Congestion Avoidance in Intelligent Transport Networks Based on WSN-IoT through Controlling Data Rate of Zigbee Protocol by Learning Automata
Abstract
:1. Introduction
- In the method proposed in this article, a new mechanism based on LA is used to determine the appropriate data rate of each active network node among working rates of the Zigbee protocol. This model specifies the optimal strategy for determining the data rate of things by considering the behavioral criteria of nodes in the routing process. This mechanism, by using reward and penalty operators, can determine the optimal data rate for each active node of the intelligent transport network in an adaptable manner and in accordance with the behavior of the things.
- This research provides an efficient solution to form the communication platform of nodes in transport networks based on WSN-IoT infrastructure. This method is a hierarchical and low-cost communication structure, based on MBF, which checks the existence of the path only by performing a few bit comparisons. In this method, the value of the existing routes is also determined based on the functional criteria of the objects. This structure can manage nodes with low energy at the lowest cost and provide a mechanism to form alternative paths for each node to reach its destination.
2. Related Works
3. Proposed Model (CARLA)
- The strength of the received signal in a wireless communication has a direct relationship with the distance between the transmitter and the receiver. Therefore, the distances between the nodes can be estimated through the strength of the received signal.
- The deployment of sensor nodes in the network environment is random and uniform. Further, the density of sensor nodes in different areas of the environment is almost uniform. Some network nodes have mobility capabilities; therefore, the assumed network structure changes dynamically.
- The characteristics of each thing (such as initial energy, buffer memory capacity, etc.) can be different from other things. Therefore, the assumed network is heterogeneous. When the remaining energy of a node reaches one percent of its initial energy, the node notifies its neighbors of its energy depletion by broadcasting a message about reducing energy consumption. As a result, the node with low energy will be removed.
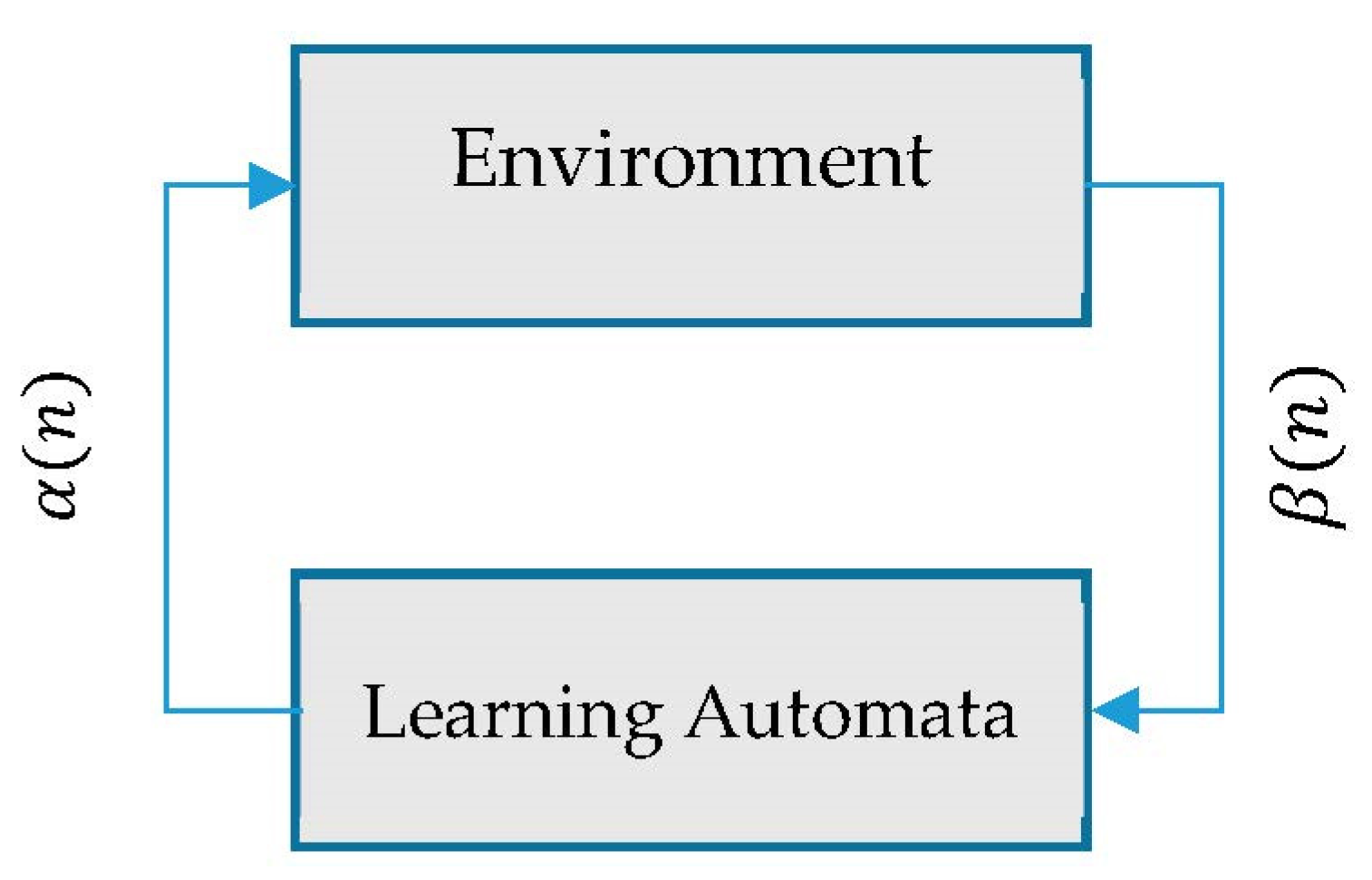
- Each sensor node in the network is equipped with an automata unit, which is used to determine the appropriate data rate for that node.
- (1)
- Topology control (construction and control of hierarchical local tree in each node);
- (2)
- Management of nodes with low energy level;
- (3)
- Data rate control using LA;
- (4)
- Local hierarchical tree-based routing.
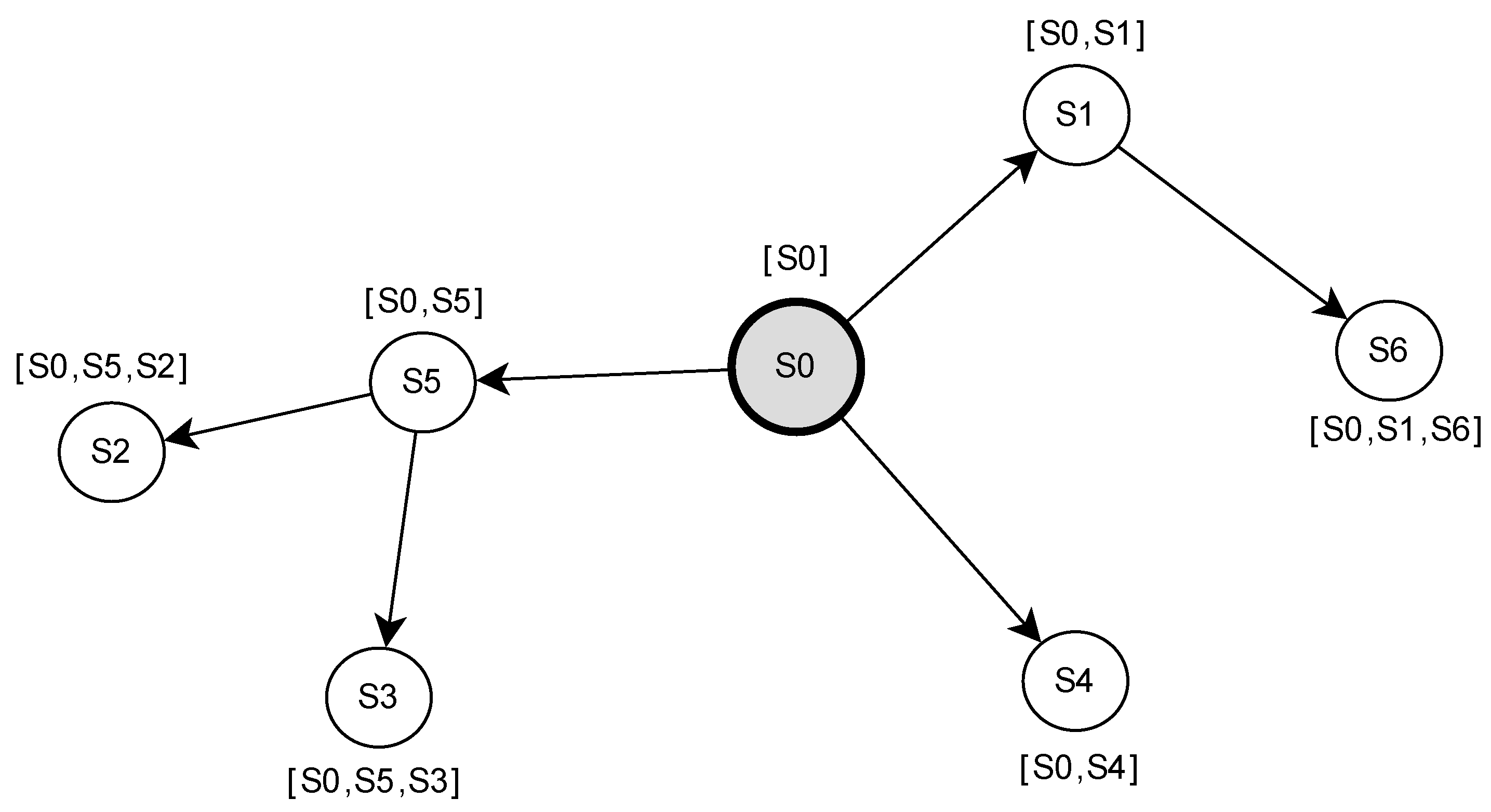
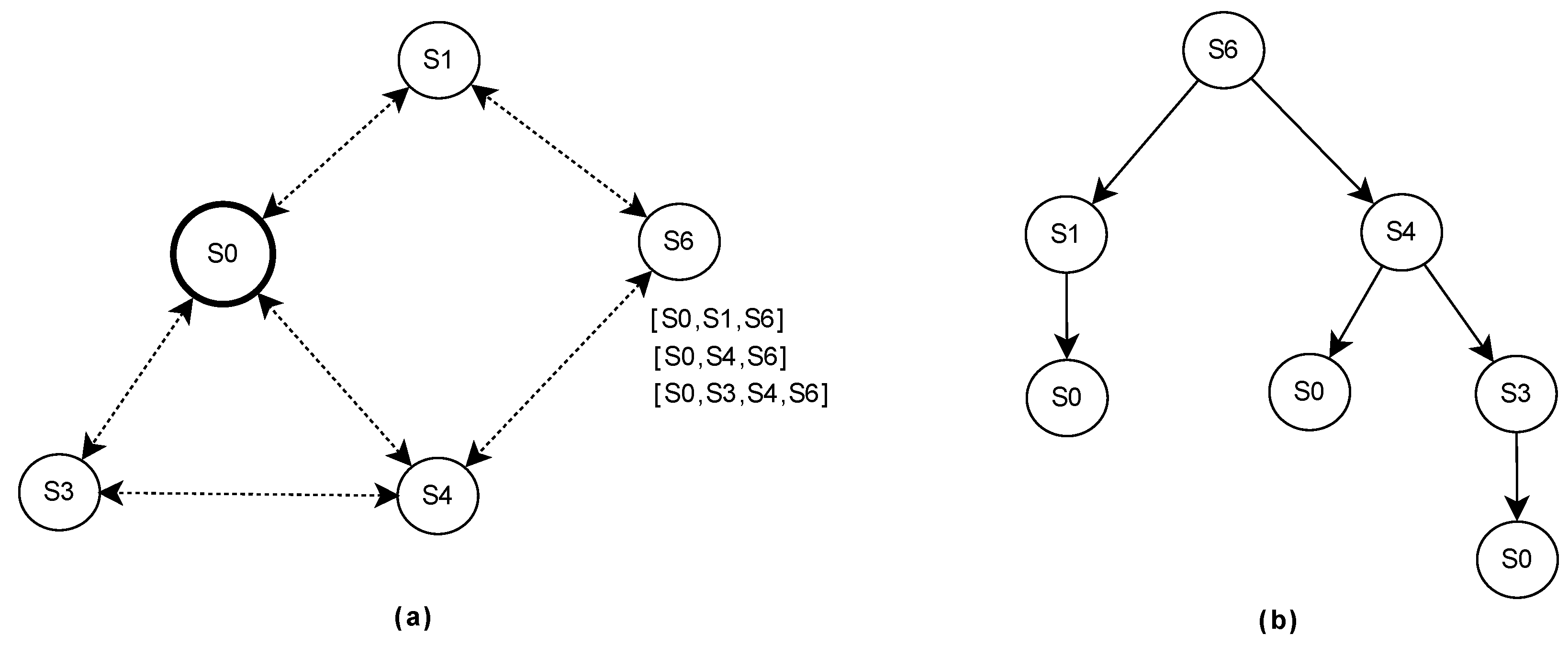
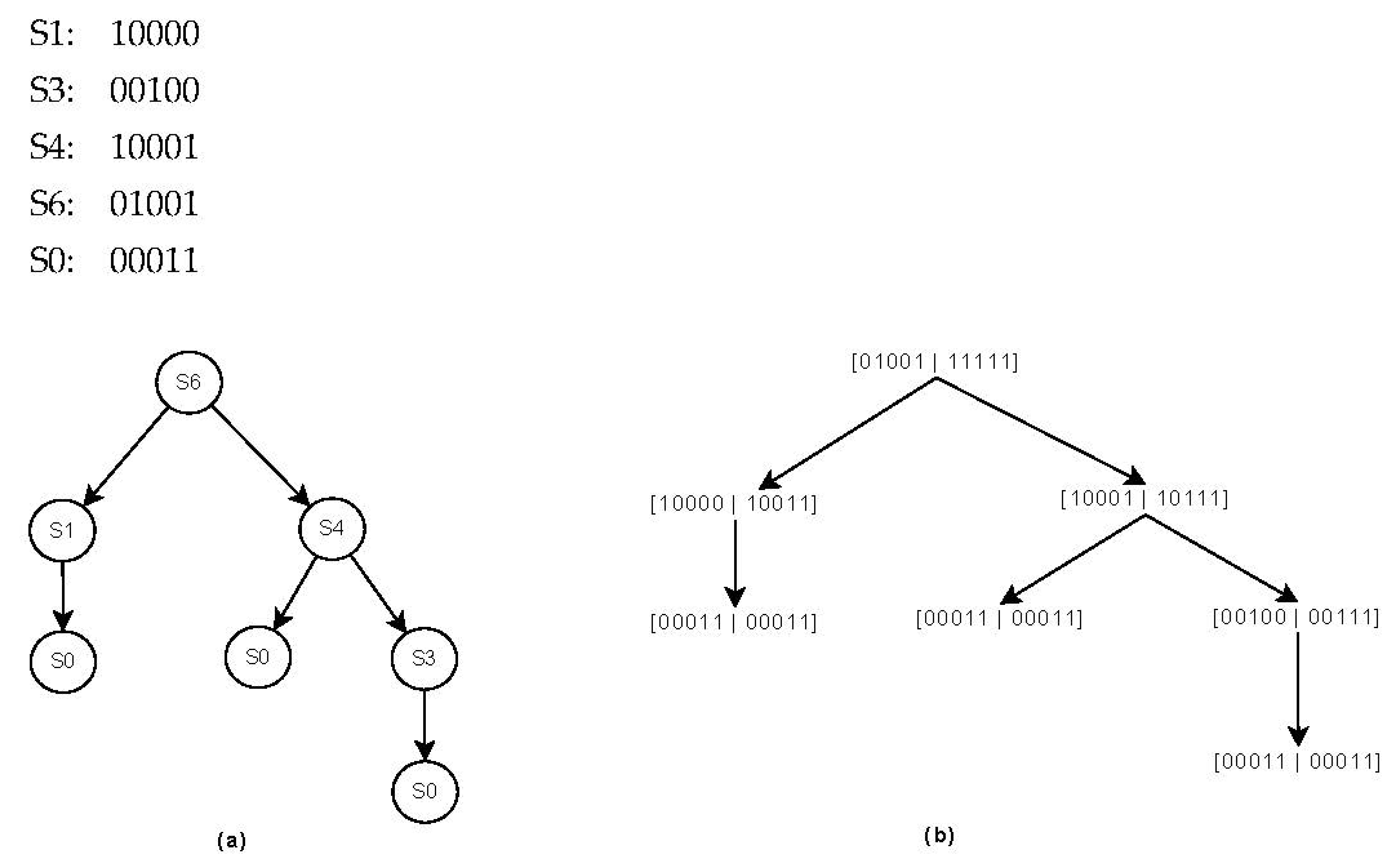
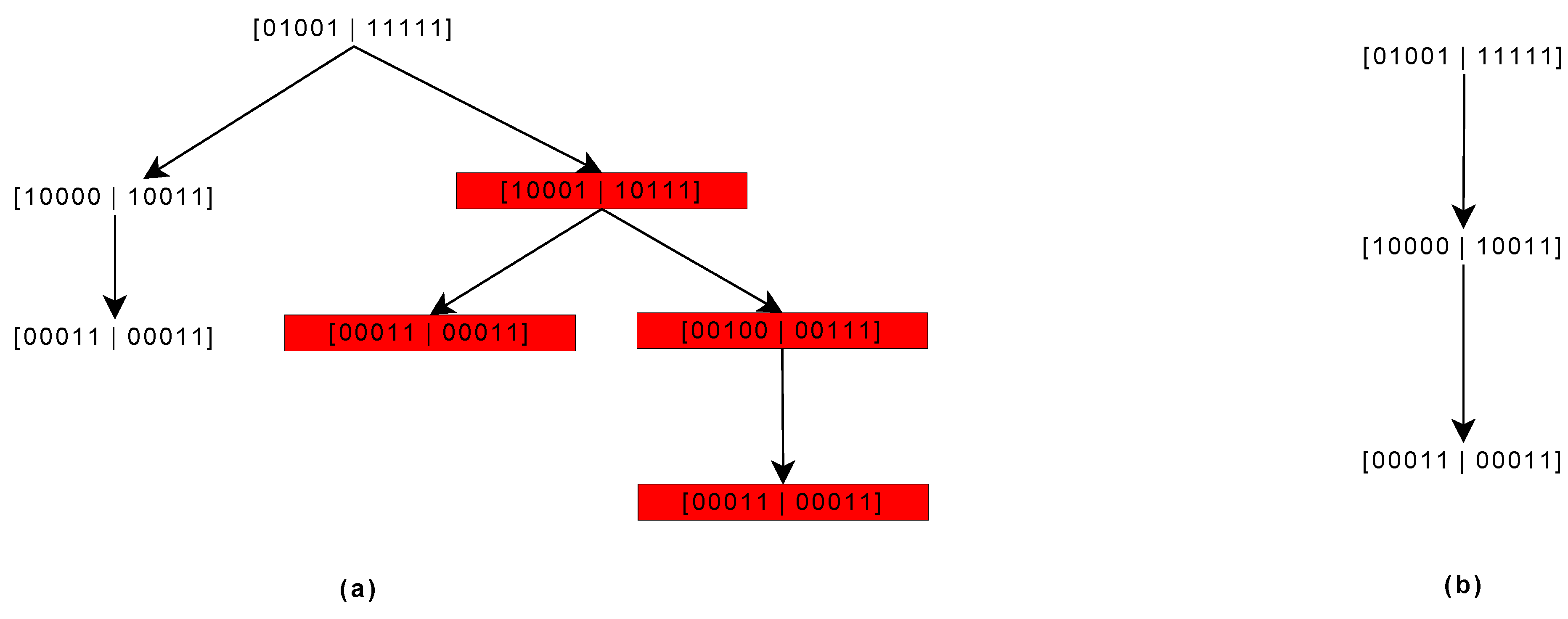
3.1. Topology Control
3.2. Management of Nodes with Low Energy
3.3. Data Rate Control Using LA
3.4. Routing Based on Local Hierarchical Tree
3.5. Updating Automata Actions at the end of Each Round of the Cycle
- If at the end of a cycle, the rate of successful packet delivery by the node in the completed cycle is higher than the rate of successful packet delivery by the node in the previous cycles, the selected rate for the node in the last cycle is considered an optimal action. In this case, the probability of choosing it will also increase with the reward of the action related to this rate.
- If at the end of a cycle, the rate of successful packet delivery by the node in the completed cycle is lower than the rate of successful packet delivery by the node in the previous cycles, the selected rate for the node in the last cycle is considered a wrong action. In this case, the probability of choosing it will decrease with the penalty for this rate.
3.6. Complexity of CARLA
4. Simulation and Results
- Evaluation of CARLA performance in the condition of changing the speed of the network nodes;
- Evaluation of CARLA performance in the condition of changing the number of network nodes.
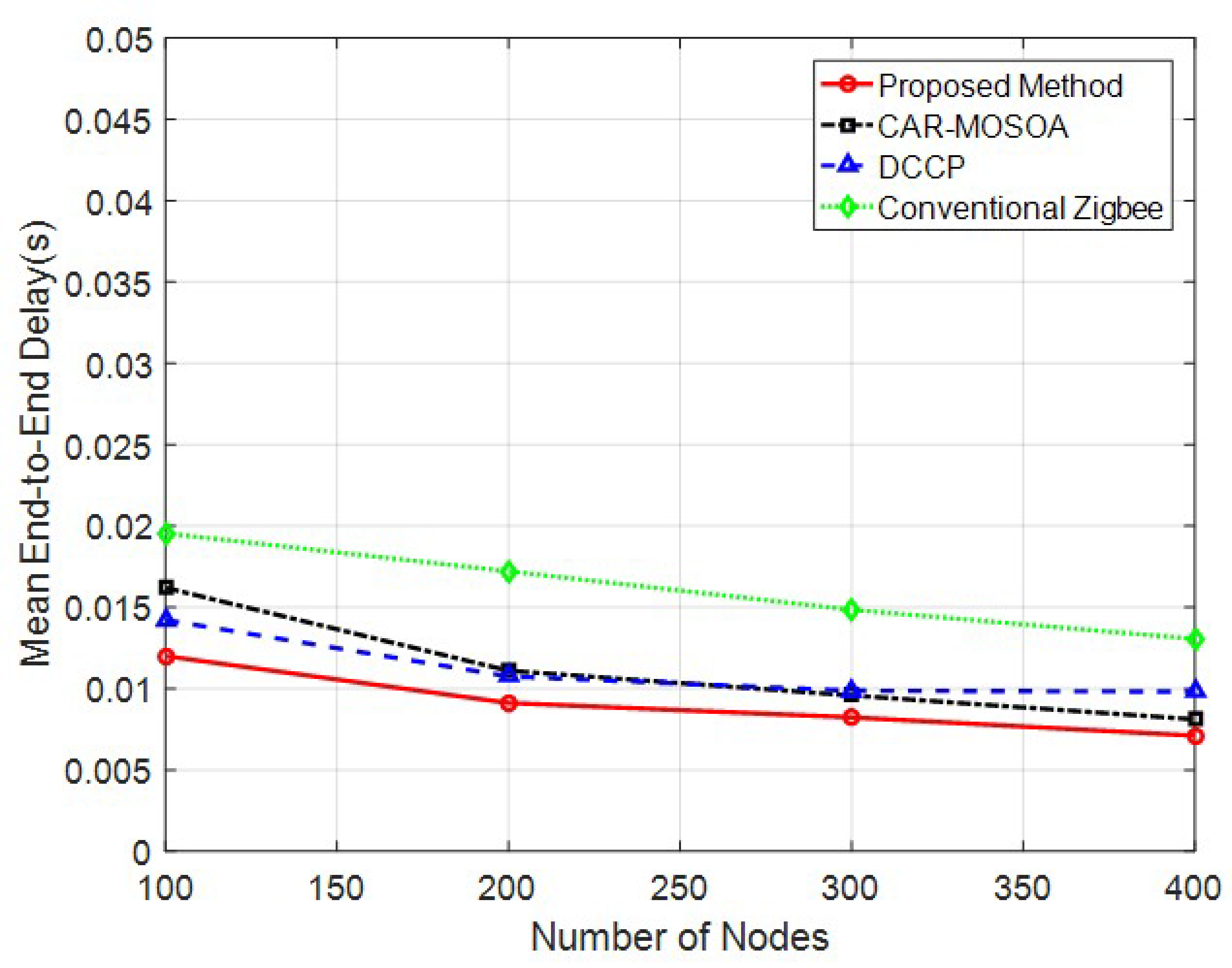
4.1. Change in the Number of Network Nodes
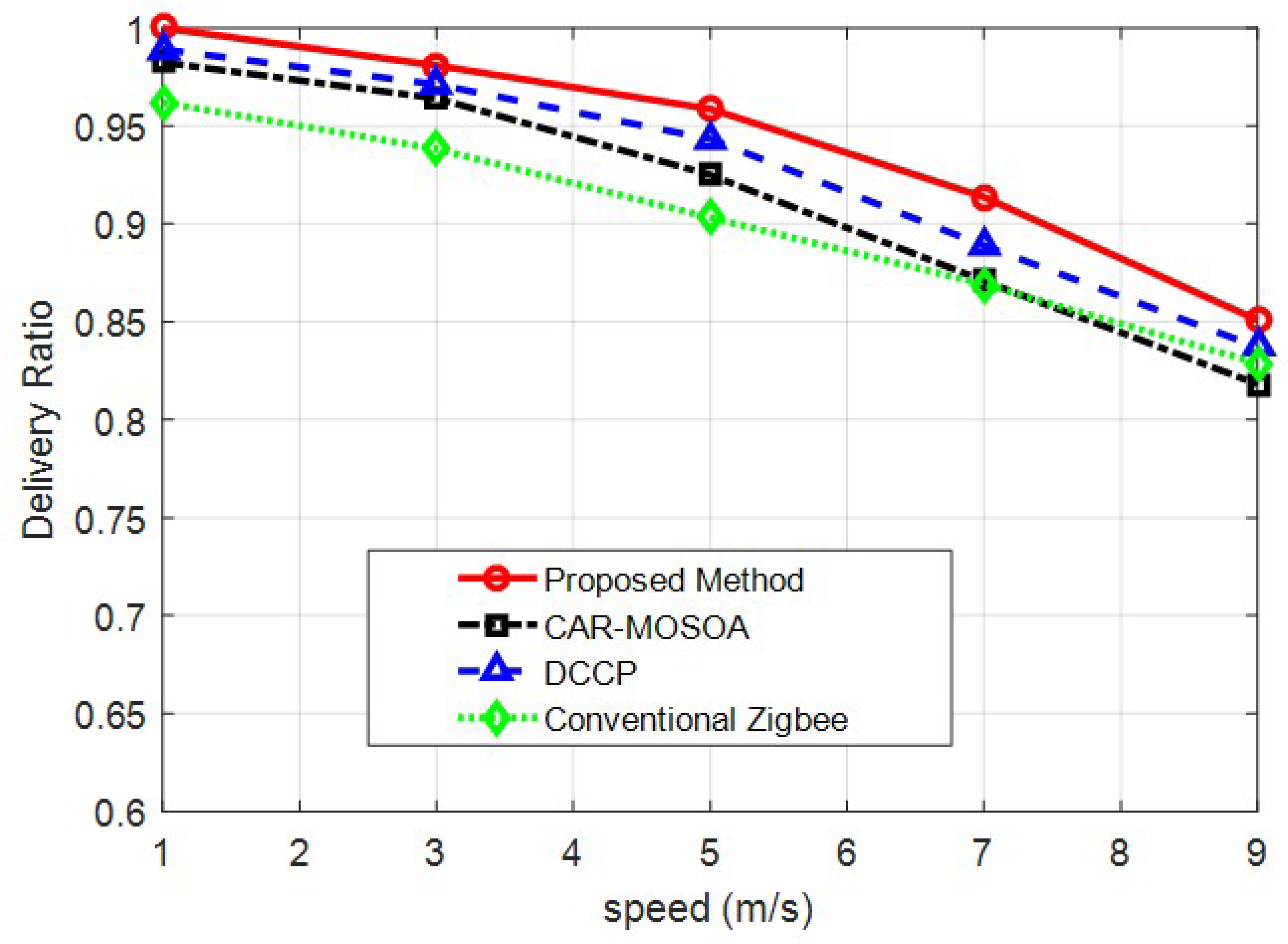
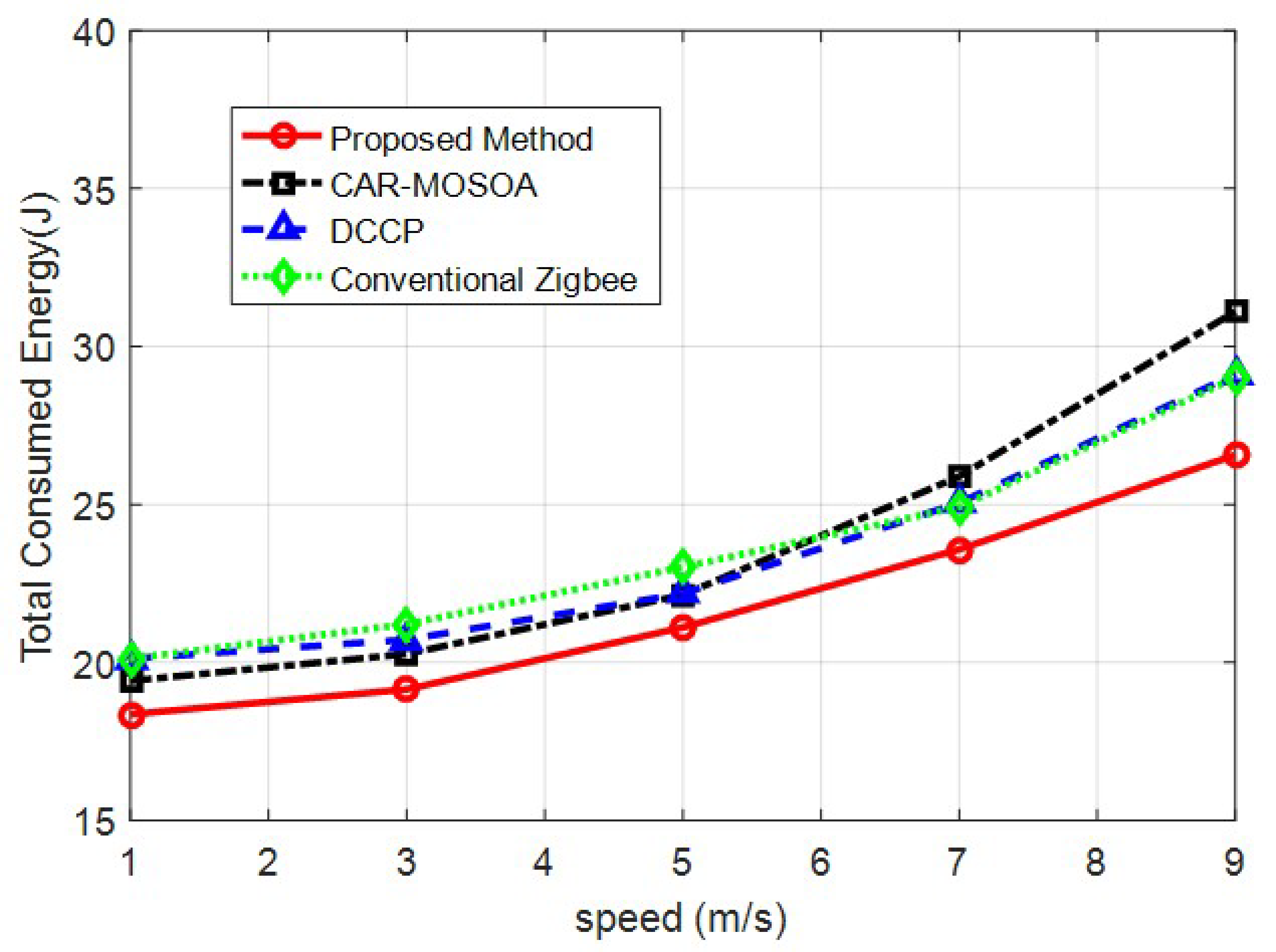
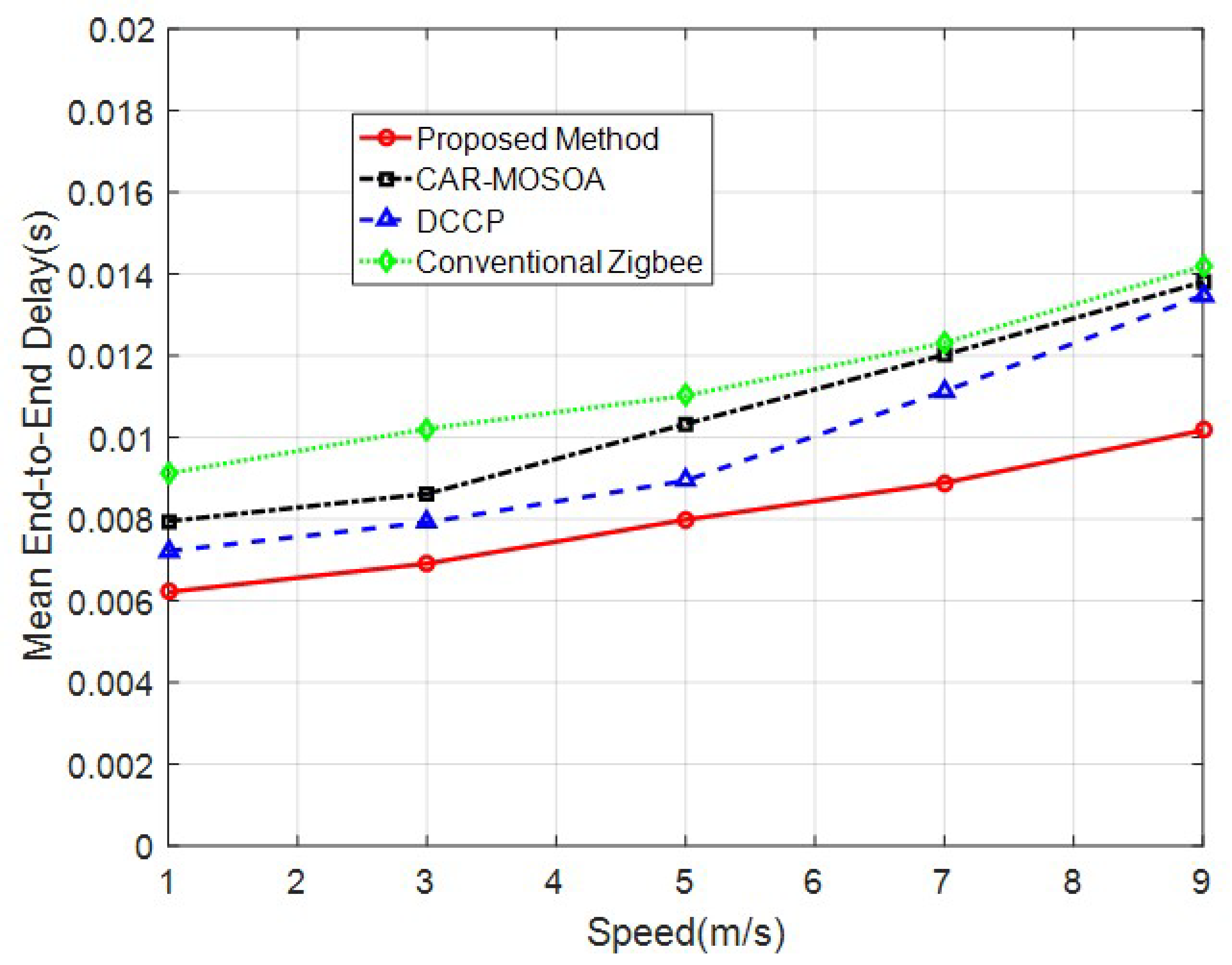
4.2. Changes in the Speed of Mobile Nodes
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Fahmy, H.M.A. Wireless Sensor Networks; Springer International Publishing: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Jain, V.K.; Mazumdar, A.P.; Faruki, P.; Govil, M.C. Congestion control in Internet of Things: Classification, challenges, and future directions. Sustain. Comput. Inform. Syst. 2022, 35, 100678. [Google Scholar] [CrossRef]
- Yadav, S.L.; Ujjwal, R.L. Mitigating congestion in wireless sensor networks through clustering and queue assistance: A survey. J. Intell. Manuf. 2021, 32, 2083–2098. [Google Scholar] [CrossRef]
- Cao, K.; Ding, H.; Wang, B.; Lv, L.; Tian, J.; Wei, Q.; Gong, F. Enhancing Physical Layer Security for IoT with Non-Orthogonal Multiple Access Assisted Semi-Grant-Free Transmission. IEEE Internet Things J. 2022, 9, 24669–24681. [Google Scholar] [CrossRef]
- Dai, X.; Xiao, Z.; Jiang, H.; Alazab, M.; Lui, J.C.; Dustdar, S.; Liu, J. Task co-offloading for d2d-assisted mobile edge computing in industrial internet of things. IEEE Trans. Ind. Inform. 2022, 19, 480–490. [Google Scholar] [CrossRef]
- Yuan, H.; Yang, B. System Dynamics Approach for Evaluating the Interconnection Performance of Cross-Border Transport Infrastructure. J. Manag. Eng. 2022, 38, 04022008. [Google Scholar] [CrossRef]
- Balador, A.; Cinque, E.; Pratesi, M.; Valentini, F.; Bai, C.; Gómez, A.A.; Mohammadi, M. Survey on decentralized congestion control methods for vehicular communication. Veh. Commun. 2021, 33, 100394. [Google Scholar] [CrossRef]
- Godoy, P.D.; Cayssials, R.L.; Garino, C.G.G. Communication channel occupation and congestion in wireless sensor networks. Comput. Electr. Eng. 2018, 72, 846–858. [Google Scholar] [CrossRef]
- Bohloulzadeh, A.; Rajaei, M. A survey on congestion control protocols in wireless sensor networks. Int. J. Wirel. Inf. Netw. 2020, 27, 365–384. [Google Scholar] [CrossRef]
- Grover, A.; Kumar, R.M.; Angurala, M.; Singh, M.; Sheetal, A.; Maheswar, R. Rate aware congestion control mechanism for wireless sensor networks. Alex. Eng. J. 2022, 61, 4765–4777. [Google Scholar] [CrossRef]
- Gherbi, C.; Roumaissa, D. IoT based traffic congestion control for environmental applications. Informatica 2021, 45, 13–23. [Google Scholar] [CrossRef]
- Upreti, K.; Kumar, N.; Alam, M.S.; Verma, A.; Nandan, M.; Gupta, A.K. Machine learning-based Congestion Control Routing strategy for healthcare IoT enabled wireless sensor networks. In Proceedings of the 2021 Fourth International Conference on Electrical, Computer and Communication Technologies (ICECCT), Erode, India, 15–17 September 2021; pp. 1–6. [Google Scholar]
- Sankari, B.S.; Nemani, R. Squirrel Search Algorithm Based Support Vector Machine for Congestion Control in WSN-IoT. Wirel. Pers. Commun. 2022, 124, 1945–1960. [Google Scholar] [CrossRef]
- Kasthuribai, P.T. Optimized support vector machine-based congestion control in wireless sensor network-based Internet of Things. Int. J. Comput. Netw. Appl. 2021, 8, 444–454. [Google Scholar] [CrossRef]
- Jagannathan, P.; Gurumoorthy, S.; Stateczny, A.; Divakarachar, P.B.; Sengupta, J. Collision-Aware Routing Using Multi-Objective Seagull Optimization Algorithm for WSN-Based IoT. Sensors 2021, 21, 8496. [Google Scholar] [CrossRef] [PubMed]
- Majeed, U.; Malik, A.N.; Abbas, N.; Abbass, W. An Energy-Efficient Distributed Congestion Control Protocol for Wireless Multimedia Sensor Networks. Electronics 2022, 11, 3265. [Google Scholar] [CrossRef]
- Kaur, G.; Chanak, P.; Bhattacharya, M. A Green Hybrid Congestion Management Scheme for IoT-enabled WSNs. IEEE Trans. Green Commun. Netw. 2022, 6, 2144–2155. [Google Scholar] [CrossRef]
- Suma, S.; Harsoor, B. Dynamic shortest path routing algorithm to reduce retransmission and congestion avoidance for mobile nodes in wireless sensor network. In IoT Based Control Networks and Intelligent Systems; Springer: Berlin/Heidelberg, Germany, 2022; pp. 649–659. [Google Scholar]
- Chappala, R.; Anuradha, C.; Murthy, P.S.R.C. Adaptive Congestion Window Algorithm for the Internet of Things Enabled Networks. Int. J. Adv. Comput. Sci. Appl. 2021, 12. [Google Scholar] [CrossRef]
- Srivastava, V.; Tripathi, S.; Singh, K.; Son, L.H. Energy efficient optimized rate-based congestion control routing in wireless sensor network. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 1325–1338. [Google Scholar] [CrossRef]
- Alejandrino, J.; Concepcion, R.; Lauguico, S.; Palconit, M.G.; Bandala, A.; Dadios, E. Congestion detection in wireless sensor networks based on artificial neural network and support vector machine. In Proceedings of the 2020 IEEE 12th International Conference on Humanoid, Nanotechnology, Information Technology, Communication and Control, Environment, and Management (HNICEM), Manila, Philippines, 3–7 December 2020; pp. 1–6. [Google Scholar]
- Khorov, E.; Kiryanov, A.; Lyakhov, A.; Bianchi, G. A tutorial on IEEE 802.11 ax high efficiency WLANs. IEEE Commun. Surv. Tutor. 2018, 21, 197–216. [Google Scholar] [CrossRef]
- Patgiri, R.; Nayak, S.; Borgohain, S.K. rDBF: A r-dimensional bloom filter for massive scale membership query. J. Netw. Comput. Appl. 2019, 136, 100–113. [Google Scholar] [CrossRef]
- Narendra, K.S.; Thathachar, M.A. Learning Automata: An Introduction; Courier Corporation: North Chelmsford, MA, USA, 2012. [Google Scholar]
- Jiang, S.; Zhao, C.; Zhu, Y.; Wang, C.; Du, Y. A Practical and Economical Ultra-wideband Base Station Placement Approach for Indoor Autonomous Driving Systems. J. Adv. Transp. 2022, 2022, 3815306. [Google Scholar] [CrossRef]





| Parameter | Value |
|---|---|
| Dimensions of the environment | 800 × 800 m |
| Number of network nodes | Variable (between 100 and 400) |
| Initial energy of each node | Random (between 0.5 and 1 joule) |
| Buffer capacity of each node | Random (between 50 and 100 KB) |
| Allowable range for data rate | 20 to 250 kilobits per second |
| Movement pattern of nodes | Random Way Point |
| Simulation time | 2000 rounds of topology formation |
| Speed of nodes | Random (from 2 to 10 m per second) |
| Experiment | Method | PDR | Energy (j) | Delay (s) |
|---|---|---|---|---|
| Number of Nodes | Proposed Method | 0.9425 | 28.39 | 0.009116 |
| CAR-MOSOA [15] | 0.8691 | 34.48 | 0.01125 | |
| DCCP [16] | 0.9064 | 31.12 | 0.01116 | |
| Conventional Zigbee | 0.8684 | 34.86 | 0.01616 | |
| Speed of Nodes | Proposed Method | 0.9408 | 21.75 | 0.008035 |
| CAR-MOSOA [15] | 0.9121 | 23.76 | 0.01055 | |
| DCCP [16] | 0.9259 | 23.42 | 0.009738 | |
| Conventional Zigbee | 0.9003 | 23.66 | 0.01137 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, Z.; Chen, L.; Li, F.; Jin, G. Congestion Avoidance in Intelligent Transport Networks Based on WSN-IoT through Controlling Data Rate of Zigbee Protocol by Learning Automata. Electronics 2023, 12, 2070. https://doi.org/10.3390/electronics12092070
He Z, Chen L, Li F, Jin G. Congestion Avoidance in Intelligent Transport Networks Based on WSN-IoT through Controlling Data Rate of Zigbee Protocol by Learning Automata. Electronics. 2023; 12(9):2070. https://doi.org/10.3390/electronics12092070
Chicago/Turabian StyleHe, Zhou, Lian Chen, Feng Li, and Ge Jin. 2023. "Congestion Avoidance in Intelligent Transport Networks Based on WSN-IoT through Controlling Data Rate of Zigbee Protocol by Learning Automata" Electronics 12, no. 9: 2070. https://doi.org/10.3390/electronics12092070
APA StyleHe, Z., Chen, L., Li, F., & Jin, G. (2023). Congestion Avoidance in Intelligent Transport Networks Based on WSN-IoT through Controlling Data Rate of Zigbee Protocol by Learning Automata. Electronics, 12(9), 2070. https://doi.org/10.3390/electronics12092070









