LACE: Low-Cost Access Control Based on Edge Computing for Smart Buildings
Abstract
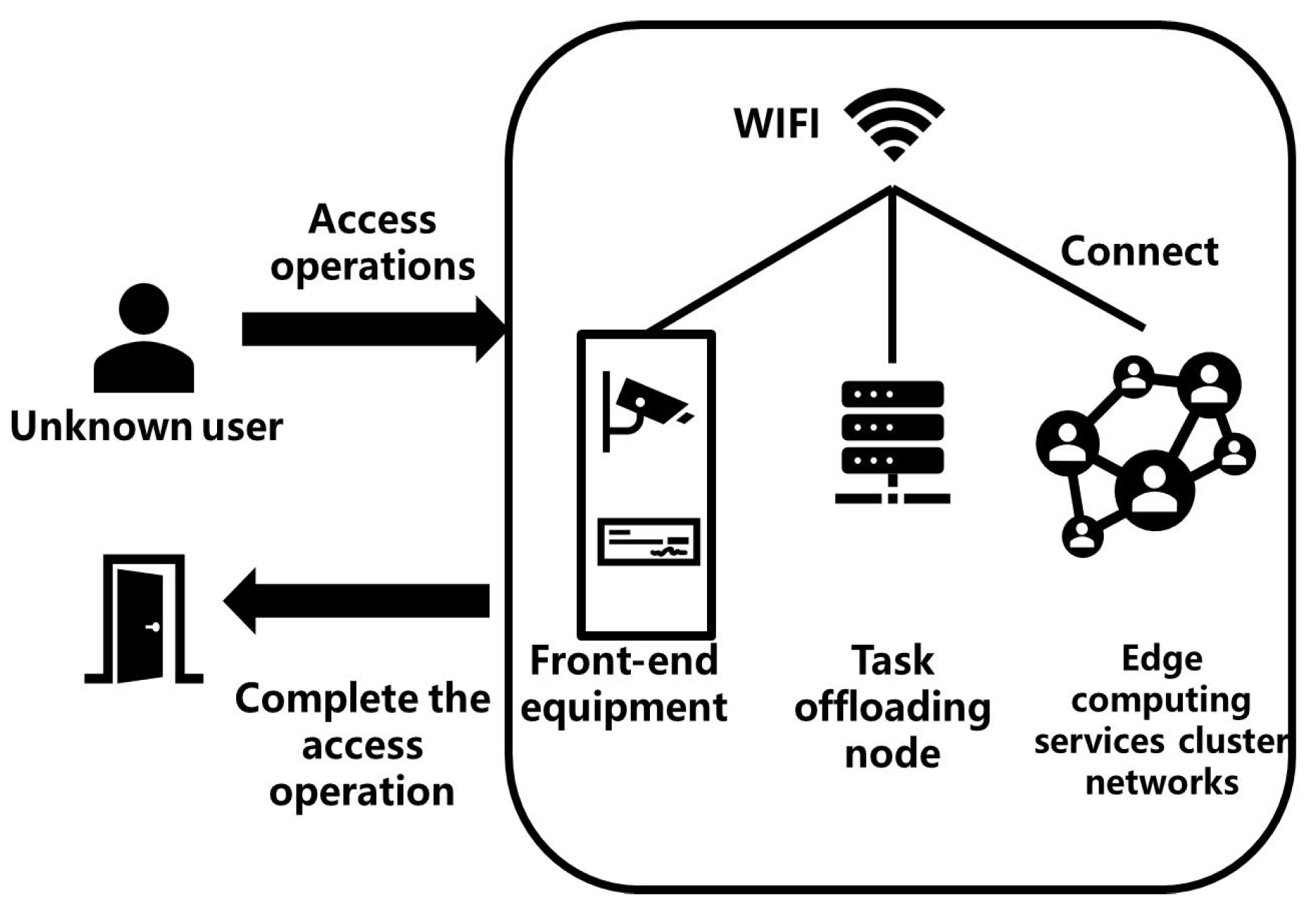
1. Introduction
- There is the problem of insufficient local bandwidth and high latency caused by network congestion.
- There are specific privacy and security issues with the cloud platform solution, as the access control system may involve private premises data.
2. Related Work
2.1. Traditional Intelligent Access Control System Solutions
2.2. Existing Edge-Based Solutions
2.3. Main Contributions
- High compatibility, traditional intelligent home gateways or other devices are bound to their specific operating system. There are specific differences when different types of IoT devices exist in the environment, i.e., multiple other gateways are needed for service provision, but the current smartphone operating system is more uniform, with a significant market share occupied by Android, iOS, and Hongxing. Using a smartphone operating system as the underlying system development can significantly provide the compatibility of the service system.
- Low hardware device requirements, compared to other solutions. This system hardly needs to deploy additional computing devices and provides services entirely by utilizing existing idle computing resources.
3. Solution Design
- The ability to capture and store biometric data of different users, such as faces and gestures.
- The ability to process, analyze, and differentiate data from different users so as to return different results for different users with different feature information, such as granting or denying access.
- The ability to transmit data securely and reliably between different terminals.
- The ability to perform self-processing and recovery from some task exceptions.
3.1. System Overview
3.2. Front-End IoT Device Design
- Capture and briefly save image data.
- Exchange data with task offloading nodes via WiFi, Bluetooth, or Zigbee technology.
- Execute the command issued by the mobile edge server after completing the calculation and perform the granting or denying access for the person requesting access.
- 1
- The infrared radar sensor detects an incoming object, and the camera acquires image data.
- 2
- The task scheduler sends a task request to the task offloading node via the communication module.
- 3
- The task scheduler acquires data from the sensor cluster via the communication module and submits the task data to the designated set of mobile edge servers based on the content returned by the task offloading node.
- 4
- Based on the results returned by the set of mobile edge servers, an operation command is sent to the operation execution layer.
- 5
- If the operation is successful, the task is completed; Otherwise, the same process is repeated.
3.3. Edge-Side Design
3.3.1. Communication Module
| Algorithm 1: Data transfer algorithm |
 |
3.3.2. Computing Service Module
3.4. Task Offloading Module Design
4. Implementation
4.1. IoT Front-End Device Implementation
4.2. Communication Module
4.3. Calculation Module
4.3.1. Face Detection Module
4.3.2. Target Detection Module
4.3.3. Gesture Recognition Module
4.4. UI Module
4.5. Recognition Effect Display
5. Evaluation
Shortcomings and Future Directions for Improvement
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Belani, D.; Makwana, A.H.; Pitroda, J.; Vyas, C.M. Intelligent building new era of todays world. In Proceedings of the Trends and Challenges of Civil Engineering in Todays Transforming World, Surat, India, 17 March 2014. [Google Scholar]
- Li, W.; Xue, K.; Xue, Y.; Hong, J. TMACS: A Robust and Verifiable Threshold Multi-Authority Access Control System in Public Cloud Storage. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 18. [Google Scholar] [CrossRef]
- Mon, E.E.; Naing, T.T. The privacy-aware access control system using attribute-and role-based access control in private cloud. In Proceedings of the 2011 4th IEEE International Conference on Broadband Network and Multimedia Technology, Shenzhen, China, 28–30 October 2011; pp. 24–36. [Google Scholar]
- Li, Q.; Ma, J.; Li, R.; Liu, X.; Xiong, J.; Chen, D. Secure, efficient and revocable multi-authority access control system in cloud storage. Comput. Secur. 2016, 59, 45–59. [Google Scholar] [CrossRef]
- Loukatos, D.; Lygkoura, K.A.; Maraveas, C.; Arvanitis, K.G. Enriching IoT Modules with Edge AI Functionality to Detect Water Misuse Events in a Decentralized Manner. Sensors 2022, 22, 4874. [Google Scholar] [CrossRef] [PubMed]
- Yang, S.U.; Shu, J.; Zhang, Z.; Software, S.O. Intelligent Access Control System based on Bluetooth Technology. Intell. Comput. Appl. 2014, 2, 9–17. [Google Scholar]
- Turner, V.; Reinsel, D.; Gantz, J.F.; Minton, S. The Digital Universe of Opportunities: Rich Data and Increasing Value of the Internet of Things. J. Telecommun. Digit. Econ. 2014, 2, 19–29. [Google Scholar]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A Survey on Mobile Edge Computing: The Communication Perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef]
- Wang, R.; Tsai, W.T.; He, J.; Liu, C.; Li, Q.; Deng, E. A Video Surveillance System Based on Permissioned Blockchains and Edge Computing. In Proceedings of the 2019 IEEE International Conference on Big Data and Smart Computing (BigComp), Kyoto, Japan, 27 February–22 March 2019; pp. 19–24. [Google Scholar]
- Yu, Z.; Hu, J.; Min, G.; Zhao, Z.; Miao, W.; Hossain, M.S. Mobility-aware proactive edge caching for connected vehicles using federated learning. IEEE Trans. Intell. Transp. Syst. 2021, 22, 5341–5351. [Google Scholar] [CrossRef]
- Cong, R.; Zhao, Z.; Min, G.; Feng, C.; Jiang, Y. EdgeGO: A mobile resource-sharing framework for 6g edge computing in massive IoT systems. IEEE Internet Things J. 2021, 9, 12–13. [Google Scholar] [CrossRef]
- Soyata, T.; Muraleedharan, R.; Funai, C.; Kwon, M.; Heinzelman, W. Cloud-Vision: Real-time face recognition using a mobile-cloudlet-cloud acceleration architecture. In Proceedings of the Computers & Communications, Amsterdam, The Netherlands, 17 March 2012; p. 18. [Google Scholar]
- Tang, K.S.; Man, K.F.; Chen, G.; Kwong, S. An optimal fuzzy PID controller. IEEE Trans. Ind. Electron. 2001, 48, 757–765. [Google Scholar] [CrossRef]
- Zhou, G.; Birdwell, J.D. PID autotuner design using machine learning. In Proceedings of the Computer-Aided Control System Design, Napa, CA, USA, 17–19 March 1992; pp. 12–22. [Google Scholar]
- Strm, K.J.; Hgglund, T. PID controllers: Theory, Design and Tuning. Instrum. Soc. Am. Res. Triangle Park 1995, 23, 26. [Google Scholar]
- Ji-Ai, H.E.; Zheng-Hua, D.A. Simulation of BP Neural PID Controller. J. Gansu Educ. Coll. Sci. Ed. 2005, 56, 19–33. [Google Scholar]
- Perkins, C.E.; Jagannadh, T. DHCP for mobile networking with TCP/IP. In Proceedings of the IEEE Symposium on Computers & Communications, Alexandria, Egypt, 27–29 July 1995; pp. 5–7. [Google Scholar]
- Wang, J.; Hu, J.; Min, G.; Zomaya, A.Y.; Georgalas, N. Fast adaptive task offloading in edge computing based on meta reinforcement learning. IEEE Trans. Parallel Distrib. Syst. 2021, 32, 242–253. [Google Scholar] [CrossRef]
- Banegas, D.M.; Gracià, R.S. Offloading personal security applications to the Network Edge: A mobile user case scenario. In Proceedings of the Wireless Communications & Mobile Computing Conference, Paphos, Cyprus, 5–9 September 2016; pp. 22–40. [Google Scholar]
- Kan, T.Y.; Yao, C.; Wei, H.Y. QoS-Aware Mobile Edge Computing System: Multi-Server Multi-User Scenario. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–16. [Google Scholar]
- Ma, L.; Zhuo, Y.; Liao, K.; Liu, S.; Qiao, J.; Han, Z.; Wang, J. Development and research of digital campus system based on android. Int. J. Smart Home 2014, 8, 25–36. [Google Scholar] [CrossRef]
- Wisanto, A.A.; Triwidiastuti, F.; Priyadi, P.R. Implementasi Sekuritas pada Web Service dengan Menggunakan Autentifikasi OkHttp pada Library Retrofit di Piranti Mobile. JI-Tech 2020, 16, 35–41. [Google Scholar]
- Belkhir, A.; Abdellatif, M.; Tighilt, R.; Moha, N.; Guéhéneuc, Y.G.; Beaudry, É. An observational study on the state of REST API uses in android mobile applications. In Proceedings of the 2019 IEEE/ACM 6th International Conference on Mobile Software Engineering and Systems (MOBILESoft), Montréal, ON, Canada, 25–26 May 2019; pp. 66–75. [Google Scholar]
- Schroff, F.; Kalenichenko, D.; Philbin, J. Facenet: A unified embedding for face recognition and clustering. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Boston, MA, USA, 7–12 June 2015; pp. 815–823. [Google Scholar]
- Ding, H.; Zhou, S.K.; Chellappa, R. FaceNet2ExpNet: Regularizing a Deep Face Recognition Net for Expression Recognition. In Proceedings of the 2017 12th IEEE International Conference on Automatic Face & Gesture Recognition (FG 2017), Washington, DC, USA, 30 May–3 June 2017; pp. 44–47. [Google Scholar]
- Wu, Z.; Chen, X.; Gao, Y.; Li, Y. Rapid Target Detection in High Resolution Remote Sensing Images Using YOLO Model. Isprs-Int. Arch. Photogramm. Remote Sens. Spat. Inf. Sci. 2018, 42, 1915–1920. [Google Scholar] [CrossRef]
- Howard, A.G.; Zhu, M.; Chen, B.; Kalenichenko, D.; Wang, W.; Weyand, T.; Andreetto, M.; Adam, H. MobileNets: Efficient Convolutional Neural Networks for Mobile Vision Applications. arXiv 2017, arXiv:1704.04861. [Google Scholar]
- Loukatos, D.; Arvanitis, K.G. Multi-Modal Sensor Nodes in Experimental Scalable Agricultural IoT Application Scenarios. In IoT-Based Intelligent Modelling for Environmental and Ecological Engineering; Springer: Berlin/Heidelberg, Germany, 2021; pp. 101–128. [Google Scholar]
- Hu, B.; Tian, X.; Yang, C.; Jiang, W.; Dong, S.; Chen, M.; Chen, W.; Chen, S.; Weng, Z. A dynamic resource chain task unloading method based on improved greedy algorithm. J. Phys. Conf. Ser. 2021, 1883, 23–25. [Google Scholar]








| Method | Product | Core Device | Specification | Latency (5 KB) | Cost($/Month) |
|---|---|---|---|---|---|
| Cloud computing | Huawei cloud | General computing plus C6 | 8-cores 32 G | 200 ms | 171.74 |
| Edge gateway | Yuanan IoT | COTX-SA | 256-cores 32 GB | 215 ms | >388.55 |
| LACE | LACE | Huawei P30 | 8-cores 32 GB | 70 ms | 0 |
| Distance (m) | CPU Load (%) | Movement Speed (km/h) | Average Computing Time (ms) |
|---|---|---|---|
| 0 | 0 | 0 | 90 |
| 0 | 50 | 0 | 3985 |
| 0 | 100 | 0 | 4760 |
| 5 | 0 | 0 | 436 |
| 5 | 50 | 0 | 3228 |
| 5 | 100 | 0 | 5437 |
| 15 | 0 | 0 | 4275 |
| 15 | 50 | 0 | 5746 |
| 15 | 100 | 0 | 6690 |
| <10 | 0 | 5 | 106 |
| <10 | 100 | 5 | 4437 |
| <10 | 0 | 10 | 123 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huang, H.; Tan, H.; Xu, X.; Zhang, J.; Zhao, Z. LACE: Low-Cost Access Control Based on Edge Computing for Smart Buildings. Electronics 2023, 12, 412. https://doi.org/10.3390/electronics12020412
Huang H, Tan H, Xu X, Zhang J, Zhao Z. LACE: Low-Cost Access Control Based on Edge Computing for Smart Buildings. Electronics. 2023; 12(2):412. https://doi.org/10.3390/electronics12020412
Chicago/Turabian StyleHuang, Haifeng, Hongmin Tan, Xianyang Xu, Jianfei Zhang, and Zhiwei Zhao. 2023. "LACE: Low-Cost Access Control Based on Edge Computing for Smart Buildings" Electronics 12, no. 2: 412. https://doi.org/10.3390/electronics12020412
APA StyleHuang, H., Tan, H., Xu, X., Zhang, J., & Zhao, Z. (2023). LACE: Low-Cost Access Control Based on Edge Computing for Smart Buildings. Electronics, 12(2), 412. https://doi.org/10.3390/electronics12020412







