Abstract
Traditional vehicle ad hoc networks (VANETs) have evolved toward the Internet of Vehicles (IoV) during the past ten years with the introduction of 5G communication technology and the growing number of vehicles linked to the Internet. The coexistence of IEEE 802.11p and 5G becomes critical to build a heterogeneous IoV system that benefits from both technologies, being that the IEEE 802.11p standard remains the best option for direct communications and safety-critical applications. The IEEE 1609 standard family and the ETSI ITS-G5 standard family both use the IEEE 802.11p standard as a MAC mechanism. To avoid dangerous situations, vehicles require the periodic exchange of awareness messages. With the increase in vehicle density, the MAC layer will suffer from radio channel congestion problems, which in turn will have a negative impact on the safety application requirements. Therefore, the decentralized congestion control (DCC) mechanism has been specified by ETSI to mitigate channel congestion; this was achieved by adapting transmission parameters such as transmit power and data rate. However, several studies have demonstrated that DCC has drawbacks and suffers from poor performance when the channel load is very high. This paper investigates a new promising DCC technique called transmission timing control (TTC), to reduce the channel load for periodic cooperative awareness. It consists of spreading the transmissions over time to avoid contention on the transmission channel. The objective of the paper is to propose an analytical study to calculate the probability of successful transmission using TTC. Obtained results showed a convergence between the applied experiments and our mathematical model, achieving an error margin of only 5%, which confirms the validity of the equation proposed.
1. Introduction
Recent years have seen the transformation of conventional vehicle ad hocnetworks into the Internet of Vehicles (IoV) driven by the Internet of Things (IoT), which promises enormous scientific value and commercial interest [1]. As a result, scientists and researchers are constantly exploring and creating cutting-edge wireless technologies for vehicle communication. In this sense, the introduction of 5G gives the wireless network access to more spectrum resources, enabling vehicle-to-everything applications that allow for enormous data delivery and low-latency communications. However, vehicular communications still require direct short-range communications (DSRC) to enable safety-related applications in order for data to be transferred successfully and promptly without going via an access point [2,3]. Hence, combining short-range technologies (IEEE- 802.11p/ITS-G5) [4] and long-range technologies (5G) is still necessary for seamless network connectivity in order to maximize the benefits of each of them, and thus achieve improved vehicular communications [5,6,7].
One of the most significant use-cases for safety-related applications in the IoV is cooperative awareness [8]. It is provided by a beaconing mechanism in which cars periodically broadcast a beacon message known as cooperative awareness message (CAM) in Europe [9], as standardized by the European Telecommunications Standards Institute (ETSI) [10]. In the USA the message is called a basic safety message (BSM), which is used by the IEEE 1609.0 standard known under the work named the “Wireless Access in Vehicular Environment” (WAVE) [11,12]. The transmission frequencies for CAM/BSM messages generally range from 1 to 10 Hz, where each vehicle communicates with its neighbors to advertise location, speed, and direction. This enables better visibility of the neighborhood in real-time and increased driver awareness. Typically, the control channel (CCH) is the frequency channel where the CAM/BSM is delivered, and the service channels (SCHs) are open to non-safety traffic. Controlling access to the collision area is required since vehicles use the same radio channels. It can be defined as the radio range covering the one-hop and two-hop neighbors of each vehicle, which causes the known direct and hidden collision problems, respectively [5].The medium access control (MAC) layer controls the access to the communication medium. It is essential to the administration of the channel. The IEEE 802.11p standard’s MAC layer [3] is selected as the top candidate for short-range vehicle communication. Enhanced distributed channel access (EDCA) is a distributed channel access that uses the carrier sense multiple access/collision avoidance (CSMA/CA) technology to reduce the likelihood of collision between multiple vehicles accessing the medium. Its mechanism is based on retransmission techniques, backoffs, and carrier sensing (CS). Its simplicity, dynamic nature, and asynchronicity make it a commonly used contention-based MAC approach.
In North America, the WAVE architecture implements the MAC layer using 802.11p/1609.4 standards, offering a switching mechanism between many physical channels [13,14]. As a result, the “start-of-interval contention” problem may arise immediately after channel switching from SCH to CCH since several WAVE devices may begin the channel access contention period at the same time [15,16].This causes a significant collision risk, particularly when the network is dense.
The backoff mechanism is the only method of congestion control for safety message beaconing in a WAVE system which uses a short contention window length (CW). This method is insufficient to stop many vehicles from using the channel at the same time. It might lead to significant issues while supporting real-time applications with high communication reliability and low latency, such as safety message beaconing under dynamic topologies. Most of the planned asynchronous MAC for V2V under IoV are still based on CSMA/CA.
In a previous work we have proposed a novel scalable random access MAC for vehicular networks with the objective to prevent the start-of-interval contention problem, which occurs upon switching to the CCH. The aim was to provide an efficient one-hop broadcast access to the CCH, attempting to minimize the risk of direct and hidden collision problems. The proposal is called CSSA MAC [17] (carrier sense for slotted-ALOHA random multiple access MAC), and it tries to combine the advantages and simplicity of the two MAC mechanisms: CSMA and Slotted-ALOHA (S-ALOHA) [18]. It can be seamlessly integrated in IEEE 1609.4 on top of the IEEE 802.11p standard. Its main idea is to spread the transmission time of beacons of the contending vehicles over a spreading window (SW) within the CCH interval. Therefore, this interval is virtually slotted, the same way as the S-ALOHA MAC method, where the virtual slots represent the possible start of transmission times (STT) of the beacons. The beacon spreading process relies on randomly selecting the STT from the SW by contending vehicles. Hence, with this mechanism, the CSSA MAC aims to ensure a more efficient use of the limited bandwidth available.
The objective of this paper is to calculate, through both analytic and simulation studies, the probability of a successful transmission when adopting the CSSA MAC protocol. To this end, it is important to predict the number of occupied virtual slots or STTs which can be extracted from the SW size, as well as the number of contender vehicles, and then to estimate the number of beacons assigned to each STT.
The remainder of this paper is organized as follows: Section 2 presents related work on the topic, while Section 3 describes the proposed CSSA MAC. The analysis of the successful transmission probability is demonstrated in Section 4, followed by a discussion in Section 5, where the strengths and limitations of the proposal are presented. Finally, the paper is concluded in Section 6, highlighting the main findings and future work.
2. Related Work
The performance of beaconing within the context of vehicle networks using the CSMA-like MAC-based systems has been widely investigated in the literature, and all the proposed protocols are categorized according to the method adopted.
They can be classified under two important classes: EDCA parameter adaptation mechanisms, and distributed congestion control (DCC) mechanisms. The CSMA/CA parameters, such as the contention window (CW) and access priority, are the only mechanisms that the EDCA parameter adaptation acts upon. The CW value used in the standard is deemed to be not optimal, according to researchers who have been studying and addressing the backoff problem [19,20]. In this regard, several modified backoff algorithms have been published in the literature [21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52]. However, establishing an optimal contention window size is a difficult challenge to achieve. Increasing the CW size can lead to the beacon expiration problem; in addition, decreasing its size may lead to an increased number of collisions. Therefore, adapting only the contention window is not sufficient to decrease the risk of collision under high contention.
Regarding the second class, the basic goal of distributed congestion control (DCC) techniques in the context of vehicular communication is to reduce the strain on shared communication channels, and to coordinate equitable channel access among cars in the context of vehicular communication. To this aim, the DCC transmission parameters such as (1) the transmitted power, (2) the generation rate, (3) the transfer rate, and (4) the transmission time are often dynamically adjusted by the congestion control algorithms [53]. Through cross-layer design, the European ITS architecture ETSI standard provides the option to adapt these parameters. Note that the transmission timing control is not standardized yet. Instead, a more comprehensive survey of DCC-based approaches for vehicular environments is provided and categorized in [54] with the goal of identifying outstanding open problems, along with potential future research areas.
The most obvious way to manage channel load in congested situations in a vehicular network is to adjust the beacon rate generation. Since vehicles often travel at modest speeds in densely populated areas, reducing the frequency of beaconing has proven to be a successful method for reducing congestion [55,56,57,58,59,60,61,62,63,64,65,66,67,68]. However, the rate adaptation of such beacons should be properly developed because sending fewer messages can easily have the effect of harming rather than benefiting the performance of safety applications. It is important to consider how this change would affect each safety application because it remains unknown whether or not all applications can handle such a reduction. Moreover, predicting a maximum value between 5Hz and 10Hz might be problematic in some circumstances since the maximum frequency of these signals is still an open research problem. The third DCC mechanism is data rate adjustment. It requires employing high data rates at a high vehicle density to shorten a beacon’s transmission time. In practical terms, this refers to using signal modulation that results in a smaller channel occupation [69,70]. However, any modulation that produces a higher data rate often demands a higher signal-to-noise (SNR) ratio at the receiver in order to be successfully demodulated [68]. Adjusting the transmission power is another option that may be used to reduce channel congestion by reducing the number of nearby vehicles while maintaining network cohesion. It thereby remains as one of the most researched approaches among DCC-like mechanisms. In fact, it can reduce interference and improve the probability that surrounding vehicles will be able to successfully receive signals [46,68,71]. In some cases, transmission power regulation can be quite effective, but it cannot be viewed as a universal VANET communications solution.
The transmission timing control is a promising technique in this category, which is not standardized yet. It comprises spreading the density of transmissions over the CCH interval, which is an effective solution to avoid contention on the transmission channel. Some proposals in the literature [72,73,74] have investigated the idea of spreading out the channel access of the transmitters during the CCH interval in order to avoid the contention problem. However, these mechanisms propose a slight modification to the IEEE 1609.4 standard to improve it, and they do not investigate the level of contention according to the channel load through an analytical study. Moreover, the optimal interval of spreading should be designed carefully by taking into consideration the number of contending vehicles, because a large interval with few contenders will increase the transmission delay beacon expiration problem. On the other hand, a small interval with a high number of contenders leads to increasing the probability of collisions. The best adaptation remains an open problem, and many solutions still suggest those that use machine learning for smart- and self-optimization of network parameters [45,75,76].
Hence, in this paper we specifically address this issue, proposing a novel DCC technique that attempts to reduce the channel load for periodic cooperative awareness.
3. Taxonomy of MAC Proposals
The previous section presents many different variants and alternatives that have been proposed based on a CSMA-like MAC to improve the transmission efficiency by adapting the transmission parameters of the IEEE WAVE/802.11p standard. The adaptation is performed according to some mechanisms such as channel load estimation (local density estimation), along with vehicles’ coordinate information such as speed and position of vehicles, time of packet sending, beacon collision/expiration detection, and local beacon expiration estimation. Therefore, we introduce a taxonomy that can be helpful to have a global view and general understanding of works in this area. Table 1 shows a classification of the proposed protocols according to their transmission parameters, and the adaptation mechanism which they act on.

Table 1.
Classification of CSMA-like MAC protocols.
4. The CSSA MAC Protocol
The CSSA MAC protocol consists of two parts: (1) the first spreadsthe vehicle’s beacons at the beginning of each CCH interval, where they are spread in time over the SW (a STT is randomly allocated for each beacon). Such a solution can be enabled through a minor modification to the IEEE 1609.4 standard; and (2) the second uses medium access: when the STT is reached, a vehicle has a chance to access the channel, and attempts to transmit using the conventional IEEE 802.11p’s CSMA/CA. The system under consideration is formed by vehicles which have the same communication range, as well as the carrier sensing range. The system uses the MAC protocol as defined in IEEE 802.11p/1609.4, and operates in one CCH, which is used for the transmission of a beacon message, also known in the WAVE architecture as a BSM (CAM in the ETSI architecture). These messages are always transmitted at the beginning of each CCH interval. All the vehicles transmit beacon packets of the same size, at the same transmission rate λ, and start at the same time instant. It is assumed that the transmission duration between two successive beacons is equal to the CCH interval, being reasonable to limit the lifetime of a beacon message to one CCH interval. The time synchronization at the MAC layer can be obtained easily using GPS timestamps. The CCH interval is partitioned into a variable number of virtual STTs, where their borders and size are calculated at the beginning of each CCH interval according to the beacon size and the beacon transmission rate, as shown in Figure 1.
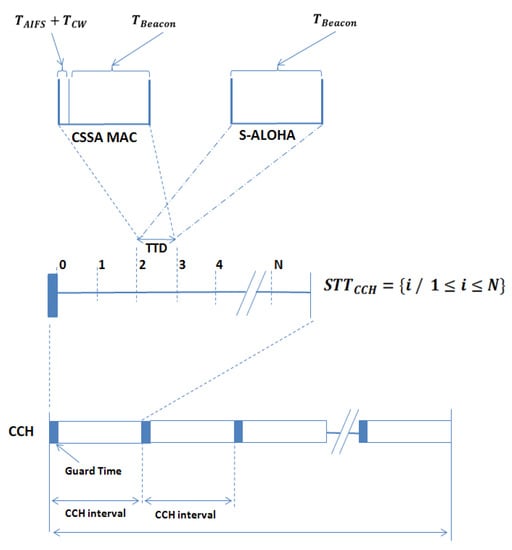
Figure 1.
Sync interval, guard interval, CCH interval and TTD interval.
The duration of the TTD for the beacon’s transmission consists of a guard time , which is a guard interval that accounts for the propagation delay and timing inaccuracy, an AIFS period, the minimum contention window (CWmin) interval, and the beacon transmission time (TBeacon). Note that the CWmin is used to ensure competition between the vehicles having selected the same STT, when they arrive at the MAC layer. The duration of the used can be adjusted according to the CW value and the chosen beacon size, as presented in Equation (1):
After that the channel is slotted virtually, the size of is calculated according to Equation (2):
where refers to the beacon transmission rate (note that is equal to the CCH interval).
The proposed idea consists of randomly spreading the beacon, based on the S-ALOHA principle, throughout the entire SW time interval; with the main goal to prevent simultaneous channel access attempts. The size of the SW can cover the whole CCH interval, or part of it, so it can vary within the following range: . CSSA MAC adjusts the SW according to the number of neighbors or the local density (LD) within a two-hop range, where the beacon messages are used as the notification. At the beginning of each CCH interval, each vehicle updates the size of their SW according to the local density. When beacons arrive to the IEEE 1609.4 layer, they are spread randomly over the SW and each wait for the duration time before being passed on to the MAC layer (see Figure 2).
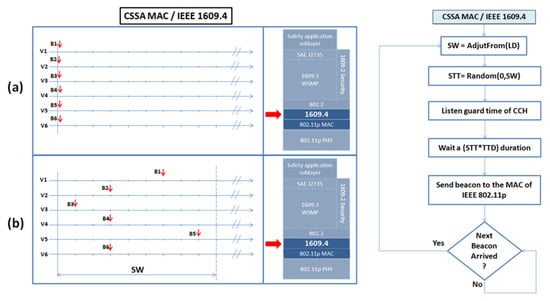
Figure 2.
CSSA MAC functioning: (a) beacons simultaneously arriving to the IEEE 1609.4 layer; (b) beacons being spread over the SW.
When it is time for a vehicle to access the MAC layer (i.e., IEEE 802.11p) it may bethat several beacons fall within the same STT, meaning that they will compete for channel access. Before transmitting the beacon packet, each vehicle invokes the backoff procedure using the minimum contention window interval (CWmin) to reduce the collision probability between them. When the counter reaches zero, the vehicle broadcasts its beacon. If there are no contenders for the selected STT, the vehicle transmits successfully without any contention; otherwise, it will face the risk of collision (see Figure 3).
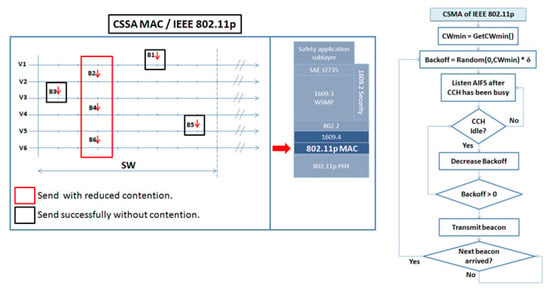
Figure 3.
CSSA MAC functioning: beacons arriving to the IEEE 802.11p layer and being transmitted using the CSMA method.
5. Analysis of Successful Transmission Probability
Spreading the beacons of vehicles over the SW results in a set of occupied STTs where each of them receive at least one beacon. The calculation of the average successful transmission probability depends on predicting the number of beacons in each occupied STT, where vehicles therein compete to gain access to the channel. Therefore, the Imbrical Spreading Function (ISF) is proposed. Yet, before that, it is important to predict the number of occupied STTs.
5.1. Predicting the Number of Occupied STTs
The first step to be investigated is predicting the number of occupied STTs after beacon spreading. This is equivalent to the famous occupancy problem [77], where (m) distinguishable balls are randomly distributed into (n) distinguishable boxes.
To begin with, let be the random variable which determines the number of the occupied boxes when distributing (m) distinguishable balls into (n) distinguishable boxes, and be the probability that (k) boxes are occupied. The probability is calculated as shown in Equation (3):
where gives the number of possible ways to distribute (n) balls in (k) boxes, and (k) boxes are occupied. represents all possible cases of distributing (n) balls over (m) boxes [78]. is defined as presented in Equation (4):
where representes all the possible arrangements of (k) occupied boxes over (m) boxes and is named “the Stirling number of the second kind”. This way, the deduced expression of Equation (4) can be written as:
The number of all possibilities by which (m) distinguishable balls can be distributed into (n) distinguishable boxes is:
Equation (3) can be deduced from Equations (5) and (6), and can be written as presented in Equation (7):
Equation (7) is implemented and compared with a simulation performed in MATLAB, where N beacons are distributed 200 times over a SW. Note that, in all simulations, the size of the SW is taken as being arbitrarily equal to the number of beacons (NB = SW). The graphs of Figure 4 present a comparison between the analytical and simulation results where NB is equal to 10 beacons. It shows a match in the results which confirms the correctness of the equation used. Instead, Figure 5 shows some examples of distributing 10 beacons over a SW of 10 STTs. It is notable that in Figure 4 and Figure 5 the highest occupancy value is 7, denoted by the connected red line, compared to the occupancy value 6, indicated by the dotted red line.
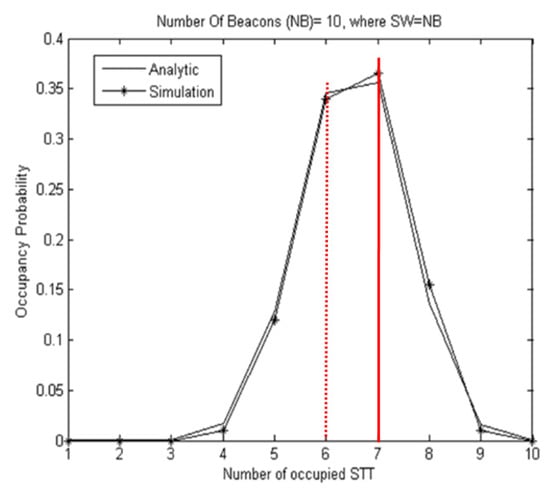
Figure 4.
Comparison between the analytical and the simulation results of the occupancy probability for a number of beacons equal to 10, where SW = NB.

Figure 5.
An example of simulation results performed in MATLAB of distributing 10 beacons over the SW of 10 STTs.
Figure 6 show the occupancy probability when varying the number of occupied STTs. It is noticeable that the occupancy possibilities do not have the same probability of appearance. In each experience, there is one occupancy possibility which has the highest probability; thisis called the highest occupancy possibility (HOP) and is indicated by the red circle.
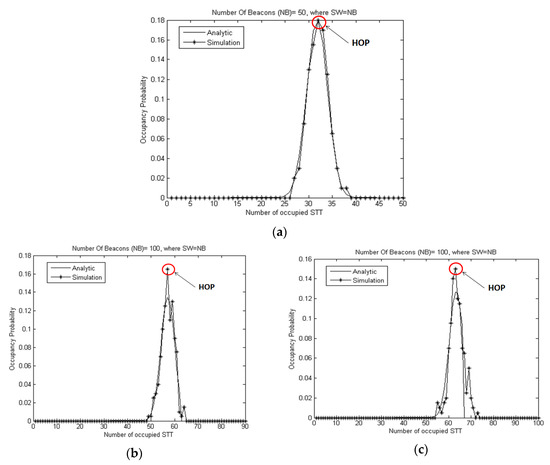
Figure 6.
Comparison between analytical and simulation results of the occupancy probability for a different number of beacons, and where SW = NB.
Figure 7 presents the impact of the SW size on the occupancy possibilities and on the HOP, for different values of the NB (number of beacons) parameter. It is shown that, when the SW increases, the whole graph shifts to the right, and the value of the HOP gets closer to the maximum number of beacons. This means that the occupied STTs will receiveonly one beacon (on average) as the SW increases.
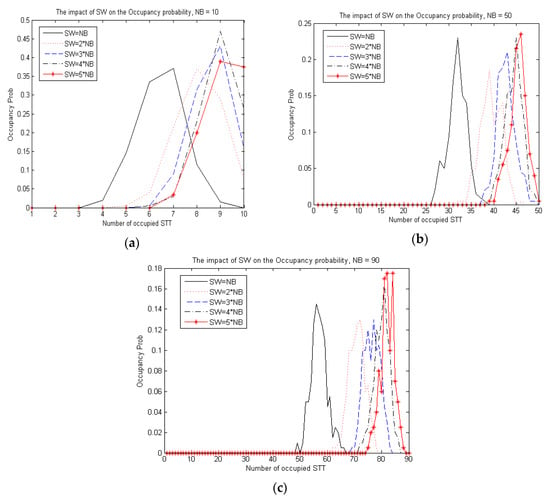
Figure 7.
Impact of the SW size on the occupancy possibilities and on the HOP.
A more general study about the impact of the SW on the HOP is needed to ascertain the previous results. Let HOP(NB, SW) be the function which returns the HOP value when spreading NB beacons over the SW. This way, the occupancy ratio (OR) can be defined as shown in Equation (8):
The worst case takes place when the is equal to 1, meaning that the occupancy is minimal, and the best case occurs when the HOP is equal to the number of beacons (NB); in this case, each occupied STT receives only one beacon.
Now, let us define the average occupancy ratio (AvgOR) for a set of NB values, and for a given SW. The AvgOR can be determined as presented in Equation (9):
Figure 8 shows the analytical and the simulation results of the AvgOR, where the average results of a different number of beacons are taken:, for each SW size. The SW sizes taken represent a set of multiples of NB, where Note that, when multiple NB values equal zero (k = 1), it means that the SW has just one STT (SW = 1). It is notable from the graph that the results of both the analytical and simulation graphs clearly match each other. Moreover, the occupancy ratio increases when the SW size increases.
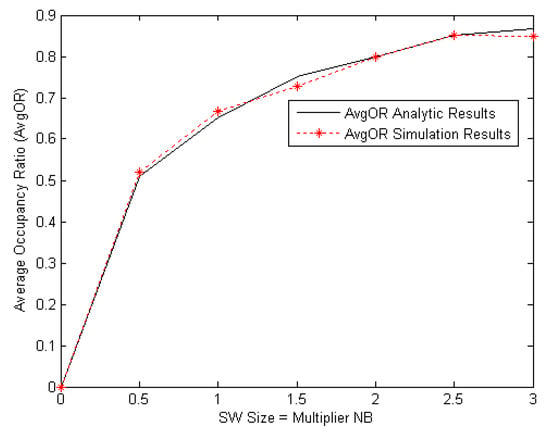
Figure 8.
Impact of SW size on the average occupancy ratio.
The results of the AvgOR graph can be used as a model to estimate and predict the number of occupied STTs, noted as HOP, for any number of beacons belonging to the NBset, spread over any SW size belonging to the SWset.
The HOP can be extracted using Equation (10), and the ISF can then be computed recursively as follows:
5.2. Predicting the Number of Beacons in the Occupied STTs
The second stage in the process of calculating the average successful transmission probability is to predict the number of beacons in each STT. To this end, the ImbricalSpreading Function (ISF), as shown in Algorithm 1, performs the spreading process multiple times over the occupied STTs recursively in a nested loop. After each round of beacon spreading, the function assigns one beacon to each occupied STT and, in the next round, the remaining ones are respread once again exclusively over the previously occupied STTs. The process is repeated several times until there are no beacons left to be spread.
The ISF calculation is performed based on the highest occupancy possibility (HOP) function presented in Equation (10). The notification can be read as the recursive distribution of NB beacons over the SW spreading window. For thispurpose, let be the highest occupancy possibilities in round (i) of spreading, and let be the remaining beacons in round (i) of spreading, where represents the number of beacons to be spread in round (i), and is the spreading window of round (i). The ISF function is defined as follows:
| Algorithm 1: Imbrical Spreading Function |
| 1: Input: NB and SW |
| 2: Output: Array of of the spreading rounds |
| 3: i = 1; |
| 4: While Do |
| 5: |
| 6:; |
| 7:; |
| 8:; |
| 9: |
| 10: end |
After executing the ISF function, the following information can be extracted. Let be the set of the highest occupancy possibilities of all the rounds, and be the number of STTs which receive (i) beacons, and finally, let be the set the occupied STTs which have the same number of beacons. They can be defined as follows:
Table 2 and Table 3 show the analytical results of an application example generated by the imbrical spreading function with (NB, SW) = (10,10) and (NB, SW) = (15,15), respectively. Furthermore, the function is implemented in MATLAB, and compared with a simulation of spreading beacons over a SW.

Table 2.
Application example of the imbrical spreading function where (NB, SW)=(10,10).

Table 3.
Application example of the imbrical spreading function where (NB, SW)=(15,15).
Figure 9 and Figure 10 present a comparison between the theoretical distribution of beacons extracted from Table 2 and Table 3, and some simulation results showing the real occupancy distribution status of the SW using the same spreading parameters. Due to the random nature of the simulation, it may bethat some distributions do not provide the exact same result as the ISF function; yet, in general, the ISF function and the simulations return similar results.
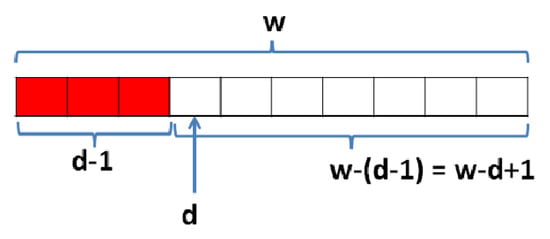
Figure 9.
Visualization of Equation (3).

Figure 10.
Comparison between the theoretical distribution of beacons using the ISF function and the simulated distribution where (NB, SW)=(10,10).
The information extracted from Table 2 is presented as follows:
- The
- , means that there are “4” STTs which receive “1” beacon.
- , means that there are “3” STTs which receive “2” beacons.
- means that there are “4” STTs with“1” beacon and “3” STTs with“2” beacons.
The information extracted from Table 3 is presented as follows:
- The
- , means there are “6” STTs which receive “1” beacon.
- , means there are “3” STTs which receive “2” beacons.
- , means there is“1” STT which receives “3” beacons.
- means that there are “4” STTs with“1” beacon and “3” STTs with“2” beacons.
5.3. The Successful Transmission Probability Calculation
The average successful transmission probability of the occupied STTs can be calculated by predicting the number of occupied STTs, as well as the number of beacons in each STT, as shown in the previous sections. Notice that successful transmission in each STT is considered in only two cases. The first if the STT contains only one beacon, so the vehicle gains access to the channel without contention, and, in the second case, if only one of them sends its beacon exclusively. This means that the backoff of the winner must be unique compared to the other contenders, and expires before them, otherwise a collision will occur. These phenomena can be modeled by Equation (11) defined as p(k, cw, d, v) [28], and visualized in Figure 9. It represents the probability that k vehicles generate beacon messages at the same time, and select the backoff counter from the contention window of w slots, and (d − 1) have passed from the count down before the first transmission attempt, and that v ≤ k vehicles transmit the backoff number d.
where:
- is the probability that a vehicle selects one of the backoff numbers d from w;
- is the probability of not selecting a backoff number lower than d which represents the interval [0, d−1];
- is the probability of not selecting slot d among w−d+1;
- represents all the possibilities where v among k vehicles can select d.
The probability of successful transmission will be equal to “one” if one and only one vehicle (v = 1) can select the backoff number d. Let be the random variation which counts the number of transmissions at one occupied STT among contenders. Therefore, represents the successful transmission probability of one occupied STT, as shown in Equation (12):
From this, the average successful transmission probability, denoted as Avg STP(NB, SW, CW), applies to all the occupied STTs during a SW interval with a given CW (contention window).It can be calculated using Equation (13):
where returns the number of all the occupied STTs generated from the first spreading round by the ISF function, is the set of the different highest occupancy possibilities of the different spreading rounds, and represents the number of STTs which receive exactly i beacons.
To ensure the correctness of the analytical study, the ISF function is implemented and compared with a simulation performed in MATLAB (see Figure 11). In this experiment, the simulated spreading of each configuration (NB, SW) is repeated 200 times, and the average result is taken. Note that, in all simulations and studies, the size of the SW is taken as being equal to the number of beacons (NB=SW). The results are presented in Figure 12, and they show a match between the two graphs which confirms that the analytical study is acceptable for general cases.
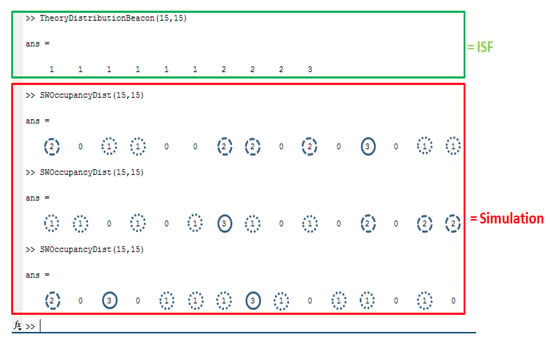
Figure 11.
Comparison between the theoretical distribution of beacons using the ISF function and the simulated distribution, where (NB, SW) = (15,15).
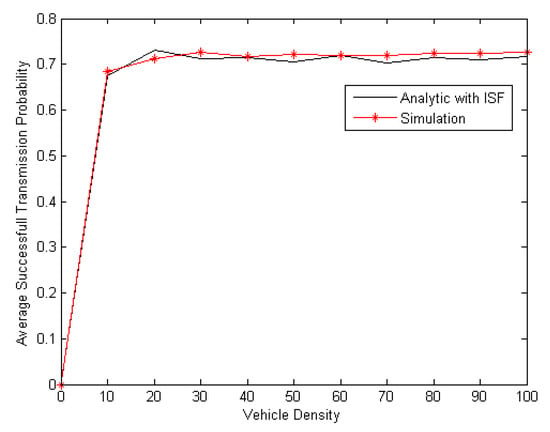
Figure 12.
Comparison between the simulation and the analytical results of the average successful transmission probability of the CSSA MAC protocol.
6. Discussion
The CSSA MAC considers the access scheme and the channel switching problem concurrently. The main advantage of CSSA MAC is the combination of the principles of two famous random medium access methods. In addition, it also has the advantage of being simple to implement over the physical layer of IEEE 802.11, and not requiring any additional overhead for the synchronization between contending vehicles.
It adopts the spreading technique used in S-ALOHA, consisting of assigning each beacon a random slot (STT). This decreases the “start-of-interval contention” problem, taking place when a high number of vehicles attempt to transmit at the same time (beginning of the CCH period). On the other hand, the CSSA MAC uses the contention period generated from a CW before sending, which is adopted in the CSMA method. Additionally, it tries to reduce the risk of collisions for the slotted method used by S-ALOHA, when two or more vehicles select the same STT and start transmitting. This way, the CSSA MAC allows beacons to be spread, thereby avoiding high contention when switching to the CCH channel, forcing them to instead contend at the beginning of each STT to minimize collisions.
The analytical study performed in this paper allows predicting the number of occupied virtual slots or STTs, which can be extracted from the SW size and the number of contender vehicles, and then estimate the number of beacons sent to each STT. The objective is to predict the probability of successful transmission of the CSSA MAC protocol; our simulation study confirms the correctness of the analytical prediction.
Adapting the two parameters, SW and CW, as a function from the number of contending stations has not been studied in this work. They have an important role in the performance of the proposed protocol as increasing their sizes has the side effect of lowering the efficiency in case of a low number of contending stations; implying that a high fraction of the channel time is wasted. On the other hand, decreasing them will increase the number of active vehicles per STT, which increases their chance of successful transmission. Therefore, in a scenario with a high number of vehicles, the collision risk increases.
Regarding the limitations of the CSSA MAC scheme, the fact that the CSSA MAC method works randomly means there is still a risk that several stations pick similar STT values. Therefore, it is likely that several vehicles will contend to access the channel on thesame STT. In this case, the protocol relies on the IEEE 802.11p CSMA/CA procedure to reduce the risk of simultaneous transmissions. When a vehicle succeeds in transmitting in a given STT, the other vehicles around should again contend to transmit in the following STT. Obviously, the higher the number of contending vehicles, the higher the collision risk will be.
The proposed solution does not add any additional signaling exchanges, to avoid the risk of hidden collisions, and the vehicle that successfully transmits in a given STT will not transmit through the same STT in the next CCH intervals. Thus, contention will take place at future occasions due to lack of a memory mechanism, which is a feature that allows to seamlessly adapt to the constantly changing conditions of vehicular environments.
7. Conclusions
The focus of this paper was to investigate, through analytical and simulation-based studies, the probability of a successful transmission of the CSSA MAC protocol previously proposed for vehicular networks with the objective to prevent the start-of-interval contention problem which occurs upon switching to the CCH.
To this end, the ISF is proposed to predict the number of occupied virtual slots (or STTs) from both the SW size and the number of contender vehicles, and then to estimate the number of beacons sent to each STT. Both simulation and analytical analysis revealed similar results, and highlight the effectiveness of the ISF compared to the legacy CSSA MAC solution by efficiently spreading beacons among the available slots.
As future work, the proposed scheme will be tested in scenarios where hidden collision issues take place, as well as emergent collisions caused by vehicular mobility. Obviously, dynamically determining the number of contending vehicles is a challenge that has to be addressed in order to adapt parameters SW and CW. Moreover, the proposal will be compared with other protocols in order to prove its superior performance.
As mentioned before, the arrival of 5G technology offers IoV communications the opportunity to deliver huge amounts of data, and to decrease the latency of transmission, being an ideal companion to extend IEEE-802.11p/ITS-G5 technologies, as the latter will focus on enabling direct communications in a flexible way without infrastructure requirements. Therefore, more work is necessary in order to highlight the limitations and advantages of each technology by emphasizing the most significant use-cases for each of them, highlighting how they can be optimally integrated and optimized.
Author Contributions
The authors contributed equally to this work. All authors have read and agreed to the published version of the manuscript.
Funding
This work is derived from the R&D project PID2021-122580NB-I00, funded by the MCIN/AEI/10.13039/501100011033 and the “ERDF A way of making Europe”.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
All implementation details, sources and data are available upon request from the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Yang, F.; Wang, S.; Li, J.; Liu, Z.; Sun, Q. An overview of Internet of Vehicles. China Commun. 2014, 11, 1–15. [Google Scholar] [CrossRef]
- Duo, R.; Wu, C.; Yoshinaga, T.; Zhang, J.; Ji, Y. SDN-based Handover Scheme in Cellular/IEEE 802.11p Hybrid Vehicular Networks. Sensors 2020, 20, 1082. [Google Scholar] [CrossRef] [PubMed]
- Wu, Q.; Xia, S.; Fan, Q.; Li, Z. Performance analysis of IEEE 802.11 p for continuous backoff freezing in IoV. Electronics 2019, 8, 1404. [Google Scholar] [CrossRef]
- Baiocchi, A.; Turcanu, I.; Lyamin, N.; Sjöberg, K.; Vinel, A. Age of Information in IEEE 802.11 p. In Proceedings of the 17th IFIP/IEEE International Symposium on Integrated Network Management (IM): ITAVT Workshop, Bordeaux, France, 17–21 May 2021. [Google Scholar]
- Tahir, M.N.; Katz, M. Performance evaluation of IEEE 802.11p, LTE and 5G in connected vehicles for cooperative awareness. Eng. Rep. 2021, 4, e12467. [Google Scholar] [CrossRef]
- Arena, F.; Pau, G.; Severino, A. A review on IEEE 802.11 p for intelligent transportation systems. J. Sens. Actuator Netw. 2020, 9, 22. [Google Scholar] [CrossRef]
- Puttagunta, H.; Agrawal, D.P. Performance of 802.11 P in VANET at 5G Frequencies for Different Channel Models. In Proceedings of the 2020 11th IEEE Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Virtual, 4–7 November 2020; IEEE: New York, NY, USA, 2020; pp. 0468–0472. [Google Scholar]
- Patil, A.; Muthuchidambaranathan, P.; Shet, N.S.V. Congestion control mechanisms in vehicular networks: A perspective on Internet of vehicles (IoV). In Autonomous and Connected Heavy Vehicle Technology; Academic Press: Cambridge, MA, USA, 2022. [Google Scholar]
- ETSI EN 302 637-2 Draft V.0.0.5; Intelligent Transport Systems (ITS); Vehicular Communications; Basic Set of Applications; Part 2: Specification of Cooperative Awareness Basic Service. ETSI: Alpes Maritimes, France, June 2012. Available online: https://2020.standict.eu/sites/default/files/ts_103301v010201p.pdf (accessed on 1 October 2022).
- ETSI TC ITS (2010) ETSI EN 302 665 V1.1.1 (2010–09); Intelligent Transport Systems (ITS); Communications Architecture. ETSI: Alpes Maritimes, France.
- Xiang, W.; Gozalvez, J.; Niu, Z.; Altintas, O.; Ekici, E. Wireless access in vehicular environments. EURASIP J. Wirel. Commun. Netw. 2009, 2009, 1–2. [Google Scholar] [CrossRef][Green Version]
- SAE Std. J2735; Dedicated Short Range Communications (DSRC) Message Se Dictionary. DSRC Committee. ETSI: Alpes Maritimes, France, 2009. [CrossRef]
- IEEE 802.11p/D10.0; Part11: Wireless LAN Medium Access Control (MAC) and the Physical Layer (PHY) Specifications: Amendment 7: Wireless Access in Vehicular Environment, Draft 7.0. IEEE: New York, NY, USA, 2010. Available online: https://ieeexplore.ieee.org/servlet/opac?punumber=8624658 (accessed on 26 November 2022).
- IEEE Std 1609.4TM-2010; IEEE Standard for Wireless Access in Vehicular Environments (WAVE)- Multi-channel Operation. IEEE Vehicular Technology Society. IEEE: New York, NY, USA, 2010.
- Toutouh, J.; Alba, E. Distributed fair rate congestion control for vehicular networks. In Proceedings of the Distributed Computing and Artificial Intelligence, 13th International Conference, Sevilla, Spain, 1–3 June 2016; Springer: Cham, Switzerland, 2016; pp. 433–442. [Google Scholar]
- Ahmad, A.; Doughan, M.; Mougharbel, I.; Marot, M. A new adapted back-off scheme for broadcasting on IEEE 1609.4 control channel in VANET. In Proceedings of the 2012 The 11th Annual Mediterranean Ad Hoc Networking Workshop (Med-Hoc-Net), Ayia Napa, Cyprus, 19–22 June 2012; IEEE: New York, NY, USA, 2012; pp. 9–15. [Google Scholar]
- Ouladdjedid, L.K.; Yagoubi, M.B.; Menouar, H. CSSA MAC: Carrier sense with slotted Aloha multiple access MAC in vehicular network. Int. J. Veh. Inf. Commun. Syst. 2018, 3, 336–354. [Google Scholar] [CrossRef]
- Abramson, N. The Aloha System: Another alternative for computer communications. In Proceedings of the November 17–19, 1970, Fall Joint Computer Conference (AFIPS ‘70 (Fall)), Houston, TX, USA, 17–19 November 1970; ACM: New York, NY, USA; pp. 281–285. [Google Scholar] [CrossRef]
- Rossi, G.V.; Leung, K.K. Optimised CSMA/CA protocol for safety messages in vehicular ad-hoc networks. In Proceedings of the 2017 IEEE Symposium on Computers and Communications (ISCC), Heraklion, Greece, 3–6 July 2017; IEEE: New York, NY, USA, 2017; pp. 689–696. [Google Scholar]
- Taherkhani, N.; Pierre, S. Prioritizing and scheduling messages for congestion control in vehicular ad hoc networks. Comput. Netw. 2016, 108, 15–28. [Google Scholar] [CrossRef]
- Torrent-Moreno, M.; Mittag, J.; Santi, P.; Hartenstein, H. Vehicle-to-vehicle communication: Fair transmit power control for safety-critical information. IEEE Trans. Veh. Technol. 2009, 58, 3684–3703. [Google Scholar] [CrossRef]
- Mertens, Y.; Wellens, M.; Mahonen, P. Simulation-based performance evaluation of enhanced broadcast schemes for IEEE 802.11-based vehicular networks. In Proceedings of the VTC Spring 2008—IEEE Vehicular Technology Conference, Marina Bay, Singapore, 11–14 May 2008; pp. 3042–3046. [Google Scholar] [CrossRef]
- Bai, F.; Stancil, D.D.; Krishnan, H. Toward understanding characteristics of dedicated short range communications (DSRC) from a perspective of vehicular network engineers. In Proceedings of the Sixteenth Annual International Conference on Mobile Computing and Networking, New York, NY, USA, 20 September 2010; ACM: New York, NY, USA, 2010; pp. 329–340. [Google Scholar] [CrossRef]
- Yang, Q.; Xing, S.; Xia, W.; Shen, L. Modelling and performance analysis of dynamic contention window scheme for periodic broadcast in vehicular ad hoc networks. IET Commun. 2015, 9, 1347–1354. [Google Scholar] [CrossRef]
- Chrysostomou, C.; Djouvas, C.; Lambrinos, L. Contention window adaptation for broadcast beaconing in vehicular ad hoc networks. In Proceedings of the Wireless Communications and Mobile Computing Conference (IWCMC), Nicosia, Cyprus, 4–8 August 2014; IEEE: New York, NY, USA; pp. 1039–1044. [Google Scholar]
- Wu, Y.J.; Wang, W.S.; Hwang, W.S. A modified backoff algorithm for safety message delivery in IEEE 802.11 p/WAVE networks. In Proceedings of the 2014 International Conference on Computer, Information and Telecommunication Systems (CITS), Jeju, Republic of Korea, 7–9 July 2014; IEEE: New York, NY, USA, 2014; pp. 1–5. [Google Scholar]
- Dang, D.N.M.; Hong, C.S.; Lee, S.; Huh, E.-N. An Efficient and Reliable MAC in VANETs. IEEE Commun. Lett. 2014, 18, 616–619. [Google Scholar] [CrossRef]
- Campolo, C.; Vinel, A.; Molinaro, A.; Koucheryavy, Y. Modeling Broadcasting in IEEE 802.11p/WAVE Vehicular Networks. IEEE Commun. Lett. 2010, 15, 199–201. [Google Scholar] [CrossRef]
- Stanica, R.; Chaput, E.; Beylot, A.L. Enhancements of IEEE 802.11 p protocol for access control on a VANET control channel. In Proceedings of the 2011 IEEE International Conference on Communications (ICC), Kyoto, Japan, 5–9 June 2011; IEEE: New York, NY, USA, 2011; pp. 1–5. [Google Scholar]
- Wang, Y.; Ahmed, A.; Krishnamachari, B.; Psounis, K. IEEE 802.11 p performance evaluation and protocol enhancement. In Proceedings of the ICVES 2008. IEEE International Conference on Vehicular Electronics and Safety, Columbus, OH, USA, 22–24 September 2008; IEEE: New York, NY, USA, 2008; pp. 317–322. [Google Scholar]
- Stanica, R.; Chaput, E.; Beylot, A.-L. Reverse back-off mechanism for safety vehicular ad hoc networks. Ad Hoc Networks 2014, 16, 210–224. [Google Scholar] [CrossRef]
- Shah, S.A.A.; Ahmed, E.; Xia, F.; Karim, A.; Shiraz, M.; Noor, R.M. Adaptive Beaconing Approaches for Vehicular Ad Hoc Networks: A Survey. IEEE Syst. J. 2016, 12, 1263–1277. [Google Scholar] [CrossRef]
- Rawat, D.B.; Popescu, D.C.; Yan, G.; Olariu, S. Enhancing VANET performance by joint adaptation of transmission power and contention window size. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 1528–1535. [Google Scholar] [CrossRef]
- Kloiber, B.; Harri, J.; Strang, T.; Sand, S. Bigger is better—Combining contention window adaptation with geo-based backoff generation in dsrc networks. In Proceedings of the 2013 International Conference on Connected Vehicles and Expo (ICCVE), Vienna, Austria, 3–7 November 2014; pp. 227–233. [Google Scholar] [CrossRef]
- Chaabouni, N.; Hafid, A.; Sahu, P.K. A collision-based beacon rate adaptation scheme (CBA) for VANETs. In Proceedings of the 2013 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Chennai, India, 15–18 December 2013; IEEE: New York, NY, USA; pp. 1–6. [Google Scholar]
- Amer, H.M.; Hadi, E.A.; Shihab, L.G.; Al Mohammed, H.H.; Khami, M.J. Hybrid power control and contention window adaptation for channel congestion problem in internet of vehicles network. Int. J. Electr. Comput. Eng. (IJECE) 2022, 12, 497–505. [Google Scholar] [CrossRef]
- Alonso Gómez, A. Survey on Decentralized Congestion Control Methods for Vehicular Communication; Elsevier: Amsterdam, The Netherlands, 2022. [Google Scholar]
- Lyamin, Q.N.; Deng, A. Vinel, Study of the platooning fuel efficiency under ETSI ITS-G5 communications. In Proceedings of the 2016 IEEE 19th International Conference on Intelligent Transportation Systems, ITSC, Rio de Janeiro, Brazil, 1–4 November 2016; pp. 551–556. [Google Scholar]
- Bansal, G.; Kenney, J.; Rohrs, C. LIMERIC: A linear adaptive message rate algorithm for DSRC congestion control. IEEE Trans. Veh. Technol. 2013, 62, 4182–4197. [Google Scholar] [CrossRef]
- Bansal, G.; Lu, H.; Kenney, J.; Poellabauer, C. EMBARC: Error Model Based Adaptive Rate Control for Vehicle-to-Vehicle Communications; ACM Press: New York, NY, USA, 2013; p. 41. [Google Scholar]
- Balador, A.; Cinque, E.; Pratesi, M.; Valentini, F.; Bai, C.; Gómez, A.A.; Mohammadi, M. Survey on decentralized congestion control methods for vehicular communication. Veh. Commun. 2021, 33, 100394. [Google Scholar] [CrossRef]
- Bilstrup, K.; Uhlemann, E.; Ström, E.G.; Bilstrup, U. On the Ability of the IEEE 802.11 p and STDMA to Provide Predictable Channel Access. In Proceedings of the16th World Congress on Intelligent Transport Systems (ITS), Stockholm, Sweden, 21–25 September 2009; p. 10. [Google Scholar]
- Zhao, H.; Du, A.; Zhu, H.; Li, D.; Liu, N. A self-adaptive back-off optimization scheme based on beacons probability prediction for vehicle Ad-Hoc networks. China Commun. 2016, 13, 132–138. [Google Scholar] [CrossRef]
- Alhameed, M.; Mahgoub, I. VANET Adaptive Beaconing Based on Fuzzy Logic. In Proceedings of the 2017 IEEE 15th Intl Conf on Dependable, Autonomic and Secure Computing, 15th Intl Conf on Pervasive Intelligence and Computing, 3rd Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Orlando, FL, USA, 6–10 November 2017; IEEE: New York, NY, USA, 2017; pp. 736–743. [Google Scholar]
- Farias, P.V.G.; Bordim, J.L.; Caetano, M.F. A Density-Based Congestion Avoidance Protocol for Strict Beaconing Requirements in VANETs. In Proceedings of the 2019 Seventh International Symposium on Computing and Networking (CANDAR), Nagasaki, Japan, 25–28 November 2019; IEEE: New York, NY, USA, 2019; pp. 130–136. [Google Scholar]
- Zheng, H.; Wang, H. An optimized MAC Protocol for Safety Messages9 Broadcasting in VANETs. In Proceedings of the 2019 5th International Conference on Transportation Information and Safety (ICTIS), Liverpool, UK, 14–17 July 2019; IEEE: New York, NY, USA, 2019; pp. 833–838. [Google Scholar]
- Chang, S.W.; Cha, J.; Lee, S.S. Adaptive EDCA mechanism for vehicular ad-hoc network. In Proceedings of the International Conference on Information Network, Bali, Indonesia, 1–3 February 2012; IEEE: New York, NY, USA, 2012; pp. 379–383. [Google Scholar]
- Torgunakov, V.; Loginov, V.; Khorov, E. A Study of the Impact of the Contention Window on the Performance of IEEE 802.11 bd Networks with Channel Bonding. In Proceedings of the 2021 International Conference Engineering and Telecommunication (En&T), Dolgoprudny, Russian Federation, 24–25 November 2021; IEEE: New York, NY, USA, 2021; pp. 1–5. [Google Scholar]
- Dou, Z.; Zhou, X.; Yang, Q.; Yang, L.; Tian, J. Improvement and Performance Evaluation of IEEE 802.11p Protocol in Dense Scenario of VANET. Mob. Inf. Syst. 2022, 2022, 1–19. [Google Scholar] [CrossRef]
- Mohammed, M.A.; Shareef, S.M.; Ghafoor, K.Z. Adaptive and Optimized Control Channel Utilization in Vehicular Ad Hoc Networks. Wirel. Commun. Mob. Comput. 2022, 2022, 1–12. [Google Scholar] [CrossRef]
- Septa, N. The Performance Analysis of 802.11 p with Cooperative Communication and Dynamic Contention Window. Res. Sq. 2022. [Google Scholar] [CrossRef]
- Jibukumar, M.G. An Enhancement for IEEE 802.11p to Provision Quality of Service with Context Aware Channel Access for the Forward Collision Avoidance Application in Vehicular Ad Hoc Network. Sensors 2021, 21, 6937. [Google Scholar] [CrossRef]
- Huang, C.-L.; Fallah, Y.P.; Sengupta, R.; Krishnan, H. Adaptive intervehicle communication control for cooperative safety systems. IEEE Netw. 2010, 24, 6–13. [Google Scholar] [CrossRef]
- Cheng, B.; Rostami, A.; Gruteser, M.; Lu, H.; Kenney, J.; Bansal, G. Evolution of vehicular congestion control without degrading legacy vehicle performance. In Proceedings of the 2016 IEEE 17th International Symposium on a World of Wireless, Mobile and Multimedia Networks, WoWMoM, Coimbra, Portugal, 21–24 June 2016; pp. 1–6. [Google Scholar]
- Spyrou, E.D.; Vlachos, E.; Stylios, C. Game-Theoretic Power and Rate Control in IEEE 802.11p Wireless Networks. Electronics 2022, 11, 1618. [Google Scholar] [CrossRef]
- Kenney, J.B.; Bansal, G.; Rohrs, C.E. LIMERIC: A linear message rate control algorithm for vehicular DSRC systems. In Proceedings of the Eighth ACM International Workshop on Vehicular Inter-Networking, Las Vegas, NV, USA, 23 September 2011; pp. 21–30. [Google Scholar]
- Cheng, B.; Rostami, A.; Gruteser, M.; Kenney, J.; Bansal, G.; Sjoberg, K. Performance evaluation of a mixed vehicular network with CAM-DCC and LIMERIC vehicles. In Proceedings of the 2015 IEEE 16th International Symposium on a World of Wireless, Mobile and Multimedia Networks, WoWMoM, Boston, MA, USA, 14–17 June 2015; pp. 1–6. [Google Scholar]
- Tielert, T.; Jiang, D.; Chen, Q.; Delgrossi, L.; Hartenstein, H. Design methodology and evaluation of rate adaptation based congestion control for Vehicle Safety Communications. In Proceedings of the 2011 IEEE Vehicular Networking Conference, VNC, New York, NY, USA, 16–18 December 2011; pp. 116–123. [Google Scholar]
- Bansal, G.; Kenney, J. Achieving weighted-fairness in message rate-based congestion control for DSRC systems. In Proceedings of the 2013 IEEE 5th International Symposium on Wireless Vehicular Communications, WiVeC, Dresden, Germany, 2–3 June 2013; pp. 1–5. [Google Scholar]
- Lorenzen, T.; Garrosi, M. Achieving Global Fairness at Urban Intersections Using Cooperative DSRC Congestion Control; ACM Press: New York, NY, USA, 2016; pp. 52–59. [Google Scholar]
- Egea-Lopez, E.; Pavon-Marino, P. Distributed and Fair Beaconing Rate Adaptation for Congestion Control in Vehicular Networks. IEEE Trans. Mob. Comput. 2016, 15, 3028–3041. [Google Scholar] [CrossRef]
- Lorenzen, T. SWeRC: Self-weighted semi-cooperative DSRC congestion control based on LIMERIC. In Proceedings of the 2017 IEEE 86th Vehicular Technology Conference, VTCFall, Toronto, ON, Canada, 24–27 September 2017; pp. 1–7. [Google Scholar]
- Rostami, A.; Cheng, B.; Bansal, G.; Sjoberg, K.; Gruteser, M.; Kenney, J.B. Stability Challenges and Enhancements for Vehicular Channel Congestion Control Approaches. IEEE Trans. Intell. Transp. Syst. 2016, 17, 2935–2948. [Google Scholar] [CrossRef]
- Math, C.; Ozgur, A.; Groot, S.; Li, H. Data rate based congestion control in V2V communication for traffic safety applications. In Proceedings of the 2015 IEEE Symposium on Communications and Vehicular Technology in the Benelux, SCVT, Luxembourg, 24 November 2015; pp. 1–6. [Google Scholar]
- Math, C.; Li, H.; Groot, S.; Niemegeers, I. Fair decentralized data-rate congestion control for V2V communications. In Proceedings of the 2017 24th International Conference on Telecommunications, ICT, Limassol, Cyprus, 3–5 May 2017; pp. 1–7. [Google Scholar]
- Das, S.; Barman, S.; Bhunia, S. Performance analysis of IEEE 802.11 rate adaptation algorithms categorized under rate controlling parameters. In Proceedings of the 2014 International Conference on Information and Communication Technology for Competitive Strategies, Udaipur, India, 14–16 November 2014; ACM: New York, NY, USA, 2014. [Google Scholar]
- Segata, M.; Bloessl, B.; Joerer, S.; Sommer, C.; Gerla, M.; Cigno, R.L.; Dressler, F. Toward Communication Strategies for Platooning: Simulative and Experimental Evaluation. IEEE Trans. Veh. Technol. 2015, 64, 5411–5423. [Google Scholar] [CrossRef]
- Dayal, A.; Colbert, E.; Marojevic, V.; Reed, J. Risk Controlled Beacon Transmission in V2V Communications. In Proceedings of the 2019 IEEE 89th Vehicular Technology Conference (VTC2019-Spring), Kuala Lumpur, Malaysia, 28 April–1 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Karamad, E.; Ashtiani, F. A modified 802.11-based MAC scheme to assure fair access for vehicle-to-roadside communications. Comput. Commun. 2008, 31, 2898–2906. [Google Scholar] [CrossRef]
- Park, Y.; Kim, H. Collision Control of Periodic Safety Messages With Strict Messaging Frequency Requirements. IEEE Trans. Veh. Technol. 2012, 62, 843–852. [Google Scholar] [CrossRef]
- Batsuuri, T.; Bril, R.J.; Lukkien, J.J. Performance and fairness in VANETs. In Proceedings of the 29th International Conference on Consumer Electronics (ICCE 2011), Las Vegas, NV, USA, 9–12 January 2011; IEEE: New York, NY, USA, 2011; pp. 637–638. [Google Scholar] [CrossRef]
- Balador, A.; Böhm, A.; Calafate, C.T.; Cano, J.C. A reliable token-based MAC protocol for V2V communication in urban VANET. In Proceedings of the 2016 IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Valencia, Spain, 4–8 September 2016; IEEE: New York, NY, USA, 2016; pp. 1–6. [Google Scholar]
- Li, S.; Liu, Y.; Wang, J.; Sun, Z. SCMAC: A Slotted-Contention-Based Media Access Control Protocol for Cooperative Safety in VANETs. IEEE Internet Things J. 2020, 7, 3812–3821. [Google Scholar] [CrossRef]
- Zhang, H.; Yang, N.; Huangfu, W.; Long, K.; Leung, V.C.M. Power Control Based on Deep Reinforcement Learning for Spectrum Sharing. IEEE Trans. Wirel. Commun. 2020, 19, 4209–4219. [Google Scholar] [CrossRef]
- Spantideas, S.T.; Giannopoulos, A.E.; Kapsalis, N.C.; Kalafatelis, A.; Capsalis, C.N.; Trakadas, P. Joint energy-efficient and throughput-sufficient transmissions in 5G cells with deep Q-learning. In Proceedings of the 2021 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), Athens, Greece, 7–10 September 2021; IEEE: New York, NY, USA, 2021; pp. 265–270. [Google Scholar]
- Yang, H.; Xie, X. An actor-critic deep reinforcement learning approach for transmission scheduling in cognitive internet of things systems. IEEE Syst. J. 2019, 14, 51–60. [Google Scholar] [CrossRef]
- Dupuis, P.; Zhang, J.X.; Whiting, P. Refined Large Deviation Asymptotics for the Classical Occupancy Problem. Methodol. Comput. Appl. Probab. 2006, 8, 467–496. [Google Scholar] [CrossRef][Green Version]
- Feller, W. An Introduction to Probability Theory and Its Applications; John Wiley & Sons: Hoboken, NJ, USA, 2008; Volume 1. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).