Abstract
With the widespread adoption of blockchain technology, its public ledger characteristic enhances transaction transparency but also amplifies the risk of privacy breaches. Attackers can infer users’ real identities and behaviors by analyzing public transaction patterns and address relationships, posing a severe threat to users’ privacy and security, and thus hindering further advancements in blockchain applications. To address this challenge, covert communication has emerged as an effective strategy for safeguarding the privacy of blockchain users and preventing information leakage. But existing blockchain-based covert communication schemes rely solely on the immutability of blockchain itself for robustness and suffer from low transmission efficiency. To tackle these issues, this paper proposes a stealthy communication model with blockchain smart contract for bidding systems. The model initiates by preprocessing sensitive information using a secret-sharing algorithm-the Shamir (t, n) threshold scheme-and subsequently embeds this information into bidding amounts, facilitating the covert transfer of sensitive data. We implemented and deployed this model on the Ethereum platform and conducted comprehensive performance evaluations. To assess the stealthiness of our approach, we employed a suite of statistical tests including the CDF, the Kolmogorov–Smirnov test, Welch’s t-test and K–L divergence. These analyses confirmed that amounts carrying concealed information were statistically indistinguishable from regular transactions, thus validating the effectiveness of our solution in maintaining the anonymity and confidentiality of information transmission within the blockchain ecosystem.
1. Introduction
Blockchain technology is revolutionizing various fields such as financial transactions, smart contracts, and supply chain management with its decentralization, transparency, and immutability [1,2]. Despite offering a highly secure distributed ledger, the public nature of the blockchain ledger also raises privacy concerns. Although users’ identities and transaction information are encrypted, the increasing amount of blockchain data makes de-anonymization attacks possible [3]. Attackers can infer users’ real identities and transaction behaviors by analyzing public transaction patterns and address relationships, thus threatening users’ privacy and security. This also limits the widespread application of blockchain technology in scenarios with higher privacy requirements [4].
The most straightforward method of privacy protection is to upload encrypted information to the blockchain, which can only be decrypted by nodes holding the key [5,6,7]. However, this solution somewhat contradicts the fundamental principles of blockchain, as it is a distributed database whose blocks must be mutually recognized and maintained. Another approach to solving this issue is to introduce a mixing system service, which conceals the relationship between incoming and outgoing transactions by switching between different users’ transactions. However, we cannot be sure whether the transaction information is recorded by the service provider, leading to potential privacy leaks [8].
Covert communication [9,10,11], as a technology for transmitting covert information within normal communication, provides a new strategy for addressing privacy protection issues in blockchain [12,13]. By establishing covert channels within the blockchain network, it is possible to protect the privacy of sensitive information without sacrificing the system’s transparency. This method allows users to transmit encrypted information through covert channels during blockchain transactions, thereby protecting user privacy and defending against de-anonymization attacks without drawing attention from outsiders.
Current research focuses on blockchain-based storage covert channels. Common carriers of blockchain-based covert storage channels are special fields for on-chain transactions, including the coinbase transaction of Bitcoin [14,15], custom storage fields [16,17,18], input/output addresses [19,20,21], and digital signatures [22,23,24]. However, these fields often exhibit distinct formats and characteristics [25], leading to noticeable discrepancies between fields containing secret information and normal ones, which in turn diminishes the stealthiness of the model. Furthermore, the robustness of previous blockchain-based covert channel models often relies solely on the blockchain’s inherent immutability, and they have low channel capacity.
To address this issue, this paper proposes a stealthy communication model with blockchain smart contract for bidding systems. This mechanism embeds certain sensitive information in the blockchain, such as transaction content and identities of the transacting parties, into the transaction amounts for transmission and storage, thus preventing attackers from obtaining and analyzing it. At the same time, we use secret-sharing to preprocess sensitive information, enhancing the robustness and transmission efficiency of the scheme. Additionally, another advantage of this method is that it does not require extensive modifications to the underlying architecture of the blockchain system. It simply adds a layer of covert communication mechanisms on top of the existing system, making it highly practical and feasible. Our contributions can be summarized as follows.
- A stealthy communication model with blockchain smart contract for bidding systems is proposed, which can effectively reduce the risk of blockchain privacy leakage.
- The proposed scheme uses the secret-sharing algorithm to enhance the robustness of the system and supports the adjustment of transmission parameters to ensure the transmission performance.
- The experimental results show that by adjusting the transmission index of the proposed scheme, the concealment, robustness, and channel capacity can be taken into account, and the availability and effectiveness of the scheme are effectively improved.
The structure of this paper is as follows. In Section 2, we introduce the relevant background knowledge of smart contracts. In Section 3, the stealthy communication model with blockchain smart contract for bidding systems proposed and its design goals are introduced. In Section 4, we will introduce the details of the model and algorithm. In Section 5, we will perform implementation and experimental evaluation on the proposed scheme. In Section 6, we review the related research on blockchain-based covert channels. Finally, we summarize the content of this paper and put forward the prospect in Section 7.
2. Preliminaries
The concept of smart contracts was first proposed by Nick Szabo in 1996 and is defined as ‘computerized trading agreements that enforce contract terms’. It is designed to meet common contract conditions and reduce the need for trusted third parties [26]. However, due to the technical limitations and lack of awareness at that time, smart contracts were not widely used, and the emergence of blockchain technology in 2008 provided a feasible solution for smart contracts. With its invariance, decentralization, and traceability, the blockchain provides a trusted execution environment for smart contracts [27]. Ethereum discovered the possibility of combining blockchain with smart contracts and established a set of specifications and frameworks for smart contracts in the white book ‘A next-generation smart contract and decentralized application platform’ [28], which greatly promoted the development of smart contracts. The covert channel proposed in this paper is based on the smart contract of Ethereum platform. Therefore, the following will introduce in detail the process of building and participating in smart contracts on the Ethereum platform.
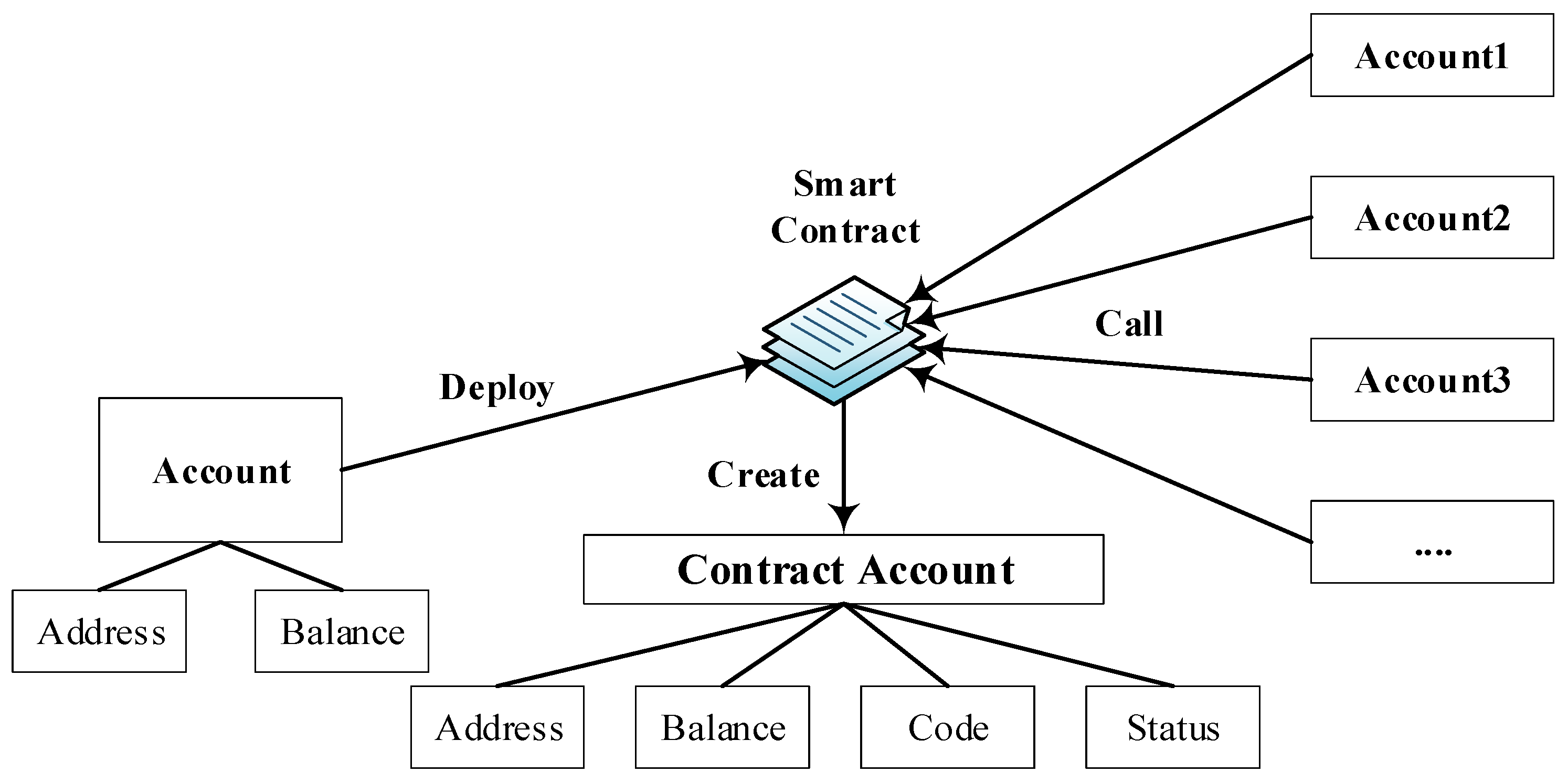
As shown in the Figure 1, the user first creates a personal account for their Ethereum wallet, which is generated based on public key encryption and includes the user’s address and balance. Then the user deploys the compiled smart contract code to the blockchain, and the contract account is generated after the contract is successfully deployed, which includes the contract address, balance, status, and code. Other personal accounts can invoke the smart contract on the chain through the contract address, save/take Ether to the contract, or change the contract status according to the code.
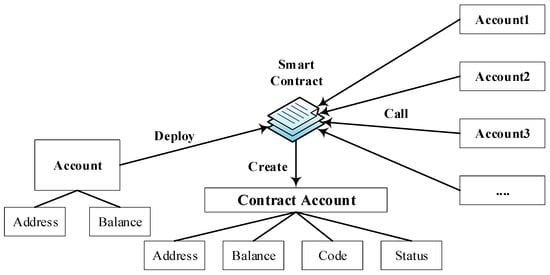
Figure 1.
Deployment and call of smart contracts: select an Ethereum wallet to create an account and utilize a suitable smart contract platform and programming language to write the smart contract code. Once the code is prepared, compile it into a bytecode executable on the blockchain and deploy it onto the chain. Thereafter, other accounts can invoke the smart contract on-chain to conduct transactions or perform additional operations.
The blockchain smart contract is only a computer code stored on the blockchain and is automatically executed when the predetermined terms and conditions are met. Therefore, its execution does not require manual intervention, and it can be executed only if the specified conditions are satisfied. Under the premise that our scheme strictly abides by the Ethereum rules, transactions executed according to the logic of smart contract code can be written to blocks normally, so it is feasible to construct covert channels based on blockchain smart contracts.
3. System Design
In this section, we introduce the system model, the threat model, and the design goals of our proposed models.
3.1. System Model
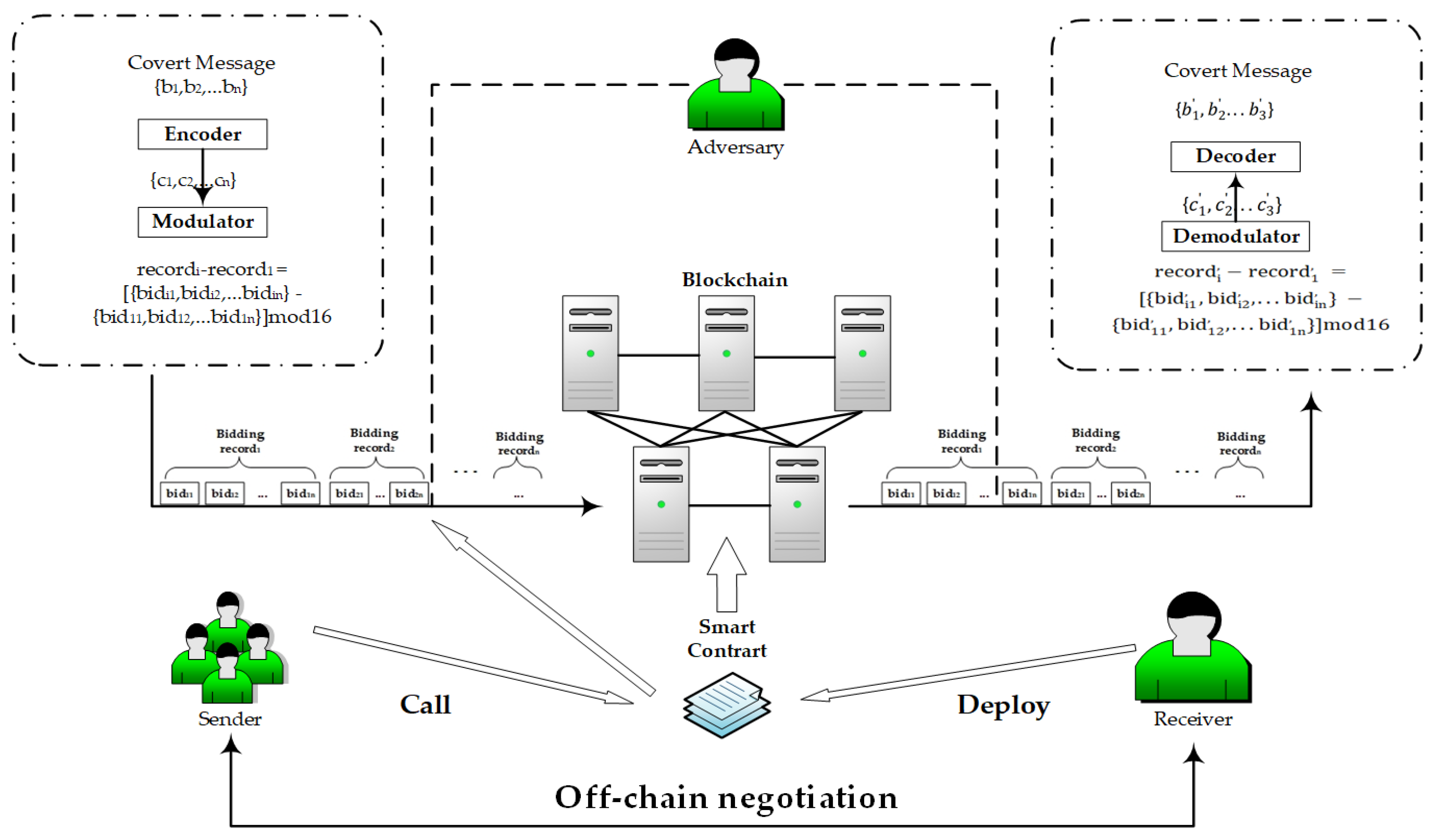
This section introduces the stealthy communication model with blockchain smart contract for bidding systems proposed in this paper. Figure 2 shows the system model of the proposed scheme.
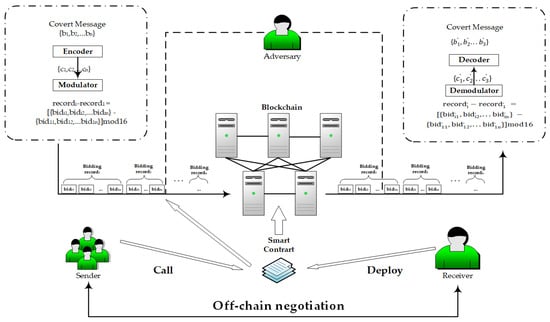
Figure 2.
System model of stealthy communication model with blockchain smart contract for bidding systems: 1. sender: data processing, contract call; 2. receiver: contract deployment, information extraction; 3. adversary: data analysis, termination of contract calls.
As shown in Figure 2, the complete stealthy communication process can be divided into the following parts:
- Off-chain negotiation: The sender and the receiver complete the information pre-negotiation out of chain. It can be achieved through other means of communication between mobile devices, e-mails, and other communicators. The off-chain negotiation information may include the receiver’s wallet address, hidden information coding rules, embedding location, and mode selection.
- Contract generation and deployment: The communication receiver creates and deploys the contract by using off-chain negotiation. For example, the parameters used to embed secret information, the number of parameters and the chain where the deployment is located. Once confirmed by the miners, the contract will be formally deployed to the blockchain and cannot be tampered with. The smart contract after successful deployment will be recorded in the ‘contract pool’ of the contract creator (receiver). According to the information processing and transmission rules in the covert channel model, the sender can call the corresponding smart contract in the ‘contract pool’ to transmit secret information.
- Covert information preprocessing: The sender first encrypts or encodes the data T to be transmitted according to the results of the off-chain negotiation, so that the processed information T′ meets the requirements of the embedded format, thereby improving the confidentiality and availability of the information.
- Information transmission: The sender calls the contract in the receiver’s ‘contract pool’ and embeds the processed secret information into the contract parameters in a specified order. When the smart contract is invoked, the receiver can view the corresponding parameters in the transaction.
- Information extraction: The information receiver, that is, the creator of the contract, obtains the address information and the corresponding parameters according to the record, from which the sender sends the T′ in advance.
- Information restoration: The receiver decodes and decrypts the extracted T′ according to the rules to obtain the initial secret information.
3.2. Threat Model
We assume that there is an adversary with strong monitoring and data analysis capabilities in the blockchain network. The adversary can monitor and analyze the contracts and data in the blockchain network to detect stealthy communication. Therefore, it is easy for adversaries to obtain the characteristics of blockchain transactions. At the same time, the adversary will use statistical methods to detect transactions. After detecting the covert channel, it can prohibit the invocation of its related contracts. In the evaluation, we will also use these techniques to evaluate the invisibility of our scheme.
3.3. Design Goals
In this section, we introduce the design goals of the proposed stealthy communication model with blockchain smart contract for bidding systems, including high concealment, strong robustness, and high channel capacity.
- High concealment: Concealment means that the adversary cannot distinguish between covert information and normal information and cannot detect covert channels. In the model proposed in this paper, concealment means that the threat model cannot distinguish between normal transactions and transactions containing hidden information.
- Strong robustness: Robustness refers to the receiver’s ability to correctly recover covert information. In the process of covert information transmission, information errors or loss may occur due to network delay or human interference. Covert channels require strong robustness to accurately transmit covert information and resist interference.
- High channel capacity: Channel capacity refers to the number of covert information transmitted per unit time in covert channel. Covert channels require high channel capacity to meet the requirements of transmitting a large amount of covert information.
4. Proposed Scheme
In this section, we will show the pseudo-code and process descriptions of all algorithms used in proposed scheme.
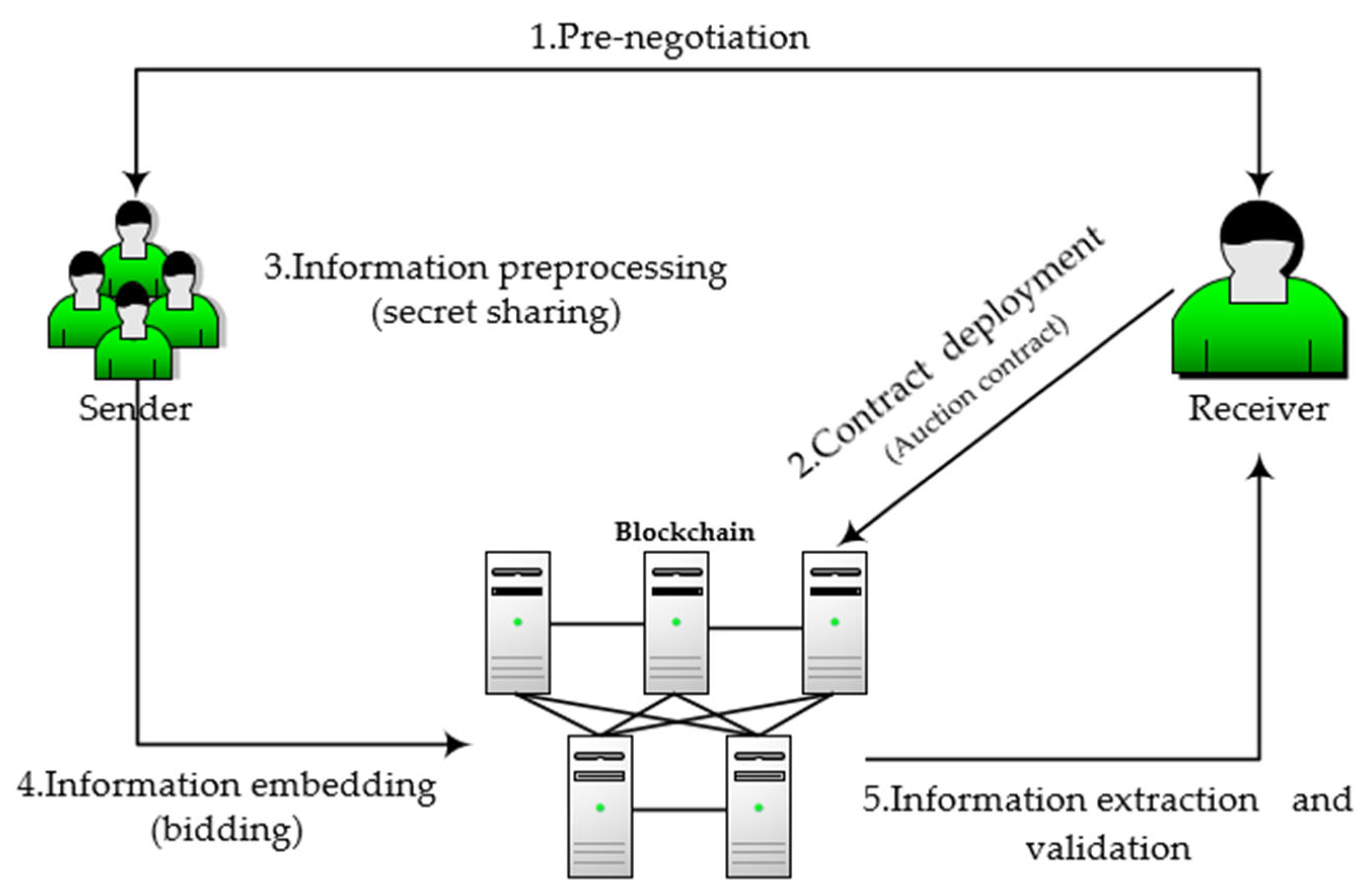
In our proposed scheme, a complete covert communication process includes five steps, as shown in Figure 3. The sender and the receiver need to pre-negotiate, and then the sender needs to deploy the smart contract to the chain to facilitate the transmission of hidden information. The sender preprocesses the information and then embeds it into the blockchain transaction that invokes the smart contract. The receiver extracts the hidden information through the transaction log and verifies it. The detailed process will be shown in Section 4.2, Section 4.3, Section 4.4, Section 4.5 and Section 4.6 of this chapter.
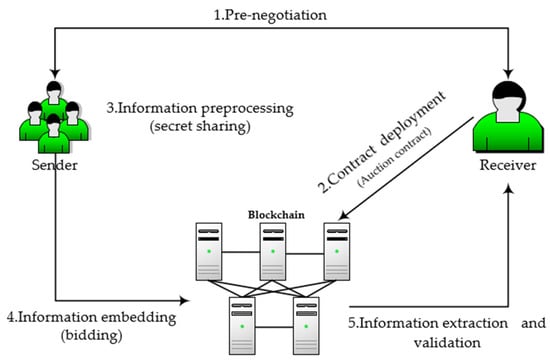
Figure 3.
Implementation steps of system model: 1. Pre-negotiation. 2. Contract deployment (Auction contract). 3. Information preprocessing (secret-sharing). 4. Information embedding (bidding). 5. Information extraction and validation.
4.1. Symbol
The symbols used in this work are shown in Table 1. The algorithms and processes also use the same symbols, unless otherwise explicitly mentioned.

Table 1.
The Main Symbols.
4.2. Pre-Negotiate
Both communicating parties pre-agree on the information processing method and share necessary parameters: the large prime number p, the random variable seed k, and the address of the contract deployer. These parameters are transmitted through an off-chain communication channel [29]. Additionally, to facilitate effective filtering of covert transactions, the sender, when establishing the covert channel, should inform the receiver of the sender’s address for the first covert transaction. This address can subsequently be used to determine whether a given auction contains hidden information or not.
4.3. Contract Deployment
The receiver generates the smart bidding contract (such as ERC20 token) in batches according to the pre-negotiation results and then deploys the contract to the main network of Ethereum. After success, it will be stored in the receiver’s ‘contract pool’.
4.4. Information Preprocessing
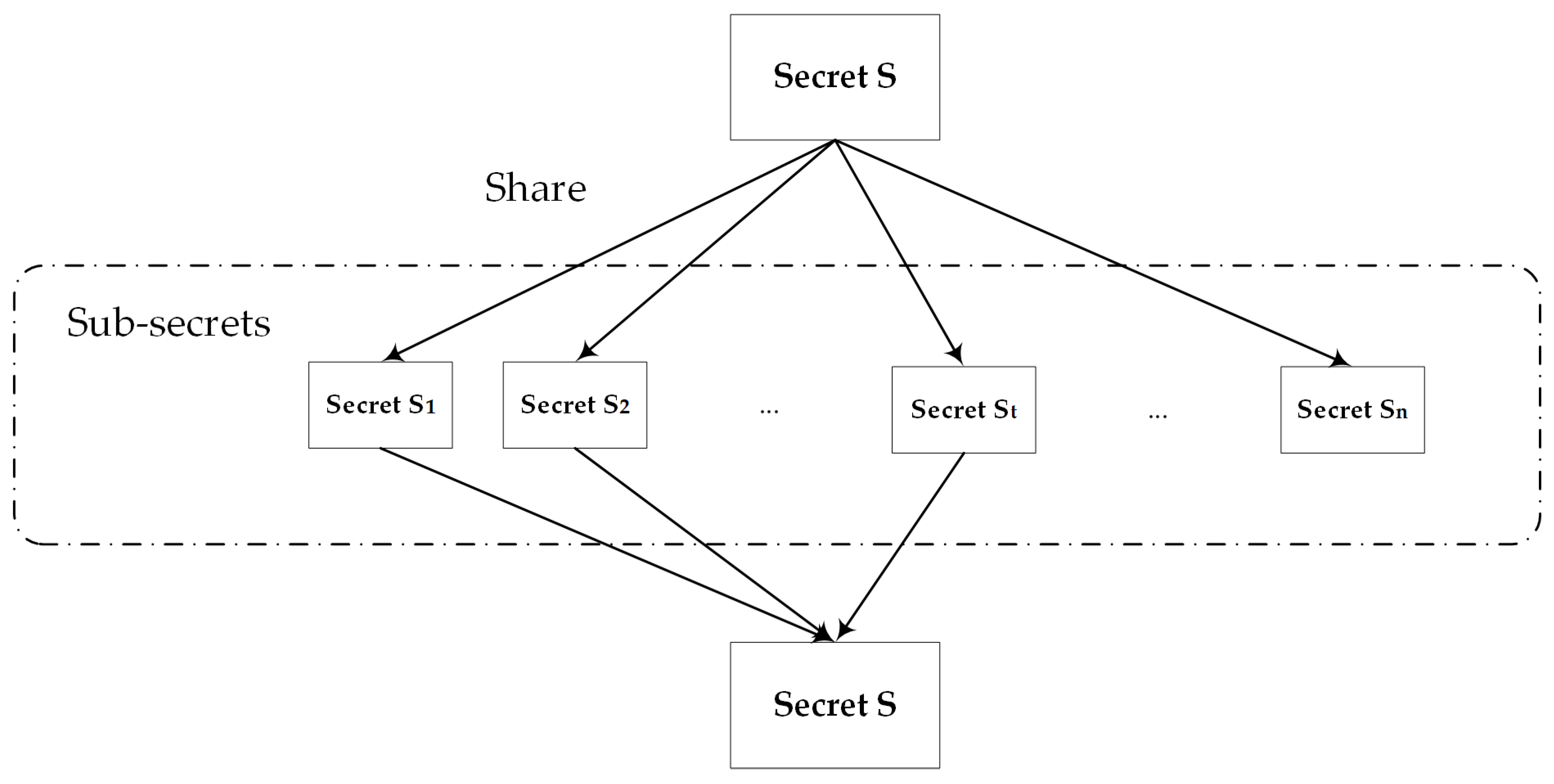
The sender uses the secret-sharing [30] algorithm to process the secret information S. Secret-sharing allows the secret owner to share the secret S to n participants, so that any t secret shares are sufficient to reconstruct S, and any fewer than t − 1 secret shares cannot know any information of S. That is, the equality (1) is satisfied.
This technology can build a robust key management mechanism for the cryptosystem; even if a disaster destroys half of the information or only a part of the security is destroyed, it can still operate safely and reliably. Figure 4 shows the secret-sharing process.
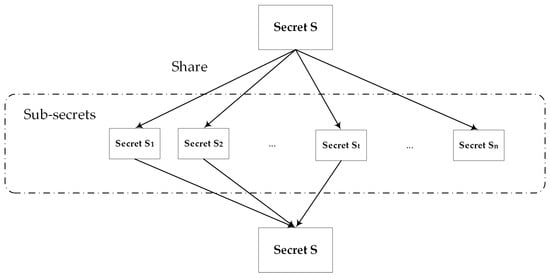
Figure 4.
The sharing and reconstruction process of secret-sharing: 1. The secret S is divided into n sub-secrets, with each piece being held by a different participant. 2. Upon acquiring t of these sub-secrets, the original secret S can be reconstructed.
In this paper, the secret-sharing module selects the most classic and widely used Shamir secret-sharing algorithm [31]. The Shamir (t, n) threshold scheme divides the secret into n parts and gives them to n participants, respectively, by constructing a t − 1 polynomial and taking the secret to be shared as a constant term of the polynomial, so that t participants can jointly recover the secret, but fewer than t participants cannot obtain any information from the shared secret.
As shown in Algorithm 1, the sender selects the covert information S to be shared, recovers the threshold t and the number of sub-secrets n, and randomly generates a large enough prime number p (p > s). The sender first converts the secret information S into a digital form s and then constructs a random k − 1 degree polynomial:
in which a0 = s, ai (1 ≤ i ≤ t − 1) is a random number less than p. The sub-secret si is generated by the following formula:
in which xi is the token number of the auction.
| Algorithm 1: Information preprocessing |
| input: covert information S, the number of sub-secrets n, threshold t, large prime number p, random variable seeds k, selected token ID xi output: sub-secrets [ ] s = string_to_int (S); init sub-secrets = [ ], i = 1; random.seed (k); while i < t do ai = random(1,p − 1) i++ end I = 1 while i < n + 1 do sub-secrets [i] = s + i++ end return sub-secrets [ ] |
4.5. Information Embedding
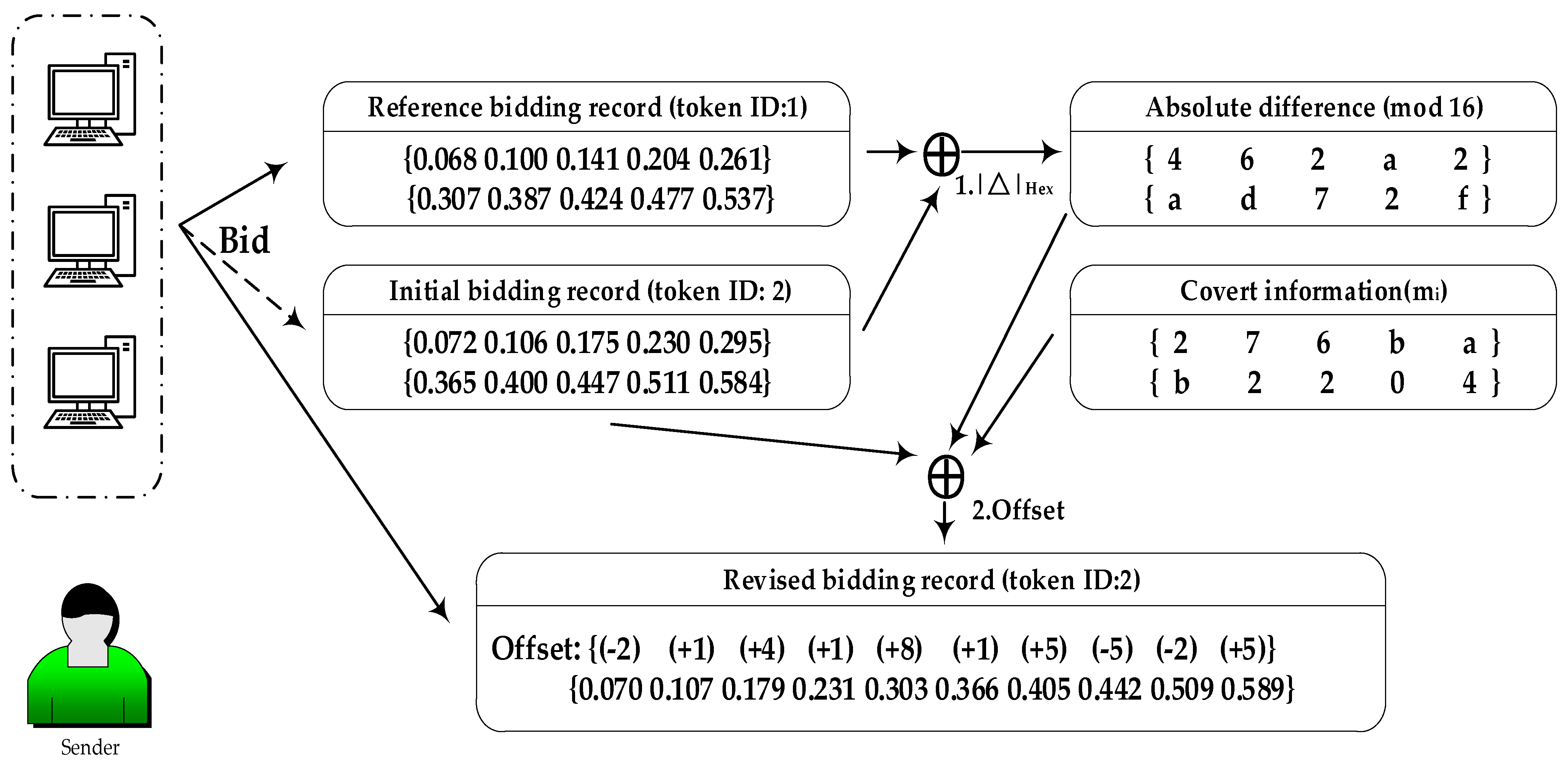
Since the processed sub-secrets si are in numerical form, they can be directly utilized within the auction contract. However, embedding information directly into the auction amounts would inevitably disrupt the original distribution of these amounts, compromising the stealthiness of the model. To address this, we employ a replay modification of previous bidding records and then utilize the differences in bids to embed the information, striving to maintain the original distribution intact. Research indicates that the vast majority of Ethereum transaction amounts fall within the range of 0 to 1 ether. To reduce the cost of auction bids, we select decimal places 2 to 3 (i.e., the hundredths to thousandths place) as the carriers for information. Therefore, the maximum number of bits that can be embedded in a bidding is 6.
The format of the share is . The token ID of the auction is utilized to convey the number xi. Next, the difference between the two bidding amounts is calculated, followed by taking the remainder of this difference divided by 2e, in which e is the number of bits embedded. This remainder is then used in conjunction with the secret message mi to compute Offset. Finally, this Offset is added to the initial bidding amount, yielding the final bidding amount for submission. The specific calculation process is shown in the following formula:
Taking e = 4 as an example, (2276bab2204) is the share to be transmitted; the corresponding process for embedding information is illustrated in Figure 5.
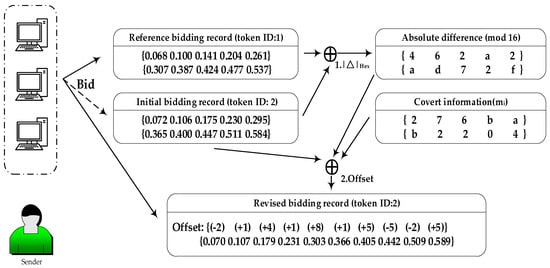
Figure 5.
Information embedding: 1. After taking the difference between the initial bidding record and the reference bidding record, then taking that result modulo 16 to obtain . 2. The result of subtracting from the secret message mi is then plugged into Formula (6) to derive the offset. This offset is subsequently applied to the initial bidding record, yielding the revised bidding record.
In this process, the sender can use multiple wallets to participate in the auction, reduce the number of repeated bids for an object at the same address, and effectively improve the concealment of information transmission. At the same time, the sender can participate in other auction contracts to further improve information redundancy.
4.6. Information Extraction and Validation
After determining the smart contract containing covert information, the receiver first restores the sub-secret si and its corresponding xi, then calculate s through Formula (7) and finally restore the hidden information S through Formula (8).
Finally calculates the hash value of S to verify the authenticity of the covert information.
5. System Implementation and Evaluation
In this section, the implementation details of the system will be elaborated on, along with pertinent performance evaluation.
5.1. Implementation
This paper opts to conduct experiments on the Sepolia testnet, which is currently one of the most widely-used Ethereum test networks and is recommended by the Ethereum core team. It is a vital component of the blockchain ecosystem, simulating the working environment of the main network. It enables application testing without impacting the blockchain, serving as a sandbox for testing blockchain applications. The successful execution of experiments on the testnet further validates the feasibility of our proposed scheme.
During experimentation, the sender transmits covert information by manipulating the bid amounts in the auction. Specifically, the contract deployer utilizes Remix to batch compile and deploy the smart bidding contracts onto the Sepolia testnet. The sender initiates by invoking a contract as a reference bidding contract for normal bidding, where the hash value of the information can be placed in the memo field. Subsequently, based on the sub-secret, the corresponding token’s smart bidding contract is selected, and bids embedded with secret information are transmitted sequentially. These transmissions can be parallelized according to the threshold value of the secret-sharing algorithm. The receiver, guided by the pre-agreed criteria, filters out the smart contracts containing covert information, extracts the secret information from the transaction logs of these contracts and then restores the original message. Lastly, the hash value of the restored message is compared with the received one to further authenticate the integrity of the transmitted information.
5.2. Tamper Resistance and System Security
The data in the blockchain are distributed across multiple nodes in the network rather than being centrally stored on a single server, making any attempt to tamper with the data require simultaneously changing data on at least 51% of the nodes in the network [32]. When there are only a few nodes in the network, attackers can easily compromise more than half of the blockchain nodes without expending significant resources, resulting in lower security for the blockchain. However, as the number of network nodes continues to increase, the security of the blockchain gradually improves. Currently, the scale of the blockchain is massive, with a large and continuously increasing number of nodes in the network, making it practically impossible to tamper with blockchain data in practice.
In addition, the data in blockchain are linked together in the form of blocks, with each block encrypted using a hashing algorithm and then stored in the next block. This structure ensures that if data in a block are tampered with, their hash value will change, disrupting the continuity of the entire chain, which can be immediately detected, thereby making blockchain data tamper-proof [33]. Therefore, once the special transaction created by the sender is deployed to the chain, its hidden information cannot be tampered with.
At the same time, Ethereum, the platform which the scheme is based on, divides the blockchain network into multiple fragments by implementing sharding technology. Each fragment can independently process transactions and smart contracts, thereby improving the throughput of the overall network, thereby alleviating the congestion control problem of the blockchain. Ethereum’s consensus algorithm shifts from proof of work (PoW) to proof of stake (PoS) and other more efficient algorithms. These algorithms can effectively defend against sybil attacks and collusion attacks.
5.3. Concealment
The scheme selects 1000 bidding records as normal records and uses a set of these normal bids as reference bidding records. Then, random numbers are generated according to the number of bits embedded e as the embedded content. Utilizing the above-described information embedding method, the normal records are modified, yielding altered bidding records. Subsequently, evaluation will be conducted to assess whether those datasets (the original and the modified ones) are statistically indistinguishable.
Cumulative distribution function (CDF), the Kolmogorov–Smirnov (K–S) test, Welch’s t-test and K–L divergence [34,35,36,37] are employed to evaluate the concealment of the proposed scheme.
CDF is an integral of the probability density function, which can completely describe the probability distribution of a real random variable. It is defined as follows:
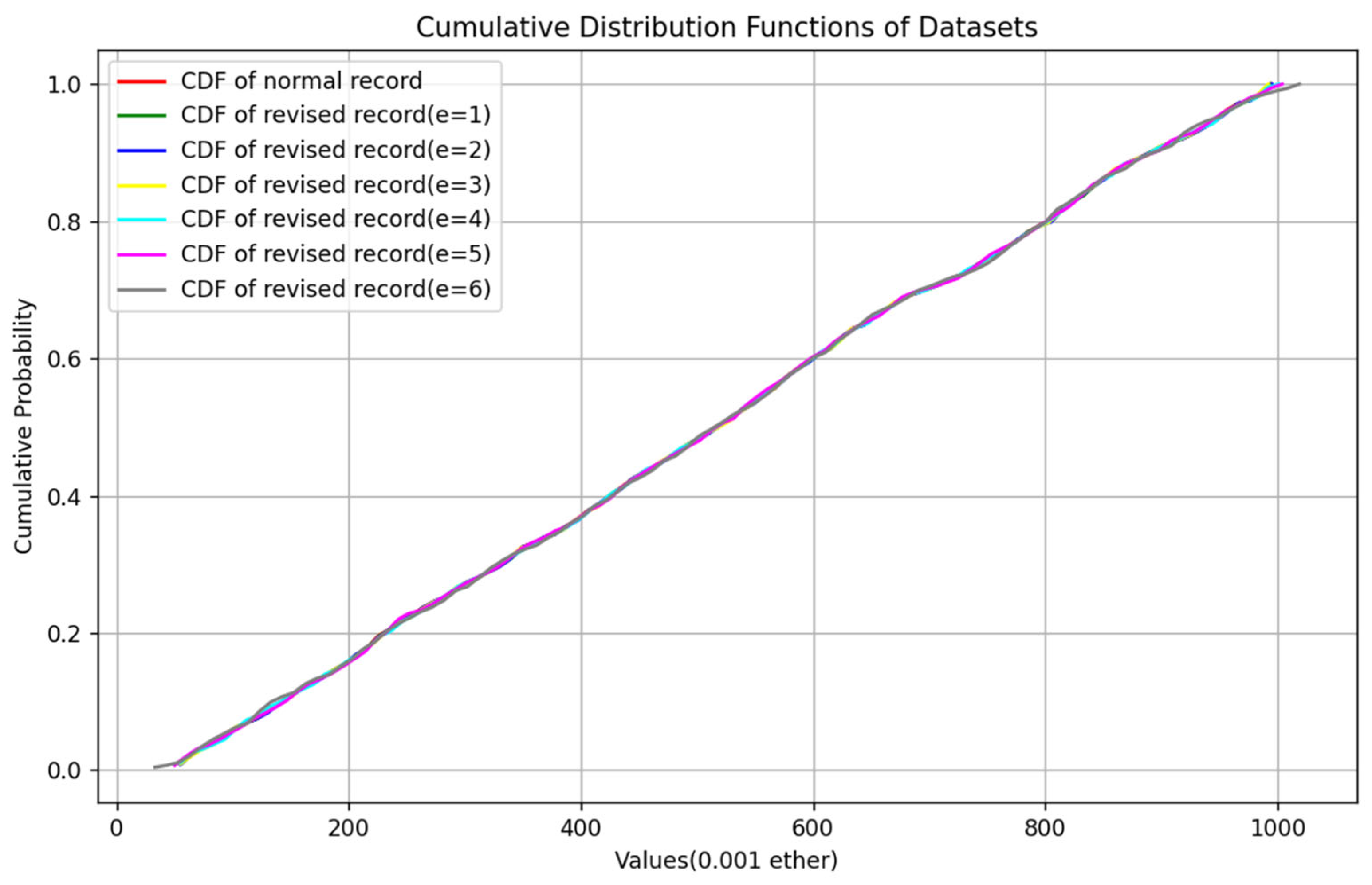
where X is a random variable and x represents all real numbers. By comparing the similarity of the cumulative distribution function of the amount of the normal bidding record and revised bidding record, we can intuitively see whether they are indistinguishable. Figure 6 shows their CDF function curves.
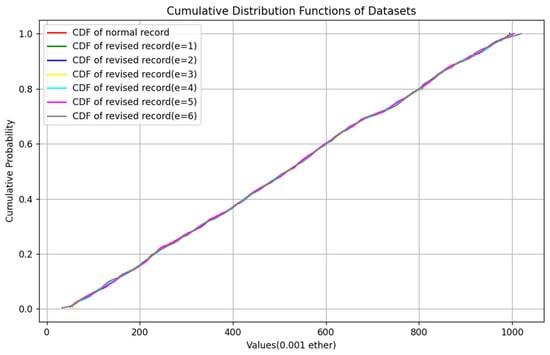
Figure 6.
CDF function curves of normal bidding record and revised bidding record (e = 1–6).
The K–S test is based on the difference of the cumulative distribution function. Calculating the K–S index measures whether the observed data satisfy a theoretical distribution or the degree of deviation between the two sample distributions and makes a statistical inference accordingly. Welch’s t-test is a statistical hypothesis testing method used to compare the means of two independent samples, particularly when the variances of the two populations are unequal or unknown. It serves as an improvement over the classic independent samples t-test, which assumes that both samples come from normal distributions with equal variances. By relaxing the assumption of equal variances, Welch’s t-test provides a more robust analysis, reducing the risk of incorrect conclusions due to unequal variability in the groups being compared.
In general, we use the K–S test and Welch’s t-test p value to determine whether there is a difference in the distribution of the two samples. When the p value is greater than 0.05, it means that the two samples have the same distribution. The experimental results are shown in Table 2.

Table 2.
The p value of K–S test and Welch’s t-test.
We also use K–L divergence to measure the bidding amount distribution before and after modification. It is a tool to measure the difference between two probability distributions. It is widely used in model evaluation, optimization and comparison in machine learning, especially in supervised learning, unsupervised learning and reinforcement learning. The smaller the value of K–L divergence is, the closer the two distributions are. The larger the value, the greater the difference between the two distributions. The K–L divergence results are shown in Table 3.

Table 3.
The K–L divergence of different values of e.
The results in the table show that the proposed scheme has good concealment. However, during the experimental process, we observed that when the number of bits embedded was set to 5 or 6, there were instances where the size order of two adjacent bids within the same record would inversely change after modification, rendering the bids invalid for use. Consequently, in subsequent text, we opt for e = 4 to conduct the channel capacity test.
In addition, compared with the previous covert communication model using bidding contracts [38], the concealment of the scheme has been greatly improved, because in the previous scheme, the users directly embed secret information into the bidding amount, without considering the possible original distribution of the bidding amount.
5.4. Robustness
The robustness referred to in this paper denotes the capability to recover the original secret information even when some of the shares sent by the sender are lost or damaged. Previous blockchain-based covert channel schemes primarily relied on the tamper-resistant nature of blockchain technology to ensure robustness; however, this reliance is inherently limited. Encountering malicious miners who refuse to include specific transactions in blocks or manipulate transactions during the packaging process could jeopardize the accurate recovery of confidential information. In contrast, our proposed scheme not only harnesses the inherent immutability of blockchain but also integrates an efficient data preprocessing mechanism—the secret-sharing algorithm—thereby furnishing an additional layer of assurance for the system’s robustness. This ensures that information remains reliably recoverable even amidst such potential disruptions [39].
The secret-sharing scheme fragments a secret into n parts, mandating at least t parts for the reconstruction of the original secret. This design enables the system to withstand a certain degree of share loss or compromise. Even if n t shares are inaccessible, the secret can still be retrieved by combining the remaining t shares. This fault tolerance mechanism bolsters the system’s robustness, ensuring secure storage and retrieval of secrets. Specifically, this paper employs Shamir’s (t, n) threshold scheme, which theoretically guarantees accurate recovery of secret information as long as the loss rate is below (n − t)/n.
5.5. Channel Capacity
We use the transmission efficiency to describe the channel capacity [40]. Transmission efficiency refers to the amount of covert information transmitted per unit time in bit/s. Its definition is shown in (10).
in which len(message) is the number of bits of covert information transmitted in unit time T, and T is the length of time.
Under Ethereum’s current consensus algorithm (proof of work), the target block time is approximately every 12 s for a new block to be generated, although the actual block time may fluctuate [41]. However, with the evolution and upgrades of Ethereum technology, its block generation speed may be further reduced.
Senders have to wait for the previous transaction to be uploaded onto the chain before conducting the next information embedding. Therefore, the same bidding contract can only embed information once within a single block time. However, by leveraging the secret-sharing scheme, it is possible to participate in t separate smart bidding contracts within one block time, thereby increasing the throughput of information embedding. Thus, the channel capacity of the proposed scheme in this paper is approximately 4t/12 ≈ 0.33t bit/s. The transaction fee for a single bidding is approximately 0.00005 ETH, which converts to approximately 0.194 USD, so the cost of scheme is 0.0485 USD/bit. Table 4 compares the capacity and cost of the scheme with other blockchain-based covert channels.

Table 4.
Comparison of transmission efficiency.
Based on security requirements, the threshold t in our scheme is set to be greater than 1. However, a higher t value implies that a larger number of participants must collaborate to recover the secret, enhancing security but also complicating the secret restoration process. When t = 2, our scheme’s channel capacity surpasses that of existing blockchain-based covert storage channels. Further, with t equal to 3, the capacity reaches up to 1 bit/s, which is what most of the current blockchain-based covert storage channel schemes cannot achieve.
6. Related Works
Partala [19] was the first to propose a blockchain-based covert channel (BLOCCE), demonstrating its security and feasibility. BLOCCE employs the least significant bit (LSB) of addresses to store a single bit of covert information. However, since each address can only transmit one bit of data, it takes a lot of computing costs to generate the address.
Fionov [24] directly encoded hidden information as transaction output or address, but the output generated in this way cannot be used, and the bitcoin in the transaction will not be able to enter the market circulation again, affecting the healthy development of bitcoin. Another scheme discussed in the article conceals information within auxiliary factors used in the construction of signature algorithms. Computing these cofactors entails solving the elliptic curve discrete logarithm problem, which is considered unfeasible. However, the recipient of the hidden information, in possession of the private key, can readily extract the cofactor from the signature through computation.
Zhang [38] developed voting contracts and bidding contracts, leveraging calls from different accounts to transmit secret information directly via contract parameters. The scheme also employs cryptographic algorithms and a dual-round protocol to ensure data privacy. It further tailors information embedding and transmission methodologies to suit various scenarios, thereby enhancing the adaptability and versatility of the covert communication system.
Liu [42] proposed a hash-based multiple-bit embedding (hash-based MBE) scheme that embeds secret data and obfuscation data within the VALUE field of Ethereum transactions. The length of the VALUE field is determined based on historical statistical data of typical Ethereum transactions. Given that the VALUE field contains both secret and obfuscation data, the latter serves to confuse potential attackers. Prior to establishing the covert channel, the sender and receiver agree upon a mixing hash root, which dictates the positions of meaningful bits within the VALUE field of each transaction. This approach leverages the complexity introduced by the combination of genuine transactional data and deliberately inserted noise to enhance the concealment of the covert communication.
7. Conclusions and Future Work
This paper presents a stealthy communication model with blockchain smart contract for bidding systems, addressing privacy leakage issues in blockchain by embedding secret information into transaction parameters. By utilizing the difference in bidding amounts within smart auction contracts as a mapping for secret information sequences and transmitting information via contract invocations, our approach prevents data privacy leaks that arise from public transparency. The distributed storage and chained structure of blockchain enhance the immutability of information. Incorporating secret-sharing algorithms improves the robustness and transmission efficiency of the scheme. Experimental results demonstrate that the distribution of modified bidding records is indistinguishable from that of normal records, highlighting the enhanced robustness and high channel capacity of the proposed model. Consequently, the proposed mechanism ensures secure transmission of secret information at an acceptable cost, confirming the feasibility of employing this mechanism for conveying confidential information. For example, in business transactions, some information (such as contract details, transaction terms, etc.) need to be confidential. After negotiation, both parties can use the model to transmit private data on the public blockchain, protect the business secrets of the enterprise, avoid the snooping of competitors or unrelated parties, and ensure that the information is permanently retained and cannot be tampered with.
Looking ahead, we intend to investigate consolidating multiple bids within the same smart contract, with the dual aim of enhancing the transmission efficiency of our solution and reducing the cost per bit. This approach would facilitate faster data transmission, mitigate the risk of data interception during transmission, and make the technology more affordable for a broader range of organizations and individuals. Consequently, it is anticipated to elevate the overall level of data privacy protection within blockchain ecosystems.
Author Contributions
Conceptualization, Q.L., C.L. (Chen Liang), N.S. and Y.-a.T.; methodology, Q.L., C.L. (Chen Liang) and Y.-a.T.; validation, C.L. (Chen Liang), N.S. and C.L. (Chunying Li); formal analysis, N.S. and C.L. (Chunying Li); writing—original draft preparation, Q.L.; writing—review and editing, C.L. (Chen Liang), N.S., Y.-a.T. and C.L. (Chunying Li); supervision, C.L. (Chen Liang), N.S. and Y.-a.T.; project administration, C.L. (Chen Liang), Y.-a.T. and C.L. (Chunying Li); funding acquisition, C.L. (Chen Liang) and C.L. (Chunying Li). All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by R&D Program of Beijing Municipal Education Commission (KM202311232013), and the Key Field Special Project of Ordinary Universities in Guangdong Province (No. 2023ZDZX1009).
Data Availability Statement
Data is contained within the article .
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Peng, K. Security challenges and opportunities for smart contracts in Internet of things: A survey. IEEE Internet Things J. 2021, 8, 12004–12020. [Google Scholar] [CrossRef]
- Zhang, Q.; Li, Y.; Wang, R.; Liu, L.; Tan, Y.-A.; Hu, J. Data security sharing model based on privacy protection for blockchain-enabled industrial Internet of Things. Int. J. Intell. Syst. 2021, 36, 94–111. [Google Scholar] [CrossRef]
- Bhushan, B.; Sharma, N. Transaction privacy preservations for blockchain technology. In Proceedings of the International Conference on Innovative Computing and Communications, Delhi, India, 21–23 February 2020; Springer: Singapore, 2020; pp. 377–393. [Google Scholar]
- Chen, Y.; Chen, H.; Zhang, Y.; Han, M.; Siddula, M.; Cai, Z. A survey on blockchain systems: Attacks, defenses, and privacy preservation. High-Confid. Comput. 2022, 2, 100048. [Google Scholar] [CrossRef]
- Zheng, J.; Tan, Y.A.; Zhang, Q.; Zhang, X.; Zhu, L.; Zhang, Q. Cross-cluster asymmetric group key agreement for wireless sensor networks. Sci. China Inf. Sci. 2018, 61, 048103:1–048103:3. [Google Scholar] [CrossRef]
- Zhu, H.; Tan, Y.-a.; Zhu, L.; Wang, X.; Zhang, Q.; Li, Y. An Identity-Based Anti-Quantum Privacy-Preserving Blind Authentication in Wireless Sensor Networks. Sensors 2018, 18, 1663. [Google Scholar] [CrossRef] [PubMed]
- Sun, H.; Tan, Y.-A.; Zhu, L.; Zhang, Q.; Li, Y.; Wu, S. A fine-grained and traceable multidomain secure data-sharing model for intelligent terminals in edge-cloud collaboration scenarios. Int. J. Intell. Syst. 2022, 37, 2543–2566. [Google Scholar] [CrossRef]
- Tiwari, R.; Sharma, N.; Kaushik, I.; Tiwari, A.; Bhushan, B. Evolution of IoT & Data Analytics using Deep Learning. In Proceedings of the 2019 International Conference on Computing, Communication, and Intelligent Systems (ICCCIS), Greater Noida, India, 18–19 October 2019; pp. 418–423. [Google Scholar]
- Liang, C.; Tan, Y.-A.; Zhang, X.; Wang, X.; Zheng, J.; Zhang, Q. Building packet length covert channel over mobile VoIP traffics. J. Netw. Comput. Appl. 2018, 118, 144–153. [Google Scholar] [CrossRef]
- Tan, Y.-A.; Zhang, X.; Sharif, K.; Liang, C.; Zhang, Q.; Li, Y. Covert Timing Channels for IoT over Mobile Networks. IEEE Wirel. Commun. 2018, 25, 38–44. [Google Scholar] [CrossRef]
- Tan, Y.-A.; Xu, X.; Liang, C.; Zhang, X.; Zhang, Q.; Li, Y. An end-to-end covert channel via packet dropout for mobile networks. Int. J. Distrib. Sens. Netw. 2018, 14, 1550147718779568. [Google Scholar] [CrossRef]
- Chen, Z.; Zhu, L.; Jiang, P.; Zhang, C.; Gao, F.; He, J.; Xu, D.; Zhang, Y. Blockchain meets covert communication: A survey. IEEE Commun. Surv. Tutor. 2023, 24, 2163–2192. [Google Scholar] [CrossRef]
- Zhang, T.; Wu, Q.; Wang, Q.; Han, T.; Li, B.; Zhu, Y. Covert communication via blockchain: Hiding patterns and communication patterns. Comput. Stand. Interfaces 2024, 90, 103851. [Google Scholar] [CrossRef]
- Matzutt, R.; Hiller, J.; Henze, M.; Ziegeldorf, J.H.; Mullmann, D.; Hohlfeld, O.; Wehrle, K. A quantitative analysis of the impact of arbitrary blockchain content on bitcoin. In Proceedings of the Financial Cryptography and Data Security (FC), Nieuwpoort, The Netherlands, 7 December 2018; pp. 420–438. [Google Scholar]
- Matzutt, R.; Hohlfeld, O.; Henze, M.; Rawiel, R.; Ziegeldorf, J.H.; Wehrle, K. Poster: I don’t want that content! on the risks of exploiting bitcoin’s blockchain as a content store. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24 October 2016; pp. 1769–1771. [Google Scholar]
- Ali, S.T.; McCorry, P.; Lee, P.H.-J.; Hao, F. ZombieCoin: Powering next-generation botnets with bitcoin. In Proceedings of the Financial Cryptography and Data Security (FC), San Juan, Puerto Rico, 5 September 2015; pp. 34–48. [Google Scholar]
- Franzoni, F.; Abellan, I.; Daza, V. Leveraging bitcoin testnet for bidirectional botnet command and control systems. In Proceedings of the Financial Cryptography and Data Security (FC), Kota Kinabalu, Sabah, Malaysia, 10 February 2020; pp. 3–19. [Google Scholar]
- Gao, F.; Zhu, L.; Gai, K.; Zhang, C.; Liu, S. Achieving a covert channel over an open blockchain network. IEEE Netw. 2020, 34, 6–13. [Google Scholar] [CrossRef]
- Partala, J. Provably secure covert communication on blockchain. Cryptography 2018, 2, 18. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, Z.; Wang, W.; Waqas, R.; Zhao, C.; Kim, S.; Chen, H.L. A covert communication method using special bitcoin addresses generated by vanitygen. Comput. Mater. Contin. 2020, 65, 597–616. [Google Scholar]
- Wang, W.; Su, C. CCBRSN: A system with high embedding capacity for covert communication in bitcoin. ICT Syst. Secur. Priv. Prot. 2020, 580, 324–337. [Google Scholar]
- Ali, S.T.; McCorry, P.; Lee, P.H.-J.; Hao, F. Zombiecoin 2.0: Managing next-generation botnets using bitcoin. Int. J. Inf. Secur. 2018, 17, 411–422. [Google Scholar] [CrossRef]
- Alsalami, N.; Zhang, B. Uncontrolled randomness in blockchains: Covert bulletin board for illicit activity. In Proceedings of the 2020 IEEE/ACM 28th International Symposium on Quality of Service (IWQoS), Hangzhou, China, 15–17 June 2020; pp. 1–10. [Google Scholar]
- Fionov, A. Exploring covert channels in bitcoin transactions. In Proceedings of the 2019 International Multi-Conference on Engineering, Computer and Information Sciences (SIBIRCON), Novosibirsk, Russia, 21–27 October 2019; pp. 59–64. [Google Scholar]
- Bartoletti, M.; Pompianu, L. An Analysis of Bitcoin OP_RETURN Metadata. In Proceedings of the Financial Cryptography and Data Security (FC), Sliema, Malta, 19 November 2017; pp. 218–230. [Google Scholar]
- Szabo, N. Smart Contracts: Building Blocks for Digital Markets. EXTROPY J. Transhumanist Thought 1996, 18, 28. [Google Scholar]
- Hewa, T.M.; Ylianttila, M.; Liyanage, M. Survey on blockchain based smart contracts: Applications, opportunities and challenges. J. Netw. Comput. Appl. 2021, 177, 102857. [Google Scholar] [CrossRef]
- Buterin, V. Ethereum White Paper: A Next Generation Smart Contract & Decentralized Application Platform. White Pap. 2014, 3, 2. [Google Scholar]
- Barradas, D.; Santos, N.; Rodrigues, L.; Nunes, V. Poking a hole in the wall: Efficient censorship-resistant internet communications by parasitizing on WebRTC. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, 9–13 November 2020; pp. 35–48. [Google Scholar]
- Chattopadhyay, A.K.; Saha, S.; Nag, A.; Nandi, S. Secret sharing: A comprehensive survey, taxonomy and applications. Comput. Sci. Rev. 2024, 51, 100608. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Li, F.; Zhao, H.; Li, Z. Research on the progress in cross-chain technology of blockchains. J. Softw. 2019, 30, 1649–1660. [Google Scholar]
- Bhutta, M.N.M.; Khwaja, A.A.; Nadeem, A.; Ahmad, H.F.; Khan, M.K.; Hanif, M.A.; Song, H.B. A survey on blockchain technology: Evolution architecture and security. IEEE Access 2021, 9, 61048–61073. [Google Scholar] [CrossRef]
- Zhang, X.; Liang, C.; Zhang, Q.; Li, Y.; Zheng, J.; Tan, Y.-A. Building covert timing channels by packet rearrangement over mobile networks. Inf. Sci. 2018, 445, 66–78. [Google Scholar] [CrossRef]
- Zhang, X.; Zhu, L.; Wang, X.; Zhang, C.; Zhu, H.; Tan, Y.-A. A packetreordering covert channel over VOLTE voice and video traffics. J. Netw. Comput. Appl. 2019, 126, 29–38. [Google Scholar] [CrossRef]
- Shen, T.; Zhu, L.; Gao, F.; Chen, Z.; Zhang, Z.; Li, M. A Blockchain-Enabled Group Covert Channel against Transaction Forgery. Mathematics 2024, 12, 251. [Google Scholar] [CrossRef]
- Liang, C.; Baker, T.; Li, Y.; Nawaz, R.; Tan, Y.-A. Building Covert Timing Channel of the IoT-Enabled MTS Based on Multi-Stage Verification. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2578–2595. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, Z.; Wang, W.; Jin, Z.; Su, Y.; Chen, H. Research on a Covert Communication Model Realized by Using Smart Contracts in Blockchain Environment. IEEE Syst. J. 2022, 16, 2822–2833. [Google Scholar] [CrossRef]
- Fehr, S.; Yuan, C. Robust Secret Sharing with Almost Optimal Share Size and Security Against Rushing Adversaries. In Proceedings of the 18th International Conference on Theory of Cryptography (TCC 2020), Durham, NC, USA, 16–19 November 2020; pp. 470–498. [Google Scholar]
- Zhu, L.; Liu, Q.; Chen, Z.; Zhang, C.; Gao, F.; Yang, Z. A Novel Covert Timing Channel Based on Bitcoin Messages. IEEE Trans. Comput. 2023, 72, 2913–2924. [Google Scholar] [CrossRef]
- BLOCKS. Available online: https://ethereum.org/en/developers/docs/blocks/ (accessed on 27 February 2024).
- Liu, S.; Fang, Z.; Gao, F.; Koussainov, B.; Zhang, Z.; Liu, J.; Zhu, L. Whispers on Ethereum: Blockchain-based Covert Data Embedding Schemes. In Proceedings of the 2nd ACM International Symposium on Blockchain and Secure Critical Infrastructure(BSCI ’20), Taipei, Taiwan, 5–9 October 2020; pp. 171–179. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).