Author Contributions
Conceptualization, G.B.S.; methodology, Y.M.A.; software, Y.M.A.; validation, G.B.S., Y.M.A., and A.B.M.; experiment and analysis, Y.M.A.; writing—original draft preparation, G.B.S. and Y.M.A.; writing—review and editing, G.B.S., Y.M.A., and A.B.M.; supervision, A.B.M. All authors have read and agreed to the published version of the manuscript.
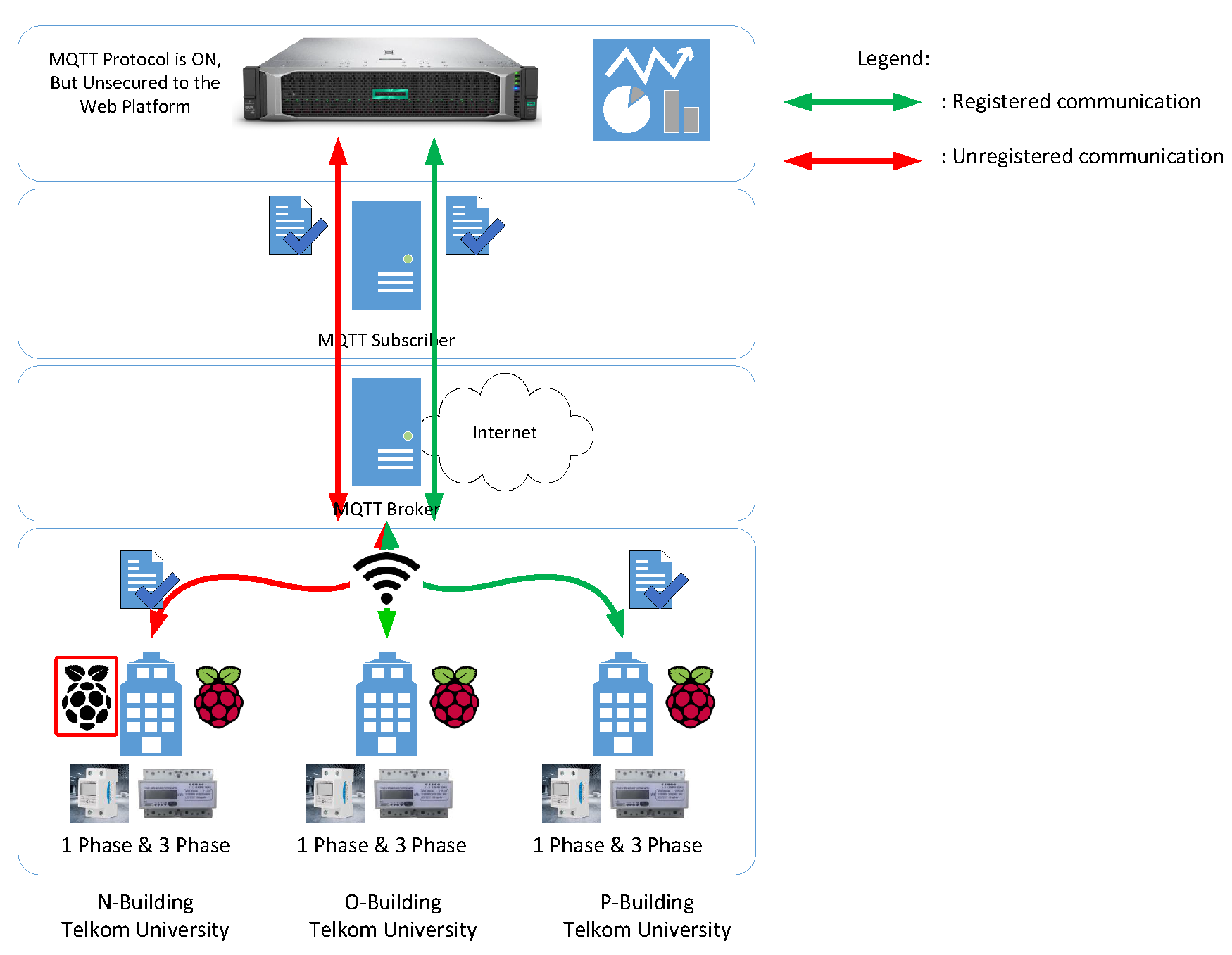
Figure 1.
IoT Architecture for ESM.
Figure 1.
IoT Architecture for ESM.
Figure 2.
The adversary’s perspective.
Figure 2.
The adversary’s perspective.
Figure 3.
Network sniffing result on the conventional topology in 1-phase.
Figure 3.
Network sniffing result on the conventional topology in 1-phase.
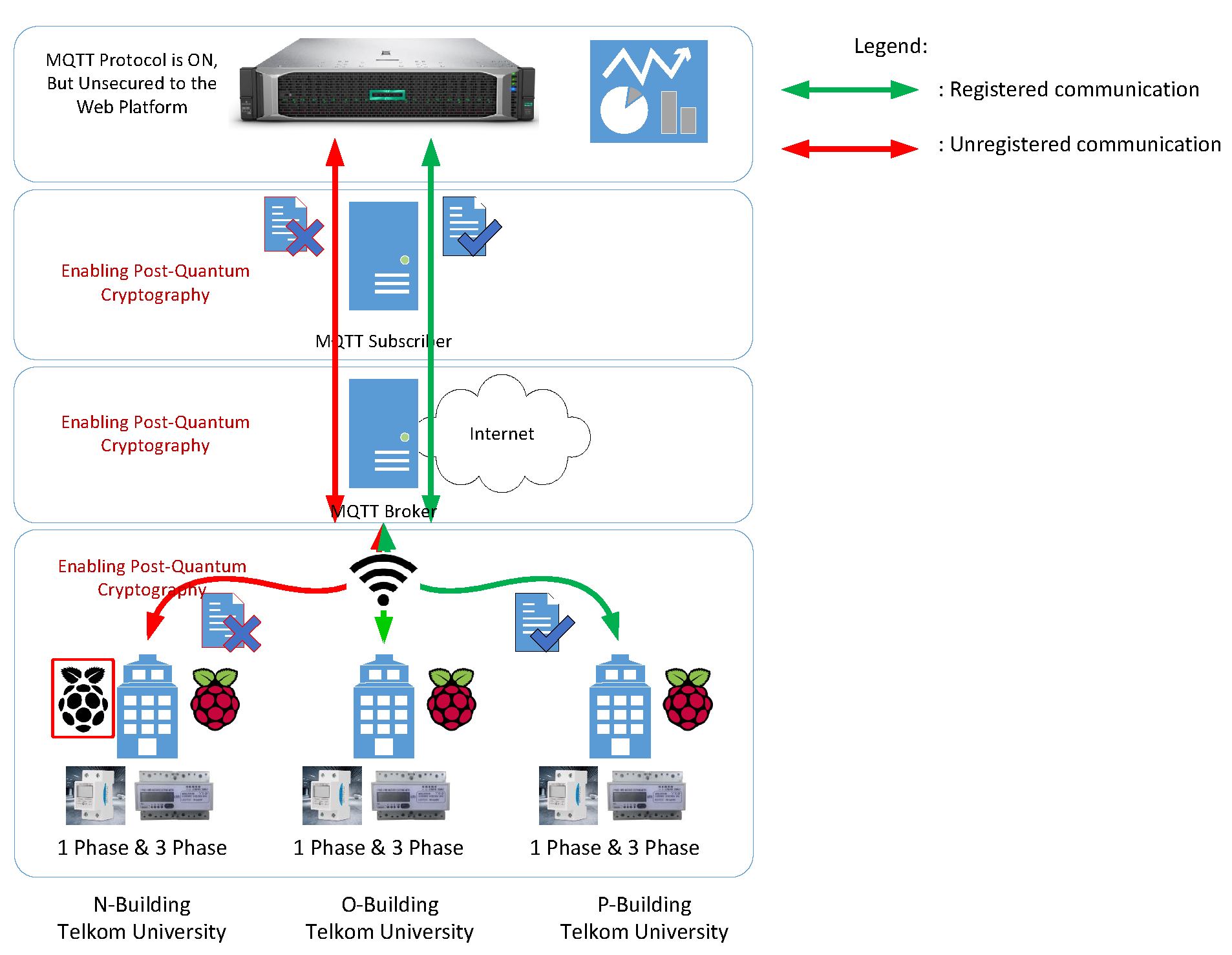
Figure 4.
Analyzing the secured topology in 1-phase.
Figure 4.
Analyzing the secured topology in 1-phase.
Figure 5.
Device threats and attack scenarios.
Figure 5.
Device threats and attack scenarios.
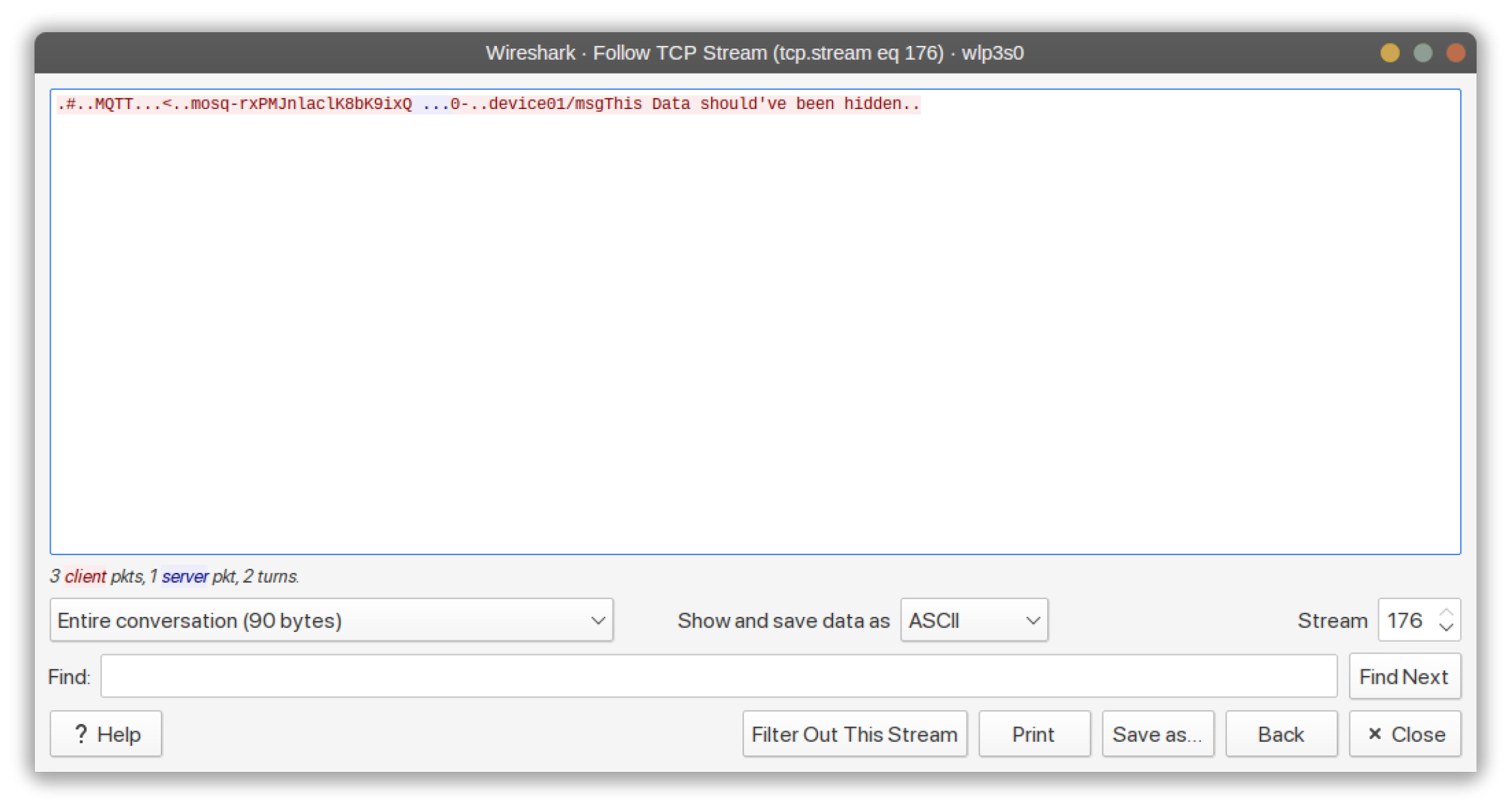
Figure 6.
Adversary performs sniffing using Wireshark on unencrypted data.
Figure 6.
Adversary performs sniffing using Wireshark on unencrypted data.
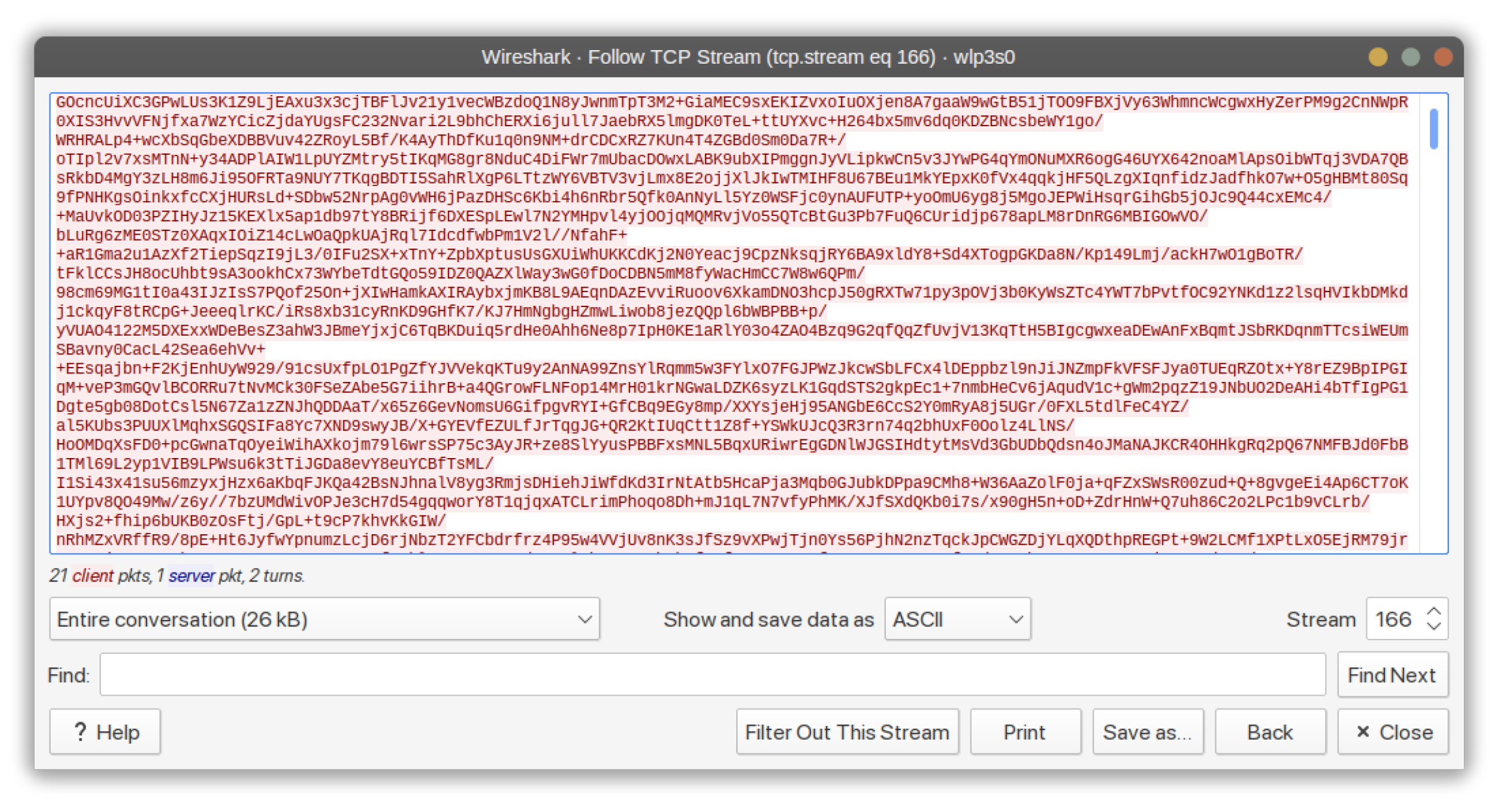
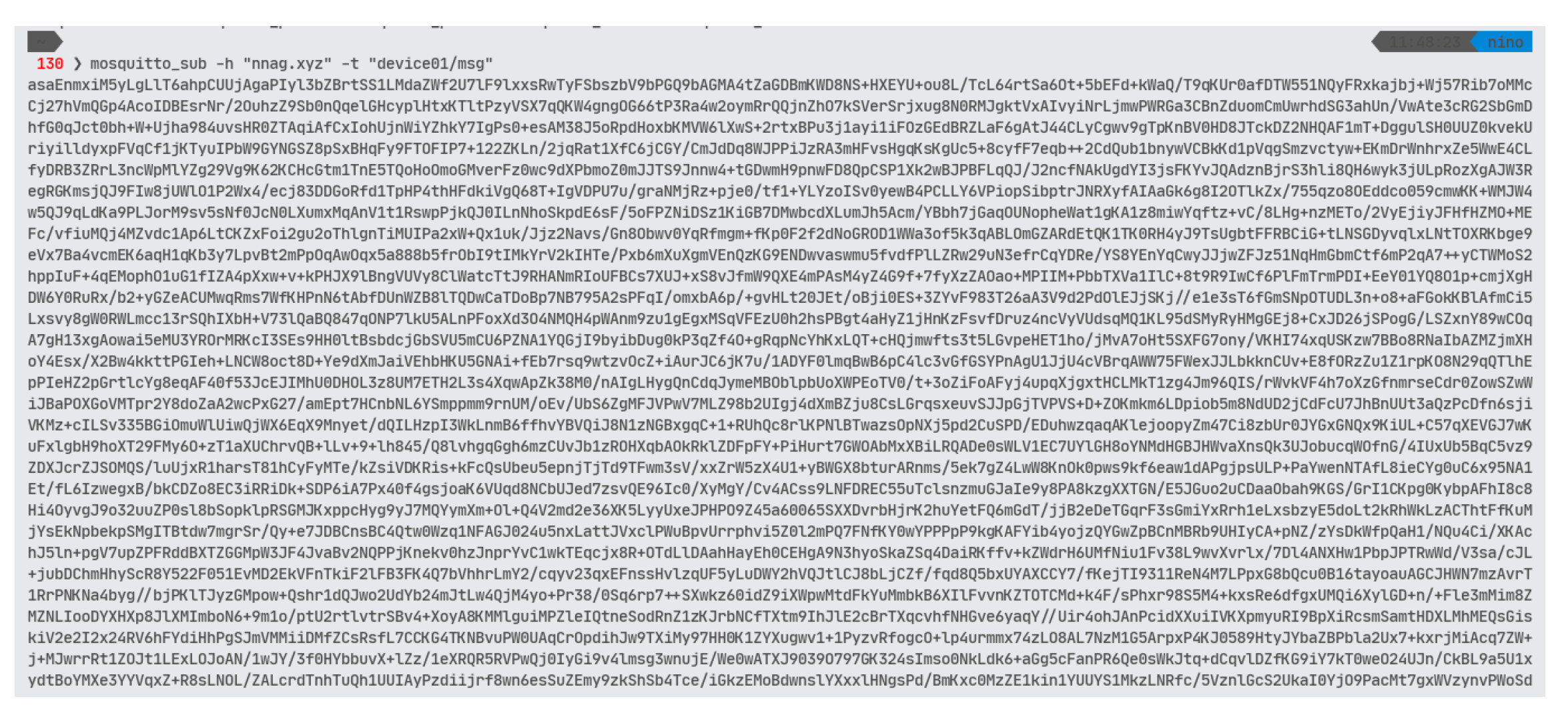
Figure 7.
Sniffed Publisher NTRU-Encrypted Payload on Wireshark.
Figure 7.
Sniffed Publisher NTRU-Encrypted Payload on Wireshark.
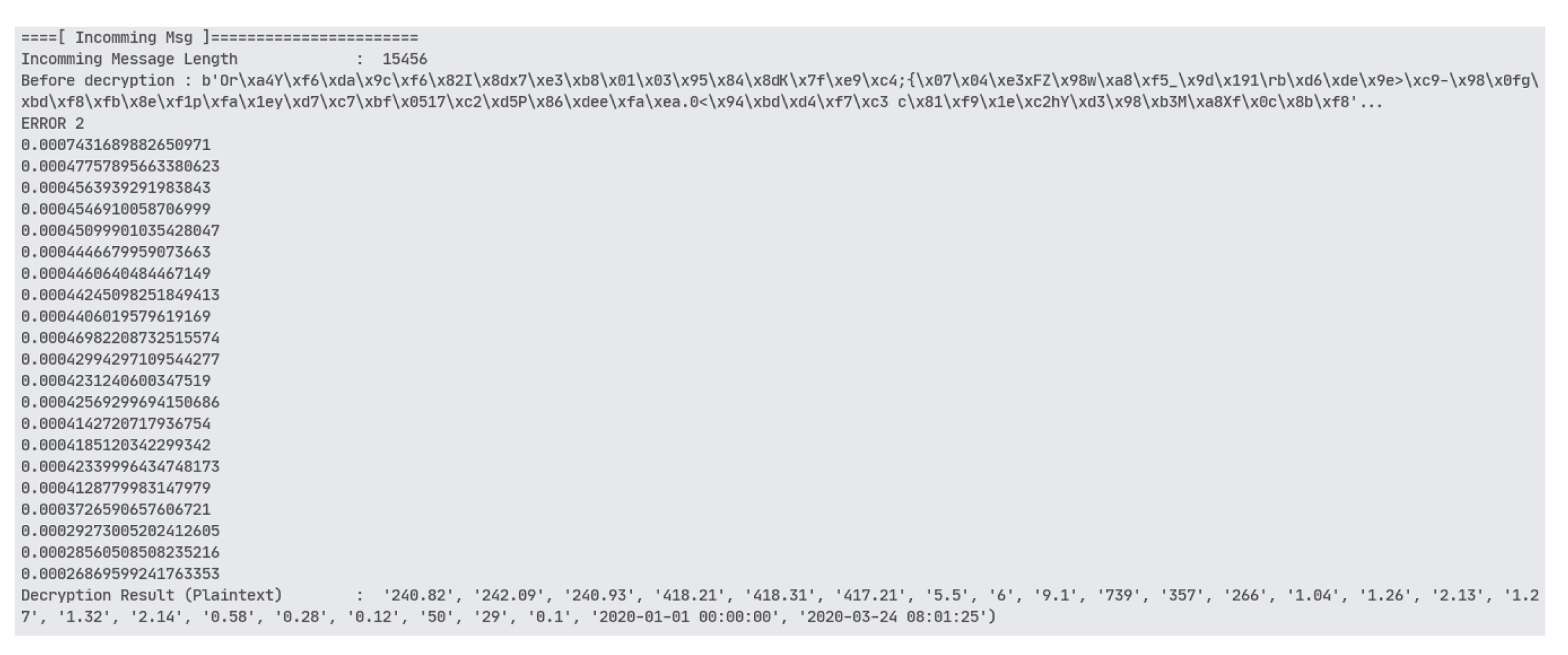
Figure 8.
Data transmission between subscribers and publishers occurs with the correct keys (private key and public key).
Figure 8.
Data transmission between subscribers and publishers occurs with the correct keys (private key and public key).
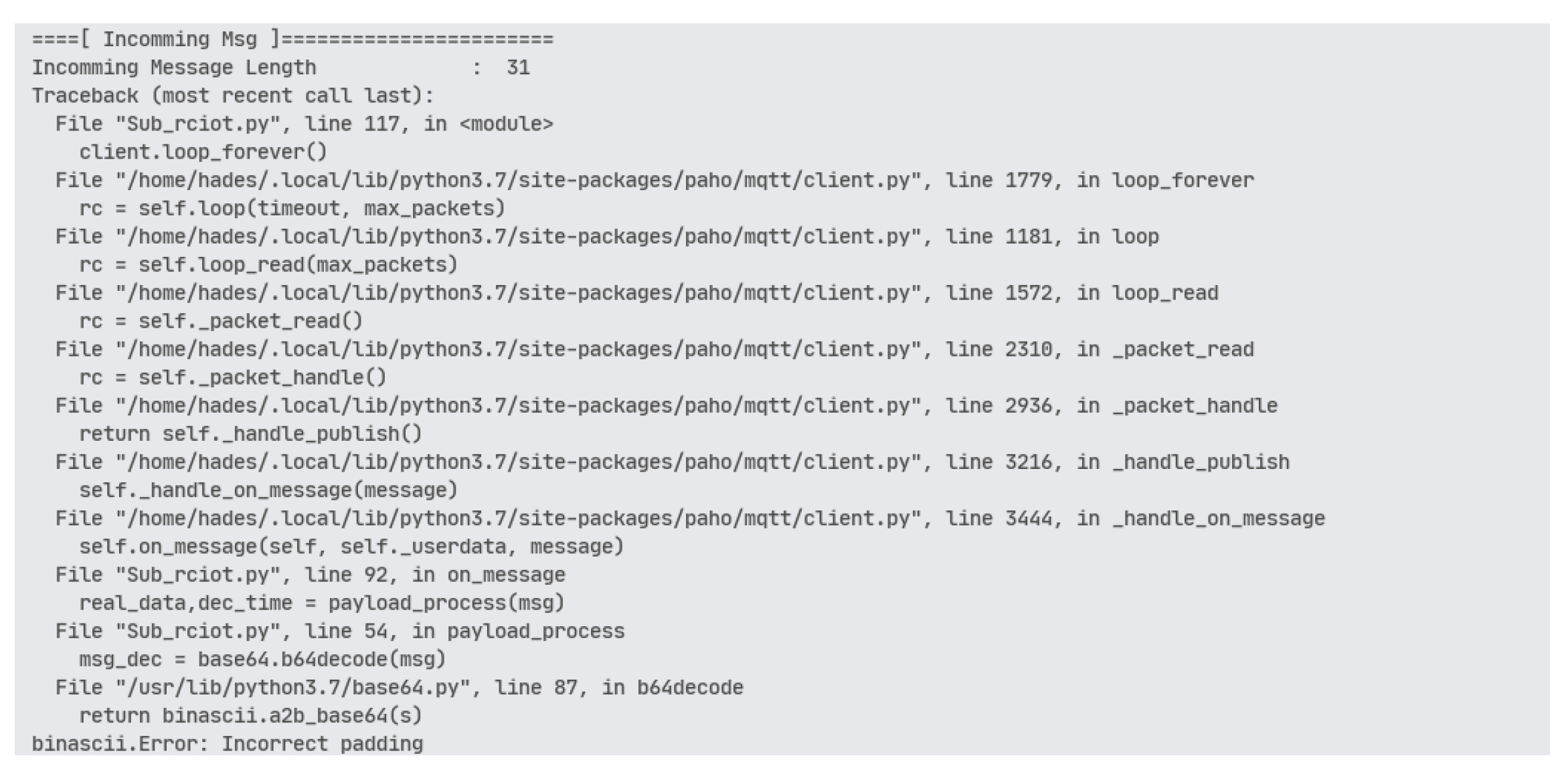
Figure 9.
Subscriber trying to receive a payload from the publisher with the wrong public key.
Figure 9.
Subscriber trying to receive a payload from the publisher with the wrong public key.
Figure 10.
Subscriber trying to subscribe using the wrong private key.
Figure 10.
Subscriber trying to subscribe using the wrong private key.
Figure 11.
Attacks to data integrity in the publisher’s devices.
Figure 11.
Attacks to data integrity in the publisher’s devices.
Figure 12.
The firewall rules on the broker’s devices.
Figure 12.
The firewall rules on the broker’s devices.
Figure 13.
Devices successfully delivered the payload (whitelisted).
Figure 13.
Devices successfully delivered the payload (whitelisted).
Figure 14.
Devices not on the whitelist fail the transmission process.
Figure 14.
Devices not on the whitelist fail the transmission process.
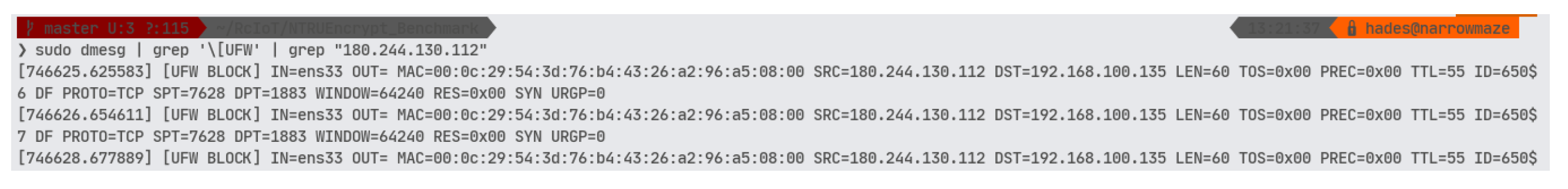
Figure 15.
Log of the firewall on the broker thwarting payload delivery.
Figure 15.
Log of the firewall on the broker thwarting payload delivery.
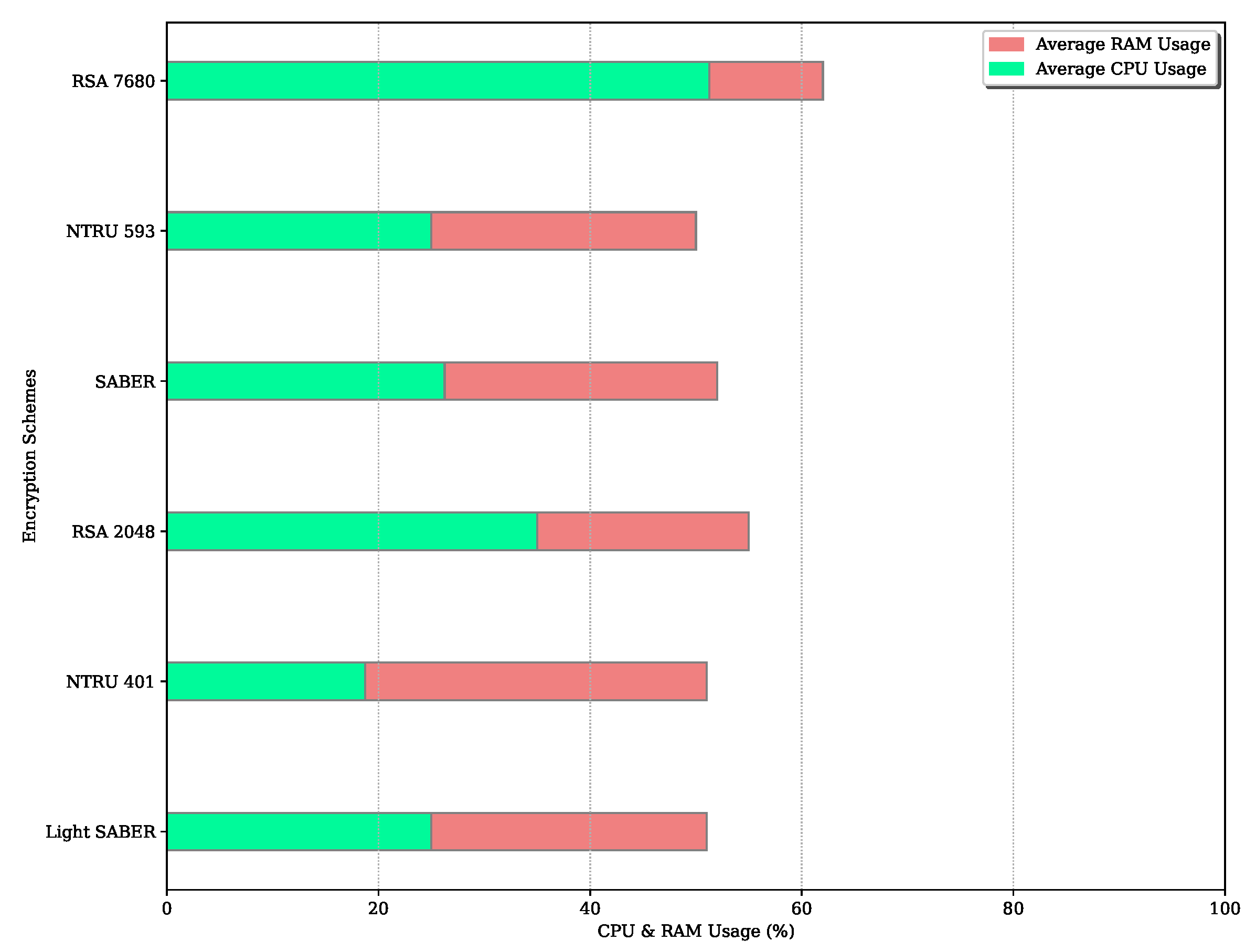
Figure 16.
Average CPU andRAM Usage for the Encryption Process.
Figure 16.
Average CPU andRAM Usage for the Encryption Process.
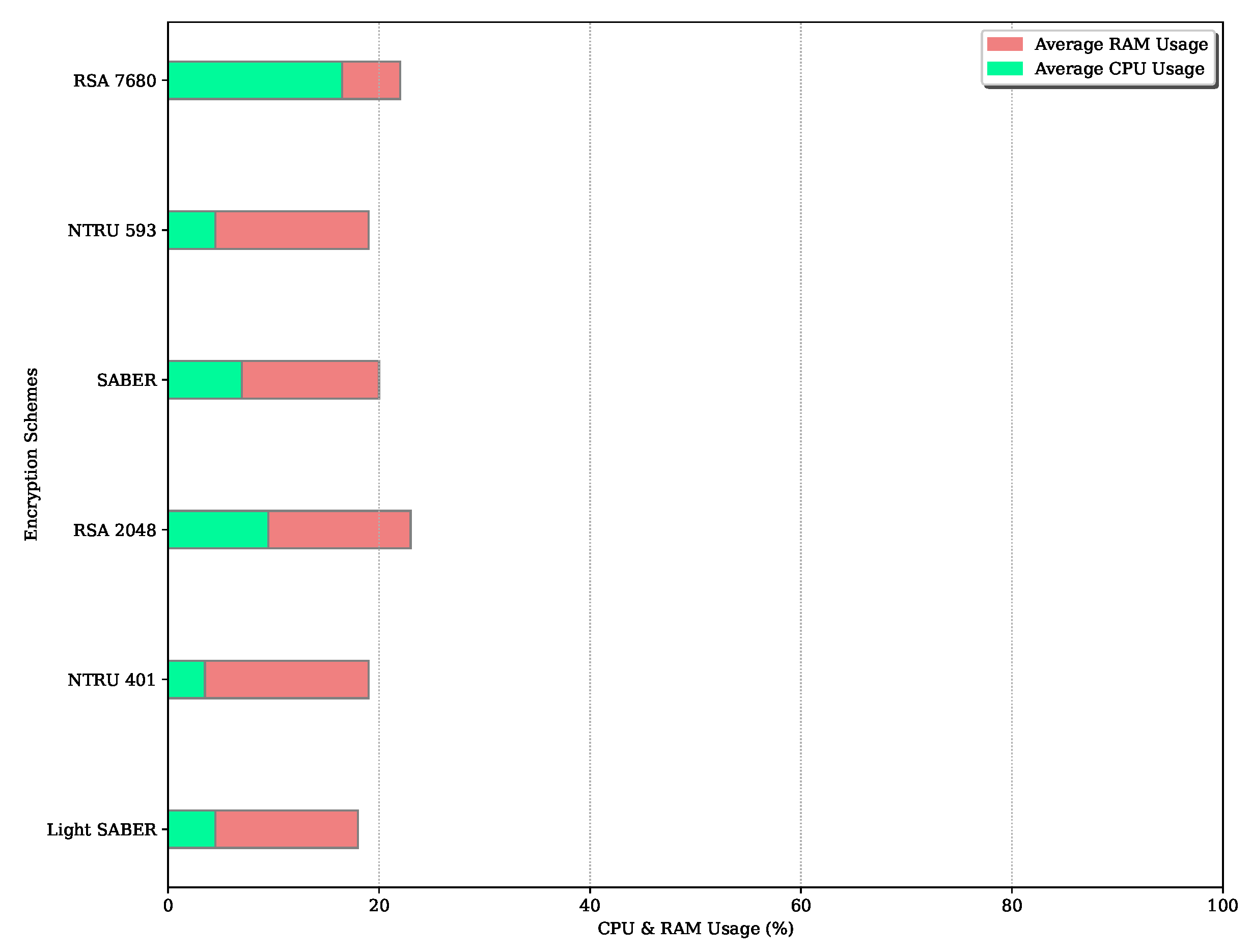
Figure 17.
Average CPU and RAM Usage for the Decryption Process.
Figure 17.
Average CPU and RAM Usage for the Decryption Process.
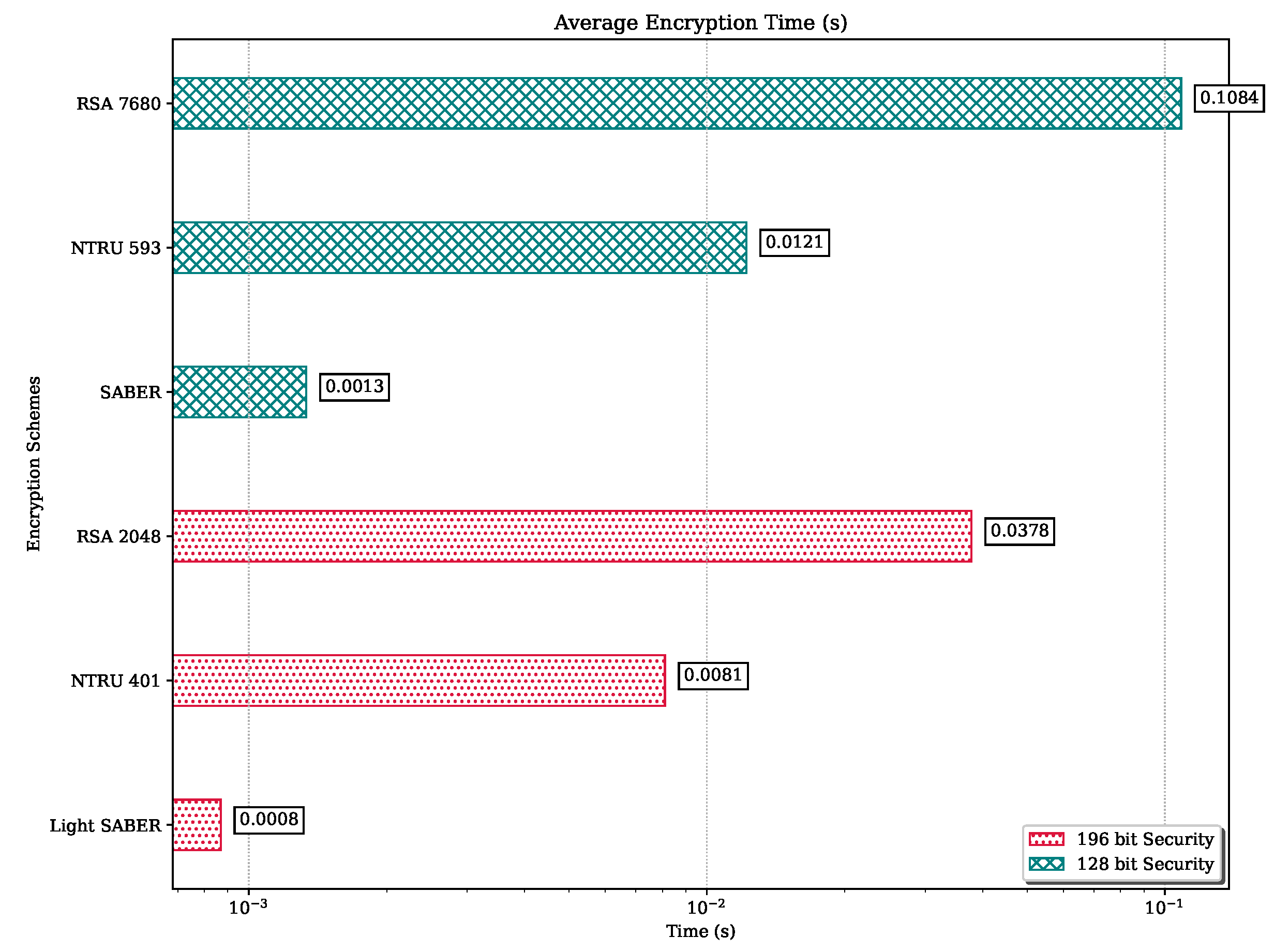
Figure 18.
Encryption Average Time for Publisher.
Figure 18.
Encryption Average Time for Publisher.
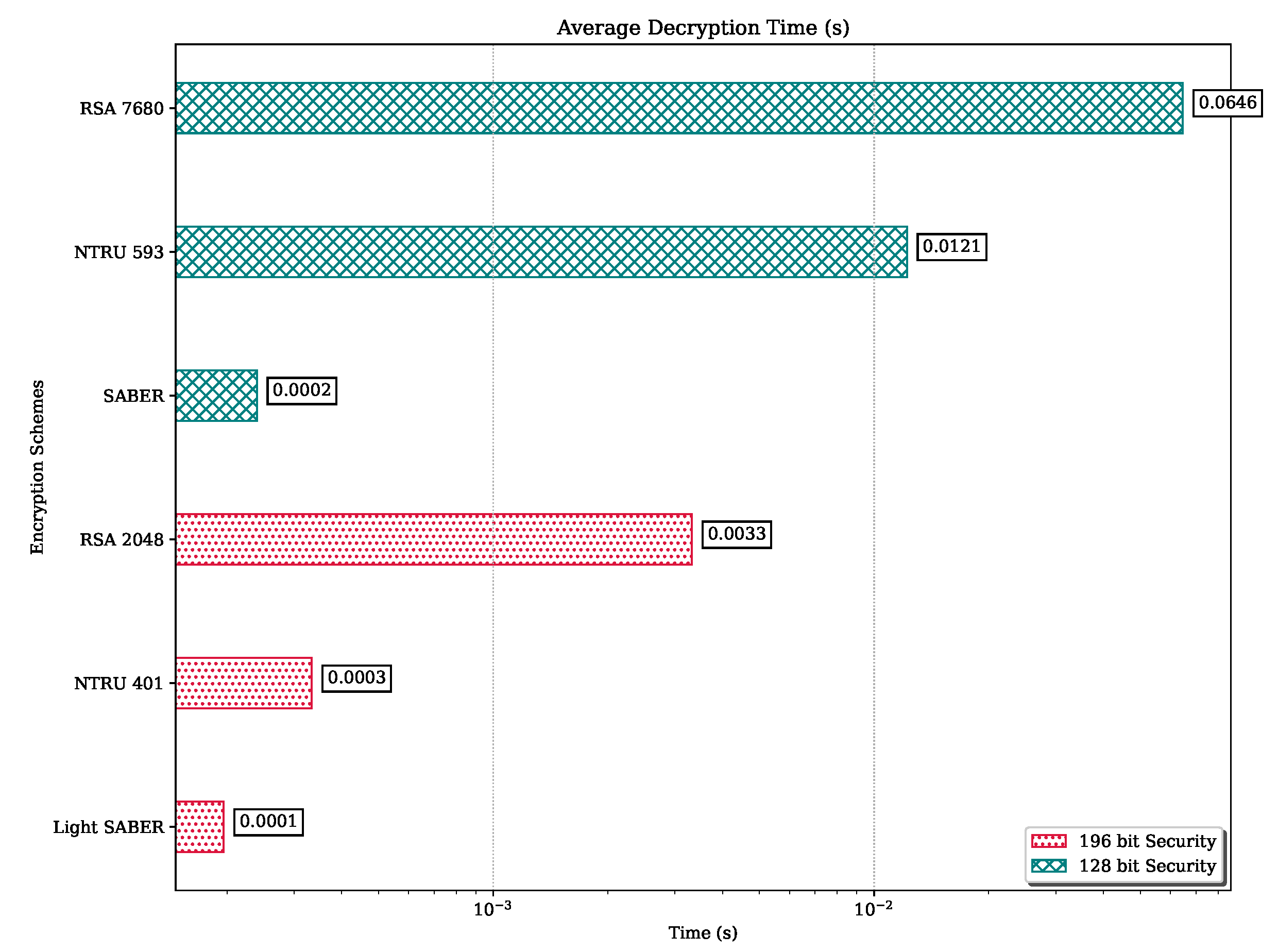
Figure 19.
Decryption Average Time for Subscriber.
Figure 19.
Decryption Average Time for Subscriber.
Figure 20.
Encryption Time.
Figure 20.
Encryption Time.
Figure 21.
Decryption Time.
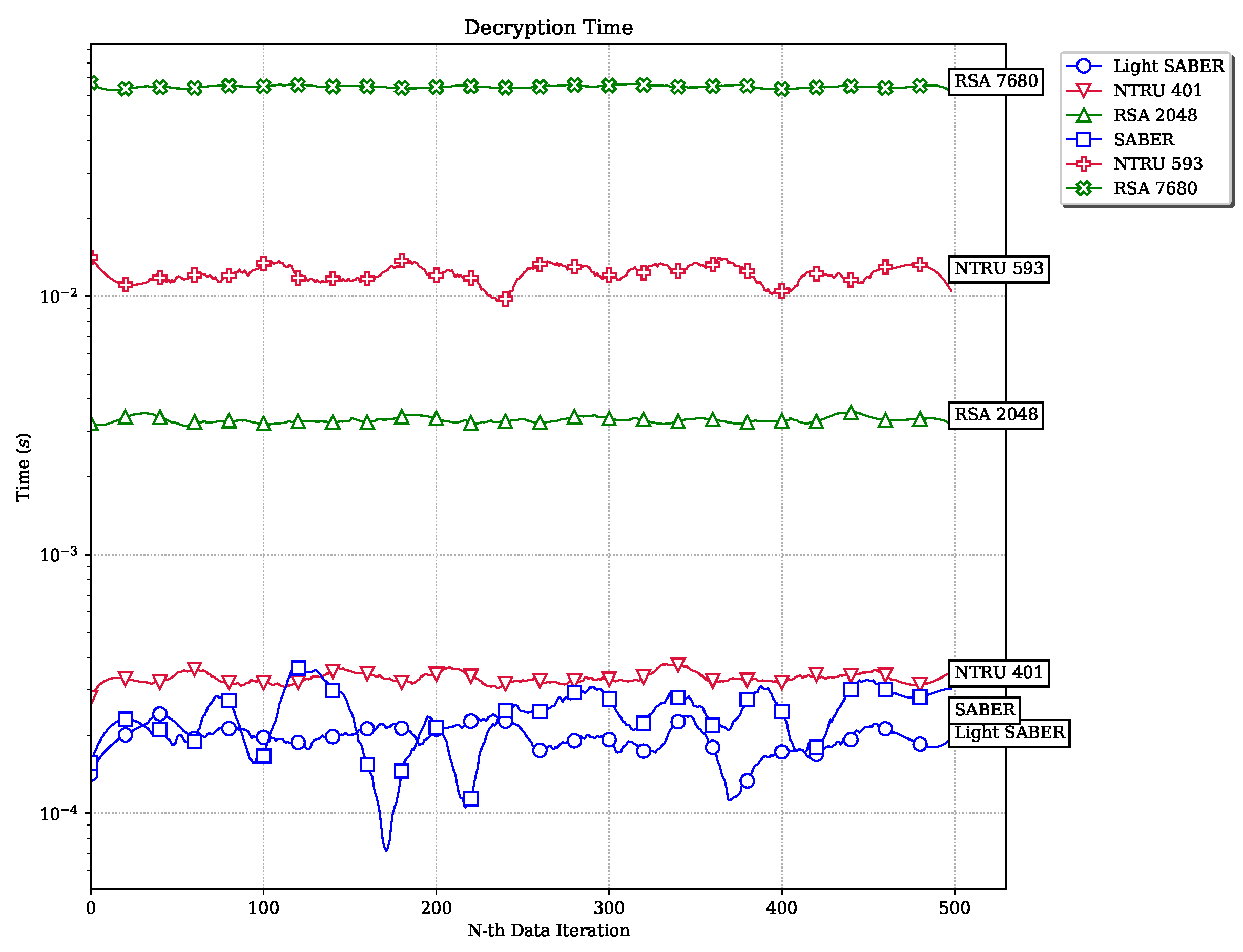
Figure 21.
Decryption Time.
Table 1.
Public-Key Encryption (PKE) schemes.
Table 1.
Public-Key Encryption (PKE) schemes.
| Security Level | Scheme | Artifact Sizes (byte) |
|---|
| |
|---|
| Moderate: 128-bit | RSA 2048 | 1678 | 450 |
| NTRU 401 | 557 | 607 |
| Light SABER | 1568 | 672 |
| High: 196-bit | RSA 7680 | 5972 | 1404 |
| NTRU 593 | 821 | 891 |
| SABER | 2304 | 992 |
Table 2.
SABER’s Security Level.
Table 2.
SABER’s Security Level.
| Scheme | l | n | q | p | T | | Security | |
|---|
| Light SABER | 2 | 256 | | | | 10 | NIST-I | |
| SABER | 3 | 256 | | | | 10 | NIST-II | |
| Fire SABER | 4 | 256 | | | | 10 | NIST-V | |
Table 3.
RSA’s Parameters.
Table 3.
RSA’s Parameters.
| Notation | Definition |
|---|
| Choose two distinct prime numbers |
| N | The modulus for both the public and private keys |
| Carmichael’s totient function for kept secret p and q |
| Computing the greatest common divisor of two prime numbers |
| Public key that has been released |
| Secret key that will be used |
Table 4.
NTRU’s Parameters.
Table 4.
NTRU’s Parameters.
| Notation | Definition |
|---|
| Integers |
| Ring parameters [Equation (1)] |
| p | Message space modulus. |
| Non-zero coefficient counts for product form polynomial terms |
| Non-zero coefficient counts for private key components g |
| Message representative Hamming weight constraint |
Table 5.
SABER’s Parameters.
Table 5.
SABER’s Parameters.
| Notation | Definition |
|---|
| Choose two distinct prime numbers |
| N | The modulus for both the public and private keys |
| Carmichael’s totient function for kept secret (p and q) |
| Computing the greatest common divisor of two prime numbers |
| Public key that has been released |
| Secret key that will be used |
Table 6.
Data Stream from 1-Phase Example.
Table 6.
Data Stream from 1-Phase Example.
| 1-Phase Stream Data |
| "4438ca6fc2a575cfab4fa4f1d4569964", "2022-02-28", "13:59:07", 215.4, 0.03, 3.185766, 5.622129, 6.462, 0.493, 50, 1.49 |
Table 7.
Data Stream from 3-Phase Example.
Table 7.
Data Stream from 3-Phase Example.
| 3-Phase Stream Data |
| ’6cc5dc0059d39c5392784721c78d4bb3’, ’2022-04-13’, ’11:22:03’, ’223.8’, ’223.8’, ’0.0’, ’1.70’, ’3.50’, ’0.00’, ’0.31’, ’0.63’, ’0.00’, ’0.31’, ’0.07’, ’0.35’, ’0.00’, ’0.42’, ’0.31’, ’0.71’, ’0.00’, ’0.52’, ’0.22’, ’0.50’, ’0.31’, ’19265.00’, ’11065.00’, ’30331.00’, ’50.00’ |
Table 8.
The 1-Phase Data Specification.
Table 8.
The 1-Phase Data Specification.
| Parameter | Description | Unit |
|---|
| token | Data Token | - |
| date | Monitoring Date | - |
| time | Monitoring Time | - |
| V | Voltage (V) | V |
| I | Current | A |
| P | Power | Watt |
| Q | Reactive Power (VAr) | VAr |
| S | Appearance Power (VA) | VA |
| PF | Energy (kWh) | - |
| F | Frequency (Hz) | Hz |
| E | Total Energy (kWh) | kWh |
Table 9.
The 3-Phase Data Specification.
Table 9.
The 3-Phase Data Specification.
| Parameter | Description | Measure Unit |
|---|
| token | Transmission Token | - |
| date | Monitoring Date | - |
| time | Monitoring Time | - |
| Voltage Phase R | V |
| Voltage Phase S | V |
| Voltage Phase T | V |
| Current Phase R | A |
| Current Phase S | A |
| Current Phase T | A |
| Reactive Power R | VAr |
| Reactive Power S | VAr |
| Reactive Power T | VAr |
| Reactive Power Total | VAr |
| Active Power R | Watt |
| Active Power S | Watt |
| Active Power T | Watt |
| Active Power Total | Watt |
| Appearance Power R | VA |
| Appearance Power S | VA |
| Appearance Power T | VA |
| Appearance Power Total | VA |
| Power Factor R | - |
| Power Factor S | - |
| Power Factor T | - |
| Energy Power | kWh |
| Forwarded Energy | kWh |
| Total Energy | kWh |
| Frequency | Hz |
Table 10.
Set of Multipliers for Each of The Target PKEs.
Table 10.
Set of Multipliers for Each of The Target PKEs.
| System | Parameter Set | Type | Set of Multipliers |
|---|
| NTRU | hps2048401 | Quotient | |
| NTRU | hps2048593 | Quotient | |
| saber | main | Product | |
| saber | fire | Product | |
Table 11.
Distribution of Short Elements for Each of The Target PKEs.
Table 11.
Distribution of Short Elements for Each of The Target PKEs.
| System | Parameter Set | Short Element |
|---|
| NTRU | hps2048401 | |
| NTRU | hps2048593 | |
| SABER | main | |
| SABER | fire | |
Table 12.
An Approximation Key Offset of the Noisy or Rounded Product NTRU PKEs.
Table 12.
An Approximation Key Offset of the Noisy or Rounded Product NTRU PKEs.
| System | Parameter Set | Key Offset |
|---|
| NTRU | hps2048401 | |
| NTRU | hps2048593 | |
| SABER | main | |
| SABER | fire | |
Table 13.
An Approximation Cipher Offset of the Noisy or Rounded Product NTRU PKEs.
Table 13.
An Approximation Cipher Offset of the Noisy or Rounded Product NTRU PKEs.
| System | Parameter Set | Ciphertext Offset |
|---|
| NTRU | hps2048401 | not applicable |
| NTRU | hps2048593 | not applicable |
| SABER | main | |
| SABER | fire | |
Table 14.
Set of Encoded Messages for Each of The Target Product NTRU PKEs.
Table 14.
Set of Encoded Messages for Each of The Target Product NTRU PKEs.
| System | Parameter Set | Set of Encoded Messages |
|---|
| NTRU | hps2048401 | not applicable |
| NTRU | hps2048593 | not applicable |
| SABER | main | |
| SABER | fire | |
Table 15.
Firewall rule.
| Rule No. | Source | Destination | Protocol | Port | Action |
|---|
| 1 | Unregistered | Subscriber | TCP | MQTT | deny |
| 2 | Subscriber | Unregistered | TCP | MQTT | deny |
| 3 | Registered | Subscriber | TCP | MQTT | allow |
| 4 | Subscriber | Registered | TCP | MQTT | allow |
Table 16.
Encryption time (in s) between publisher and subscriber.
Table 16.
Encryption time (in s) between publisher and subscriber.
| | Moderate Security Level | High Security Level |
|---|
| N-th Data | Light SABER | NTRU 401 | RSA 2048 | SABER | NTRU 593 | RSA 7680 |
| 1 | 0.000154 | 0.0111 | 0.0307 | 0.00027 | 0.01219 | 0.1181 |
| 2 | 0.000778 | 0.0050 | 0.0487 | 0.00177 | 0.014098 | 0.1499 |
| 3 | 0.000769 | 0.0085 | 0.0264 | 0.00186 | 0.014003 | 0.1217 |
| 4 | 0.000774 | 0.0131 | 0.0348 | 0.00162 | 0.015553 | 0.1234 |
| … | … | … | … | … | … | … |
| 498 | 0.000841 | 0.0109 | 0.0448 | 0.00063 | 0.015934 | 0.1230 |
| 499 | 0.000776 | 0.0062 | 0.0236 | 0.00041 | 0.004614 | 0.1183 |
| 500 | 0.000772 | 0.0120 | 0.0493 | 0.00079 | 0.006216 | 0.0930 |
Table 17.
Decryption time (in s) between publisher and subscriber.
Table 17.
Decryption time (in s) between publisher and subscriber.
| | Moderate Security Level | High Security Level |
|---|
| N-th Data | Light SABER | NTRU 401 | RSA 2048 | SABER | NTRU 593 | RSA 7680 |
| 1 | 0.00004 | 0.00029 | 0.00336 | 0.00006 | 0.01219 | 0.07623 |
| 2 | 0.00017 | 0.00029 | 0.00295 | 0.00017 | 0.01410 | 0.06292 |
| 3 | 0.00019 | 0.00030 | 0.00324 | 0.00018 | 0.01400 | 0.06221 |
| 4 | 0.00020 | 0.00029 | 0.00326 | 0.00021 | 0.01555 | 0.06240 |
| … | … | … | … | … | … | … |
| 498 | 0.00017 | 0.00031 | 0.00320 | 0.00030 | 0.01593 | 0.06443 |
| 499 | 0.00017 | 0.00031 | 0.00330 | 0.00008 | 0.00461 | 0.06283 |
| 500 | 0.00023 | 0.00047 | 0.00346 | 0.00051 | 0.00622 | 0.06269 |