An Efficient and Fair Map-Data-Sharing Mechanism for Vehicular Networks
Abstract
1. Introduction
- (1)
- Fair Data-Sharing Mechanism. We design a dynamic reputation unit to resolve the cold-start issue for new vehicles while revoking access rights for malicious vehicles. Furthermore, we develop an incentive mechanism based on reverse auction to balance the MC’s budget constraints with vehicular data collection capacity limits.
- (2)
- Data Security. We propose a mutual authentication mechanism between vehicles and RSUs to prevent unauthorized vehicles from sharing data and to detect vehicles that provide malicious data during the sharing process. In order to enhance the efficiency of sharing, a MHT is employed for the storage of vehicles’ anonymous certificates, thus addressing the redundant authentication issue in overlapping RSU regions. This approach facilitates single authentication for multiple data-sharing sessions.
- (3)
- Provable Security and Performance Evaluation. A security analysis demonstrates that the proposed scheme ensures anonymity, confidentiality, and unlinkability. A performance evaluation further confirms its practical effectiveness.
2. Related Works
2.1. Cloud-Based Centralized Data Sharing
2.2. Decentralized Data Sharing Based on Blockchain
3. Problem Statement
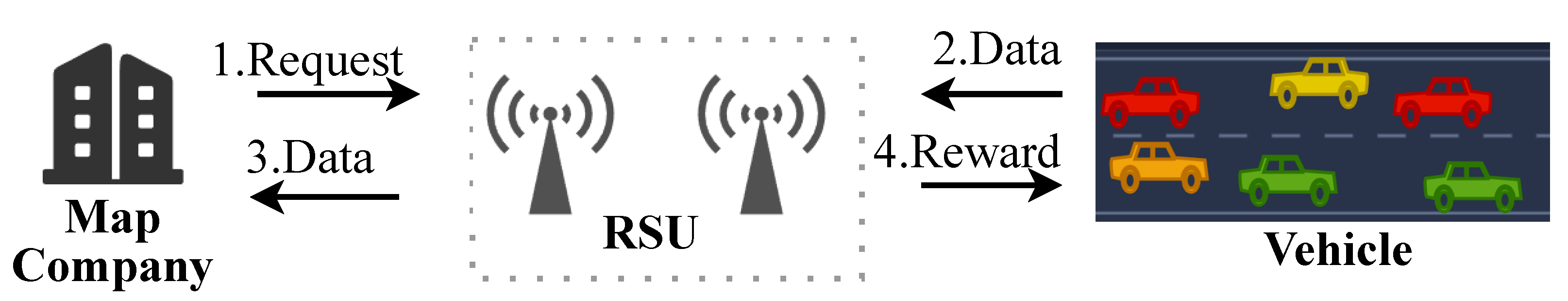
3.1. System Model
- Vehicle Administration (VA): The VA operates as a Trusted Third Party responsible for (1) system initialization via cryptographic credential issuance (public–private key pairs and digital certificates) to newly registered RSUs/vehicles, and (2) dynamic trust management through adaptive vehicle classification and automated isolation of low-trust vehicles based on predefined reputation thresholds.
- Roadside Unit (RSU): RSUs are fixed nodes with integrated storage/compute capabilities deployed across infrastructure, utilizing wireless networks to communicate with covered vehicles, authenticate identities, and process data requests.
- Map Company (MC): The MC delegates data collection tasks to RSUs. These RSUs aggregate vehicle-generated data, relay it to the MC, and disburse MC-funded incentives to participating vehicles.
- Vehicle: Vehicles collect data as required by MCs, equipped with on-board units (OBUs) integrating advanced communication devices and computational modules. These OBUs enable inter-vehicle and vehicle-to-RSU communication while providing sufficient computational resources for lightweight data processing tasks.
- Blockchain: Blockchain co-maintenance by vehicular networks, RSUs, MCs, and the VA integrates incentive-calculation smart contracts that allocate rewards according to vehicular data contribution metrics and the MC’s budgetary parameters.
3.2. Design Goals
- Data Security. To ensure data security, the proposed scheme can defend against data leakage and tampering attacks. This guarantees the confidentiality of map data throughout its entire lifecycle, including collection, transmission, storage, and sharing. Meanwhile, only the VA can identify vehicles providing malicious data.
- Efficiency. Optimize the authentication process between RSUs and vehicles by adopting lightweight protocol design, particularly for vehicles located in overlapping coverage areas of multiple RSUs. This reduces authentication latency and improves throughput.
- Fairness. Implement a transparent and fair incentive allocation mechanism to address the dynamic cold-start problem for new vehicles while also enforcing data-sharing privilege revocation for untrustworthy vehicles.
3.3. Threat Model
- Identity Tracking Attack. Attackers can infer the true identity of a vehicle by observing its communication behavior over a long period of time, which can lead to privacy leakage.
- Linkage Attack. Attackers can identify the behavioral patterns of specific vehicles by comparing data features across multiple sharing sessions, thereby inferring sensitive information.
- Data Leakage Attack. Attackers can intercept map data, thereby exposing vehicle location trajectories or environmental information.
4. Fair and Efficient Map-Data-Sharing Scheme
4.1. Main Idea
4.2. Detailed Protocol Design
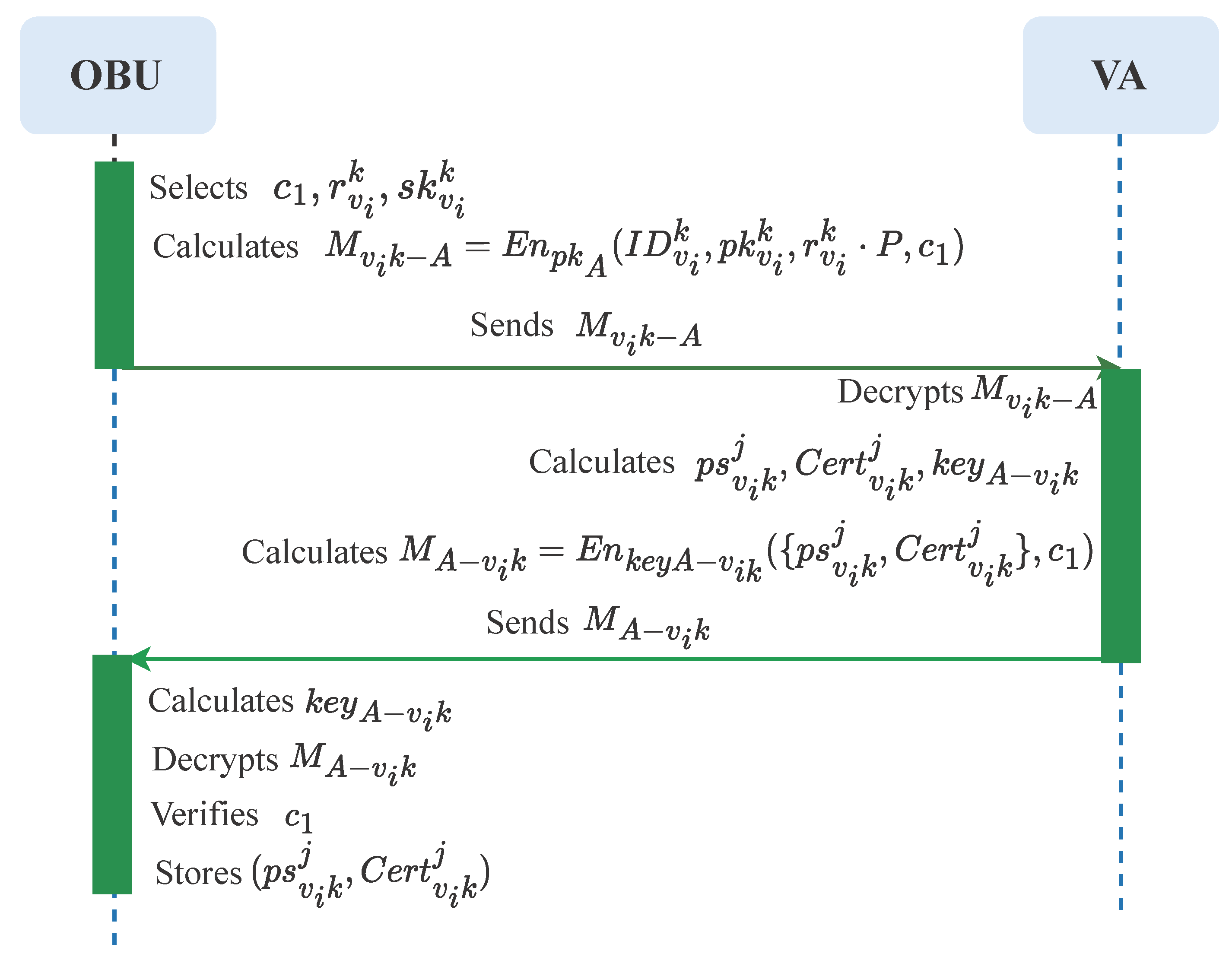
4.2.1. Registration
- (1)
- Vehicle registration
- (2)
- RSU and MC registration
4.2.2. Request Data
4.2.3. Authentication
- (1)
- Non_Overlap_Auth
- The selects a random number as the challenge and computes the key negotiate parameter , where . Subsequently, generates the signature by signing the message using its private key as per Equation (2). Finally, transmits the challenge to vehicles.
- verifies as per Equation (3). If valid, computes the session key , selects , and generates (Equation (2)), where j denotes ’s j-th pseudonym. Then, encrypts as and sends to the .
- The checks ’s validity. If valid, it computes the session key , decrypts to obtain , and verifies its validity. Next, validates using the pairingand verifies . If both checks pass, it inserts into the MHT, updates the root hash to , and generates the auxiliary path . It then computes (Equation (2)), encrypts as , and sends it to .
- Upon receiving , decrypts it using and verifies the validity of and . If valid, stores , completing the authentication. Otherwise, the authentication fails.
- (2)
- Overlap_Auth
- The selects random numbers and , computes the key negotiate parameter , and generates the signature (Equation (2)). It then sends to .
- verifies (Equation (3)). If valid, it selects , computes the session key , and encrypts the message as . Finally, sends challenge to the .
- The computes the session key and decrypts to obtain . After verifying , it calculates the MHT root hash using and checks if . If valid, is accepted. Finally, the encrypts as and sends it to .
- Upon receiving the ciphertext, decrypts it to obtain and verifies its validity. If valid, the authentication is completed; otherwise, it fails.
4.2.4. Reward
- (1)
- Reputation Unit
- (2)
- Incentive Model
| Algorithm 1 Smart Contract-based RRA Algorithm. |
| Require: Vehicle set V, Budget B, Bid information , Initial reputation Ensure: Reward allocation R, Data volume d
|
| Algorithm 2 Smart Contract-based OOA Algorithm. |
| Require: Vehicle set V, Budget B, Bid information Ensure: Optimal data allocation
|
| Algorithm 3 Smart Contract-based FPA Algorithm. |
| Require: Vehicle set V, Budget B, Bid information , Data allocation Ensure: Reward allocation R, Data volume d
|
4.2.5. Upload Data
5. Security Analysis
6. Performance Evaluation
6.1. Complexity Analysis
- (1)
- Computational overhead
- (2)
- Communication overhead
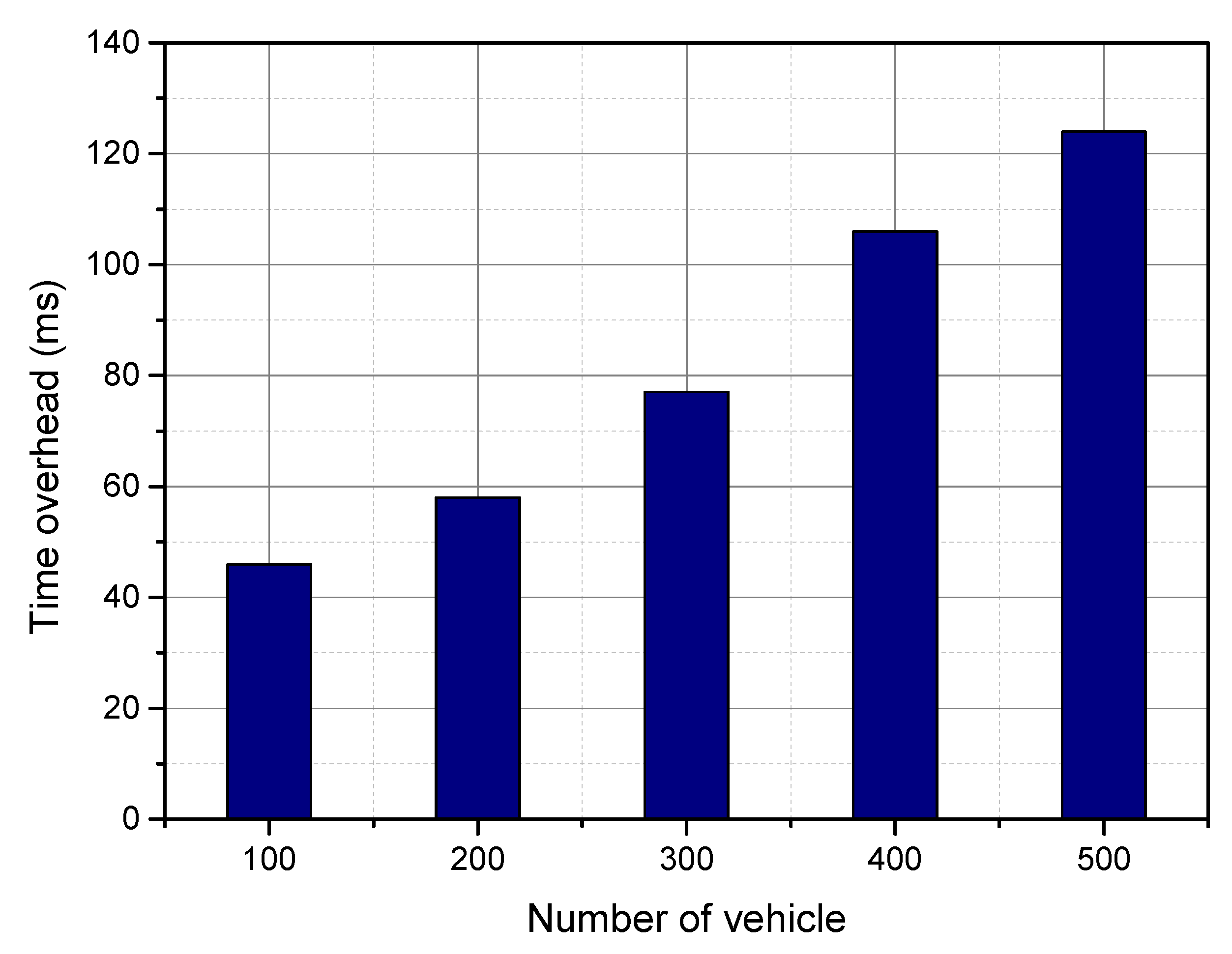
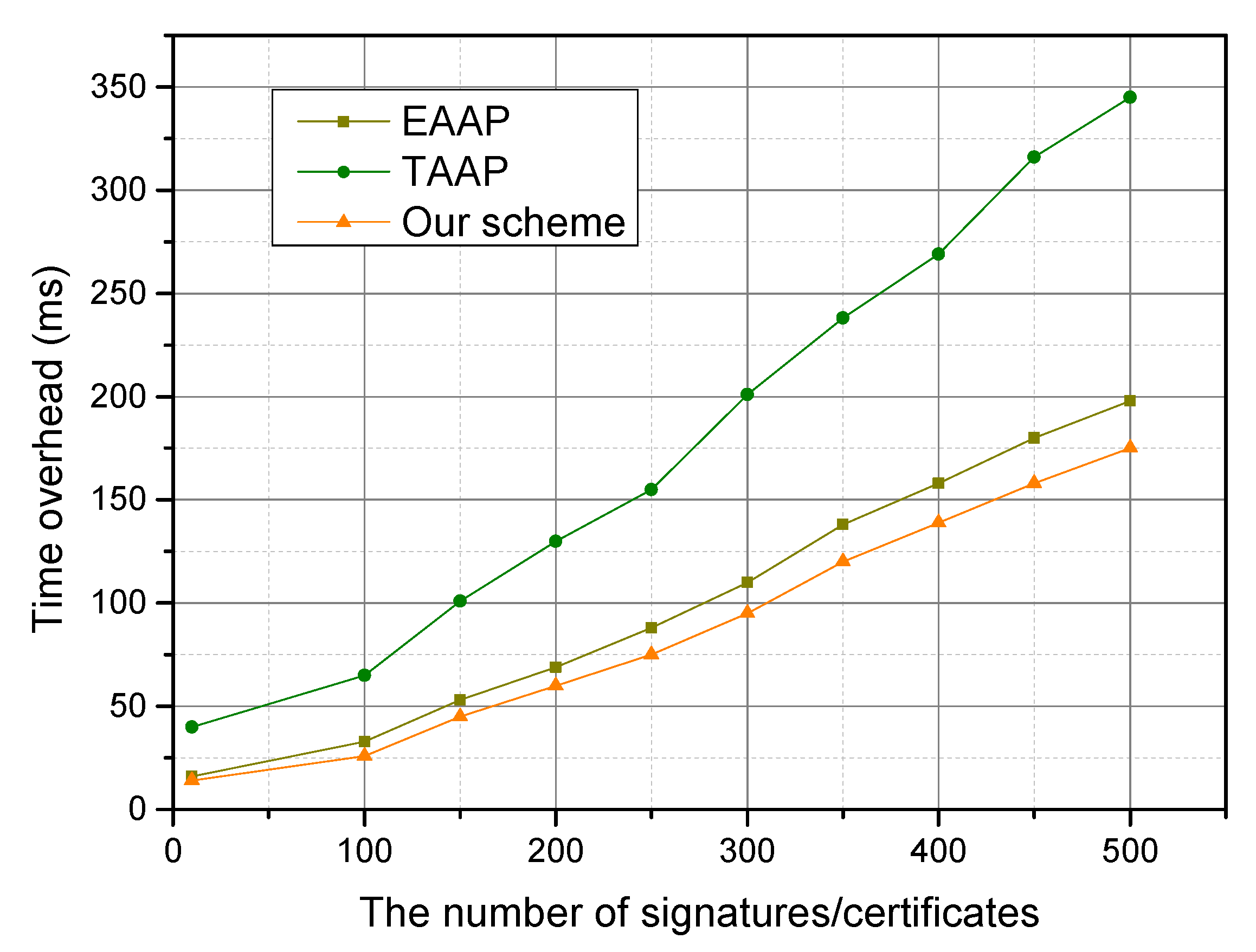
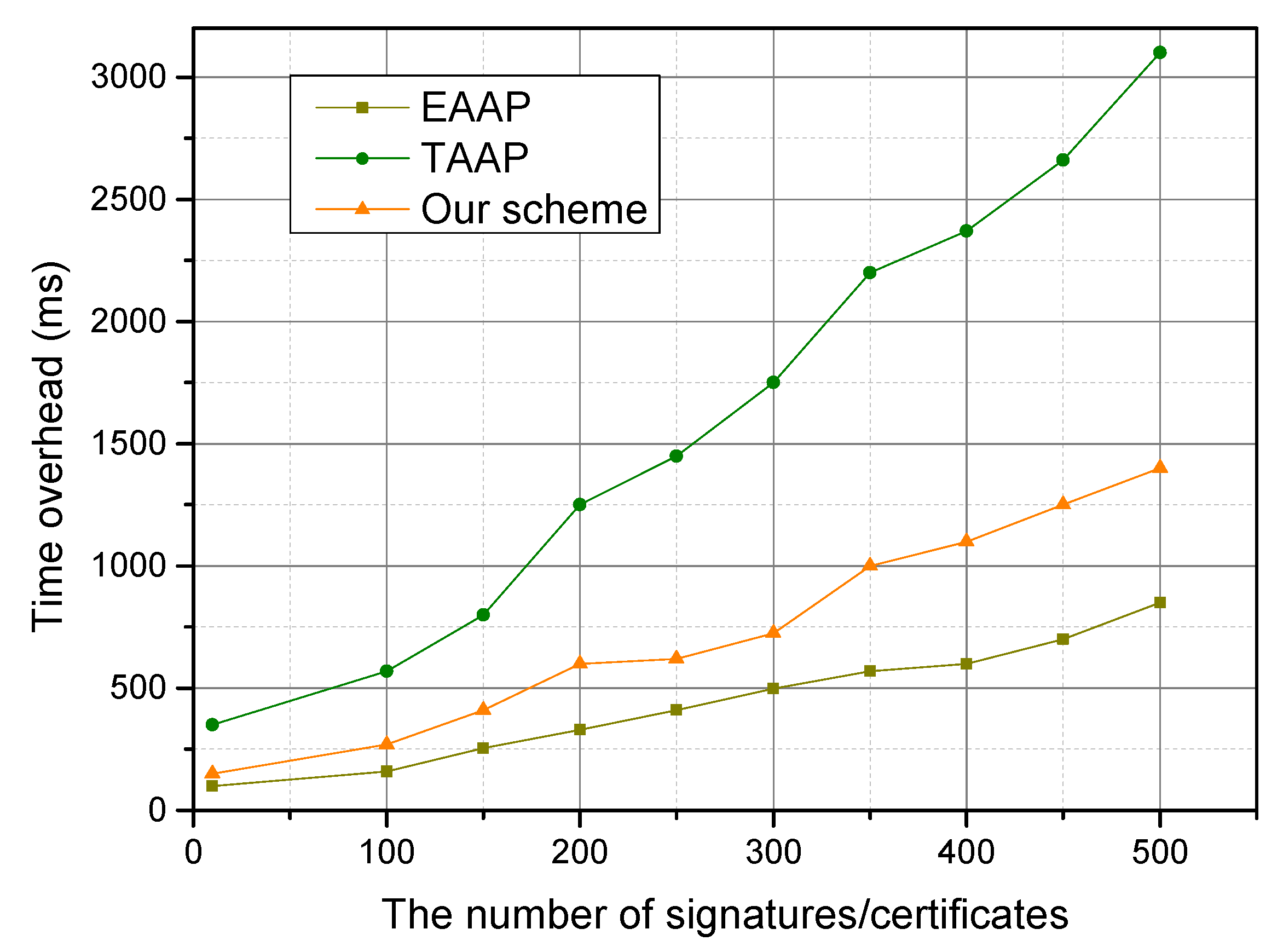
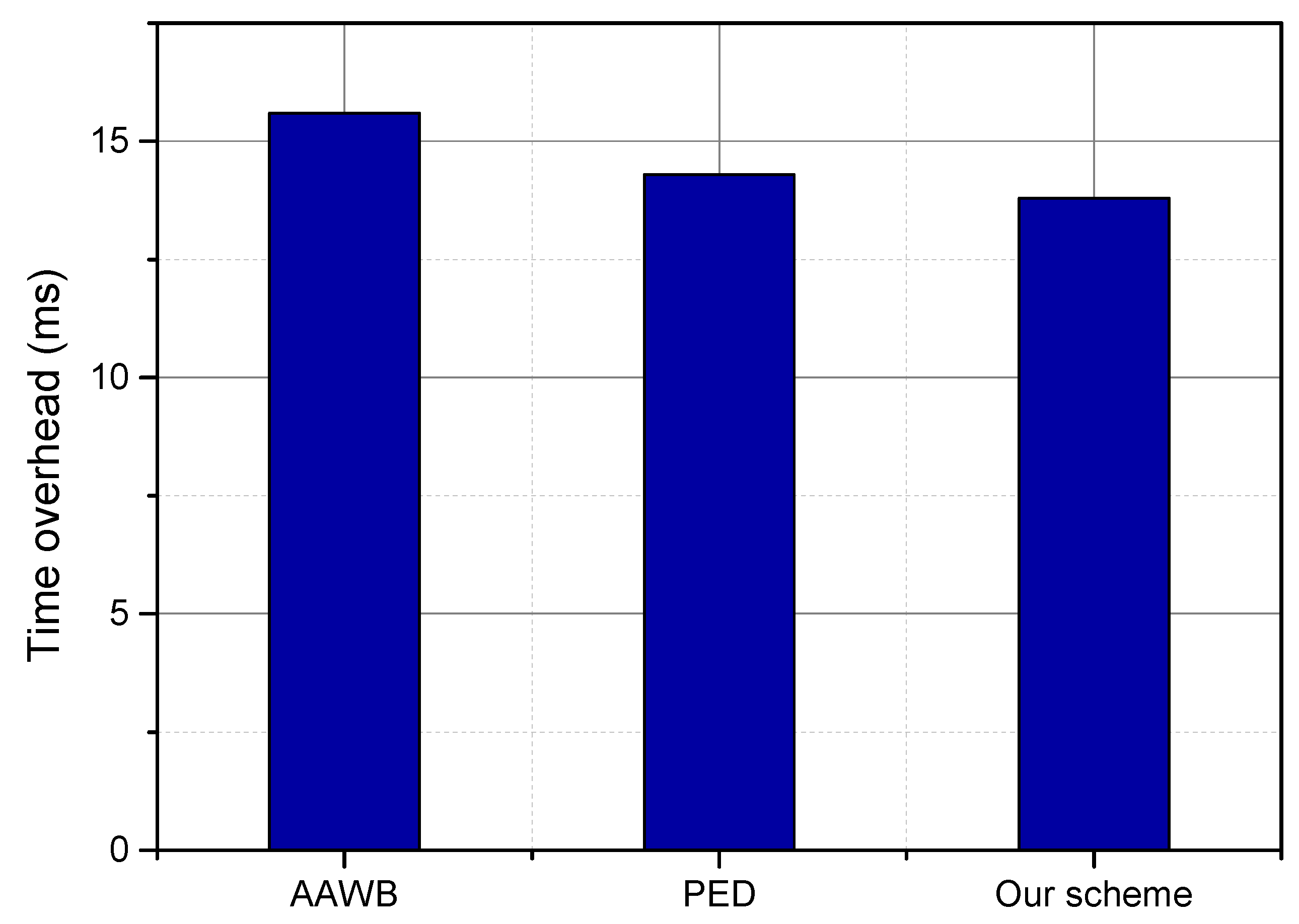
6.2. Simulation Results
7. Case Studies: Map Data Sharing in Vehicular Platooning
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Bautista, C.; Mester, G. Internet of things in self-driving cars environment. Interdiscip. Descr. Complex Syst. 2023, 21, 188–198. [Google Scholar] [CrossRef]
- Liu, L.; Chen, C.; Pei, Q.; Maharjan, S.; Zhang, Y. Vehicular edge computing and networking: A survey. Mob. Netw. Appl. 2021, 26, 1145–1168. [Google Scholar] [CrossRef]
- Taibo Institute. White Paper on High-Precision Map Technology and Applications (2022); Technical Report; Taibo Institute: Beijing, China, 2022; Available online: http://tiu.taibo.cn/p/409 (accessed on 12 June 2025).
- Song, R.; Xiao, B.; Song, Y.; Guo, S.; Yang, Y. A survey of blockchain-based schemes for data sharing and exchange. IEEE Trans. Big Data 2023, 9, 1477–1495. [Google Scholar] [CrossRef]
- Coruh, U.; Bayat, O. ESAR: Enhanced secure authentication and revocation scheme for vehicular Ad Hoc networks. J. Inf. Secur. Appl. 2022, 64, 103081. [Google Scholar] [CrossRef]
- Choi, J.Y.; Jakobsson, M.; Wetzel, S. Balancing auditability and privacy in vehicular networks. In Proceedings of the 1st ACM International Workshop on Quality of Service & Security in Wireless and Mobile Networks, Montreal, QC, Canada, 13 October 2005; pp. 79–87. [Google Scholar]
- Lin, X.; Sun, X.; Ho, P.H.; Shen, X. GSIS: A secure and privacy-preserving protocol for vehicular communications. IEEE Trans. Veh. Technol. 2007, 56, 3442–3456. [Google Scholar]
- Yang, Y.; Zhang, L.; Zhao, Y.; Choo, K.K.R.; Zhang, Y. Privacy-preserving aggregation-authentication scheme for safety warning system in fog-cloud based VANET. IEEE Trans. Inf. Forensics Secur. 2022, 17, 317–331. [Google Scholar] [CrossRef]
- Chen, W.; Chen, Y.; Chen, X.; Zheng, Z. Toward secure data sharing for the IoV: A quality-driven incentive mechanism with on-chain and off-chain guarantees. IEEE Internet Things J. 2019, 7, 1625–1640. [Google Scholar] [CrossRef]
- Liu, J.; Li, X.; Jiang, Q.; Obaidat, M.S.; Vijayakumar, P. BUA: A blockchain-based unlinkable authentication in VANETs. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Bajoudah, S.; Dong, C.; Missier, P. Toward a decentralized, trust-less marketplace for brokered IoT data trading using blockchain. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 339–346. [Google Scholar]
- Lu, Z.; Wang, Q.; Qu, G.; Zhang, H.; Liu, Z. A blockchain-based privacy-preserving authentication scheme for VANETs. IEEE Trans. Very Large Scale Integr. Syst. 2019, 27, 2792–2801. [Google Scholar] [CrossRef]
- Feng, X.; Shi, Q.; Xie, Q.; Liu, L. An efficient privacy-preserving authentication model based on blockchain for VANETs. J. Syst. Archit. 2021, 117, 102158. [Google Scholar] [CrossRef]
- Bampatsikos, M.; Politis, I.; Xenakis, C.; Thomopoulos, S.C.A. Solving the cold start problem in Trust Management in IoT. In Proceedings of the 16th International Conference on Availability, Reliability and Security, Vienna, Austria, 17–20 August 2021; pp. 1–9. [Google Scholar]
- Gazdar, T.; Alboqomi, O.; Munshi, A. A decentralized blockchain-based trust management framework for vehicular ad hoc networks. Smart Cities 2022, 5, 348–363. [Google Scholar] [CrossRef]
- Zhu, T.; Zhang, X.; Duan, J.; Zhou, Z.; Chen, X. A budget-aware incentive mechanism for vehicle-to-grid via reinforcement learning. In Proceedings of the 2023 IEEE/ACM 31st International Symposium on Quality of Service (IWQoS), Orlando, FL, USA, 19–21 June 2023; pp. 1–10. [Google Scholar]
- European Commission. Connected and Automated Mobility (CAM) White Paper; European Commission: Brussels, Belgium, 2020. [Google Scholar]
- Hu, D.; Li, Y.; Pan, L.; Li, M.; Zheng, S. A blockchain-based trading system for big data. Comput. Netw. 2021, 191, 107994. [Google Scholar] [CrossRef]
- Xie, Q.; Ding, Z.; Tang, W.; He, D.; Tan, X. Provable secure and lightweight blockchain-based V2I handover authentication and V2V broadcast protocol for VANETs. IEEE Trans. Veh. Technol. 2023, 72, 15200–15212. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Pournaghi, S.M.; Zahednejad, B.; Bayat, M.; Farjami, Y. NECPPA: A novel and efficient conditional privacy-preserving authentication scheme for VANET. Comput. Netw. 2018, 134, 78–92. [Google Scholar] [CrossRef]
- Huang, Y.; Zeng, Y.; Ye, F.; Yang, Y. Fair and protected profit sharing for data trading in pervasive edge computing environments. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications, Toronto, ON, Canada, 6–9 July 2020; pp. 1718–1727. [Google Scholar]
- Azees, M.; Vijayakumar, P.; Deboarh, L.J. EAAP: Efficient anonymous authentication with conditional privacy-preserving scheme for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2467–2476. [Google Scholar] [CrossRef]
- Shao, J.; Lin, X.; Lu, R.; Zuo, C. A threshold anonymous authentication protocol for VANETs. IEEE Trans. Veh. Technol. 2015, 65, 1711–1720. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Kumar, N.; Lee, J.H. Anonymous authentication for wireless body area networks with provable security. IEEE Syst. J. 2016, 11, 2590–2601. [Google Scholar] [CrossRef]
- Wang, C.; Wang, S.; Cheng, X.; He, Y.; Xiao, K.; Fan, S. A privacy and efficiency-oriented data sharing mechanism for IoTs. IEEE Trans. Big Data 2022, 9, 174–185. [Google Scholar] [CrossRef]
- Chen, Y.; Chen, H.; Yang, S.; Gao, X.; Guo, Y.; Wu, F. Designing Incentive Mechanisms for Mobile Crowdsensing with Intermediaries. Wirel. Commun. Mob. Comput. 2019, 2019, 8603526. [Google Scholar] [CrossRef]
- He, Y.; Zhang, X.; Wang, L.; Li, M. Performance Analysis and Optimization Design of AAV-Assisted Vehicle Platooning in NOMA-Enhanced Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2025, 26, 8810–8819. [Google Scholar] [CrossRef]








| Centralized Scheme | Decentralized Scheme | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Scheme | [5] | [6] | [8] | [7] | [9] | [10] | [12] | [13] | [11] | Our work |
| Single Point of Failure | √ | √ | √ | √ | √ | × | × | × | × | × |
| Dynamic Incentive | × | √ | × | × | √ | × | × | × | √ | √ |
| Anonymity | √ | √ | √ | √ | × | √ | √ | √ | × | √ |
| Data Privacy | √ | √ | √ | √ | × | √ | √ | √ | × | √ |
| Unlinkability | × | × | √ | × | × | √ | √ | √ | × | √ |
| Traceability | × | × | √ | √ | × | √ | × | × | × | √ |
| Notations | Description |
|---|---|
| The k-th RSU | |
| The i-th vehicle managed by | |
| , | Identifier of and |
| , | The plaintext and ciphertext of map data. |
| The j-th certificate of | |
| Validity period of | |
| The j-th pseudonym of | |
| Data-sharing request | |
| Data request announcement | |
| Random value used to generate the session key | |
| Registration phase session key encrypts VA- communication | |
| Authentication phase session key encrypts - communication | |
| Authentication phase session key encrypts - communication | |
| Session key encrypts map data between and | |
| The auxiliary path | |
| Initial reputation value | |
| The reputation gain | |
| Penalty term for the j-th sharing of | |
| Trust terms for the j-th sharing of | |
| Reputation of after the j-th sharing | |
| Reputation threshold | |
| Accumulated historical reputation | |
| B | Budget for sharing data |
| ’s bid | |
| Challenge |
| Symbol | Description |
|---|---|
| Point multiplication | |
| Bilinear pairing | |
| Hashing | |
| Exponential operation on | |
| Exponentiation on | |
| map-to-point operations |
| Scheme | Issue Key | Calculate Sign /Certificate | Build /Update MHT | Verify the Sign/Certificate | |
|---|---|---|---|---|---|
| Non_Overlap | Overlap | ||||
| EAAP | – | ||||
| TAAP | – | ||||
| Our Scheme | / | ||||
| Comparison Scheme | Single-User Overhead | Multi-User Overhead |
|---|---|---|
| PED | ||
| AAWB | ||
| Our Scheme |
| Comparison Scheme | Issue Key and Pseudonym | Mutual Authentication |
|---|---|---|
| EAAP | ||
| TAAP | ||
| Our Scheme |
| Round | Seed | Vehicle |
|---|---|---|
| 1 | 42 | |
| 2 | 42 | |
| ⋮ | ⋮ | ⋮ |
| 100 | 42 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fan, K.; Liu, Q.; Liu, C.; Lu, N.; Shi, W. An Efficient and Fair Map-Data-Sharing Mechanism for Vehicular Networks. Electronics 2025, 14, 2437. https://doi.org/10.3390/electronics14122437
Fan K, Liu Q, Liu C, Lu N, Shi W. An Efficient and Fair Map-Data-Sharing Mechanism for Vehicular Networks. Electronics. 2025; 14(12):2437. https://doi.org/10.3390/electronics14122437
Chicago/Turabian StyleFan, Kuan, Qingdong Liu, Chuchu Liu, Ning Lu, and Wenbo Shi. 2025. "An Efficient and Fair Map-Data-Sharing Mechanism for Vehicular Networks" Electronics 14, no. 12: 2437. https://doi.org/10.3390/electronics14122437
APA StyleFan, K., Liu, Q., Liu, C., Lu, N., & Shi, W. (2025). An Efficient and Fair Map-Data-Sharing Mechanism for Vehicular Networks. Electronics, 14(12), 2437. https://doi.org/10.3390/electronics14122437





