Cybersecurity Conceptual Framework Applied to Edge Computing and Internet of Things Environments
Abstract
1. Introduction
- Application Layer: The most frequent attacks include malware, viruses, and spyware. These are followed by malicious code injections, phishing, cross-site scripting (XSS), and botnet attacks.
- Network Layer: Denial-of-service (DoS), replay attacks, and man-in-the-middle (MitM) attacks are the most prevalent. Other notable threats include selective forwarding, Sybil attacks, and sinkhole attacks.
- Perception Layer: The most common threats are node capture and node tampering attacks. These are followed by eavesdropping and cyber-physical attacks.
2. Related Work
3. Contribution
- Integrated security approach: Combines the structured, policy-based framework of the NIST with the automation and continuous integration capabilities of DevSecOps to provide a comprehensive security model.
- Framework Design for Edge and IoT Contexts: Tailors the cybersecurity framework to address the specific needs and threats of distributed computing environments, such as Edge devices and IoT systems.
- Support for Proactive Security: Embeds security throughout the software development lifecycle (SDLC), infrastructure deployment, and operational processes to enable continuous risk mitigation and security monitoring.
- Incident Detection and Response: Ensures rapid threat detection and automated incident response mechanisms to improve system resilience and operational continuity.
- Real-World Applicability: Demonstrates potential applications in critical sectors such as industrial IoT, smart cities, healthcare, and autonomous networks, where cybersecurity is vital for safety and performance.
- Compliance Facilitation: Enhances continuous compliance with industry regulations through integrated security governance practices.
- Foundation for Future Research: Provides a basis for empirical testing, expert validation, and real-world deployment, promoting iterative refinement and adaptation across diverse operational settings.
4. Methodology
- Data Extraction: The relevant data were systematically extracted from each source, focusing on key elements such as the context of the problem, proposed solutions, results obtained, and conclusions drawn.
- Categorization and Coding: The extracted information was categorized into thematic areas to facilitate comparison. The categories identified were as follows:
- Cybersecurity-Related
- ∘
- Cybersecurity
- ∘
- Security
- Industry-Related
- ∘
- Smart industry
- ∘
- Industry 4.0
- ∘
- Industry 5.0
- Theoretical-Related
- ∘
- Framework
- ∘
- Industrial standards
- ∘
- Regulatory compliance
- ∘
- Security standards
- ∘
- Best practices
- ∘
- Assessment methodologies
- Technology-Related
- ∘
- Cyber-physical systems
- ∘
- Cloud computing
- ∘
- Edge Computing
- ∘
- Fog computing
- ∘
- Machine learning
- ∘
- Deep learning
- ∘
- Internet of Things
- ∘
- Industrial Internet of Things
- ∘
- Blockchain
- ∘
- Artificial intelligence
- Analysis of Differences and Similarities: The extracted data were analyzed for both similarities and discrepancies across sources, considering aspects such as context, perspective, and accuracy.
- Interpretation and Synthesis: The findings from the comparative analysis were synthesized to provide a comprehensive and critical view of the existing knowledge base. This allowed us to define the core elements to be integrated into the proposed framework.
- Participant Selection: The first step was to define the profile of the participants. Specifically, software developers with advanced knowledge in cybersecurity were chosen, ensuring that they possessed the necessary expertise to assess the technical aspects and applicability of the proposal.
- Recruitment of Participants: Participants were recruited from various software development companies based in Mexico and the United States of America, and Universities from Mexico and Ecuador, ensuring a diverse range of professional backgrounds and experiences. Selected participants were recognized for their expertise in the fields of cybersecurity and software development.
- Survey Design: An online survey was developed to gather demographic information from the participants, as well as their experience and technical perception regarding the foundational principles, relevance, and feasibility of implementing the proposed framework. The survey was designed to capture both quantitative and qualitative data that would provide insights into the participants’ views.

5. Proposed Framework
5.1. Summary
5.2. Synergy
5.3. Framework Components
5.3.1. Core: Govern
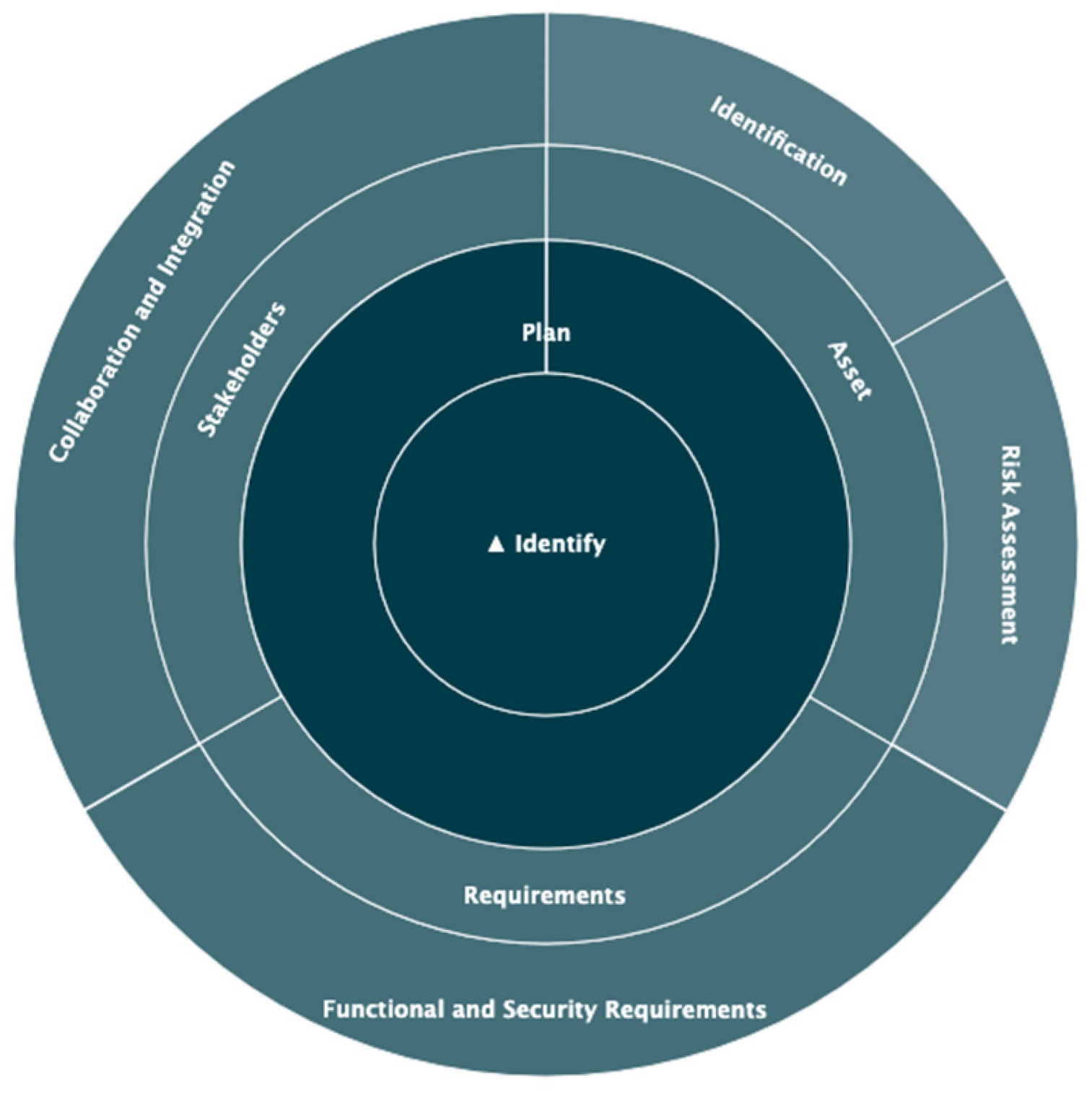
5.3.2. First Quadrant: Identify–Plan
- Asset inventory and environment topology
- ∘
- Identify and document all IoT devices, Edge Computing nodes, networks, platforms, and software involved.
- ∘
- Maintain an up-to-date record of asset location, connectivity, and relationships.
- ∘
- Implement an automated asset discovery and change monitoring system.
- Classification and categorization of sensitive data
- ∘
- Determine what data are critical, confidential, or sensitive within the Edge and IoT environments.
- ∘
- Apply data labeling schemes based on regulations such as GDPR, HIPAA, or national standards.
- ∘
- Assess the criticality of information based on its impact on privacy, integrity, and availability.
- Threat analysis and risk modeling
- ∘
- Implement threat modeling methodologies (STRIDE, PASTA, DREAD) to evaluate potential attacks at each layer of the ecosystem.
- ∘
- Maintain a taxonomy of threats specific to the IoT and Edge Computing, including physical, network, and software attacks.
- ∘
- Evaluate attack vectors using tools such as “MITRE ATT&CK” for the IoT.
- Vulnerability assessment and security testing
- ∘
- Perform regular vulnerability scans on IoT devices, gateways, and management platforms.
- ∘
- Apply penetration testing (pentesting) to assess the exposure of the environment in different attack scenarios.
- ∘
- Integrate vulnerability detection tools into the development and operation cycle.
- Evaluation of regulations and standards
- ∘
- Identify the applicable regulatory frameworks (ISO 27001, IEC 62443 [48], among others).
- ∘
- Assess compliance with privacy, data protection, and industrial safety regulations.
- ∘
- Establish compliance metrics and remediation plans for regulatory breaches.
- Definition of risk profiles and impact matrix
- ∘
- Classify risks according to their probability and severity using impact matrices.
- ∘
- Establish risk profiles for each type of device and operating environment.
- ∘
- Prioritize risks based on their impact on business continuity and security.
- Incident response and recovery plans
- ∘
- Develop specific cybersecurity incident response plans in Edge Computing and the IoT.
- ∘
- Simulate attack scenarios to assess the effectiveness of plans and improve resilience.
- ∘
- Integrate automatic response mechanisms for rapid incident mitigation.
- Security training and awareness
- ∘
- Implement specific cybersecurity training programs for teams and end users.
- ∘
- Establish attack simulations (phishing, social engineering) to strengthen the security culture.
- ∘
- Foster a security mindset by design in all phases of development and implementation.
5.3.3. Second Quadrant: Protect–Build and Verify
- Security by design and protection of the attack surface
- ∘
- Apply the principle of “security by design” in the development and integration of IoT/Edge devices and systems.
- ∘
- Reduce the attack surface by eliminating unnecessary services, closing unused ports, and applying secure default configurations.
- ∘
- Use hardening techniques to strengthen security across devices, gateways, and platforms.
- Secure identity, access, and authentication management
- ∘
- Implement identity and access management (IAM) with Zero Trust-based authentication and authorization controls.
- ∘
- Use multi-factor authentication (MFA) and access credentials based on certificates, biometrics, or physical tokens.
- ∘
- Apply the principle of least privilege and segregation of duties in users, devices, and applications.
- Data encryption in transit and at rest
- ∘
- Implement end-to-end encryption (E2EE) for communication between IoT devices and Edge Computing nodes.
- ∘
- Use robust encryption algorithms (AES-256, ECC, TLS 1.3) and properly manage cryptographic keys.
- ∘
- Protect data at rest with secure storage, hashing, and database encryption techniques.
- Protection against malware, ransomware, and malicious code
- ∘
- Deploy malware detection and prevention (EDR/XDR) solutions on Edge and IoT devices.
- ∘
- Implement secure boot mechanisms and signed firmware to prevent malicious code execution.
- ∘
- Apply continuous monitoring with threat intelligence to identify new attack vectors.
- Network segmentation and micro-segmentation
- ∘
- Implement network segmentation at physical and logical levels, separating critical devices, IT environments, and OT environments.
- ∘
- Apply next-generation firewalls (NGFWs) and access-control lists (ACLs) to restrict unauthorized traffic.
- ∘
- Use identity- and context-based micro-segmentation techniques to improve security in distributed networks.
- Building resiliency and availability in systems
- ∘
- Design redundant architectures with high-availability (HA) and automatic-failover mechanisms.
- ∘
- Implement secure backup and disaster recovery strategies with encrypted backups.
- ∘
- Use security orchestration and automation platforms to improve operational resiliency.
- Updates and Vulnerability Management
- ∘
- Implement an update and patch management process for firmware, operating systems, and IoT/Edge applications.
- ∘
- Apply compatibility tests before deploying updates to critical environments.
- ∘
- Automate vulnerability detection and remediation with Vulnerability Management tools.
- Safety testing and continuous evaluation
- ∘
- Perform penetration testing (Pentesting) and security audits on devices, networks, and applications.
- ∘
- Apply fuzzing techniques and static code analysis (ESLint 9.27.0) to detect vulnerabilities in IoT/Edge software.
- ∘
- Assess compliance with security standards through regular reviews and compliance audits.
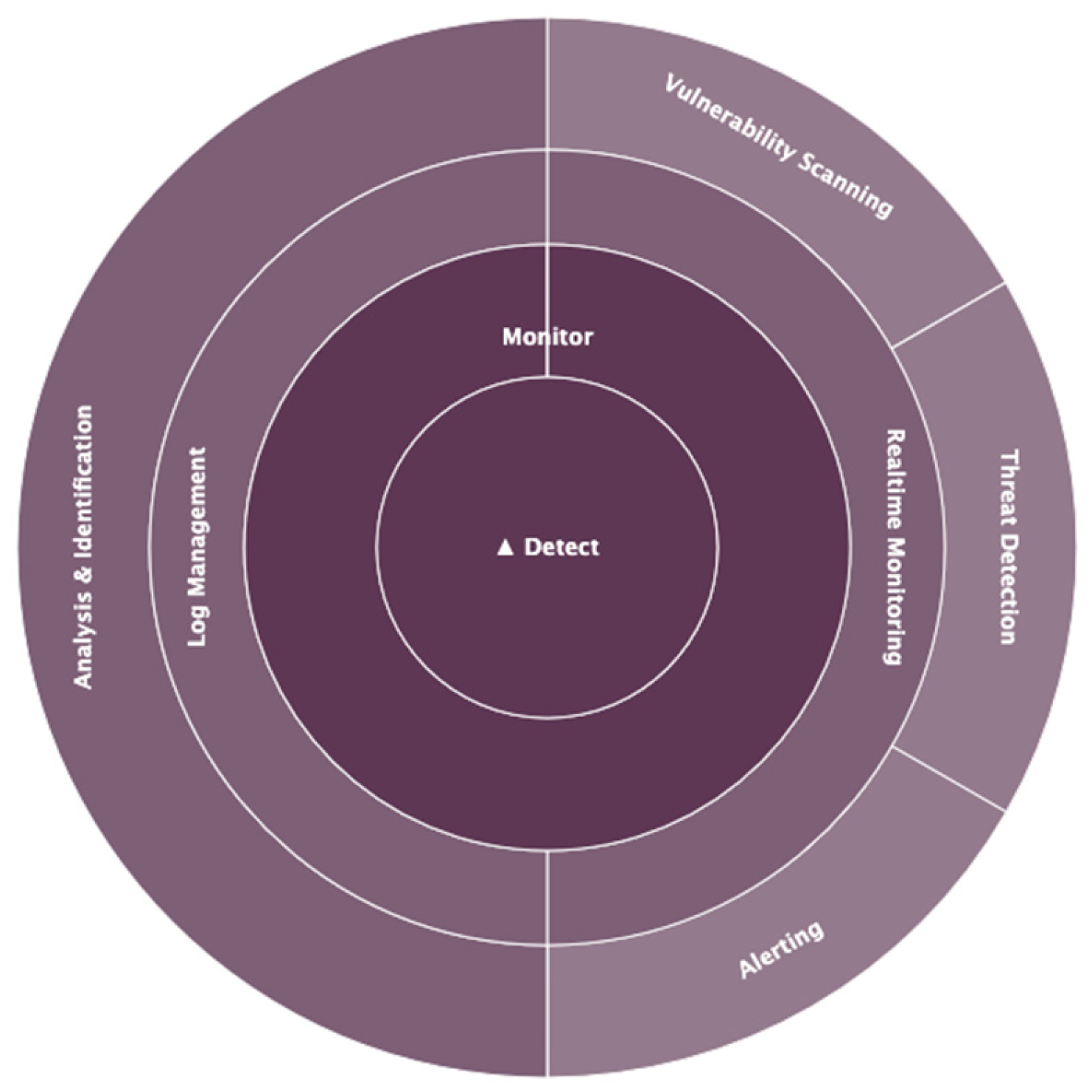
5.3.4. Third Quadrant: Detect–Monitor
- Implementation of a real-time monitoring system
- ∘
- Deploy threat detection tools (IDS/IPS, SIEM, SOAR) adapted to IoT and Edge Computing environments.
- ∘
- Configure security sensors on IoT devices, gateways, and cloud platforms to collect critical events.
- ∘
- Implement advanced telemetry mechanisms to obtain real-time data on suspicious activity.
- Using threat intelligence for early detection
- ∘
- Integrate threat intelligence feeds to update indicator of compromise (IoC) databases.
- ∘
- Apply tools such as MITRE ATT&CK for ICS/IoT to map-attacker tactics and techniques.
- ∘
- Use machine learning and behavioral analysis to detect anomalies in traffic, authentications, and access.
- Continuous attack-surface monitoring
- ∘
- Implement exposure assessment tools to identify exploitable vulnerabilities in Edge and IoT devices.
- ∘
- Monitor API interfaces, firmware, and network connections for improper access or unauthorized changes.
- ∘
- Apply automated security testing to continuously assess the security posture of the environment.
- Log analysis and event auditing
- ∘
- Configure log centralization (Syslog, ELK Stack, Graylog, Splunk) to correlate security events.
- ∘
- Implement record retention in compliance with cybersecurity regulations and standards.
- ∘
- Establish audit policies to detect improper access and unauthorized changes to critical systems.
- Event correlation and forensic analysis
- ∘
- Apply pattern detection using SIEM and correlation tools to analyze distributed attacks.
- ∘
- Use Threat Hunting techniques to identify advanced persistent threats (APTs) within the network.
- ∘
- Develop digital forensics procedures to investigate security incidents in IoT and Edge devices.
- Anomaly detection in IoT networks and traffic
- ∘
- Implement intrusion detection systems (NIDS and HIDS) with specific rules for IoT and Edge Computing.
- ∘
- Analyze traffic patterns for unusual behavior, such as unexpected connections or increased requests.
- ∘
- Use AI-based detection models to prevent denial-of-service (DDoS) attacks on IoT devices.
- Data and device integrity security
- ∘
- Implement firmware and configuration integrity check to detect malicious modifications.
- ∘
- Apply cryptographic hashing to verify that files and firmware have not been tampered with.
- ∘
- Monitor supply chain attacks that may compromise devices and software.
- Real-time vulnerability assessment and management
- ∘
- Integrate Vulnerability Management tools for vulnerability scanning and prioritization.
- ∘
- Establish automated patching and mitigation processes based on asset criticality and exposure.
- ∘
- Perform impact analysis before deploying updates to critical systems.
- Priority-based incident response and alerting
- ∘
- Set up a system of alerts and automatic notifications based on criticality levels.
- ∘
- Implement automated response flows (SOAR) to reduce incident detection and reaction time.
- ∘
- Define escalation protocols to notify the appropriate teams based on the severity of the event.
- Continuous evaluation and improvement of the detection process
- ∘
- Perform attack simulations (Red Team/Blue Team/Purple Team) to improve detection ability.
- ∘
- Constantly adjust detection rules and policies based on new cyberattack tactics and techniques.
- ∘
- Establish metrics and KPIs to measure the effectiveness of threat monitoring and detection systems.
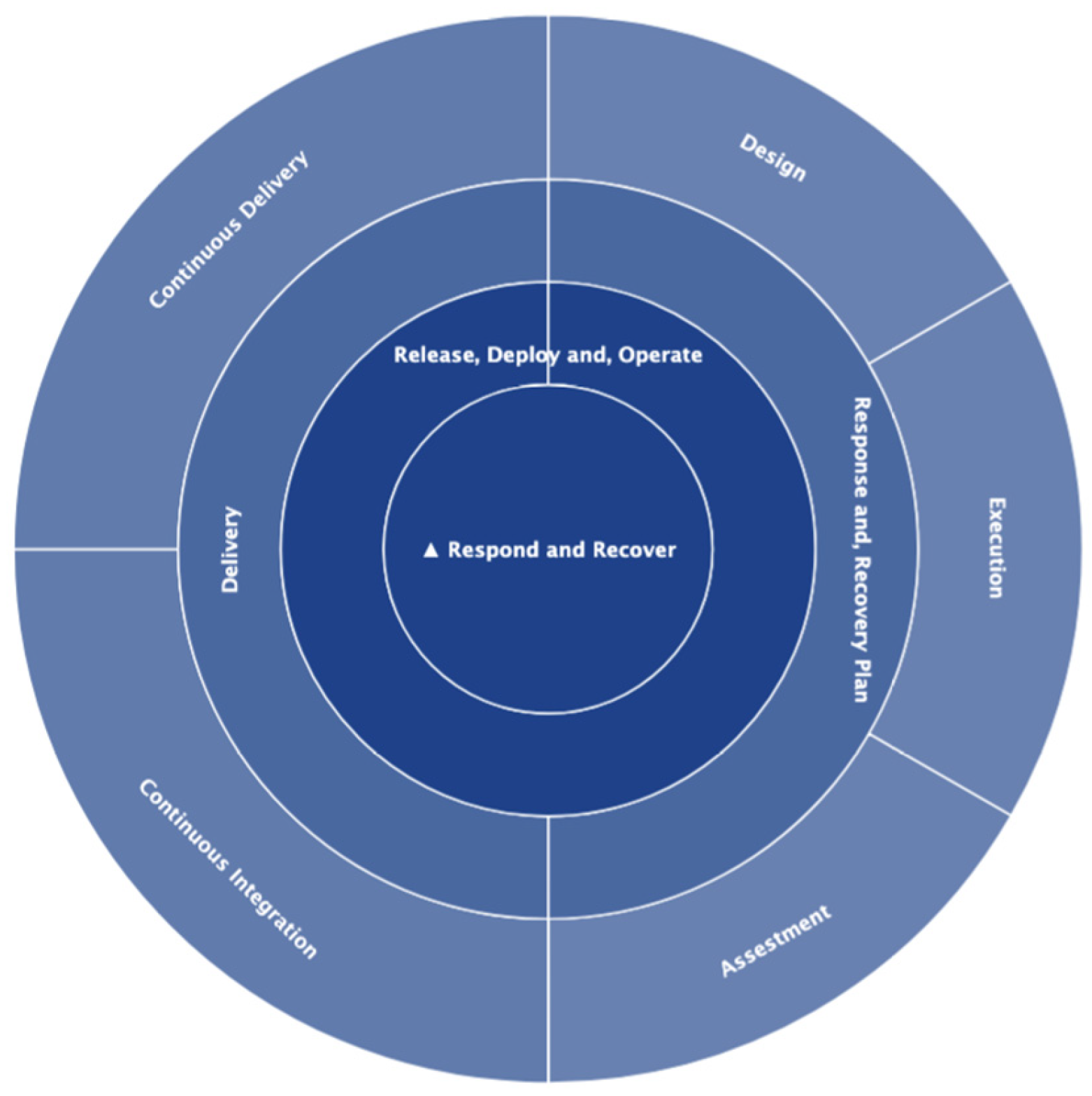
5.3.5. Fourth Quadrant: Respond and Recover–Release, Deploy, and Operate
- Development of an incident response plan (IRP) specific to Edge and IoT
- ∘
- Define an incident response plan (IRP) that contemplates specific IoT and Edge Computing threats.
- ∘
- Establish procedures for containment, mitigation, and eradication of threats in distributed environments.
- ∘
- Integrate multidisciplinary teams (CSIRT/SOC/OT security) for efficient incident management.
- Implementing an attack containment mechanism
- ∘
- Apply micro-segmentation strategies and dynamic access-control lists to isolate compromised devices.
- ∘
- Implement automated response mechanisms with SOAR (security orchestration, automation, and response) tools.
- ∘
- Develop sandboxing and quarantine policies for suspicious or compromised devices.
- Threat elimination and eradication strategies
- ∘
- Design secure reimagining processes of Edge and IoT devices to prevent malware persistence.
- ∘
- Apply forced updates and critical patches to affected devices without compromising availability.
- ∘
- Deploy Threat Hunting tools to identify malicious actors within the environment.
- Response orchestration and automation
- ∘
- Integrate automatic incident responses into the software and firmware deployment pipeline.
- ∘
- Use AI- and ML-based models to prioritize responses based on attack criticality.
- ∘
- Implement real-time corrective actions, such as revoking credentials and disabling compromised access.
- Recovery and business continuity strategies
- ∘
- Design high-availability (HA) and redundancy architectures in Edge Computing and IoT.
- ∘
- Implement a disaster recovery plan (DRP) with multi-location backup.
- ∘
- Validate the effectiveness of recovery plans through periodic incident simulations.
- Versioning management and secure deployment of firmware and software
- ∘
- Use digitally signed firmware and integrity validation mechanisms prior to deployment.
- ∘
- Establish a secure CI/CD pipeline, ensuring that updates do not introduce vulnerabilities.
- ∘
- Implement secure rollback strategies in case of failures in updates or deployments.
- Post-deployment validation and monitoring
- ∘
- Implement a post-deployment testing process to validate that there are no insecure configurations.
- ∘
- Establish an intensive monitoring period after releasing new firmware/software versions.
- ∘
- Apply penetration testing and fuzzing techniques to detect residual vulnerabilities.
- Forensic assessment and post-incident impact analysis
- ∘
- Perform digital forensics to determine the root cause of the incident and its scope.
- ∘
- Establish a timeline of the attack to understand how it happened and how to prevent future incidents.
- ∘
- Generate detailed reports with indicators of compromise (IoCs) and tactics used in the attack.
- Communication and coordination during and after an incident
- ∘
- Develop secure communication protocols with internal and external stakeholders during incidents.
- ∘
- Establish alternative channels for communication in the event of network infrastructure disruptions.
- ∘
- Comply with incident reporting regulations and standards within established times.
- Continuous evaluation and improvement of the response process
- ∘
- Implement a continuous improvement methodology based on lessons learned after each incident.
- ∘
- Adjust the security framework based on threat intelligence and new adversarial tactics.
- ∘
- Regularly train safety teams with Red Team/Blue Team/Purple Team exercises.
5.4. Implementation Challenges and Mitigation Strategies in IoT and Edge Computing Environments
6. Conceptual Evaluation by Expert Panel
6.1. Evaluation Design
6.2. Experts Information and Feedback
6.2.1. Demographic Information
6.2.2. Perceptions of Methodological Aspects
- “The relevance of the framework is supported by how its elements and structure facilitate decision-making and the implementation of specific measures, all aligned with key cybersecurity standards and principles”.
- “This is an approach I wasn’t familiar with, and upon reviewing it, there appear to be many ways to implement it, thus adding value in various potential scenarios”.
- “I consider this framework to be unique and innovative; I haven’t heard of anything similar to it so far”.
- “There may be several studies related to security in devices, but none have taken into account the IoT devices we use in our daily lives... and if we also consider it at the AI level, it’s an area that is growing in an interesting way”.
- “The framework’s simple implementation is evident due to its integral components. I believe it could lead to benefits and/or improvements in cybersecurity in Edge Computing and IoT environments”.
- “The proposed framework favors and enables the necessary actions to achieve its purpose, as it offers a clear structure organized by levels, which will facilitate its implementation”.
6.2.3. Perceptions of Potential Efficacy and Efficiency in Practice
- “I believe the proposed framework is one of the best available options for implementation, as meeting expectations on time can significantly improve security implementation”.
- “The components of the framework help identify and prioritize critical requirements to ensure data integrity and privacy in Edge Computing and IoT environments”.
- “It was very helpful to follow the framework content while going through the components. I believe that it would be beneficial in practice”.
- “The framework allows for measures such as encryption, authentication, and network segmentation, facilitating implementation to reduce common risks in the mentioned environments. Additionally, its practical approach helps visualize how to act against various threats”.
- “The framework aligns with recognized standards such as NIST and ISO/IEC, integrating best practices that strengthen security in the proposed environments”.
- “Being maintainable and scalable, it offers better control and integration of new technologies”.
- “The framework includes elements such as authentication and access control, which are fundamental for establishing trust models in the proposed environment”.
6.3. Discussion and Limitations
6.4. Member Checking
6.5. Preliminary Practical Example
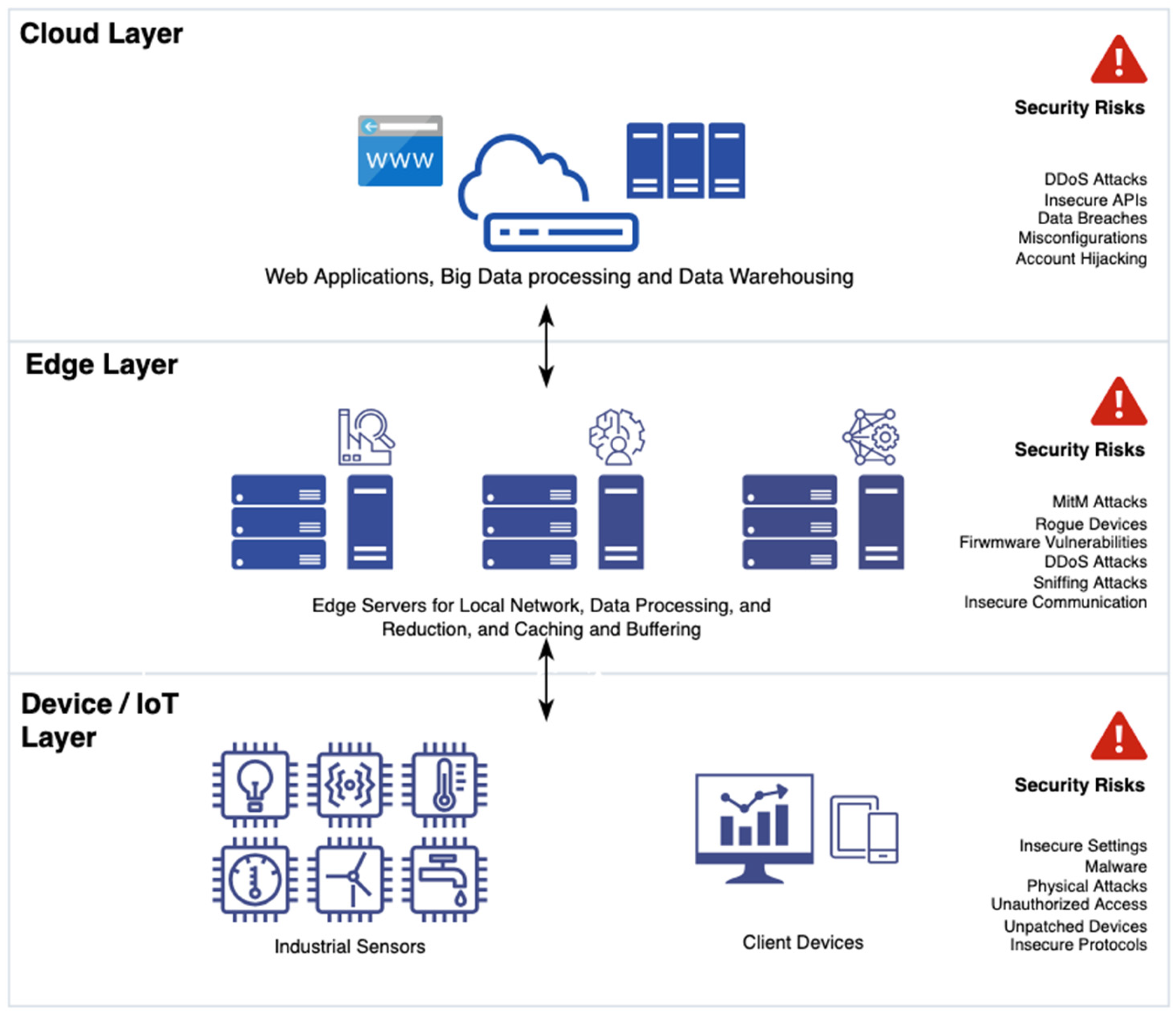
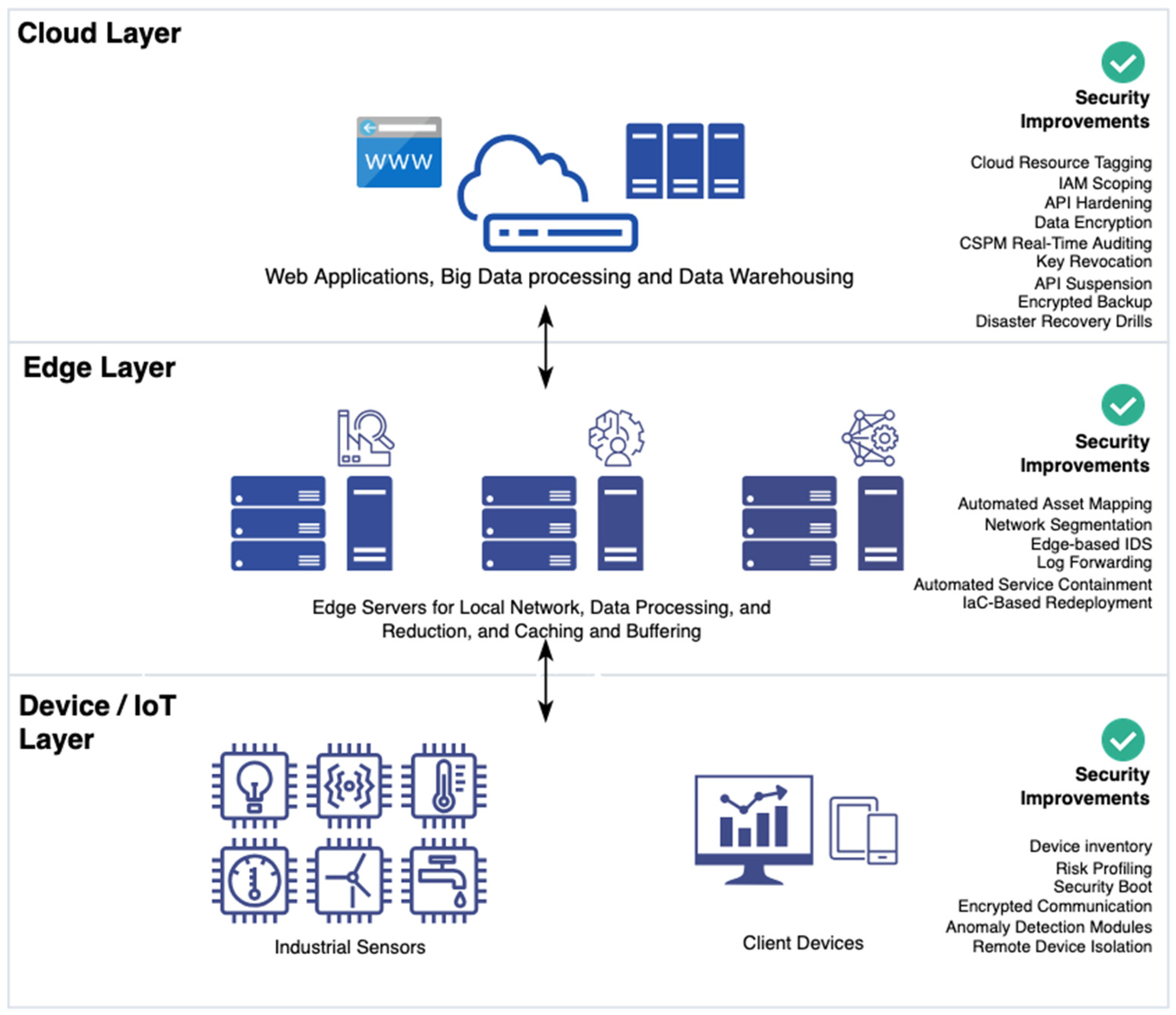
6.5.1. Overview
- Edge Server 1: Performs preliminary data processing and reduction.
- Edge Server 2: Manages data caching, buffering, and local failover storage.
- Edge Server 3: Handles local network services, access control, and routing.
6.5.2. Cybersecurity Challenges
6.5.3. Layer-Specific Improvements After Framework Implementation
- Device Layer Improvements
- All IoT devices were inventoried and associated with unique digital identities. Risk profiling was performed based on physical exposure and network behavior.
- Firmware signing and secure boot processes were implemented. Secure communication channels were established using mutual TLS. Hardcoded credentials were eliminated in favor of rotating tokens and certificate-based authentication.
- Lightweight anomaly detection modules were deployed directly on devices to identify unusual data patterns or firmware changes.
- Compromised or malfunctioning devices could be remotely isolated via Edge layer policies.
- Device configurations were version-controlled, allowing secure re-provisioning or rollback in case of breach.
- Edge Layer Improvements
- An automated asset inventory system was deployed to map all Edge components and dependencies.
- Role-based access control (RBAC) was enforced on all Edge servers. Network segmentation and virtual LANs (VLANs) were implemented to restrict lateral movement. All inter-server communications were encrypted using TLS 1.3.
- Edge servers were instrumented with intrusion detection systems (IDSs) and behavior-based logging. Monitoring agents forwarded logs to a central SIEM system.
- Automated containment strategies were established, such as blocking IPs exhibiting malicious behavior or shutting down specific services.
- Edge configurations were maintained as Infrastructure as Code (IaC), allowing automated redeployment in clean environments if needed.
- Cloud Layer Improvements
- Cloud assets were tagged and classified by sensitivity. Identity and access management policies were refined to enforce least privilege.
- API gateways were hardened using Web Application Firewalls (WAFs) and OAuth2.0-based authentication. Data in transit and at rest were encrypted using AES-256. Secrets management was integrated with CI/CD pipelines.
- Continuous cloud posture monitoring tools (e.g., CSPM) were introduced to audit misconfigurations. Audit logs were collected for compliance tracking.
- Cloud-based incident response playbooks were automated to revoke keys, suspend user accounts, or disable APIs under specific threat triggers.
- Regular encrypted backups were scheduled, and recovery procedures were validated through simulations and drills.
6.5.4. Results and Observations
- The MTTD (Mean Time to Detect) and MTTR (Mean Time to Respond) were significantly reduced due to automated monitoring and responsive controls.
- Device-level attacks, such as spoofing and rogue firmware uploads, were effectively mitigated through secure boot, signed firmware, and runtime anomaly detection.
- Edge-level resilience was improved through policy-driven segmentation, continuous monitoring, and automated rollback of compromised services.
- Cloud service integrity and confidentiality were strengthened through improved API security, encryption, and fine-grained authorization and authentication policies.
- The architecture demonstrated enhanced cyber-resilience, with the ability to maintain business continuity and quickly recover from cyber incidents.
7. Concluding Remarks
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Dritsas, E.; Trigka, M. A Survey on Cybersecurity in IoT. Future Internet 2025, 17, 30. [Google Scholar] [CrossRef]
- Zhukabayeva, T.; Zholshiyeva, L.; Karabayev, N.; Khan, S.; Alnazzawi, N. Cybersecurity Solutions for Industrial Internet of Things–Edge Computing Integration: Challenges, Threats, and Future Directions. Sensors 2025, 25, 213. [Google Scholar] [CrossRef] [PubMed]
- ElSayed, Z.; Abdelgawad, A.; Elsayed, N. Cybersecurity and Frequent Cyber Attacks on IoT Devices in Healthcare: Issues and Solutions. arXiv 2025, arXiv:2501.11250. [Google Scholar]
- Alotaibi, B. A Survey on Industrial Internet of Things Security: Requirements, Attacks, AI-Based Solutions, and Edge Computing Opportunities. Sensors 2023, 23, 7470. [Google Scholar] [CrossRef]
- Tange, K.; De Donno, M.; Fafoutis, X.; Dragoni, N. A Systematic Survey of Industrial Internet of Things Security: Requirements and Fog Computing Opportunities. IEEE Commun. Surv. Tutor. 2020, 22, 2489–2520. [Google Scholar] [CrossRef]
- Malatji, M.; Marnewick, A.L.; Solms, S.V. Cybersecurity Capabilities for Critical Infrastructure Resilience. Inf. Comput. Secur. 2021, 30, 255–279. [Google Scholar] [CrossRef]
- Reyes-Acosta, R.; Dominguez-Baez, C.; Mendoza-Gonzalez, R.; Vargas Martin, M. Analysis of Machine Learning-Based Approaches for Securing the Internet of Things in the Smart Industry: A Multivocal State of Knowledge Review. Int. J. Inf. Secur. 2024, 24, 31. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D.; Page, K.; Nurse, J.R.C.; Mantilla Montalvo, R.; Santos, O.; Maddox, L.; Burnap, P. Cyber Risk at the Edge: Current and Future Trends on Cyber Risk Analytics and Artificial Intelligence in the Industrial Internet of Things and Industry 4.0 Supply Chains. Cybersecurity 2020, 3, 13. [Google Scholar] [CrossRef]
- Matta, V.D.R.; Maheswara Rao, V.V.R.; Battula, V.S.J.; Addagatla, M.B. Mitigating Security Challenges in Edge Computing: Attacks, Defence Strategies, and Algorithms. In Proceedings of the 2025 3rd International Conference on Intelligent Data Communication Technologies and Internet of Things (IDCIoT), Bengaluru, India, 5–7 February 2025; pp. 462–470. [Google Scholar]
- Joshi, S.D.; Khairnar, V.A.; Somvanshi, S.V. A Comprehensive Study on Internet of Things (IoT): State-of-the-Art: Security Challenges, Future Directions, Applications and Opportunities. Int. J. Adv. Res. Sci. Commun. Technol. 2024, 4, 474–481. [Google Scholar] [CrossRef]
- Almuqren, A.A. Cybersecurity Threats, Countermeasures and Mitigation Techniques on the IoT: Future Research Directions. J. Cyber Secur. Risk Audit. 2025, 2025, 1–11. [Google Scholar] [CrossRef]
- Alotaibi, E.; Sulaiman, R.B.; Almaiah, M. Assessment of Cybersecurity Threats and Defense Mechanisms in Wireless Sensor Networks. J. Cyber Secur. Risk Audit. 2025, 2025, 47–59. [Google Scholar] [CrossRef]
- Almanasir, R.; Al-solomon, D.; Indrawes, S.; Almaiah, M.; Islam, U.; Alshar’e, M. Classification of Threats and Countermeasures of Cloud Computing. J. Cyber Secur. Risk Audit. 2025, 2025, 27–42. [Google Scholar] [CrossRef]
- Çetin, A.; Öztürk, S. Comprehensive Exploration of Ensemble Machine Learning Techniques for IoT Cybersecurity Across Multi-Class and Binary Classification Tasks. J. Future Artif. Intell. Technol. 2025, 1, 371–384. [Google Scholar] [CrossRef]
- Lamture, P.; Singh, T. Navigating Digital Transformation in the US IT Industry: Building Robust Cybersecurity Frameworks for New and Emerging Technologies. Int. J. Eng. Appl. Sci. Manag. 2025, 6, 1–7. [Google Scholar] [CrossRef]
- Sebestyen, H.; Popescu, D.E.; Zmaranda, R.D. A Literature Review on Security in the Internet of Things: Identifying and Analysing Critical Categories. Computers 2025, 14, 61. [Google Scholar] [CrossRef]
- Alshuaibi, A.; Almaayah, M.; Ali, A. Machine Learning for Cybersecurity Issues: A Systematic Review. J. Cyber Secur. Risk Audit. 2025, 2025, 36–46. [Google Scholar] [CrossRef]
- Narciandi-Rodriguez, D.; Aveleira-Mata, J.; García-Ordás, M.T.; Alfonso-Cendón, J.; Benavides, C.; Alaiz-Moretón, H. A Cybersecurity Review in IoT 5G Networks. Internet Things 2025, 30, 101478. [Google Scholar] [CrossRef]
- Qudus, L. Advancing Cybersecurity: Strategies for Mitigating Threats in Evolving Digital and IoT Ecosystems. Int. Res. J. Mod. Eng. Technol. Sci. 2025, 7, 3195–3201. [Google Scholar] [CrossRef]
- Mtsweni, J.; Gcaza, N.; Thaba, M. A Unified Cybersecurity Framework for Complex Environments. In SAICSIT ’18, Proceedings of the Annual Conference of the South African Institute of Computer Scientists and Information Technologists, Port Elizabeth, South Africa, 26 September 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 1–9. [Google Scholar]
- Aljumaiah, O.; Jiang, W.; Addula, S.R.; Almaiah, M.A. Analyzing Cybersecurity Risks and Threats in IT Infrastructure Based on NIST Framework. J. Cyber Secur. Risk Audit. 2025, 2025, 12–26. [Google Scholar] [CrossRef]
- Igwenagu, U.; Salami, A.A.; Arigbabu, A.S.; Esambe, M.C.; Oladoyinbo, T.O.; Olaniyi, O.O. Securing the Digital Frontier: Strategies for Cloud Computing Security, Database Protection, and Comprehensive Penetration Testing. J. Eng. Res. Rep. 2024, 26, 60–75. [Google Scholar] [CrossRef]
- Sandu, A.K. DevSecOps: Integrating Security into the DevOps Lifecycle for Enhanced Resilience. Technol. Manag. Rev. 2021, 6, 1–19. [Google Scholar]
- Rajapakse, R.N.; Zahedi, M.; Babar, M.A.; Shen, H. Challenges and Solutions When Adopting DevSecOps: A Systematic Review. Inf. Softw. Technol. 2022, 141, 106700. [Google Scholar] [CrossRef]
- Buksh, Z.; Sharma, N.A.; Chand, R.; Kumar, J.; Shawkat Ali, A.B.M. Cybersecurity Challenges in Smart Grid IoT. In IoT for Smart Grid; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2025; pp. 175–206. ISBN 978-1-394-27940-1. [Google Scholar]
- National Institute of Standards and Technology. The NIST Cybersecurity Framework (CSF) 2.0; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2024; p. NIST CSWP 29. [Google Scholar]
- National Institute of Standards and Technology. Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018; p. NIST CSWP 04162018. [Google Scholar]
- NIST SP 800-53; Security and Privacy Controls for Information Systems and Organizations. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020.
- Stankovic, J.A. Research Directions for the Internet of Things. IEEE Internet Things J. 2014, 1, 3–9. [Google Scholar] [CrossRef]
- Eito-Brun, R. Incorporating Innovation Management Practices to ISO/IEC 29110. In Systems, Software and Services Process Improvement; Springer International Publishing: Cham, Switzerland, 2017; pp. 15–25. [Google Scholar]
- Kim, G.; Humble, J.; Debois, P.; Willis, J. The DevOps Handbook: How to Create World-Class Agility, Reliability, and Security in Technology Organizations; IT Revolution: London, UK, 2016; ISBN 978-1-942788-07-2. [Google Scholar]
- Lokiny, N.; Nandanampati, R. DevSecOps: Integrating Security into DevOps with AI in Cloud. J. Sci. Eng. Res. 2020, 7, 239–242. [Google Scholar]
- Tissir, N.; El Kafhali, S.; Aboutabit, N. Cybersecurity Management in Cloud Computing: Semantic Literature Review and Conceptual Framework Proposal. J. Reliab. Intell. Environ. 2021, 7, 69–84. [Google Scholar] [CrossRef]
- ISO 27032:2023; Cybersecurity—Guidelines for Internet Security. International Organization for Standardization: Geneva, Switzerland, 2023.
- ISO 27001-2022; Information Security, Cybersecurity and Privacy Protection—Information Security Management Systems—Requirements. International Organization for Standardization: Geneva, Switzerland, 2022.
- Taherdoost, H. Understanding Cybersecurity Frameworks and Information Security Standards—A Review and Comprehensive Overview. Electronics 2022, 11, 2181. [Google Scholar] [CrossRef]
- Khaleefah, A.D.; Al-Mashhadi, H.M. Methodologies, Requirements and Challenges of Cybersecurity Frameworks: A Review. Int. J. Wirel. Microw. Technol. 2024, 13, 1–13. [Google Scholar] [CrossRef]
- Chauhan, M.; Shiaeles, S. An Analysis of Cloud Security Frameworks, Problems and Proposed Solutions. Network 2023, 3, 422–450. [Google Scholar] [CrossRef]
- Awan, K.A.; Ud Din, I.; Almogren, A.; Nawaz, A.; Khan, M.Y.; Altameem, A. SecEdge: A Novel Deep Learning Framework for Real-Time Cybersecurity in Mobile IoT Environments. Heliyon 2025, 11, e40874. [Google Scholar] [CrossRef]
- Sandhyakumari, G.; Bharathi, M.; Madhurima, V.; Tabassum, S.; Neelima, K.; Kumar, N.A. A Dynamic Cybersecurity Framework for Energy-Efficient Internet of Things. In Convergence of Cybersecurity and Cloud Computing; IGI Global Scientific Publishing: Hershey, PA, USA, 2025; pp. 165–190. ISBN 979-8-3693-6859-6. [Google Scholar]
- Okegbile, S.D.; Gambo, I.P. Artificial Intelligence-Driven Security Framework for Internet of Things-Enhanced Digital Twin Networks. Internet Things 2025, 31, 101564. [Google Scholar] [CrossRef]
- Garousi, V.; Felderer, M.; Mäntylä, M.V. Guidelines for Including Grey Literature and Conducting Multivocal Literature Reviews in Software Engineering. Inf. Softw. Technol. 2019, 106, 101–121. [Google Scholar] [CrossRef]
- Semantic Scholar. AI-Powered Research Tool. Available online: https://www.semanticscholar.org/ (accessed on 10 March 2025).
- Krippendorff, K. Content Analysis: An Introduction to Its Methodology; SAGE Publications, Inc.: Thousand Oaks, CA, USA, 2019; ISBN 978-1-5063-9566-1. [Google Scholar]
- Naeem, M.; Ozuem, W.; Howell, K.; Ranfagni, S. A Step-by-Step Process of Thematic Analysis to Develop a Conceptual Model in Qualitative Research. Int. J. Qual. Methods 2023, 22, 16094069231205789. [Google Scholar] [CrossRef]
- Mora, M. Descripción del Método de Investigación Conceptual; Universidad Autónoma de Aguascalientes: Aguascalientes, Mexico, 2003. [Google Scholar]
- Torrecilla-Salinas, C.J.; De Troyer, O.; Escalona, M.J.; Mejías, M. A Delphi-Based Expert Judgment Method Applied to the Validation of a Mature Agile Framework for Web Development Projects. Inf. Technol. Manag. 2019, 20, 9–40. [Google Scholar] [CrossRef]
- IEC 62443; Cybersecurity Standards. International Electrotechnical Commission: Geneva, Switzerland, 2021.
- García-García, J.A.; Reding-Bernal, A.; López-Alvarenga, J.C. Cálculo del tamaño de la muestra en investigación en educación médica. Investig. En Educ. Médica 2013, 2, 217–224. [Google Scholar] [CrossRef]
- Kite, M.E.; Whitley, B.E., Jr. Principles of Research in Behavioral Science, 3rd ed.; Routledge: New York, NY, USA, 2012; ISBN 978-0-203-08521-9. [Google Scholar]
- Taherdoost, H. Validity and Reliability of the Research Instrument; How to Test the Validation of a Questionnaire/Survey in a Research. Int. J. Acad. Res. Manag. 2016, 5, 28–36. [Google Scholar] [CrossRef]
- NIST SP 800-207; NIST Zero Trust Architecture. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020.






| Study Title/Authors | Focus Area | Key Contributions | Cybersecurity Approach | Applicability to IoT/Edge Computing | Limitations/Challenges |
|---|---|---|---|---|---|
| NIST Cybersecurity Framework (CSF) | Risk management framework | A structured approach to managing cybersecurity risks. Core functions: Identify, Protect, Detect, Respond, and Recover. | Risk-based methodology, governance structures, continuous monitoring, and incident response. | Applicable to centralized enterprise environments. Limited applicability to decentralized IoT systems. | Assumes centralized control and resource-rich infrastructures, limiting adaptability for IoT. |
| DevSecOps Integration | Security in SDLC | Integrates security practices early in the software development lifecycle (SDLC). Principles include shift-left security, collaboration, and automation. | Continuous integration, automated testing, and security practices embedded in development. | Highly applicable to agile, cloud-native, and dynamic systems, but less focused on strategic risk management. | Focuses on tactical security; may overlook long-term risk management and governance. |
| Cloud Security and Risk Management [33] | Cloud computing security | Proposes a framework for managing cyber risks in cloud computing, integrating ISO and NIST standards. | Risk management, cloud security policies, and compliance with ISO and NIST standards. | Direct applicability to cloud environments, but limited focus on IoT/Edge-specific challenges. | Incomplete integration for decentralized, resource-constrained environments like IoT. |
| Cybersecurity Standards Review [36] | Cybersecurity standards | A review of widely adopted cybersecurity standards and frameworks for selecting the right framework. | Analysis of standards (ISO, NIST, etc.) for securing information systems. | Useful for aligning cybersecurity strategies with organizational needs, but limited focus on IoT/Edge-specific systems. | Does not deeply explore IoT-specific security challenges. |
| Cloud Security Threats and Frameworks [37] | Cloud computing | Explores cloud computing security gaps and presents frameworks for improving security, trust, and data protection. | Reviews ISO and NIST frameworks, focusing on cloud security. | Cloud-based IoT systems can benefit, though IoT-specific risks are not deeply addressed. | Limited focus on decentralized IoT environments, which require different strategies. |
| Integrated Cybersecurity Strategies [22] | Cloud, database, penetration testing | Empirically investigates integrated strategies for cloud security, database protection, and penetration testing. | Combining multiple security strategies to improve resilience against threats. | Applicable to cloud-based IoT, but may not fully address real-time IoT/Edge security needs. | Requires further validation in IoT/Edge contexts. |
| Cloud Security Frameworks Comparison [38] | Cloud security | Compares various frameworks (COBIT5, NIST, ISO, CSA STAR, AWS) for securing cloud infrastructure. | Detailed comparison and recommendations for cloud security frameworks. | Primarily focused on cloud, but frameworks could be adapted to IoT/Edge systems requiring cloud connectivity. | Focus on cloud security, not specific to IoT/Edge environments, which have unique characteristics. |
| SecEdge Framework for IoT [39] | IoT security | Proposes the SecEdge framework for IoT using transformer-based models and federated learning for real-time threat detection. | AI-driven, federated learning, real-time model updates for dynamic IoT environments. | Highly relevant to IoT environments, especially in real-time threat detection and data privacy. | Focused on specific IoT models, may not generalize to all IoT/Edge ecosystems. |
| Comprehensive IoT Security Framework [40] | IoT security | Proposes a framework for mitigating risks like malware, DoS, and MitM in IoT. Emphasizes data privacy and regulatory compliance. | Focus on data integrity, privacy, and regulatory compliance (GDPR, HIPAA). | Direct relevance for securing IoT supply chains and data integrity in IoT environments. | Challenges in ensuring full regulatory compliance across different regions. |
| AI-driven Security for DTNs [41] | Delay-Tolerant Networks (DTNs) | AI-driven security framework combining LSTM, transfer learning, and differential privacy for enhanced detection and privacy. | AI, LSTM, and differential privacy for threat detection and privacy. | Relevant for Edge and IoT systems that require real-time data processing and privacy protection. | Lacks comprehensive scalability for large IoT ecosystems. |
| Phase | Edge Computing | IoT | Outcome |
|---|---|---|---|
| Asset Identification |
|
| Comprehensive asset inventory for risk assessment and compliance |
| Risk Assessment |
|
| Comprehensive risk assessment for Edge Computing and/or IoT environment |
| Requirements |
|
| Clear and comprehensive specifications for secure system development and deployment |
| Collaboration and Integration |
|
| Strengthened collaboration and integration for functionality, compliance, and threat mitigation |
| Phase | Edge Computing | IoT | Outcome |
|---|---|---|---|
| Security Controls |
|
| Robust security posture to protect against cyber threats |
| Data Protection |
|
| Enhanced protection of sensitive data against unauthorized access and loss |
| Phase | Edge Computing | IoT | Outcome |
|---|---|---|---|
| Real-Time Monitoring |
|
| Enhanced visibility of security posture and rapid response to threats |
| Log Management |
|
| Comprehensive log management strategy to enhance security and operational visibility |
| Phase | Edge Computing | IoT | Outcome |
|---|---|---|---|
| Delivery |
|
| Streamlined and secure application delivery process, enhancing deployment efficiency and security throughout lifecycle |
| Log Management |
|
| Comprehensive response and recovery strategy to mitigate security incidents and ensure system resilience |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Reyes-Acosta, R.E.; Mendoza-González, R.; Oswaldo Diaz, E.; Vargas Martin, M.; Luna Rosas, F.J.; Martínez Romo, J.C.; Mendoza-González, A. Cybersecurity Conceptual Framework Applied to Edge Computing and Internet of Things Environments. Electronics 2025, 14, 2109. https://doi.org/10.3390/electronics14112109
Reyes-Acosta RE, Mendoza-González R, Oswaldo Diaz E, Vargas Martin M, Luna Rosas FJ, Martínez Romo JC, Mendoza-González A. Cybersecurity Conceptual Framework Applied to Edge Computing and Internet of Things Environments. Electronics. 2025; 14(11):2109. https://doi.org/10.3390/electronics14112109
Chicago/Turabian StyleReyes-Acosta, Ricardo Emmanuel, Ricardo Mendoza-González, Edgar Oswaldo Diaz, Miguel Vargas Martin, Francisco Javier Luna Rosas, Julio César Martínez Romo, and Alfredo Mendoza-González. 2025. "Cybersecurity Conceptual Framework Applied to Edge Computing and Internet of Things Environments" Electronics 14, no. 11: 2109. https://doi.org/10.3390/electronics14112109
APA StyleReyes-Acosta, R. E., Mendoza-González, R., Oswaldo Diaz, E., Vargas Martin, M., Luna Rosas, F. J., Martínez Romo, J. C., & Mendoza-González, A. (2025). Cybersecurity Conceptual Framework Applied to Edge Computing and Internet of Things Environments. Electronics, 14(11), 2109. https://doi.org/10.3390/electronics14112109









