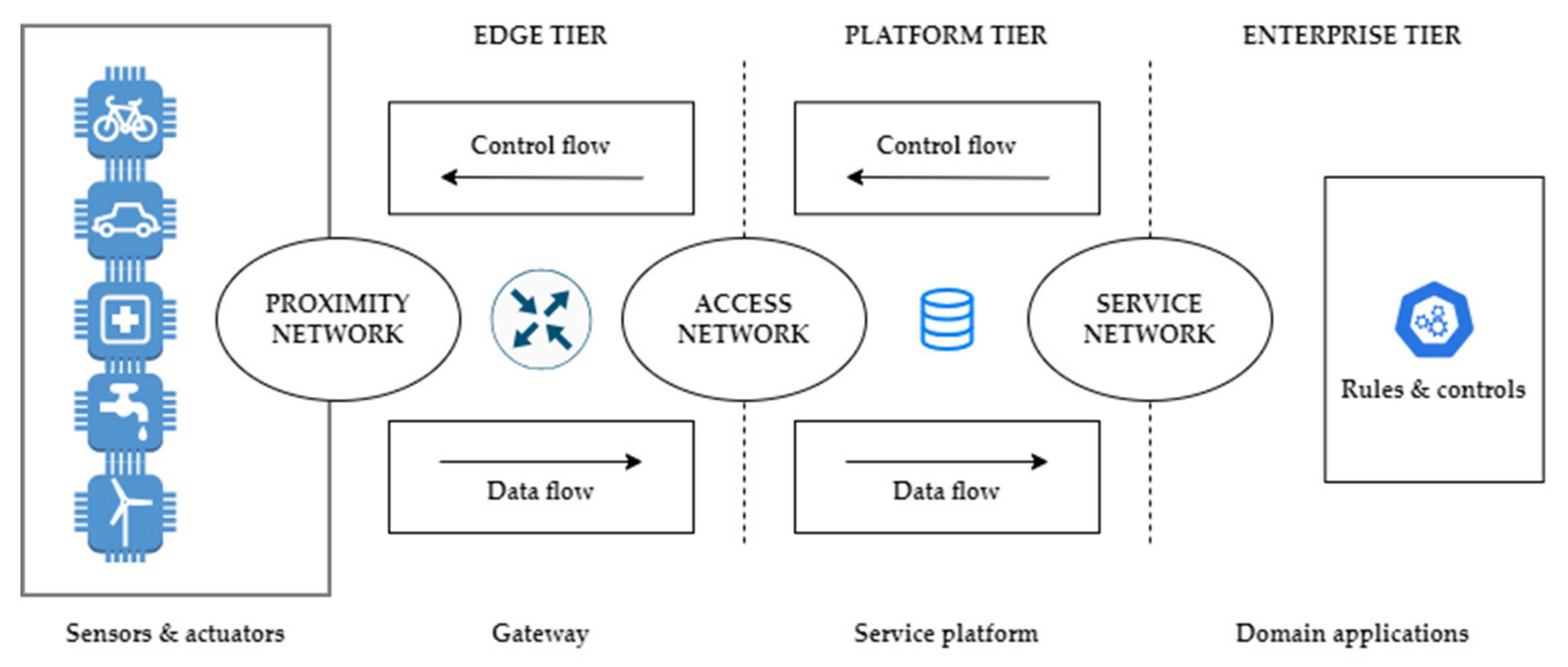
4. Application of Fuzzy Set Theory in IIoT
| Reference | Method | IIoTArea | Effect and Application | Data | Evaluation Metrics | Test Environment | Limitations |
|---|---|---|---|---|---|---|---|
| [33] | FL | All | Feature selection to improve intrusion detection systems | Public WUSTL-EHMS-2020 | Accuracy | Simulation (python) | Traditional mutual information-based feature selection methods cannot cope with noise, uncertainty, and imprecision in IoT data. |
| [34] | FL | All | Trust management in fog nodes and attack detection | N/A synthetic | Accuracy, TPR, TNR, FPR, FNR | Simulation (Cooja Contiki) | Reliance on a simulation-based environment requires validation of scalability and deployment in real, heterogeneous IIoT environments. |
| [35] | FL | All | Risk assessment to reduce false alarm rates in intrusion detection system | N/A synthetic | accuracy | simulation | A lack of real-time learning mechanisms is a general limitation, typical of static rule-based systems. |
| [36] | FL | All | Risk assessment in compliance with ISO/IEC 27001 | N/A Real data based on the ISO/IEC 27001 standard. | risk matrix | Simulation (Matlab) | Computational cost of Mamdani defuzzification method; subjectivity in defining rules and membership functions. |
| [37] | FL | All | Risk assessment | N/A | risk matrix | N/A | Static analysis based on subjective rules and membership functions. |
| [38] | FL | Automotive | Risk assessment using TARA method | Public Case study extracted from ISO/SAE 21434. | risk matrix | Simulation (Matlab) | Lack of real-world validation; static case study based on a standard. Inferential rules are subjectively derived from expert knowledge, affecting objectivity. |
| [39] | FL | All | Risk assessment model for information security | N/A Expert opinions | risk matrix | N/A | High subjectivity from expert opinions, lack of transparency in method choices, and no empirical validation in a real IIoT environment. |
| [40] | FL | All | Risk assessment for attacks on operational network | N/A The study is based on publicly available reports (CISA, SMICI) | risk matrix, FAR | simulation | Static model with predefined rules and membership functions; requires integration of machine learning for dynamic updates. |
| [41] | FL | All | Decision support system for edge computing efficacy and security | N/A synthetic | network throughput, end-to-end delay, energy consumption, packet overhead | simulation (Matlab) | Lack of scalability with increased routing requests; inefficient resource consumption and network complexity due to malicious routing requests. |
| [42] | FL | BMS | Multilayer risk assessment to support decision-making, trust management, and access control | N/A The input data comes from monitoring systems and databases (CVSS) | risk matrix | simulation (Matlab) | Static, non-adaptive model; lack of transparency in fuzzy parameter selection. |
| [43] | FL | All | Risk assessment for access control policies with decision support | N/A synthetic | accuracy, TPR, TNR, FPR, FNR | simulation | High subjectivity of core concepts; lack of empirical validation. |
| [44] | FL | All | Classification and reduction of false alarm rates | Public CICIoT2023, Aposemat IoT-23 | Balanced accuracy, accuracy, precision, recall, and F1-score. | simulation (Matlab) | Static fuzzy component; non-transparent parameter selection. |
| [45] | FL | All | Control method for assessing network security | N/A synthetic | Time performance | simulation (laboratory environment) | Lack of transparency in selecting fuzzy logic parameters; absence of objective performance evaluation metrics. |
| [46] | FL | All | Detection of jamming attacks | N/A synthetic | Accuracy, precision, recall | simulation (Cooja Contiki) | Lack of transparency in selecting fuzzy logic parameters; static fuzzy component. |
| [47] | FL | All | Jamming attack detection extended validation test | N/A synthetic | Accuracy, precision, recall | simulation (Cooja Contiki) | Static model; lack of empirical validation; false positives (difficulty in distinguishing between overload and attacks). |
| [48] | FL | All | Assessment of security to support decision-making (for crypto key sharing) | N/A synthetic | Accuracy, overhead, security level | simulation | Subjectivity from reliance on expert knowledge; lack of transparency in selecting fuzzy logic parameters. |
| [49] | FIS | All | Attacker profile and attack success rate | N/A Expert opinions | Profile matrix | simulation (Matlab) | Subjectivity from reliance on subjective attributes (knowledge, motivation); static nature. |
| [50] | FIS | All | Decision-making and control | N/A Data acquired from sensors | MAE, RMSE | simulation (Matlab, laboratory environment) | Subjectivity from reliance on expert knowledge; lack of empirical validation in a real-world environment. |
| [51] | FIS | All | Post-cyber incident decision-making | N/A synthetic | N/A | simulation (Matlab) | Static model; lack of empirical validation in a real-world environment. |
| [52] | FIS | All | Decision support in reaction to a cyberincident with response scoring | N/A synthetic | Accuracy, detection rate, FAR | simulation (Matlab, python) | Lack of empirical validation in a real-world environment. |
| [53] | FIS | All | Botnet risk assessment | Public CICIoT2023 | Accuracy, risk matrix | simulation (Matlab) | Lack of empirical validation in a real-world environment; trade-off between accuracy and interpretability, requiring a balance between the number of rules and readability. |
| [54] | FIS | All | Risk assessment using multiple FIS | N/A synthetic | Risk matrix | simulation | Static model with no empirical validation in a real-world environment; limited scope of risk assessment. |
| [55] | FIS | IACS | Risk assessment model for software | N/A Expert opinions | Risk matrix | simulation (Matlab) | High effort is required from experts and subjectivity based on their knowledge, which hinders scalability and verification of results. |
| [56] | FIS | All | Intrusion detection classification in the IIoT network | Public NSL-KDD | RMSE, accuracy, precision, sensitivity, specificity, F1-score | simulation (python) | Lack of empirical validation in a real-world environment; limited granularity of classification, hindering precise differentiation of threat severity. |
| [26] | FCM/FL | All | Detection of classical attacks and zero-day attacks with a decision support system | N/A synthetic | Accuracy | simulation (Cooja Contiki) | Subjectivity from expert knowledge, lack of empirical validation, false alarms, limited detection scope. |
| [57] | FCM | All | Attack detection | Public NSL-KDD | Accuracy, Positive Predictive Value, Sensitivity, F-score, Mathew Correlation Coefficient | simulation | Instability of created algorithm from random weight and bias assignment, potentially leading to suboptimal performance; lack of empirical validation in a real-world environment. |
| [58] | FIS/FCM | All | Trust management model in access control | N/A synthetic | RMSE, precision, recall, F1-score | simulation (Matlab) | Limited scope of trust assessment; lack of full implementation, which reduces practical utility; exclusive focus on performance and flexibility. |
| [59] | FCM | All | Attack detection | Public NSL-KDD, AWID, BoT-IoT | Accuracy, detection, precision, F1-score | simulation (python) | Scalability limitations remain an open question; lack of empirical validation in a real-world environment. |
| [60] | FCM | All | Anomaly detection | N/A synthetic | RMSE | simulation (Matlab, laboratory environment) | Validation conducted in a prototype installation; lack of quantitative evaluation metrics. |
| [61] | FCM | Medical IoT | Anomaly detection | Public WUSTL-EHMS | Accuracy, precision, recall, F1-score | simulation (python) | Lack of empirical validation in a real-world environment; lack of transparency in the decision-making process. |
| [62] | FCM | All | Confidence grouping in an intelligent city for risk assessment | Public NSL-KDD | Risk matrix, true rate, false rate, precision, recall, F-score | simulation | Requires extended evaluation and further research on scalability. |
Challenges and Limitations of Fuzzy Set Methods
- NSL-KDD is one of the earliest and most widely used intrusion detection datasets; however, it is not IoT-specific and has outdated traffic patterns that may not reflect modern IoT threats;
- CICIDS2017 provides realistic network traffic covering multiple attack scenarios, and although often used in IoT research, it was originally designed for general network intrusion detection, not for resource-constrained IoT environments;
- BoT-IoT is a purpose-built dataset for IoT security research, generated using simulated IoT devices under normal and attack conditions, although its synthetic nature limits the diversity of device types and real-world variability;
- CSE-CIC-IDS2018 expands CICIDS2017 with more comprehensive attack coverage while still reflecting traditional IT networks more closely than heterogeneous IoT deployments; The TON_IoT datasets include telemetry, network traffic, and system logs from IoT testbeds and industrial IoT, making them valuable for anomaly detection, but their scale is relatively small compared to real-world IoT ecosystems; CICIoT2023 is a new, large-scale dataset that integrates traffic from multiple IoT devices with different attack types, providing more up-to-date coverage, although it remains limited to the devices included in its testbed;
- UNSW-NB15 is another general intrusion detection dataset widely used in IoT research. Its limitation is that it is generated in an emulated environment that may not reflect IoT-specific constraints;
- IoT-23 is a collection of malicious and benign IoT traffic traces published by Stratosphere IPS, offering realistic behaviourof IoT malware, although it lacks representation of normal, heterogeneous IoT usage.
- The Edge-IIoTset focuses on attack scenarios on industrial IoT and edge computing environments, making it crucial for IIoT research. However, its availability is relatively recent, and its popularity is still growing.
5. Hybrid Fuzzy Models
| Reference | Method | IIoTArea | Effect and Application | Data | Evaluation Metrics | Test Environment | Limitations |
|---|---|---|---|---|---|---|---|
| [66] | NFS | All | Anomaly detection | Public IIoT23 | Accuracy, precision, recall, F1-score, FPR, FNR | N/A | Challenges with computational performance and scalability for large-scale deployment; optimization required for real-time operation. |
| [67] | ANFIS | All | Intrusion recognition and classification | Public N-BaIoT | Accuracy, precision, recall, F1-score, | simulation | Potential loss of fuzzy rule interpretability; uncertain scalability and performance in resource-constrained IoT. |
| [68] | ANFIS | All | Distributed Denial of Service attack recognition | Public UNSW-NB15, CICDDoS2019 | Accuracy | simulation (python) | Model complexity and rule explosion problem hinder scalability; manual fuzzy rule definition limits adaptability to new attack types. |
| [69] | ANFIS | All | Production system control | N/A Real data | Accuracy, RMSE, Average Absolute Relative Error, Median Absolute Deviation | Real-world IIoT environment | Model complexity leading to the curse of dimensionality with a large number of input variables. |
| [70] | ANFIS | All | Routing process optimization | N/A synthetic | RMSE | simulation (Matlab) | Lack of verification in a real-world IIoT environment; computational complexity from combining three techniques. |
| [71] | ANFIS | Battlefield IoT | Intrusion Detection System | N/A Real data | Accuracy, precision, recall, F1-score, FPR, TPR | simulation (Matlab) | Lack of verification in a real-world environment;dependence on external optimization. |
Challenges and Limitations of Neuro-Fuzzy Systems
6. Discussion and Future Research Directions
- Firstly, scalability and computational overhead remain recurring concerns, and there is a lack of empirical research in real IIoT environments. The vast majority of the analysed work is based on simulations, which undermines the practical value and universality of the proposed solutions [72,73]. While simulations are a valuable tool for rapid prototyping, they are unable to fully capture the complexity and dynamics of real-world systems [74].
- Secondly, a research gap lies in the lack of dynamic and adaptive profiling mechanisms [75]. Current fuzzy approaches often rely on static thresholds or historical data, limiting their effectiveness against novel or evolving attack vectors and focusing predominantly on identifying known anomalies [76,77].
- Finally, current studies often focus on isolated security challenges rather than holistic, integrated IIoT security architectures [78,79]. There is a paucity of research exploring seamless integration of individual fuzzy-based components into multi-layered security frameworks, leaving interdependencies and cascading effects across the IIoT stack largely unaddressed [80].
- The first phase of work involves creating a model that not only detects threats but also automatically assesses and prioritises risk in real-time. This will lay the groundwork for a more proactive security posture [83].
- The next stage will be the development of a dynamic, conceptual framework for IIoT system profiling. Such a framework should be able to profile and continuously update the current behaviour of devices and networks, leveraging the flexibility of fuzzy methods to handle uncertainty and incomplete data [84].
- The ultimate goal, which represents a long-term perspective, is the creation of an integrated, adaptive security architecture. This architecture will combine dynamic profiling with proactive risk management and intelligent decision-making, fully exploiting the advantages of fuzzy logic while building upon a solid foundation of explainable artificial intelligence [85].
7. Conclusions
Supplementary Materials
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| IIoT | Industrial Internet of Things |
| FIS | Fuzzy Inference System |
| ANFIS | Adaptive Neuro Fuzzy Inference System |
| IT | Information Technology |
| OT | Operational Technology |
| IACS | Industrial Automation and Control Systems |
| SCADA | Supervisory Control and Data Acquisition |
| ICS | Industrial Control System |
| BMS | Building Management System |
| DDoS | Distributed Denial of Service |
| MITM | Man in the middle |
| FL | Fuzzy Logic |
| FCM | Fuzzy C-Means |
| IDS | Intrusion Detection System |
| NFS | Neuro-Fuzzy System |
| N/A | Not Available |
| TPR | True Positive Rate |
| TNR | True Negative Rate |
| FPR | False Positive Rate |
| FNR | False Negative Rate |
| CISA | Cybersecurity and Infrastructure Security Agency |
| SMICI | Significant Multi-domain Incidents against Critical Infrastructure |
| FAR | False Alarm Rate |
| CVSS | Common Vulnerability Scoring System |
| MAE | Mean Absolute Error |
| RMSE | Root Mean Square Error |
References
- Lella, I.; Theocharidou, M.; Magonara, E.; Malatras, A.; Naydenov, R.S.; Ciobanu, C.; Chatzichristos, G. (Eds.) ENISA Threat Landscape 2024: July 2023 to June 2024; European Union Agency for Cybersecurity: Athens, Greece, 2024. [Google Scholar]
- Dhirani, L.L.; Armstrong, E.; Newe, T. Industrial IoT, Cyber Threats, and Standards Landscape: Evaluation and Roadmap. Sensors 2021, 21, 3901. [Google Scholar] [CrossRef]
- NIS2 Directive. Directive (EU)2022/2555 of the European Parliament and of the Council of 14 December 2022 on measures for a high common level of cybersecurity across the Union. Off. J. Eur. Union 2022, L333, 80–152. [Google Scholar]
- PRISMA 2020 Flow Diagram. Available online: https://www.prisma-statement.org/prisma-2020-flow-diagram (accessed on 8 August 2025).
- Masdari, M.; Khezri, H. Towards fuzzy anomaly detection-based security: A comprehensive review. Fuzzy Optim. Decis. Mak. 2021, 20, 1–49. [Google Scholar] [CrossRef]
- Bansal, K.; Singhrova, A. Review on intrusion detection system for IoT/IIoT-brief study. Multimed. Tools Appl. 2024, 83, 23083–23108. [Google Scholar] [CrossRef]
- Alotaibi, B. A Survey on Industrial Internet of Things Security: Requirements, Attacks, AI-Based Solutions, and Edge Computing Opportunities. Sensors 2023, 23, 7470. [Google Scholar] [CrossRef] [PubMed]
- D’Aniello, G. Fuzzy logic for situation awareness: A systematic review. J. Ambient Intell. Hum. Comput. 2023, 14, 4419–4438. [Google Scholar] [CrossRef]
- Abdalla, A.Y.; Abdalla, T.Y.; Chyaid, A.M. Internet of Things-Based Fuzzy Systems for Medical Applications: A Review. IEEE Access 2024, 12, 163883–163902. [Google Scholar] [CrossRef]
- Czeczot, G.; Rojek, I.; Mikołajewski, D.; Sangho, B. AI in IIoT Management of Cybersecurity for Industry 4.0 and Industry 5.0 Purposes. Electronics 2023, 12, 3800. [Google Scholar] [CrossRef]
- Stouffer, K.; Pease, M.; Tang, C.Y.; Zimmerman, T.; Pillitteri, V.; Lightman, S.; Hahn, A.; Saravia, S.; Sherule, A.; Thompson, M. Guide to Operational Technology (OT) Security; NIST Special Publication 800-82r3; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2023. [CrossRef]
- Liebl, S.; Lathrop, L.; Raithel, U.; Sollner, M.; Aβmuth, A. Threat Analysis of Industrial Internet of Things Devices. arXiv 2024, arXiv:2405.16314. [Google Scholar] [CrossRef]
- Nair, A.; Greeshma, M.R. Mastering Information Security Compliance Management: A Comprehensive Handbook on ISO/IEC 27001:2022; Packt Publishing Ltd.: Birmingham, UK, 2023. [Google Scholar]
- IEC 62443-4-1:2018; Security for Industrial Automation and Control Systems Part 4-1: Secure Product Development Lifecycle Requirements. International Electrotechnical Commission: Geneva, Switzerland, 2018.
- IEC 62443-4-2:2019; Security for Industrial Automation and Control Systems Part 4-2: Technical Security Requirements for IACS Components. International Electrotechnical Commission: Geneva, Switzerland, 2019.
- Krzysztoń, E. Human in the IT security system. In XLIII Studencka Konferencja Naukowa—Potencjał Innowacyjny w Inżynierii Produkcji i Technologii Materiałów; Wyd. Politechniki Częstochowskiej: Częstochowa, Poland, 2019. [Google Scholar]
- Liderman, K. IC Ssecurity—Subject content proposal. Przegląd Teleinformatyczny 2020, 8, 3–30. [Google Scholar] [CrossRef]
- ISO/IEC 27001:2022; Information Security, Cybersecurity and Privacy Protection—Information Security Management Systems—Requirements. International Organization for Standardization: Geneva, Switzerland, 2022.
- Krawiec, J. Internet of Things (IoT). In Cyber Security Issues; OWPW: Warszawa, Poland, 2020. [Google Scholar]
- Krzysztoń, E.; Rojek, I.; Mikołajewski, D. A Comparative Analysis of Anomaly Detection Methods in IoT Networks: An Experimental Study. Appl. Sci. 2024, 14, 11545. [Google Scholar] [CrossRef]
- Industrial IoT Consortium (IIC). The Industrial Internet Reference Architecture, Version 1.10.2022. Available online: https://www.iiconsortium.org/wp-content/uploads/sites/2/2022/11/IIRA-v1.10.pdf (accessed on 2 April 2025).
- Abdullahi, S.M.; Lazarova-Molnar, S. On the Adoption and Deployment of Secure and Privacy-Preserving IIoT in Smart Manufacturing: A Comprehensive Guide with Recent Advances. Int. J. Inf. Secur. 2025, 24, 53. [Google Scholar] [CrossRef]
- McLaughlin, S.; Konstantinou, C.; Wang, X.; Davi, L.; Sadeghi, A.-R.; Maniatakos, M.; Karri, R. The Cybersecurity Landscape in Industrial Control Systems. Proc. IEEE 2016, 104, 1039–1057. [Google Scholar] [CrossRef]
- Țălu, M. Security and Privacy in the IIoT: Threats, Possible Security Countermeasures, and Future Challenges. Comput. AI Connect 2025, 2, 11. [Google Scholar] [CrossRef]
- Okunlola, O.A.; Olaoye, J.; Okunlola, O.S.; Okunlola, A.O.; Alao, O. Cybersecurity Strategies for Integrating Industrial IoTa nd Edge Computing: Challenges, Risks, and Future Perspectives. Int. J. Future Eng. Innov. 2025, 2, 87–95. [Google Scholar] [CrossRef]
- Zahra, S.R.; Chishti, M.A. Fuzzy Logic and Fog Based Secure Architecture for Internet of Things (FLFSIoT). J. Ambient Intell. Hum. Comput. 2023, 14, 5903–5927. [Google Scholar] [CrossRef]
- Tariq, U.; Ahmed, I.; Khan, M.; Bashir, A. Fortifying IoT Against Crimpling Cyber-Attacks: A Systematic Review. Karbala Int. J. Mod. Sci. 2023, 9, 9. [Google Scholar] [CrossRef]
- Zadeh, L.A. Fuzzy Sets. Inf. Control 1965, 8, 338–353. [Google Scholar] [CrossRef]
- Prokopowicz, P.; Czerniak, J.; Mikołajewski, D.; Apiecionek, L.; Ślęzak, D. Theory and Applications of Ordered Fuzzy Numbers: A Tribute to Professor Witold Kosiński; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Shinohara, Y. Fuzzy Set Concepts for Risk Assessment; IIASA Working Paper WP-76-2; International Institute for Applied Systems Analysis: London, UK, 1976; Available online: https://pure.iiasa.ac.at/id/eprint/578/1/WP-76-002.pdf (accessed on 2 April 2025).
- Fakhravar, H. Quantifying Uncertainty in Risk Assessment Using Fuzzy Theory. arXiv 2020, arXiv:2009.09334. [Google Scholar] [CrossRef]
- Alaaraji, Z.; SyedAhmad, S.S.; Kausar, N.; Anis, F.G.; Ozbilge, E.; Cagin, T. Fuzzy Theory in Fog Computing: Review, Taxonomy, and Open Issues. IEEE Access 2022, 10, 126931–126956. [Google Scholar] [CrossRef]
- Saq, A.; Zainal, A.; Al-rimy, B.; Alyami, A.; Abosaq, H. Intrusion Detection in IoT using Gaussian Fuzzy Mutual Information-based Feature Selection. Eng. Technol. Appl. Sci. Res. 2024, 14, 17564–17571. [Google Scholar] [CrossRef]
- Zahra, S.; Chishti, M.A. A generic and light weight security mechanism for detecting malicious behavior in the uncertain Internet of Things using fuzzy logic-and fog-based approach. Neural Comput. Appl. 2022, 34, 6927–6952. [Google Scholar] [CrossRef]
- Bamhdi, A.M. FLORA: FuzzyLogic—Objective Risk Analysis for Intrusion Detection and Prevention. Int. J. Comput. Sci. Netw. Secur. 2023, 23, 177–190. [Google Scholar] [CrossRef]
- Sikman, L.; Latinovic, T.; Sarajlic, N. Modelling of Fuzzy Expert System for an Assessment of Security Information Management System UIS (University Information System). Gazette 2022, 29, 60–65. [Google Scholar] [CrossRef]
- Pokorádi, L. Fuzzy logic-based risk assessment. Acad. Appl. Res. Mil. Sci. 2002, 1, 63–73. [Google Scholar]
- Merola, F.; Bernardeschi, C.; Lami, G. A Risk Assessment Framework Based on Fuzzy Logic for Automotive Systems. Safety 2024, 10, 41. [Google Scholar] [CrossRef]
- Amirova, A.; Tokhmetov, A. A Model for Risk Analysis in the Industrial Internet of Things. J. Theor. Appl. Inf. Technol. 2021, 99, 3449–3459. [Google Scholar]
- Nakonechna, Y.; Savchuk, B.; Kovalova, A. Fuzzy logic in risk assessment of multi-stage cyber attacks on critical infrastructure networks. Theor. Appl. Cybersecur. 2024, 6, 31–823. [Google Scholar] [CrossRef]
- Haseeb, K.; Ahmad, I.; Siraj, M.; Abbas, N.; Jeon, G. Multi-Criteria Decision-Making Framework with Fuzzy Queries for Multimedia Data Fusion. ACM Trans. Asian Low-Resour. Lang. Inf. Process. 2024, just accepted. [Google Scholar] [CrossRef]
- Lytvyn, V.; Bakurova, A.; Zaritskyi, O.; Gritskevich, A.; Hrynchenko, P.; Tereschenko, E.; Shyrokorad, D. Fuzzy logic-based methodology for building access control systems based on fuzzy logic. In Proceedings of the Modern Data Science Technologies Workshop (MoDaST-2024), Lviv, Ukraine, 31 May–1 June 2024; Volume 3723, pp. 104–120. Available online: https://ceur-ws.org/Vol-3723/ (accessed on 2 April 2025).
- Parkinson, S.; Khana, S. Identifying high-risk over-entitlement in access control policies using fuzzy logic. Cybersecurity 2022, 5, 6. [Google Scholar] [CrossRef]
- Akande, H.B.; Imoize, A.; Adeniran, T.; Lee, C.-C.; Bamidele, A. RF—FLIDS: A Novel Hybrid Intrusion Detection Model for Enhanced Anomaly Detection in IoT Networks. Secur. Priv. 2025, 8, e70041. [Google Scholar] [CrossRef]
- Zhang, R.; Hu, Z. Access Control Method of Network Security Authentication Information Based on Fuzzy Reasoning Algorithm. Measurement 2021, 185, 110103. [Google Scholar] [CrossRef]
- Savva, M.; Ioannou, I.; Vassiliou, V. Performance evaluation of a Fuzzy Logic-based IDS (FLIDS) technique for the Detection of Different Types of Jamming Attacks in IoT Networks. In Proceedings of the 2023 21st Mediterranean Communication and Computer Networking Conference (MedComNet), Island of Ponza, Italy, 13–15 June 2023. [Google Scholar] [CrossRef]
- Savva, M.; Ioannou, I.; Vassiliou, V. Fuzzy Logic-based IDS (FLIDS) for the Detection of Different Types of Jamming Attacks in IoT Networks. Comput. Commun. 2025, 241, 108251. [Google Scholar] [CrossRef]
- Senthil Pandi, S.; Roja Ramani, D.; Senthilselvi, A.; Dhanasekaran, S.; Kalpana, B.; Alangudi Balaji, N. Advancing IoT security with flame: A hybrid approach combining fuzzy logic and artificial lizard search optimization. Comput. Secur. 2024, 145, 103984. [Google Scholar] [CrossRef]
- Pricop, E.; Mihalache, S.F. Fuzzy approach on modelling cyber attacks patterns on data transfer in industrial control systems. In Proceedings of the 2015 7th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Bucharest, Romania, 25–27 June 2015; IEEE: New York, NY, USA. [Google Scholar]
- Sunardi, S.; Widodo, A.M.; Putra, K.T.; Darmarjati, C.; Prayitno, P. Design of IoT-Based Control System Using Fuzzy Inference System. J. Polimesin 2022, 20, 2. [Google Scholar]
- Slavyanov, K.; Dimov, R. Application of fuzzy logic in cybersecurity decision making and analysis after a cyber incident detection. ETR 2024, 2, 259–263. [Google Scholar] [CrossRef]
- Prabavathy, S.; Sundarakantham, K.; Shalini, S.M. Design of Cognitive Fog Computing for Autonomic Security System in Critical Infrastructure. J. Univers. Comput. Sci. 2018, 24, 577–602. [Google Scholar]
- Mashaleh, A.; Ibrahim, N.; Alauthman, M.; Almseidin, M.; Gawanmeh, A. IoT Smart Devices Risk Assessment Model Using Fuzzy Logic and PSO. Comput. Mater. Contin. 2024, 78, 2245–2267. [Google Scholar] [CrossRef]
- Kerimkhulle, S.; Dildebayeva, Z.; Tokhmetov, A.; Amirova, A.; Tussupov, J.; Makhazhanova, U.; Adalbek, A.; Taberkhan, R.; Zakirova, A.; Salykbayeva, A. Fuzzy Logic and Its Application in the Assessment of Information Security Risk of Industrial Internet of Things. Symmetry 2023, 15, 1958. [Google Scholar] [CrossRef]
- Abdymanapov, S.; Muratbekov, M.; Sharipbay, A.; Barlybayev, A. Fuzzy Expert System of Information Security Risk Assessment on the Example of Analysis Learning Management Systems. IEEE Access 2021, 9, 156556–156565. [Google Scholar] [CrossRef]
- Bamidele, A.; Ayo, F.; Panigrahi, R.; Garg, A.; Bhoi, A.K.; Barsocchi, P. A Multi-level Random Forest Model-Based Intrusion Detection Using Fuzzy Inference System for Internet of Things Networks. Int. J. Comput. Intell. Syst. 2023, 16, 31. [Google Scholar] [CrossRef]
- Rathore, S.; Park, J. Semi-supervised learning based distributed attack detection framework for IoT. Appl. Soft Comput. 2018, 72, 79–89. [Google Scholar] [CrossRef]
- Kesarwani, A.; Khilar, P. Development of Trust Based Access Control Models Using Fuzzy Logic in Cloud Computing. J. King Saud Univ. Comput. Inf. Sci. 2019, 34, 1958–1967. [Google Scholar] [CrossRef]
- Elsedimy, E.; Abo Hashish, S. An intelligent hybrid approach combining fuzzy C-means and the sperm whale algorithm for cyber attack detection in IoT networks. Sci. Rep. 2025, 15, 1005. [Google Scholar] [CrossRef]
- Hore, U.; Wakde, D. An Effective Approach of IIoT for Anomaly Detection Using Unsupervised Machine Learning Approach. J. ISMAC 2022, 4, 184–197. [Google Scholar] [CrossRef]
- Koo, J.; Siddiqui, I.; Qureshi, N.M.F.; Attique, M.; Shin, D. A Fuzzy-Based Duo-Secure Multi-Modal Framework for IoMT Anomaly Detection. J. King Saud Univ. Comput. Inf. Sci. 2022, 35, 131–144. [Google Scholar] [CrossRef]
- Yin, Q. Design and Application of Smart City Internet of Things Service Platform Based on Fuzzy Clustering Algorithm. Mob. Inf. Syst. 2022, 2022, 8405306. [Google Scholar] [CrossRef]
- Ibrahim, K.; Sajid, A.; Ullah, I.; Khan, I.; Kaushik, K.; Askar, S.S.; Abouhawwash, M. Fuzzy Inference Rule Based Task Offloading Model (FI-RBTOM) for Edge Computing. Peer J Comput. Sci. 2025, 11, e2657. [Google Scholar] [CrossRef]
- Apiecionek, L. Fuzzy Neural Networks—A Review with Case Study. Appl. Sci. 2025, 15, 6980. [Google Scholar] [CrossRef]
- Apiecionek, Ł. Liczby Rozmyte w Architekturze Sztucznych Sieci Neuronowych; Wydawnictwo Uniwersytetu Kazimierza Wielkiego: Bydgoszcz, Poland, 2024. [Google Scholar]
- Rahane, K.; Pawar, A. Intelligent System Vulnerability Detection Using Neuro-Fuzzy Approach. J. Comput. Res. Dev. 2025, 25, 48–71. [Google Scholar]
- Alrayes, F.S.; Alshuqayran, N.; Nour, M.K.; Al Duhayyim, M.; Mohamed, A.; Mohammed, A.A.A.; Mohammed, G.P.; Yaseen, I. Optimal Fuzzy Logic Enabled Intrusion Detection for Secure IoT-Cloud Environment. Comput. Mater. Contin. 2022, 74, 6737–6753. [Google Scholar] [CrossRef]
- Usha, G.; Karthikeyan, H.; Gautam, K.; Pachauri, N. DDoS attack detection in intelligent transport systems using adaptive neuro-fuzzy inference system. Sci. Rep. 2025, 15, 20597. [Google Scholar] [CrossRef]
- Abou Elaz, M.A.; Alhasnawi, B.N.; Sedhom, B.E.; Bureš, V. ANFIS-optimized control for resilient and efficient supply chain performance in smart manufacturing. Results Eng. 2025, 25, 104262. [Google Scholar] [CrossRef]
- Semenova, O.; Kryvinska, N.; Semenov, A.; Martyniuk, V.; Voytsehovska, O. Genetic Neuro-Fuzzy Approach towards Routing in Industrial IoT. Int. J. Electron. Telecommun. 2024, 70, 935–941. [Google Scholar] [CrossRef]
- Alkanjr, B.; Alshammari, T.; Alanazi, A.; Alalwany, E. An IDS-based Adaptive Neural Fuzzy Inference System (ANFIS) for IoBT Security Utilizing Particle Swarm Optimization. Eng. Technol. Appl. Sci. Res. 2025, 15, 24141–24147. [Google Scholar] [CrossRef]
- Apiecionek, Ł. Fuzzy Network Solutions for IoT Security. In Proceedings of the IEEE EUROCON 2025—21st International Conference on Smart Technologies, Gdynia, Poland, 4–6 June 2025; pp. 1–5. [Google Scholar]
- Zohaib, M.; Abdul-Aziz Alsanad, A.; Azeem Akbar, M. Success Factors of IoT Security: A Structured Analysis Using Fuzzy-AHP. IEEE Access 2024, 12, 186186–186209. [Google Scholar] [CrossRef]
- Ali, H.S.; Sridevi, R. Mobility and Security Aware Real-Time Task Scheduling inFog-Cloud Computing for IoT Devices: A Fuzzy-Logic Approach. Comput. J. 2024, 67, 782–805. [Google Scholar] [CrossRef]
- Liao, T.H. The importance of human interactivity in artificial intelligence use in advertising: Development of a new scale. Int. J. Advert. 2025, 1–36. [Google Scholar] [CrossRef]
- Aaisha, M.; Ghosh, U.; Kumar Sharma, P.; Javed, A. A Fuzzy-Based Approach to Enhance Cyber Defence Security for Next-Generation IoT. IEEE Internet Things J. 2023, 10, 2079–2086. [Google Scholar]
- Kumar Mishra, R.; Kumar Yadav, R.; Nath, P. Secure IoT data management and sharing architecture for information security using cryptographic technique. J. Intell. Fuzzy Syst. 2023, 45, 10951–10966. [Google Scholar] [CrossRef]
- Navaneethan, M.; Janakiraman, S. An optimized deep learning model to ensure data integrity and security in IoT based e-commerce block chain application. J. Intell. Fuzzy Syst. 2023, 44, 8697–8709. [Google Scholar] [CrossRef]
- Chirag Sharma, S.; Khan, S.; Mahajan, S.; Alsagri, H.S.; Almjally, A.; Alabduallah, B.I.; Ansari, A.A. Lightweight Security for IoT. J. Intell. Fuzzy Syst. 2023, 45, 5423–5439. [Google Scholar] [CrossRef]
- Sureshkumar, T.; Sivaraj, R.; Vijayakumar, M. Design and implementation of a framework for blockchain based security using IoT. J. Intell. Fuzzy Syst. 2023, 44, 905–918. [Google Scholar] [CrossRef]
- Xu, Y.; de Souza, R.W.R.; Medeiros, E.P.; Jain, N.; Zhang, L.; Passos, L.A.; de Albuquerque, V.H.C. Intelligent IoT security monitoring based on fuzzy optimum—Path forest classifier. Soft Comput. 2023, 27, 4279–4288. [Google Scholar] [CrossRef]
- Kotenko, I.V.; Parashchuk, I.B.; Desnitsky, V. Determination of the Transition Probability Matrix for an IoT Fuzzy Security Model. In Proceedings of the 2023 IEEE International Conference on Internet of Things and Intelligence Systems (IoTaIS), Bali, Indonesia, 28–30 November 2023; pp. 40–44. [Google Scholar]
- Zukifl, Z.; Khan, F.; Tahir, S.; Afzal, M.; Iqbal, W.; Rehman, A.; Saeed, S.; Almuhaideb, A.M. FBASHI: Fuzzy and Blockchain-Based Adaptive Security for Healthcare IoTs. IEEE Access 2022, 10, 15644–15656. [Google Scholar] [CrossRef]
- Swaroop, J.; Nagalakshmi, T.J.; Subash Sharma, S. Girl Child Security System based on IOT Technology with GPS Tracker Comparing with Fuzzy Classifier Based Safety Device. In Proceedings of the 2022 International Conference on Cyber Resilience (ICCR), Dubai, United Arab Emirates, 6–7 October 2022; pp. 1–6. [Google Scholar]
- Hong, E.; Lee, S.; Oh, M.K.; Seo, S.H. Two-Factor Device DNA-Based Fuzzy Vault for Industrial IoT Device Security. IEEE Access 2021, 9, 99009–99023. [Google Scholar] [CrossRef]
- Deepika, J.; Rajan, C.; Senthil, T. Security and Privacy of Cloud-and IoT-Based Medical Image Diagnosis Using Fuzzy Convolutional Neural Network. Comput. Intell. Neurosci. 2021, 2021, 6615411. [Google Scholar] [CrossRef]
- Bagher Haghparast, M.; Berehlia, S.; Akbari, M.; Sayadi, A. Developing and evaluating a proposed health security framework in IoT using fuzzy analytic network process method. J. Ambient Intell. Humaniz. Comput. 2021, 12, 3121–3138. [Google Scholar] [CrossRef]
- Richa, V.; Shalini, C. A Fuzzy AHP Approach for Ranking Security Attributes in Fog-IoT Environment. In Proceedings of the 2020 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kharagpur, India, 1–3 July 2020; pp. 1–5. [Google Scholar]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Krzysztoń, E.; Mikołajewski, D.; Prokopowicz, P. Review of Fuzzy Methods Application in IIoT Security—Challenges and Perspectives. Electronics 2025, 14, 3475. https://doi.org/10.3390/electronics14173475
Krzysztoń E, Mikołajewski D, Prokopowicz P. Review of Fuzzy Methods Application in IIoT Security—Challenges and Perspectives. Electronics. 2025; 14(17):3475. https://doi.org/10.3390/electronics14173475
Chicago/Turabian StyleKrzysztoń, Emanuel, Dariusz Mikołajewski, and Piotr Prokopowicz. 2025. "Review of Fuzzy Methods Application in IIoT Security—Challenges and Perspectives" Electronics 14, no. 17: 3475. https://doi.org/10.3390/electronics14173475
APA StyleKrzysztoń, E., Mikołajewski, D., & Prokopowicz, P. (2025). Review of Fuzzy Methods Application in IIoT Security—Challenges and Perspectives. Electronics, 14(17), 3475. https://doi.org/10.3390/electronics14173475








