Leakage Power Attack-Resilient Design: PMOS-Reading 9T SRAM Cell
Abstract
1. Introduction
2. Related Work
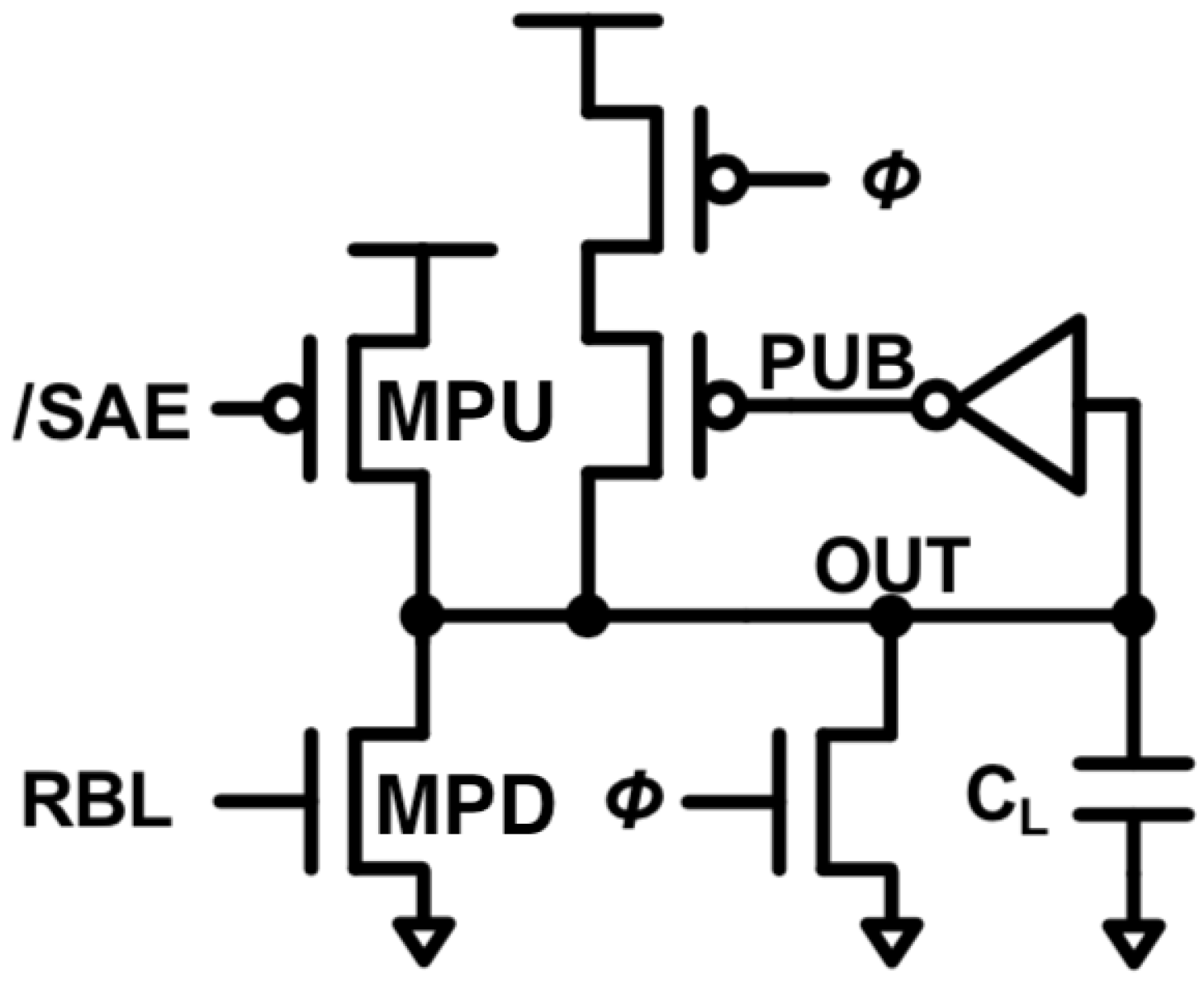
2.1. Comparison with the Conventional 6T Design
2.2. PG9T Leakage Analysis
3. Proposed Work
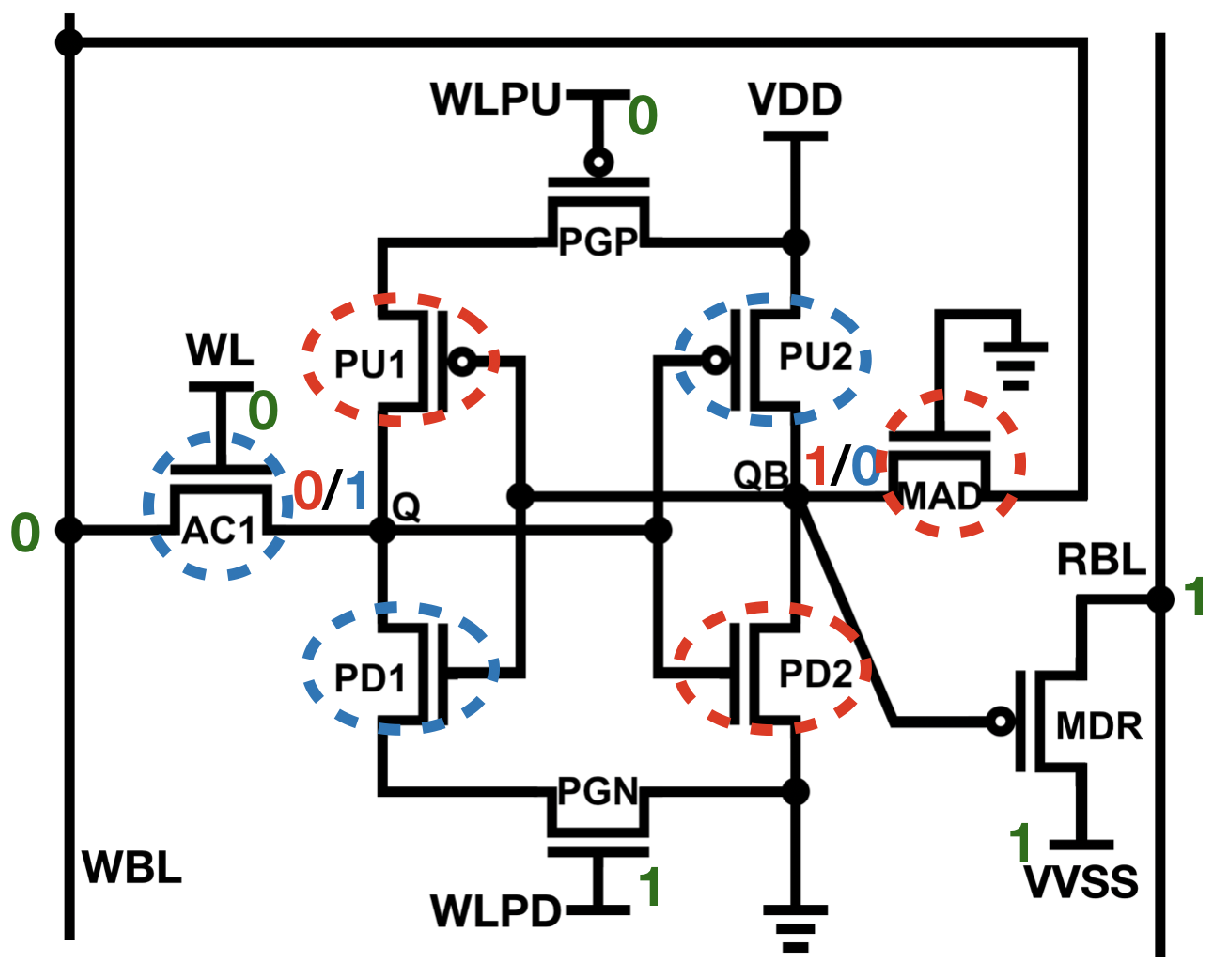
3.1. PMOS-Reading 9T Design
3.2. PR9T Leakage Analysis
4. LPA Attacks
4.1. Algorithm for the LPA Attack Mechanism
| Algorithm 1 Leakage power analysis attack algorithm |
|
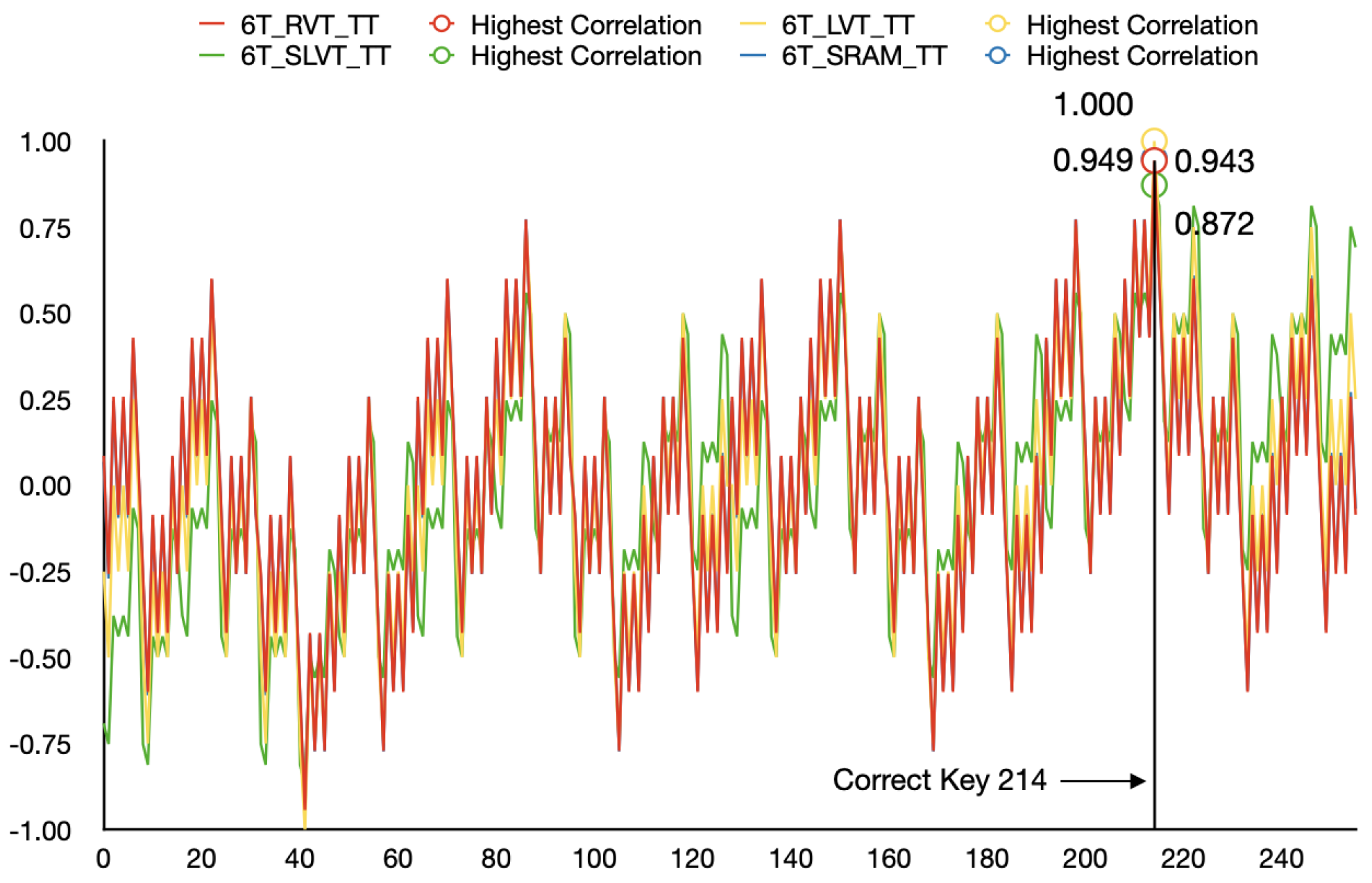
4.2. LPA Attack Results for 6T Cell and PR9T Cell
4.3. Evidence of Resilience against LPA Using Principal Component Analysis
5. Performance Comparison and Discussion
5.1. Dynamic Power Consumption
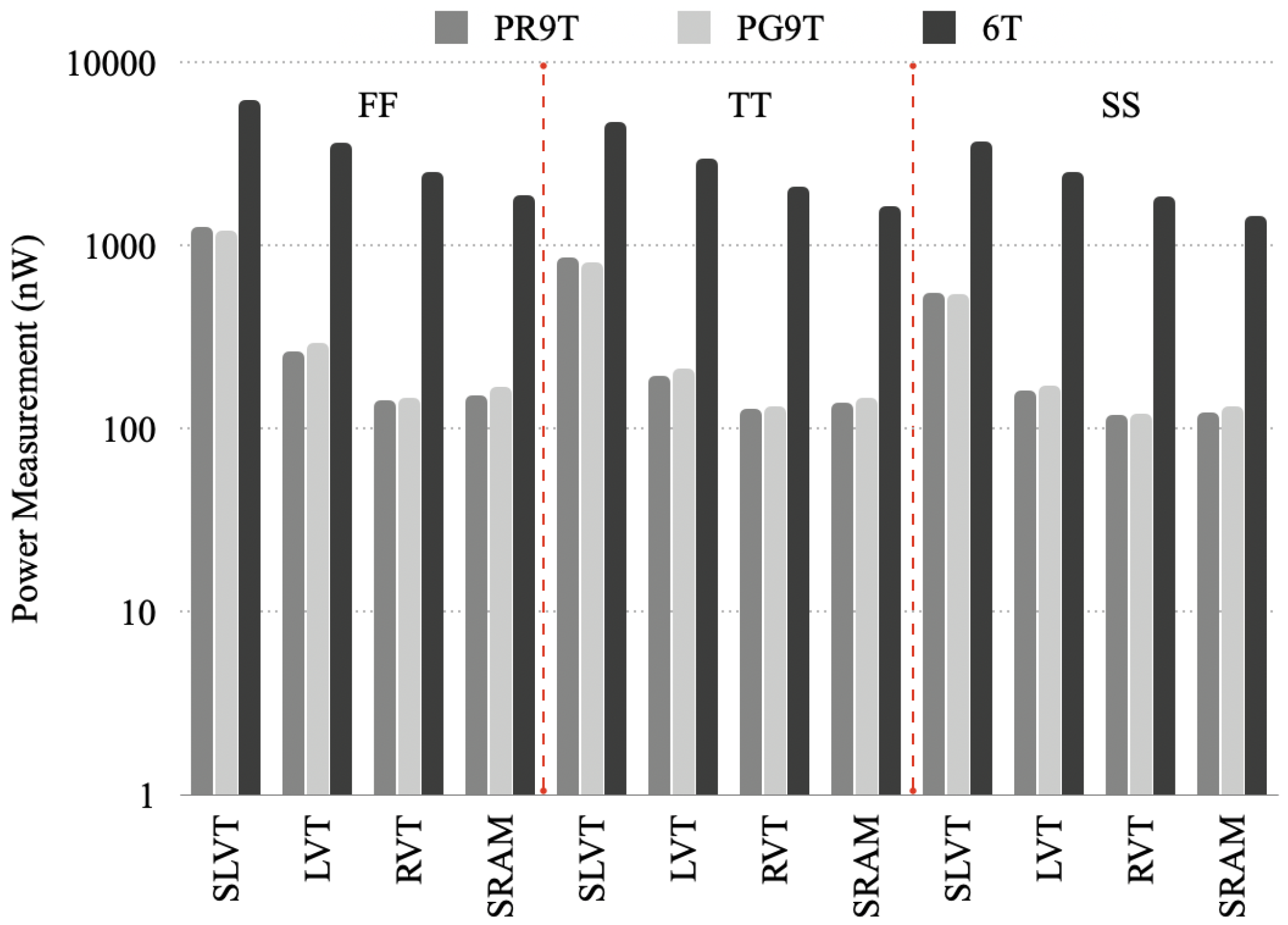
5.2. Static Power Consumption
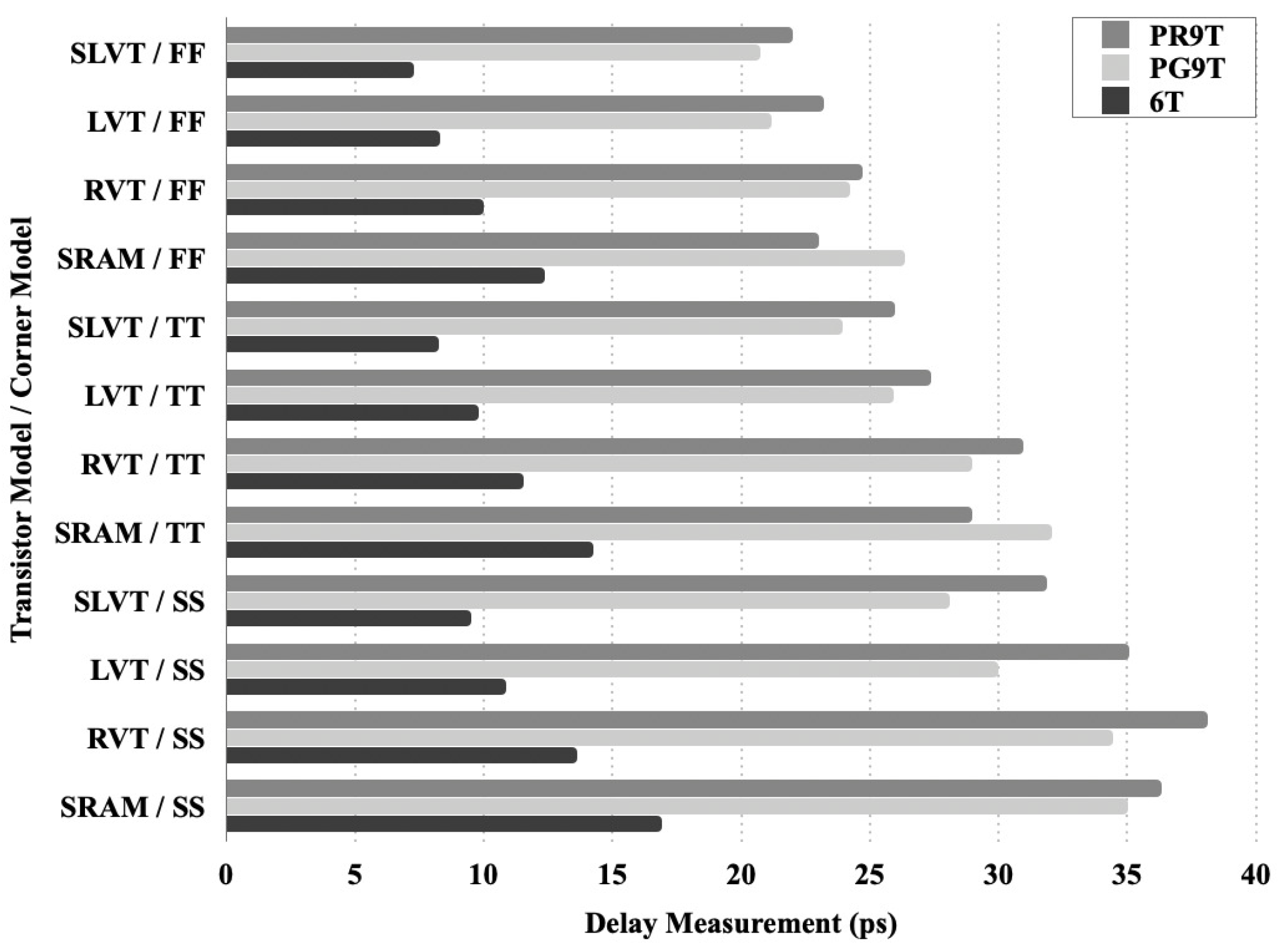
5.3. Delay Performance
5.4. Static Noise Margin
5.5. SRAM Model Process Corner Comparison
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AES | Advanced encryption standard |
| CNN | Convolutional neural network |
| DES | Data encryption standard |
| DL | Deep learning |
| DPA | Differential power attack |
| HSNM | Hold static noise margin |
| LB10T | Leakage balanced 10 transistor |
| LPA | Leakage power analysis |
| LVT | Low-threshold-voltage transistor |
| MLP | Multilayer perceptron |
| PCA | Principal component analysis |
| PG9T | Power-gated nine transistor |
| PR9T | PMOS-reading nine transistor |
| RSNM | Read static noise margin |
| RVT | Regular-threshold-voltage transistor |
| S-box | Substitution box |
| SCA | Side-channel attack |
| SLVT | Super-low-threshold-voltage transistor |
| SNM | Static noise margin |
| SRAM | Static random access memory |
References
- Lerman, L.; Veshchikov, N.; Picek, S.; Markowitch, O. On the Construction of Side-Channel Attack Resilient S-boxes. In Proceedings of the International Workshop on Constructive Side-Channel Analysis and Secure Design, Paris, France, 13–14 April 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 102–119. [Google Scholar]
- Biryukov, A.; De Cannière, C. Data encryption standard (DES). In Encyclopedia of Cryptography and Security; van Tilborg, H.C.A., Ed.; Springer: Boston, MA, USA, 2005; pp. 129–135. [Google Scholar] [CrossRef]
- Dworkin, M.; Barker, E.; Nechvatal, J.; Foti, J.; Bassham, L.; Roback, E.; Dray, J. Advanced Encryption Standard (AES); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2001. [CrossRef]
- Schneier, B. Description of a New Variable-Length Key, 64-bit Block Cipher (Blowfish). In Proceedings of the Fast Software Encryption, Cambridge Security Workshop, Cambridge, UK, 9–11 December 1993; Springer: Berlin/Heidelberg, Germany, 1993; pp. 191–204. [Google Scholar]
- Tiri, K.; Verbauwhede, I. A VLSI design flow for secure side-channel attack resistant ICs. In Proceedings of the Design, Automation and Test in Europe, Munich, Germany, 7–11 March 2005; Volume 3, pp. 58–63. [Google Scholar] [CrossRef]
- Aamir, M.; Sharma, S.; Grover, A. ChaCha20-in-Memory for Side-Channel Resistance in IoT Edge-Node Devices. IEEE Open J. Circuits Syst. 2021, 2, 833–842. [Google Scholar] [CrossRef]
- Tiri, K. Side-Channel Attack Pitfalls. In Proceedings of the 2007 44th ACM/IEEE Design Automation Conference, San Diego, CA, USA, 4–8 June 2007; pp. 15–20. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 1999; Springer: Berlin/Heidelberg, Germany, 1999; pp. 388–397. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B.; Rohatgi, P. Introduction to differential power analysis. J. Cryptogr. Eng. 2011, 1, 5–27. [Google Scholar] [CrossRef]
- Alioto, M.; Giancane, L.; Scotti, G.; Trifiletti, A. Leakage Power Analysis Attacks: A Novel Class of Attacks to Nanometer Cryptographic Circuits. IEEE Trans. Circuits Syst. I Regul. Pap. 2010, 57, 355–367. [Google Scholar] [CrossRef]
- Alioto, M.; Bongiovanni, S.; Djukanovic, M.; Scotti, G.; Trifiletti, A. Effectiveness of Leakage Power Analysis Attacks on DPA-Resistant Logic Styles Under Process Variations. IEEE Trans. Circuits Syst. I Regul. Pap. 2014, 61, 429–442. [Google Scholar] [CrossRef]
- Prasad, G.; Mandi, B.C.; Ramu, P.; Sowrabh, T.V.; Kumar, A.H. Statistical Analysis of 5T SRAM Cell for Low Power and Less Area SRAM Based Cache Memory for IoT Applications. In Proceedings of the 2020 First International Conference on Power, Control and Computing Technologies (ICPC2T), Raipur, India, 3–5 January 2020; pp. 368–372. [Google Scholar] [CrossRef]
- Patt, Y.N.; Patel, S.J.; Evers, M.; Friendly, D.H.; Stark, J. One billion transistors, one uniprocessor, one chip. Computer 1997, 30, 51–57. [Google Scholar] [CrossRef]
- Neve, M.; Peeters, E.; Samyde, D.; Quisquater, J. Memories: A Survey of Their Secure Uses in Smart Cards. In Proceedings of the Second IEEE International Security in Storage Workshop, Washington, DC, USA, 31 October 2003; p. 62. [Google Scholar] [CrossRef]
- Liu, W.; Luo, R.; Yang, H. Cryptography Overhead Evaluation and Analysis for Wireless Sensor Networks. In Proceedings of the 2009 WRI International Conference on Communications and Mobile Computing, Kunming, China, 6–8 January 2009; Volume 3, pp. 496–501. [Google Scholar] [CrossRef]
- Trimberger, S. Security in SRAM FPGAs. IEEE Des. Test Comput. 2007, 24, 581. [Google Scholar] [CrossRef]
- Konur, E.; Ozelci, Y.; Arikan, E.; Eksi, U. Power Analysis Resistant SRAM. In Proceedings of the 2006 World Automation Congress, Budapest, Hungary, 24–26 July 2006; pp. 1–6. [Google Scholar] [CrossRef]
- Rožić, V.; Dehaene, W.; Verbauwhede, I. Design solutions for securing SRAM cell against power analysis. In Proceedings of the 2012 IEEE International Symposium on Hardware-Oriented Security and Trust, San Francisco, CA, USA, 3–4 June 2012; pp. 122–127. [Google Scholar] [CrossRef]
- Giterman, R.; Vicentowski, M.; Levi, I.; Weizman, Y.; Keren, O.; Fish, A. Leakage Power Attack-Resilient Symmetrical 8T SRAM Cell. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2018, 26, 2180–2184. [Google Scholar] [CrossRef]
- Naz, S.F.; Chawla, M.; Shah, A.P. Leakage Power Attack and Half Select Issue Resilient Split 8T SRAM Cell. In Proceedings of the 2023 21st IEEE Interregional NEWCAS Conference (NEWCAS), Edinburgh, UK, 26–28 June 2023; pp. 1–2. [Google Scholar] [CrossRef]
- Weizman, Y.; Giterman, R.; Chertkow, O.; Wicentowski, M.; Levi, I.; Sever, I.; Kehati, I.; Keren, O.; Fish, A. Low-Cost Side-Channel Secure Standard 6T-SRAM-Based Memory with a 1Area and Less Than 5. IEEE Access 2021, 9, 91764–91776. [Google Scholar] [CrossRef]
- Carlson, I.; Andersson, S.; Natarajan, S.; Alvandpour, A. A high density, low leakage, 5T SRAM for embedded caches. In Proceedings of the 30th European Solid-State Circuits Conference, Leuven, Belgium, 23 September 2004; pp. 215–218. [Google Scholar] [CrossRef]
- Kushwah, C.B.; Vishvakarma, S.K. A Single-Ended with Dynamic Feedback Control 8T Subthreshold SRAM Cell. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2016, 24, 373–377. [Google Scholar] [CrossRef]
- Calhoun, B.H.; Chandrakasan, A.P. A 256-kb 65-nm Sub-threshold SRAM Design for Ultra-Low-Voltage Operation. IEEE J.-Solid-State Circuits 2007, 42, 680–688. [Google Scholar] [CrossRef]
- Oh, T.W.; Jeong, H.; Kang, K.; Park, J.; Yang, Y.; Jung, S.O. Power-Gated 9T SRAM Cell for Low-Energy Operation. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2017, 25, 1183–1187. [Google Scholar] [CrossRef]
- Chen, K.; Oruklu, E. Side-Channel Attack Resilient Design of a 10T SRAM Cell in 7nm FinFET Technology. In Proceedings of the 2019 IEEE 62nd International Midwest Symposium on Circuits and Systems (MWSCAS), Dallas, TX, USA, 4–7 August 2019; pp. 860–863. [Google Scholar]
- Clark, L.T.; Vashishtha, V.; Shifren, L.; Gujja, A.; Sinha, S.; Cline, B.; Ramamurthy, C.; Yeric, G. ASAP7: A 7-nm finFET predictive process design kit. Microelectron. J. 2016, 53, 105–115. [Google Scholar] [CrossRef]
- Park, J.; Jeong, H.; Jung, S. Pulsed PMOS sense amplifier for high speed single-ended SRAM. In Proceedings of the 2018 International Conference on Electronics, Information, and Communication (ICEIC), Honolulu, HI, USA, 24–27 January 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Qin, H.; Cao, Y.; Markovic, D.; Vladimirescu, A.; Rabaey, J. SRAM leakage suppression by minimizing standby supply voltage. In Proceedings of the International Symposium on Signals, Circuits and Systems. Proceedings, SCS 2003. (Cat. No.03EX720), San Jose, CA, USA, 22–24 March 2004; pp. 55–60. [Google Scholar]
- Maghrebi, H.; Portigliatti, T.; Prouff, E. Breaking Cryptographic Implementations Using Deep Learning Techniques. In Proceedings of the Security, Privacy, and Applied Cryptography Engineering, Hyderabad, India, 14–18 December 2016; Carlet, C., Hasan, M.A., Saraswat, V., Eds.; Springer: Cham, Switzerland, 2016; pp. 3–26. [Google Scholar]
- Benadjila, R.; Prouff, E.; Strullu, R.; Cagli, E.; Dumas, C. Deep learning for side-channel analysis and introduction to ASCAD database. J. Cryptogr. Eng. 2020, 10, 163–188. [Google Scholar] [CrossRef]
- Timon, B. Non-Profiled Deep Learning-based Side-Channel attacks with Sensitivity Analysis. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2019, 2019, 107–131. [Google Scholar] [CrossRef]













| Type | Corner | SRAM | RVT | LVT | SLVT |
|---|---|---|---|---|---|
| NMOS | FF | 0.28 | 0.20 | 0.13 | 0.07 |
| TT | 0.27 | 0.19 | 0.12 | 0.06 | |
| SS | 0.26 | 0.18 | 0.11 | 0.05 | |
| PMOS | FF | −0.23 | −0.20 | −0.14 | −0.08 |
| TT | −0.22 | −0.19 | −0.13 | −0.07 | |
| SS | −0.21 | −0.18 | −0.12 | −0.06 |
| Layout | Written | Corner | Threshold Selection | |||
|---|---|---|---|---|---|---|
| SLVT | LVT | RVT | SRAM | |||
| Pre-layout | 0 | FF | 1.002 | 1.002 | 0.917 | 0.810 |
| TT | 1.002 | 0.999 | 0.873 | 0.885 | ||
| SS | 1.002 | 0.995 | 0.932 | 0.815 | ||
| 1 | FF | 1.358 | 1.369 | 1.225 | 1.107 | |
| TT | 1.297 | 1.307 | 1.180 | 1.099 | ||
| SS | 1.208 | 1.206 | 1.115 | 1.097 | ||
| Post-layout | 0 | FF | 1.003 | 0.996 | 0.939 | 0.734 |
| TT | 1.002 | 0.998 | 0.930 | 0.797 | ||
| SS | 1.002 | 0.995 | 0.966 | 0.798 | ||
| 1 | FF | 1.340 | 1.347 | 1.224 | 0.999 | |
| TT | 1.284 | 1.293 | 1.179 | 0.978 | ||
| SS | 1.190 | 1.199 | 1.121 | 1.261 | ||
| Layout | Written | Corner | Threshold Selection | |||
|---|---|---|---|---|---|---|
| SLVT | LVT | RVT | SRAM | |||
| Pre-layout | 0 | FF | 1.001 | 0.991 | 0.900 | 0.729 |
| TT | 1.001 | 0.990 | 0.893 | 0.751 | ||
| SS | 1.001 | 0.988 | 0.880 | 0.735 | ||
| 1 | FF | 1.165 | 1.153 | 1.011 | 0.866 | |
| TT | 1.152 | 1.140 | 1.000 | 0.867 | ||
| SS | 1.128 | 1.114 | 0.971 | 0.867 | ||
| Post-layout | 0 | FF | 1.001 | 0.992 | 0.905 | 0.594 |
| TT | 1.001 | 0.991 | 0.902 | 0.599 | ||
| SS | 1.001 | 0.990 | 0.888 | 0.650 | ||
| 1 | FF | 1.154 | 1.142 | 1.015 | 0.739 | |
| TT | 1.143 | 1.132 | 1.003 | 0.747 | ||
| SS | 1.123 | 1.109 | 0.979 | 0.783 | ||
| Layout | Written | Corner | Threshold Selection | |||
|---|---|---|---|---|---|---|
| SLVT | LVT | RVT | SRAM | |||
| Pre-layout | 0 | FF | 1.000 | 1.000 | 1.000 | 0.909 |
| TT | 1.000 | 1.000 | 1.001 | 0.900 | ||
| SS | 1.000 | 1.000 | 1.001 | 0.932 | ||
| 1 | FF | 1.000 | 1.000 | 1.000 | 0.936 | |
| TT | 1.000 | 1.000 | 1.000 | 0.938 | ||
| SS | 1.000 | 1.000 | 1.000 | 0.938 | ||
| Post-layout | 0 | FF | 1.000 | 1.000 | 1.000 | 0.952 |
| TT | 1.000 | 1.000 | 0.989 | 0.869 | ||
| SS | 1.000 | 1.000 | 0.977 | 0.929 | ||
| 1 | FF | 1.000 | 1.000 | 0.999 | 0.970 | |
| TT | 1.000 | 1.000 | 1.000 | 0.970 | ||
| SS | 1.000 | 1.000 | 1.000 | 0.970 | ||
| Layout | Written | Corner | Threshold Selection | |||
|---|---|---|---|---|---|---|
| SLVT | LVT | RVT | SRAM | |||
| Pre-layout | 0 | FF | 1.000 | 1.000 | 1.000 | 0.864 |
| TT | 1.000 | 1.000 | 1.000 | 0.862 | ||
| SS | 1.000 | 1.000 | 1.000 | 0.861 | ||
| 1 | FF | 1.000 | 1.000 | 1.000 | 0.911 | |
| TT | 1.000 | 1.000 | 1.000 | 0.913 | ||
| SS | 1.000 | 1.000 | 1.000 | 0.913 | ||
| Post-layout | 0 | FF | 1.000 | 0.997 | 0.969 | 0.871 |
| TT | 0.999 | 0.996 | 0.985 | 0.837 | ||
| SS | 0.999 | 0.993 | 0.972 | 0.886 | ||
| 1 | FF | 1.000 | 1.000 | 0.996 | 0.938 | |
| TT | 1.000 | 0.999 | 0.995 | 0.942 | ||
| SS | 1.000 | 0.999 | 1.004 | 0.945 | ||
| Corner | Device Type | |||
|---|---|---|---|---|
| SLVT | LVT | RVT | SRAM | |
| FF | ||||
| TT | ||||
| SS | ||||
| Parameter | PR9T | PG9T | 6T |
|---|---|---|---|
| Leakage power (Storing 0) (pW) | 86.72 | 82.00 | 105.1 |
| Leakage power (Storing 1) (pW) | 89.44 | 82.06 | 100.0 |
| Dynamic power (nW) | 158.2 | 146.4 | 520.8 |
| Delay (write 0) (ps) | 23.54 | 32.58 | 20.00 |
| Delay (write 1) (ps) | 50.29 | 112.2 | 53.48 |
| Delay (read) (ps) | 23.03 | 26.35 | 12.37 |
| HSNM (mV) | 337.6 | 337.6 | 337.4 |
| RSNM (mV) | 337.6 | 337.6 | 176.7 |
| Parameter | PR9T | PG9T | 6T |
|---|---|---|---|
| Leakage power (Storing 0) (pW) | 61.67 | 57.67 | 73.76 |
| Leakage power (Storing 1) (pW) | 63.57 | 58.99 | 70.48 |
| Dynamic power (nW) | 145.4 | 129.9 | 438.7 |
| Delay (write 0) (ps) | 28.25 | 38.55 | 21.23 |
| Delay (write 1) (ps) | 64.77 | 139.0 | 57.53 |
| Delay (read) (ps) | 29.00 | 32.06 | 14.27 |
| HSNM (mV) | 308.6 | 308.6 | 308.4 |
| RSNM (mV) | 308.6 | 308.6 | 164.4 |
| Metrics | PR9T | PG9T | 6T |
|---|---|---|---|
| Leakage power (Storing 0) (pW) | 45.45 | 42.88 | 54.54 |
| Leakage power (Storing 1) (pW) | 45.87 | 34.01 | 51.93 |
| Dynamic power (nW) | 133.7 | 121.1 | 393.8 |
| Delay (write 0) (ps) | 33.68 | 43.22 | 24.07 |
| Delay (write 1) (ps) | 88.39 | 187.9 | 65.88 |
| Delay (read) (ps) | 36.32 | 35.01 | 16.90 |
| HSNM (mV) | 267.2 | 267.2 | 266.5 |
| RSNM (mV) | 267.2 | 267.2 | 143.8 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, M.; Balasubramanian, P.; Chen, K.; Oruklu, E. Leakage Power Attack-Resilient Design: PMOS-Reading 9T SRAM Cell. Electronics 2024, 13, 2551. https://doi.org/10.3390/electronics13132551
Yang M, Balasubramanian P, Chen K, Oruklu E. Leakage Power Attack-Resilient Design: PMOS-Reading 9T SRAM Cell. Electronics. 2024; 13(13):2551. https://doi.org/10.3390/electronics13132551
Chicago/Turabian StyleYang, Muyu, Prakash Balasubramanian, Kangqi Chen, and Erdal Oruklu. 2024. "Leakage Power Attack-Resilient Design: PMOS-Reading 9T SRAM Cell" Electronics 13, no. 13: 2551. https://doi.org/10.3390/electronics13132551
APA StyleYang, M., Balasubramanian, P., Chen, K., & Oruklu, E. (2024). Leakage Power Attack-Resilient Design: PMOS-Reading 9T SRAM Cell. Electronics, 13(13), 2551. https://doi.org/10.3390/electronics13132551






